mirror of
https://github.com/HackTricks-wiki/hacktricks.git
synced 2025-10-10 18:36:50 +00:00
93 lines
5.8 KiB
Markdown
93 lines
5.8 KiB
Markdown
# 135, 593 - Pentesting MSRPC
|
|
|
|
{{#include ../banners/hacktricks-training.md}}
|
|
|
|
## Basic Information
|
|
|
|
Protokali ya Microsoft Remote Procedure Call (MSRPC), mfano wa mteja-server unaowezesha programu kuomba huduma kutoka kwa programu iliyoko kwenye kompyuta nyingine bila kuelewa maelezo ya mtandao, ilitokana awali na programu za chanzo wazi na baadaye ikakuzwa na kupewa hakimiliki na Microsoft.
|
|
|
|
Mchoro wa mwisho wa RPC unaweza kufikiwa kupitia bandari ya TCP na UDP 135, SMB kwenye TCP 139 na 445 (ikiwa na kikao kisicho na thamani au kilichothibitishwa), na kama huduma ya wavuti kwenye bandari ya TCP 593.
|
|
```
|
|
135/tcp open msrpc Microsoft Windows RPC
|
|
```
|
|
## Jinsi MSRPC inavyofanya kazi?
|
|
|
|
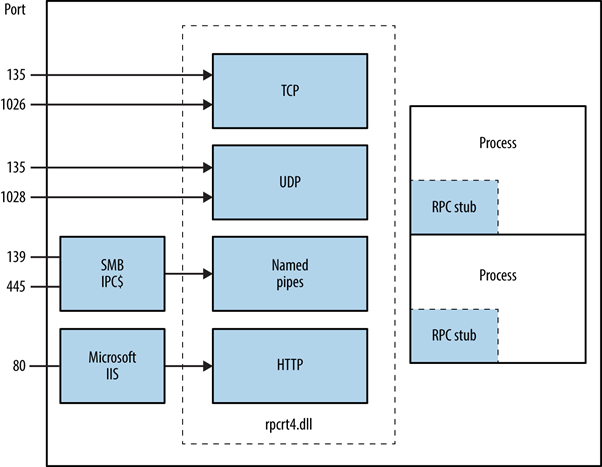
Iliyanzishwa na programu ya mteja, mchakato wa MSRPC unahusisha kuita utaratibu wa stub wa ndani ambao kisha unashirikiana na maktaba ya wakati wa mteja kuandaa na kupeleka ombi kwa seva. Hii inajumuisha kubadilisha vigezo kuwa katika muundo wa kawaida wa Uwakilishi wa Takwimu za Mtandao. Chaguo la itifaki ya usafirishaji linatolewa na maktaba ya wakati wa ikiwa seva iko mbali, kuhakikisha kuwa RPC inatumwa kupitia safu ya mtandao.
|
|
|
|
|
|
|
|
## **Kutambua Huduma za RPC Zilizofichuliwa**
|
|
|
|
Ufunuo wa huduma za RPC kupitia TCP, UDP, HTTP, na SMB unaweza kubainishwa kwa kuuliza huduma ya mlocator ya RPC na mwisho mmoja mmoja. Zana kama rpcdump husaidia katika kutambua huduma za RPC za kipekee, zinazoonyeshwa na thamani za **IFID**, zikifunua maelezo ya huduma na viunganisho vya mawasiliano:
|
|
```
|
|
D:\rpctools> rpcdump [-p port] <IP>
|
|
**IFID**: 5a7b91f8-ff00-11d0-a9b2-00c04fb6e6fc version 1.0
|
|
Annotation: Messenger Service
|
|
UUID: 00000000-0000-0000-0000-000000000000
|
|
Binding: ncadg_ip_udp:<IP>[1028]
|
|
```
|
|
Upatikanaji wa huduma ya RPC locator umewezeshwa kupitia protokali maalum: ncacn_ip_tcp na ncadg_ip_udp kwa upatikanaji kupitia bandari 135, ncacn_np kwa muunganisho wa SMB, na ncacn_http kwa mawasiliano ya RPC ya mtandao. Amri zifuatazo zinaonyesha matumizi ya moduli za Metasploit kukagua na kuingiliana na huduma za MSRPC, hasa zikizingatia bandari 135:
|
|
```bash
|
|
use auxiliary/scanner/dcerpc/endpoint_mapper
|
|
use auxiliary/scanner/dcerpc/hidden
|
|
use auxiliary/scanner/dcerpc/management
|
|
use auxiliary/scanner/dcerpc/tcp_dcerpc_auditor
|
|
rpcdump.py <IP> -p 135
|
|
```
|
|
All options except `tcp_dcerpc_auditor` are specifically designed for targeting MSRPC on port 135.
|
|
|
|
#### Notable RPC interfaces
|
|
|
|
- **IFID**: 12345778-1234-abcd-ef00-0123456789ab
|
|
- **Named Pipe**: `\pipe\lsarpc`
|
|
- **Description**: Kiolesura cha LSA, kinachotumika kuorodhesha watumiaji.
|
|
- **IFID**: 3919286a-b10c-11d0-9ba8-00c04fd92ef5
|
|
- **Named Pipe**: `\pipe\lsarpc`
|
|
- **Description**: Kiolesura cha LSA Directory Services (DS), kinachotumika kuorodhesha maeneo na uhusiano wa kuaminiana.
|
|
- **IFID**: 12345778-1234-abcd-ef00-0123456789ac
|
|
- **Named Pipe**: `\pipe\samr`
|
|
- **Description**: Kiolesura cha LSA SAMR, kinachotumika kufikia vipengele vya umma vya database ya SAM (mfano, majina ya watumiaji) na kujaribu nywila za watumiaji bila kujali sera ya kufunga akaunti.
|
|
- **IFID**: 1ff70682-0a51-30e8-076d-740be8cee98b
|
|
- **Named Pipe**: `\pipe\atsvc`
|
|
- **Description**: Mpangaji wa kazi, unatumika kutekeleza amri kwa mbali.
|
|
- **IFID**: 338cd001-2244-31f1-aaaa-900038001003
|
|
- **Named Pipe**: `\pipe\winreg`
|
|
- **Description**: Huduma ya rejista ya mbali, inatumika kufikia na kubadilisha rejista ya mfumo.
|
|
- **IFID**: 367abb81-9844-35f1-ad32-98f038001003
|
|
- **Named Pipe**: `\pipe\svcctl`
|
|
- **Description**: Meneja wa kudhibiti huduma na huduma za seva, unatumika kuanzisha na kusitisha huduma kwa mbali na kutekeleza amri.
|
|
- **IFID**: 4b324fc8-1670-01d3-1278-5a47bf6ee188
|
|
- **Named Pipe**: `\pipe\srvsvc`
|
|
- **Description**: Meneja wa kudhibiti huduma na huduma za seva, unatumika kuanzisha na kusitisha huduma kwa mbali na kutekeleza amri.
|
|
- **IFID**: 4d9f4ab8-7d1c-11cf-861e-0020af6e7c57
|
|
- **Named Pipe**: `\pipe\epmapper`
|
|
- **Description**: Kiolesura cha DCOM, kinachotumika kwa ajili ya kujaribu nywila na ukusanyaji wa taarifa kupitia WM.
|
|
|
|
### Identifying IP addresses
|
|
|
|
Using [https://github.com/mubix/IOXIDResolver](https://github.com/mubix/IOXIDResolver), comes from [Airbus research](https://www.cyber.airbus.com/the-oxid-resolver-part-1-remote-enumeration-of-network-interfaces-without-any-authentication/) is possible to abuse the _**ServerAlive2**_ method inside the _**IOXIDResolver**_ interface.
|
|
|
|
This method has been used to get interface information as **IPv6** address from the HTB box _APT_. See [here](https://0xdf.gitlab.io/2021/04/10/htb-apt.html) for 0xdf APT writeup, it includes an alternative method using rpcmap.py from [Impacket](https://github.com/SecureAuthCorp/impacket/) with _stringbinding_ (see above).
|
|
|
|
### Executing a RCE with valid credentials
|
|
|
|
It is possible to execute remote code on a machine, if the credentials of a valid user are available using [dcomexec.py](https://github.com/fortra/impacket/blob/master/examples/dcomexec.py) from impacket framework.
|
|
|
|
**Remember to try with the different objects available**
|
|
|
|
- ShellWindows
|
|
- ShellBrowserWindow
|
|
- MMC20
|
|
|
|
## Port 593
|
|
|
|
The **rpcdump.exe** from [rpctools](https://resources.oreilly.com/examples/9780596510305/tree/master/tools/rpctools) can interact with this port.
|
|
|
|
## References
|
|
|
|
- [https://www.cyber.airbus.com/the-oxid-resolver-part-1-remote-enumeration-of-network-interfaces-without-any-authentication/](https://www.cyber.airbus.com/the-oxid-resolver-part-1-remote-enumeration-of-network-interfaces-without-any-authentication/)
|
|
- [https://www.cyber.airbus.com/the-oxid-resolver-part-2-accessing-a-remote-object-inside-dcom/](https://www.cyber.airbus.com/the-oxid-resolver-part-2-accessing-a-remote-object-inside-dcom/)
|
|
- [https://0xffsec.com/handbook/services/msrpc/](https://0xffsec.com/handbook/services/msrpc/)
|
|
|
|
{{#include ../banners/hacktricks-training.md}}
|